A Systematic Literature Review of Reliable Provisioning for Virtual Network Function Chaining
Abstract
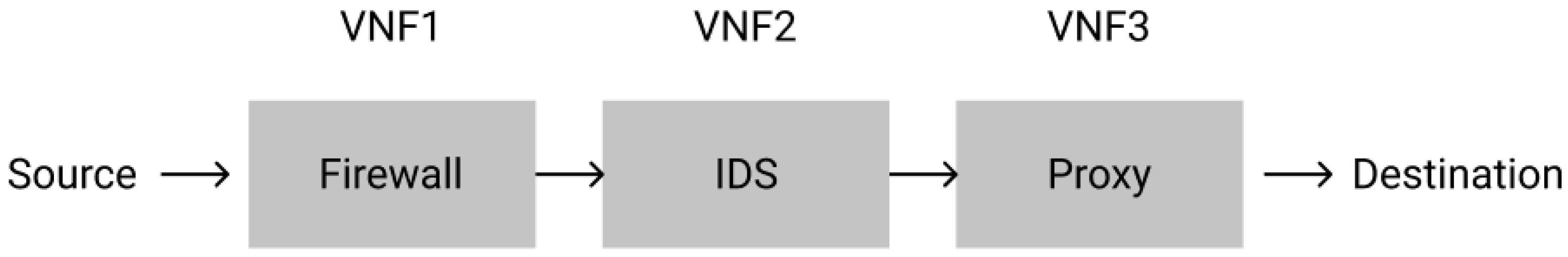
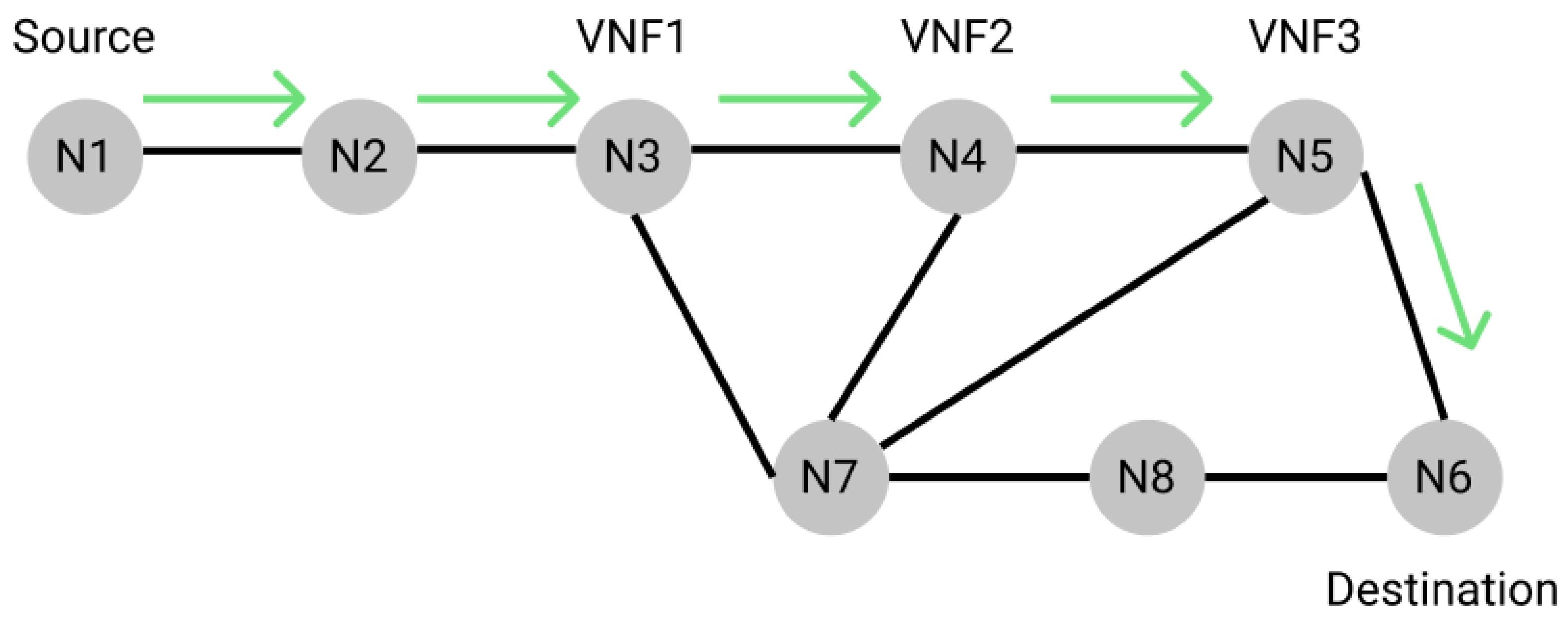
1. Introduction
2. Background
3. Research Method
3.1. Research Questions (RQ)
3.1.1. RQ1
3.1.2. RQ2
3.2. Search Process
3.3. Study Selection Criteria
- Articles include sufficient information to answer the research questions. The papers cover different aspects of the algorithm and explain the problem in more detail.
