AICrit: A Design-Enhanced Anomaly Detector and Its Performance Assessment in a Water Treatment Plant
Abstract
:1. Introduction
- RQ 1: How effective is AICrit in detecting the cyber-physical attacks that have an adverse impact on the physical processes of underlying SWaT?, and
- RQ 2: How efficient is AICrit in supporting the plant operators toward active incident response and recovery?
- Provides detailed information on the attacks launched, and their impact, on an operational water treatment plant during a large cyber exercise.
- The performance of AICrit is compared with that of DAD—a design-centric anomaly detection mechanism.
- Lessons learned during the exercise are reported. We believe that these lessons are useful to researchers in the design of machine learning-based defense mechanisms for safeguarding CI and translating them to large-scale systems.
2. Preliminaries and Background
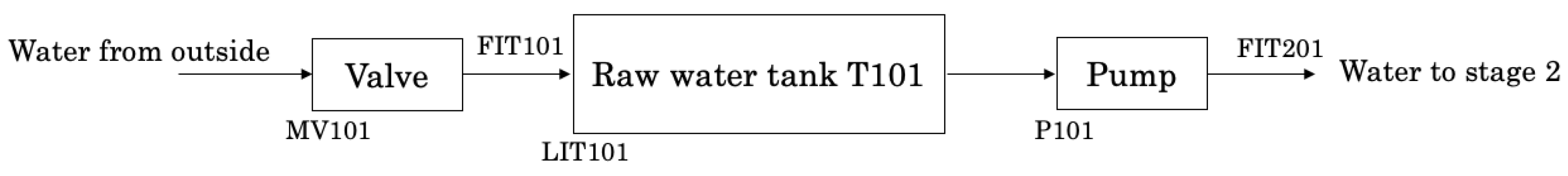
2.1. SWaT—Architecture
2.2. AICrit
- PbNN (Physics-based Neural Network) approach [5]: This method employs a physics-based deep learning algorithm to model the behavior of LIT101. It considers the spatiotemporal relationships between the interdependent components of LIT101, i.e., FIT101 and FIT201, as a non-linear function formulated as follows,where and denote measurements from the sensors LIT101, FIT101 and FIT201, respectively, at time t. With the availability of historical data, a physical model can be built using Equation (1) to predict with minimal error.
- NN (Neural network) approach [6]: This method considers the prediction of LIT101 as a time series forecasting problem. The LSTM is utilized to learn and model the temporal dependencies represented as present in the historical readings of LIT101.The resulting model is then deployed to predict LIT101.
2.3. CISS2021-OL
- Red team: Up to 10 local and international teams from government organizations, the private sector, and academia.
- Blue team: Commercial vendors were invited based on their past performance in similar events and nominations by Singapore Government agencies.
- IHL Anomaly Detection teams: Anomaly detectors from iTrust.
- CII Blue Teams: CII operators and regulators.
- Observers: Singapore Government agencies and their invitees.
- Red Week—September 6 to 11: Each red team was assigned a 5-h slot during which they were able to launch attacks. Points earned by each team were weighted based on the impact of the attack and the number of defense mechanisms successfully bypassed. Blue team members were commercial vendors who deployed their technologies to defend against the red team attacks.
- Blue Week—September 13 to 17: A composite red team from multiple organizations was formed to launch attacks defended by the blue team consisting of CI operators and regulators. An 8-h slot was available to the blue team for responding to the attacks launched.
3. CISS2021-OL Attacks
- A4: Drain water from the UF process: In this attack, the attacker intended to manipulate the status of the actuators in stage 3 to drain water during the ultrafiltration process. This attack was executed in two steps. First, PLC3 was set to manual mode wherein the operator could directly control the actuator status. In the second step, the measurement from level sensor LIT301 was set to 1100 mm, and valves MV301 and MV302 valves were closed. Subsequently, the attackers opened valve MV303 and switched on the pumps P301 and P302.
- A7: Control the chemical dosing system: The attacker intended to degrade the water quality by disrupting the chemical dosing system. The attackers changed the commands sent, and measurements received, by PLC2. First, all pumps in stage 2 were started, and valves MV201 and MV301 opened. Subsequently, measurements from chemical sensors AIT201 (conductivity), AIT202 (pH), and AIT203 (ORP) received by the PLC2 were set to 69, 11, and 111, respectively.
