An Evolutionary Game Theoretic Analysis of Cybersecurity Investment Strategies for Smart-Home Users against Cyberattacks
Abstract
1. Introduction
Contributions
- Modeling the competition between cybersecurity investment and cyberattacks as a non-cooperative game among three populations: smart-home users, manufacturers, and attackers.
- Deriving the replicator dynamics of these three populations using EGT, analyzing the Nash equilibrium solutions of the proposed evolutionary game model, and identifying the conditions for asymptotic stability of equilibrium solutions.
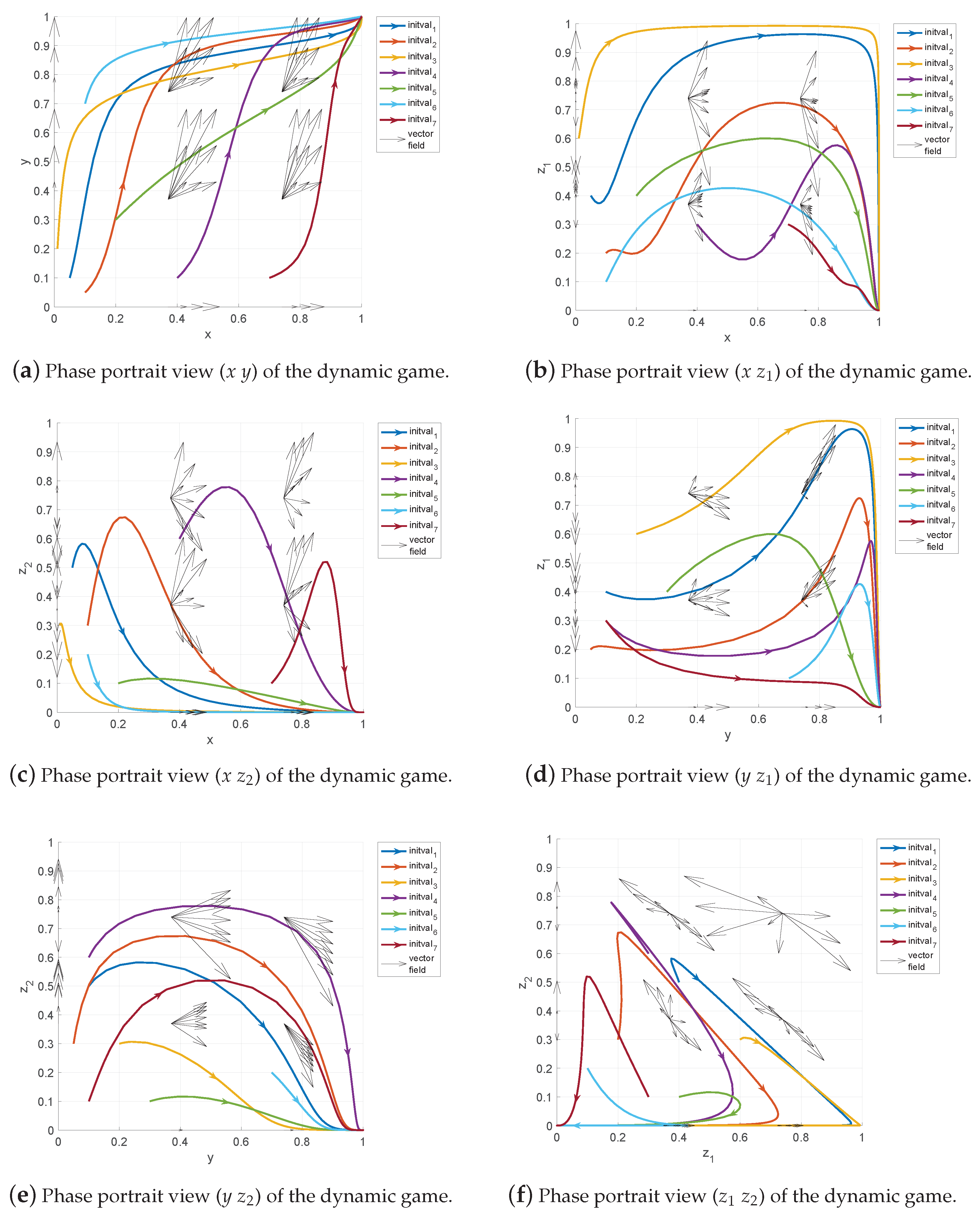
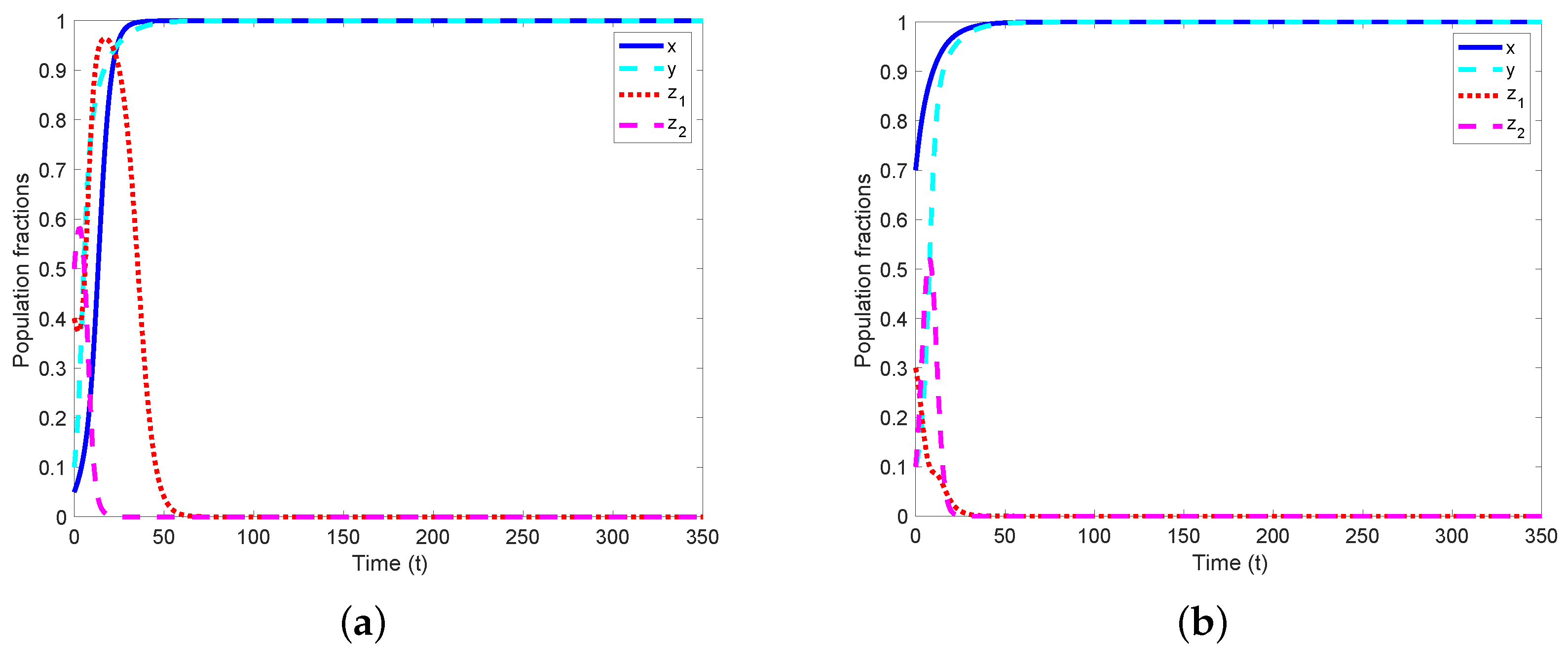
- Validating our theoretical results using four-dimensional phase portraits with state combinations and plotting the evolution of population fractions to confirm the existence of a unique ESS in the proposed game.
- Analyzing and discussing the numerical results of the proposed game by investigating the impacts of costs and benefits of cybersecurity investment and cyberattack costs on the ESS.
2. Related Work
2.1. Cybersecurity Awareness for Home Users
2.2. Game-Theoretic Approaches for Cybersecurity Investment
