Communication Analysis and Privacy in CAI Based on Data Mining and Federated Learning
Abstract
1. Introduction
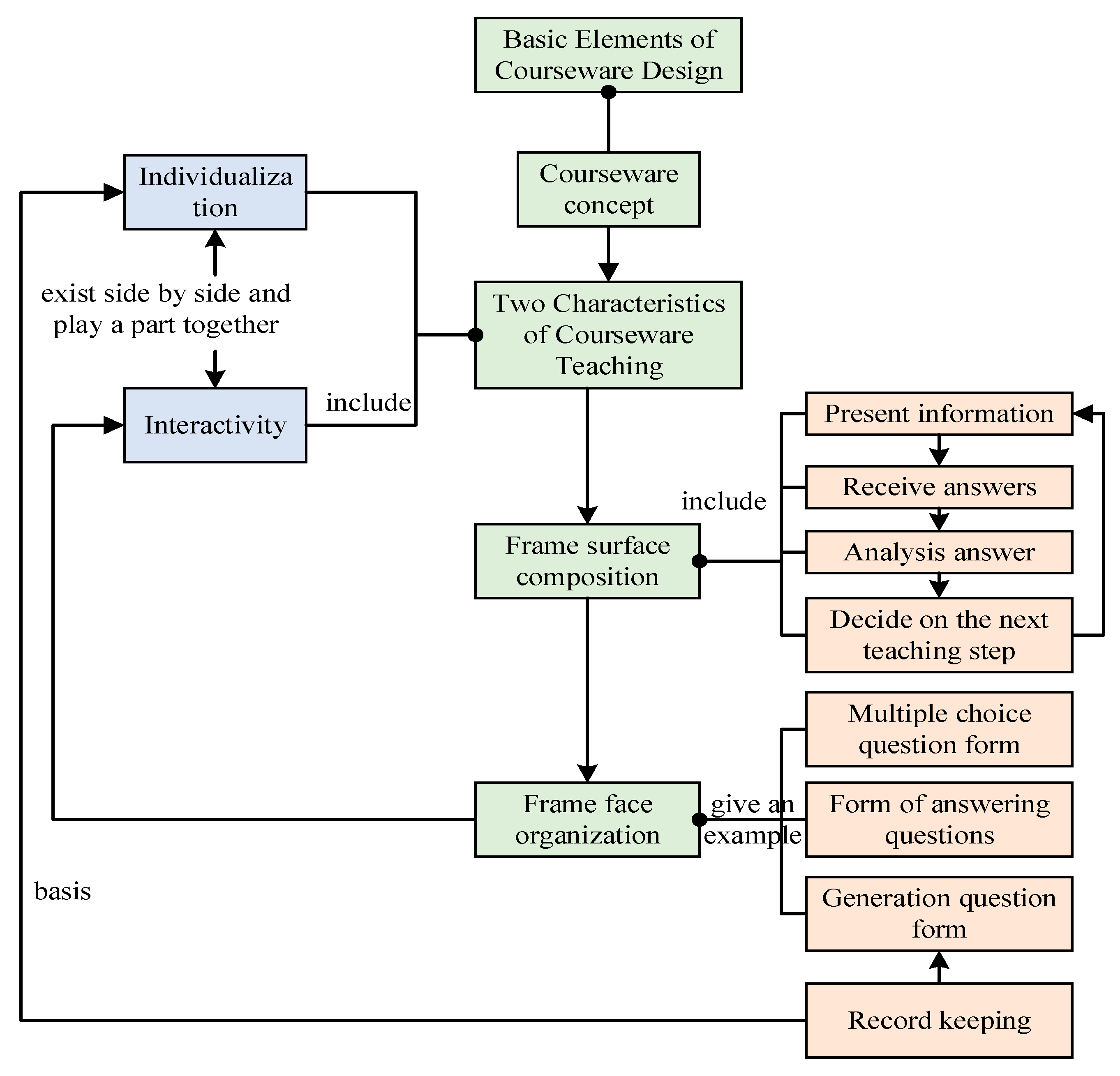
2. Related Works
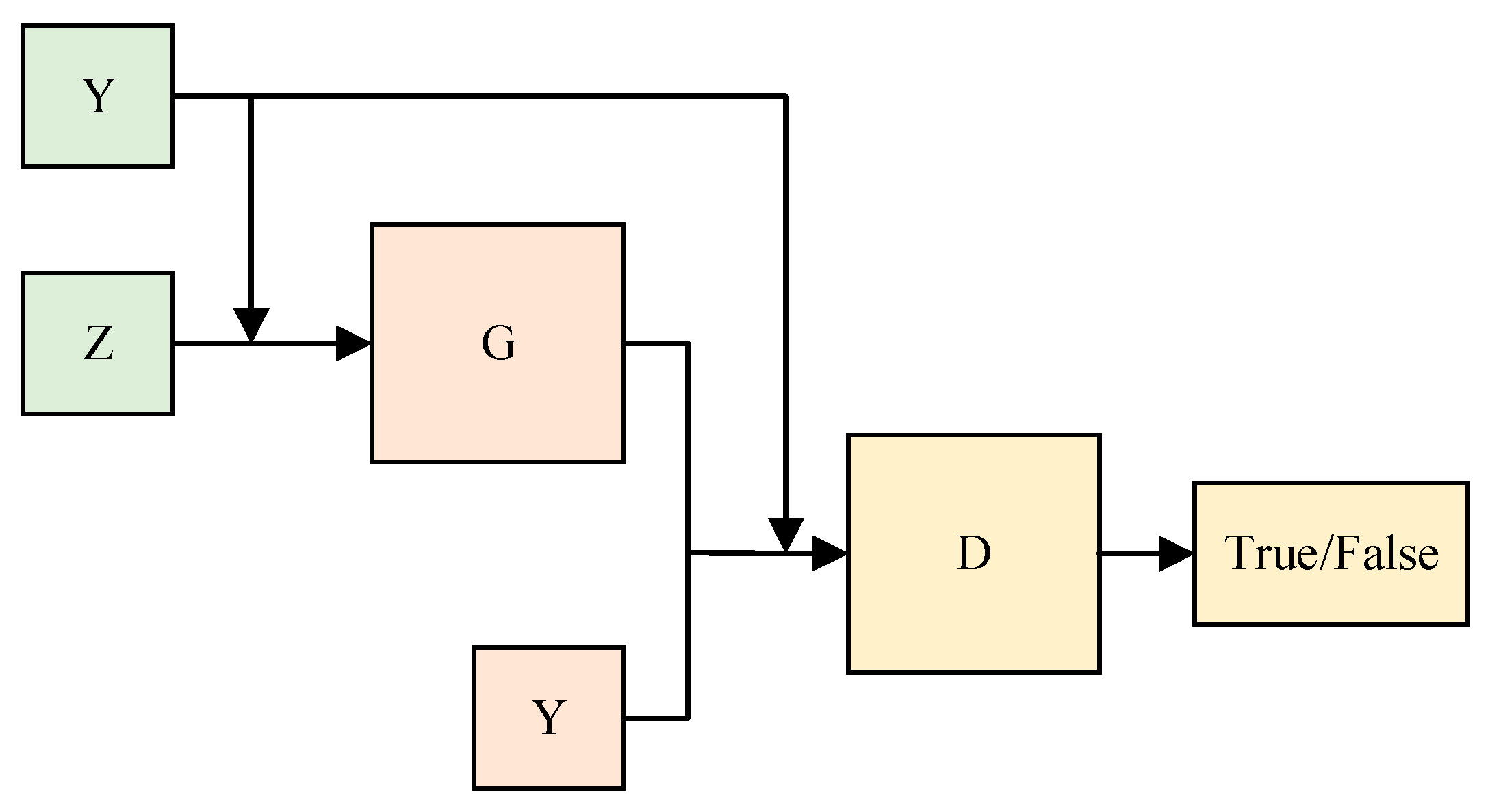
3. Optimization of Smith–Regan Model
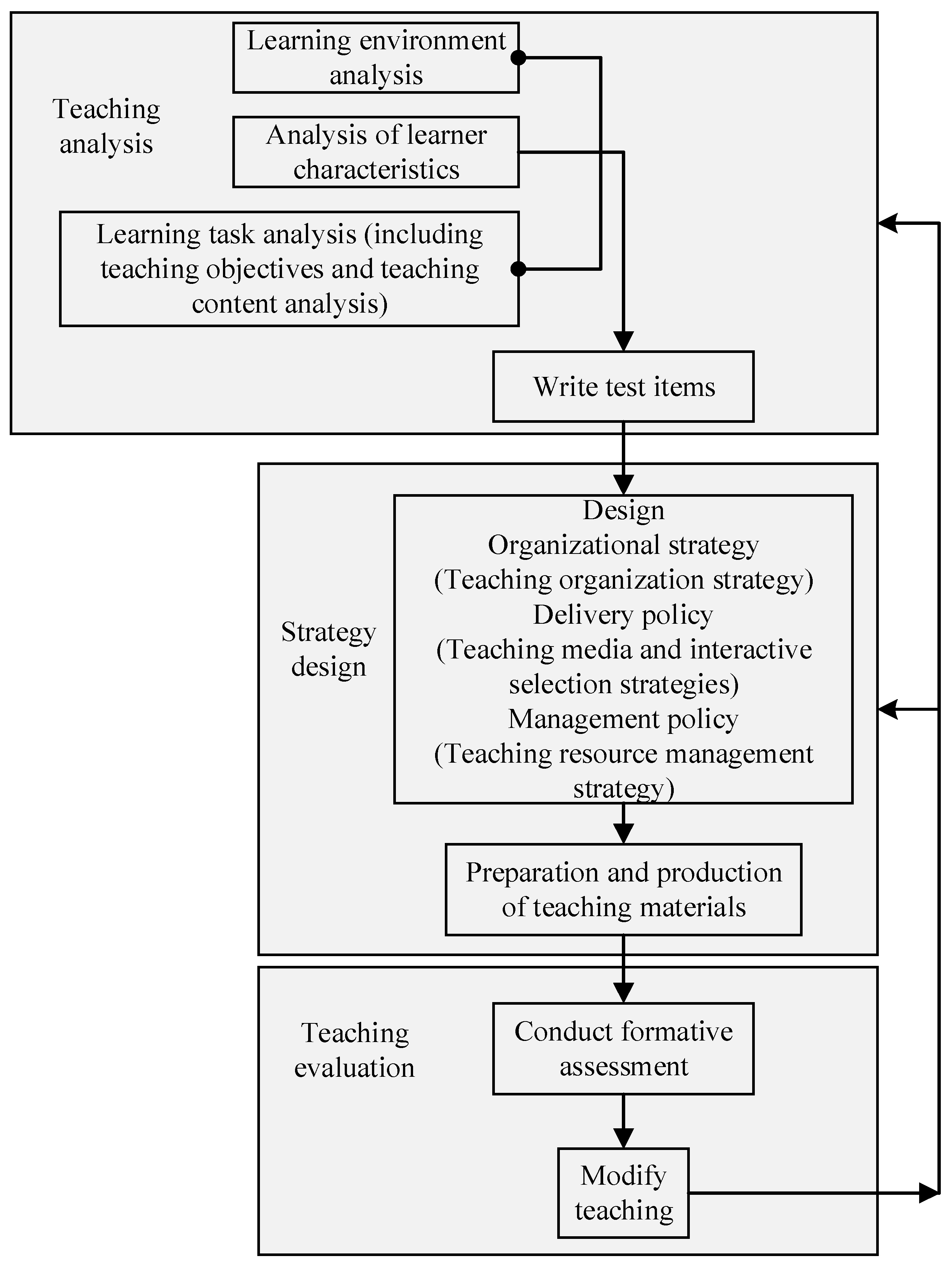
4. Methods
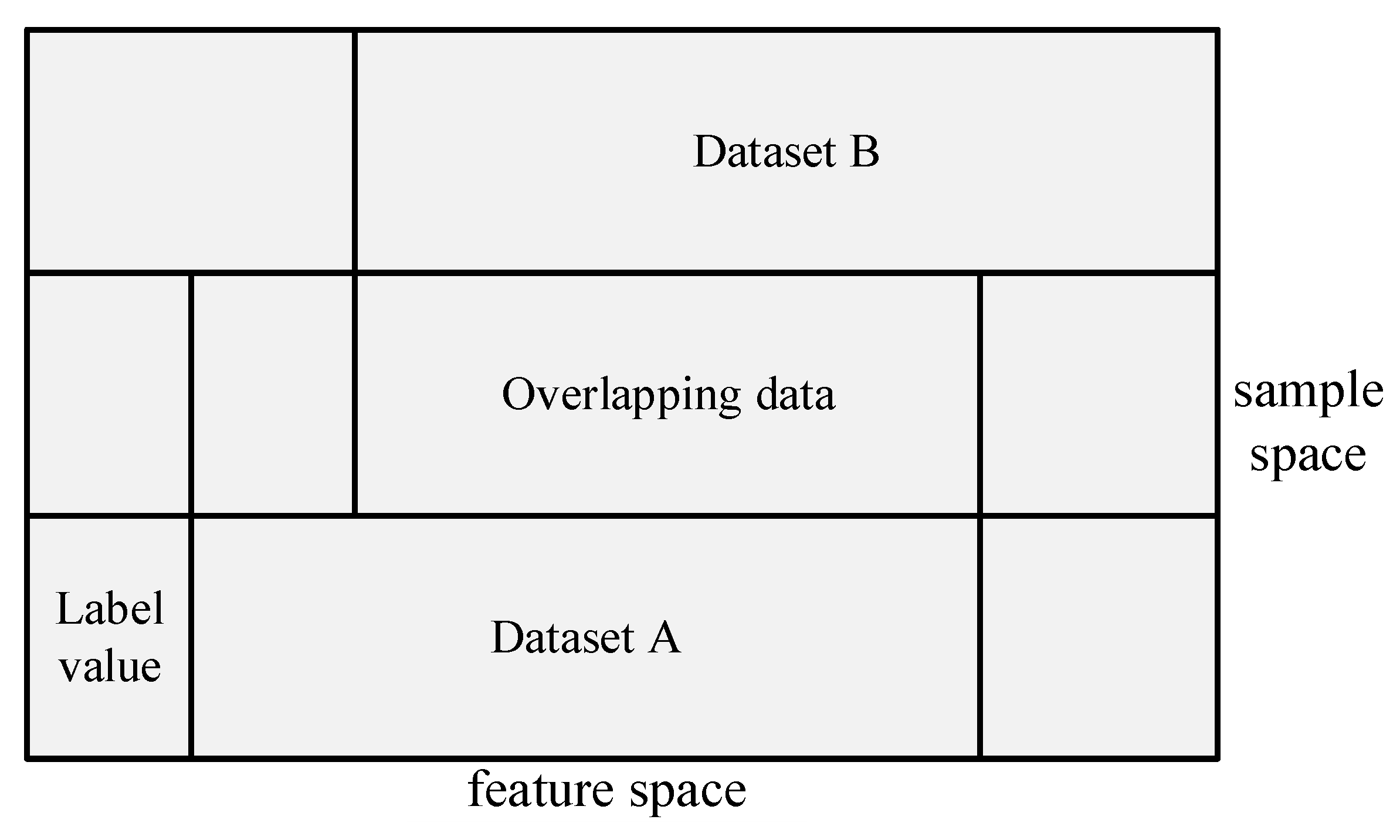
4.1. Data Selection
4.2. Research Assumptions
5. Case Study
5.1. Testing of System Software
5.2. Practical Application of the System
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Xiong, Z.; Cai, Z.; Takabi, D.; Li, W. Privacy threat and defense for federated learning with non-iid data in AIoT. IEEE Trans. Ind. Inform. 2021, 18, 1310–1321. [Google Scholar] [CrossRef]
- Pang, J.; Huang, Y.; Xie, Z.; Li, J.; Cai, Z. Collaborative city digital twin for the COVID-19 pandemic: A federated learning solution. Tsinghua Sci. Technol. 2021, 26, 759–771. [Google Scholar] [CrossRef]
- Pang, J.; Huang, Y.; Xie, Z.; Han, Q.; Cai, Z. Realizing the heterogeneity: A self-organized federated learning framework for IoT. IEEE Internet Things J. 2020, 8, 3088–3098. [Google Scholar] [CrossRef]
- Li, D.; Luo, Z.; Cao, B. Blockchain-based federated learning methodologies in smart environments. Clust. Comput. 2022, 25, 2585–2599. [Google Scholar] [CrossRef]
