Abstract
Wireless body area networks (WBANs) can be used to realize the real-time monitoring and transmission of health data concerning the human body based on wireless communication technology. With the transmission of these sensitive health data, security and privacy protection issues have become increasingly prominent. Fine-grained authentication allows physicians to run authentication checks of another specific entity according to their identifying attributes. Hence, it plays a key role in preserving the security and privacy of WBANs. In recent years, substantial research has been carried out on fine-grained authentication. However, these studies have put considerable effort into WBAN performances, resulting in weakened security. This paper proposes a fine-grained user authentication and key agreement protocol based on physical unclonable functions (PUFs) while maintaining robust security and performance. This will allow physicians to perform mutual authentication and obtain key agreements with authorized body area sensor nodes according to their identity parameters, such as occupation type and title. We then provide comprehensive security and heuristic analyses to demonstrate the security of the proposed protocol. Finally, the performance comparison shows that the proposed protocol is more robust in security, cost-effective communication, and computational overheads compared to three leading alternatives.
1. Introduction
Wireless body area networks (WBANs) [1] have been widely used in healthcare as a mature wireless communication technology. By deploying tiny body area sensor nodes and communication devices around the body, medical staff can monitor and transmit physiological parameters and health status data in real time, effectively enhancing people’s quality of life.
As shown in Figure 1, WBANs involve collaboration among medical staff, gateway nodes, and body area sensor nodes (BASNs). Medical staff or physicians are the users and controllers of the system. They obtain the patient’s physiological parameters by communicating with BASNs and performing the operation of diagnosis and treatment. As an intermediate device, the gateway node (GWN) bridges medical staff and BASNs and is responsible for data transmission, forwarding, and coordination. BASNs are equipped to collect patients’ biological data, including heart rate, blood pressure, body temperature, etc., while allowing medical staff to access these data in real time. In addition, BASNs can receive instructions from medical staff to perform corresponding operations as needed. Medical staff can rapidly assess the patient’s physical condition via this network topology model and perform corresponding medical operations.
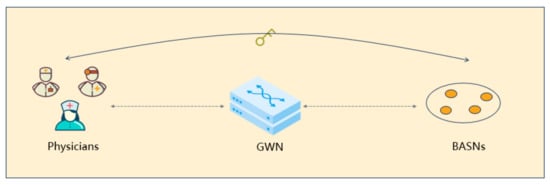
Figure 1.
WBANs network topology.
However, the openness of WBANs communication will undoubtedly lead to illegal network intrusion. If adequate security protection measures for health data involving personal privacy are not implemented, serious consequences will arise, including personal privacy disclosure, data tampering, and unauthorized access [2,3]. Meanwhile, given the different identity authentication requirements for users of different professional levels, it is important to perform personalized authentication according to corresponding levels and permissions to ensure that each user can only access the resources for which they have permission. Naturally, realizing efficient, safe, and credible data transmission and personalized authentication mechanisms in WBANs is essential.
Fine-grained authentication [4] is an authentication technology designed to provide detailed and precise identity verification in order to identify and authorize users in detail according to the users’ unique attributes and permissions. The advantage of this authentication technology is that it can provide a higher level of security and precise control and meet WBANs’ requirements for real-time accuracy and personalization in the authentication process.
This paper aims to provide an efficient and reliable fine-grained authentication solution to ensure the privacy and security of medical data. By carrying out this study, we expect to provide a useful reference and guidance for developing fine-grained authentication technology in order to promote the expansion and application of authentication in WBANs.
1.1. Related Work
In the health field, fine-grained user authentication is an important security measure that aims to ensure that only authorized individuals or entities can gain authentication from other specific entities, maintaining personal privacy and data security. In this section, we summarize existing fine-grained authentication schemes for healthcare systems.
Chatterjee et al. pioneered an attribute-based fine-grained access control scheme to secure communication in the client–server architecture [5]. This groundbreaking scheme utilizes smart cards and biometric authentication for verification purposes. Furthermore, it enables the establishment of session keys to encrypt subsequent communications. However, it is important to highlight that the solution’s communication overheads are relatively substantial, potentially impacting the overall user experience.
Wang et al. [6] introduced an access control with fog computing to achieve a more optimal balance between efficiency and security. This approach is well suited for a range of scenarios, including data storage, directory management, and file organization. However, Singh et al. in [7] reported that the scheme proposed by Wang et al. cannot achieve mutual authentication or resist device impersonation attacks.
Ogundoyin et al. recognized the sensitivity of medical data and consequently introduced a lightweight privacy-preserving authentication and fine-grained access control solution: PAASH [8]. They presented an elliptic curve cryptography (ECC)-based certificateless signature scheme. Simultaneously, they employed attribute-based encryption and signature technology to achieve precise access control. Nevertheless, Benil et al. [9] highlighted that the PAASH fails to counter impersonation, forgery, and modification attacks.
There are also works for securing communication in WBANs. The authors of Ali et al. in [10] offered a robust authentication and access control solution by using expensive bilinear pairing. However, the password of the user can be effectively guessed by the adversary if there is no use of “modulus” operations.
Similarly, one research study [11] designed an E-health-oriented proposal that is relevant to authentication, key agreement, and access control. Furthermore, this study was the first to propose a method of transferring the ownership of patient information from the former physician to the new physician. Before the application of this charming proposal, forward secrecy and three-factor security should be applied.
For the scenario of wireless medical sensor networks, Yao et al. [12] proposed multiple solutions for user–server authentication, patient–server authentication, and user–patient authentication scenarios. However, the password verifier table is stored in the registration center and can face password-guessing attacks, which lead to the exposure of the user’s password.