2.3. Evolutionary Game Theory
3. Proposed Game Model
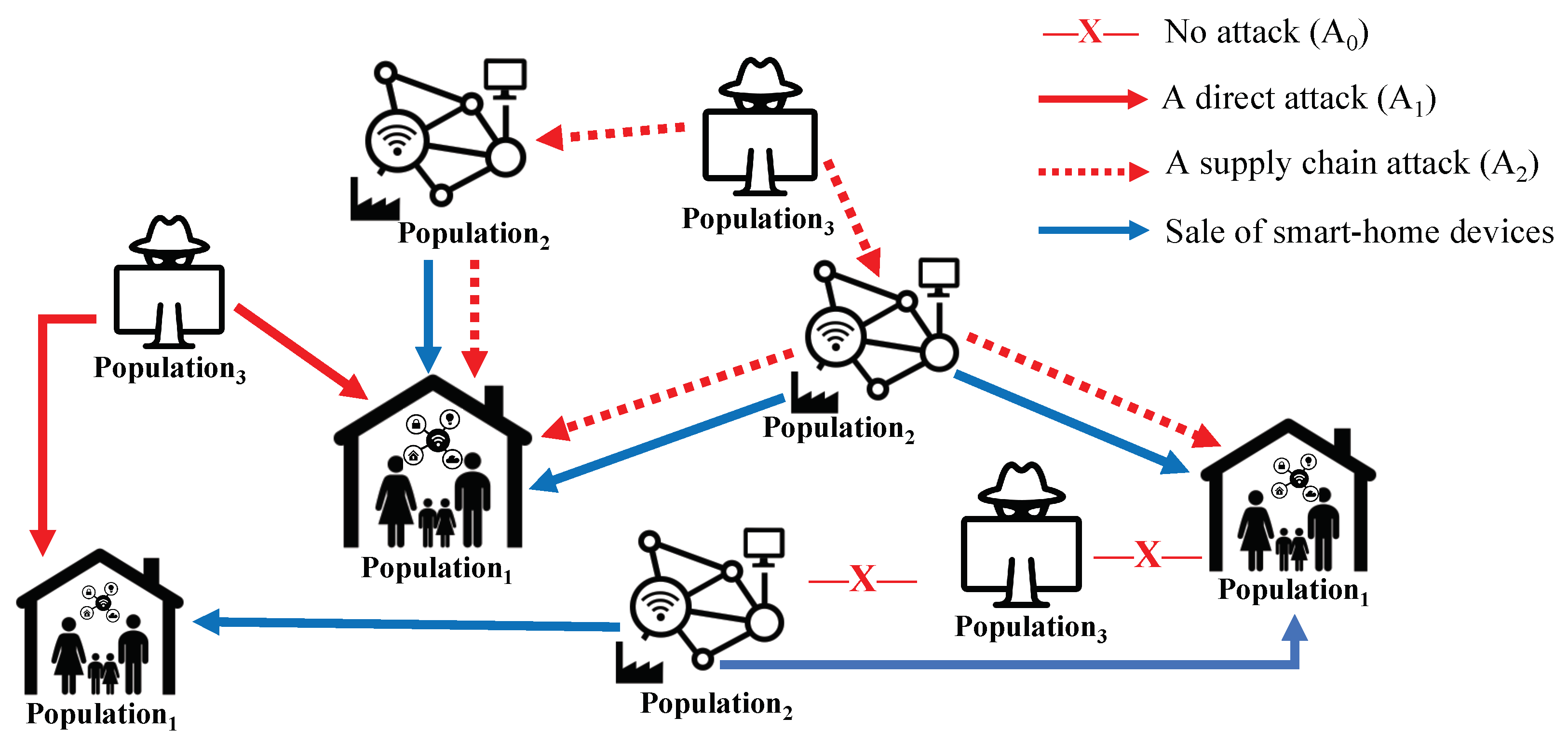
3.1. System Model
3.2. Game Modeling
3.3. Normal-Form Game
4. Game Analysis
4.1. Replicator Dynamics
4.1.1. Replicator Equation of
4.1.2. Replicator Equation of
4.1.3. Replicator Equations of
4.2. Conditions for ESS
4.2.1. Nash Equilibrium
4.2.2. Jacobian Matrix
4.2.3. Equilibrium Stability Analysis
- is asymptotically stable.
- The other Nash equilibrium solutions are not asymptotically stable.
| Pure Nash Equilibrium Solutions | Eigenvalues | Sign of Eigenvalues | Conditions for Asymptotic Stability | ESS | |||
