1. Introduction
Information security has become crucial today, especially with the increasing Internet of Things (IoT) adoption. The IoT refers to a network of connected devices, sensors, and machines that can communicate with each other and exchange data over the Internet. The proliferation of IoT devices has led to an exponential increase in the number of attack vectors that cybercriminals can exploit. Many IoT devices have limited processing power and memory, making them more susceptible to security breaches. Furthermore, the vast amounts of data generated by these devices provide valuable insights into people’s daily lives, making them attractive targets for hackers seeking to steal personal information.
Securing IoT devices is critical to prevent cyber attacks and protect users’ privacy. The security of these devices must be designed into them from the start rather than being added as an afterthought. The use of encryption, authentication, signature, and access control mechanisms can help secure IoT devices and protect them from unauthorized access.
On the other hand, Software-Defined Networking (SDN) can provide additional security measures for IoT devices [
1]. SDN can provide a centralized control plane for network traffic, monitoring, and analyzing traffic patterns and detecting anomalies that may indicate a security breach. A novel intrusion detection system for IoT was presented in [
1], based on software-defined networking and deep learning techniques. The proposed system utilizes a deep learning classifier to detect anomalies in the IoT without imposing security profiles on the IoT devices themselves. The system was implemented and tested in a simulated environment, and the results were evaluated using various performance metrics and compared against other relevant methods.
Cryptography aims to protect private information from unauthorized access, ensuring data integrity and authentication while offering other services [
2,
3,
4]. The encryption method plays a crucial role in guaranteeing security by encrypting messages so that they are clear only to the sender and intended recipient [
5,
6,
7,
8]. Unfortunately, some standard encryption algorithms are difficult to implement in resource-constrained environments due to their implementation scale, heavy complexity, and power consumption [
9].
To this end, lightweight encryption techniques are needed to balance the implementation cost, speed, security performance, and power consumption on resource-constrained devices, i.e., the IoT and wireless sensor networks. Lightweight cryptography is designed to be simpler and faster than traditional cryptography for securing resource-limited devices such as smart cards, radio frequency identification (RFID) tags, sensor networks, and embedded systems [
9,
10,
11,
12].
Meanwhile, lightweight asymmetric encryption techniques may not offer the same security level and functionality as more complex algorithms. However, they can still be helpful in specific contexts where performance and efficiency are critical. Hence, when selecting an asymmetric encryption technique, it is essential to carefully evaluate the trade-offs between security, functionality, and computational resources.
The digital signature is an essential element in asymmetric encryption. It offers several services, including authenticity, integrity, and non-repudiation of a digital message. Using a digital signature, the message receiver can verify its identity, guarantee that the message has not been tampered with during transmission, and prevent the denial of having sent the message. Several digital signature schemes have been proposed to offer practical mechanisms for achieving message integrity [
13,
14], authenticity, and non-repudiation. Digital signature schemes are used in electronic funds transfer, data exchange, and software distribution. Compared with physical signatures, they cannot be changed nor copied by someone else, and the signers cannot repudiate signatures later [
15,
16].
In asymmetric encryption, digital signature schemes are based on the public key. The output of the signature process is called the digital signature, a cryptographic value calculated from the data and a private key. The signer’s private key is used to sign the data, while the signatory’s public key is used to verify the signature by the recipient [
17,
18].
In cryptography, asymmetric techniques have gained significant importance due to their capability to secure digital communication channels. These techniques use different keys for encryption and decryption, and their security relies on the computational complexity of certain mathematical problems, such as factoring large numbers or discrete logarithms. However, some lightweight asymmetric techniques do not offer additional security such as the digital signature.
Despite lacking a digital signature, these lightweight asymmetric techniques are ideal for use in resource-constrained environments, such as embedded systems and mobile devices. They provide basic encryption and decryption functionality while minimizing computational resources, enabling them to be used in low-power devices with limited processing capabilities.
One common approach to creating a public key in such lightweight asymmetric techniques is to use a key of the form , where p is a large prime number and k and r are random integers. This approach has led to the development of numerous asymmetric encryption techniques, but none include a corresponding digital signature.
To address this gap, the paper proposes a technique for creating digital signatures for these lightweight asymmetric encryption techniques. The proposed method uses the private keys k, r, and p to generate a signature that can be verified using the public key . By providing a digital signature for these encryption techniques, this new method enhances the security level and opens up new possibilities for their use in applications that require stronger security guarantees.