- A17: Disrupt the RO process: The attacker intended to exploit the vulnerabilities in the SCADA workstation to redirect water from the RO process to the UF backwash tank. A cyber-criminal attacker model was designed to launch this attack. Using Metasploit [8], the attacker exploited the Windows-7 vulnerabilities to retrieve various login credentials. Using administrative credentials and RDP [9], the attacker gained access to the SCADA workstation to control the entire plant. Using SCADA’s user interface, the attacker manually closed all valves in stage 5, except MV503 and MV504, thereby redirecting water from the RO process to the UF backwash tank.
- A22: Manipulating the valves to disturb the raw water tank filling process: The objective of this attack was to stop the inflow of raw water into tank T101 for 2 min. To realize the objective, MV101 was set to manual mode and closed.
- A25: Damage the water pumps: The objective of this attack was to damage the water pumps that transfer water from the raw water tank to stage 2. The attackers alternately opened and closed pumps P101 and P102.
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A1 | SSSP | MV101 | Stop Raw Water Filling | Close MV101 |
| A2 | MSMP | All pumps in stage 2, FIT201, AIT202, and AIT203 | Disrupt the chemical dosing process |
|
| A3 | MSMP | MV301, MV303, and P602 | Stop the backwash process |
|
| A4 | MSMP | LIT301, MV301, MV301, MV303, P301, and P302 | Redirect water in T301 into UF drain |
|
| A5 | MSMP | MV501, MV504, MV502, MV503, and P601 | Redirect all water from RO process to RO reject tank |
|
| A6 | MSMP | All actuators in stage 5, P601, P602, and P603 | Redirect all water from RO process to RO reject tank |
|
| A7 | MSMP | All pumps in stage 2, FIT201, AIT202, and AIT203 | Disrupt the chemical dosing process |
|
| A8 | MSMP | LIT301, MV301, MV301, MV303, P301, and P302 | Redirect all water in T301 into UF drain |
|
| A9 | MSMP | All actuators in stage 5, P601, P602, and P603 | Redirect all water from RO process to RO reject tank |
|
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A10 | SSSP | MV101 | Stop raw water filling | Close MV101 indefinitely when LIT101 drop below 500 mm |
| A11 | MSMP | MV501, MV504, MV502, MV503, and P601 | Redirect all water from RO process to RO reject tank |
|
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A12 | SSSP | LIT101 | Disturb the water filling process in T101 | Set LIT101 to 900 |
| A13 | SSSP | P602 | Suspend the backwash process | Switch OFF the pump P602 |
| A14 | MSMP | P101 and MV201 | Degrade the water quality | Switch ON P101 and open MV201 |
| A15 | MSMP | MV201, MV301, MV302, and MV304 | Redirect all water in T301 into the UF drain |
|
| A16 | SSMP | All valves in stage 5 | Redirect all water from the RO process to tank T602 and empty tank T601 |
|
| A17 | NA | PLC3 | Stop the UF process | Comment out the entire UF process in PLC3 code |
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A18 | SSSP | FIT101 | Disturb the water filling process in T101 | Set FIT101 to 0 |
| A19 | SSSP | P602 | Stop the backwash process | Switch OFF the pump P602 |
