Enhancing the Performance of SQL Injection Attack Detection through Probabilistic Neural Networks
Abstract
1. Introduction
2. Related Work
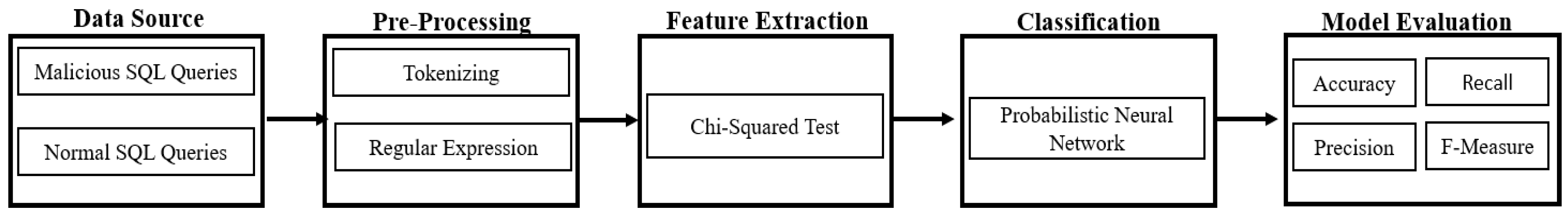
3. Detection of SQL Injection Using Probabilistic Neural Network
3.1. Data Collection
3.2. Pre-Processing
3.3. Feature Extraction
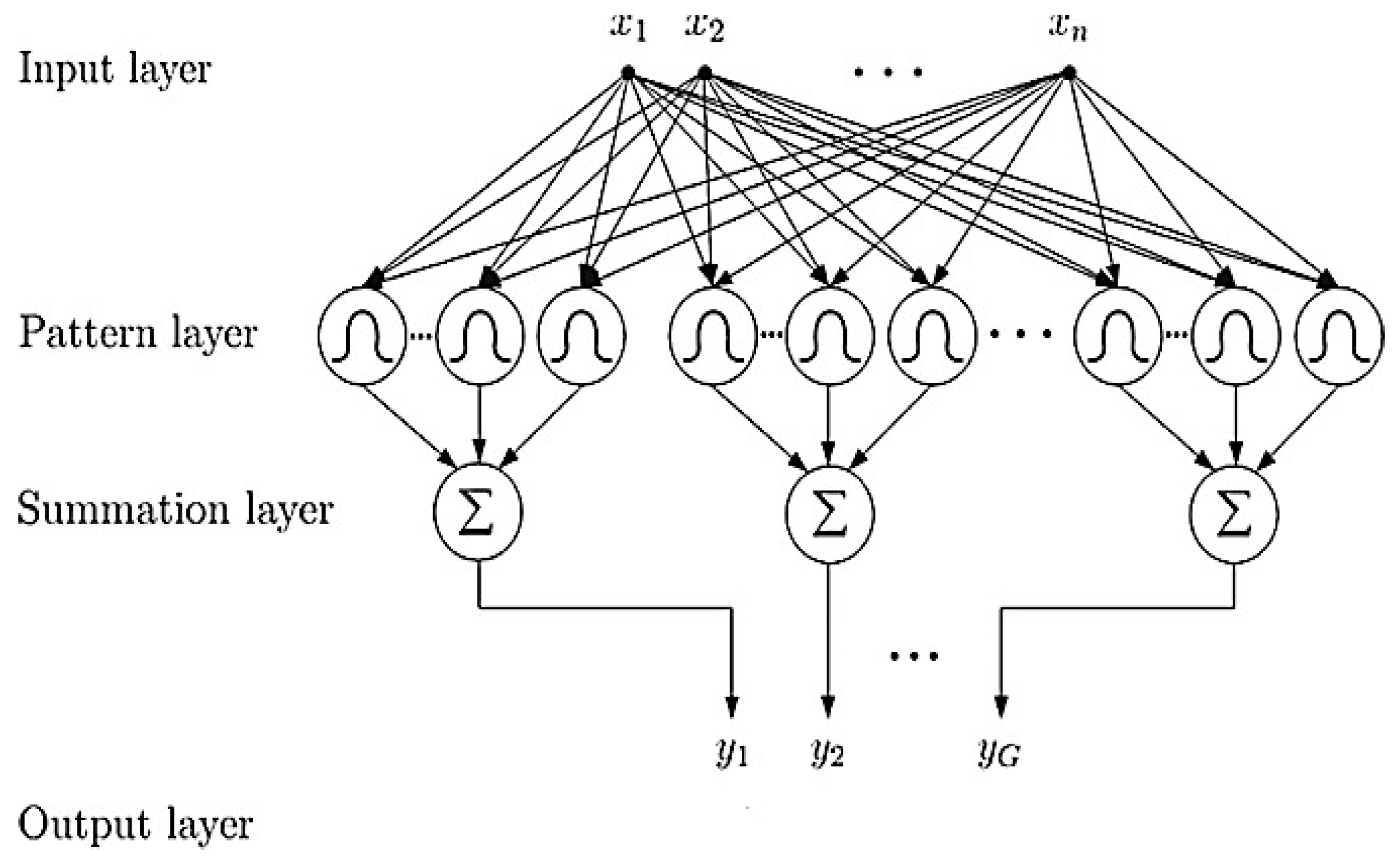
3.4. Probabilistic Neural Network
3.5. Smoothing Parameter Selection
| Algorithm 1: Standard Bat Algorithm |
| Begin Initialize position, velocity and other parameters for each bat While (Stop criteria is met?) Randomly generates the frequency Update the velocity Update the position If rand< Update the position End Calculate the fitness; If (rand<)&& (< ) Replace the position with the new one Update and End Select the current global best position End Output the best position End |
3.6. Model Evaluation
4. Experimental Results and Implementation Details
- The bat size was limited to 30, and the number of iterations was set to a maximum of 100, as represented in Equation (9).
- 2.
- For each bat, the position was calculated randomly. The position of the bat gave the smoothing parameter h.
- 3.
- The bat’s primary position was randomly generated with a uniform distribution of [0, 10].
- 4.
- The fitness function ff, as given in Equation (10), was used; this takes the induvial solution of a problem as the input and generates the output to define “how fit and good” the solution is with respect to the actual problem.
- 5.
- The position of the bat was updated to:
- 6.