The rest of the paper is organized as follows:
Section 2 discusses and reviews the relevant works and presents the encryption techniques that use
as a public key.
Section 3 explains the proposed scheme. In
Section 4, we perform an analyses against attacks.
Section 5 presents the experimental results and discussions. Finally, the conclusion is presented in
Section 6.
2. Related Work
The RSA signature scheme was introduced in the late 1970s and is still widely used today. It involves hashing the message to be signed and then encrypting the hash value using the sender’s private key. In the 1990s, the Digital Signature Algorithm (DSA) was introduced based on the discrete logarithm problem [
19]. The DSA quickly became popular and is widely used in various applications today. The early 2000s saw the introduction of the Elliptic Curve Digital Signature Algorithm (ECDSA), which is based on elliptic curve cryptography [
20,
21]. ECDSA is known for its small key size and fast computation time and is commonly used in resource-constrained environments. In recent years, there has been a trend towards developing lightweight digital signature schemes designed to be fast and efficient, particularly for use in resource-constrained environments such as the IoT and other embedded systems [
22,
23,
24]. This section sheds some light on the recent related work in the literature.
In [
25], El Gamal proposed the El Gamal signature scheme, which is one of the first digital signature schemes based on the algebraic nature of modular exponentiation. The El Gamal signature scheme involves generating a digital signature for a message using a private key and verifying the signature using a public key. The El Gamal signature scheme ensures the authenticity of data sent over insecure channels. However, the El Gamal signature algorithm has difficulty computing discrete logarithms; furthermore, it is a non-deterministic algorithm, meaning that there are many valid signatures for a given message, and the algorithm considers each of these valid signatures to be authentic [
26].
In [
27], Mohammed et al. added some improvements to the ElGamal signature scheme. A new blind signature scheme was proposed in their work based on the number theory operations and modular arithmetic techniques. This scheme has the advantage of ensuring greater anonymity for participants, where if a message is signed multiple times, the corresponding signatures will differ.
A new and fast cryptographic digital signature scheme was proposed in [
28] by Alia et al. The vital link between Mandelbrot and Julia fractal sets was used to generate the private and public keys using their particular functions (i.e., Mandelfn and Juliafn functions). The first fractal function inputs the selected private key and generates the corresponding public key. The message is then signed with the recipient’s public key using the second fractal function, and the received message is verified against the recipient’s private key. In [
23], Mughal et al. proposed a lightweight Shortened Complex Digital Signature Algorithm (SCDSA) based on short complex numbers for both signature and verification operations. This algorithm aims to secure the communication between user-centric IoT devices and mitigate the communication and computational overhead on the network. Due to the multi-option parameter selection mechanism, their scheme is secure enough to resist traffic analysis attacks and has better resilience than extensive operations in DSA-based schemes.
Johnson et al. presented an Elliptic Curve Digital Signature Algorithm (ECDSA) in [
21] based on the curve drawn by a mathematical equation. On the curve, a point is selected randomly and considered its point of origin. Then, a random number is generated. It is precisely this random number that is known as the private key. Then, combining the private key and the origin point using a specific equation, a second point on the curve is obtained and considered the public key. This process is considered safe, and it is only possible to establish the mathematical relationship from the private key to the public key, but not the opposite. The ECDSA is used across many security systems and is the basis of Bitcoin security. The ECDSA provides higher security with shorter key lengths than many popular algorithms such as the RSA and DSA. However, this algorithm is unsuitable for constrained devices that are limited in resource computation. To improve the ECDCA’s computational cost, Junru in [
29] proposed two schemes named ECDSA 1 and ECDSA 2. Junru’s goal is to improve the ECDCA’s computational cost while keeping the same security level as compared to the ECDSA. ECDSA 1 is suitable for constrained devices on the signatory’s side, whereas ECDSA 2 is relevant for constrained devices on the verifier’s side.