1.2. Motivations and Contribution
Given the increasing adoption of WBANs in security-critical scenarios, the need to provide a fine-grained three-factor authentication solution increases. However, according to our performance analysis in Section 5, most existing fine-grained user authentication protocols commonly cannot balance security and performance:
- Security: In terms of security, similar approaches exhibit the same security problems to greater and lesser degrees [10,11,12]: for example, the lack of mutual authentication, the inevitable smart card loss attacks, or the failure to provide forward secrecy.
- Performance: From the view of storage, communication, and computation costs, existing solutions still require more resources in order to ensure the functionality of fine-grained authentication. However, WBANs are more resource-constrained than conventional networks, and a tiny body area sensor device cannot run extensive operations according to the published protocols.
Thereupon, we consider a robust and effective fine-grained user authentication scheme that can maintain a good balance between security and performance. The specific contributions of this study are as follows:
- Fine-grained authentication protocol: We design a fine-grained authentication protocol for WBANs. This proposed scheme slows for mutual authentication among users with varying privileges and corresponding authorized BASNs while also facilitating the negotiation of a session key for encrypting subsequent data transmission.
- Complete security analysis: The proposed protocol’s security is rigorously examined via heuristic and provable security analyses, which show that the proposed protocol attains multiple desired security properties and exhibits resilience against all known attacks.
- Performance evaluation: Via a comparative assessment of storage, communication, and computational overheads for the proposed protocol and also other established methods, we show the advantages of the proposed protocol with respect to performance.
2. Preliminaries
In this section, we introduce preliminaries, which include the system model, adversary model, physically unclonable function, fuzzy extractor, and RSA cryptosystem, in order to ease the reader’s understanding of this study.
2.1. System Model
As shown in Figure 2, based on the standard single-gateway model [13], our system model consists of three entities: physicians at different occupational levels (A, B, and C), a gateway node (GWN), and a series of body area sensor nodes (BASNs).
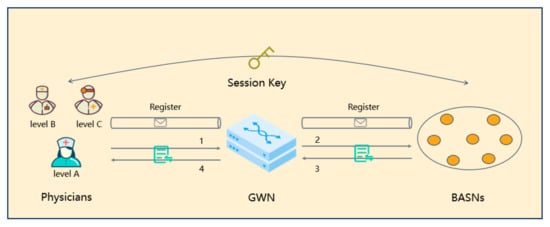
Figure 2.
System model of the proposed scheme.
In the registration phase, users and BASNs register at the gateway, which corresponds to the registration process in Figure 2. At the same time, the gateway sets the user’s fine-grained authentication parameters according to the user’s occupation level and type in order to prepare for subsequent fine-grained authentication between users and BASNs. At the end of registration, the physicians (BASNs) retain real-time fine-grained authentication parameters (resp. secret value), and GWN stores the identity of BASNs.
In the login and authentication phase, if the user wants to access the data of some body area sensor nodes, they first need to initiate an authentication request in the gateway, which corresponds to process 1 in Figure 2. Next, the gateway authenticates the user. If authentication is successful, the gateway node sends the user’s request to the BASN, which corresponds to process 2 in Figure 2. After the BASN receives the request, it first verifies the identity of the gateway, and if the authentication passes, it sends the authentication-related parameters to the gateway, which corresponds to process 3. Upon the gateway’s receipt of data from BASN, it first authenticates the BASN and then updates relevant fine-grained authentication parameters according to the user’s occupation; then, it sends the relevant authentication data to the user, which corresponds to process 4. Finally, the user negotiates a consistent session key with BASN via authentication data from the gateway node. The purpose of this phase is to ensure that only legitimate physicians can access the data resources of BASNs.
2.2. Adversary Model
The Dolev–Yao (DY) model, which portrays the capabilities of the adversary, has been widely used in formal and heuristic analyses with respect to the security of authentication protocols [14]. Currently, the latest research [15] has taken this a step further by consolidating adversary capabilities in order to comprehensively evaluate the authentication protocol. In this refined threat model, an adversary 𝒜 possesses six capacities (A-), which are as follows:
- (A-1) can intercept, modify, insert, and delete any messages that are being transmitted through the open channel.
- (A-2) can systematically enumerate all elements within the Cartesian product of the identity space and password space, which is denoted as .
- (A-3) is capable of obtaining previously established session keys between the physician and BASN.
- (A-4) possesses the capability to acquire the secret key of the GWN in situations where the system eventually experiences failure.
- (A-5) can breach some specific BASNs, extracting sensitive data stored within them. Furthermore, can manipulate the compromised BASN so that it can participate in subsequent communications involving the GWN, other users, and body area sensor nodes.
- (A-6) could potentially register as either a legitimate user or even the role of the GWN administrator only if the security of the physician’s password is evaluated during the registration phase.Carrying out formal and heuristic analyses in Section 4, based on the DY adversary’s capability, we can quantify the advantage of the adversary relative to their ability to bypass semantic security, and via heuristic analyses, we prove that the protocol can resist all kinds of attacks issued by the DY adversary.
2.3. Physical Unclonable Function
The physical unclonable function (PUF) [16] generates an output based on physical characteristics, such as delay, resistance, capacitance, or reflection properties. Since the output of the PUF is based on slight randomness and unevenness in the manufacturing process, it is difficult for an adversary to generate the same response sequence as the original PUF via copying or simulation. Therefore, the PUF has a high degree of security and protection in security systems, and it is widely used to protect sensitive information in cryptographic authentication protocols.
During the registration phase of the authentication protocol, the user or device generates a unique identifier or a unique key via PUF and stores it securely. In the login phase, PUF generates a response: , . Response is compared with a previously registered identifier or key. If matches the key, the login can be seen as a success, and the user is allowed to send the authentication request to the GWN. This PUF-based user-authentication mechanism takes advantage of the physical properties and unclonability of the PUF in order to ensure a secure, unique, and difficult-to-forge identity verification process. In the proposed protocol, we use a physical unclonable function , which configures the embedded trigger sum for the user, where the sum refers to the number of times that the user is allowed to try to use in the event that the user forgets the secret key.