- Liu, D.; Simeone, O. Privacy for free: Wireless federated learning via uncoded transmission with adaptive power control. IEEE J. Sel. Areas Commun. 2020, 39, 170–185. [Google Scholar] [CrossRef]
- Yin, X.; Zhu, Y.; Hu, J. A comprehensive survey of privacy-preserving federated learning: A taxonomy, review, and future directions. ACM Comput. Surv. (CSUR) 2021, 54, 131. [Google Scholar] [CrossRef]
- Zhao, B.; Fan, K.; Yang, K.; Wang, Z.; Li, H.; Yang, Y. Anonymous and privacy-preserving federated learning with industrial big data. IEEE Trans. Ind. Inform. 2021, 17, 6314–6323. [Google Scholar] [CrossRef]
- Zhou, H.; Wu, T.; Sun, K.; Zhang, C. Towards high accuracy pedestrian detection on edge gpus. Sensors 2022, 22, 5980. [Google Scholar] [CrossRef]
- Lim, W.Y.B.; Luong, N.C.; Hoang, D.T.; Jiao, Y.; Liang, Y.C.; Yang, Q.; Miao, C. Federated learning in mobile edge networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2020, 22, 2031–2063. [Google Scholar] [CrossRef]
- Yang, Q.; Liu, Y.; Cheng, Y.; Kang, Y.; Chen, T.; Yu, H. Federated learning. Synth. Lect. Artif. Intell. Mach. Learn. 2019, 13, 1–207. [Google Scholar]
- Sun, P.; Che, H.; Wang, Z.; Wang, Y.; Wang, T.; Wu, L.; Shao, H. Pain-FL: Personalized privacy-preserving incentive for federated learning. IEEE J. Sel. Areas Commun. 2021, 39, 3805–3820. [Google Scholar] [CrossRef]
- Mohamed, M.S.E.; Chang, W.T.; Tandon, R. Privacy amplification for federated learning via user sampling and wireless aggregation. IEEE J. Sel. Areas Commun. 2021, 39, 3821–3835. [Google Scholar] [CrossRef]