In [
30], Lavanya and Natarajan designed a Lightweight Digital Signature Algorithm (LWDSA) based on the ECDSA and cryptographic hash functions dedicated to WSNs. In this modified the ECDSA, the major variation is using the MBLAKE2b hash function instead of SHA-1 to generate the hash code. The LWDSA outputs have been compared with the traditional authentication process of the ECDSA. The analysis of the QoS parameters such as the latency, energy, throughput, etc., were performed over a 30-node network simulated in NS-2. Their simulation performed better by reducing the computation time and energy consumption, increasing the network lifetime. However, the computation time has not been clearly indicated for the generation and verification of the signature process. In addition, it is challenging to measure QoS parameters for a large-scale and dynamic WSN network in order to validate the proposed scheme.
Kavin et al. aimed to develop an Enhanced Digital Signature Algorithm (EDSA) in [
31] to ensure the integrity and secure access of the data stored in the cloud. The idea of EDSA focuses on elliptic curve square points generated by improved equations. The proposed EDSA generates two elliptic curves by applying the improved equations, which are used as public keys to perform the signing and verification process. In addition, a new basic formula is introduced for performing digital signature operations such as signing, verifying, and comparing. A compression technique is used to reinforce reducing the bit size of the signature.
A new digital signature scheme based on Iterated Function Systems (IFSs) was designed in [
32] by Al-Saidi et al. Fractals were used to design the digital signature system based on IFS transformations. The receiver requests a signature from the signer, who then delivers a fractal signature to the requester without knowing the content of the message. The proposed scheme includes initialization, signing, extraction, and verification. The advantage of the fractal is that only a few parameters must be stored. The fractal scheme outperforms the DSA and RSA schemes due to the lower computational overhead and smaller key sizes. However, the scheme still incurs high computational overhead for constrained devices and needs to be adapted to such device types.
In [
33], Wei et al. proposed a new attribute-based proxy signature scheme on a lattice that can resist quantum attacks. The scheme has the properties of both attribute-based signatures and proxy signatures providing fine-grained access control. The scheme allows the original signer to sign a warrant using their attribute keys to delegate signing authority. Then, the proxy signer signs the message only when the attribute set of the original signer satisfies the access structure and the warrant is valid. The verifier also checks the original signer’s attributes and the validity of the signature. This feature provides fine-grained access control; however, the main disadvantage of lattice-based constructions is that they generally involve operations on, and storage of, large
matrices. This resulted in the schemes being rather inefficient and unsuitable for practical use.
Zhou et al. proposed a mixed private and consortium-based blockchain in [
34] to realize the secure storage of medical cyber physical data. In the system, a threshold signature system based on blockchain was proposed for joint consultation. Using the security and threshold properties of the threshold signature, the treatment can be carried out when the threshold number is reached, and medical data can be uploaded to the consortium blockchain. Despite being application-domain-dependent, the security analysis and performance analysis showed that the scheme has advantages in safety and performance and is suitable for the medical environment to a certain extent.
Within the medical data domain as well, Al-Zubaidie et al. developed the Pseudonymization and Anonymization with the XACML (PAX) modular system in [
35]. The proposed system uses a random pseudonym to separate personal information about patients’ data, anonymity to hide subjects’ information, and XACML to create distributed access control policies to authorize subjects’ requests to objects’ records in Electronic Health Records (EHRs). It provides a security and privacy solution to the problem of safe-access decisions for patients’ data in the EHR. The results of theoretical and experimental security analysis proved that PAX provides security features in preserving the privacy of healthcare users and is safe against known attacks. However, the validity of the solution has not been demonstrated for other application domains.
Encryption Techniques That Use as a Public Key
In asymmetric encryption, there are two keys: a public key () for encryption and another private key (), which is used for decryption. Any user can send a message encrypted by to its owner, and only the owner of can decrypt this message. In addition to encryption, could play another vital role: message signing. In general, when sending a message, a user must sign it using his/her for two reasons: to ensure message integrity and authenticity.
Many schemes use the RSA as a signature system, and this forces these techniques to use two private keys and two public keys, i.e., two pairs (, ) and (e, d), where (, ) are the keys used in the encryption/decryption processes and (e, d) are the RSA keys used for signing. Otherwise, these techniques must use encryption/decryption keys that respect the RSA conditions and . In the RSA and elliptic curve, it is difficult or impossible because their keys may have a specific form and/or satisfy particular conditions. Therefore, some solutions propose using a signature scheme compatible with their key pair (, ).
Among the asymmetric encryption techniques that do not have—to the best of our knowledge—a signature scheme compatible with their key pair are techniques that use a public key of the following form:
where
is the public key,
k and
p are the private key, and
r is an integer used to mask private keys and generate encryption noises. In addition, the public primitive
with the trapdoor
p and
q, which are two large prime numbers.