|---|---|---|---|---|---|---|---|
| ✗ | |||||||
| ✗ | |||||||
| ✗ | |||||||
Uncertain | ✗ | ||||||
Uncertain | ✗ | ||||||
| ✓ | |||||||
Uncertain | ✗ | ||||||
Uncertain | ✗ | ||||||
Uncertain | ✗ | ||||||
Uncertain | ✗ | ||||||
Uncertain | ✗ | ||||||
Uncertain | ✗ | ||||||
5. Numerical Results
5.1. Numerical Validation of the Stability of
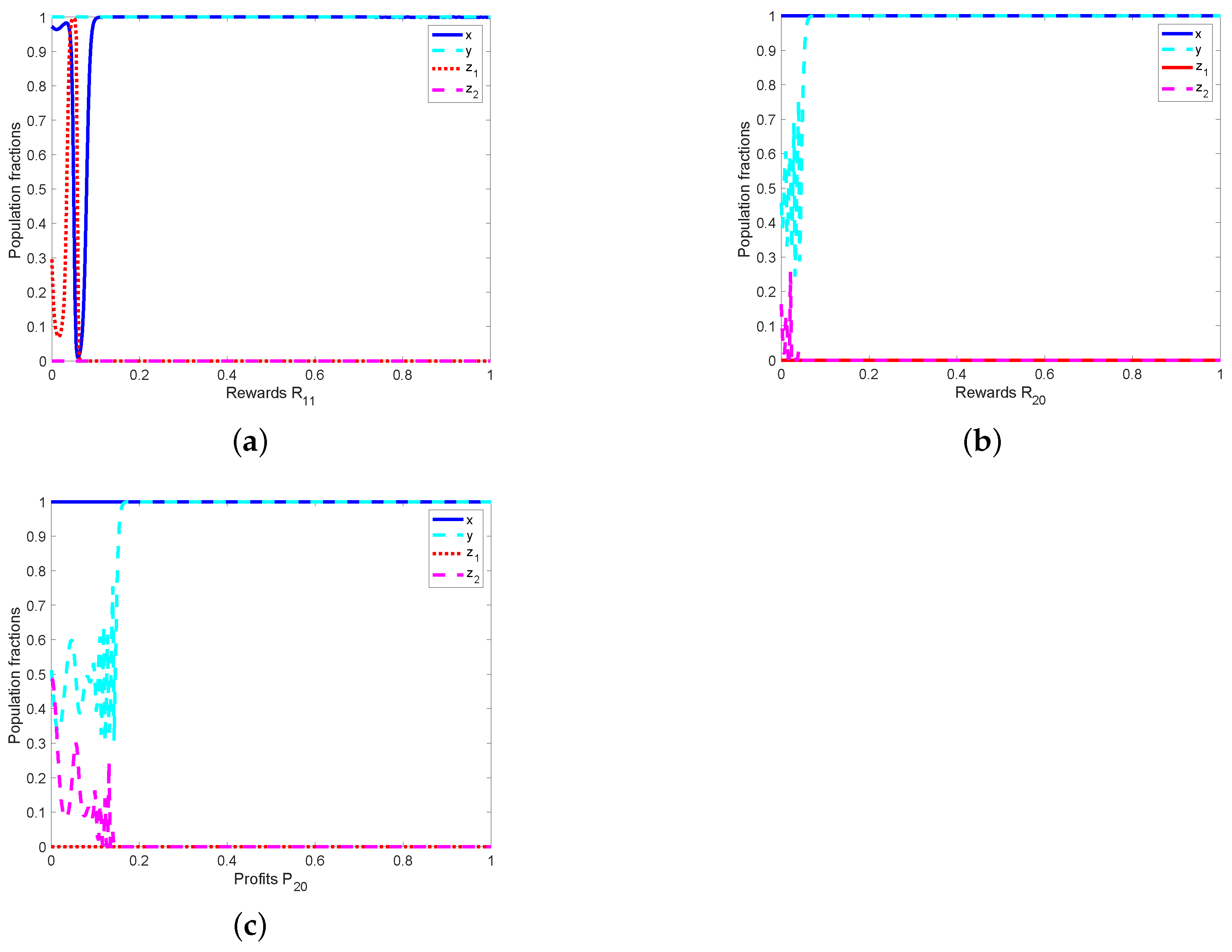
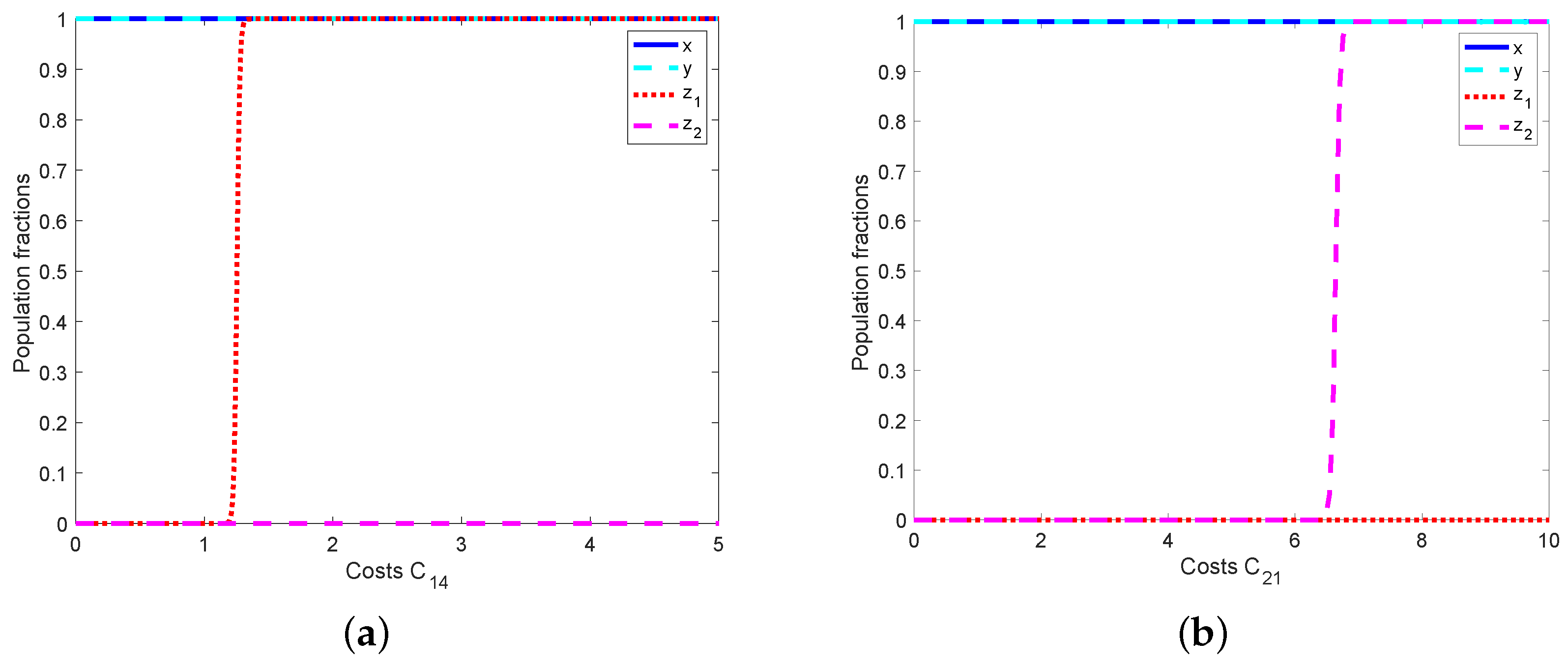
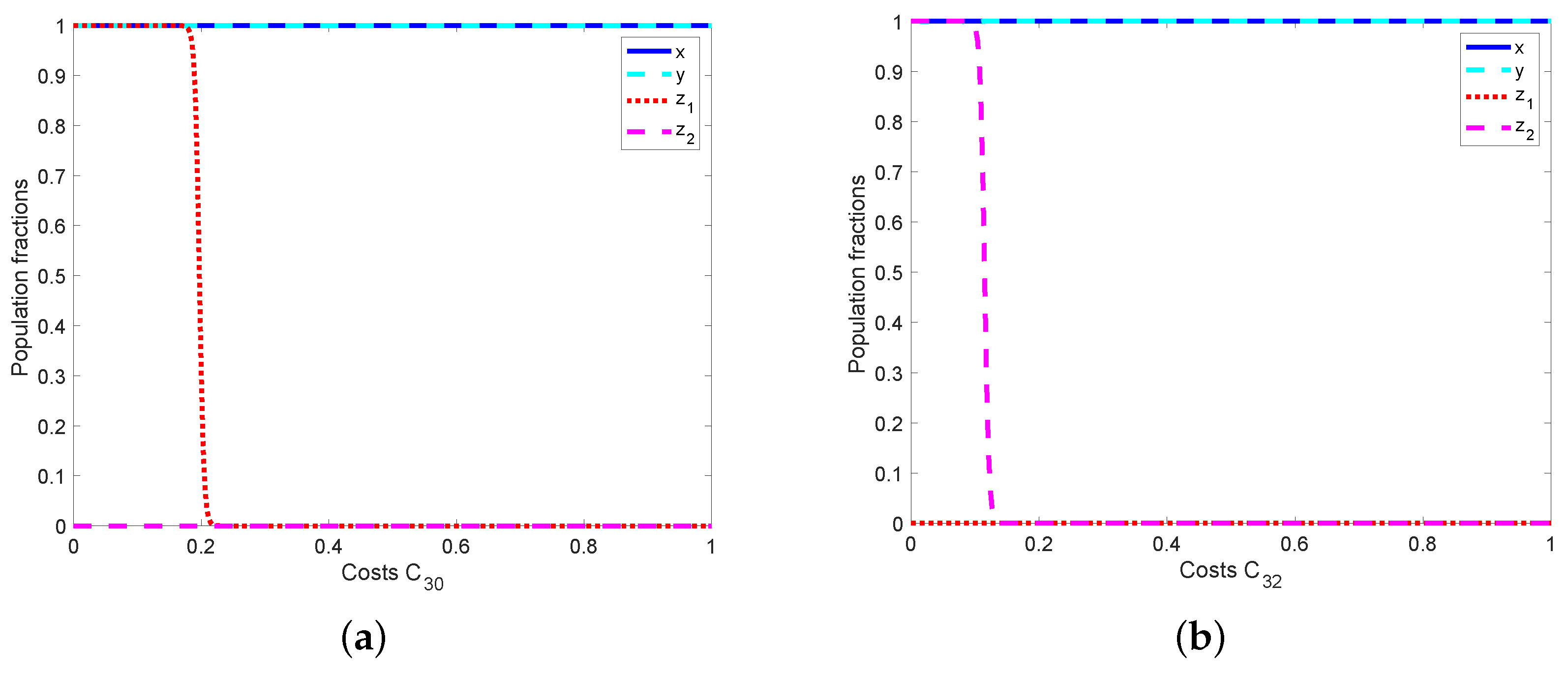
5.2. Analyzing the Effects of Cybersecurity and Cyberattack Costs on
5.2.1. The Impact of Cybersecurity Costs
5.2.2. The Impact of Rewards for Commitment to Cybersecurity
5.2.3. The Impact of Cyberattack Costs
5.2.4. Costs of Setting up Cyberattack Operations
6. Discussions
6.1. Interpretation of the Results
6.1.1. Cybersecurity Costs
6.1.2. Rewards
6.1.3. Cyberattack Costs
6.1.4. Operation Costs of Cyberattacks
6.2. Limitations and Future Work
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Statista. Smart Home Report 2022. 2022. Available online: https://www.statista.com/study/42112/smart-home-report/ (accessed on 10 January 2023).
