1. Introduction
The proliferation of the digital realm has given rise to a myriad of opportunities and advancements in various domains. However, this rapid expansion has also led to an increased vulnerability to cyber threats, making network security a critical concern in today’s interconnected world. Among the numerous cyber attacks, portscan attacks have garnered significant attention, as they pose a considerable risk to the integrity of both internal and external networks. Accurately identifying and classifying these attacks is of paramount importance in order to bolster our defenses against the evolving landscape of cyber threats.
In recent years, machine learning has emerged as a powerful tool for addressing complex classification problems in various fields, including network security. Several machine learning models have been employed to distinguish between normal and attack instances in network data. However, the quest for more accurate and efficient classification techniques remains ongoing.
This study presents an innovative approach to enhance the classification performance of machine learning models by integrating graph theory with network data analysis. By converting the network data into graph-based representations, we aim to uncover previously inaccessible insights and patterns, thereby improving the discriminative capabilities of machine learning algorithms.
Our primary contributions in this work are as follows:
We demonstrate the application of graph theory to network data, specifically focusing on port scan attacks both inside and outside networks.
We provide a comprehensive experimental analysis, encompassing data preprocessing, visualization, feature analysis, and machine learning model comparison, to assess the efficacy of graph theory representation in improving classification performance.
We highlight the modest yet meaningful improvement in accuracy achieved by incorporating graph theory representation in the analysis of network data.
This work not only represents a significant stride towards more robust and adaptive network security solutions, but also paves the way for future research endeavors to delve deeper into the intricate interplay between graph theory and network data analysis. By unearthing novel insights and refining classification processes, we move closer to the ultimate goal of creating a more secure and resilient digital landscape in the face of relentless cyber threats.
The remainder of this paper is organized as follows:
Section 2 delves into the related work, providing an overview of the existing research and techniques employed in the domain of network security and machine learning.
Section 3 presents our proposed approach, detailing the integration of graph theory with machine learning models to enhance classification performance. In
Section 4, we elaborate on the graph theory representation, outlining the methodology employed for converting network data into graph-based representations.
Section 5 describes the data used in this study, including its source, characteristics, and preprocessing steps.
Section 6 delves into the experiments and results, illustrating the efficacy of our approach in improving the classification performance of machine learning models. Finally,
Section 7 concludes the paper, summarizing our findings and outlining potential avenues for future research.
2. Related Work
Wide deployment of IoT networks would be hindered without addressing effective support of IoT security and establishing firm resilience against IoT attacks. Effective immunization of IoT systems requires reliable detection of malicious activities at early stages. Therefore, the development of intrusion detection systems (IDSs) towards securing IoT systems becomes critical. IDSs enables the detection of abnormal actions and system abuses by monitoring IoT network traffic and observing user activities. A wide range of IDSs have been introduced in the literature towards effective security support of IoT systems.
2.1. Integrated ML Approaches
Shafiq et al. [
1] used machine learning technique for the development of a security approach to prevent bot attacks over IoT networks. A novel security framework assisted with a hybrid algorithm was proposed to secure the network from malicious and anomaly traffic. Shafic et al. [
2] proposed a malicious bot detection method based on machine learning for IoT networks. They introduced CorrAUC, which is a novel approach developed with a feature selection method using refined and effective features. The performance results of the proposed model showed its efficiency and a high accuracy level of up to 96%. Pokhrel et al. [
3] utilized a KNN and NB classifiers in addition to a MLP ANN to develop a model for botnet detection for IoT networks using the Bot-IoT dataset.
Popoola et al. [
4] designed and developed a hybrid deep learning approach to identify bot attacks in IoT networks. LAE was applied for achieving dimensionality reduction. In addition, Bot-IoT dataset was used to validate the effectiveness of the proposed model. Alothman et al. [
5] presented a novel machine-learning-based approach with the SMOTE technique to prevent botnet attacks. The proposed model incorporated random forest and multilayer perceptron and utilized the Bot-IoT dataset. Asadi et al. [
6] proposed a botnet detection approach based on LSTM, SVM, and Autoencoder for enabling fast and reliable botnet traffic identification. It also applies game theory of cooperative combination. Qiao et al. [
7] presented how the concept drift analysis based on dynamic residual projection can prevent botnet attacks. Using a subdataset of the Bot-IoT dataset, the proposed approach was able to achieve superior performance.
2.2. Integrated DL Approaches
Apostol et al. [
8] proposed an unsupervised deep learning approach for bot anomaly detection using deep autoencoders. By comparing it with different unsupervised techniques, the experimental results indicate the efficiency of the proposed approach. Popoola et al. [
9] developed another deep-learning-based botnet detection algorithm by which highly imbalanced traffic data can be handled. It incorporates SMOTE (synthetic minority oversampling technique) for effective class balance. Shobana et al. [
10] proposed a novel approach that can help in identifying botnet attacks using balanced network traffic.
Deep learning models are very efficient in feature selection and classification. Koroniotis et al. [
11] designed a deep-learning-based forensic framework that applies particle swarm optimization (PSO) for optimized learning. It enables tracking and identifying attack behaviors based on multiple digital investigation phases. Ge et al. [
12] introduced the development of binary and multiclass deep-learning-based classifiers that apply a feed-forward neural network model of multiple embedding layers. The evaluation results showed that both binary and multiclass classifications achieved high detection accuracy levels. Ullah et al. [
13] designed and developed a deep-learning-based system to identify the presence of anomalies in IoT networks. Convolutional neural network was utilized to build a transfer learning model for multiclass classification considering a wide range of IoT attacks in addition to binary classification. The model was validated with different intrusion detection datasets and showed a high detection rate.
Baig et al. [
14] proposed an intelligent framework for DoS attack detection that enables feature generation and ranking in addition to data generation. The proposed model was tested under realistic scenario and the results indicated higher accuracy compared with traditional approaches. Kumar et al. [
15] designed a distributed framework to identify DDoS attacks when leveraging fog computing in blockchain-IoT applications. It relies on RF and XGBoost techniques to enable decision making with full autonomy. Papadopoulos et al. [
16] proposed a methodology on adversarial attack for intrusion detection system. The proposed methodology comprises of two approaches, where the first one is label poisoning and the second one is fast gradient sign method.
Nimbalkar et al. [
17] proposed a feature selection method to identify intrusions in IoT networks. Information gain and gain ratio were utilized for ranking the top 50% features to detect DoS and DDoS attacks with better performance. Koroniotis et al. [
11] proposed particle deep framework on network forensics with deep learning and particle swarm optimization. Derhab et al. [
18] developed a deep-learning-based framework to detect intrusions using a combination of CNN and casual combination. Compared with other learning-based frameworks, higher detection accuracy was achieved by the proposed framework during testing on the Bot-IoT dataset. ULLAH et al. [
19] presented a deep-learning-based approach based on CNN model and a gated recurrent network for anomaly detection in IoT networks. It supported both binary and multiclass classification. The results illustrated the ability of the proposed model to achieve high accuracy, precision, F1 score, and recall values.
2.3. Graph-Based Approaches
Islam et al. [
20] proposed a graph-based four-stages intrusion detection system using a chi-squared method. The proposed system was able to detect strong and weak cyber attacks with better performance than similar systems. In [
21], two techniques for identifying unusual patterns in graph-based data are defined. Using the ideas of entropy and conditional entropy, they also created two metrics for determining a graph’s regularity. In addition, applying the graph neural network (GNN) was considered by different research works. In [
22], a multiagent system implemented based on GNN was proposed. The main objective was to develop a collaborative and cooperative agents for distributed anomaly detection in IoT in [
23], a GNN-based approach for IoT network intrusion detection using flow-based data was proposed. It was based on capturing edge features in addition to topological patterns of a network flow graph.