- Studies that proposed novel reliable provisioning algorithms. The algorithm considers new approaches to address the issue and resolve the problem differently.
- Papers that are not outdated and published in recent years.
- Studies are relevant to the research topic. The ones that discuss the research questions and consider the same perspective.
4. Results of the Systematic Literature Review
4.1. Different Strategies Used for Reliable Service Function
4.1.1. Reliable Provisioning by a Protection Scheme or Recovery Plans
4.1.2. Evaluation Approaches and Simulation Setup
4.2. Different Algorithms to Provide a Reliable Provisioning
4.2.1. Failure Type
4.2.2. Occurrence of the Failure
5. Discussion
5.1. Protection Scheme or Recovery Plans
5.2. Failure Type
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kibalya, G.; Serrat, J.; Gorricho, J.L.; Bujjingo, D.G.; Sserugunda, J.; Zhang, P. A reinforcement learning approach for placement of stateful virtualized network functions. In Proceedings of the 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 18–20 May 2021; pp. 672–676. [Google Scholar]
- Grinberg, S.; Weiss, S. Architectural virtualization extensions: A systems perspective. Comput. Sci. Rev. 2012, 6, 209–224. [Google Scholar] [CrossRef]
- Kuribayashi, S.I. Allocation of Virtual Cache & Virtual WAN Accelerator Functions for Cost-Effective Content Delivery Services. In Proceedings of the 2019 XXVII International Conference on Information, Communication and Automation Technologies (ICAT), Sarajevo, Bosnia and Herzegovina, 20–23 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Kaur, K.; Mangat, V.; Kumar, K. A comprehensive survey of service function chain provisioning approaches in SDN and NFV architecture. Comput. Sci. Rev. 2020, 38, 100298. [Google Scholar] [CrossRef]
- Xing, H.; Zhou, X.; Wang, X.; Luo, S.; Dai, P.; Li, K.; Yang, H. An integer encoding grey wolf optimizer for virtual network function placement. Appl. Soft Comput. 2019, 76, 575–594. [Google Scholar] [CrossRef]
- Naudts, B.; Tavernier, W.; Verbrugge, S.; Colle, D.; Pickavet, M. Deploying SDN and NFV at the speed of innovation: Toward a new bond between standards development organizations, industry fora, and open-source software projects. IEEE Commun. Mag. 2016, 54, 46–53. [Google Scholar] [CrossRef]
- Wang, X.; Xing, H.; Zhan, D.; Luo, S.; Dai, P.; Iqbal, M.A. A two-stage approach for multicast-oriented virtual network function placement. Appl. Soft Comput. 2021, 112, 107798. [Google Scholar] [CrossRef]
- Venâncio, G.; Duarte, E.P., Jr. NHAM: An NFV High Availability Architecture for Building Fault-Tolerant Stateful Virtual Functions and Services. In Proceedings of the LADC’22: The 11th Latin-American Symposium on Dependable Computing, Fortaleza, Brazil, 21–24 November 2022; Association for Computing Machinery: New York, NY, USA, 2023; pp. 35–44. [Google Scholar] [CrossRef]
- Asdikian, J.P.H.; Askari, L.; Ayoub, O.; Musumeci, F.; Bregni, S.; Tornatore, M. Availability Evaluation of Service Function Chains Under Different Protection Schemes. In Proceedings of the 2022 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Athens, Greece, 5–8 September 2022; pp. 244–249. [Google Scholar]
- Shaghaghi, A.; Zakeri, A.; Mokari, N.; Javan, M.R.; Behdadfar, M.; Jorswieck, E.A. Proactive and AoI-Aware Failure Recovery for Stateful NFV-Enabled Zero-Touch 6G Networks: Model-Free DRL Approach. IEEE Trans. Netw. Serv. Manag. 2022, 19, 437–451. [Google Scholar] [CrossRef]
- Yamada, D.; Shinomiya, N. Computing and Network Resource Minimization Problem for Service Function Chaining against Multiple VNF Failures. In Proceedings of the TENCON 2019—2019 IEEE Region 10 Conference (TENCON), Kochi, India, 17–20 October 2019; pp. 1478–1482. [Google Scholar] [CrossRef]
