Performance Analysis of P2P Networks with Light Communication Links: The Static Managed Case
Abstract
:1. Introduction
- We develop a mathematical analysis of P2P-managed systems with no mobility capabilities that allow for the introduction of light-based transmissions.
- We provide a detailed performance comparison between LiFi 2.0 and WiFi 7 networks.
- Several scenarios are proposed in order to evaluate average download time and node variation in networks (P2P-WiFi, P2P-LiFi, centralized WiFi (C-WiFi) and centralized-LiFi (C-LiFi) networks).
- A P2P-LiFi concept is introduced based on the operation and characteristics of LOS and NLOS scenarios.
- We provide performance metrics in terms of the average download time for different file sizes across different network population sizes.
- In addition to a numerical solution for the continuous-time Markov chain (CTMC), discrete event simulations (DES) of each scenario are provided to validate the analytical model.
2. Related Work
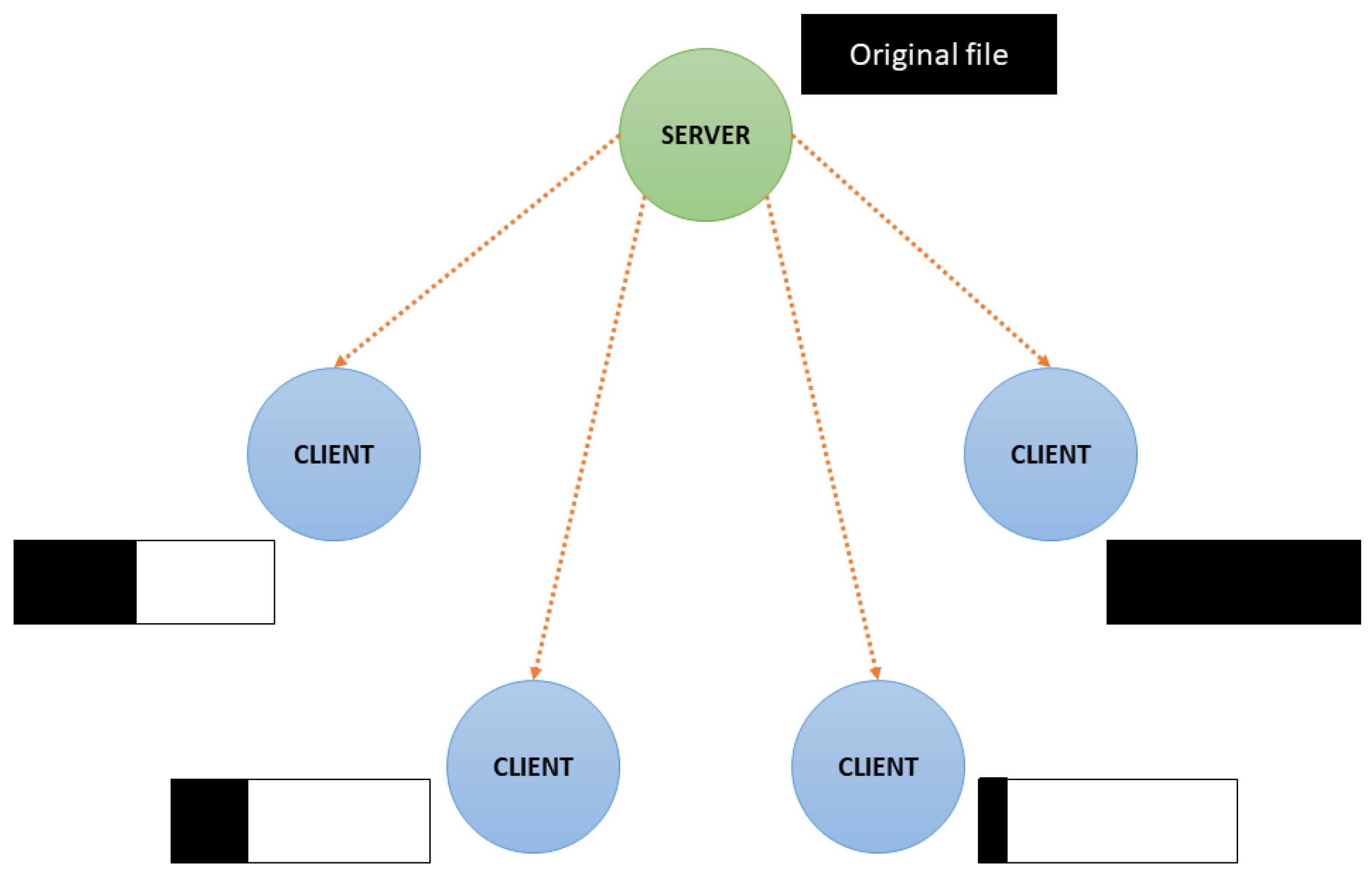
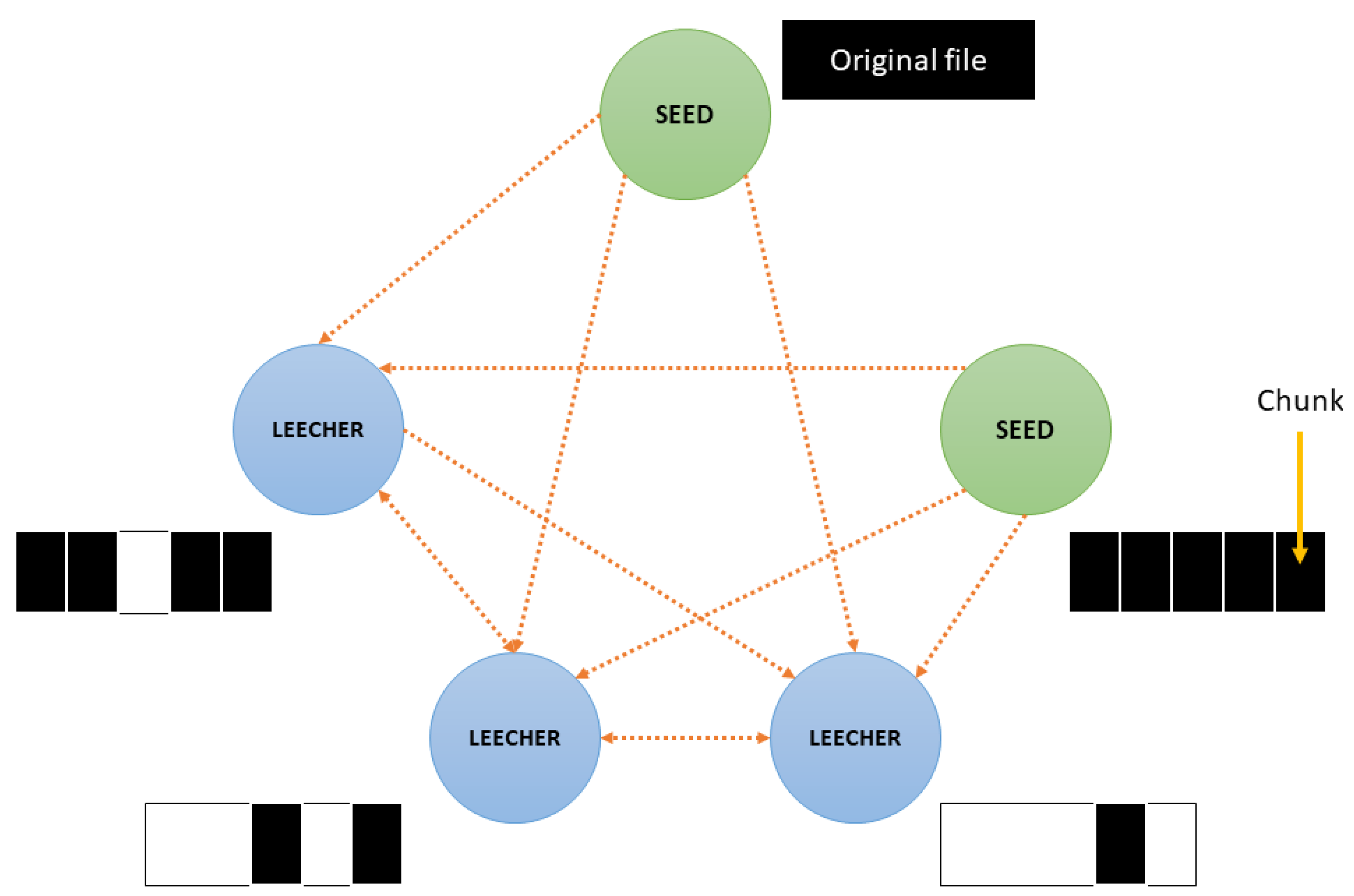
3. Centralized and Decentralized Networks
- do not connect with other , because they already have all the information available on the network.
- reach—and preferably try to connect with—a , since it can share all available chunks.
- also try to connect with other that have different between them.
