CAVeCTIR: Matching Cyber Threat Intelligence Reports on Connected and Autonomous Vehicles Using Machine Learning †
Abstract
1. Introduction
“Can we expand existing IoV cybersecurity frameworks and provide the cybersecurity stakeholders (with an emphasis on cybersecurity experts) with an approach implementing an automatic process that analyzes and correlates CTI reports with newly detected malicious activities (e.g., cyber-attacks) on CAVs in an IoV environment?”
2. Related Work
2.1. Importance of CTI
2.2. Extracting and Sharing CTI Information
2.3. Use and Analysis of CTI in IoV Systems
2.4. Synthesis
3. nIoVe Framework
- Attack attribution, which identifies low-level and high-level IOCs and aims to assist security experts in attributing the detected attack to known threat actors by attempting to identify common tactics, techniques, and procedures;
- Digital forensic readiness, which enables the nIoVe framework to automatically collect forensic data from various sources and to create a CTI report containing all the necessary information about the attack. This step is vital for further digital investigation, preservation of the integrity of the collected data, and maintenance of a valid chain of custody.
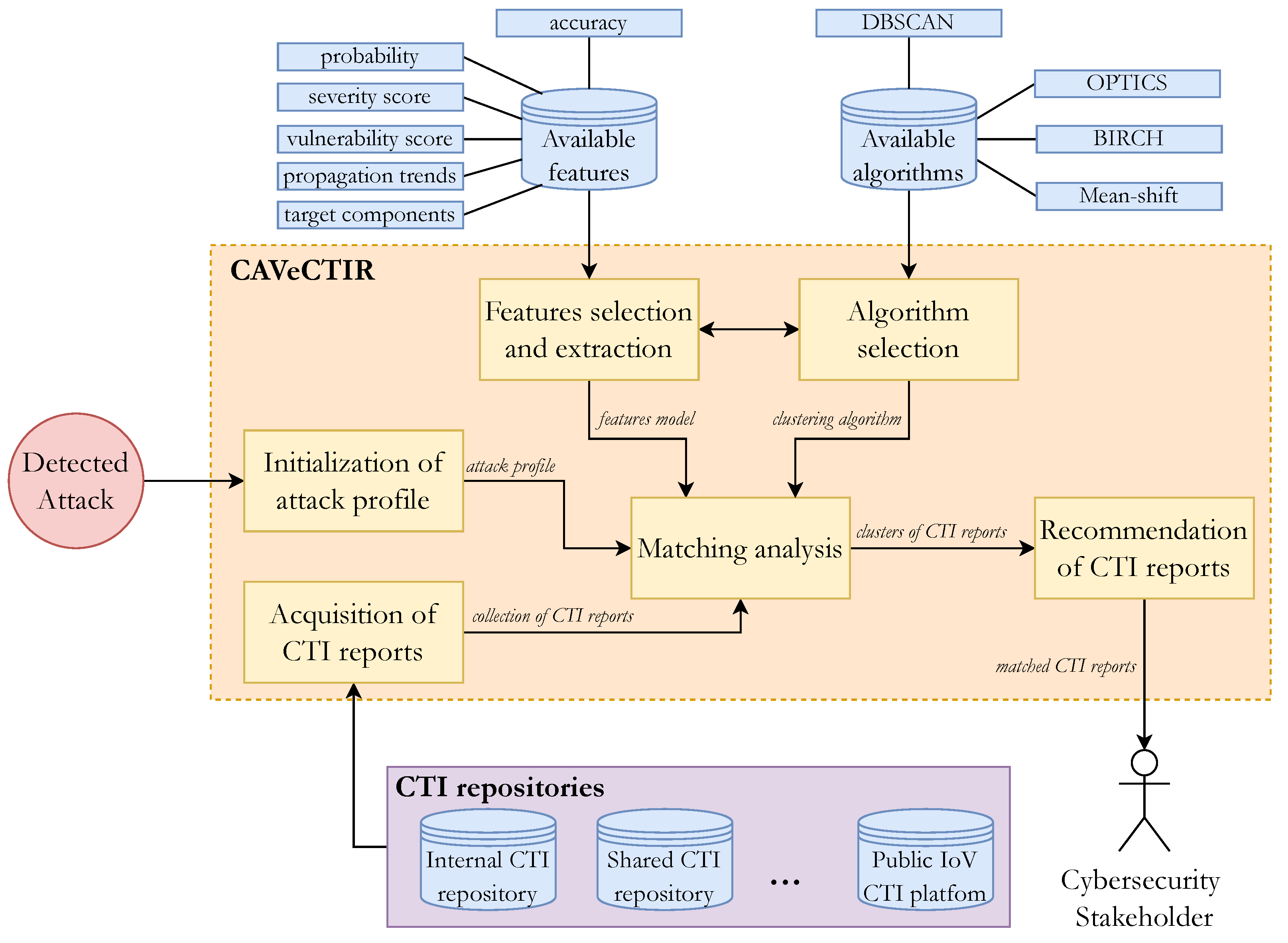
CAVeCTIR Method
- Initialization of attack profile: CAVeCTIR extracts characteristics of the detected attack directly and initializes the attack profile. These characteristics include the IoV components (e.g., sensors) that have been attacked, propagation trends, risk assessment regarding the overall IoV system, and the level of confidence regarding the impact of the attack. Based on these, an initial attack profile is generated and assigned to a new forensic case.
- Acquisition of CTI reports: In parallel with the previous step, CAVeCTIR seeks, processes, and acquires CTI reports from various platforms and repositories, including both the internal MISP-based CTI repository and other external repositories to which the organization has access (e.g., shared threat intelligence repository). The output of this step is a collection of the acquired CTI reports.
- Features selection/extraction: Based on the collected information related to the detected attack and the CTI reports, CAVeCTIR aims to reduce the number of features and rank the importance of these features through feature selection and extraction processes. It generates a features model fed to the matching analysis process, aiming to provide an efficient and quick machine-learning clustering approach.
