Towards a Provably Secure Authentication Protocol for Fog-Driven IoT-Based Systems
Abstract
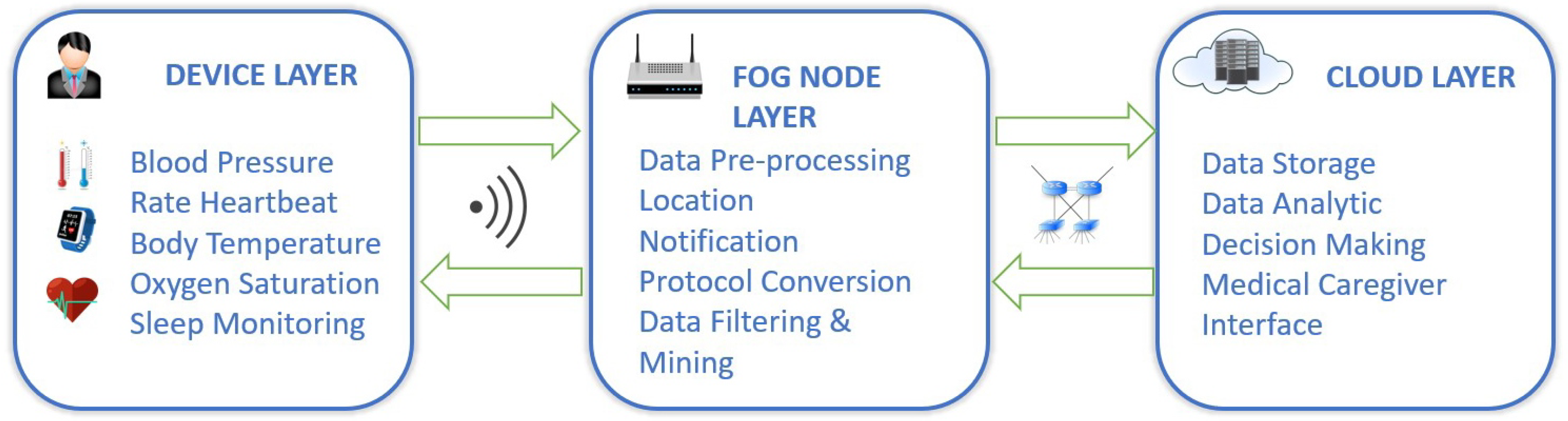
:1. Introduction
- This paper presents a three-party identity-based authenticated key agreement scheme to secure the communication of data among the participants in an IoT based fog-driven healthcare system. The robust identity-based three-party AKA protocol is designed using hash, XOR and concatenation operations.
- The proposed protocol ensures mutual authentication among users, fog-nodes and cloud service providers for the establishment of a shared session key. This shared session key is used by all the participants.
- Our designed protocol guarantees that the identity of any user can not be exposed to any adversary except the cloud server.
2. Complexity Assumptions
Threat Assumption Model
- has full control over the public channel.
- can be a user or cloud service provider.
- is assumed to be honest but curious, whereas, is assumed as untrustworthy entity; because of that, it does not keep any verifier of .
- can intercept the messages that are exchanged over the public channel between , or .
- can modify and replay the intercepted messages to misuse them.
- The cloud service provider is a secure entity, so, cannot access it.
- can be an insider or outsider. An outsider can be a deceitful user and internal can be a cloud server, provider or user.
3. Proposed ITP-AKA Protocol
3.1. User Registration Phase
- 1:
- randomly chooses , identity and computes . sends to via a secure channel.
- 2:
- After receiving request, computes the following values: . Further, selects for the respective user and calculates and stores in its database corresponding to and using x. then transmits to using a private channel.
- 3:
- After receiving the message from , computes and stores in its tamper-proof device.
3.2. Fog-Node Registration Phase
- 1:
- sends its identity to the . On obtaining the identity, calculates and selects . stores in its database corresponding to using x, and transmits to the fog-node via a secure channel.
- 2:
- After taking the message from , stores in its tamper-proof device.