It is essential here to mention that
r is not necessarily private, and it can be published where the adversary knows (
,
n):
We note here that there are two equations ((
1) and (
2)) and three unknown numbers (
k,
p, and
q); then, it is challenging with large
p and
q to obtain the private values
k and
p as long as there is no mathematical relation between
k and
p (
).
r verifies
, whose goal is to generate a noise greater than
n.
Table 1 illustrates some encryption schemes that use
as a public key.
In [
36,
37], the authors used a symmetric scheme; however, we mean here the asymmetric version of this technique where
and
. Defining a signature scheme for these kinds of lightweight asymmetric techniques is challenging. In the next section, we will explain, in detail, the proposed digital signature scheme dedicated to the techniques that use
as a public key.
Table 1.
Schemes that use as a public key.
Table 1.
Schemes that use as a public key.
| Scheme | Enc | Dec |
|---|
| [38] | | |
| [39] | | , c← |
| [40] | | |
| [36] | | |
| [37] | | |
3. The Proposed Signature Scheme
In asymmetric encryption techniques, the receiver needs to authenticate the author of sent data and guarantee its non-repudiation, which is ensured by digital signature.
In fact, there are many algorithms that are used to create signatures, and these algorithms use smaller keys, for example Elliptic-Curve-Cryptography (ECC)-based signature algorithms, but to use ECC, both the private and public keys must be created over an elliptic curve. In this paper, we studied the creation of an accompanying signature for cryptographic algorithms that have a linear and very special public key generated independently of ECC, where , with p a prime number and k and r random numbers.
To the best of our knowledge, there is still no corresponding signature for this form of keys. We focused on this type of public key for its ease of creation and also for its resistance to attacks so the secret parameters (k, r, and p) cannot be extracted from it.
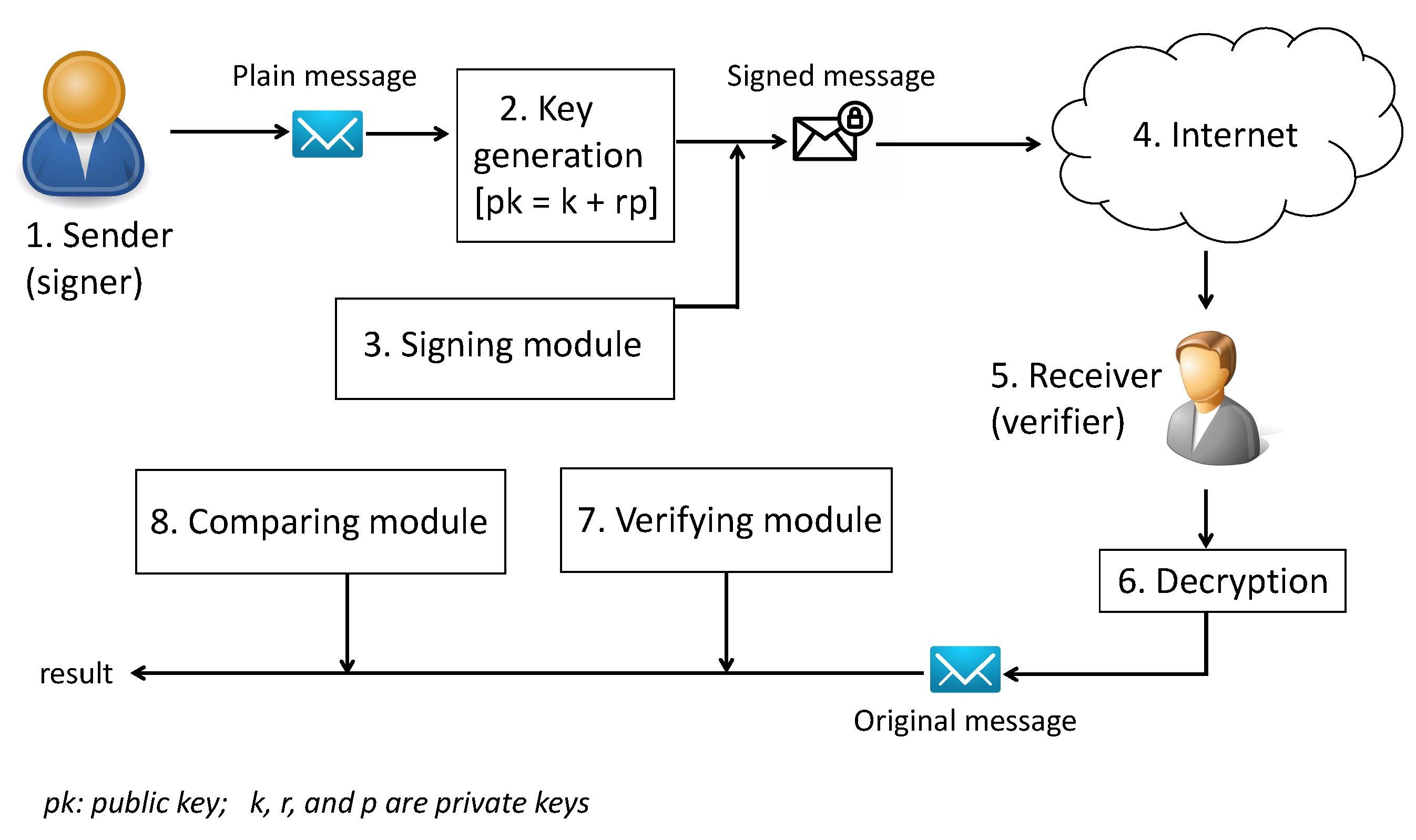
To provide a suitable scenario describing the new signature scheme’s functional mode, we need certain details about the planned architectural model to use.
Figure 1 shows the proposed architectural model. Most modern cryptographic architectures follow a layered approach, with each layer providing a specific security function. The proposed architecture layers include the following components: the sender, the encryption operation, the signing module, the Internet, the receiver, the decryption operation, the verifying module, and the comparing module:
Sender: This plays the role of the signer and transforms the plain text into a cipher text that will be used later for data validity.
Key generation: This component is responsible for providing all keys required for the signing and verifying processes, including private keys, split public keys, and whole public keys.