- Cain, A.A.; Edwards, M.E.; Still, J.D. An exploratory study of cyber hygiene behaviors and knowledge. J. Inf. Secur. Appl. 2018, 42, 36–45. [Google Scholar] [CrossRef]
- Furnell, S.; Bryant, P.; Phippen, A. Assessing the security perceptions of personal Internet users. Comput. Secur. 2007, 26, 410–417. [Google Scholar] [CrossRef]
- Furnell, S.; Tsaganidi, V.; Phippen, A. Security beliefs and barriers for novice Internet users. Comput. Secur. 2008, 27, 235–240. [Google Scholar] [CrossRef]
- Tomczyk, Ł.; Potyrała, K. Parents’ knowledge and skills about the risks of the digital world. S. Afr. J. Educ. 2021, 41, 1–19. [Google Scholar] [CrossRef]
- D’Arcy, J.; Hovav, A.; Galletta, D. User awareness of security countermeasures and its impact on information systems misuse: A deterrence approach. Inf. Syst. Res. 2009, 20, 79–98. [Google Scholar] [CrossRef]
- Aldawood, H.; Skinner, G. Challenges of implementing training and awareness programs targeting cyber security social engineering. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference (CCC), Melbourne, VIC, Australia, 8–9 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 111–117. [Google Scholar]
- Morrison, B.; Coventry, L.; Briggs, P. How do Older Adults feel about engaging with Cyber-Security? Hum. Behav. Emerg. Technol. 2021, 3, 1033–1049. [Google Scholar] [CrossRef]
- Zhang, Z.J.; He, W.; Li, W.; Abdous, M. Cybersecurity awareness training programs: A cost-benefit analysis framework. Ind. Manag. Data Syst. 2021, 121, 613–636. [Google Scholar] [CrossRef]
- Douha, N.Y.R.; Fall, D.; Taenaka, Y.; Kadobayashi, Y. Threat Level Assessment of Smart-Home Stakeholders Using EBIOS Risk Manager. In Proceedings of the Fifteenth International Conference on Emerging Security Information, Systems and Technologies (IARIA SECURWARE 2021), Athens, Greece, 14–18 November 2021; pp. 31–40. [Google Scholar]
- Krichen, M.; Alroobaea, R. A New Model-Based Framework for Testing Security of IoT Systems in Smart Cities Using Attack Trees and Price Timed Automata. In Proceedings of the 14th International Conference on Evaluation of Novel Approaches to Software Engineering (ENASE 2019), Setubal, Portugal, 4–5 May 2019; pp. 570–577. [Google Scholar] [CrossRef]
- Tabrizi, F.M.; Pattabiraman, K. Formal Security Analysis of Smart Embedded Systems. In Proceedings of the 32nd Annual Conference on Computer Security Applications (ACSAC ’16), New York, NY, USA, 5–7 April 2016; pp. 1–15. [Google Scholar] [CrossRef]
- Kumar, P.; Braeken, A.; Gurtov, A.; Iinatti, J.; Ha, P.H. Anonymous Secure Framework in Connected Smart Home Environments. IEEE Trans. Inf. Forensics Secur. 2017, 12, 968–979. [Google Scholar] [CrossRef]
- Sandholm, W. Evolutionary Game Theory in Encyclopedia of Complexity and System Science; Springer: New York, NY, USA, 2009. [Google Scholar]
- Tosh, D.; Sengupta, S.; Kamhoua, C.; Kwiat, K.; Martin, A. An evolutionary game-theoretic framework for cyber-threat information sharing. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 7341–7346. [Google Scholar] [CrossRef]
- Alabdel Abass, A.A.; Xiao, L.; Mandayam, N.B.; Gajic, Z. Evolutionary Game Theoretic Analysis of Advanced Persistent Threats Against Cloud Storage. IEEE Access 2017, 5, 8482–8491. [Google Scholar] [CrossRef]
- Douha, N.Y.R.; Sane, B.O.; Sasabe, M.; Fall, D.; Taenaka, Y.; Kadobayashi, Y. Cost-benefit Analysis Toward Designing Efficient Education Programs for Household Security. In Proceedings of the Fifteenth International Conference on Emerging Security Information, Systems and Technologies (IARIA SECURWARE 2021), Athens, Greece, 14–18 November 2021; pp. 59–68. [Google Scholar]
- Kritzinger, E.; von Solms, S. Cyber security for home users: A new way of protection through awareness enforcement. Comput. Secur. 2010, 29, 840–847. [Google Scholar] [CrossRef]
- Howe, A.E.; Ray, I.; Roberts, M.; Urbanska, M.; Byrne, Z. The Psychology of Security for the Home Computer User. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012; pp. 209–223. [Google Scholar] [CrossRef]
- Alotaibi, F.; Clarke, N.; Furnell, S. An analysis of home user security awareness & education. In Proceedings of the 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017; pp. 116–122. [Google Scholar] [CrossRef]
- Ricci, J.; Breitinger, F.; Baggili, I. Survey results on adults and cybersecurity education. Educ. Inf. Technol. 2019, 24, 231–249. [Google Scholar] [CrossRef]
- Pattnaik, N.; Li, S.; Nurse, J.R. A Survey of User Perspectives on Security and Privacy in a Home Networking Environment. ACM Comput. Surv. 2022. just accepted. [Google Scholar] [CrossRef]