- Algorithm selection: Several algorithms are supported for both supervised and unsupervised machine learning. Focusing on the unsupervised techniques, the supported algorithms include k-means clustering, mean-shift clustering, density-based spatial clustering of applications with noise (DBSCAN), affinity propagation, hierarchical clustering, balanced iterative reducing and clustering using hierarchies (BIRCH), and ordering points to identify the clustering structure (OPTICS). The selection of the most effective algorithm depends on various factors, including the selected features, the knowledge of the number of clustering, and the sample size.
- Matching analysis: Having as input the profile of the detected attack, the acquired CTI reports, the features model, and the appropriate machine-learning algorithm, CAVeCTIR proceeds with the matching analysis, which aims to cluster the CTI reports dynamically and in real-time. Similarities and differences between the CTI reports are recorded. In the end, the detected attack is matched with one or more CTI reports, which are characterized as interrelated, meaning that they describe malicious activities, tools, techniques, and processes that share common patterns with the newly detected attack.
- Recommendation of matched CTI reports: The outcome of the previous step is a series of clusters containing matched recorded CTI reports. Based on the detected attack, CAVeCTIR recommends the corresponding cluster to the cybersecurity stakeholders (e.g., cybersecurity experts and analysts). This cluster contains CTI reports, from both internal and external sources, that match the profile of the detected attack, according to the selected machine-learning approach. Therefore, the cybersecurity stakeholders have full access to the matched CTI reports, assess their relevance to the detected attack, estimate the impact on the IoV environment, and can adopt the same or similar post-incident forensic analysis processes (including tools, methods, and techniques) to identity and eventually attribute the detected IoV attack quickly and accurately.
4. Evaluation Study
4.1. Setup
4.1.1. Attack Scenarios
4.1.2. Environments
- Simulated environment. To simulate the attacks on CAVs, we used the co-simulation tool of the nIoVe framework (Figure 4). The co-simulation tool is based on the CARLA open-source simulator that supports the development, training, and validation of autonomous driving systems. The interface of the co-simulation tool (i) enables the security expert to execute a specific attack scenario, (ii) provides a console to view the progress of the attack, and (iii) provides a live video stream of the CAV moving in a metropolitan area.