Signing module: By applying the newly proposed signing formulas, this component creates a digital signature of the original message that is sent by the signer. It uses private keys for extracting the two parts of the signature. The created digital signature will be sent along with the encrypted message to the Internet for further processing
Internet: Its role is to transport information to the receiver directly or to the cloud for storing, allowing the authorized user to access the stored data.
Receiver: This obtains the authorization for accessing the specific data, which are transported by the Internet and stored in an encrypted format with a signature. The encrypted message will be accessed by the receiver and decrypted using the decryption operation. The receiver then has the original data and a digital signature created by the sender using the sender’s private key. The authorized receiver can then verify the originality of the message with the help of the sender’s public key.
Decryption operation: This transforms the cipher text into plain text.
Verifying module: The verification module verifies the sent digital signature of the original message that is created by the sender. New values will be created by applying the verification formula.
Comparing module: The created values using the signature, which is available along with the original message, will be compared to each other. If both values are the same, then the integrity of the data is validated; otherwise, the accessed data are a modified message or a fake message.
3.1. The Proposed Scheme
The proposed DS technique uses the private key k and the secret trapdoor p of the sender to generate a DS represented in two parts and , which are used for performing the signing and verifying processes. Moreover, new base formulas are also introduced for conducting digital signature operations such as signing and verifying. Our proposed protocol is explained under three subsections including the signing, verification, and comparison processes. However, first, let us define the following primitives:
The sender integer random r split into two other random numbers and where .
The sender private key is ,
The sender public key is , where , with p and q two large prime numbers; is a small modulus (160 bits).
To generate a secure public key, the integer r must verify . Furthermore, p and q must be secure primes, i.e., they are of the form and , respectively, with and also primes:
The plain message m is encrypted by the encryption function using receiver public key , .
The plain message m is signed by the signing function Sig() using sender private keys ().
The receiver private key is
The cipher message c is decrypted by the decryption function using receiver private key , .
The received signature is verified by the verifying function Verf() using sender public keys ().