| A20 | ||||
| A21 | MSMP | MV301, MV502, MV503, and P602 | Suspend the backwash process |
|
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A22 | SSSP | MV201 | Disturb the water filling process in T101 | Close MV201 for 2 min |
| A23 | MSMP | All pumps in stage 2 and UV401 | Degrade water quality |
|
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A24 | MSMP | P203, P204, P403, and P404 | Degrade water quality |
|
| A25 | SSMP | P101 and P102 | Destroy the pumps | Continuously turn P101 and P102 ON and OFF |
| A26 | MSMP | All valves in stages 1, 2, and 3 | Redirect all water in T301 into the UF drain |
|
| ID | Type | Target(s) | Intention | Description |
|---|---|---|---|---|
| A27 | SSMP | MV301, MV302, MV303, P301, P302 and LIT301 | Redirect all water in T301 into UF drain |
|
4. Results
5. Discussion
5.1. Impact of CISS2021-OL on AICrit
| Differentiators * | AICrit in [2] | AICrit in CISS2021-OL |
|---|---|---|
| Type | Insider | Insider and external |
| Launchers | Authors | Hackers from outside |
| Entry | Network | Network and physical |
| Launch point | SCADA | Network and inside SWaT |
| Targets | SSSP | SSSP, SSMP, MSSP, and MSMP |
| Launched | 13 | 27 |
| Detected | 13 | 23 |
| False positives | 0 | 0 |
| Process impact | Minor | Major ** |
5.2. AICrit Vs. DAD
5.3. Suitability Assessment for Detectors to Large-Scale Plants
5.4. Lessons from the CISS2021-OL
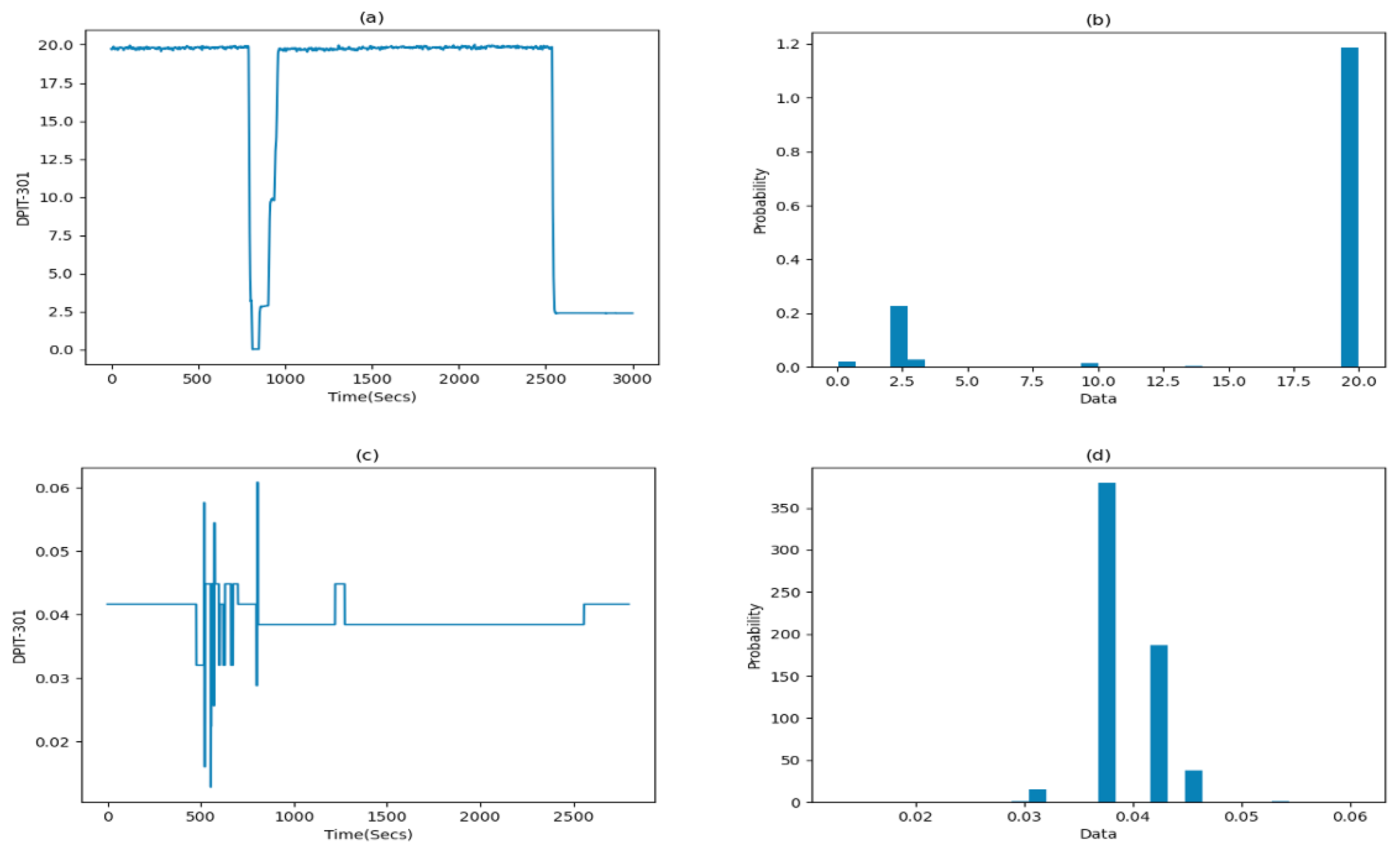
- Automated re-training/re-tuning AICrit: The representative models along with the intrinsic parameters of the AICrit discussed in [2] were built and fine-tuned using the operational data. Thus, any change in the data characteristics due to process upgrades or aging factors of components leads to an unacceptable number of false alarms. For example, prior to CISS2021-OL, UF membranes in stage 3 were replaced. This caused a large variation in the data generated by the differential indicator (DPIT-301) sensor (Figure 2). Thus, the retraining process was carried out in AICrit to achieve zero false positives. However, for large-scale plants, an automated mechanism is needed to initiate the retraining process in response to a significant change in the data characteristics, such as mean and standard deviation. Nevertheless, this introduces a new research question: how frequently should this process be conducted to consistently achieve zero false alarms, given the highly dynamic nature of large-scale plant operations?
- Detector placement: The placement of detectors is another important research area as it plays a crucial role in their performance. In CISS2021-OL, all detectors received the data from the clone historian, which is a copy of the primary historian. As discussed in Section 4, the adversaries were successful in disrupting the primary historian, and none of the detectors received process data. Thus, it is advised to deploy the detectors in a distributed manner so that compromising all data sources at the same time becomes harder for an attacker.