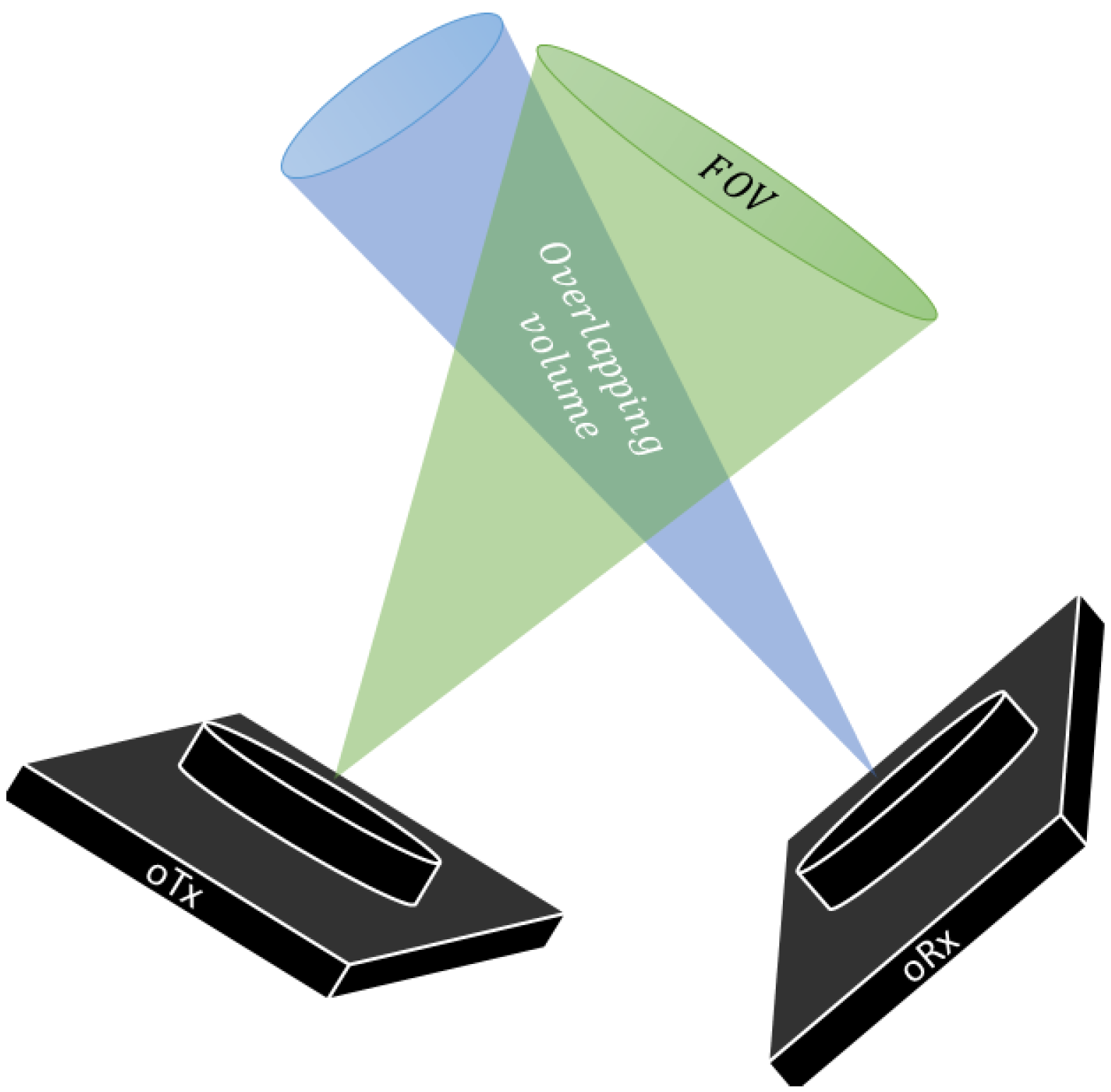
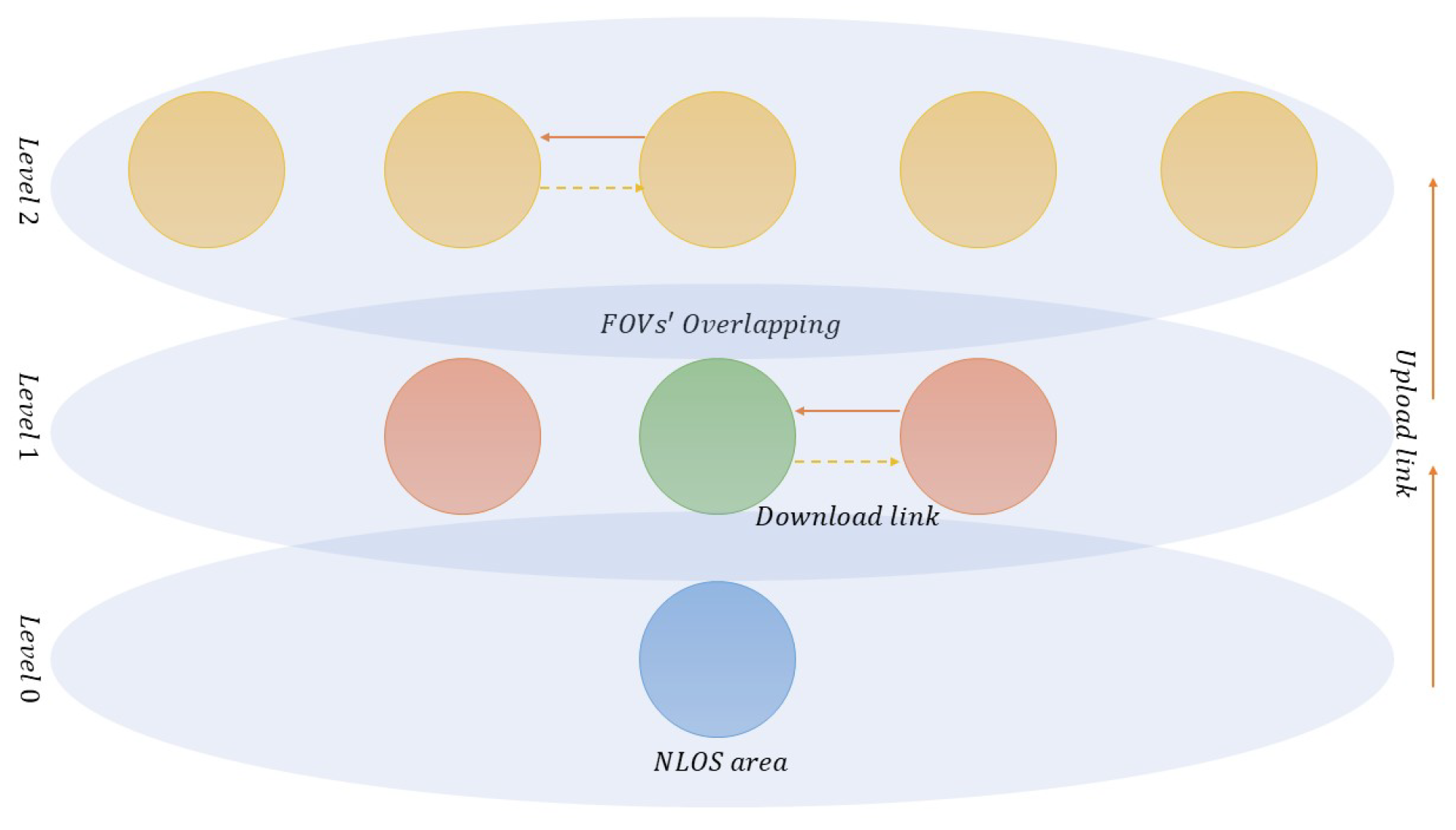
4. LiFi- and WiFi-Based Communication P2P Architectures
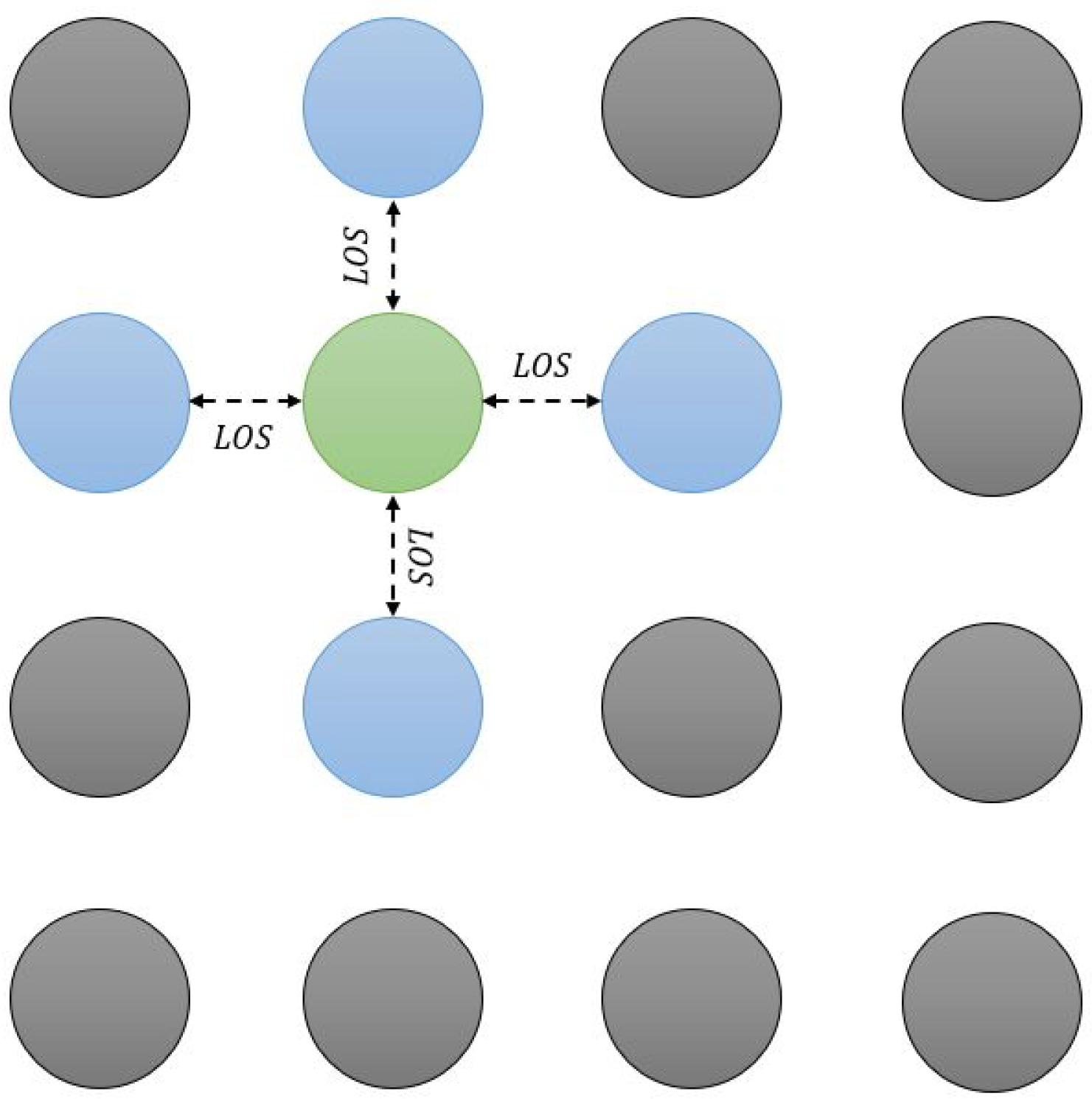
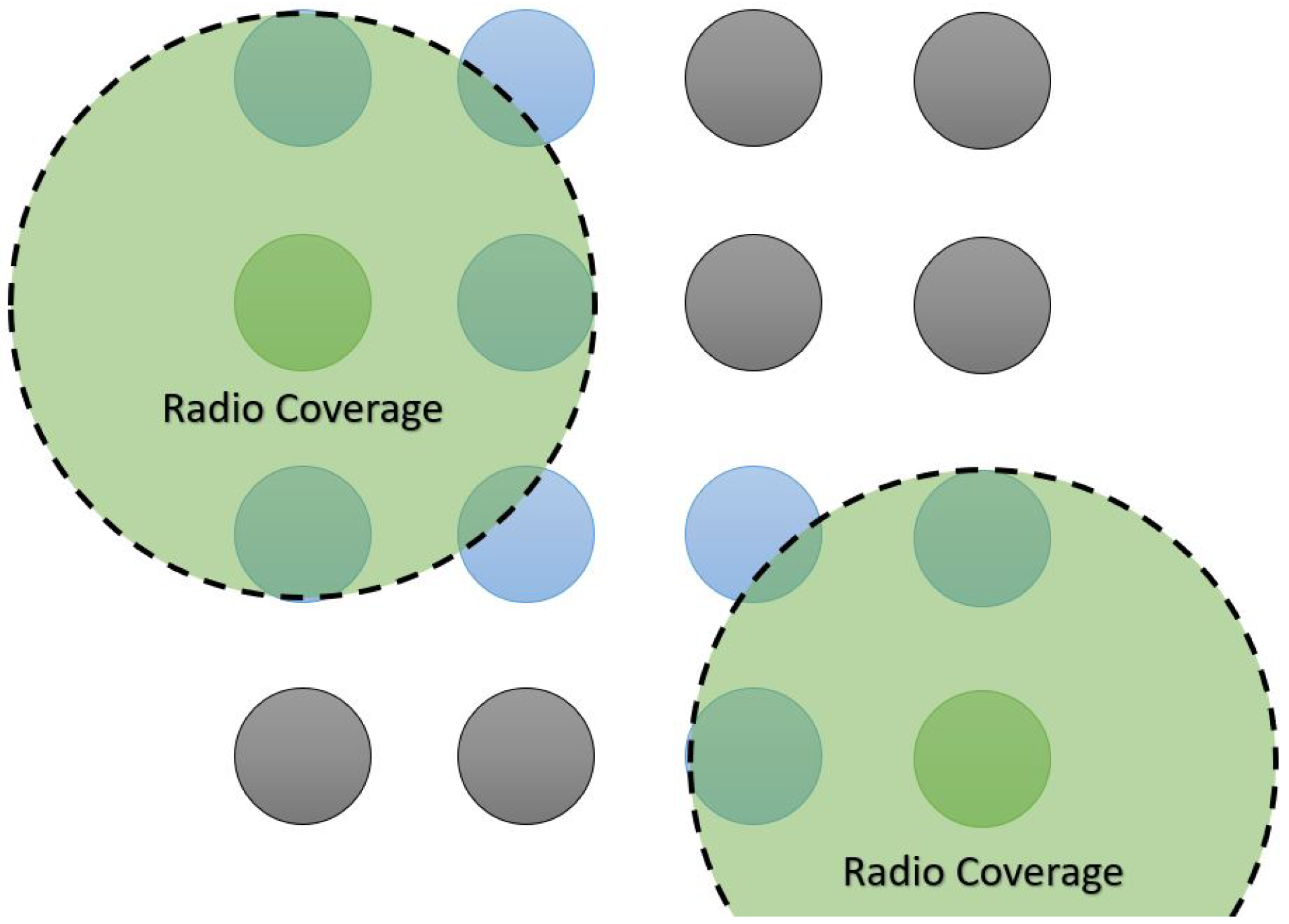
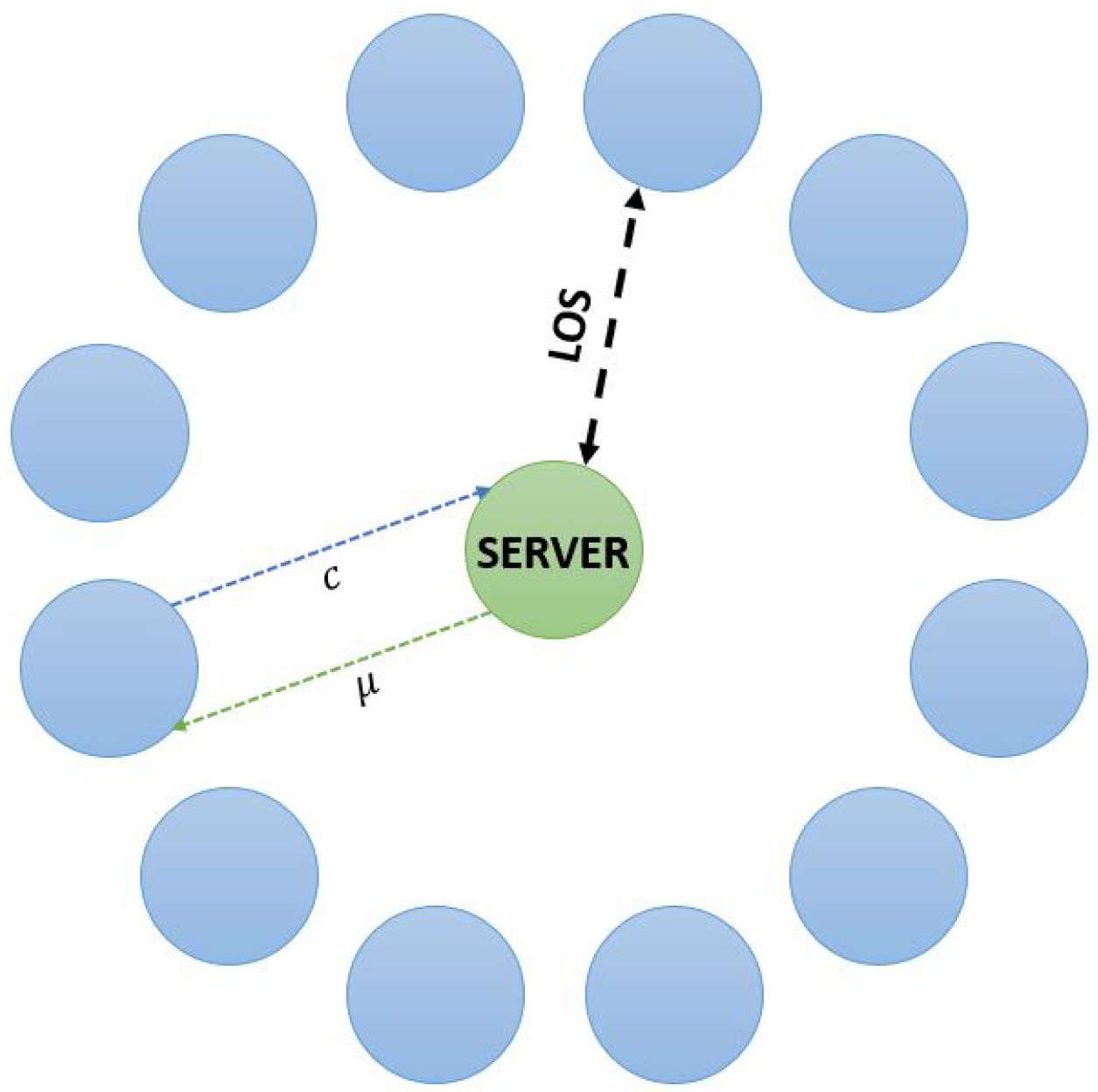
5. System Description
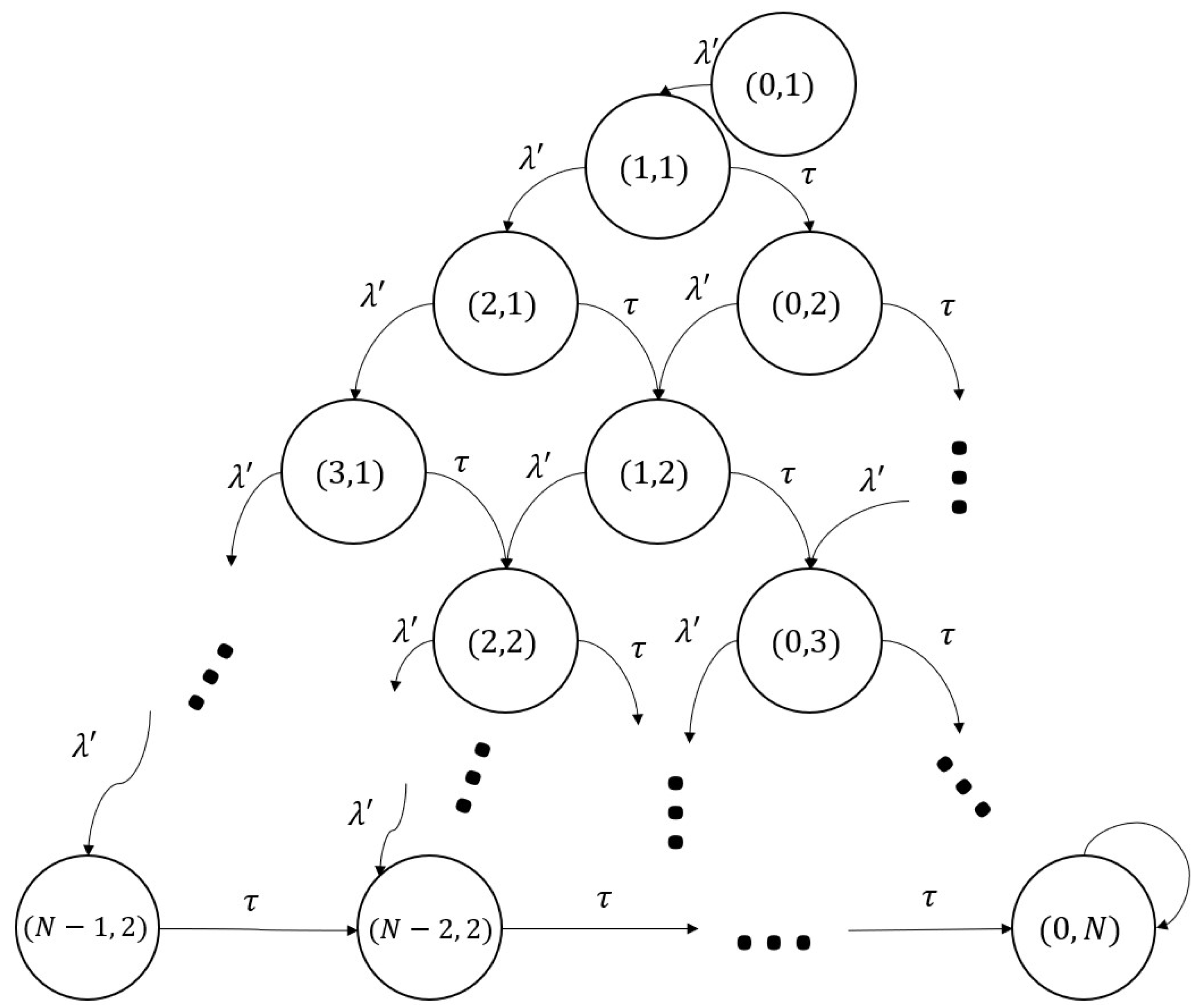
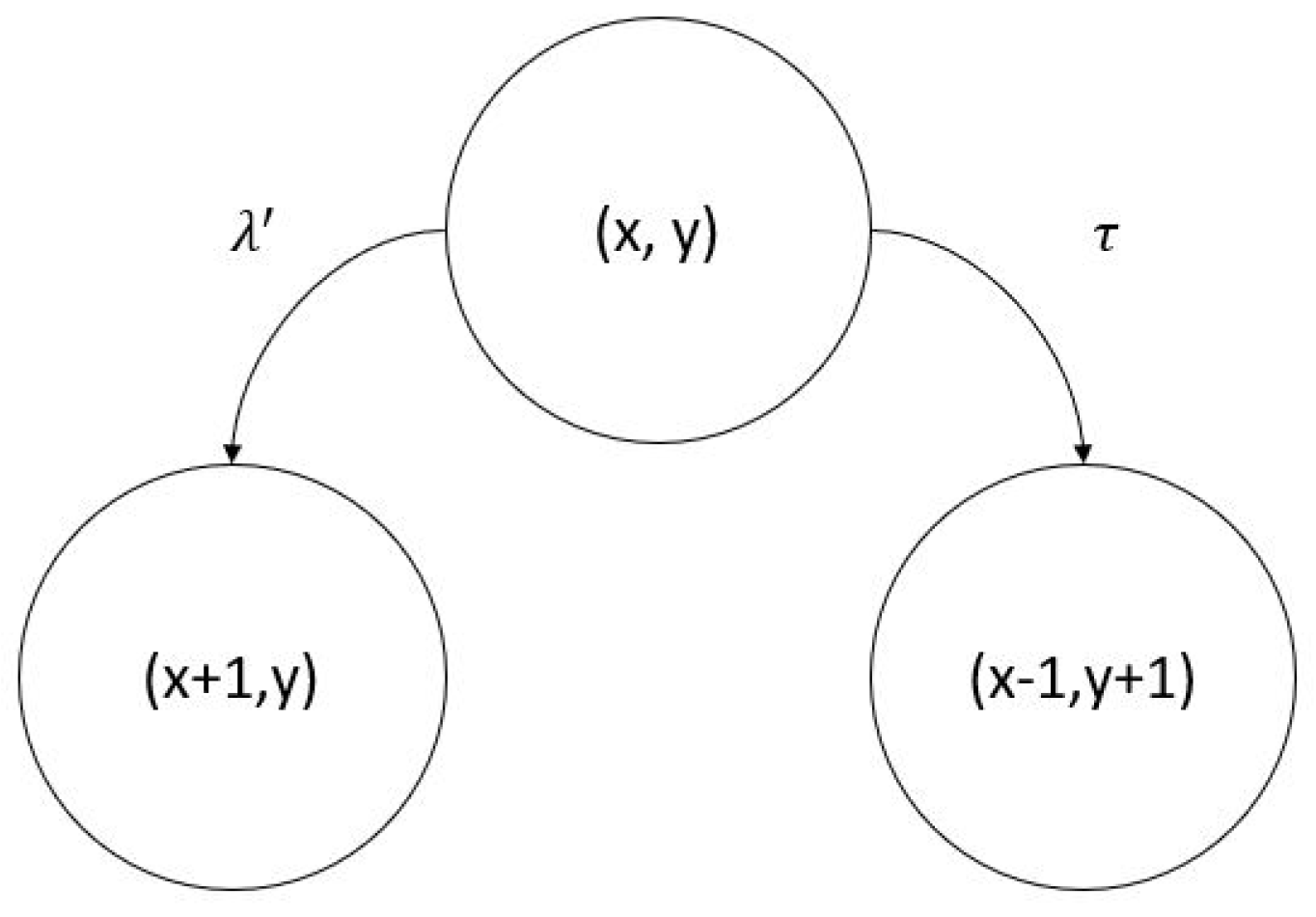
6. Mathematical Analysis
- To state with rate , when a new peer (with no chunks of the file) requests and starts the file download procedure