2.4. Other IDS Approaches
Alkadi et al. [
24] proposed a framework based on blockchain for intrusion detection in cloud networks and IoT systems. It facilitates secured data migration in a reliable manner by acting as a decision support system to the users. Sudheera et al. [
25] proposed a novel technique for correlated attack stage identification in IoT networks. A distributed framework named ‘Adept’ was introduced for improving the detection of individual attacks in a precise manner.
Albulayhi et al. [
26] proposed several approaches to prevent cyber attacks and detect anomaly. An improved anomaly detection approach was developed by incorporating the one class support vector machine (OC-SVM). Aldhaheri et al. [
27] suggested a network-based novel approach to identify attacks with artificial immune system. A hybrid deep learning and DeepDCA algorithm were combined for developing an IDS framework. It utilized the IoT-Bot dataset and enabled the selection of a set of convenient features. Nwafor et al. [
28] introduced an IDS approach which relies on provenance graphs for the detection of anomalous IoT data. Samdekar et al. [
29] developed an experimental setup to improve the performance of intrusion detection in IoT devices using machine learning classifiers. The main aim of the study was to identify the behaviour and anomalies in IoT networks.
Soe et al. [
30] proposed a lightweight machine learning technique-based intrusion detection approach for preventing cyber attacks. A new feature selection algorithm (CST-GR) was developed to limit the selected features to those really necessary. Pant et al. [
31] developed a novel machine learning based approach for identifying malicious and anomaly data in IoE. DL and WGBoost with PSO were used to explore the individual proposed ML (machine learning) algorithms. Ferrag et al. [
32] developed an intrusion detection system for an IoT network based on rule-based concepts and decision tree. The experimental result of the proposed IDS showed a decent performance in terms of detection rate, time overhead, false alarm detection, and accuracy.
Zixu et al. [
33] proposed an auto-encoder- and GAN-based approach for anomaly detection that addresses the privacy preservation and data aggression. The proposed unsupervised hierarchical approach offered high accuracy with high impact, as shown by the evaluation results. Kumar et al. [
34] proposed an intelligent cyber attack detection approach, where different learning algorithms, such as K-means, XGBoost, and random forest were used for preventing IoT attacks. Huong et al. [
35] presented an edge-cloud architecture, which implemented LocKedge, a detection mechanism of multiattacks. The detection functionality is performed at the edge layer, which enabled the system to provide a quick response to the attacks.
3. Proposed Approach
In this section, we present our proposed method for enhancing the classification performance of machine learning models in the context of network data analysis, specifically focusing on port scan attacks both inside and outside networks. By integrating graph theory representation with machine learning algorithms, we aim to uncover previously inaccessible insights and patterns, thereby improving the discriminative capabilities of these models. The proposed method comprises the key steps that are summarized in
Figure 1.
Data preprocessing is a crucial step in ensuring that the raw network data are transformed into a suitable format for analysis. This process typically involves handling missing values, outliers, and noise, as well as standardizing the range of the input features. In our approach, we employ various scaling techniques, such as minimal scaling, robust scaling, and standard scaling, to standardize the data and ensure that the machine learning models can effectively analyze and classify the instances. Next, to incorporate graph theory into the analysis of network data, we convert the preprocessed data into graph-based representations. This process involves constructing graphs that capture the underlying structure and relationships within the network data. Nodes in the graph represent individual instances, while edges signify the relationships between them. We explore different graph construction techniques, such as adjacency matrices and distance-based methods, to identify the most suitable representation for the given dataset.
Once the graph-based representations have been created, we proceed with feature extraction and dimensionality reduction. This step aims to identify and extract the most informative features from the graph representations, while reducing the complexity and computational cost of the subsequent machine learning algorithms. We employ techniques such as principal component analysis (PCA) to transform the high-dimensional graph-based data into a lower-dimensional space, preserving the most critical features and patterns. Following this, with the graph-based representations and extracted features in hand, we apply various machine learning models to classify the network data instances as either normal or attack. In our approach, we experiment with logistic regression, support vector machines (SVM), and K-means clustering, assessing their performance in terms of accuracy. By comparing the classification performance of these models before and after applying graph theory representation, we can evaluate the efficacy of our proposed method in improving their discriminative capabilities. There are many advantages to integrating graph theory representation with machine learning algorithms. The network data generated in heterogeneous environments, such as the IIoT environment, are enormous by nature. This kind of environment has the potential for malicious traffic to be hidden within the normal ones and remain undetected, especially if it is minimal, such as one connection. In the proposed graph-based methodology, the network traffic is represented, and as few connections as possible are captured. This connection can be an attack such as stealthy attack, which is known to be a hard attack to be detected and classified. An advantage of the proposed methodology is its improvement of ML, which is able to detect this type of attack and classify it, as is proven by the experiments results. On the other hand, there are some limitations with the proposed approach. For example, data preprocessing is a crucial step in ensuring that the raw network data are transformed into a suitable format for converting the data into graph-based representations, and therefore, any error occurring at this stage negatively affects the representation of the data in the graph. Moreover, zero padding that is performed to help preserve the length of network traffic when building an adjacency matrix negatively can lead to a higher computational cost.
4. Graph Theory Representation
Given the significance of graph theory in several domains and its practical application in modeling and solving problems, several researchers have devoted time and effort to explore and advance the ideas in this subject [
36,
37,
38]. A graph theory technique can help in identifying the IoT device’s behaviour and attack pattern. Here, we employ the adjacency matrices of a graph, a powerful method for analyzing network structure and a useful approach to representing the topology of networks. Building a star network of IoT devices has the advantage of allowing us to thoroughly validate the characteristics of the predicted behavior. To demonstrate that either external or internal attackers are port scanning, we model the provided sending and receiving packets on a start graph by using Matlab simulation. The star graph consists of N-1 nodes connected to a central node, through which we can visualise the flow of data to and from the attacking or target nodes. There are two distinct situations to consider: the case in which the attacked node is the central one, and the case in which the attacked node is one of the external nodes. We say that a targeted node with the specified destination host IP address and destination port (dstIP, dstPort) is compromised if there are several nodes with the same source IP address but different source ports (srcIP, srcPort) that are exploiting the open ports to carry out the malicious actions; this type of attack is known as an external port scanning attack, as shown in
Figure 2. On the other hand, an internal port scanning attack is present when the specified source host IP address and the same port target the specific destination host IP address and any port, as shown in
Figure 3.
To convert the preprocessed data into graph-based representation, each traffic flow is composed of the primary futures srcIP, srcPort, dstIP, and dstPort, where a node in the graph represents two values (srcIP, srcPort), from which one edge leads to the other node, which also represents two values (dstIP, dstPort), as shown in
Figure 2 and
Figure 3. To illustrate how graph theory applies to network data, we assume that an attacker performs an internal port scan, where it sends a large number of packets from the same srcIP and srcPort to the target node with the same dstIP but various ports. Here, we indicate that each packet going from the malicious node, also known as the source node, to the target node (i.e., sink node) is represented by an edge. As a result, a sink node has an indegree of at most 1 but zero outdegree, while a source node has a number of outgoing edges but zero indegree, meaning that an attacker performs an internal port scan (see
Figure 3). On the other hand, external port scanning is distinct from the preceding situation in that the attacking node launches its attacks from the same srcIP but with different ports towards the target node with the same srcIP and srcPort. In this scenario, the source node, where the number of outdegrees does not exceed 1 and the incoming edges are zero, becomes the one that attacks, while the target node receives a number of incoming edges but zero outdegrees (see
Figure 2).