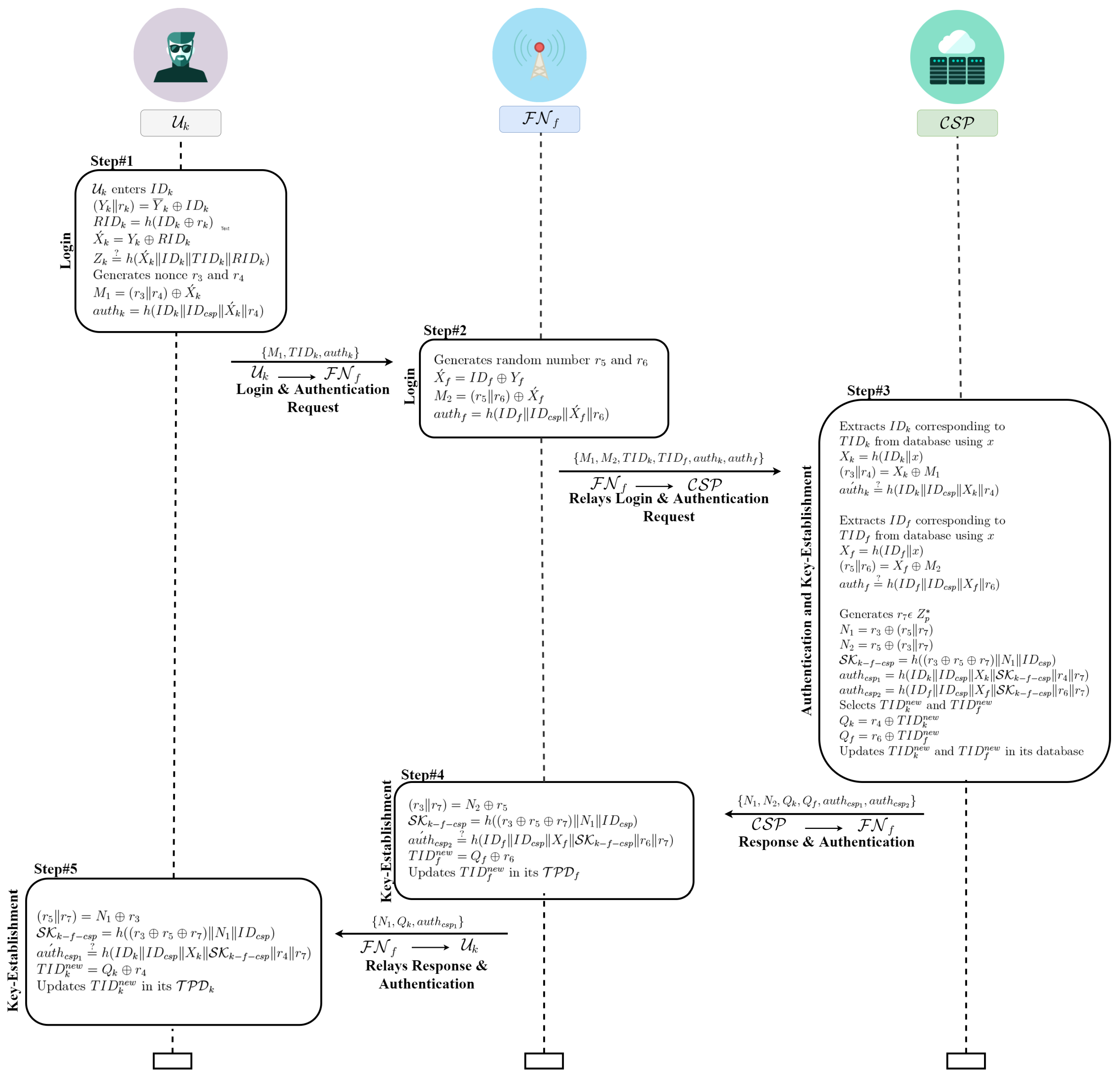
3.3. Login and Authentication Phase
- Step#1 • Login:
- inputs its identity and computes , , . After that, verifies . If the condition is true, generates arbitrary numbers , and calculates , and forwards the login request message towards . Otherwise, the login request by is rejected. .