2.4. Fuzzy Extractor
The fuzzy extractor [17] is an important concept in cryptography, and it is especially suitable for correcting data inconsistencies caused by noise or changes. In the field of cryptographic authentication, fuzzy extractors are used to deal with the variability and noise that may be present when physical characteristics are collected to ensure authentication.
The fuzzy extractor works by converting irregular physical characteristics into a stable and consistent key or bit string. This stable key can be used for the following authentication. Importantly, the fuzzy extractor allows for the extraction of fixed and verifiable information without compromising the accuracy of physical characteristic identification in order to ensure stability and consistency during the login phase of the authentication protocol.
In this paper, the fuzzy extractor is utilized to mitigate the influence of noise during PUF execution. The system executes the PUF to obtain the , response during the registration process; then, it adds to the fuzzy extractor and stores the auxiliary string . During the login phase, the system can execute the PUF to obtain the current response and employ the stored in memory to determine . If and are not equal, this indicates that an unauthorized user attempted to initiate a login request, and the system dismisses this illegal login request.
2.5. RSA Cryptosystem
In the realm of public key cryptography, the RSA cryptosystem [18], founded on the intricacies of the large number factorization problem, is elucidated below. To aid comprehension, an example involving a message sender denoted as who transmits a message to a message receiver is presented.
Initiation: The message receiver selects two substantial prime numbers . Subsequently, computes and Euler’s totient function of , which is denoted as . Next, chooses an integer that satisfies . The receiver then computes . The outcome is that publicizes the public key while keeping the private key confidential.
Encryption: The message sender takes the message and performs an encryption operation using ’s public key . Consequently, transmits the resultant cipher to .
Decryption: Upon the receipt of the cipher , message receiver employs private key to decipher the message. This is accomplished via the computation .
In Section 3 (i.e., step L2 in the user login phase and step V10 in the authentication and key agreement phase), we provide the detailed method of using RSA to securely transmit secret values.
3. The Proposed Protocol
Aiming at the solving common security and storage problems of authentication protocols in WBANs, we propose a fine-grained user authentication method based on the physical unclonable function (PUF). Specifically, it includes seven phases, namely system initialization, body area sensor node and user registration, user login, authentication and key agreement, password update, and dynamic node addition. To promote the understanding of researchers, some notations used in the proposed protocol are explained in Table 1.

Table 1.
Notations with related descriptions in the proposed protocol.
3.1. System Initialization Phase
In the initialization phase, given a security parameter , the gateway node selects a long-term key pair and generates a unique identity GID. Then, saves and publicizes identity GID.
3.2. Registration Phase
The registration phase comprises the following: In the terminal of the GWN, the user and BASN need to complete the registration of identity information and receive authentication parameters in order to be ready for future identity authentication and key agreement. Specifically, the registration phase includes the registration of the BASN and users.
3.2.1. Registration Phase of BASN
The registration of includes R11~R13:
R11: ; the transmits identity to gateway node via a secure channel. Then, gateway collects and stores it in identity set .
R12: ; GWN calculates secret value for and also returns secret value to via a secure channel.
R13: stores secretly.
Note that the secure channel can be understood here as comprising the user and node devices that are within the same physical space (such as a computer room managed by a hospital administrator); then, the registration and sharing of secret values can be completed in a face-to-face manner.
3.2.2. Registration Phase for User
The registration of user includes R21~R23:
- R21: ; user transmits the calculated to via a secure channel.
Specifically, inputs the of their own choice to the personal digital assistant (PDA). The PDA selects a random number , where is a system security parameter. Then, PDA calculates the following: hash value ; is a large prime number.
- R22: {Registration Package (RP)}. The sends a registration package to .
After receives information from user , it first records the registration timestamp , selects a pseudo-random identity , and computes . Secondly, determines the body area sensor node identity set , which is authorized for the authentication of , and binds the authorization check polynomial; the authorized authentication time threshold; and the authorization, authentication, and verification value for user , where is a subset of , the check polynomial is , the time threshold is , and the authentication verification value is . Furthermore, uses symmetrical algorithms (e.g., the well-known AES [19]) to generate symmetric ciphertext and configures the physically unclonable function with embedded trigger , where , and refers to the number of times the user is allowed to try to use . Here, we set the maximum value to 3 and the initial value to 0. Finally, sends the registration package (RP) to , where RP stores parameters .
- R23: After receives RP, updates and calculates as follows: At first, inputs to PDA, and PDA computes . PDA then uses to compute the following: , . After that, PDA updates secret value . Finally, PDA stores a series of values: .
During registration, the gateway node no longer issues smart cards to users, thereby avoiding offline password-guessing attacks, which result from smart card loss attacks. At the same time, the periodicity of modulo calculations makes it impossible for the adversary to guess passwords effectively in order to protect password security. Meanwhile, the gateway needs to encrypt these fine-grained authentication parameters to prevent users from tampering with them. Additionally, to ease the understanding of readers, Figure 3 summarizes the registration operation of the user and BASN.
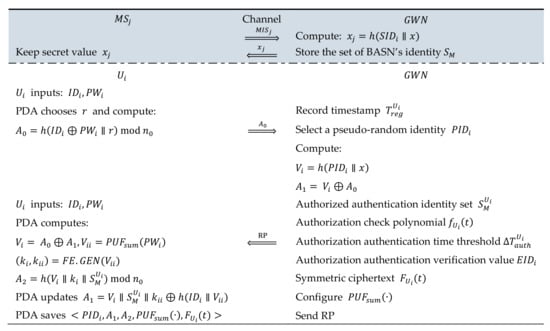
Figure 3.
Registration of the user and BASN.