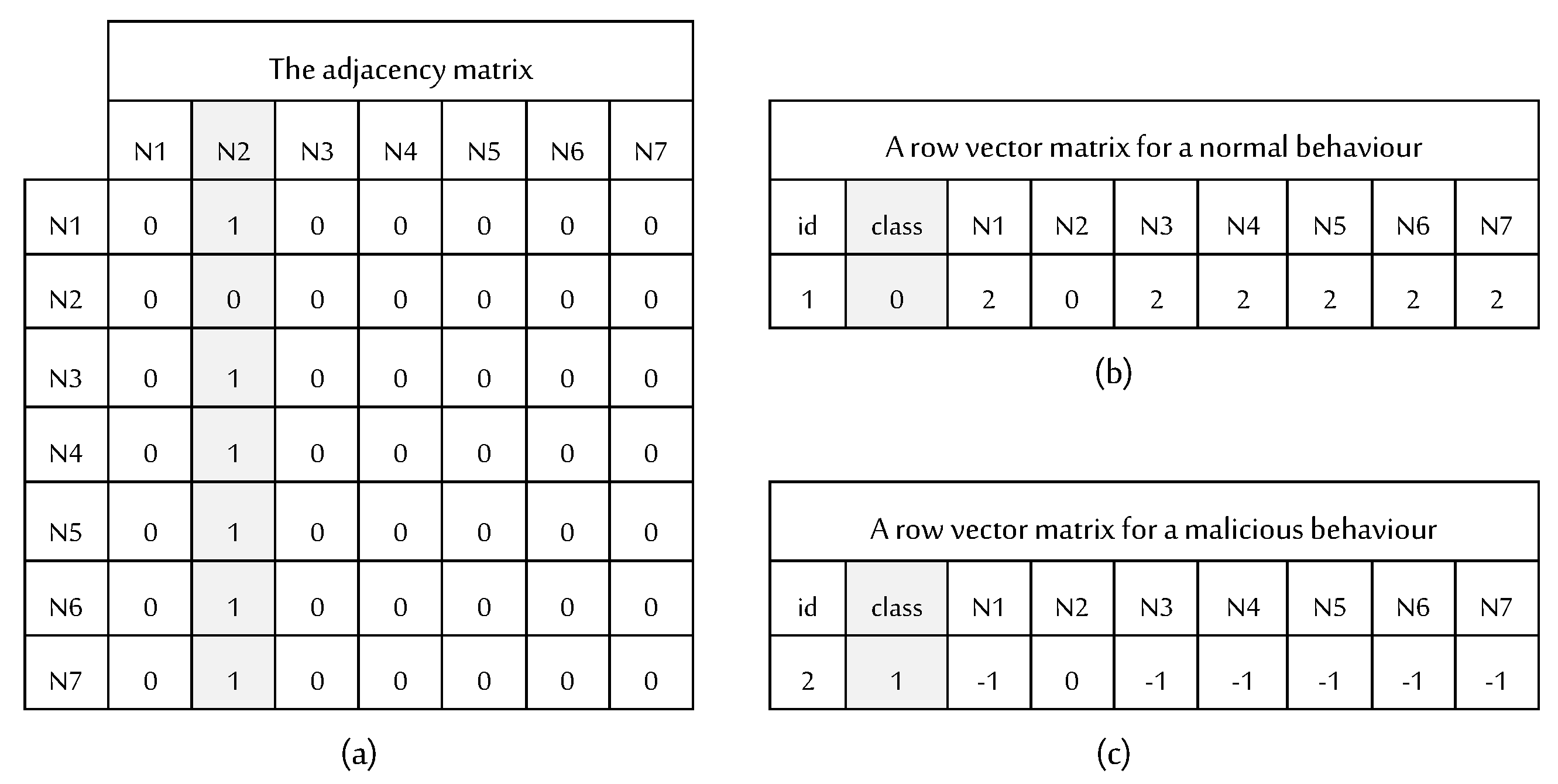
Once the model is deployed and a star graph depicting the sending and receiving of packets is built, an adjacency matrix is used to represent the star graph as a matrix. An adjacency matrix () is a matrix that contains rows and columns used to represent a simple labelled graph with the numbers 0, 1 in the position of (,), according to the condition of whether or not the two and are adjacent such that its element is one when there is an edge from vertex to vertex , and zero when there is no edge. As a star graph is considered a network traffic, we employed differently labeled entries to distinguish between normal and abnormal behaviour while representing the adjacency matrix of a certain star graph. Based on the data collected from the preprocessed data, if the network traffic class is normal, the adjacency matrix entries of the star network topology are 2 s; otherwise, they are −1 s. As a result, the adjacency matrix is created by specifying the direction of the in/out edges between the nodes, and any zero entries are then removed to convert the matrix into a row vector, which is shown as:
The first element of each row refers to an identifier.
The second element is the traffic flow behaviour type, which is represented by a zero for normal behaviour or a one for malicious behavior.
If the scenario is an external port scan, then the remaining elements in the row represent the direction of outgoing edges from the malicious nodes with the same srcIP but different srcPort to the targeted node with the same dstIP and dstPort, see
Figure 4.
If an attacker performs an internal port scanning, then the third element in a row shows the number of outgoing edges, and therefore, the remaining elements in the row represent the direction of outgoing edges from the central malicious node with the same srcIP and srcPort to the targeted nodes with the same dstIP but different dstPort, see
Figure 5.
When a given network traffic is abnormal, the entries of the matrix are labeled with −1; otherwise, they are labeled with 2.
5. Data
In light of the compelling diversity found in its collection environment, paralleling the complexity inherent in the Internet of Things (IoT) milieu, this study employs the ISOT Cloud Intrusion Detection Dataset (ISOT-CID) for IIoT data.
The distinguished ISOT Cloud Intrusion Detection Dataset, as expounded by Aldribi et al. [
39,
40], is a richly diverse assemblage of data accrued in two separate stages. This data repository embodies a wide spectrum of cloud strata, such as guest hosts, hypervisors, and networks, embodying an array of data types culled from a variety of sources. These sources comprise system logs, resource (for instance, CPU) utilizations, network traffic, system call traces, and memory dumps. It accommodates traces of an array of attacks, including masquerade, denial of service, stealth operations, irregular user actions, and both external and internal data assaults. The principal aim of assembling this dataset was to foster the creation and appraisal of an extensive variety of intrusion detection system (IDS) models. The dataset is methodically categorized, embracing a fusion of both normal and malevolent activities.
As referenced earlier, the ISOT-CID dataset enfolds a wide array of attacks recognized as principal threats in the sphere of cloud computing. These onslaughts, which transpired across both the application and network layers, sprouted from both within and outside the cloud. They encompass key categories such as breaches of authentication, denial of service (DOS), backdoors, remote-to-local (R2L), input validation, probing, and information disclosure.
Considering the primary focus of this study is on the IoT network, the network traffic of the ISOT-CID dataset was conscientiously chosen for evaluating the proposed methodologies. The dataset integrates three distinctive network flows: local traffic, internal, and external. The external signifies the communication between the virtual machine and an external machine (referred to as “instance-outside” traffic). The internal traffic represents the interaction between one computation unit and another, denoted as “hypervisor-hypervisor” traffic, while the local traffic stands for the exchange of information between two instances situated on an identical compute node, which is termed as “instance-instance” traffic. The network traffic encapsulates a sum total of 22,372,418 network packets for the initial phase, out of which 22,356,769 packets are harmless, with 15,649 deemed harmful. In the second phase, the dataset subsumes an aggregate of 11,509,254 network packets, with 9,502,872 packets being innocuous and 2,006,382 identified as harmful.
For the sake of simplicity and to facilitate the implementation of the proposed solution, only a subset of the data features was considered. These included those indicative of the primary network properties of the flows, such as the IP addresses and port numbers of flow source and destination, along with the type of the communication protocol. Additionally, the time and date marking the start and end of the flow burst were included, as well as the total number of transmitted and received data packets. Each instance of the dataset is labeled with a value representing its class.