- Restoring SWaT operation: One of the major challenges faced during the CISS2021-OL was to bring back SWaT to its normal state after a successful attack. It is necessary to avoid the cascading effect of an attack. This involves several processes including (i) resetting all network communications, (ii) restoring the control codes of all PLCs, (iii) bringing back all sensors and actuators to auto mode in case they are set to manual mode by the adversaries, and (iv) reverting all devices such as the SCADA, HMI, and historian to their respective states that existed prior to the attack launch. Performing the above tasks manually is a time-consuming and error-prone task and thus needs automation.
6. Related Work
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AITX | Chemical sensor in stage X |
| CII | Critical Information Infrastructure |
| CI | Critical Infrastructure |
| CISS | Critical Infrastructure Security Showdown |
| DAD | Distributed Attack Detection |
| DPITX | Pressure sensor in stage X |
| FITX | Flow meter sensor in stage X |
| HMI | Human Machine Interface |
| ICS | Industrial Control Systems |
| LCL | Lower Control Limit |
| LITX | Water level sensor in stage X |
| MSMP | Multi Stage Multi Point attack |
| MVX | Motorized Valve stage X |
| PNN | Probabilistic Neural Networks |
| PLC | Programmable Logic Controller |
| PLCX | Programmable Logic Controller for stage X |
| PX | Pump in stage X |
| RIO | Remote Input Output |
| SCADA | Supervisory Control And Data Acquisition |
| SSMP | Single Stage Multi Point attack |
| SSSP | Single Stage Single Point attack |
| SWaT | Secure Water Treatment plant |
| TTP | Tactics, Techniques, and Procedures |
| TX | Water tank in stage X |
| UCL | Upper Control Limit |
| UF | Ultra-filtration |
| UV | Ultraviolet |
References
- Hassanzadeh, A.; Rasekh, A.; Galelli, S.; Aghashahi, M.; Taormina, R.; Ostfeld, A.; Banks, M.K. A review of cybersecurity incidents in the water sector. J. Environ. Eng. 2020, 146, 03120003. [Google Scholar] [CrossRef]
- Raman, G.M.R.; Mathur, A.P. AICrit: A unified framework for real-time anomaly detection in water treatment plants. J. Inf. Secur. Appl. 2022, 64, 103046. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. Distributed Attack Detection in a Water Treatment Plant: Method and Case Study. IEEE Trans. Dependable Secur. Comput. 2021, 18, 86–99. [Google Scholar] [CrossRef]
- Mathur, A.P.; Tippenhauer, N.O. SWaT: A water treatment testbed for research and training on ICS security. In Proceedings of the 2016 International Workshop on Cyber-physical Systems for Smart Water Networks (CySWater), Vienna, Austria, 11 April 2016; pp. 31–36. [Google Scholar]
- Raman, M.G.; Mathur, A.P. A Hybrid Physics-Based Data-Driven Framework for Anomaly Detection in Industrial Control Systems. IEEE Trans. Syst. Man, Cybern. Syst. 2021, 52, 6003–6014. [Google Scholar] [CrossRef]
- Raman, M.R.G.; Somu, N.; Mathur, A. A multilayer perceptron model for anomaly detection in water treatment plants. Int. J. Crit. Infrastruct. Prot. 2020, 31, 100393. [Google Scholar] [CrossRef]
- CISS2022-OL. Critical Infrastructure Security Showdown 2021—Online (CISS2021-OL). Technical Report. 2022. Available online: https://itrust.sutd.edu.sg/ciss/ciss-2021-ol/ (accessed on 22 May 2022).