3.3. Login Phase
In the login phase, the user needs to be verified via the PDA. Upon the PDA’s authentication of the user identity’s legitimacy, the user can log in via the PDA successfully; then, the PDA generates an authentication request for some specific BASN. Furthermore, the PDA transmits this authentication request to the GWN. The login phase includes three steps from L1 to L3:
L1: Firstly, enters the identity and password . Secondly, PDA uses the physically unclonable function to verify the user’s identity. Specifically, PDA computes and . Thirdly, PDA compares whether is equal to ; if =, the user’s identity can be verified. Then, it proceeds to step L2 to continue the execution; otherwise, will add 1 to the value of automatically when the user tries to enter another again for the login. If the value exceeds the preset maximum value, the session will be terminated, and the user’s account will be frozen until re-registers.
L2: PDA runs a 1024-bit RSA cryptosystem to generate public key and private key for , and PDA keeps secret. Then, the PDA selects a random number ; chooses the identity of , which the user wants to acquire; extracts the timestamp ; and calculates the following parameters: and , where is the public key of .
L3: . PDA sends the requested information to in a public channel.
3.4. Authentication and Key Agreement Phase
In the authentication and key agreement phase, three entities (i.e., user, GWN, and BASN) first verify the identity of the communicating party when communicating with each other. At the same time, and can negotiate a consistent session key. This phase includes ten steps from V1 to V10:
V1: Upon ’s receipt of the requested information by user , it first extracts the current timestamp and checks whether the time gap between and is less than time threshold . If not, directly discards the request information; if so, decrypts and obtains .
Then, verifies whether is authorized to obtain authentication with , for which its identity is . calculates and and checks whether the two values are equal. If so, further judges whether belongs to case (a), case (b), or case (c):
- (a)
- (b)
- (c)
- .
If it belongs to case (a), this means that does not have authentication authority with respect to ; if it belongs to case (b), this means that the authentication authority of exceeds the time threshold for to be authorized; if it belongs to case (c), this means that the body area sensor node that wants to access can be authorized for authentication within a valid period of time. further computes and . Finally, compares and . If they are equal, i.e., , this means that can be validated, and the operation proceeds to step V2; otherwise, terminates this session.
V2: selects random number , extracts the current timestamp , and computes the following: , and .
V3: . sends to the body area sensor node .
V4: firstly extracts timestamp and checks whether the time gap between and is less than time threshold . If so, recovers . At the same time, computes and compares the value of and . If the two values are equal, identity is verified, and proceeds to step V5; otherwise, terminates this session.
V5: selects random number , extracts timestamp , and computes via the RSA algorithm: , , where represent the intermediate parameters, and represents the session key of and .
V6: . sends information to .
V7: firstly checks the validity of the timestamp. Next, uses the secret value to compute : . Then, checks the consistency of and . If the two values are equal, executes step V8; otherwise, it terminates this communication.
V8: computes and updates the parameters as follows:
updates the new pseudo-random identity for ;
updates ;
updates the authorization verification value , the authorized authentication time threshold , and the authorized authentication body area sensor node identity set . Specifically, if the authentication authority of needs to be revoked, then computes and sets ; otherwise, computes , updates , and further updates the authorized authentication identity set according to situations (d), (e), (f), and (g):
- (d)
- If there is no change in the identity set of the body area sensor node, then .
- (e)
- If there is a newly added identity set with respect to the body area sensor node, then .
- (f)
- If identity set is removed from the body area sensor node, then .
- (g)
- If cases (e) and (f) occur simultaneously, then .
updates the value of , where .
updates .
computes and further computes .
V9: ; sends related information to .
V10: uses to recover , i.e., . Then, uses private key and then computes , and . If equals , accepts session key and completes the authentication; otherwise, rejects the session key. After accepting the session key, the PDA computes parameters . Finally, the PDA updates the value from to . Additionally, Figure 4 summarizes the login, authentication, and key agreement operations of the user and BASN.
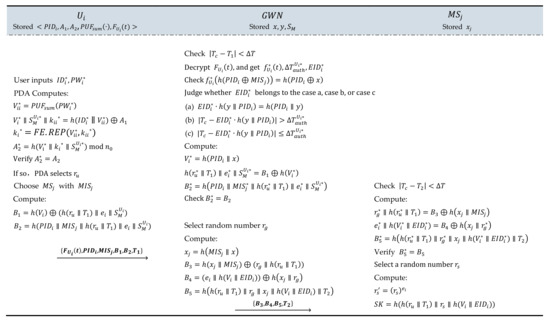
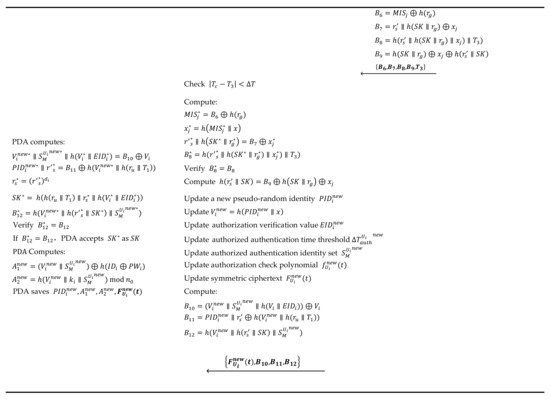
Figure 4.
Login, authentication, and key agreement.
3.5. Password Update Phase
can update the password by following steps U1~U2 below without interacting with :
U1: At first, enters . PDA then uses to verify the identity of . Specifically, PDA computes . If is equal to , PDA continues to run step U2; otherwise, this session is terminated.
U2: Via the new password , which is chosen by , the PDA computes the new parameters: , , and . Finally, the PDA updates the value of to .
3.6. Dynamic Increase in Sensor Nodes
In order to adapt or meet the continuous medical needs of WBANs, the addition of new body area sensor nodes is undoubtedly necessary. When a new body area sensor node joins WBANs, only needs to initiate a registration request as in Section 3.2.1. After is successfully registered, broadcasts identity and stores in identity set .