6. Experiments and Results
In this section, we present an in-depth description of the experiments conducted to assess the effectiveness of applying graph theory on network data (port scan attacks, both inside and outside) for enhancing the classification performance of machine learning models. The experimental procedure consists of several subsections, covering data preprocessing, visualization, feature analysis, machine learning model comparison, and discussion of the results.
6.1. Data Preprocessing and Visualization
Before applying the machine learning models on the dataset, we performed data preprocessing to ensure that the data was in a suitable format for analysis. Data preprocessing involved cleaning the dataset by removing any inconsistencies or missing values, encoding categorical variables, and scaling the numerical features. Scaling was a critical step, as it helped normalize the range of the input features and improved the performance of the machine learning models.
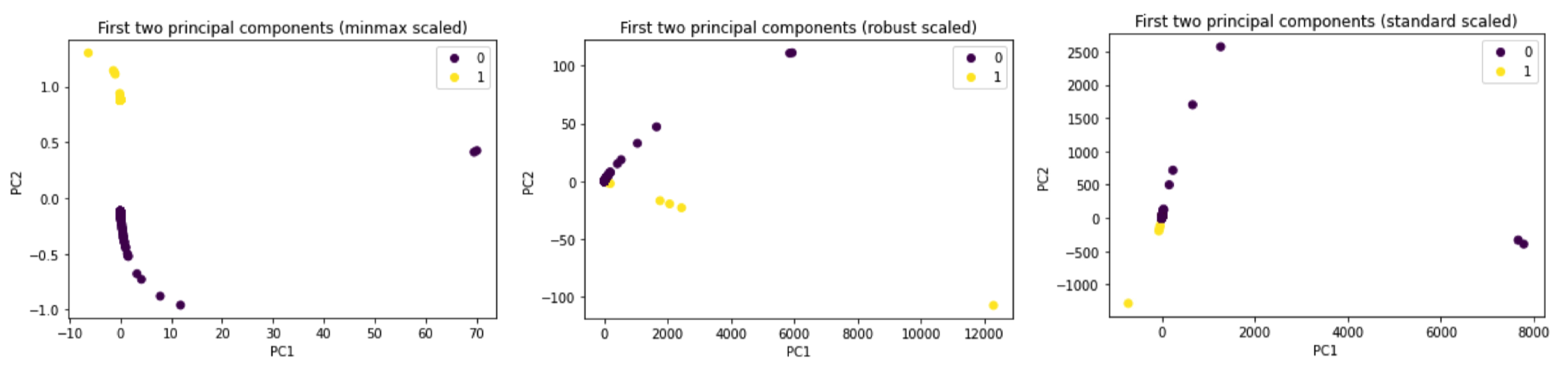
To visualize the dataset and identify patterns, we employed principal component analysis (PCA) after scaling the data, as shown in
Figure 6. PCA is a widely used dimensionality reduction technique that transforms a dataset into a new coordinate system by projecting it onto a lower-dimensional space. We experimented with three different scaling methods: minimal scaling, robust scaling, and standard scaling. Each scaling method has its advantages and is suitable for different types of data distributions.
Minimal scaling is appropriate for datasets with minimal noise and minimal outliers, as it scales the features based on the minimum and maximum values of each feature. Robust scaling is suitable for datasets with a significant number of outliers, as it utilizes the interquartile range to scale the features. Standard scaling is applicable for datasets that follow a Gaussian distribution, as it scales the features based on their mean and standard deviation.
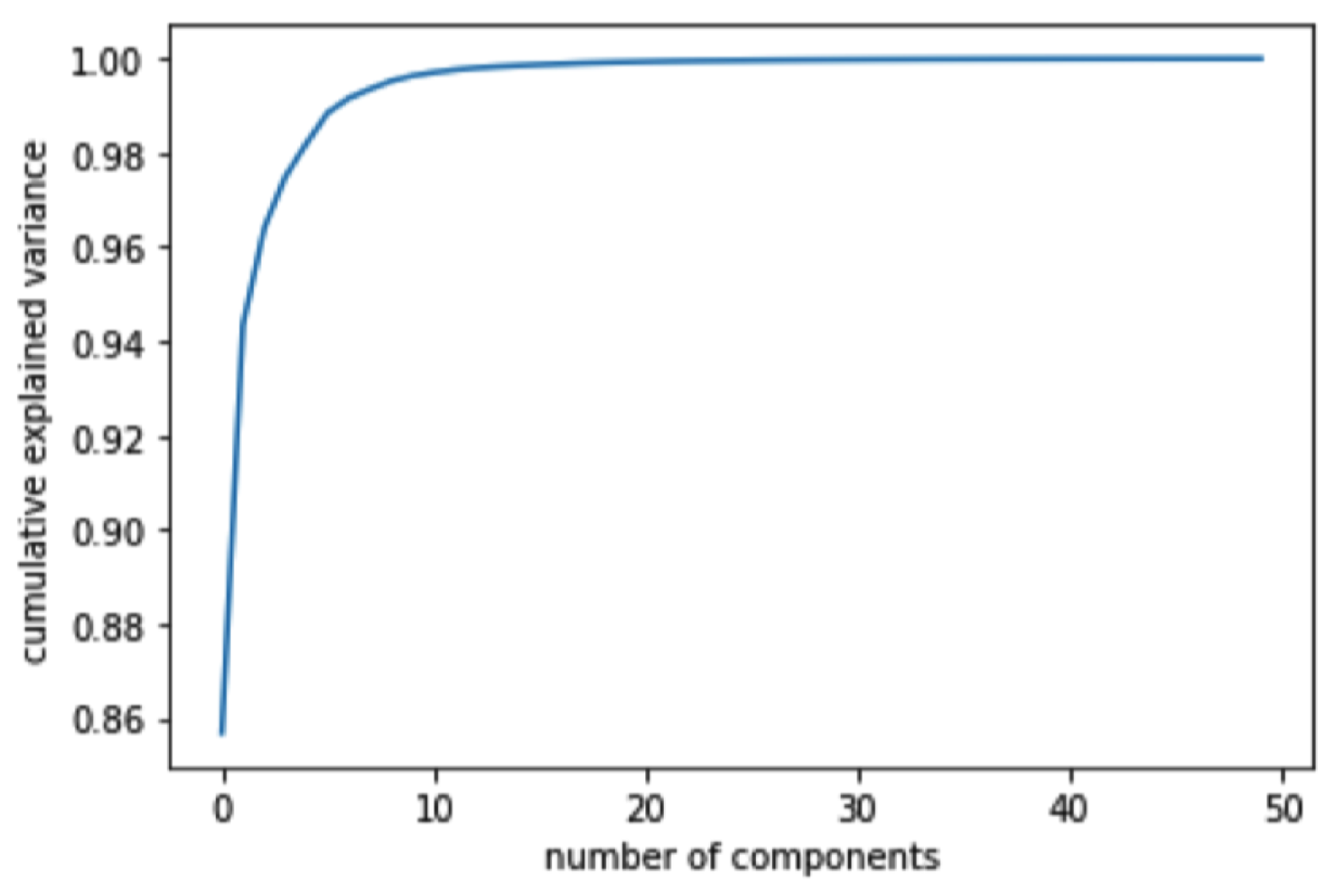
PCA was applied to reduce the dimensionality of the dataset while retaining the most critical features. The first two principal components were plotted (
Figure 7) to visualize the data distribution after applying each scaling technique. This allowed us to identify the components that best described the data (
Figure 8) and provided valuable insights into the underlying structure of the dataset. By comparing the different scaling methods, we could determine which method was the most effective for our dataset.