- Ahmed, U.; Srivastava, G.; Lin, J.C.W. A federated learning approach to frequent itemset mining in cyber-physical systems. J. Netw. Syst. Manag. 2021, 29, 42. [Google Scholar] [CrossRef]
- Rieke, N.; Hancox, J.; Li, W.; Milletari, F.; Roth, H.R.; Albarqouni, S.; Cardoso, M.J. The future of digital health with federated learning. NPJ Digit. Med. 2020, 3, 119. [Google Scholar] [CrossRef] [PubMed]
- Hu, R.; Guo, Y.; Li, H.; Pei, Q.; Gong, Y. Personalized federated learning with differential privacy. IEEE Internet Things J. 2020, 7, 9530–9539. [Google Scholar] [CrossRef]
- Li, D.; Han, D.; Weng, T.H.; Zheng, Z.; Li, H.; Liu, H.; Li, K.C. Blockchain for federated learning toward secure distributed machine learning systems: A systemic survey. Soft Comput. 2022, 26, 4423–4440. [Google Scholar] [CrossRef]
- Cheng, K.; Fan, T.; Jin, Y.; Liu, Y.; Chen, T.; Papadopoulos, D.; Yang, Q. Secureboost: A lossless federated learning framework. IEEE Intell. Syst. 2021, 36, 87–98. [Google Scholar] [CrossRef]
- Imteaj, A.; Thakker, U.; Wang, S.; Li, J.; Amini, M.H. A survey on federated learning for resource-constrained iot devices. IEEE Internet Things J. 2021, 9, 1–24. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Benslimane, A. Learning in the air: Secure federated learning for UAV-assisted crowdsensing. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1055–1069. [Google Scholar] [CrossRef]