4. Security Analysis of the Proposed Protocol
In this section, we carry out the security analysis of the protocol, which includes formal security and heuristic security analyses. Given the DY adversary’s capabilities, via formal security analysis, we can demonstrate that the adversary does not have a significant and strong advantage with respect to breaking the semantic security of the session key in our protocol. Then, via heuristic analysis, one can observe that the proposed protocol not only fulfills the desired attributes but also demonstrates resilience against a multitude of known attacks [20,21].
4.1. Formal Security Proof
Formal security analysis is an effective method for demonstrating the semantic security of the proposed protocol. It employs formal mathematical techniques to prove whether the proposed protocol satisfies the desired security properties within a specific security model. In this type of analysis, the initial step involves defining a formal model that describes participants, furthering the DY adversary’s capabilities. Subsequently, security properties need to be precisely defined. Lastly, the desired security properties are proven to be satisfied within the defined security model via mathematical, logical deduction.
4.1.1. Basis for Security Proof
In this study, three primary participants within our protocol are identified as follows: a physician denoted as , a gateway node referred to as , and a body area sensor node labeled as . Before initiating the simulation, the simulator selects the RSA cryptosystem, employing two large prime numbers and with equal bit lengths, i.e., . Subsequently, selects a set of personal information . Simultaneously, generates a long-term key pair , and owns an identity–secret key pair .
During the proof process, three entities will instantiate , and , with their respective instances denoted as , and . For the sake of simplicity, these instances can collectively be marked as when distinguishing them is unnecessary. Moreover, each instance is treated as an oracle. This implies that if a message input is valid, invalid, or null, the oracle’s state accordingly is an acceptance, rejection, or “”, respectively, where “” indicates that there is no response to the input.
Subsequently, we introduce certain terms that are pertinent to this proof:
Accepted State: An instance reaches an accepted state upon receiving the final expected protocol message. Notably, the ordered concatenation of all exchanged messages (both sent and then received) shapes the session identifier for the current session of .
Partnering: Instances and are considered partnered if they simultaneously meet the following criteria: (a) both are in an accepted state, (b) mutual authentication has occurred, and they share an identical session identifier.
Adversary: In this context, adversary can interact solely with honest entities by initiating query oracles and controlling the simulator. aims to compromise the security of authentication messages and re-construct the session key within protocol . The queries that can launch include the following:
- -
- Execute (): This query allows to simulate the entire authentication process and access exchanged messages between , and .
- -
- Send (): can send message and conduct an active attack on instance . If is valid and has received , the simulator responds to with the computation of ; otherwise, this query is terminated.
- -
- Reveal (): This query results in revealing the session key calculated by and its partner to adversary .
- -
- Corrupt (): In this query, can obtain authentication factors associated with based on value . Specifically, the oracle exposes the password to when and exposes the data stored in the registration package to when .
- -
- Corrupt (): In this query, can gain access to the long-term key possessed by .
- -
- Corrupt (): This query enables to obtain the secret value of .
Freshness: An instance of , , or is deemed fresh if the session key between and remains undisclosed to via the aforementioned reveal query.
Test (): This query assesses the semantic security of session key . In this query, can make only one inquiry. Considering protocol , instance can only either be or . Formally, if test has been queried before, the query outputs “” (null). Otherwise, the oracle flips an unbiased coin . If , test () provides the real session key to ; if , test () yields a random string with the same length as the real session key and sends it to .
Semantic Security: Given a protocol , probabilistic polynomial time (PPT) adversary requests new instances for a series of queries, including execute query, send query, corrupt query, and test query. endeavors to compromise protocol by guessing the value of in the test query and returns a guessed value . Let denote ’s successful guess of as , i.e., . Then, the advantage of successfully breaking the semantic security of protocol concerning the session key is defined as .
4.1.2. Security Proof
In this section, we set up a total of eight games to simulate the semantic security of the adversary’s ability to break the session key from different perspectives. Among these simulated games, the only difference is that the latter game provides more information to the adversary; the former and latter games are indistinguishable to the adversary. In each game, the simulator responds to queries from the adversary, who, in turn, obtains different information to increase their advantage of interfering with semantic security. Finally, based on the advantage of the adversary in each game, the total advantage of the adversary in interfering with the semantic security of the session key can be quantified.
Theorem 1.
Let be the proposed protocol, be the space of password, and be the system’s security parameter. Then, PPT adversary breaks with a negligible advantage by making a series of queries, including execute query, send query, hash query, and PUF query, where encounters the following.
Proof.
We now demonstrate and prove that the adversary’s advantage in breaking the semantic security of the session key is factually negligible due to the involvement of with . is set to be the event during which guesses in the test query of .
: This game simulates a real attack by a random oracle. Bit is then randomly chosen at the beginning of this game. Thus, we obtain the following:
: This game shapes hash list . For example, initiates a hash query and hash oracle takes to retrieve . If there is a retrieved hash value, , in , responds to the hash value. Otherwise, a random string will be sent to ; meanwhile, is stored in .
Using the known list in this game, performs a test query to distinguish the real session key and the random string. Factually, given , only secret values including ’s , and ’s essentially comprise . Hence, has no way of computing and cannot distinguish whether or other than making guesses.
Thus, compared to , ’s chance of winning this game does not empower ’s advantage.
: In this game, the active attack is modeled based on . can execute the send query and hash query to try to persuade a participant to accept a forged message. Thus, ’s advantage may be enhanced by finding the collision that generates a valid message compared with . That is, if the following collisions occur, this game is aborted:
- (i)
- A collision can be found in the hash values or PUF’s outputs, and the probability is or , where and denote the length of output by the hash function and PUF, respectively.
- (ii)
- Another collision that can be found is relative to the choice of random numbers , where the probability is .
Thus, we have the following:
: In this game, desires to guess without asking the hash query.