- Hmaity, A.; Savi, M.; Musumeci, F.; Tornatore, M.; Pattavina, A. Protection strategies for virtual network functions placement and service chains provisioning. Networks 2017, 70, 373–387. [Google Scholar] [CrossRef]
- Kibalya, G.; Serrat-Fernandez, J.; Gorricho, J.L.; Bujjingo, D.G.; Serugunda, J. A multi-stage graph aided algorithm for distributed service function chain provisioning across multiple domains. IEEE Access 2021, 9, 114884–114904. [Google Scholar] [CrossRef]
- Mechtri, M.; Ghribi, C.; Soualah, O.; Zeghlache, D. Etso: End-to-end sfc orchestration framework. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 903–904. [Google Scholar]
- Mechtri, M.; Ghribi, C.; Soualah, O.; Zeghlache, D. NFV orchestration framework addressing SFC challenges. IEEE Commun. Mag. 2017, 55, 16–23. [Google Scholar] [CrossRef]
- Herrera, J.G.; Botero, J.F. Resource allocation in NFV: A comprehensive survey. IEEE Trans. Netw. Serv. Manag. 2016, 13, 518–532. [Google Scholar] [CrossRef]
- Hmaity, A.; Savi, M.; Musumeci, F.; Tornatore, M.; Pattavina, A. Virtual network function placement for resilient service chain provisioning. In Proceedings of the 8th International Workshop on Resilient Networks Design and Modeling (RNDM), Halmstad, Sweden, 13–15 September 2016; pp. 245–252. [Google Scholar]
- Wang, M.; Cheng, B.; Chen, J. Joint availability guarantee and resource optimization of virtual network function placement in data center networks. IEEE Trans. Netw. Serv. Manag. 2020, 17, 821–834. [Google Scholar] [CrossRef]
- Alleg, A.; Ahmed, T.; Mosbah, M.; Boutaba, R. Joint diversity and redundancy for resilient service chain provisioning. IEEE J. Sel. Areas Commun. 2020, 38, 1490–1504. [Google Scholar] [CrossRef]
- Gao, T.; Li, X.; Zou, W.; Huang, S. Survivable VNF placement and scheduling with multipath protection in elastic optical datacenter networks. In Proceedings of the 2019 Optical Fiber Communications Conference and Exhibition (OFC), San Diego, CA, USA, 3–7 March 2019; pp. 1–3. [Google Scholar]
- Yamada, D.; Shinomiya, N. A solving method for computing and network resource minimization problem in service function chain against multiple VNF failures. In Proceedings of the 2019 IEEE 5th International Conference on Collaboration and Internet Computing (CIC), Los Angeles, CA, USA, 12–14 December 2019; pp. 30–38. [Google Scholar]
- Askari, L.; Tamizi, M.; Ayoub, O.; Tornatore, M. Protection Strategies for Dynamic VNF Placement and Service Chaining. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–9. [Google Scholar]
- Tajiki, M.M.; Shojafar, M.; Akbari, B.; Salsano, S.; Conti, M.; Singhal, M. Joint failure recovery, fault prevention, and energy-efficient resource management for real-time SFC in fog-supported SDN. Comput. Netw. 2019, 162, 106850. [Google Scholar] [CrossRef]
- Gu, Y.; Hu, Y.; Ding, Y.; Lu, J.; Xie, J. Elastic virtual network function orchestration policy based on workload prediction. IEEE Access 2019, 7, 96868–96878. [Google Scholar] [CrossRef]
- Mao, W.; Wang, L.; Zhao, J.; Xu, Y. Online fault-tolerant VNF chain placement: A deep reinforcement learning approach. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–25 June 2020; pp. 163–171. [Google Scholar]
- Siasi, N.; Jaesim, A.; Aldalbahi, A.; Ghani, N. Link Failure Recovery in NFV for 5G and Beyond. In Proceedings of the 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 21–23 October 2019; pp. 144–148. [Google Scholar]
- Abu-Lebdeh, M.; Naboulsi, D.; Glitho, R.; Tchouati, C.W. On the placement of VNF managers in large-scale and distributed NFV systems. IEEE Trans. Netw. Serv. Manag. 2017, 14, 875–889. [Google Scholar] [CrossRef]
- Chiang, M.J.; Yen, L.H. Distributed approach to adaptive VNF manager placement problem. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–6. [Google Scholar]
- IEEEXplore Digital Library. Available online: https://ieeexplore.ieee.org/Xplore/home.jsp (accessed on 11 December 2022).