- Kumar, R.; Khan, A.A.; Kumar, J.; Golilarz, N.A.; Zhang, S.; Ting, Y.; Wang, W. Blockchain-federated-learning and deep learning models for covid-19 detection using ct imaging. IEEE Sens. J. 2021, 21, 16301–16314. [Google Scholar] [CrossRef]
- Yin, L.; Feng, J.; Xun, H.; Sun, Z.; Cheng, X. A privacy-preserving federated learning for multiparty data sharing in social IoTs. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2706–2718. [Google Scholar] [CrossRef]
- Dayan, I.; Roth, H.R.; Zhong, A.; Harouni, A.; Gentili, A.; Abidin, A.Z.; Li, Q. Federated learning for predicting clinical outcomes in patients with COVID-19. Nat. Med. 2021, 27, 1735–1743. [Google Scholar] [CrossRef] [PubMed]
- Yang, Q. Toward responsible ai: An overview of federated learning for user-centered privacy-preserving computing. ACM Trans. Interact. Intell. Syst. (TiiS) 2021, 11, 32. [Google Scholar] [CrossRef]
- Huang, A.; Liu, Y.; Chen, T.; Zhou, Y.; Sun, Q.; Chai, H.; Yang, Q. Starfl: Hybrid federated learning architecture for smart urban computing. ACM Trans. Intell. Syst. Technol. (TIST) 2021, 12, 43. [Google Scholar] [CrossRef]