in the system, and it becomes a leecher. Note that for the LiFi case, this highly depends on the position of the node with respect to the seeds and other leechers. Indeed, in light communications, it is not possible to reach all nodes directly, as opposed to a broadcast using RF. Here, it is relevant to consider the specific architecture of the network, as explained in previous sections.
- To state with rate , when a leecher acquires all the available data in the network and it becomes a seed.
| Algorithm 1: P2P-LiFi/P2P-WiFi/centralized numerical solution algorithm. |
 |
| Algorithm 2: P2P-LiFi/P2P-WiFi/centralized DES solution algorithm. |
 |
7. Numerical Results
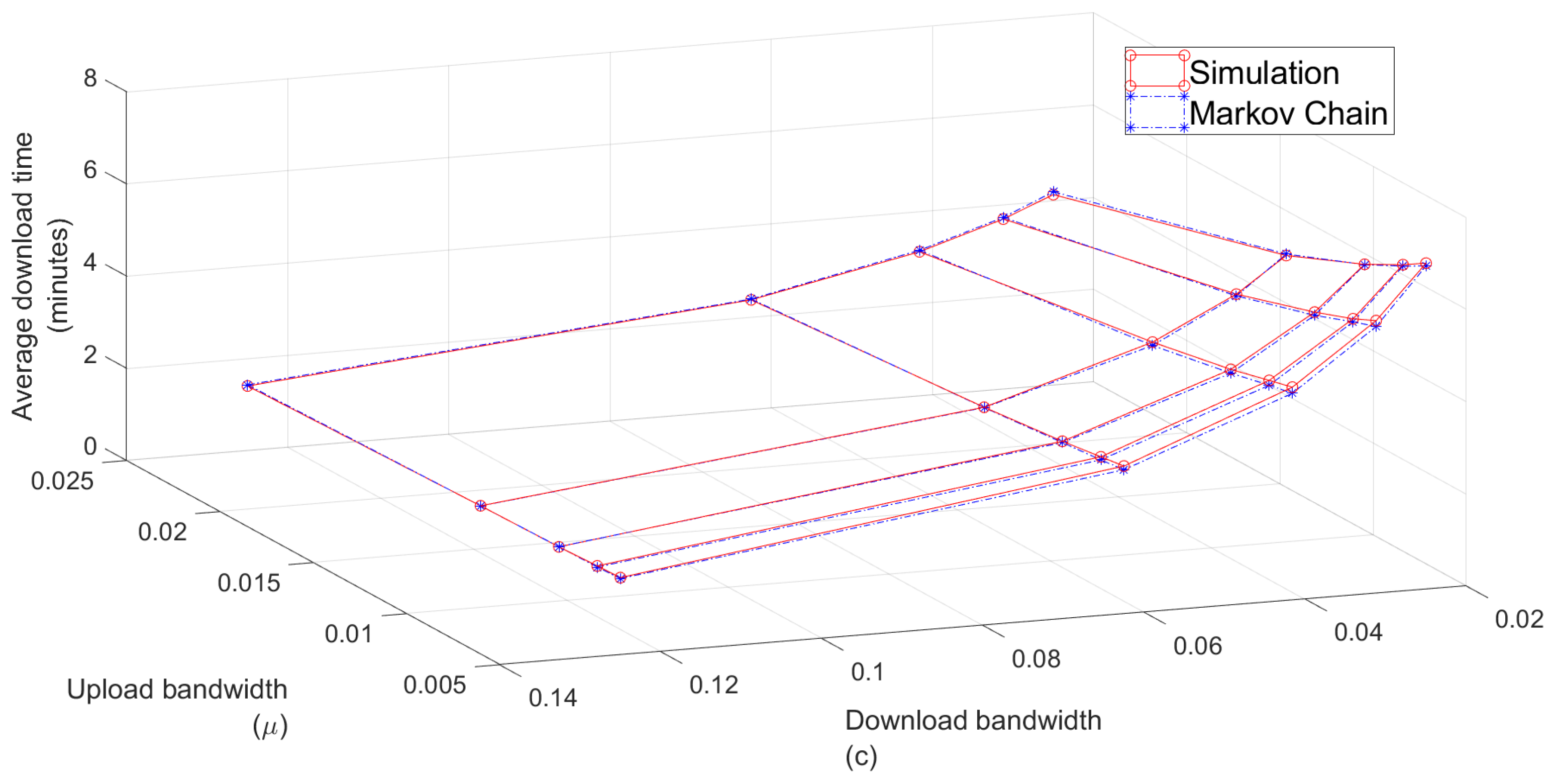
7.1. Validation of the Analytical Model
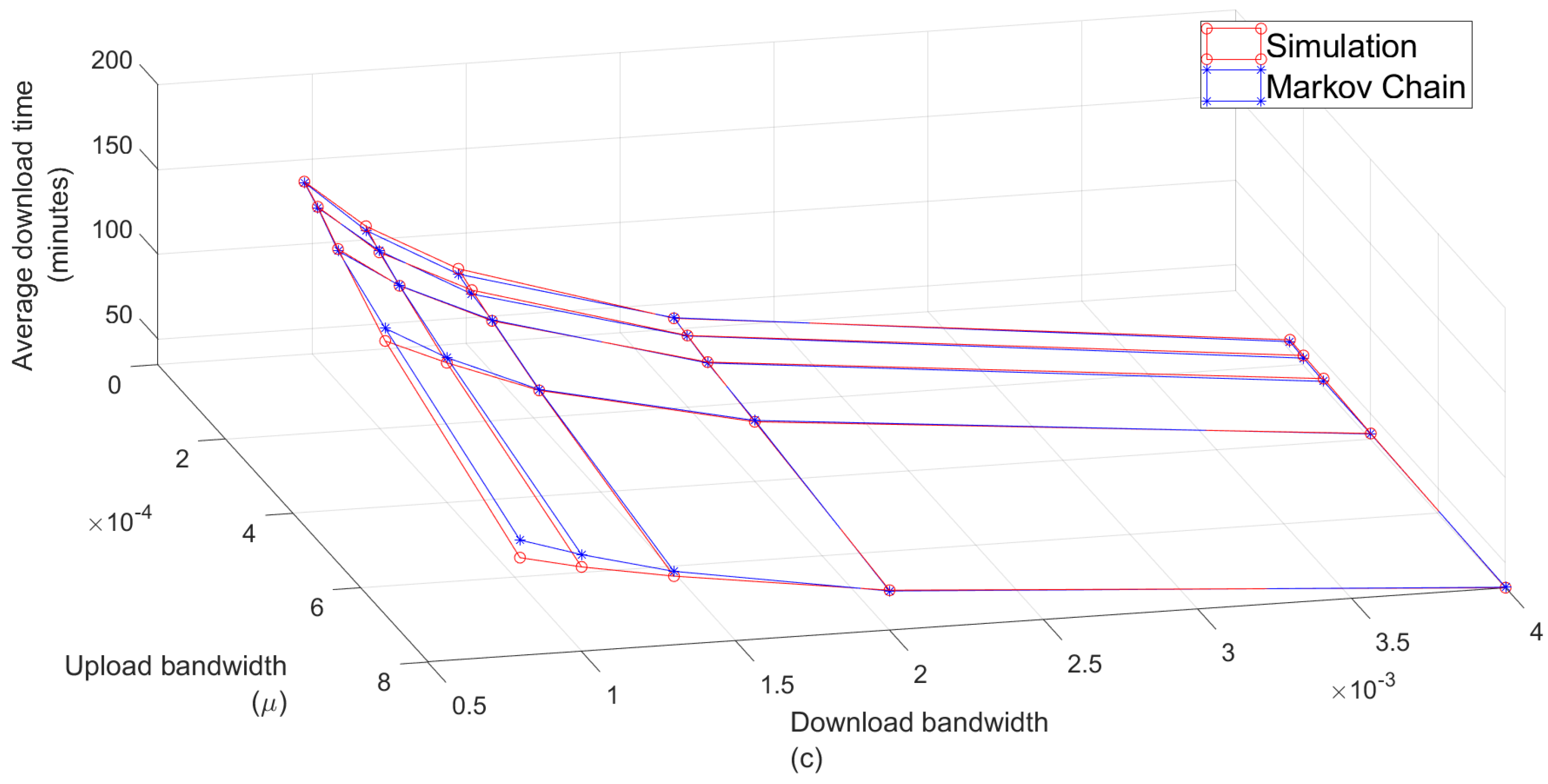
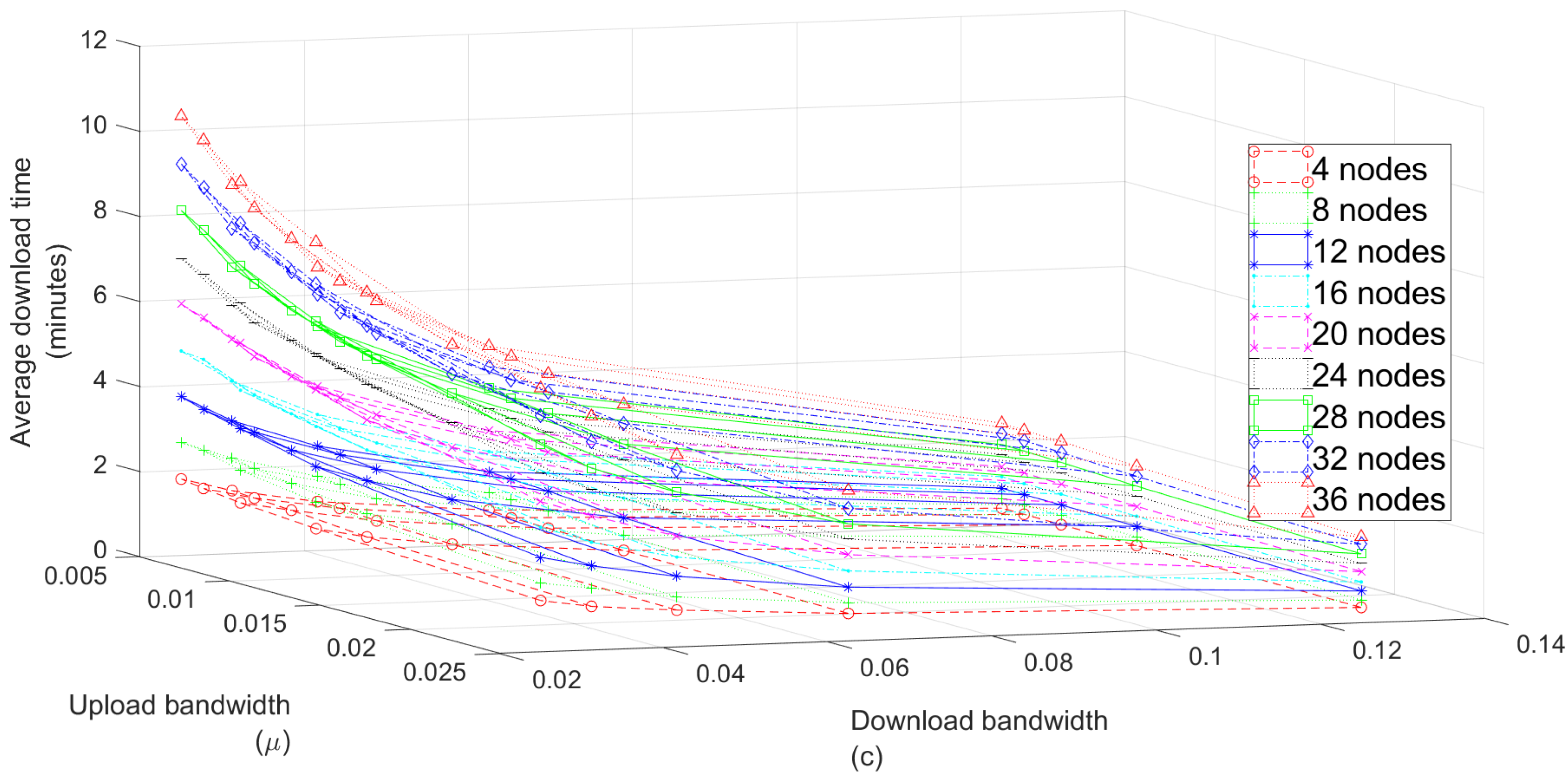
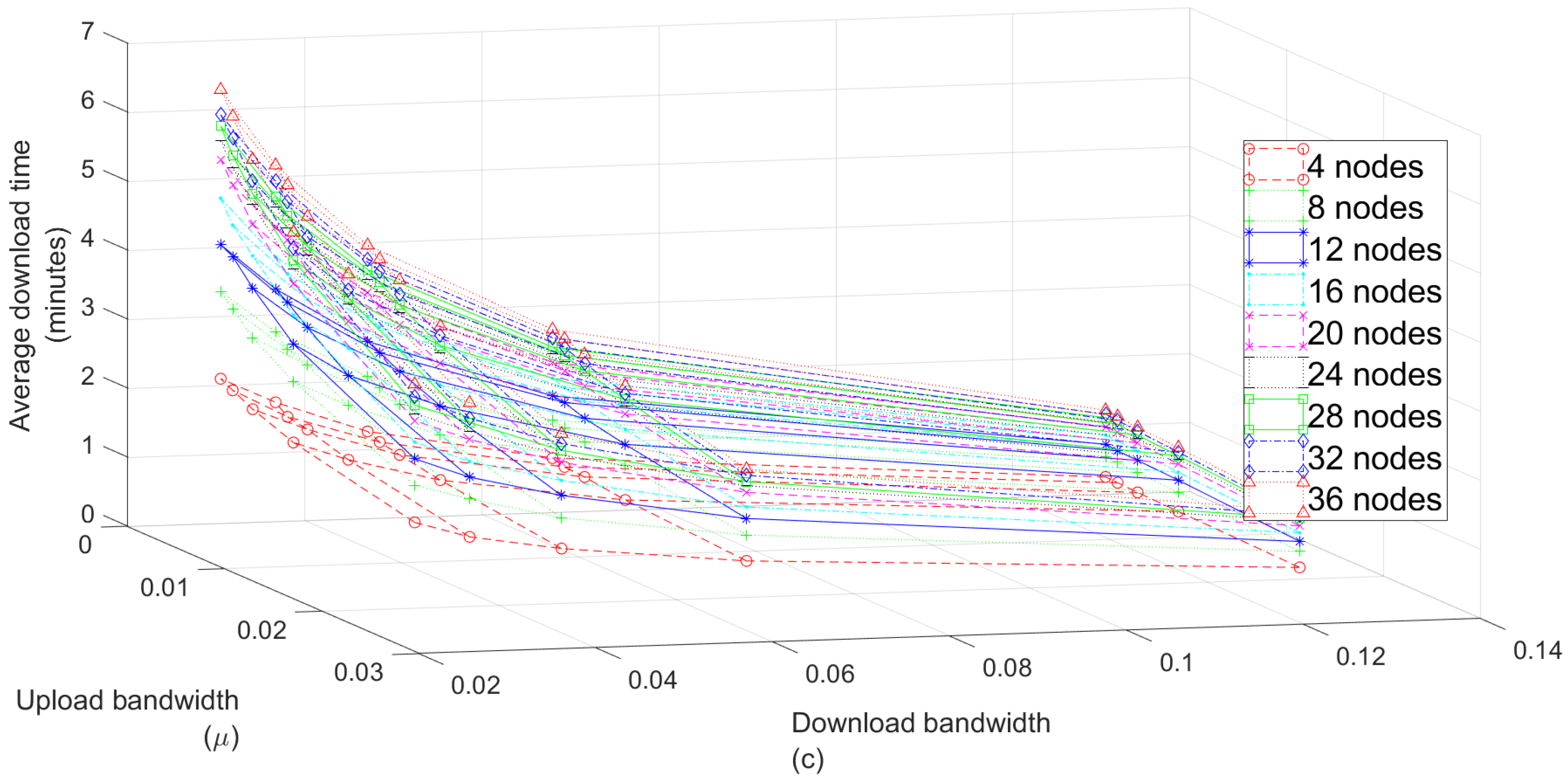
7.2. Impact of the Number of Nodes in the System
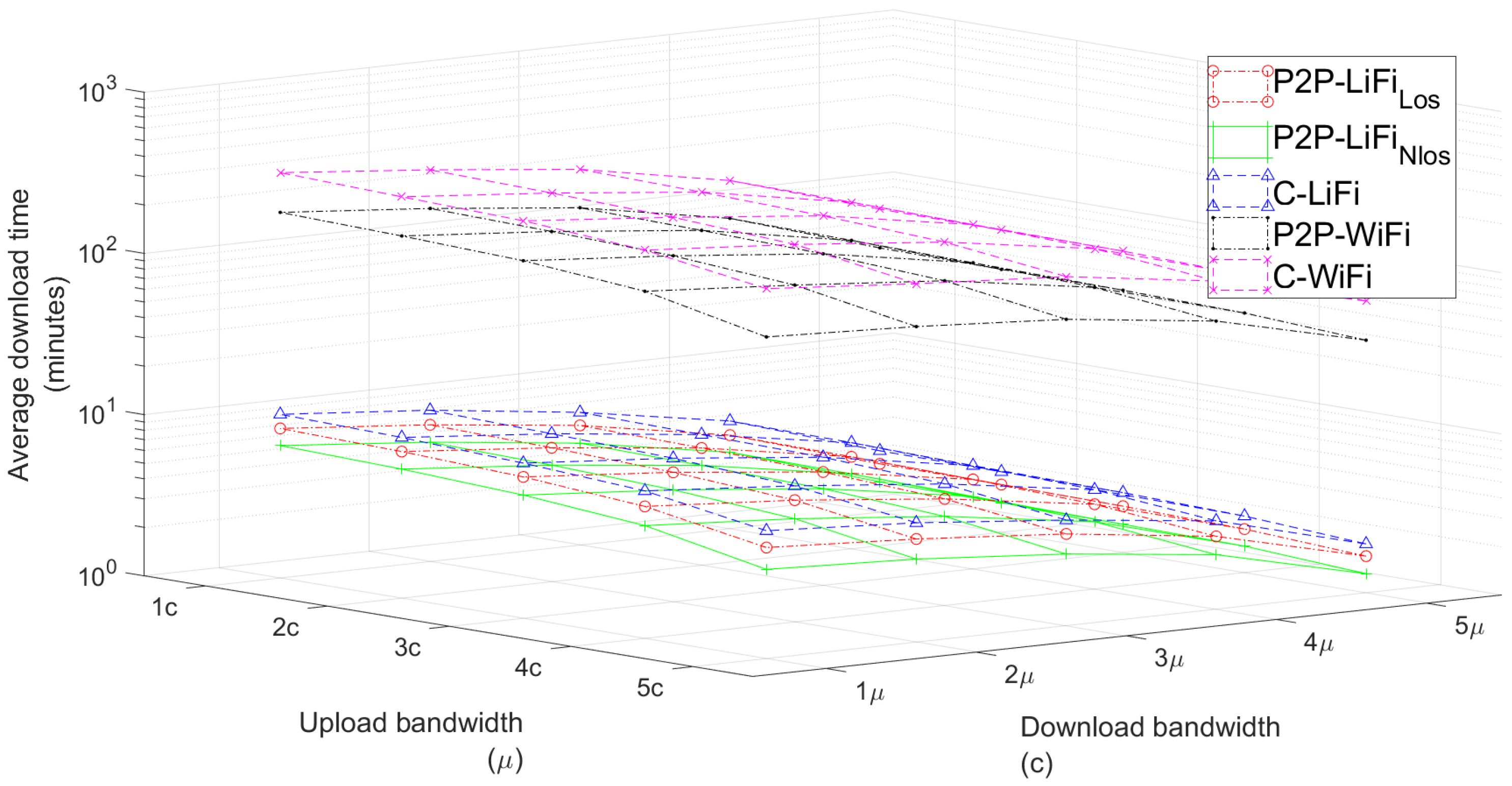
7.3. WiFi vs. LiFi Performance Comparison
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| AP | Access Point |
| AR | Augmented Reality |
| BER | Bit Error Ratio |
| C-LiFi | Centralized LiFi |
| CTMC | Continuous-Time Markov Chain |
| C-WiFi | Centralized WiFi |
| D2D | Device-to-Device Communication |
| DES | Discrete Event Simulations |
| DFL | Decentralized Federated Learning |
| EDCA | Enhanced Distributed Channel Access |
| FOV | Field of View |
| HMM | Hidden Markov Model |
| IoE | Internet of Everything |
| IoT | Internet of Things |
| IR | Infrared |
| LiFi | Light Fidelity |
| LOS | Line of Sight |
| ML | Machine Learning |
| NLOS | Non-Line of Sight |
| P2P | Peer-to-Peer |
| QoS | Quality of Service |
| RF | Radio Frequency |
| SA-MAC | Self-Adaptive Medium Access Control |
| SINR | Signal-to-Interference-and-Noise Ratio |
| SNR | Signal-to-Noise Ratio |
| UV | Ultraviolet |
| VL | Visible Light |
| VR | Virtual Reality |
| WiFi | Wireless Fidelity |
Appendix A. Markov Chain’s Numerical Solution Algorithm
- 1.