6.2. Feature Analysis before Graph Theory Representation
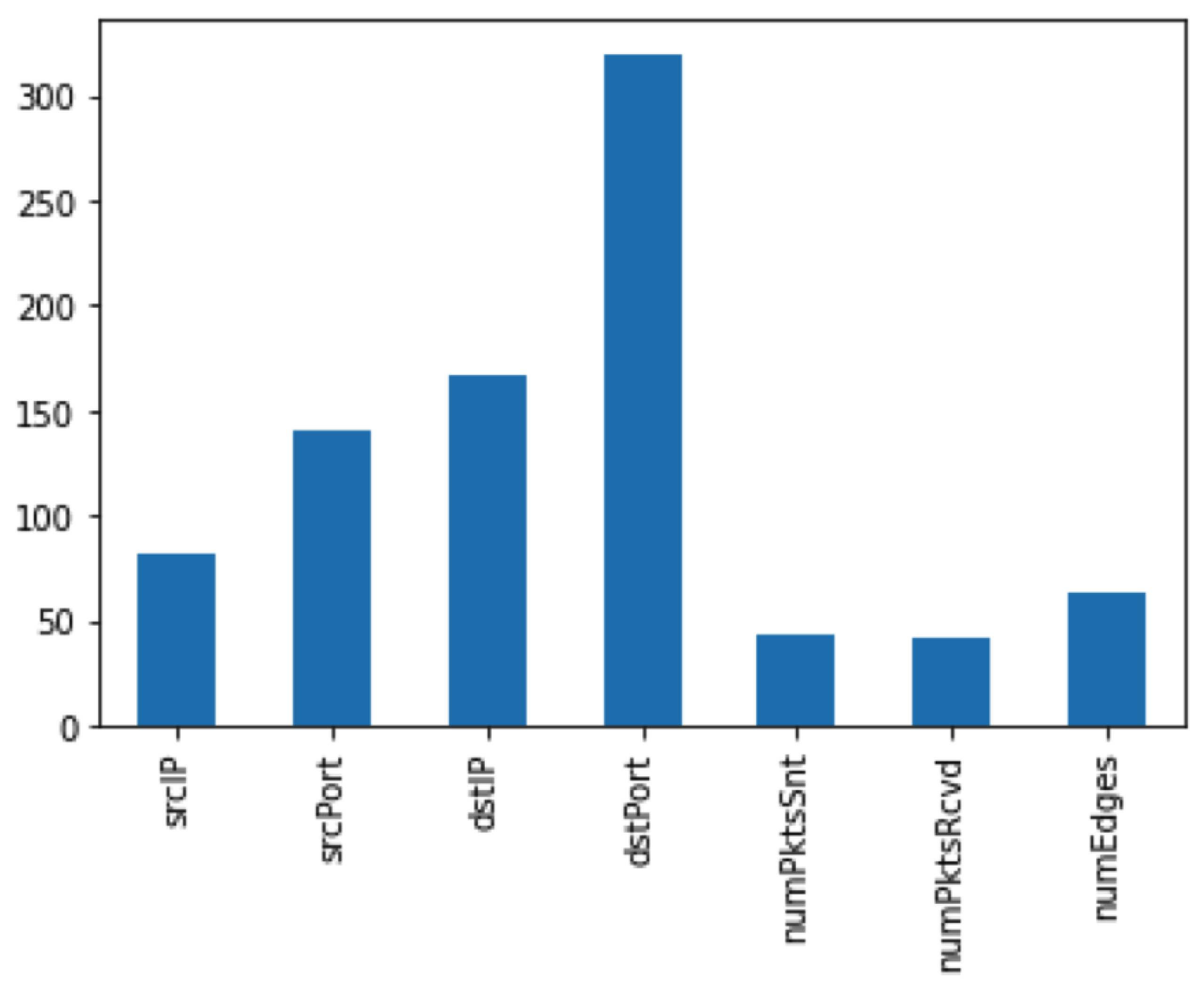
We further analyzed the dataset before applying graph theory representation. We generated a figure illustrating the count of unique values for each training feature (
Figure 9). This enabled us to identify potential patterns and gain a better understanding of the dataset’s characteristics. By examining the distribution of unique values, we could determine which features were more informative for the classification task and which features might require additional processing or transformation. Upon examining the distribution of unique values as demonstrated in
Figure 9, we observed distinct distributions of unique values among the features. Some features exhibited a wide range of unique values, indicating their potential informativeness in the classification task. These features may possess discriminative power, enabling them to contribute significantly to the classification model’s performance. On the other hand, certain features displayed a limited range of unique values or a concentrated distribution within a specific range, suggesting a potential need for additional processing or transformation.
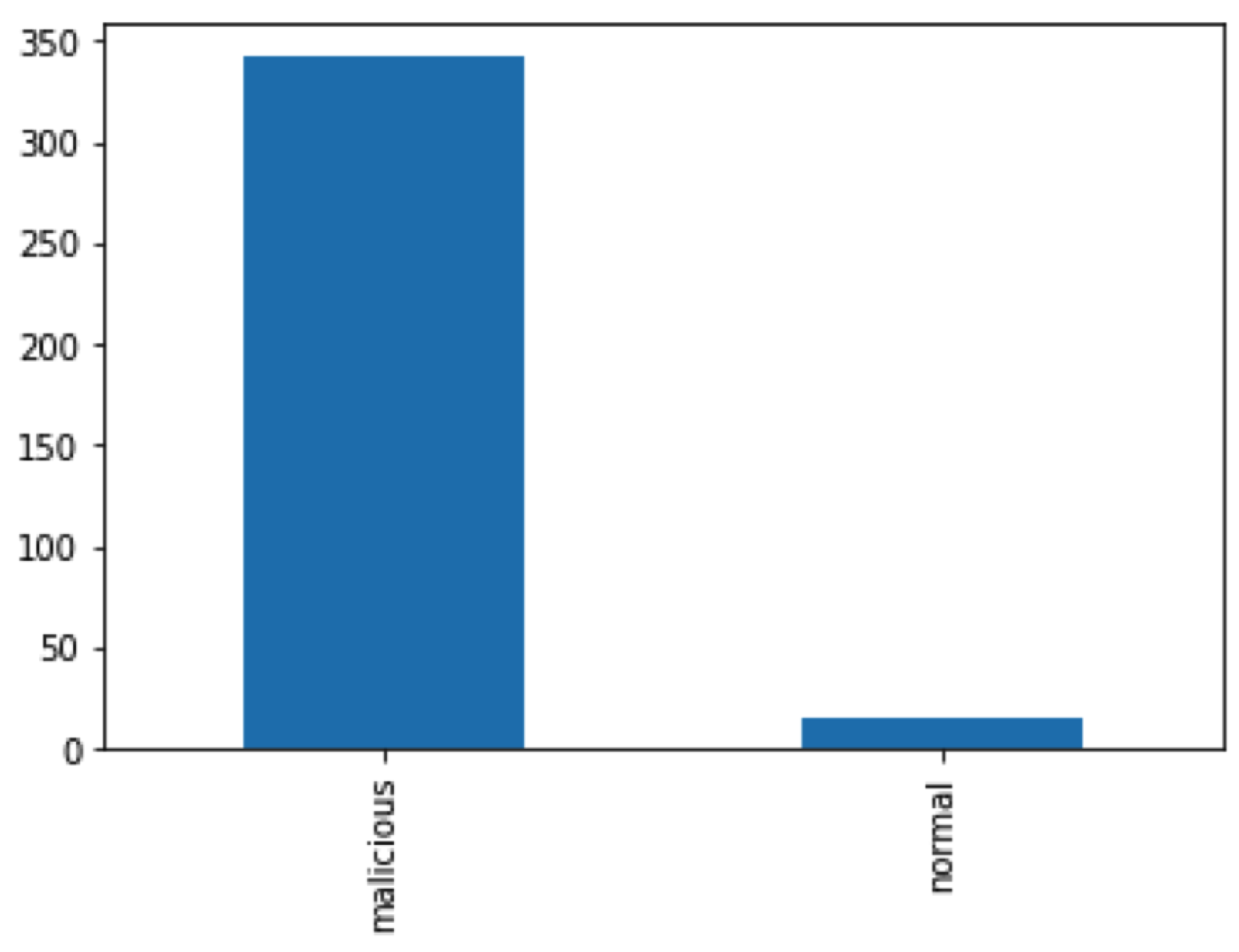
In addition, we investigated the distribution of classes in the dataset.