- Steps 4 and 5 were repeated until Tmax was achieved.
- Scenario 1: Using 100% Training Data.
| Classifier | Accuracy | Precision | Recall | F-Measure |
|---|---|---|---|---|
| PNN | 98.69% | 0.975% | 0.961% | 0.964% |
| SVM | 95.62% | 0.95% | 0.884% | 0.878% |
| Decision Tree | 96.31% | 0.917% | 0.926% | 0.916% |
| ANN | 97.25% | 0.984% | 0.876% | 0.932% |
- Scenario 2: Partitioning the data into 80:20 Training and Testing.
| Classifier | Accuracy | Precision | Recall | F-Measure |
|---|---|---|---|---|
| PNN | 98.11% | 0.978% | 0.972% | 0.917% |
| SVM | 96.65% | 0.942% | 0.975% | 0.978% |
| Decision Tree | 97.42% | 0.96% | 0.889% | 0.881% |
| ANN | 98.18% | 0.984% | 0.876% | 0.932% |
- Scenario 3: Using 10-Fold Cross Validation.
| Classifier | Accuracy | Precision | Recall | F-Measure |
|---|---|---|---|---|
| PNN | 99.19% | 0.995% | 0.981% | 0.928% |
| SVM | 96.32% | 0.96% | 0.889% | 0.881% |
| Decision Tree | 97.33% | 0.972% | 0.968% | 0.938% |
| ANN | 98.54% | 0.98% | 0.963% | 0.924% |
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Khan, N.; Abdullah, J.; Khan, A.S. Defending Malicious Script Attacks Using Machine Learning Classifiers. Wirel. Commun. Mob. Comput. 2017, 2017, 5360472. [Google Scholar] [CrossRef]
- OWASP: Top 10 Web Application Security Risks. 2021. Available online: https://owasp.org/www-project-top-ten/ (accessed on 1 March 2023).
- SQL Injection Attacks Rise Over 300% in 10 Years, Imperva. Available online: https://www.imperva.com/blog/sql-injection-attacks-rise-over-300-in-10-years/ (accessed on 1 March 2023).