- Real-world. This environment is a real smart city environment. The choice of this scenario is motivated by the fact that a real-life trial presents no danger for humans in this case (e.g., vehicle passengers, pedestrians, and other road users). It is mainly based on the communication between the road-side unit (RSU) and the CAV, with two on-board units (OBUs) installed (one responsible for the vehicle movement and the other responsibilities of the communication).
- Hybrid. The deployment and the testing of the cybersecurity framework take part in a real-world-like environment of a setup that meets specific requirements. Like the real-work environment, it is based on the OBUs of the CAV.
4.1.3. Analysis Tools
- Silhouette coefficient [42]. The Silhouette coefficient is defined for each sample and is composed of two scores, and . A higher Silhouette coefficient score relates to a model with better defined clusters.
- Calinski–Harabasz score [43]. The Calinski–Harabasz score (also known as the Variance Ratio Criterion) is the ratio of the sum of between-cluster dispersion and of inter-cluster dispersion for all clusters. For a set of data E of size , which has been clustered into k clusters, the Calinski–Harabasz score s is defined as the ratio of the between-cluster dispersion mean and the within-cluster dispersion:where is the trace of the between-cluster dispersion matrix and is the trace of the within-cluster dispersion matrix defined by:with as the set of points in cluster q, the center of cluster q, the center of E, and the number of points in cluster q. The score is higher when the clusters are dense and well separated, which relates to a standard concept of a cluster. Moreover, the score is computed fast.
- Davies–Bouldin index [44]. The Davies–Bouldin index signifies the average ‘similarity’ between clusters, where the similarity is a measure that compares the distance between clusters with the size of the clusters themselves.The index is defined as the average similarity between each cluster for and its most similar one . In the context of this index, the similarity is defined as a measure that trades off:
- -
- : the average distance between each point of cluster i and the centroid of that cluster (also known as cluster diameter).
- -
- : the distance between cluster centroids i and j.
A simple choice to construct so that it is nonnegative and symmetric is:Then the Davies–Bouldin index is defined as:A lower Davies–Bouldin index relates to a model with better separation between the clusters. Zero is the lowest possible score. Values closer to zero indicate a better partition.
4.1.4. Study Procedure
4.2. Results
- with , which defines the maximum distance between two samples for one to be considered as in the neighborhood of the other.
- with , which defines the number of samples (i.e., total weight) in a neighborhood for a point to be considered as a core point (including the point itself).
- Silhouette coefficient: our result (s = 0.792) is similar to or better than the coefficient scores reported regarding the clustering of the Conti and Ryuk families (s = 0.725) and Babuk family (s = 0.786) used in CTI processes [47], clusters containing malicious URLs (s = 0.383) [48], and TTP profile extraction and group clustering in IoT () [49].
- Performance timing: the maximum execution time (in seconds) for the clustering was . The DBSCAN performance timings vary widely in the literature (e.g., [52], [53], and [54]). However, this metric highly depends on the computational resources, the data size, and the complexity of the machine-learning problem. Since CAVeCTIR contributes to the post-incident forensics investigation, the reported timing is acceptable.