- Step#2 • Login:
- After receiving the authentication request from , generates an arbitrary numbers , and computes , , . forwards to the . .
- Step#3 • Authentication & Key Establishment:
- After receiving the authentication request message from , extracts user’s corresponding to from its database using x, and determines , . For authenticating the user, verifies . If the condition is false, the current session will be ended. Otherwise, extracts fog-node corresponding to from its database using x, and determines , . Now, for authenticating the fog-node, verifies . If this condition is wrong, the session will be aborted. Once the aforementioned conditions are true, then generates an arbitrary number and computes , , , . Furthermore, selects for the user and for the fog-node and computes , and updates the value of and for the user and the fog-node in its database and transmits the response message to the . .
- Step#4 • Key Establishment:
- On receiving the response message from , computes , . Furthermore, authenticates by verifying . If this condition is wrong, the current session will be ended. Otherwise, it will calculate and update the value of in the tamper-proof device of the fog-node and relays to . .
- Step#5 • Key Establishment:
- On receiving the response message from , computes . Moreover, authenticates by verifying . If this condition goes wrong, the current session will be ended. Otherwise, it will calculate and update the value of in the user tamper-proof device.
3.4. User Revocation Phase
- 1:
- randomly chooses a new , identity and computes . sends to using a private channel.
- 2:
- After getting request, computes the following values . Afterwords, selects for the respective and calculates and stores in its database corresponding to using x. then transmits to via a private channel.
- 3:
- After getting the message from , computes and storesin its tamper-proof device.
4. Security Analysis
4.1. Informal Security Analysis
4.1.1. Providing Mutual Authentication
4.1.2. Providing User Anonymity and Untraceability
4.1.3. Resisting Tamper-Proof Device Stolen Attacks
4.1.4. Resisting User Masquerading Attacks
4.1.5. Resisting Fog-Node Masquerading Attacks
4.1.6. Resisting Cloud Service Provider Masquerading Attacks
4.1.7. Stolen-Verifier Attacks
4.1.8. Resisting Known Session Key Attacks
4.1.9. Perfect Forward and Backward Secrecy
4.2. Formal Security Analysis
Random Oracle Model
- (: After getting the query, C initiates a new session and returns the login message produced by the user. Particularly, C chooses and randomly and computes Moreover, C returns to , and is set to an expecting state.
- (): After getting this query, C first breaks the into picks , and computes , , . Then C returns to and sets to an expecting state.
- (): After getting this query, C breaks the into and computes and and checks either and holds or not. If not, query is rejected by C and returns nothing. Else, C picks and calculates and sends to and instance terminates.
- (): After getting this query, it is assumed that is in an expecting state, and determines if holds or not, If not, then C rejects query otherwise C returns back to and fog instance terminates.
- (): After getting this send query, it is supposed that is in an expecting state, C breaks into which verifies . If this condition does not hold then C rejects query and returns nothing. Otherwise, C calculates and the instance of the client is accepted and terminated. Furthermore, are added to list.
- Event (): Collision on the result hash queries.
- Event (): Collision on the copy of all messages ().
- When initiates a ()) query, C generates and forwards to .
- When generates a query , C generates a message to .
- When initiates a query , C sets and terminates the instance.