- Li, J.; Zhang, C.; Zhao, Y.; Qiu, W.; Chen, Q.; Zhang, X. Federated learning-based short-term building energy consumption prediction method for solving the data silos problem. In Building Simulation; Tsinghua University Press: Beijing, China, 2022; Volume 15, pp. 1145–1159. [Google Scholar]
- Yue, M.; Jong, M.S.-Y.; Dai, Y. Pedagogical Design of K-12 Artificial Intelligence Education: A Systematic Review. Sustainability 2022, 14, 15620. [Google Scholar] [CrossRef]
- Massaro, A.; Giannone, D.; Birardi, V.; Galiano, A.M. An Innovative Approach for the Evaluation of the Web Page Impact Combining User Experience and Neural Network Score. Future Internet 2021, 13, 145. [Google Scholar] [CrossRef]
- Yang, B.; Wei, L.; Pu, Z. Measuring and Improving User Experience Through Artificial Intelligence-Aided Design. Front. Psychol. 2020, 11, 595374. [Google Scholar] [CrossRef]
- Massaro, A.; Meuli, G.; Savino, N.; Galiano, A.M. Voice analysis rehabilitation platform based on LSTM algorithm. Int. J. Telemed. Clin. Pract. 2022, 3, 327–340. [Google Scholar] [CrossRef]
- Chaturvedi, I.; Cambria, E.; Welsch, R.E. Teaching Simulations Supported by Artificial Intelligence in the Real World. Educ. Sci. 2023, 13, 187. [Google Scholar] [CrossRef]
- Zhang, C.; Li, M.; Wu, D. Federated Multidomain Learning with Graph Ensemble Autoencoder GMM for Emotion Recognition. IEEE Trans. Intell. Transp. Syst. 2022. early access. [Google Scholar] [CrossRef]