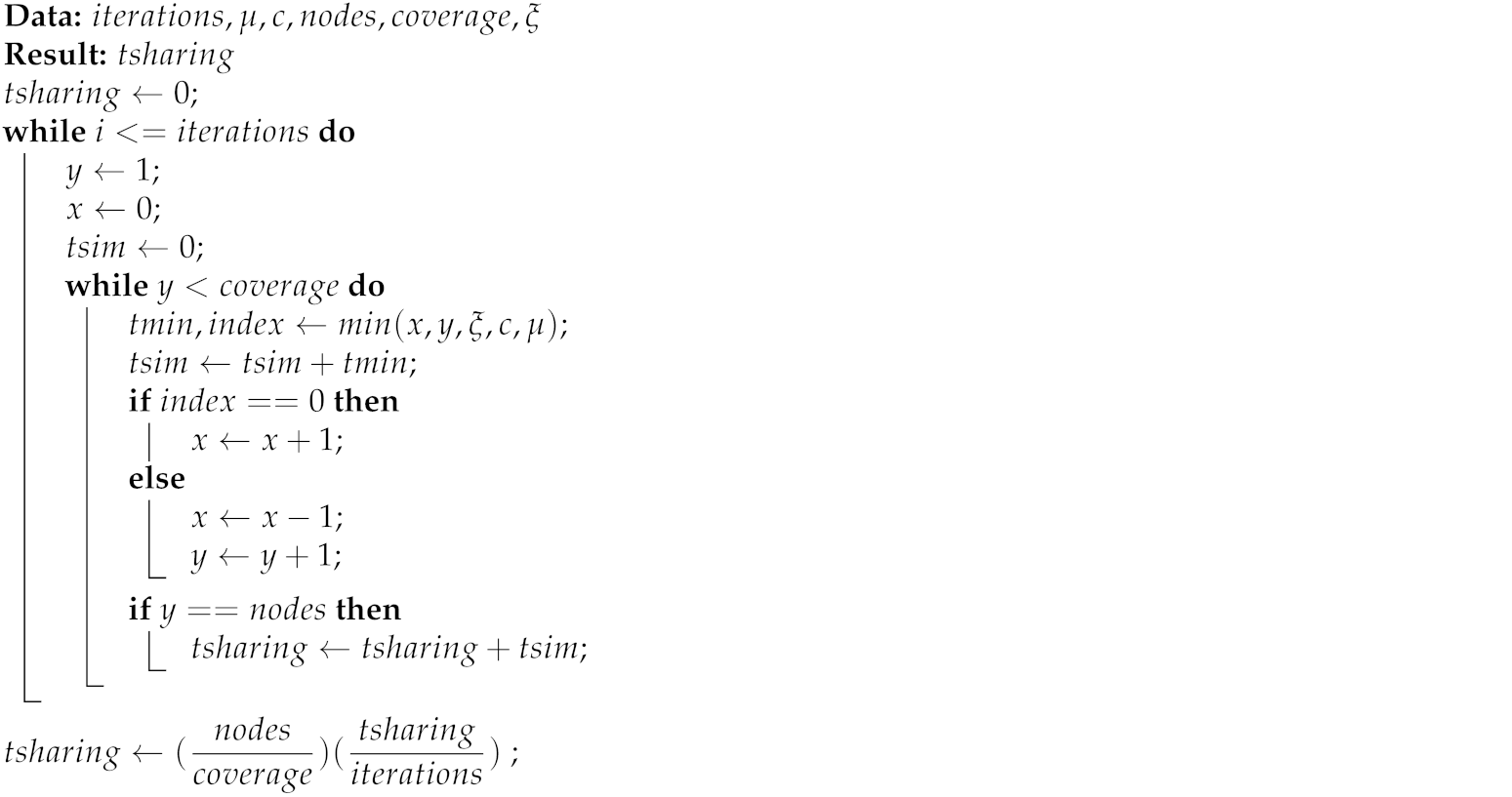
- The process begins with the input data of the bandwidths (c and ) and the control variable (); those variables will allow fpr the calculation of the system rates (’, ), in addition, the number of iterations () is defined, as well as the number of nodes in the scenario () and the size of the clusters () into which the number of nodes will be divided (the greater coverage, the more peers that one node can reach in the networks; on the other hand, a very small coverage could provide enough information about average download times in the network). These input variables will allow for the calculation of the time in which the information is shared () in the proposed networks.
- 2.
- Once the input data have been entered into the algorithm, the process will be repeated in the indicated number of iterations (until the chain obtains a steady state in the long term); therefore, for each iteration, it initializes the values of the simulation time () and the counters of leechers (x) and seeds (y), taking into account that for the studied networks, there must be at least one server in the system at all times.
- 3.
- The system starts at state , which corresponds to the case where the system is in initial conditions (in other words, there is just one seed in the system and the other peers are not asking for information yet); the calculation of the time in which the next transition will take place is equivalent to obtaining the minimum number () of the times and calculated with rates ’ and , respectively ( and are the random times that correspond to an event of conversion from a leecher to seed or an event of a request of information from one peer, and they are modeled as random variables exponentially distributed), as well as the position () of this calculated time.
- 4.
- The following step indicates the addition of the calculated minimum time to the simulation time, and then there are two possible conditions:
- If the minimum time corresponds to the one created by the rate, it indicates that a node has requested information for the first time in the system, indicating the presence of a leecher in the system .
- Instead, if the smallest time corresponds to that created by rate, it indicates that a node has obtained all the circulating chunks, indicating that a conversion from a leecher to a seed has occurred .
- 5.
- The process continues until all the nodes present in the cluster of the network have become seeds (recalling that the dimension of the clusters can be equal to or less than the number of nodes); it is at this specific moment when the simulation time is added to the sharing time. Finally (at the end of the repetitions), the sharing time is normalized by the number of iterations and the relationship between nodes and clusters.
| Algorithm A1: P2P-LiFi/P2P-WiFi/centralized numerical solution algorithm |
 |
Appendix B. DES Algorithm
- 1.
- As an initial step, input variables for bandwidths (), iterations (), nodes (), and cluster dimensions () are entered. It is important to highlight that at the end of this process, the average time in which a file of a certain size is shared in all the nodes of the network () will be obtained.
- 2.
- Subsequently, the process will be repeated according to the number of iterations, so the following step is to initialize the simulation time (), the counter concerned with the nodes that contain full chunks (y), and the counter concerned with nodes that do not contain all the information available in the system (x).
- 3.
- In the succeeding stage, a seed (state ) is added to the queue with its respective initial parameters such as occurrence time, ID, chunk list, upload status, and connection list (depending on the range of coverage and the nature of the technology). Afterward, this process is repeated for all the leechers that are in the scenario (), remembering there are additional parameters in these kinds of nodes with respect to the seeds (downloading connection status, list of downloading connections, etc.).
- 4.
- Once all nodes have been initialized and added to the queue, the below subroutine is initialized until the number of seeds is equal to the nodes present in the cluster:
- Total conversions from leechers to seeds () are calculated between the time the last event occurred to the time at which simulation is located (generally time among events). Above is an important point in the system simulation, because the number of conversions is found through all the nodes present in the network by the chunk-updating function ().
- Chunk updating is conducted by inspecting each node in the queue, and includes the processes of search and link between nodes; these connections depend on the occupancy states, the limit of uploading and downloading connections, the coverage lists, and even the transmission efficiency (nodes that can transmit a greater number of chunks between them are more likely to connect).
- Next, conversions are added to the number of seeds, and those same conversions are subtracted from the number of leechers, obtaining the new state: . Subsequently, the time of the following state in the queue is taken, and the subroutine is repeated.
- 5.
- When the previous point is completed, the simulation time is added to the total sharing time and a new iteration of the process begins. At the end of the iterations, the sharing time is normalized.
| Algorithm A2: P2P-LiFi/P2P-WiFi/centralized DES solution algorithm |
 |
References
- Zikria, Y.B.; Ali, R.; Afzal, M.K.; Kim, S.W. Next-generation internet of things (iot): Opportunities, challenges, and solutions. Sensors 2021, 21, 1174. [Google Scholar] [CrossRef]
- Armin, W. The future of 5G smart home network security is micro-segmentation. Netw. Secur. 2020, 11, 11–13. [Google Scholar]
- Cheng, C.; Xiaogang, C.; Dibakar, D.; Dmitry, A.; Carlos, C. Overview and Performance Evaluation of Wi-Fi 7. In Proceedings of the 2018 International Symposium on Recent Advances in Electrical Engineering (RAEE), Islamabad, Pakistan, 17–18 October 2018; pp. 1–6. [Google Scholar]
- Toni, A.; Marc, C.Z.; Boris, B. Time-sensitive networking in IEEE 802.11 be: On the way to low-latency WiFi 7. Sensors 2021, 21, 4954. [Google Scholar]
- Rosilah, H.; Azana, A.; Liza, L. 5G Technology in Internet of Everything (IoE) Application using Light Fidelity (Li-Fi) Indoor Communication. In Proceedings of the 1st International Conference on Informatics, Engineering, Science and Technology, INCITEST 2019, Bandung, Indonesia, 18 July 2019; pp. 32–58. [Google Scholar]
- Sadia, M.; Ragheesa, M.; Khadija, R.; Aroosh, M.; Tamkeen, S. An overview of LiFi: A 5G candidate Technology. In Proceedings of the 2018 International Symposium on Recent Advances in Electrical Engineering (RAEE), Islamabad, Pakistan, 17–18 October 2018; pp. 1–6. [Google Scholar]
- Mohammad-Dehghani, S.; Hossein, K.; Elham, S.; Ahmad Adnan, Q.; Barzan, Y.; Sanaa, M.; Ravinder, S.; Bela, B.; Dominique, C.; Bastien, B. Terabit Indoor Laser-Based Wireless Communications: LiFi 2.0 for 6G. arXiv 2022, arXiv:2206.10532. [Google Scholar]
- Harald, H.; Liang, Y.; Yunlu, W.; Cheng, C. What is lifi? J. Light. Technol. 2015, 34, 1533–1544. [Google Scholar]
- Vidya, P. A Comparison and Analysis of Wireless Fidelity to Light Fidelity and its Combination of Networks. Int. J. Innov. Sci. Res. Technol. 2022, 7, 1166–1172. [Google Scholar]
- Mario-Eduardo, R.-A.; Izlian-Yolanda, O.-F. System modeling for priority schemes in managed Peer-to-Peer networks. Comput. Sist. 2018, 22, 685–716. [Google Scholar]
- Ardimas, P.; Mohammad-Dehghani, S.; Majid, S.; Harald, H. Impact of terminal orientation on performance in LiFi systems. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Mohammad-Dehghani, S.; Ardimas, P.; Iman, T.; Harald, H.; Majid, S. Impact of device orientation on error performance of LiFi systems. IEEE Access 2019, 7, 41690–41701. [Google Scholar] [CrossRef]
- Ahmet-Burak, O.; Wasiu-O, P. LiFi-Based D2D Communication in Industrial IoT. IEEE Syst. J. 2022, 17, 1591–1598. [Google Scholar]