- Metasploit. Available online: https://www.metasploit.com/ (accessed on 7 November 2023).
- Remote Desktop Protocol. Available online: https://en.wikipedia.org/wiki/Remote_Desktop_Protocol (accessed on 7 November 2023).
- Goh, J.; Adepu, S.; Junejo, K.N.; Mathur, A. A dataset to support research in the design of secure water treatment systems. In Proceedings of the International Conference on Critical Information Infrastructures Security, Paris, France, 10–12 October 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 88–99. [Google Scholar]
- iTrust SUTD. Dataset from iTrust Testbeds. 2022. Available online: https://itrust.sutd.edu.sg/itrust-labs_datasets/ (accessed on 22 May 2022).
- Adepu, S.; Mathur, A. Assessing the effectiveness of attack detection at a hackfest on industrial control systems. IEEE Trans. Sustain. Comput. 2018, 6, 231–244. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A.P. Detecting Multi-Point Attacks in a Water Treatment System Using Intermittent Control Actions; SG-CRC: Singapore, 2016; pp. 59–74. [Google Scholar]
- Adepu, S.; Mathur, A. Generalized attacker and attack models for cyber physical systems. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; Volume 1, pp. 283–292. [Google Scholar]
- Gauthama Raman, M.R.; Somu, N.; Mathur, A.P. Anomaly detection in critical infrastructure using probabilistic neural network. In Proceedings of the Applications and Techniques in Information Security; Shankar Sriram, V.S., Subramaniyaswamy, V., Sasikaladevi, N., Zhang, L., Batten, L., Li, G., Eds.; Springer: Singapore, 2019; pp. 129–141. [Google Scholar]
- Chakravarty, I.M.; Roy, J.; Laha, R.G. Handbook of Methods of Applied Statistics; McGraw-Hill: New York, NY, USA, 1967. [Google Scholar]
- Truong, H.T.; Ta, B.P.; Le, Q.A.; Nguyen, D.M.; Le, C.T.; Nguyen, H.X.; Do, H.T.; Nguyen, H.T.; Tran, K.P. Light-weight federated learning-based anomaly detection for time-series data in industrial control systems. Comput. Ind. 2022, 140, 103692. [Google Scholar] [CrossRef]
- Wang, Y.; Peng, H.; Wang, G.; Tang, X.; Wang, X.; Liu, C. Monitoring industrial control systems via spatio-temporal graph neural networks. Eng. Appl. Artif. Intell. 2023, 122, 106144. [Google Scholar] [CrossRef]
- Tang, X.; Zeng, S.; Yu, F.; Yu, W.; Sheng, Z.; Kang, Z. Self-supervised anomaly pattern detection for large scale industrial data. Neurocomputing 2023, 515, 1–12. [Google Scholar] [CrossRef]
- Hu, Y.; Li, H.; Luan, T.H.; Yang, A.; Sun, L.; Wang, Z.; Wang, R. Detecting stealthy attacks on industrial control systems using a permutation entropy-based method. Future Gener. Comput. Syst. 2020, 108, 1230–1240. [Google Scholar] [CrossRef]
- Hu, Y.; Li, H.; Yang, H.; Sun, Y.; Sun, L.; Wang, Z. Detecting stealthy attacks against industrial control systems based on residual skewness analysis. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 74. [Google Scholar] [CrossRef]
- Tang, C.; Xu, L.; Yang, B.; Tang, Y.; Zhao, D. GRU-Based Interpretable Multivariate Time Series Anomaly Detection in Industrial Control System. Comput. Secur. 2023, 127, 103094. [Google Scholar] [CrossRef]