- When initiates a query (), C sets and returns message to . It is demonstrated that if the hard assumption holds, then the difference between and is ignorable, just as follows:
- Event (): queried oracle, which has probability of
- Event (): impersonates the user by forging the which posseses the verification executed by . The probability of generating a valid by is:
- Event (): successfully impersonates the fog-node by forging , which passes the verification executed by . Like Event , the probability of generating a valid by is:
5. Performance Comparison
5.1. Experimental Setup
5.2. Computation Overhead
5.3. Communication Overhead
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shamshad, S.; Ayub, M.F.; Mahmood, K.; Kumari, S.; Chaudhry, S.A.; Chen, C.M. An enhanced scheme for mutual authentication for healthcare services. Digit. Commun. Netw. 2022, 8, 150–161. [Google Scholar] [CrossRef]
- Shamshad, S.; Mahmood, K.; Hussain, S.; Garg, S.; Das, A.K.; Kumar, N.; Rodrigues, J.J. An Efficient Privacy-Preserving Authenticated Key Establishment Protocol for Health Monitoring in Industrial Cyber–Physical Systems. IEEE Internet Things J. 2021, 9, 5142–5149. [Google Scholar] [CrossRef]
- Mahmood, K.; Obaidat, M.; Ghaffar, Z.; Alzahrani, B.A.; Shamshad, S.; Saleem, M.A.; Hussain, S. Cloud-assisted Secure and Cost-effective Authenticated Solution for Remote Wearable Health Monitoring System. IEEE Trans. Netw. Sci. Eng. 2022. [Google Scholar] [CrossRef]
- Zia, M.; Obaidat, M.S.; Mahmood, K.; Shamshad, S.; Saleem, M.A.; Chaudhry, S.A. A Provably Secure Lightweight Key Agreement Protocol for Wireless Body Area Networks in Healthcare System. IEEE Trans. Ind. Inform. 2022, 19, 1683–1690. [Google Scholar] [CrossRef]
- Yang, J.H.; Chang, C.C. An ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. Comput. Secur. 2009, 28, 138–143. [Google Scholar] [CrossRef]
- Li, X.; Xiong, Y.; Ma, J.; Wang, W. An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 2012, 35, 763–769. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- Amin, R.; Kumar, N.; Biswas, G.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Future Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- Kumar, M.; Saxena, P. PF-AID-2KAP: Pairing-Free Authenticated Identity-Based Two-Party Key Agreement Protocol for Resource-Constrained Devices. In Proceedings of the International Conference on Futuristic Trends in Network and Communication Technologies, Solan, India, 9–10 February 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 425–440. [Google Scholar]
- Jia, X.; He, D.; Kumar, N.; Choo, K.K.R. A provably secure and efficient identity-based anonymous authentication scheme for mobile edge computing. IEEE Syst. J. 2019, 14, 560–571. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.K.R. An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad hoc networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Kumar, N.; Choo, K.K.R. Authenticated key agreement scheme for fog-driven IoT healthcare system. Wirel. Netw. 2019, 25, 4737–4750. [Google Scholar] [CrossRef]
- Chen, C.M.; Huang, Y.; Wang, K.H.; Kumari, S.; Wu, M.E. A secure authenticated and key exchange scheme for fog computing. Enterp. Inf. Syst. 2020, 15, 1200–1215. [Google Scholar] [CrossRef]
- Naqvi, H.; Chaudhry, S.; Mahmood, K. An improved authentication protocol for SIP-based VoIP. In Proceedings of the International Conference on Recent Advances in Computer Systems, Hail, Saudi Arabia, 30 November–1 December 2015; Atlantis Press: Amsterdam, The Netherlands, 2015; pp. 7–12. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Sahoo, S.S.; Mohanty, S.; Majhi, B. A secure three factor based authentication scheme for health care systems using IoT enabled devices. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 1419–1434. [Google Scholar] [CrossRef]
- Ever, Y.K. Secure-anonymous user authentication scheme for e-healthcare application using wireless medical sensor networks. IEEE Syst. J. 2018, 13, 456–467. [Google Scholar] [CrossRef]

| Authors | Year | Technique | Demerits |
|---|---|---|---|
| Yang and Chang [5] | 2009 | ECC-based | Lacks perfect forward secrecy and vulnerable to impersonation attacks |
| Li et al. [6] | 2012 | Identity-based | Prone to impersonation and DoS attacks |