We can obtain:
: In this game, tries to guess without asking the hash query. Similarly, we can obtain the following:
: In this game, via the corrupt query, computes . There are two cases we need to consider:
- Case 1, i.e., corrupt : with respect to “fuzzy keywords + honeywords”, the probability that guesses a physician’s password is no greater than [22,23,24];
- Case 2, i.e., corrupt : the probability that guesses the values of is less than .
Therefore, we obtain the following:
: In this game, initiates a corrupt () query to compromise body area sensor node , and then further obtains secret values and . However, cannot obtain from since there is no PPT solution for solving the difficulty of the large number factorization problem [18].
Therefore, we can yield the following:
: This game simulates the attack where tries to calculate the session key, which means that no longer queries the oracle’s execute query, send query, and corrupt query. However, similarly to the analysis in , cannot compute from . In other words, ’s advantage in this game is equal to the advantage in . Thus, we can have the following:
Ultimately, we can observe that has no un-negligible advantage greater than ; thus, .
From Equation (1) to Equation (8) and with respect to the triangular inequality, we yield the following:
In sum, we can conclude that adversary does not have a significant and strong advantage, , in breaking the semantic security of the session key in our protocol. □
4.2. Heuristic Analysis
The heuristic method [25,26] eschews the use of intricate formulas, making it remarkably straightforward. This approach proves to be both highly efficient and uncomplicated, enabling a succinct yet all-encompassing security analysis of the scheme. In this section, via the heuristic analysis, one can observe that our solution not only fulfills the desired attributes but also demonstrates resilience against a multitude of known attacks.
4.2.1. Mutual Authentication
The proposed scheme can attain mutual authentication since and authenticate each other bidirectionally by checking if and , respectively. Similarly, with checking whether and verifying that , and can authenticate each other successfully.
4.2.2. Session Key Agreement
The session key agreement means that no one can solely pre-compute the session key without interacting with another entity. Factually, in the proposed protocol, contains an indispensable part from (secret parameter ) and (secret parameter ); thus, our scheme meets this well-defined attribute.
4.2.3. Forward Secrecy
Forward secrecy holds if the past built session keys are still secure on the condition that the long-term secret holds; i.e., ’s is corrupted. As a matter of fact, suppose the following: the adversary knows , they can obtain from the open channel and then compute , and they can obtain . However, an important consideration is that they cannot retrieve due to the difficulty of large number factorization in RSA [18]. That is, we can retain forward secrecy.
4.2.4. User Anonymity
User anonymity mainly comprises user identity protection, which prevents the adversary from obtaining the user’s identity, and user un-traceability, which guarantees that the adversary cannot decide upon who the communicating user is, nor does it allow them to distinguish whether two instances of data interaction are from the same communicating user.
For the first form of identity protection, on the one hand, during the registration phase, only submits to ; thus, it cannot directly extract identity information for the adversary even if could be destroyed. On the other hand, cannot be used to deduce the identity of the user during the authentication phase; thus, the adversary cannot capture the user’s identity, . As for the un-traceability of another user, the randomness of breaks the statistical property, which effectively confuses the adversary in determining whether two sessions are from the same communicating user.
4.2.5. Password-Guessing Attack
In this attack, the adversary tries to guess the password via the physical unclonable function (PUF), in which the PUF generates an inherently unclonable output for a given input. That is, the adversary prepares a guessed password ; then, the PDA computes using the same operations as in the login phase. Even if may be equal to , “fuzzy keywords + honey words”, by inducing the modulus operation, cannot help the adversary in determining whether the guessed password is correct.
4.2.6. Body Area Sensor Node Impersonation Attack
This attack [25] gives the adversary, i.e., the legitimate inside user, an opportunity: The user could obtain the body area sensor node’s secret key and create a faulty session key for the new physician. However, this attack makes no sense in our scheme. Factually, this adversary cannot extract this secret from because they do not possess the secret value of . Therefore, the proposed protocol resists sensor node impersonation attacks.
4.2.7. De-Synchronization Attack
Generally, after the session key is established, have no need to update any parameters; thus, the de-synchronization attack is impossible. In our proposed protocol, needs to update the parameters for the next authentication. Then, checks whether is equal to . Luckily, the checking operation can detect this attack in a timely manner. That is, the occasion in which holds implies that this attack interferes with the normal update of parameters, and the user only asks to run the update operation of again.
4.2.8. Replay Attack
The replay attack comprises the following: the adversary usually sends old messages to pass the verification of entities and re-computes the session key. However, in each session, , , and choose random numbers , , and , respectively, to ensure the freshness and independence of exchanged messages. As a result, the adversary can neither calculate the correct session key based on the replayed message nor can they pass the authentication of .
4.2.9. Privileged Insider Attack
In order to prevent the adversary (even corrupted ) from using privileged insider attacks and extracting the identity information of legitimate users during the registration phase, only submits , which encapsulates relative to , rather than bare string , and the adversary cannot obtain the real .
4.2.10. Node Capture Attack
Even if it is possible to assume that the adversary has the node’s secret value and retrieve and , this adversary cannot re-calculate session key unless they can effectively solve the difficulty of large number factorization in RSA [18] in obtaining another important value .
4.2.11. Denial of Service (DoS) Attack
In the proposed scheme, even if the adversary may render BASN unavailable by replaying old messages repeatedly, BASN firstly verifies whether the time gap meets or not. If it does, BASN directly terminates this session. Furthermore, even if the adversary updates timestamp to obtain , BASN also ignores this session due to the following verification failure of value , where can only be derived by the original timestamp. Thus, the denial-of-service (DoS) attack cannot succeed. Similarly, the terminal of does not suffer from this DoS attack.
4.2.12. Man-in-the-Middle (MITM) Attack
In our scheme, we suppose that the adversary [26] listens and blocks the user’s login message and response messages from . To issue a man-in-the-middle (MITM) attack, the adversary must create a flow of new login and response messages or replay old messages. As discussed above, the proposed protocol can resist impersonation and replay attacks. That is, the adversary cannot be authenticated by both the user and the gateway. Hence, the proposed scheme can be used against MITM attacks.