- Alem, S.; Espes, D.; Nana, L.; Martin, E.; De Lamotte, F. A novel bi-anomaly-based intrusion detection system approach for industry 4.0. Future Gener. Comput. Syst. 2023, 145, 267–283. [Google Scholar] [CrossRef]
- Das, T.K.; Adepu, S.; Zhou, J. Anomaly detection in industrial control systems using logical analysis of data. Comput. Secur. 2020, 96, 101935. [Google Scholar] [CrossRef]
- Wu, W.; Song, C.; Zhao, J.; Xu, Z. Physics-informed gated recurrent graph attention unit network for anomaly detection in industrial cyber-physical systems. Inf. Sci. 2023, 629, 618–633. [Google Scholar] [CrossRef]
| Target | Description |
|---|---|
| Chemical dosing | Alter the amount of chemical used for dosing |
| Historian | Alter data; launch DoS attack |
| HMI/SCADA | Alter the sensor measurements and actuator states; launch a DoS attack |
| PLC | Alter the control code; launch DoS attack; alter the commands and measurements sent or received |
| Pump | Switch on or off the pumps |
| Pressure | Change the pressure values |
| RIO/Display | Control the RIO by disconnecting an analog Input/Output pin |
| Valve | Open or close the motorized valves |
| Water level | Spoof the water level in a tank |
| Team ID | ID | AICrit Response |
|---|---|---|
| RT1 | A1 | Not detected * |
| A2 | Abnormal change in FIT201 | |
| A3 | MV301 is closed but P602 is running | |
| A4 |
| |
| A5 | Both MV502 and MV503 are open | |
| A6 |
| |
| A7 |
| |
| A8 |
| |
| A9 |
| |
| RT2 | A10 | Not detected * |
| A11 | Both MV502 and MV503 are open | |
| RT3 | A12 | Abnormal change in LIT101 |
| A13 | MV301 is open but P602 is not running | |
| A14 | Not detected * | |
| A15 |
| |
| A16 | Both MV503 and MV504 are open | |
| A17 | P301 is running but FIT301 is below 1 m/hr | |
| RT6 | A18 | Not detected * |
| A19 | P602 is OFF but MV301 is open | |
| A20 | P602 is OFF but MV301 is open | |
| A21 | P602 is OFF but MV301 is close | |
| RT8 | A22 | LIT101 is below 500 mm but MV101 is closed |
| A23 |
| |
| RT9 | A24 |
|
| A25 |
| |
| A26 | MV101 is closed when LIT101 is increasing from 500 mm to 800 mm |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Raman, G.; Mathur, A. AICrit: A Design-Enhanced Anomaly Detector and Its Performance Assessment in a Water Treatment Plant. Appl. Sci. 2023, 13, 13124. https://doi.org/10.3390/app132413124
Raman G, Mathur A. AICrit: A Design-Enhanced Anomaly Detector and Its Performance Assessment in a Water Treatment Plant. Applied Sciences. 2023; 13(24):13124. https://doi.org/10.3390/app132413124
Chicago/Turabian StyleRaman, Gauthama, and Aditya Mathur. 2023. "AICrit: A Design-Enhanced Anomaly Detector and Its Performance Assessment in a Water Treatment Plant" Applied Sciences 13, no. 24: 13124. https://doi.org/10.3390/app132413124
APA StyleRaman, G., & Mathur, A. (2023). AICrit: A Design-Enhanced Anomaly Detector and Its Performance Assessment in a Water Treatment Plant. Applied Sciences, 13(24), 13124. https://doi.org/10.3390/app132413124