- ACM Digital Library. Available online: https://dl.acm.org (accessed on 11 December 2022).
- Scoups. Available online: https://www.scopus.com/home.uri (accessed on 27 February 2023).
- Web of Science. Available online: https://wos-journal.com/ (accessed on 27 February 2023).
- Google Scholar. Available online: https://scholar.google.ca (accessed on 11 December 2022).
- Deng, L.; Hinton, G.; Kingsbury, B. New types of deep neural network learning for speech recognition and related applications: An overview. In Proceedings of the 2013 IEEE International Conference on Acoustics, Speech and Signal Processing, Vancouver, BC, Canada, 26–30 May 2013; pp. 8599–8603. [Google Scholar]
- Fan, J.; Jiang, M.; Rottenstreich, O.; Zhao, Y.; Guan, T.; Ramesh, R.; Das, S.; Qiao, C. A framework for provisioning availability of NFV in data center networks. IEEE J. Sel. Areas Commun. 2018, 36, 2246–2259. [Google Scholar] [CrossRef]
- Gill, P.; Jain, N.; Nagappan, N. Understanding network failures in data centers: Measurement, analysis, and implications. In Proceedings of the ACM SIGCOMM 2011 Conference, Toronto, ON, Canada, 15–19 August 2011; pp. 350–361. [Google Scholar]
- Kong, J.; Kim, I.; Wang, X.; Zhang, Q.; Cankaya, H.C.; Xie, W.; Ikeuchi, T.; Jue, J.P. Guaranteed-availability network function virtualization with network protection and VNF replication. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Fan, J.; Ye, Z.; Guan, C.; Gao, X.; Ren, K.; Qiao, C. GREP: Guaranteeing reliability with enhanced protection in NFV. In Proceedings of the 2015 ACM SIGCOMM Workshop on Hot Topics in Middleboxes and Network Function Virtualization, London, UK, 21 August 2015; pp. 13–18. [Google Scholar]
- Soualah, O.; Mechtri, M.; Ghribi, C.; Zeghlache, D. A link failure recovery algorithm for virtual network function chaining. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 213–221. [Google Scholar]
- Natalino, C.; Coelho, F.; Lacerda, G.; Braga, A.; Wosinska, L.; Monti, P. A proactive restoration strategy for optical cloud networks based on failure predictions. In Proceedings of the 2018 20th International Conference on Transparent Optical Networks (ICTON), Bucharest, Romania, 1–5 July 2018; pp. 1–5. [Google Scholar]
- Huang, H.; Guo, S. Proactive failure recovery for NFV in distributed edge computing. IEEE Commun. Mag. 2019, 57, 131–137. [Google Scholar] [CrossRef]
- Aidi, S.; Zhani, M.F.; Elkhatib, Y. On improving service chains survivability through efficient backup provisioning. In Proceedings of the 2018 14th International Conference on Network and Service Management (CNSM), Rome, Italy, 5–9 November 2018; pp. 108–115. [Google Scholar]
- Wang, Z.; Zhang, J.; Huang, T.; Liu, Y. Service function chain composition, placement, and assignment in data centers. IEEE Trans. Netw. Serv. Manag. 2019, 16, 1638–1650. [Google Scholar] [CrossRef]
- Qi, D.; Shen, S.; Wang, G. Towards an efficient VNF placement in network function virtualization. Comput. Commun. 2019, 138, 81–89. [Google Scholar] [CrossRef]
- Zhang, S.; Wang, Y.; Li, W.; Qiu, X. Service failure diagnosis in service function chain. In Proceedings of the 2017 19th Asia-Pacific Network Operations and Management Symposium (APNOMS), Seoul, Republic of Korea, 27–29 September 2017; pp. 70–75. [Google Scholar] [CrossRef]
- Aiko, O.; Nakajima, M.; Soejima, Y.; Tahara, M. Reliable design method for service function chaining. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–4. [Google Scholar]