| Tsai and Lo [7] | 2015 | Bilinear pairing | High computation overhead and prone to impersonation attacks |
| Amin et al. [8] | 2018 | Hash-based | Prone to stolen smart-card and insider attacks |
| Kumar et al. [9] | 2018 | Identity-baseds | Lacks user anonymity and privacy |
| Jia et al. [10] | 2019 | Identity-based | Vulnerable to impersonation attacks |
| Ma et al. [11] | 2020 | Bilinear pairing | Vulnerable to impersonation and secret key leakage attacks |
| Jia et al. [12] | 2020 | Bilinear pairing | Vulnerable to ephemeral secret leakage (ESL) attack |
| Chen et al. [13] | 2020 | Bilinear pairing | Vulnerable to impersonation attacks |
| Notations | Elucidation |
|---|---|
| user of the system | |
| Identity of | |
| Tamper proof device issued to each specific | |
| Temporary identity of | |
| Fog-node | |
| Identity of | |
| Temporary identity of | |
| Tamper proof device of | |
| Cloud service provider | |
| Identity of | |
| x | Private key of |
| Session key between , and | |
| ∥ | Concatenation operator |
| ⊕ | XoR operator |
| Attacker | |
| One-way hashing function | |
| Identity-based cryptography | |
| Authenticated key agreement |
| Attribute | Arduino | Cloud Server | Mobile Device |
|---|---|---|---|
| Platform | - | Online cloud server | Android |
| System | Microcontroller: ATmega328 | PythonAnywhere | Mediatek P60 |
| RAM | SRAM: 2 KB (ATmega328) | — | 6 GB |
| Clock Speed | 16 MHz | — | 2.0 GHZ |
| IDE | Arduino IDE | Python console | Android Studio |
| Execution Time | Parameter | |||
|---|---|---|---|---|
| Hash function | ms | ms | ms | |
| Point multiplication | ms | ms | ms | |
| Encryption/decryption | ms | ms | ms |
| Protocols | Aggregated Computation Overhead | Aggregated Communication Overhead | |||
|---|---|---|---|---|---|
| Ours | 0.5904 ms | 3744 bits | |||
| Jia et al. [12] | 1.5823 ms | 4064 bits | |||
| Chen et al. [13] | 3.1449 ms | 4832 bits | |||
| Ma et al. [11] | 2.3706 ms | 4254 bits | |||
| Sahoo et al. [17] | 1.5825 ms | 2560 bits | |||
| Ever [18] | 0.91771 ms | 1120 bits |
| Protocols → | Ours | [12] | [13] | [11] | [17] | [18] |
|---|---|---|---|---|---|---|
| Security Features ↓ | ||||||
| Provides mutual authentication | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
| Provides user anonymity | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| Resists tamper-proof device stolen attack | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| Resists user masquerading attack | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ |
| Resists fog-node masquerading attack | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ |
| Resists cloud server-provider masquerading attack | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ |
| Resists stolen-verifier attack | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ |
| Free from clock synchronization problem | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| Ephemeral secret leakage (ESL) attack | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ |
| Resists insider attack | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ |
| Resists known session key attack | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rana, M.; Mahmood, K.; Saleem, M.A.; Al-Turjman, F.; Kolhar, M.S.; Altrjman, C. Towards a Provably Secure Authentication Protocol for Fog-Driven IoT-Based Systems. Appl. Sci. 2023, 13, 1424. https://doi.org/10.3390/app13031424
Rana M, Mahmood K, Saleem MA, Al-Turjman F, Kolhar MS, Altrjman C. Towards a Provably Secure Authentication Protocol for Fog-Driven IoT-Based Systems. Applied Sciences. 2023; 13(3):1424. https://doi.org/10.3390/app13031424
Chicago/Turabian StyleRana, Minahil, Khalid Mahmood, Muhammad Asad Saleem, Fadi Al-Turjman, Manjur Sayyadbadasha Kolhar, and Chadi Altrjman. 2023. "Towards a Provably Secure Authentication Protocol for Fog-Driven IoT-Based Systems" Applied Sciences 13, no. 3: 1424. https://doi.org/10.3390/app13031424
APA StyleRana, M., Mahmood, K., Saleem, M. A., Al-Turjman, F., Kolhar, M. S., & Altrjman, C. (2023). Towards a Provably Secure Authentication Protocol for Fog-Driven IoT-Based Systems. Applied Sciences, 13(3), 1424. https://doi.org/10.3390/app13031424