To imply the public key () in the signature, the main idea of our proposal consists of two steps: First, split the signature into two parts and ; one uses k and the other uses . Second, split randomly r into and , where ; keep one secret (), and the other is public. By this, we will obtain and . The receiver can easily first compute , which is equal to , and secondly compute ; finally, they are compared. The proposed protocol is explained below:
3.1.1. Signing Process
In the signing process, we need to go through the encryption process, as the cipher text will be used in the verification process to extract the original message and ensure the data integrity. To sign a message
m, the sender encrypts
m as:
Then, the sender signs the message
m by calculating
and
, which contain their private keys
,
, and
p as follows:
and
The digital signature to be sent to the receiver is
:
The workflow of a signing process in the proposed DS technique is shown in Algorithm 1.
| Algorithm 1 Signing algorithm. |
| Require: message m, secret keys , public keys |
| Ensure: |
| |
- 1:
function Sig - 2:
compute : ← - 3:
compute : ← - 4:
← - 5:
return - 6:
end function
|
3.1.2. Verifying Process
After decrypting the cipher text
c and retrieving the original message
, the receiver should calculate the value of
x using the sender’s public key
as follows:
where
The receiver uses the computed value of m to detect any manipulation of the cipher text and ensure data integrity. The use of the sender’s public key ensures authenticity.
Then, the check value
y will be calculated:
Then comes the comparison process:
The workflow of a verification process in the proposed DS scheme is shown in Algorithm 2, which ensures validity (integrity and authenticity).
| Algorithm 2 Verification algorithm. |
| Require: cipher text c, signature , public keys , private key |
| Ensure: decryption and message integrity
|
| |
-
function Verf - 2:
compute m : m← compute x : x← - 4:
compute y : y← if then - 6:
return m else - 8:
return end if - 10:
end function
|
3.1.3. Correctness
The sender calculates and using his/her private keys, where and ; the receiver recovers m and calculates , where and . Then, the receiver calculates ; this implies ; ; this gives .
Therefore, the proposal is correct and the data receiver can easily verify sender authenticity using the sender’s public key.
3.1.4. A Practical Example
To show how the proposed model works, we present the following example: prime number p of size equal to 1 kbits and prime number q of size equal to 1 kbits; this gave us a modulus of size equal to 2 kbits. We chose a secret key k of size equal to 0.5 kbits and a random number r of size equal to 1 kbits. This gave us a public key of size equal to 2 kbits. Both sub-keys and are of size equal to 0.5 kbits. The message m is equal to 7 bits. After calling the function, we obtain both and of size equal to 160 bits. After calling the function, we obtain the values of x and y (both of size equal to 160 bits). Finally, we found , demonstrating the proposed scheme’s validity and applicability.
We note that the value of x is equal to the value of y, knowing that y is calculated by using the split sender’s public key and computed m, and x is calculated by using the whole sender’s public key .
4. Analysis
The most-important security aspect of the signature scheme is retrieving the private key or forging the signature process, which we will discuss in the following.
4.1. Attacks Aiming to Recover the Private Key from the Public Key
In our proposal, the modulus n is public. The proposed scheme is based on a Factorization Problem (FB), where the adversary has to factorize to obtain p.
If there is a successful attack, the adversary calculates the secret key
k from
, where
After calculating
k, the adversary can extract the secret number
from
r since
is public, where
Then, . Now, the adversary has the whole private key () and can easily produce a valid signature.
Therefore, secure prime numbers must be used; a prime number p is called safe if , such that is also a prime number. In FB, a size of p and q that equals 1024 bits is considered secure. To achieve a valid decryption, a message m to be encrypted must be less than the private key k, so the size of k usually depends on the used encryption technique and the plain text range.
4.2. Attacks Aiming to Recover the Private Key
In this attack, the adversary tries to obtain one of the private keys k, , or p that were used to create a valid signature. Signature parts and will be sent through an insecure channel, so we suppose that an adversary can obtain both and .
In a successful attack, we assumed that the adversary can have and , either by the interception or by being a malicious receiver. We have ; if the adversary is a malicious receiver, he/she can also know m by decrypting using its private key. Therefore, to recover k, the adversary has to solve the Discrete Logarithm Problem (DLP).
After computing
k, the adversary can extract
using the public keys (
), where
Now, the adversary has k and ; thus, he/she can create a valid signature. The same for , the adversary must solve the DLP in order to recover directly . Otherwise, the adversary must solve the factorization problem in order to obtain p and then k from the public n.
We would like to point out here that r does not have to be secret. We assumed this in the proposed scheme just to increase the level of security; this means that both and can be known for everyone. Suppose, for example, that the adversary has and ; he/she still has to know k and p in order to create a valid signature ( and ).