- Pei, Z.; Wang, Y. Analysis of computer aided teaching management system for music appreciation course based on network resources. Comput. Aided Des. Appl. 2021, 19, 1–11. [Google Scholar] [CrossRef]
- Wu, H. Multimedia interaction-based computer-aided translation technology in applied English teaching. Mob. Inf. Syst. 2021, 2021, 5578476. [Google Scholar] [CrossRef]
- Sydow, D.; Morger, A.; Driller, M.; Volkamer, A. TeachOpenCADD: A teaching platform for computer-aided drug design using open source packages and data. J. Cheminformatics 2019, 11, 29. [Google Scholar] [CrossRef] [PubMed]
- Onofrei, G.; Ferry, P. Reusable learning objects: A blended learning tool in teaching computer-aided design to engineering undergraduates. Int. J. Educ. Manag. 2020, 34, 1559–1575. [Google Scholar] [CrossRef]
- Gong, W. An innovative English teaching system based on computer aided technology and corpus management. Int. J. Emerg. Technol. Learn. (Online) 2019, 14, 69. [Google Scholar] [CrossRef]
- Zhao, Z.; Yang, J. Design and Implementation of Computer Aided Physical Education Platform Based on Browser/Server Architecture. Int. J. Emerg. Technol. Learn. 2019, 14, 40. [Google Scholar] [CrossRef]

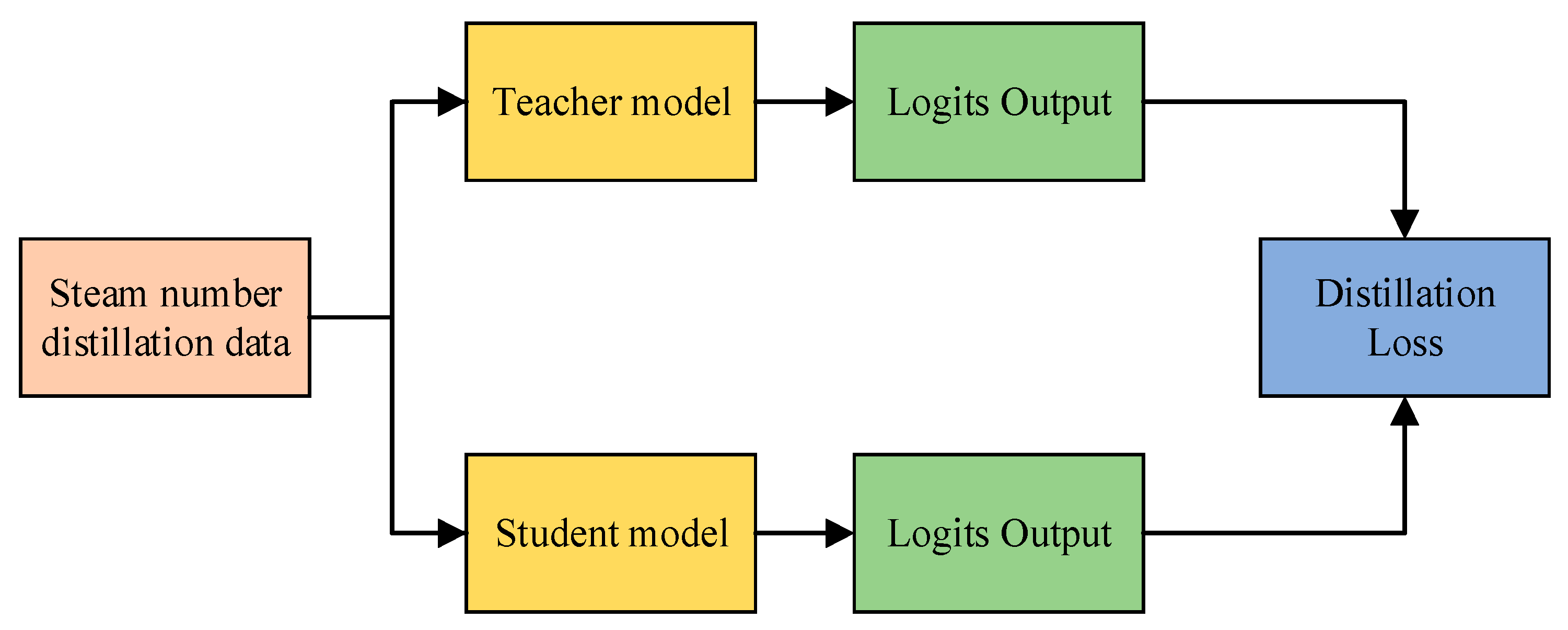
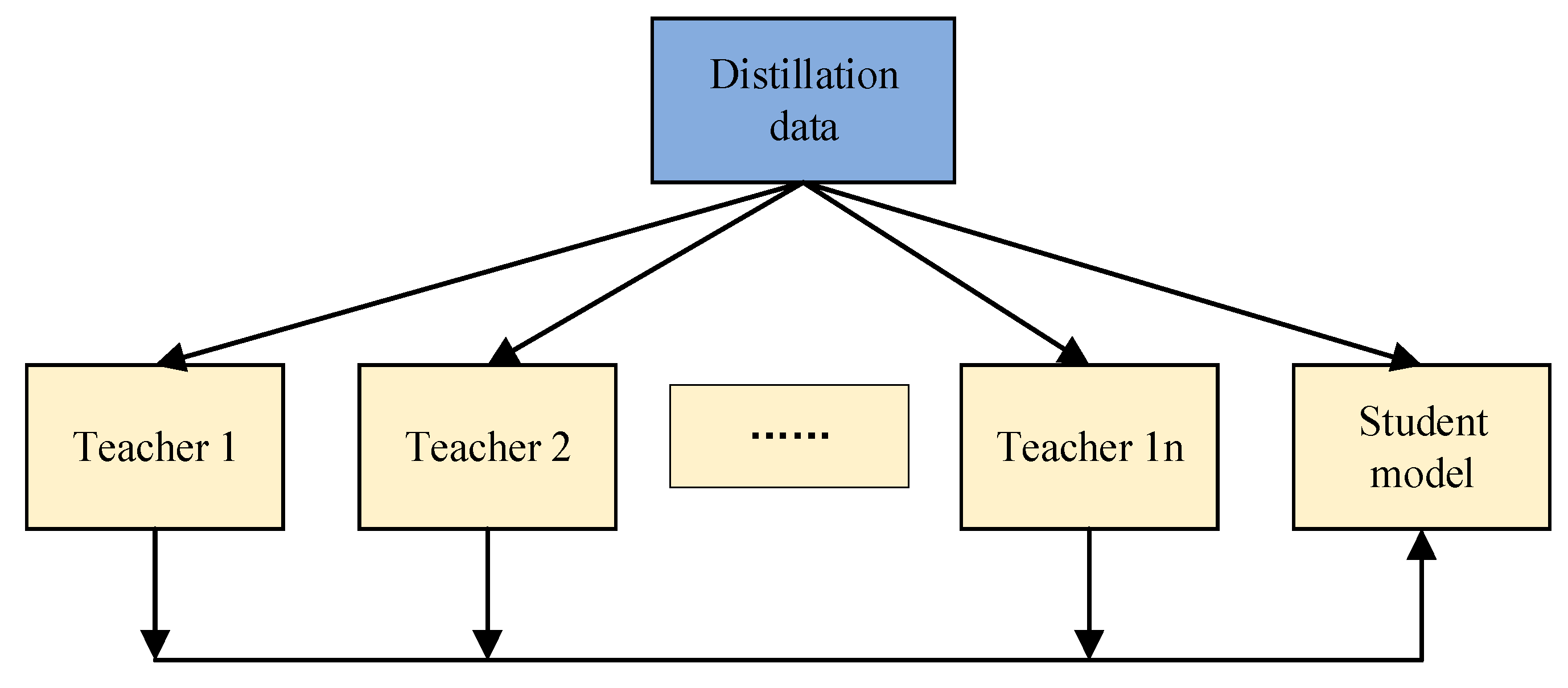
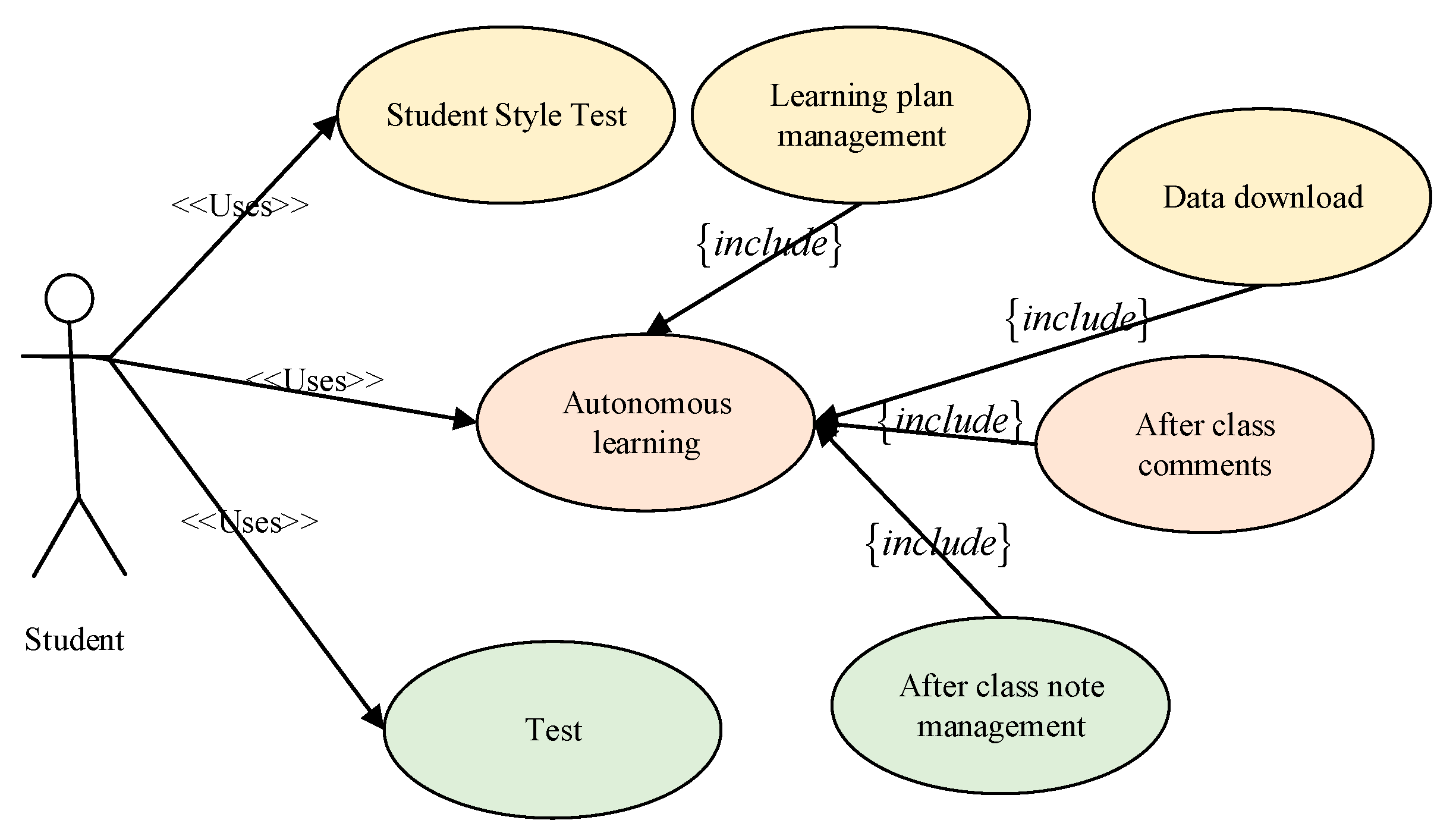
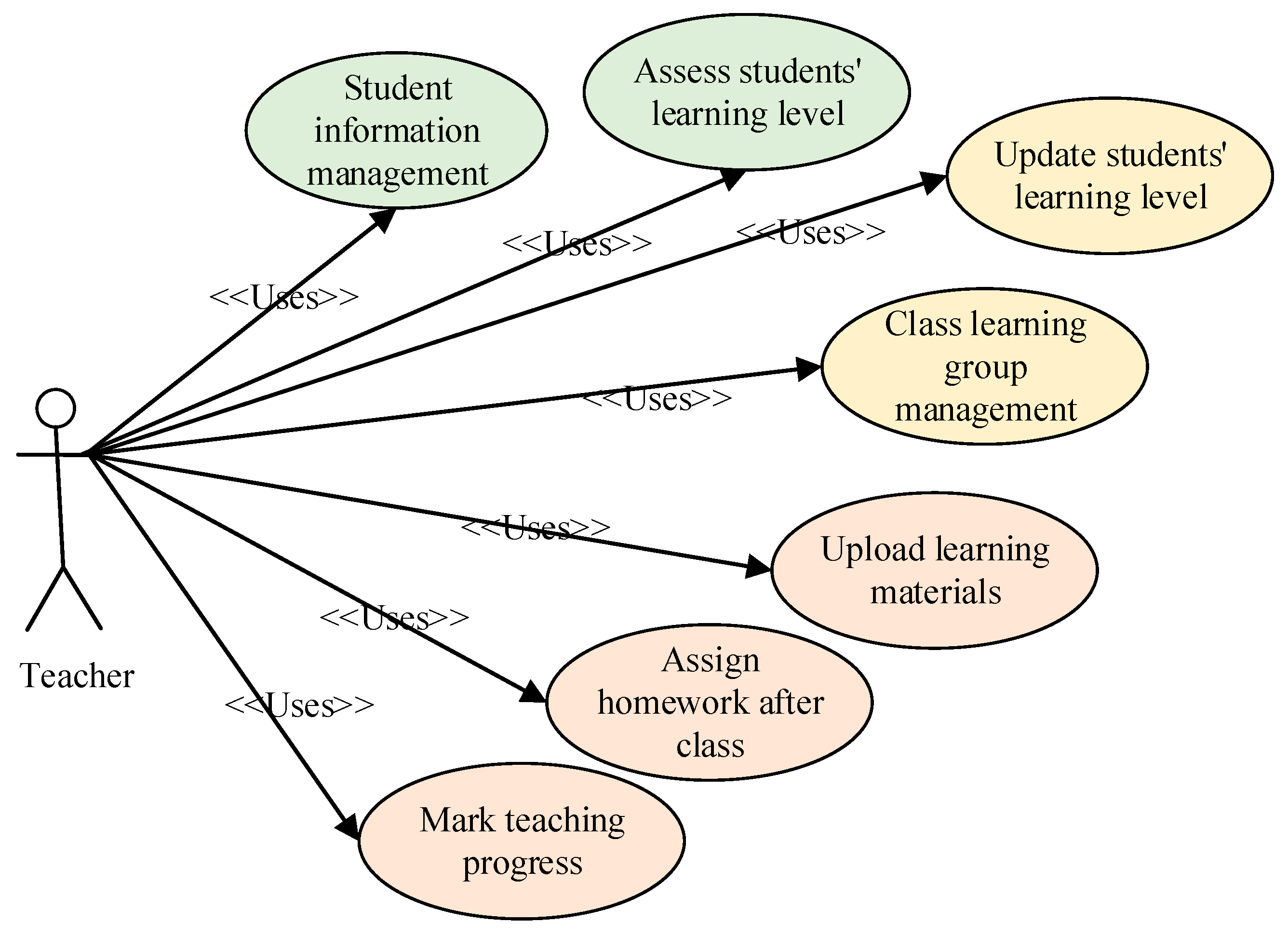
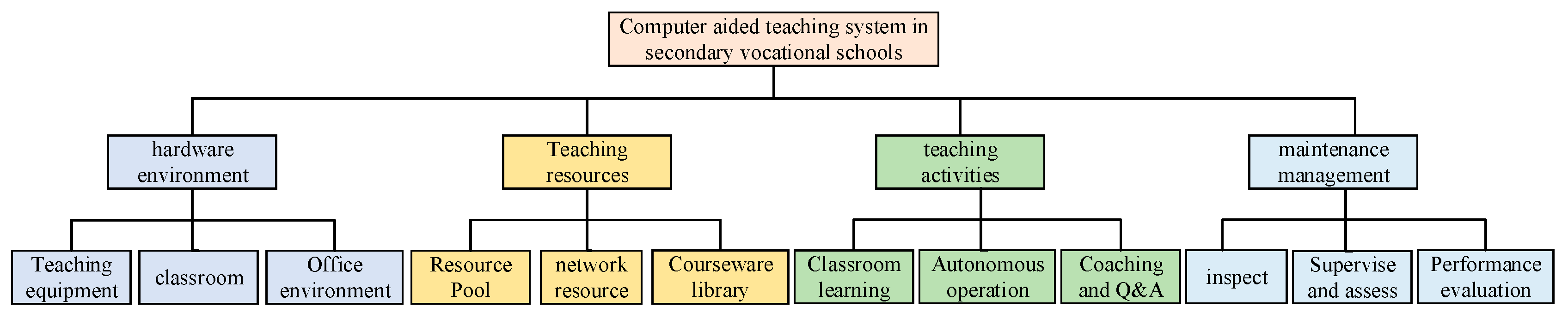
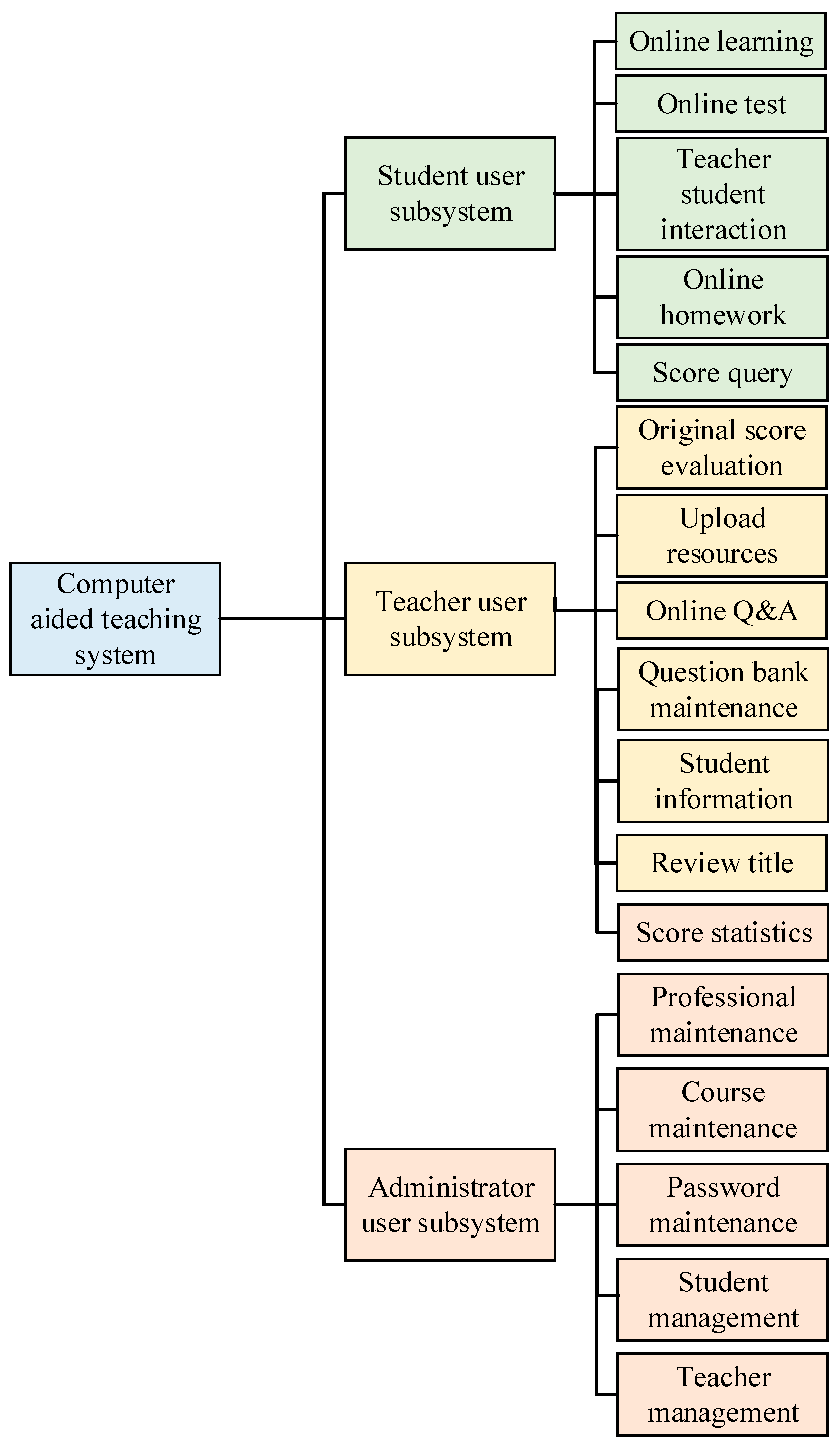