- Khan, N.; Abdullah, J.; Khan, A.S. Towards vulnerability prevention model for web browser using interceptor approach. In Proceedings of the 2015 9th International Conference on IT in Asia (CITA), Sarawak, Malaysia, 4–5 August 2015. [Google Scholar] [CrossRef]
- Jain, V.; Gaur, M.S.; Laxmi, V.; Mosbah, M. Detection of SQLite Database Vulnerabilities in Android Apps. In Proceedings of the Information Systems Security: 12th International Conference, ICISS 2016, Jaipur, India, 16–20 December 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 521–531. [Google Scholar] [CrossRef]
- Kareem, F.Q.; Ameen, S.Y.; Salih, A.A.; Ahmed, D.M.; Kak, S.F.; Yasin, H.M.; Ibrahim, I.M.; Ahmed, A.M.; Rashid, Z.N.; Omar, N. SQL Injection Attacks Prevention System Technology: Review. Asian J. Res. Comput. Sci. 2021, 6, 13–32. [Google Scholar] [CrossRef]
- Aldhyani, T.H.H.; Alkahtani, H. Cyber Security for Detecting Distributed Denial of Service Attacks in Agriculture 4.0: Deep Learning Model. Mathematics 2023, 11, 233. [Google Scholar] [CrossRef]
- Aldhyani, T.H.H.; Alkahtani, H. Artificial Intelligence Algorithm-Based Economic Denial of Sustainability Attack Detection Systems: Cloud Computing Environments. Sensors 2022, 22, 4685. [Google Scholar] [CrossRef]
- Su, G.; Wang, F.; Li, Q. Research on SQL Injection Vulnerability Attack model. In Proceedings of the 5th IEEE International Conference on Cloud Computing and Intelligence Systems (CCIS), Nanjing, China, 23–25 November 2018; pp. 217–221. [Google Scholar]
- Lee, I.; Jeong, S.; Yeo, S.; Moon, J. A novel method for SQL injection attack detection based on removing SQL query attribute values. Math. Comput. Model. 2012, 55, 58–68. [Google Scholar] [CrossRef]
- Lavecchia, A. Deep learning in drug discovery: Opportunities, challenges and future prospects. Drug Discov. Today 2019, 24, 2017–2032. [Google Scholar] [CrossRef]
- Torres, J.M.; Comesaña, C.I.; Garcia-Nieto, P.J. Machine learning techniques applied to cybersecurity. Int. J. Mach. Learn. Cybern. 2019, 10, 2823–2836. [Google Scholar] [CrossRef]
- Alkahtani, H.; Aldhyani, T.H.H. Artificial Intelligence Algorithms for Malware Detection in Android-Operated Mobile Devices. Sensors 2022, 22, 2268. [Google Scholar] [CrossRef] [PubMed]
- Yavanoglu, O.; Aydos, M. A review on cyber security datasets for machine learning algorithms. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2186–2193. [Google Scholar]
- Khan, N.A.; Alzaharani, M.Y.; Kar, H.A. Hybrid Feature Classification Approach for Malicious JavaScript Attack Detection using Deep Learning. Int. J. Comput. Sci. Inf. Secur. 2020, 5, 18. [Google Scholar]
- Alqarni, A.A.; Alsharif, N.; Khan, N.A.; Georgieva, L.; Pardade, E.; Alzahrani, M.Y. MNN-XSS: Modular Neural Network Based Approach for XSS Attack Detection. Comput. Mater. Contin. 2022, 70, 4075–4085. [Google Scholar] [CrossRef]
- Khan, N.; Abdullah, J.; Khan, A.S. A Dynamic Method of Detecting Malicious Scripts Using Classifiers. Adv. Sci. Lett. 2017, 23, 5352–5355. [Google Scholar] [CrossRef]
- Alkahtani, H.; Aldhyani, T.H.H. Developing Cybersecurity Systems Based on Machine Learning and Deep Learning Algorithms for Protecting Food Security Systems: Industrial Control Systems. Electronics 2022, 11, 1717. [Google Scholar] [CrossRef]
- Khan, N.; Johari, A.; Adnan, S. A Taxonomy Study of XSS Vulnerabilities. Asian J. Inf. Technol. 2017, 16, 169–177. [Google Scholar]
- Aliero, M.S.; Qureshi, K.N.; Pasha, M.F.; Ahmad, A.; Jeon, G. Detection of structure query language injection vulnerability in web driven database application. Concurr. Comput. Pract. Exp. 2020, 34, 5936. [Google Scholar] [CrossRef]
- Joshi, A.; Geetha, V. SQL Injection detection using machine learning. In Proceedings of the 2014 International Conference on Control, Instrumentation, Communication and Computational Technologies (ICCICCT), Kanyakumari District, India, 10–11 July 2014; pp. 1111–1115. [Google Scholar]
- Kamtuo, K.; Soomlek, C. Machine Learning for SQL injection prevention on server-side scripting. In Proceedings of the 2016 International Computer Science and Engineering Conference (ICSEC), London, UK, 29 June–1 July 2016; pp. 1–6. [Google Scholar]
- Kranthikumar, B.; Velusamy, R.L. SQL injection detection using REGEX classifier. J. Xi’an Univ. Archit. Technol. 2020, 12, 800–809. [Google Scholar]
- Wang, Y.; Cai, W.-D.; Wei, P.-C. A deep learning approach for detecting malicious JavaScript code. Secur. Commun. Netw. 2016, 9, 1520–1534. [Google Scholar] [CrossRef]
- Abaimov, S.; Bianchi, G. CODDLE: Code-Injection Detection With Deep Learning. IEEE Access 2019, 7, 128617–128627. [Google Scholar] [CrossRef]
- Kusy, M.; Zajdel, R. Probabilistic neural network training procedure based on Q(0)-learning algorithm in medical data classification. Appl. Intell. 2014, 41, 837–854. [Google Scholar] [CrossRef]
- Libinjection-Python. Available online: https://pypi.org/project/libinjection-python/ (accessed on 5 January 2023).