- Cavusoglu, H.; Raghunathan, S.; Yue, W.T. Decision-Theoretic and Game-Theoretic Approaches to IT Security Investment. J. Manag. Inf. Syst. 2008, 25, 281–304. [Google Scholar] [CrossRef]
- Douha, N.Y.R.; Bhuyan, M.; Kashihara, S.; Fall, D.; Taenaka, Y.; Kadobayashi, Y. A survey on blockchain, SDN and NFV for the smart-home security. Internet Things 2022, 20, 100588. [Google Scholar] [CrossRef]
- Nagurney, A.; Nagurney, L.S. A game theory model of cybersecurity investments with information asymmetry. NETNOMICS Econ. Res. Electron. Netw. 2015, 16, 127–148. [Google Scholar] [CrossRef]
- Nagurney, A.; Nagurney, L.S.; Shukla, S. A supply chain game theory framework for cybersecurity investments under network vulnerability. In Computation, Cryptography, and Network Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 381–398. [Google Scholar]
- Nagurney, A.; Daniele, P.; Shukla, S. A supply chain network game theory model of cybersecurity investments with nonlinear budget constraints. Ann. Oper. Res. 2017, 248, 405–427. [Google Scholar] [CrossRef]
- Tosh, D.K.; Vakilinia, I.; Shetty, S.; Sengupta, S.; Kamhoua, C.A.; Njilla, L.; Kwiat, K. Three Layer Game Theoretic Decision Framework for Cyber-Investment and Cyber-Insurance. In Proceedings of the Decision and Game Theory for Security; Rass, S., An, B., Kiekintveld, C., Fang, F., Schauer, S., Eds.; Springer: Cham, Switzerland, 2017; pp. 519–532. [Google Scholar]
- Hyder, B.; Govindarasu, M. Optimization of Cybersecurity Investment Strategies in the Smart Grid Using Game-Theory. In Proceedings of the 2020 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 17–20 February 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Sun, W.; Kong, X.; He, D.; You, X. Information Security Problem Research Based on Game Theory. In Proceedings of the 2008 International Symposium on Electronic Commerce and Security, Guangzhou, China, 3–5 August 2008; pp. 554–557. [Google Scholar] [CrossRef]
- Smith, J.M. Game theory and the evolution of fighting. In On Evolution; Edinburgh University Press: Edinburgh, UK, 1972; pp. 8–28. [Google Scholar]
- Smith, J.; Price, G.R. The logic of animal conflict. Nature 1973, 246, 15–18. [Google Scholar] [CrossRef]
- Nash, J. Non-cooperative games. Ann. Math. 1951, 54, 286–295. [Google Scholar] [CrossRef]
- Morgenstern, O.; Von Neumann, J. Theory of Games and Economic Behavior; Princeton University Press: Princeton, NJ, USA, 1953. [Google Scholar]
- Cressman, R.; Tao, Y. The replicator equation and other game dynamics. Proc. Natl. Acad. Sci. USA 2014, 111, 10810–10817. [Google Scholar] [CrossRef]
- IBM. X-Force Threat Intelligence Index 2022. 2022. Available online: https://www.ibm.com/security/data-breach/threat-intelligence/ (accessed on 17 January 2023).
- Sandholm, W.H. Evolutionary Game Theory. In Encyclopedia of Complexity and Systems Science; Springer: Berlin/Heidelberg, Germany, 2017; pp. 1–38. [Google Scholar] [CrossRef]
- Friedman, D. Evolutionary Games in Economics. Econometrica 1991, 59, 637–666. [Google Scholar] [CrossRef]
- Osborne, M.J. An Introduction to Game Theory; Oxford University Press: New York, NY, USA, 2004; Volume 3. [Google Scholar]
- Rodríguez-Licea, M.A.; Perez-Pinal, F.J.; Nuñez-Pérez, J.C.; Sandoval-Ibarra, Y. On the n-Dimensional Phase Portraits. Appl. Sci. 2019, 9, 872. [Google Scholar] [CrossRef]
- Acquisti, A.; Adjerid, I.; Balebako, R.; Brandimarte, L.; Cranor, L.F.; Komanduri, S.; Leon, P.G.; Sadeh, N.; Schaub, F.; Sleeper, M.; et al. Nudges for Privacy and Security: Understanding and Assisting Users’ Choices Online. ACM Comput. Surv. 2017, 50, 1–41. [Google Scholar] [CrossRef]
- ISO/IEC CD 27403.2; Cybersecurity—IoT Security and Privacy—Guidelines for IoT-Domotics. ISO: London, UK, 2022. Available online: https://www.iso.org/standard/78702.html (accessed on 17 January 2023).
- Sasaki, Y. The Equivalence of Evolutionary Games and Distributed Monte Carlo Learning; Economic Research Institute Study Papers; Utah State University: Logan, UH, USA, 2004. [Google Scholar]
- DeKoven, L.F.; Randall, A.; Mirian, A.; Akiwate, G.; Blume, A.; Saul, L.K.; Schulman, A.; Voelker, G.M.; Savage, S. Measuring Security Practices. Commun. ACM 2022, 65, 93–102. [Google Scholar] [CrossRef]
- European Commission. State of the Union: EU Cyber Resilience Act—Questions & Answers. 2022. Available online: https://ec.europa.eu/commission/presscorner/detail/en/qanda_22_5375 (accessed on 24 January 2023).