5. Summary Comparisons: Functionality and Performance
In this section, we begin by introducing the criteria designed for the assessment of authentication protocols in Section 5.1. Subsequently, in Section 5.2, we conduct a comparative analysis between our proposed protocol and alternative approaches to determine their alignment with the security prerequisites outlined in Section 5.1. Lastly, in Section 5.3, we provide a comparison with regard to storage, communication overheads, and computational overheads.
5.1. Security Evaluation Criteria
Over the years, Wang et al. [15,22,27] conducted in-depth studies on the security criteria of authentication protocols. Based on their studies, we summarize 10 criteria for fine-grained authentication protocols, as shown in Table 2. Additionally, states that password-guessing, privileged insider, de-synchronization, replay, stolen verifier, node impersonation, node capture, and DoS attacks cannot be effectively initiated by the adversary.

Table 2.
Criteria for evaluating authentication schemes.
5.2. Functionality Comparison
The comparative outcomes of our proposed protocol with respect to other protocols in [10,11,12] are displayed in Table 3. From our analyses, we can observe that the protocol presented in [10] is vulnerable to the verifier loss attack, resulting in an inability to achieve .

Table 3.
Functionality comparison among relevant AKA protocols.
The protocol shown in [11] falls short of achieving , , and . Specifically, neither the physician nor the sensor node can authenticate the gateway, aligning with . Also, the protocol of [11] is susceptible to user impersonation attacks, which is in line with . Additionally, it falters in attaining forward security, corresponding to .
For the protocol in [12], the server or GWN in [12] retains many more password-related parameters, which threatens the security of passwords (). As for , mutual authentication () cannot be met because the messages do not guarantee that BASN can realize mutual authentication with respect to the GWN. Additionally, the users in [12] directly submit their bare identities to the GWN or the registration center in order to complete the registration phase, and once the gateway is corrupted by the adversary, the anonymity () of the user will not be respected.
Only our proposal fulfills all the stipulated security prerequisites. It is evident that our proposal exhibits resistance against known attacks, enabling the attainment of optimal security and usability objectives. Notably, since no smart card has been used in our proposal, our proposal can meet criterium naturally.
5.3. Storage, Communication, and Computation Cost Comparisons
In order to provide a comprehensive evaluation of storage and communication overheads, Table 4 provides reasonable reference lengths for all components.

Table 4.
The lengths of all terms involved in storage and communication costs.
Simultaneously, to ascertain computational costs during the login and verification phases, we executed the RSA algorithm with a key length of 1024 bits on a 12th-generation intel core i7–12700 H with 16 G memory; we report that the elapsed time with respect to 1024-bit RSA modular exponentiation is 0.63 ms. For other cryptographic functions, based on the results from [10,11,12,28,29], the time required for the SHA-1 hash function is 0.00069 ms [28], the PUF function requires 0.43 ms [29], and symmetric encryption/decryption and the bio-hash function demand 0.1303 ms and 0.01 ms, respectively [11]. ECC point multiplication requires 0.0018 ms [12], and the fuzzy extractor function and bilinear pairing require 2.226 ms and 5.811 ms, respectively [10].
Then, we provide Table 5, which presents a comparative analysis covering the storage, communication, and computational overheads consumed in all compared schemes.

Table 5.
Storage, communication, and computation costs in the login and authentication phase.
In our protocol, our total storage overhead is the smallest at 1376 bits, and the storage overhead of Ali et al. [10] is the largest at 3952 bits. The storage overhead of each scheme increases in the order of 1376 bits, 1507 bits, 1888 bits, and 3952 bits. Moreover, our proposal has obvious advantages in terms of storage overheads. As for communication overheads, the user, GWN, and BASN costs are 1920 bits, 3616 bits, and 1664 bits, respectively, with corresponding computation times of 3.28 ms, 0.20 ms, and 0.64 ms. It is evident that our solution boasts the lowest cumulative storage overhead compared to [10,11,12]. Simultaneously, the consumed times of the user and BASN in our scheme are 3.28 ms and 0.64 ms, respectively, which can reduce the user’s and BASN’s computation cost by 68.1% and 83.8% compared to the scheme reported in [10].
In summary, our proposal outperforms others in terms of optimal security, superior storage and communication efficiency, and competitively efficient computational overheads. Other schemes, to varying degrees, require improvements in terms of security, communication overheads, or computational overheads.
6. Conclusions
With respect to high-security-requirement WBAN scenarios, we first introduced the authentication model of WBANs. Then, based on the PUFs, we proposed a fine-grained user authentication and key agreement protocol for WBANs. The proposed protocol does not need to allocate smart cards for users, and it can provide fine-grained user authentication and authorization. In the final security and performance analysis, the proposed protocol demonstrates advantages in terms of overall performance, and it is expected to significantly improve the security, efficiency, and availability of user authentication in WBANs. Regarding future studies, we will concentrate on blockchain-based authentication schemes in order to avoid single-point failure in a centralized GWN.