- Du, M.; Zheng, H.; Feng, X.; Chen, Y.; Zhao, T. Decentralized Federated Learning with Markov Chain Based Consensus for Industrial IoT Networks. IEEE Trans. Ind. Inform. 2022, 19, 6006–6015. [Google Scholar] [CrossRef]
- Fitsum, T.; Chung-G, K. Decentralized deep reinforcement learning-based dynamic uplink band selection in enhanced licensed-assisted access. In Proceedings of the 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020; pp. 477–480. [Google Scholar]
- Marios, C.; Constandinos, M.; George, V.; Muneer-Bani, Y. On the mobility scenario implementation using a Graphical P2P Discrete Event Simulator for the Bittorrent Protocol. J. Algorithms Comput. Technol. 2013, 7, 449–487. [Google Scholar]
- Vicino, D.; Lung, C.H.; Wainer, G.; Dalle, O. Investigation on software-defined networks’ reactive routing against BitTorrent. IET Netw. 2015, 4, 249–254. [Google Scholar] [CrossRef] [Green Version]
- Dimitrios, T.; Nick, R. A Comparison of Peer-to-Peer Search Methods. In Proceedings of the WebDB, San Diego, CA, USA, 12–13 June 2003; pp. 61–66. [Google Scholar]
- Gianluigi, F.; Agostino, F.; Giandomenico, S. A Jxta Based Asynchronous Peer-to-Peer Implementation of Genetic Programming. J. Softw. 2006, 1, 12–23. [Google Scholar]
- Nico, M.; Thomas, M. JXTA: A technology facilitating mobile peer-to-peer networks. In Proceedings of the 2002 International Mobility and Wireless Access Workshop, Fort Worth, TX, USA, 12 October 2002; pp. 7–13. [Google Scholar]
- María del Carmen, R.-H.; Sergio, I.; Raquel, T.; Ramón, H. Context-aware recommendations using mobile P2P. In Proceedings of the 15th International Conference on Advances in Mobile Computing & Multimedia, Salzburg, Austria, 4–6 December 2017; pp. 82–91. [Google Scholar]
- Faiza, G.; Adnan, M.; Imran, M.; Suleman, M.; Tauqeer-Ul, I.; Laith, A.; Agostino, F. A centralized strategy for multi-agent exploration. IEEE Access 2022, 10, 126871–126884. [Google Scholar]
- Michelei, R.; Tommaso, D.-N.; Eugenio, D.-S.; Francesco-Maria, D. Semantic based collaborative p2p in ubiquitous computing. Web Intell. Agent Syst.: An Int. J. 2007, 5, 375–391. [Google Scholar]
- Muhammad, A.; Saad, Q. Energy Efficient QoS-Based Access Point Selection in Hybrid WiFi and LiFi IoT Networks. IEEE Trans. Green Commun. Netw. 2021, 6, 897–906. [Google Scholar]
- Jaafaru, S.; Sadiq, I.; Abiodun-Musa, A.; Steve, A.; Ali-Nyangwarimam, O. Handover in hybrid lifi and wifi networks. In Proceedings of the 2019 15th International Conference on Electronics, Computer and Computation (ICECCO), Abuja, Nigeria, 10–12 December 2019; pp. 1–6. [Google Scholar]
- Oluwaseyi-Paul, B.; Vipin, B. Vertical handover prediction based on hidden markov model in heterogeneous VLC-WiFi system. Sensors 2022, 22, 2473. [Google Scholar]
- Küçük, K.; Msongaleli, D.L.; Akbulut, O.; Kavak, A.; Bayılmış, C. Self-adaptive medium access control protocol for aggregated VLC–RF wireless networks. J. Abbr. 2021, 488, 126837. [Google Scholar] [CrossRef]
- Rabe, A.; Lutz, L. Stochastic geometry analysis of sojourn time in RF/VLC hybrid networks. IEEE Trans. Wirel. Commun. 2022, 21, 11237–11251. [Google Scholar]
- Ngo, K.-T.; Stefano, M.; Ilenia, T. Exploiting EDCA for feedback channels in hybrid VLC/WiFi architectures. In Proceedings of the 2021 19th Mediterranean Communication and Computer Networking Conference (MedComNet), Ibiza, Spain, 15–17 June 2021; pp. 1–6. [Google Scholar]
- Ngo, K.-T.; Fabrizio, G.; Daniele, C.; Stefano, M.; Ilenia, T.; Giovanni, G. Hybrid VLC/WiFi Architectures with Priority Feedback Channels. In Proceedings of the 2022 61st FITCE International Congress Future Telecommunications: Infrastructure and Sustainability (FITCE), Rome, Italy, 29–30 September 2022; pp. 1–6. [Google Scholar]
- Monica, B.; Brejesh, L.; Abhishek, D. Mac layer performance modelling for ieee 802.15. 7 based on discrete-time Markov chain. IET Commun. 2021, 15, 1883–1896. [Google Scholar]
- Suguru, S.; Tomoki, Y.; Takahiro, H.; Shojiro, N. A data reception method to reduce interruption time in P2P streaming environments. In Proceedings of the 2010 13th International Conference on Network-Based Information Systems, Takayama, Japan, 14–16 September 2010; pp. 166–172. [Google Scholar]
- Qiu, D.; Srikant, R. Modeling and performance analysis of BitTorrent-like peer-to-peer networks. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 367–378. [Google Scholar] [CrossRef] [Green Version]
- Mario, R.-A.; Gerardo, R. Priority-based scheme for file distribution in peer-to-peer networks. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010; pp. 1–6. [Google Scholar]
- Simona, R.; Tatiana, A.; Álvaro, R.; Monica, L.; Andreea, I. VLC, OCC, IR and LiFi reliable optical wireless technologies to be embedded in medical facilities and medical devices. J. Med. Syst. 2019, 43, 308. [Google Scholar]
- Rahul, G.; Srikumar, V.; Amandeep-Singh, R.; Deepa, K. LiFi for vehicle to vehicle communication—A review. Procedia Comput. Sci. 2019, 165, 25–31. [Google Scholar]
- Kai, B.; Volker, J.; Marc, E.; Maximilian, R.; Eduward, T.; Koonen, A.M.J.; Linnartz, J.-P.; Daniel, B.; Marcel, M.; Bök, P.-B. A flexible system concept for LiFi in the Internet of Things. In Proceedings of the 2020 22nd International Conference on Transparent Optical Networks (ICTON), Bari, Italy, 19–23 July 2020; pp. 1–4. [Google Scholar]
- Matt, F. Netcraft Analysis: Online Speed Testing Tools; Netcraft Ltd.: Bath, UK, 2013. [Google Scholar]




| State | Condition | Description |
|---|---|---|
| Penury | There is not enough bandwidth to download at the maximum rate | |
| Abundance | There is enough bandwidth for all peers to download at the maximum rate |
| State | ||
|---|---|---|
| Penury | ||
| Abundance |
| Parameter | P2P-LiFi | C-LiFi | P2P-LiFi | C-WiFi |
|---|---|---|---|---|
| c | [0.125, 0.0625, 0.0416, 0.0312, 0.025] | [0.004, 0.002, 0.0013, 0.001, 0.0008] | ||
| [0.025, 0.0125, 0.0083, 0.00624, 0.005] | [0.0008, 0.0004, 0.00026, 0.0002, 0.00016] | |||
| File size | [8 Tb, 16 Tb, 24 Tb, 32 Tb, 40 Tl | |||
| Nodes | [4, 8, 12, 16, 20, 24, 28, 32, 36] | |||
| Max. upload | 4 per node | 4 per server | 4 per node | 4 per server |
| Max. download | 1 per node | Not applicable | 1 per node | Not applicable |
| Radio Coverage | Variable | Max. | Variable | Max. |
| Noises | Not considered | |||
| Bandwidth | Average Download Time (min) | |||||
|---|---|---|---|---|---|---|
| Down | Up | P2P | P2P | C-LiFi | P2P WiFi | C-WiFi |
| 1c | 1 | 1.20 | 1.00 | 0.95 | 29.84 | 30.37 |
| 2c | 2 | 2.39 | 1.99 | 1.93 | 59.96 | 60.97 |
| 3c | 3 | 3.61 | 2.97 | 2.90 | 91.45 | 93.70 |
| 4c | 4 | 4.79 | 3.99 | 3.87 | 120.70 | 121.22 |
| 5c | 5 | 6.02 | 5.04 | 4.80 | 150.13 | 150.57 |
| Bandwidth | Average Download Time (min) | |||||
|---|---|---|---|---|---|---|
| Down | Up | P2P- | P2P- | C-LiFi | P2P- WiFi | C-WiFi |
| 1c | 1 | 1.69 | 1.31 | 2.01 | 37.02 | 64.75 |
| 2c | 2 | 3.36 | 2.62 | 4.14 | 74.56 | 129.66 |
| 3c | 3 | 5.05 | 3.98 | 6.24 | 114.02 | 196.12 |
| 4c | 4 | 6.76 | 5.28 | 8.26 | 148.54 | 257.31 |
| 5c | 5 | 8.44 | 6.61 | 10.32 | 184.76 | 325.89 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hernández-Oregón, G.; Rivero-Angeles, M.E.; Chimal-Eguía, J.C.; Coyac-Torres, J.E. Performance Analysis of P2P Networks with Light Communication Links: The Static Managed Case. Appl. Sci. 2023, 13, 7906. https://doi.org/10.3390/app13137906
Hernández-Oregón G, Rivero-Angeles ME, Chimal-Eguía JC, Coyac-Torres JE. Performance Analysis of P2P Networks with Light Communication Links: The Static Managed Case. Applied Sciences. 2023; 13(13):7906. https://doi.org/10.3390/app13137906
Chicago/Turabian StyleHernández-Oregón, Gerardo, Mario E. Rivero-Angeles, Juan C. Chimal-Eguía, and Jorge E. Coyac-Torres. 2023. "Performance Analysis of P2P Networks with Light Communication Links: The Static Managed Case" Applied Sciences 13, no. 13: 7906. https://doi.org/10.3390/app13137906
APA StyleHernández-Oregón, G., Rivero-Angeles, M. E., Chimal-Eguía, J. C., & Coyac-Torres, J. E. (2023). Performance Analysis of P2P Networks with Light Communication Links: The Static Managed Case. Applied Sciences, 13(13), 7906. https://doi.org/10.3390/app13137906