- Regular Expression Operations. Available online: https://docs.python.org/3/library/re.html (accessed on 5 January 2023).
- Zeinali, Y.; Story, B.A. Competitive probabilistic neural network. Integr. Comput.-Aided Eng. 2017, 24, 105–118. [Google Scholar] [CrossRef]
- Chang, D.T. Probabilistic Deep Learning with Probabilistic Neural Networks and Deep Probabilistic Models. arXiv 2021, arXiv:2106.00120. [Google Scholar]
- Zhu, H.; Lu, L.; Yao, J.; Dai, S.; Hu, Y. Fault diagnosis approach for photovoltaic arrays based on unsupervised sample clustering and probabilistic neural network model. Sol. Energy 2018, 176, 395–405. [Google Scholar] [CrossRef]
- Yang, X.S. A new metaheuristic bat-inspired algorithm. In Nature Inspired Cooperative Strategies for Optimization; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Naik, S.M.; Jagannath, R.P.K.; Kuppili, V. Estimation of the Smoothing Parameter in Probabilistic Neural Network Using Evolutionary Algorithms. Arab. J. Sci. Eng. 2020, 45, 2945–2955. [Google Scholar] [CrossRef]
- Zhang, M.; Cui, Z.; Chang, Y.; Ren, Y.; Cai, X.; Wang, H. Bat algorithm with individual local search. In International Conference on Intelligence Science; Springer: Berlin/Heidelberg, Germany, 2018; pp. 442–451. [Google Scholar]
- PyTorch Machine Learning Framework. Available online: https://pytorch.org (accessed on 5 January 2023).

| Feature Name | Feature Description |
|---|---|
| Token_Count | Counts the presence of specific tokens in the whole dataset |
| Token_Type | Category to which the token belongs, such as plain text or SQL injection attack |
| Token_Value | The actual parameter value of the token |
| Type_Protocol | Transmission Control Protocol (TCP) Internet Protocol (IP) Internet Control Message Protocol (ICMP) |
| Length_TCP | Data Offset; The size of the TCP header in 32-bit words |
| http_content_length | Length of Entity Body |
| Type_Port_Req | Port Type |
| Source_Data_length | Number of Characters in a String |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alarfaj, F.K.; Khan, N.A. Enhancing the Performance of SQL Injection Attack Detection through Probabilistic Neural Networks. Appl. Sci. 2023, 13, 4365. https://doi.org/10.3390/app13074365
Alarfaj FK, Khan NA. Enhancing the Performance of SQL Injection Attack Detection through Probabilistic Neural Networks. Applied Sciences. 2023; 13(7):4365. https://doi.org/10.3390/app13074365
Chicago/Turabian StyleAlarfaj, Fawaz Khaled, and Nayeem Ahmad Khan. 2023. "Enhancing the Performance of SQL Injection Attack Detection through Probabilistic Neural Networks" Applied Sciences 13, no. 7: 4365. https://doi.org/10.3390/app13074365
APA StyleAlarfaj, F. K., & Khan, N. A. (2023). Enhancing the Performance of SQL Injection Attack Detection through Probabilistic Neural Networks. Applied Sciences, 13(7), 4365. https://doi.org/10.3390/app13074365