Knowing and does not affect the robustness of the public key (), nor does it give any information about k or p. Likewise, knowing does not affect the confidentiality of , nor does it give any information on the plaintext m or the private keys (). Assuming that the receiver has , after decrypting c and computing m, he/she will have , where ; he/she still has to solve the DLP to obtain p. Therefore, we have hidden r only because there is no need to make it public.
4.3. Attacks for Forging Signatures
We now considered the possibility of forging a given signature without knowing the private keys k and p. In order to forge the signature of a message m, the adversary must simulate the two signature parts and ; because he/she does not know either k or or p, he/she must randomly generate two numbers , or use random numbers , , and as secret keys, then calculate and . Of course, the adversary can encrypt any message m, because he/she knows the public key of the victim, where . The digital signature to be sent to the receiver is , where .
In the verifying step, the receiver will calculate x using the decrypted message m and victim public key as follows: . To generate , the receiver should calculate .
We have now and which implies . Thus, . We can clearly see that , while , , while and .
The adversary can easily compute , then obtain two numbers and where . simulates , and simulates ; knowing that is public, the adversary’s issue is to find a number that verifies . This is equivalent to the DLP.
Therefore, to forge the proposed signature scheme, the adversary has to resolve the DLP.
5. Experimental Results
Table 2 represents the sizes used in each test. The message size is fixed in all tests where
= 8 bits. In this type of public key
, generally
because
.
r must satisfy the condition
; to minimize the complexity, we can choose
with
; for example,
r = 725,
q = 307. We have
; thus, the size of the public key is
. While
and
, then
. We note here that, for security measures, we selected
p and
q with similar, but not equal sizes to prevent the square computation on
n. The size of
and
means the average size of many tests. However, we note that the sizes of
and
are always almost equal to the size of
n.
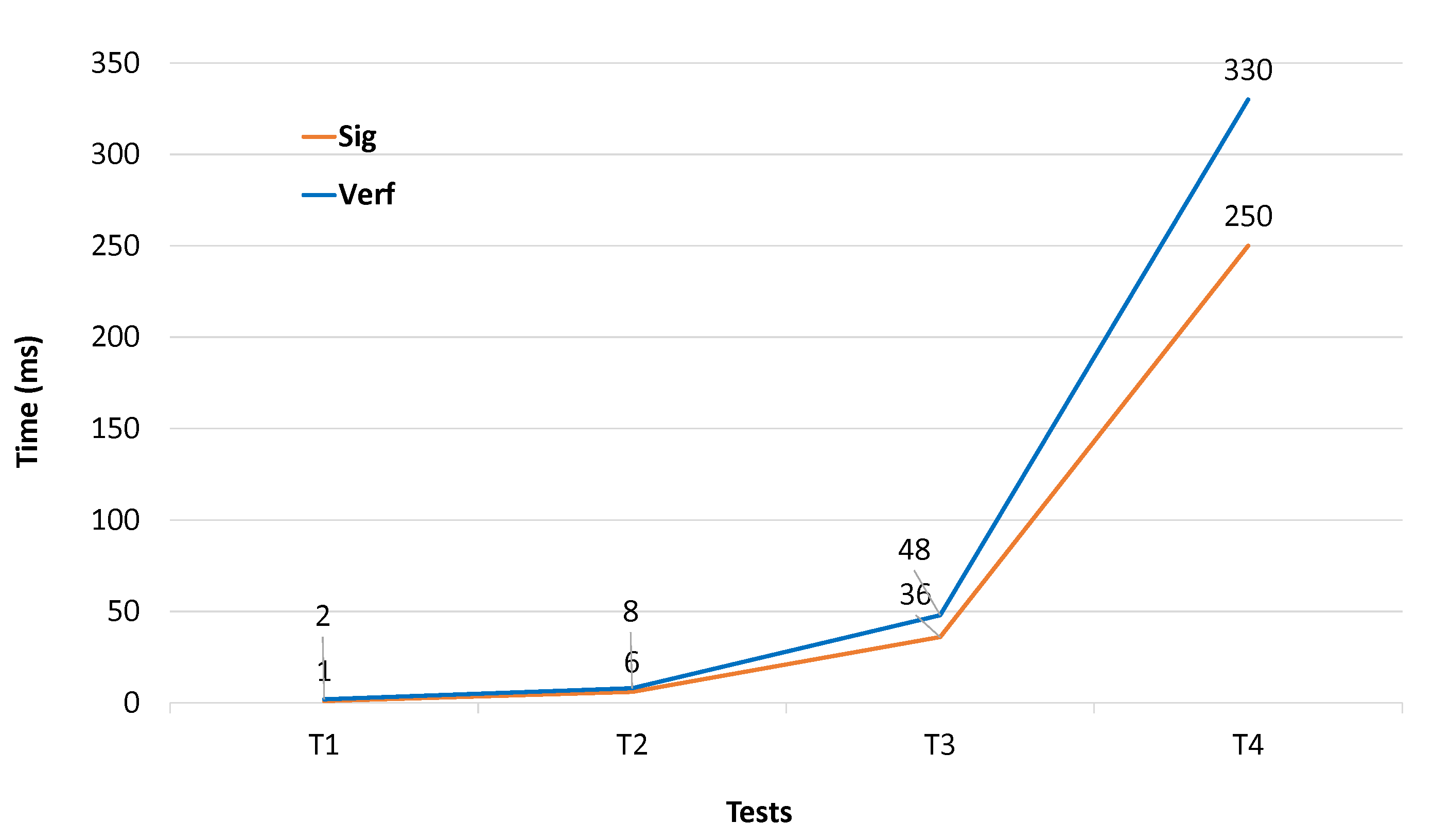
Figure 2 shows the execution time in each test, that is the Signing Process Time (SPT) and the Verification Process Time (VPT). In
, the sizes used are impractical, but used to show the increase in time. In
,
, and
, we noticed that SPT and VPT take a constant ratio between them, where
. SPT and VPT increase more rapidly in
. Of course, the sizes used in
exceed the safety recommendations, because the recommended size of primitive
p is 1024 bits, which is used in
.
The results shown in this section, namely signing and verifying time, showed the applicability of the proposed method. Four experiments were presented containing realistic example values; the implementation time was not exceeded, at the highest estimate, 250 milliseconds for signing and 330 milliseconds for verifying represented in Experiment No. 4.