Figure 10 illustrates the distribution of class frequencies, offering valuable insights into the composition of our dataset. By closely examining the plot, we identified potential class imbalances, where certain classes were overrepresented or underrepresented compared to others. This observation raised concerns regarding the fairness and effectiveness of our models in predicting minority classes or achieving accurate predictions across all classes. Understanding the implications of class imbalance, we recognized the need to address this issue proactively. To mitigate the adverse effects of class imbalance on our models, we considered several techniques, including oversampling, undersampling, and synthetic data generation.
6.3. Machine Learning Model Comparison
We experimented with several machine learning models, including logistic regression, support vector machines (SVM), and K-means clustering, to evaluate their classification performance on the dataset and, in particular, their ability to accurately identify and classify portscan attacks (normal or malicious, a binary classification). We compared the performance of these models before and after applying graph theory representation. SVM is a well-known supervised machine learning algorithm used for classification tasks, which identifies the optimal hyperplane separating different classes. Similarly, logistic regression is a statistical model used in machine learning for binary classification problems (which is the case in our study), predicting the probability of a certain class, whereas K-means is an unsupervised machine learning algorithm used for clustering, partitioning a dataset into ’K’ different clusters based on feature similarity, where in our case, given the two classes.
The machine learning models were implemented using standard parameters commonly used within the community. For logistic regression, we used L2 regularization with a default C value of 1.0. For SVM, we employed a radial basis function (RBF) kernel with a gamma value of ’scale’ and a C value of 1.0. Lastly, the K-means clustering algorithm was applied with the number of clusters set to the number of unique classes in the dataset, employing the K-means++ initialization method.
6.4. Results
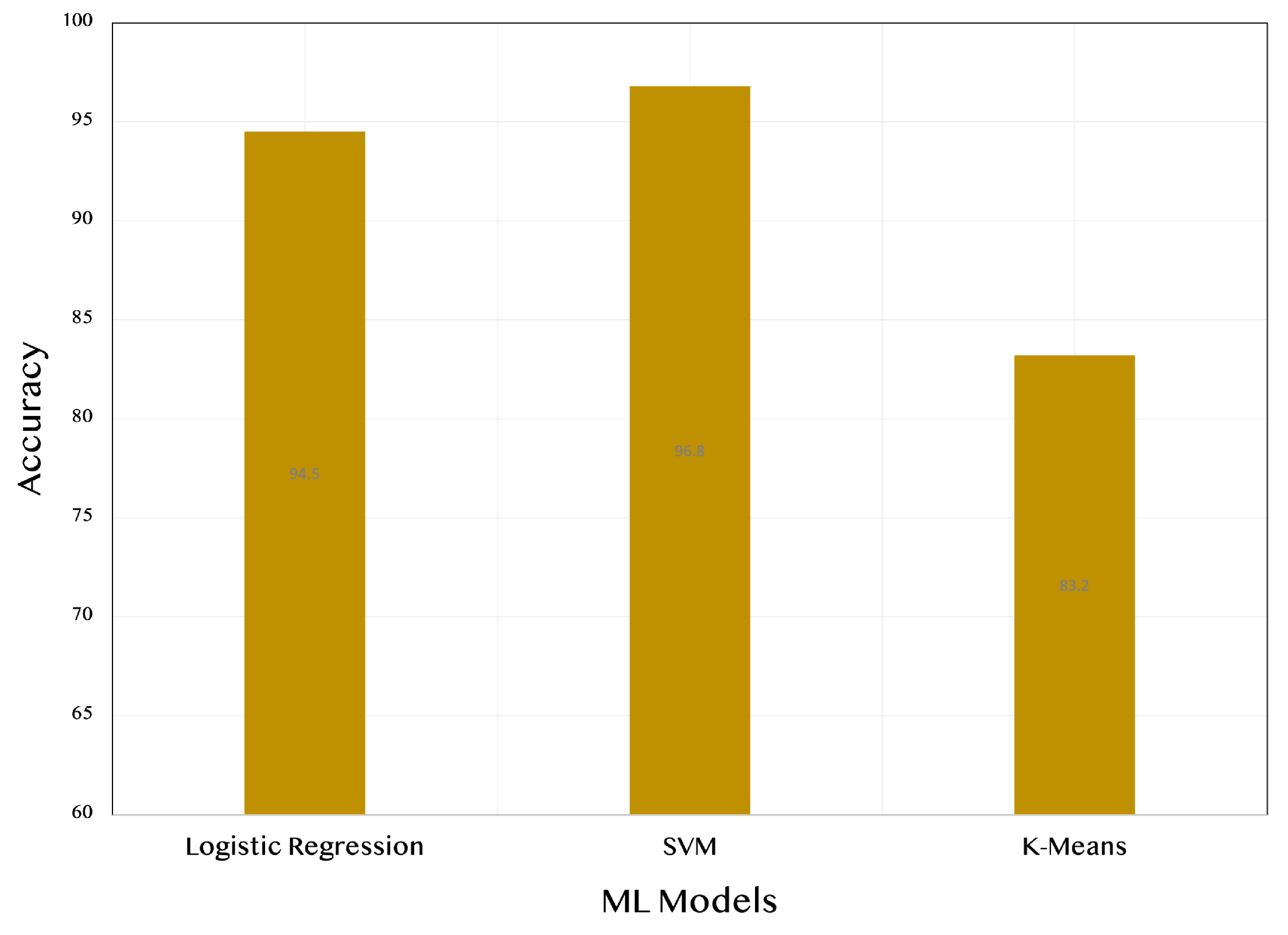
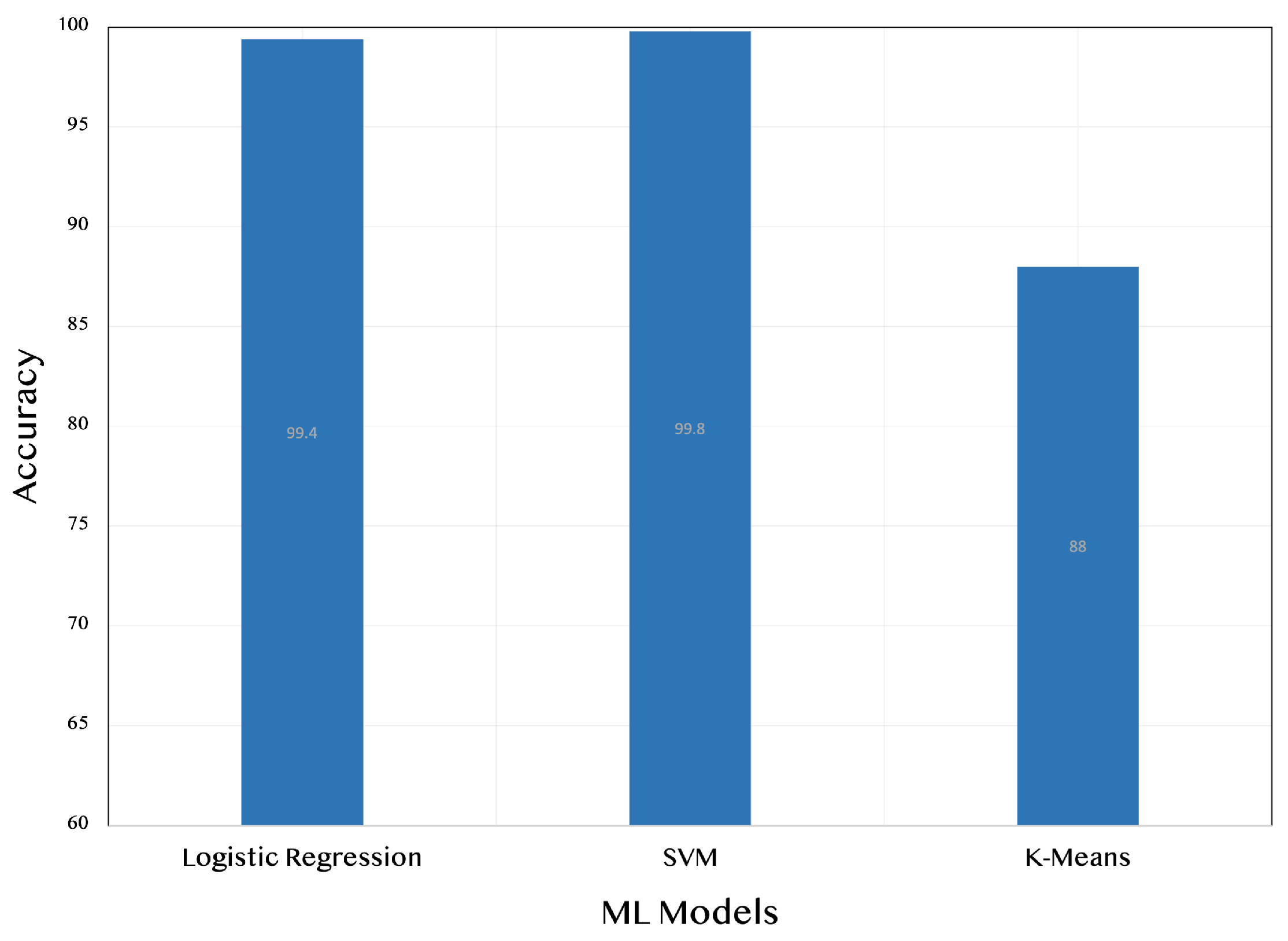
Upon comparing the classification performance of the machine learning models before and after applying graph theory representation, we observed a modest yet important improvement in the models’ accuracy. Although the improvement was not dramatic, it still showcased the potential of incorporating graph theory into the analysis of network data to enhance the ability of machine learning models to distinguish between normal and attack instances.
To visualize the improvement,
Figure 11 and
Figure 12 display the classification performance metrics before and after applying graph theory representation. The first figure illustrates the performance metrics of the logistic regression, SVM, and K-means models without graph theory representation. In contrast, the second figure shows the enhanced performance metrics achieved after incorporating graph theory into the analysis. These figures clearly demonstrate the improvement in classification accuracy, highlighting the significance of graph theory representation in the context of network data analysis. In fact, the utilization of graph theory representation enhances the accuracy of classification between normal and malicious attacks (