| Research Object | Junior Courses | High School Curriculum | Undergraduate Courses | Teacher Group |
|---|---|---|---|---|
| Number of Chinese papers/piece | 4 | 16 | 33 | 0 |
| Proportion of Chinese papers/% | 7.56 | 28.4 | 64.13 | 2 |
| Number of English papers/piece | 0 | 1 | 23 | 3 |
| Proportion of English papers/% | 0 | 4.15 | 91.66 | 8.23 |
| Environment Name | Configuration Information |
|---|---|
| Processor | Intel Xeon Processor E5-1620 @ 3.60 |
| Memory | 32 G |
| Hard disk | 2 T |
| GPU | Nividia GTX titan XP |
| GPU memory | 12 G |
| Independence | Components are independent and can be combined and deployed independently. It provides input parameter description and can conduct external data communication through the interface. |
| Standardization | Most component standards are defined at the company level. In component management, it uses the CBSE process for component specification management, which requires components to meet certain internal standards. |
| Combinability | Components are combined through interfaces. Middleware is used for composition as much as possible. Middleware combines functions through component input or external interfaces. |
| Deploy ability | To make it deployable, the component needs to be self-contained, and it must be able to run as an independent entity on the component platform that provides its component model implementation. |
| Documentation | The component document must be a complete component document produced through CBSE process validation. |
| Method | Loan Success Rate A | Accuracy A | Loan Success Rate B | Accuracy B | Average Accuracy |
|---|---|---|---|---|---|
| Local BLS | 51.7% | 73.9% | 57.5% | 82.7% | 76.9% |
| Longitudinal VBFLS | 59.3% | 85.6% | 61.6% | 88.5% | 82.7% |
| Method | Average Accuracy (%) | Training Duration (s) |
|---|---|---|
| BLS | 76.9% | 62.4 |
| Vertical V BFLS | 82.7% | 104.6 |
| MLP | 75.3% | 252.9 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, Q.; Jiang, J.; Lin, W. Communication Analysis and Privacy in CAI Based on Data Mining and Federated Learning. Appl. Sci. 2023, 13, 5624. https://doi.org/10.3390/app13095624
Hu Q, Jiang J, Lin W. Communication Analysis and Privacy in CAI Based on Data Mining and Federated Learning. Applied Sciences. 2023; 13(9):5624. https://doi.org/10.3390/app13095624
Chicago/Turabian StyleHu, Qian, Jiatao Jiang, and Weiping Lin. 2023. "Communication Analysis and Privacy in CAI Based on Data Mining and Federated Learning" Applied Sciences 13, no. 9: 5624. https://doi.org/10.3390/app13095624
APA StyleHu, Q., Jiang, J., & Lin, W. (2023). Communication Analysis and Privacy in CAI Based on Data Mining and Federated Learning. Applied Sciences, 13(9), 5624. https://doi.org/10.3390/app13095624