Table 3 shows the used notations and the corresponding runtimes for each operation.
A comparative resume of the computational costs and communication costs for the four techniques [
23,
26,
31,
41,
42] and ours is illustrated in
Table 4 and
Figure 3.
Table 4 shows the preference of the proposed scheme compared to other schemes, where the comparison was based on the full time to perform the signature and verification operations, the signature size, and scheme suitability for systems that use a public key of the form
. The only scheme with less execution time is that of [
26] because it uses only two exponentiation instead of four and does not use a hash function, so it achieved four milliseconds less time. The signature size in the scheme [
23] was equal to our scheme size (size =
+
=
= 2 × 160 = 320 bits). As for the rest of the schemes, the size of the signature was greater than that. All of these techniques are not suitable for cryptosystems that use a public key
, except for the proposed technique.
This practical comparison, which was presented in this section, shows the effectiveness of the proposed protocol, not only in a theoretical study, but also in an applied study, outperforming many modern techniques, both in execution time and in signature size. The results of this study have a significant impact on the field of research and the field of creating digital signatures, due to the new and impressive results it presents.
6. Conclusions
In conclusion, our research presented an innovative digital signature scheme that is both robust and efficient, outperforming other modern techniques in terms of signature size and execution time. The proposed scheme provides a novel digital signature for asymmetric encryption techniques, utilizing a public key in the form of , where both k and p are private keys used in both the decryption and signature processes. Through our analysis of the proposed scheme, we demonstrated its robustness against private key recovery attacks and forgery attacks.
Furthermore, we presented a real-life signature example and conducted a series of tests with various input sizes to showcase the execution time of both the signature and verification processes. By comparing our proposed scheme with other modern techniques, we established that our approach boasts a smaller signature size of only 320 bits, thanks to the use of a small-sized public key. Additionally, we achieved a faster execution time of only 48.4 ms for the whole signature operation, including signing and verification, due to the fewer operations used by our technique.
Looking towards future directions, we aim to develop an aggregate signature protocol based on our proposal, allowing for two or more digital signatures to be joined into a single, shorter signature. This would allow different signers to generate signatures using our presented scheme.