| Year | Reference | (Internet-Based) Home Users | (IoT-Based) Smart-Home Users | Cybersecurity Investment | Approach | Evolutionary Game Analysis |
|---|---|---|---|---|---|---|
| 2007 | Furnell, Bryant, and Phippen [3] | Yes | No | No | Empirical study of home users (survey) | No |
| 2008 | Furnell, Tsaganidi, and Phippen [4] | Yes | No | No | Empirical study of home users (interview) | No |
| 2008 | Sun et al. [30] | No | No | Yes | Game model using two-organization symmetric game | Yes, but no numerical results |
| 2010 | Kritzinger and von Solm [18] | Yes | No | No | Theoretical e-awareness model | No |
| 2012 | Howe et al. [19] | Yes | No | No | Literature review of factors that influence security decisions of home users | No |
| 2015 | Anna Nagurney and Ladimer Nagurney [25] | No | No | Yes | Game model using buyers and sellers | No |
| 2015 | Nagurney et al. [26] | No | No | Yes | Supply chain network game model using retailers and demand markets | No |
| 2017 | Alotaibi, Clarke, and Furnell [20] | Yes | No | No | Reviewing the existing security awareness tools for home users | No |
| 2017 | Nagurney et al. [27] | No | No | Yes | Supply chain network game model using retailers and demand markets with nonlinear budget constraints | No |
| 2017 | Tosh et al. [28] | No | No | Yes | Sequential game model using organizations, attackers, and insurers | No |
| 2019 | Ricci, Breitinger, and Baggili [21] | Yes | No | Yes | Empirical study of parents (survey) | No |
| 2020 | Hyder and Govindarasu [29] | No | No | Yes | Game model using attackers and defenders | No |
| 2021 | Łukasz and Potyrała [5] | Yes | No | No | Empirical study of parents (survey) | No |
| 2021 | Morrison, Coventry, and Briggs [8] | Yes | No | Yes | Empirical study of older adults (interview) | No |
| 2021 | Douha et al. [17] | Yes | Yes | Yes | Game model using an attacker and three categories of smart-home users | No |
| 2022 | Pattnaik, Li, and Nurse [22] | Yes | Yes | No | Literature review of user perspectives on security and privacy in a home networking environment | No |
| 2023 | This work | Yes | Yes | Yes | Game model using three-population asymmetric game | Yes |
| Parameters | Descriptions |
|---|---|
| T | invests in cybersecurity awareness training. |
| does not invest in cybersecurity awareness training. | |
| S | implements security best practices. |
| does not implement security best practices. | |
| adopts the strategy of no attack. | |
| deceives directly. | |
| deceives after compromising . | |
| Probability of compromising given the strategy T. | |
| Probability of compromising given the strategy . | |
| Probability of to compromise given the strategy S. | |
| Probability of compromising given the strategy . | |
| Cost of smart-home adoption. | |
| Households’ expenditure. | |
| Cost related to the strategy T. | |
| Cost of a security breach given the strategy . | |
| Cost of cyberattacks on involving interruption costs of smart-home | |
| services and affecting ’s comfort and safety. | |
| Cost of security implementation related to the strategy S. | |
| Cost of cyberattacks on involving loss of intellectual property and | |
| customer confidential information, and lost revenue. | |
| Cost of conducting a cyberattack targeting , given that | |
| takes the strategy T. | |
| Cost of conducting a cyberattack targeting , given that | |
| takes the strategy . | |
| Cost of conducting a cyberattack targeting , given that | |
| takes the strategy S. | |
| Cost of conducting a cyberattack targeting , given that | |
| takes the strategy . | |
| Households’ income. | |
| Amount of profit obtained by from selling smart-home devices given | |
| the strategy S. | |
| Amount of profit obtained by from selling smart-home devices given | |
| the strategy . | |
| The measure of the improved lifestyle that may enjoy by living in | |
| smart homes. | |
| Reward of for noticing security countermeasures based on | |
| the strategy T. | |
| The measure of ’s trust obtained by when considering | |
| the strategy S. |
| S | |||
| T | |||
0 | 0 | ||
| T | |||
0 | 0 | ||
| Parameters | Values |
|---|---|
| 0.3 | |
| 0.6 | |
| 0.1 | |
| 0.8 | |
| 0.1 | |
| 0.2 | |
| 0.6 | |
| 0.2 | |
| 0.8 | |
| 0.4 | |
| 0.15 | |
| 0.7 | |
| 0.25 | |
| 0.25 | |
| 0.1 | |
| 0.2 | |
| 0.15 | |
| Seven kinds of initial values : | (0.05, 0.1, 0.4, 0.5);
(0.1, 0.05, 0.2, 0.3); (0.01, 0.2, 0.6, 0.3); (0.4, 0.1, 0.3, 0.6); (0.2, 0.3, 0.4, 0.1); (0.1, 0.7, 0.1, 0.2); (0.7, 0.1, 0.3, 0.1). |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Douha, N.Y.-R.; Sasabe, M.; Taenaka, Y.; Kadobayashi, Y. An Evolutionary Game Theoretic Analysis of Cybersecurity Investment Strategies for Smart-Home Users against Cyberattacks. Appl. Sci. 2023, 13, 4645. https://doi.org/10.3390/app13074645
Douha NY-R, Sasabe M, Taenaka Y, Kadobayashi Y. An Evolutionary Game Theoretic Analysis of Cybersecurity Investment Strategies for Smart-Home Users against Cyberattacks. Applied Sciences. 2023; 13(7):4645. https://doi.org/10.3390/app13074645
Chicago/Turabian StyleDouha, N’guessan Yves-Roland, Masahiro Sasabe, Yuzo Taenaka, and Youki Kadobayashi. 2023. "An Evolutionary Game Theoretic Analysis of Cybersecurity Investment Strategies for Smart-Home Users against Cyberattacks" Applied Sciences 13, no. 7: 4645. https://doi.org/10.3390/app13074645
APA StyleDouha, N. Y.-R., Sasabe, M., Taenaka, Y., & Kadobayashi, Y. (2023). An Evolutionary Game Theoretic Analysis of Cybersecurity Investment Strategies for Smart-Home Users against Cyberattacks. Applied Sciences, 13(7), 4645. https://doi.org/10.3390/app13074645