Author Contributions
Validation, methodology, and writing—original draft, K.L.; writing—review and editing, Q.C. and G.X. (Guoai Xu); validation, G.X. (Guosheng Xu). All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Key Research and Development Program of China (No.: 2022YFB3104400) and the Fundamental Research Funds for the Central Universities under Grant No.: 2023RC69.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available in article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- O’Donovan, T.; O’Donoghue, J.; Sreenan, C.; Sammon, D.; O’Reilly, P.; O’Connor, K. A context aware wireless body area network (BAN). In Proceedings of the 2009 International Conference on Pervasive Computing Technologies for Healthcare, London, UK, 1–3 April 2009; pp. 1–8. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumar, N.; Rodrigues, J. Secure Three Factor User Authentication Scheme for Renewable-Energy-Based Smart Grid Environment. IEEE Trans. Ind. Inform. 2017, 13, 3144–3153. [Google Scholar] [CrossRef]
- Halperin, D.; Heydt-Benjamin, T.S.; Ransford, B.; Clark, S.S.; Defend, B.; Morgan, W.; Fu, K.; Kohno, T.; Maisel, W.H. Pacemakers and Implantable Cardiac Defibrillators: Software Radio Attacks and Zero-Power Defenses. In Proceedings of the 2018 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 18–22 May 2008; pp. 129–142. [Google Scholar]
- Liu, H.B.; Wang, Y.; Liu, J.; Yang, J.; Chen, Y.; Poor, H.V. Authenticating Users through Fine-Grained Channel Information. IEEE. Trans. Mob. Comput. 2018, 17, 251–264. [Google Scholar] [CrossRef]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Reddy, A.G.; Park, K.; Park, Y. On the Design of Fine Grained Access Control with User Authentication Scheme for Telecare Medicine Information Systems. IEEE Access 2017, 5, 7012–7030. [Google Scholar] [CrossRef]
- Wang, X.F.; Wang, L.; Li, Y.; Gai, K. Privacy-Aware Efficient Fine-Grained Data Access Control in Internet of Medical Things Based Fog Computing. IEEE Access 2018, 6, 47657–47665. [Google Scholar] [CrossRef]
- Singh, D.; Wazid, M.; Singh, D.P.; Das, A.K.; Joel, R. Embattle the Security of E-Health System Through A Secure Authentication and Key Agreement Protocol. In Proceedings of the 2023 International Wireless Communications and Mobile Computing (IWCMC), Marrakesh, Morocco, 19–23 June 2023; pp. 1130–1135. [Google Scholar]
- Ogundoyin, S.O.; Kamil, I.A. PAASH: A Privacy-Preserving Authentication and Fine-Grained Access Control of Outsourced Data for Secure Smart Health in Smart Cities. J. Parallel Distrib. Comput. 2021, 155, 101–119. [Google Scholar] [CrossRef]
- Benil, T.; Jasper, J. Blockchain Based Secure Medical Data Outsourcing with Data Deduplication in Cloud Environment. Comput. Commun. 2023, 209, 1–13. [Google Scholar] [CrossRef]
- Ali, Z.; Ghani, A.; Khan, I.; Chaudhry, S.A.; Islam, S.H.; Giri, D. A robust authentication and access control protocol for securing wireless healthcare sensor networks. J. Inf. Secur. Appl. 2020, 52, 2020. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Shojafar, M.; Peris-Lopez, P. LACO: Lightweight three-factor authentication, access control and ownership transfer scheme for e-health systems in IoT. Future Gener. Comp. Syst. 2019, 96, 410–424. [Google Scholar] [CrossRef]
- Yao, H.L.; Yan, Q.; Fu, X.B.; Zhang, Z.; Lan, C. ECC-based lightweight authentication and access control scheme for IoT E-healthcare. Soft Comput. 2022, 26, 4441–4461. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.T.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the Security of Public Key Protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wang, C.Y.; Wang, D.; Tu, Y.; Xu, G.; Wang, H. Understanding node capture attacks in user authentication schemes for wireless sensor networks. IEEE Trans. Dependable Secur. Comput. 2020, 19, 507–523. [Google Scholar] [CrossRef]
- Kumar, S.S.; Guajardo, J.; Maes, R.; Schrijen, G.J.; Tuyls, P. The Butterfly PUF: Protecting IP on Every FPGA. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2018; IEEE: Piscataway, NJ, USA, 2008; pp. 67–70. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2018; pp. 523–540. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. AES Proposal: Rijndael; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2003.
- Xie, Q.; Liu, D.; Ding, Z.; Tan, X.; Han, L. Provably Secure and Lightweight Patient Monitoring Protocol for Wireless Body Area Network in IoHT. J. Healthc. Eng. 2023, 2023, 4845850. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Xu, L.; Vijayakumar, P.; Kumar, N. A Novel Three-Factor Authentication Protocol for Wireless Sensor Networks with IoT Notion. IEEE Syst. J. 2021, 15, 1120–1129. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secur. Comput. 2016, 15, 708–722. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.B.; Wang, P. Zipf’s Law in Passwords. IEEE Trans. Inf. Forensic Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Wang, D.; Zou, Y.K.; Dong, Q.Y. How to Attack and Generate Honeywords. In Proceedings of the 43rd IEEE Symposium on Security and Privacy (IEEE S&P), San Francisco, CA, USA, 23–25 May 2022; pp. 489–506. [Google Scholar]
- Zou, S.H.; Cao, Q.; Wang, C.Y.; Huang, Z.; Xu, G. A Robust Two-Factor User Authentication Scheme-Based ECC for Smart Home in IoT. IEEE Syst. J. 2021, 16, 4938–4949. [Google Scholar] [CrossRef]
- Qiu, S.M.; Wang, D.; Xu, G. Practical and Provably Secure Three-Factor Authentication Protocol Based on Extended Chaotic-Maps for Mobile Lightweight Devices. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1338–1351. [Google Scholar] [CrossRef]
- Wang, D.; Gu, Q.; Cheng, H. The request for better measurement: A comparative evaluation of two-factor authentication schemes. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016. [Google Scholar]
- Wang, C.Y.; Wang, D.; Xu, G.; He, D. Efficient Privacy-Preserving User Authentication Scheme with Forward Secrecy for Industry 4.0. Sci. China Inf. Sci. 2022, 65, 112301. [Google Scholar] [CrossRef]
- Kumar, D.; Jain, S.; Khan, A.; Pathak, P.S. An improved lightweight anonymous user authenticated session key exchange scheme for Internet of Things. J. Am. Intell. Hum. Comp. 2020, 14, 5067–5083. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).