Figure 12) compared to the approach without graph theory representation (
Figure 11). This improvement is evident. By incorporating graph theory, we were able to capture the underlying network structure and the relationships between network entities more effectively. This enriched representation facilitated the discovery of critical patterns and features that are instrumental in distinguishing normal network behaviour from malicious attacks.
7. Conclusions and Future Directions
In conclusion, our comprehensive experimental analysis sheds light on the promising potential of integrating graph theory with network data analysis (portscan attacks both inside and outside) for bolstering the classification performance of machine learning models. Although the observed improvement in accuracy was not remarkably substantial, nonetheless, it underscores the importance and relevance of graph theory representation in enhancing the discriminative capabilities of machine learning algorithms when applied to network data.
As we move forward in the field of network security, it is crucial to keep exploring approaches against cyber threats. This study is a step in this direction, as we explore the use of graph theory in classifying network data. In the future, we can delve deeper into different ways to prepare the data, extract important features, and use machine learning techniques. This will help us improve the classification process even more, leading to better performance and new insights into how graph theory and network data analysis interact. Additionally, we can study how different methods of representing graphs affect the performance of machine learning models. This will help us find the most effective strategies to accurately and efficiently distinguish between normal and attack data in networks.
Author Contributions
Conceptualization, B.A., M.A. (Mohammed Alsuhaibani) and I.S.A.; methodology, B.A., M.A. (Mohammed Alsuhaibani), and I.S.A.; software, B.A. and M.A. (Mohammed Alsuhaibani); validation, B.A., M.A. (Mohammed Alreshoodi), I.S.A., A.A. and M.A. (Mohammed Alsuhaibani); formal analysis, B.A., M.A. (Mohammed Alreshoodi) I.S.A., A.A. and M.A. (Mohammed Alsuhaibani); investigation, B.A., M.A. (Mohammed Alreshoodi), I.S.A., A.A. and M.A. (Mohammed Alsuhaibani); resources, A.A.; data curation, B.A., M.A. (Mohammed Alsuhaibani), I.S.A. and A.A.; writing—original draft preparation, B.A., M.A. (Mohammed Alreshoodi), I.S.A., A.A. and M.A. (Mohammed Alsuhaibani); writing—review and editing, B.A., M.A. (Mohammed Alreshoodi), I.S.A., A.A. and M.A. (Mohammed Alsuhaibani); visualization, B.A. and M.A. (Mohammed Alsuhaibani); supervision, B.A. and M.A. (Mohammed Alreshoodi); project administration, B.A. and M.A.(Mohammed Alreshoodi). All authors have read and agreed to the published version of the manuscript.