- Sun, J.; Wo, T.; Liu, X.; Cheng, R.; Mou, X.; Guo, X.; Cai, H.; Buyya, R. CloudSimSFC: Simulating Service Function chains in Multi-Domain Service Networks. Simul. Model. Pract. Theory 2022, 120, 102597. [Google Scholar] [CrossRef]
- Ingalls, R.G. Introduction to simulation. In Proceedings of the 2011 Winter Simulation Conference (WSC), Phoenix, AZ, USA, 11–14 December 2011; pp. 1374–1388. [Google Scholar] [CrossRef]
- Fei, X.; Liu, F.; Xu, H.; Jin, H. Towards load-balanced VNF assignment in geo-distributed NFV infrastructure. In Proceedings of the 2017 IEEE/ACM 25th IWQoS, Vilanova i la Geltru, Spain, 14–16 June 2017. [Google Scholar]
- Soualah, O.; Mechtri, M.; Ghribi, C.; Zeghlache, D. A green VNFs placement and chaining algorithm. In Proceedings of the NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–5. [Google Scholar]


| Consideration | Criteria for Inclusion | Eligibility |
|---|---|---|
| Publication year | No restrictions. Results from 2014 to 2023 | The final range after screening is from 2015 to 2021 |
| Relationship with the subject | Papers related to NFV, VNF, and SFC. The paper discusses provisioning | Included when the main contribution is related to reliable provisioning |
| Type of document | The research is published in IEEE, ACM, SCOPUS, Web of Science, or Google Scholar | The research outcome is published in proceedings and journals |
| Protection Scheme | Recovery Plans |
|---|---|
| Reduce the chance of failure | Re-provision efficiently in case of a failure |
| Use backup resources | Only use resources if a failure happens |
| A common approach in provisioning algorithms | Not considered much due to its complexity in provisioning solutions |
| Algorithm | Simulation Platform | Network Topology | Number of VNFs Per SFC |
|---|---|---|---|
| JPV-ABA [18] | Java(Alevin) | Tree Topology | 2–6 VNFs |
| P-E2E [22] | C++ | Optical metro Topology | 2–5 VNFs |
| DDQP [25] | Python | Abilene, ANS, AboveNet, Integra, and BICS DC topologies | 1–7 VNFs |
| Algorithm | VNF Failure | Link Failure |
|---|---|---|
| ZT-PFR [10] | ✓ | |
| JPV-ABA [18] | ✓ | ✓ |
| P-E2E [22] | ✓ | ✓ |
| DDQP [25] | ✓ | |
| MP-VPS [20] | ✓ | |
| CS-VA [49] | ✓ | |
| Proposed algorithm [21] | ✓ | |
| BS-PUSH-BS-Pull [42] | ✓ | |
| N+P [19] | ✓ | |
| EVNFO [24] | ✓ | |
| Proposed algorithm [50] | ✓ |
| Attribute | Related RQ |
|---|---|
| Reliable Provisioning | 1 |
| Protection Scheme | 1, 2 |
| Recovery Plan | 1, 2 |
| Simulation Comparison Criteria | 1 |
| Network Topology | 1 |
| Number of VNFs | 1 |
| Simulation Platform | 1 |
| Failure Type | 2 |
| Link Failure | 2 |
| VNF Failure | 2 |
| Single Failure | 2 |
| Multiple Failure | 2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Duytam Ly, L.; Sadeghi Ghahroudi, M.; Ponce, V. A Systematic Literature Review of Reliable Provisioning for Virtual Network Function Chaining. Appl. Sci. 2023, 13, 5504. https://doi.org/10.3390/app13095504
Duytam Ly L, Sadeghi Ghahroudi M, Ponce V. A Systematic Literature Review of Reliable Provisioning for Virtual Network Function Chaining. Applied Sciences. 2023; 13(9):5504. https://doi.org/10.3390/app13095504
Chicago/Turabian StyleDuytam Ly, Le, Mahsa Sadeghi Ghahroudi, and Victor Ponce. 2023. "A Systematic Literature Review of Reliable Provisioning for Virtual Network Function Chaining" Applied Sciences 13, no. 9: 5504. https://doi.org/10.3390/app13095504
APA StyleDuytam Ly, L., Sadeghi Ghahroudi, M., & Ponce, V. (2023). A Systematic Literature Review of Reliable Provisioning for Virtual Network Function Chaining. Applied Sciences, 13(9), 5504. https://doi.org/10.3390/app13095504