Funding
The authors would like to thank the research chair of Prince Faisal for Artificial Intelligence (CPFAI) for supporting this research work.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to thanks the Chair of Prince Faisal for Artificial intelligence research (CPFAI) for funding this research work through the project number QU-CPFAI-2-7-3. Furthermore, the authors would like to extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education and the Deanship of Scientific Research, Qassim University for their support for this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A malicious bot-IoT traffic detection method in IoT network using machine-learning techniques. IEEE Internet Things J. 2020, 8, 3242–3254. [Google Scholar] [CrossRef]
- Pokhrel, S.; Abbas, R.; Aryal, B. IoT security: Botnet detection in IoT using machine learning. arXiv 2021, arXiv:2104.02231. [Google Scholar]
- Popoola, S.I.; Adebisi, B.; Hammoudeh, M.; Gui, G.; Gacanin, H. Hybrid deep learning for botnet attack detection in the internet-of-things networks. IEEE Internet Things J. 2020, 8, 4944–4956. [Google Scholar] [CrossRef]
- Alothman, Z.; Alkasassbeh, M.; Al-Haj Baddar, S. An efficient approach to detect IoT botnet attacks using machine learning. J. High Speed Netw. 2020, 26, 241–254. [Google Scholar] [CrossRef]
- Asadi, M. Detecting IoT botnets based on the combination of cooperative game theory with deep and machine learning approaches. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 5547–5561. [Google Scholar] [CrossRef]
- Qiao, H.; Novikov, B.; Blech, J.O. Concept Drift Analysis by Dynamic Residual Projection for effectively Detecting Botnet Cyber-attacks in IoT scenarios. IEEE Trans. Ind. Inform. 2021, 18, 3692–3701. [Google Scholar] [CrossRef]
- Apostol, I.; Preda, M.; Nila, C.; Bica, I. IoT botnet anomaly detection using unsupervised deep learning. Electronics 2021, 10, 1876. [Google Scholar] [CrossRef]
- Popoola, S.I.; Adebisi, B.; Ande, R.; Hammoudeh, M.; Anoh, K.; Atayero, A.A. smote-drnn: A deep learning algorithm for botnet detection in the internet-of-things networks. Sensors 2021, 21, 2985. [Google Scholar] [CrossRef]
- Shobana, M.; Poonkuzhali, S. A Novel Approach for Detecting IoT Botnet Using Balanced Network Traffic Attributes. In Proceedings of the Service-Oriented Computing–ICSOC 2020 Workshops: AIOps, CFTIC, STRAPS, AI-PA, AI-IOTS, and Satellite Events, Dubai, United Arab Emirates, 14–17 December 2020; Springer: Cham, Switzerland, 2021; pp. 534–548. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E. A new network forensic framework based on deep learning for Internet of Things networks: A particle deep framework. Future Gener. Comput. Syst. 2020, 110, 91–106. [Google Scholar] [CrossRef]
- Ge, M.; Syed, N.F.; Fu, X.; Baig, Z.; Robles-Kelly, A. Towards a deep learning-driven intrusion detection approach for Internet of Things. Comput. Netw. 2021, 186, 107784. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and development of a deep learning-based model for anomaly detection in IoT networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Baig, Z.A.; Sanguanpong, S.; Firdous, S.N.; Nguyen, T.G.; So-In, C. Averaged dependence estimators for DoS attack detection in IoT networks. Future Gener. Comput. Syst. 2020, 102, 198–209. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R. A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4112. [Google Scholar] [CrossRef]
- Papadopoulos, P.; Thornewill von Essen, O.; Pitropakis, N.; Chrysoulas, C.; Mylonas, A.; Buchanan, W.J. Launching adversarial attacks against network intrusion detection systems for iot. J. Cybersecur. Priv. 2021, 1, 252–273. [Google Scholar] [CrossRef]
- Nimbalkar, P.; Kshirsagar, D. Feature selection for intrusion detection system in Internet-of-Things (IoT). ICT Express 2021, 7, 177–181. [Google Scholar] [CrossRef]
- Derhab, A.; Aldweesh, A.; Emam, A.Z.; Khan, F.A. Intrusion detection system for internet of things based on temporal convolution neural network and efficient feature engineering. Wirel. Commun. Mob. Comput. 2020, 2020, 6689134. [Google Scholar] [CrossRef]
- Ullah, I.; Ullah, A.; Sajjad, M. Towards a hybrid deep learning model for anomalous activities detection in internet of things networks. IoT 2021, 2, 428–448. [Google Scholar] [CrossRef]
- Islam, R.; Refat, R.U.D.; Yerram, S.M.; Malik, H. Graph-based intrusion detection system for controller area networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1727–1736. [Google Scholar] [CrossRef]
- Noble, C.C.; Cook, D.J. Graph-based anomaly detection. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003; pp. 631–636. [Google Scholar]
- Protogerou, A.; Papadopoulos, S.; Drosou, A.; Tzovaras, D.; Refanidis, I. A graph neural network method for distributed anomaly detection in IoT. Evol. Syst. 2021, 12, 19–36. [Google Scholar] [CrossRef]
- Lo, W.W.; Layeghy, S.; Sarhan, M.; Gallagher, M.; Portmann, M. E-GraphSAGE: A Graph Neural Network based Intrusion Detection System for IoT. In Proceedings of the NOMS 2022-2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; pp. 1–9. [Google Scholar]
- Alkadi, O.; Moustafa, N.; Turnbull, B.; Choo, K.K.R. A deep blockchain framework-enabled collaborative intrusion detection for protecting IoT and cloud networks. IEEE Internet Things J. 2020, 8, 9463–9472. [Google Scholar] [CrossRef]
- Sudheera, K.L.K.; Divakaran, D.M.; Singh, R.P.; Gurusamy, M. ADEPT: Detection and identification of correlated attack stages in IoT networks. IEEE Internet Things J. 2021, 8, 6591–6607. [Google Scholar] [CrossRef]
- Albulayhi, K.; Sheldon, F.T. An adaptive deep-ensemble anomaly-based intrusion detection system for the internet of things. In Proceedings of the IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 10–13 May 2021; pp. 0187–0196. [Google Scholar]
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Alzahrani, B.; Al-Barakati, A. DeepDCA: Novel network-based detection of IoT attacks using artificial immune system. Appl. Sci. 2020, 10, 1909. [Google Scholar] [CrossRef] [Green Version]
- Nwafor, E.; Campbell, A.; Bloom, G. Anomaly-based intrusion detection of IoT device sensor data using provenance graphs. In Proceedings of the 1st International Workshop on Security and Privacy for the Internet-of-Things, Dallas, TX, USA, 3 November 2017; Volume 59. [Google Scholar]
- Samdekar, R.; Ghosh, S.; Srinivas, K. Efficiency enhancement of intrusion detection in iot based on machine learning through bioinspire. In Proceedings of the 3rd International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; pp. 383–387. [Google Scholar]
- Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. Towards a lightweight detection system for cyber attacks in the IoT environment using corresponding features. Electronics 2020, 9, 144. [Google Scholar] [CrossRef] [Green Version]
- Pant, S.; Sharma, M.; Sharma, D.K.; Gupta, D.; Rodrigues, J.J. Enforcing Intelligent Learning-Based Security in the Internet of Everything. IEEE Internet Things J. 2021, 10, 3071–3078. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Ahmim, A.; Derdour, M.; Janicke, H. Rdtids: Rules and decision tree-based intrusion detection system for internet-of-things networks. Future Internet 2020, 12, 44. [Google Scholar] [CrossRef] [Green Version]
- Zixu, T.; Liyanage, K.S.K.; Gurusamy, M. Generative adversarial network and auto encoder based anomaly detection in distributed IoT networks. In Proceedings of the GLOBECOM 2020-2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–7. [Google Scholar]
- Kumar, P.; Gupta, G.P.; Tripathi, R. Toward design of an intelligent cyber attack detection system using hybrid feature reduced approach for iot networks. Arab. J. Sci. Eng. 2021, 46, 3749–3778. [Google Scholar] [CrossRef]
- Huong, T.T.; Bac, T.P.; Long, D.M.; Thang, B.D.; Binh, N.T.; Luong, T.D.; Phuc, T.K. Lockedge: Low-complexity cyberattack detection in iot edge computing. IEEE Access 2021, 9, 29696–29710. [Google Scholar] [CrossRef]
- Manjunath, A.; Yatnalli, V.; Bhusare, S.S. Performance Analysis of Graph theory-based Contrast Limited Adaptive Histogram Equalization for Image Enhancement. WSEAS Trans. Syst. 2023, 22, 219–230. [Google Scholar]
- Alfarisi, R.; Susilowati, L.; Dafik; Fadekemi, O. On The Local Multiset Dimension of some Families of Graphs. WSEAS Trans. Math. 2023, 22, 64–69. [Google Scholar] [CrossRef]
- ŠEDA, M. Steiner Tree Problem in Graphs and Mixed Integer Linear Programming-Based Approach in GAMS. WSEAS Trans. Comput. 2022, 21, 257–262. [Google Scholar] [CrossRef]
- Aldribi, A.; Traore, I.; Moa, B. Data Sources and Datasets for Cloud Intrusion Detection Modeling and Evaluation. In Cloud Computing for Optimization: Foundations, Applications, and Challenges; Mishra, B.S.P., Das, H., Dehuri, S., Jagadev, A.K., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 333–366. [Google Scholar] [CrossRef]
- Aldribi, A.; Traoré, I.; Moa, B.; Nwamuo, O. Hypervisor-based cloud intrusion detection through online multivariate statistical change tracking. Comput. Secur. 2020, 88, 101646. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).