5. Discussion
5.1. Summary of Findings
5.2. Integration with Other CTI Repositories
5.3. Expandability beyond IoV
5.4. Limitations and Future Steps
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| CAV | Connected and Autonomous Vehicle |
| IoV | Internet of Vehicles |
| IOCs | indicators of compromise |
| CAN bus | Controller Area Network bus |
| GNSS | Global Navigation Satellite System |
| DoS | Denial of Service |
| IMU | Inertial Measurement Unit |
| OBU | On-Board Unit |
| RSU | Road-Side Unit |
Appendix A
References
- Sun, Y.; Wu, L.; Wu, S.; Li, S.; Zhang, T.; Zhang, L.; Xu, J.; Xiong, Y.; Cui, X. Attacks and Countermeasures in the Internet of Vehicles. Ann. Telecommun. 2016, 72, 283–295. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for Autonomous Vehicles: Review of Attacks and Defense. Comput. Secur. 2021, 103, 102–150. [Google Scholar] [CrossRef]
- Serinelli, B.M.; Collen, A.; Nijdam, N.A. Training Guidance with KDD Cup 1999 and NSL-KDD Data Sets of ANIDINR: Anomaly-Based Network Intrusion Detection System. Procedia Comput. Sci. 2020, 175, 560–565. [Google Scholar] [CrossRef]
- Hamad, M.; Tsantekidis, M.; Prevelakis, V. Intrusion Response System for Vehicles: Challenges and Vision. In Communications in Computer and Information Science; Springer International Publishing: Cham, Switzerland, 2021; pp. 321–341. [Google Scholar] [CrossRef]
- Noor, U.; Anwar, Z.; Amjad, T.; Choo, K.K.R. A Machine Learning-based FinTech Cyber Threat Attribution Framework using High-level Indicators of Compromise. Future Gener. Comput. Syst. 2019, 96, 227–242. [Google Scholar] [CrossRef]
- Gao, Y.; Xiaoyong, L.; Hao, P.; Fang, B.; Yu, P. HinCTI: A Cyber Threat Intelligence Modeling and Identification System Based on Heterogeneous Information Network. IEEE Trans. Knowl. Data Eng. 2020, 34, 708–722. [Google Scholar] [CrossRef]
- Preuveneers, D.; Joosen, W. Sharing Machine Learning Models as Indicators of Compromise for Cyber Threat Intelligence. J. Cybersecur. Priv. 2021, 1, 140–163. [Google Scholar] [CrossRef]
- Koloveas, P.; Chantzios, T.; Alevizopoulou, S.; Skiadopoulos, S.; Tryfonopoulos, C. inTIME: A Machine Learning-Based Framework for Gathering and Leveraging Web Data to Cyber-Threat Intelligence. Electronics 2021, 10, 818. [Google Scholar] [CrossRef]
- Zacharaki, A.; Paliokas, I.; Votis, K.; Alexakos, C.; Serpanos, D.; Tzovaras, D. Complex Engineering Systems as an Enabler for Security in Internet of Vehicles: The nIoVe Approach. In Proceedings of the 2019 First International Conference on Societal Automation (SA), Krakow, Poland, 4–6 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–8. [Google Scholar] [CrossRef]
- Conti, M.; Dargahi, T.; Dehghantanha, A. Cyber Threat Intelligence: Challenges and Opportunities. In Advances in Information Security; Springer International Publishing: Cham, Switzerland, 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Mavroeidis, V.; Bromander, S. Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence. In Proceedings of the 2017 European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017; IEEE: Piscataway, NJ, USA, 2017. [Google Scholar] [CrossRef]
- Barnum, S. Standardizing Cyber Threat Intelligence Information with the Structured Threat Information eXpression (STIX). Mitre Corp. 2012, 11, 1–22. [Google Scholar]
- Wagner, T.D.; Palomar, E.; Mahbub, K.; Abdallah, A.E. A Novel Trust Taxonomy for Shared Cyber Threat Intelligence. Secur. Commun. Netw. 2018, 2018, 9634507. [Google Scholar] [CrossRef]
- Schlette, D.; Böhm, F.; Caselli, M.; Pernul, G. Measuring and visualizing cyber threat intelligence quality. Int. J. Inf. Secur. 2020, 20, 21–38. [Google Scholar] [CrossRef]
- Landauer, M.; Skopik, F.; Wurzenberger, M.; Hotwagner, W.; Rauber, A. A Framework for Cyber Threat Intelligence Extraction from Raw Log Data. In Proceedings of the 2019 IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; IEEE: Piscataway, NJ, USA, 2019. [Google Scholar] [CrossRef]
- Zhao, J.; Yan, Q.; Li, J.; Shao, M.; He, Z.; Li, B. TIMiner: Automatically extracting and analyzing categorized cyber threat intelligence from social data. Comput. Secur. 2020, 95, 101867. [Google Scholar] [CrossRef]
- Deliu, I.; Leichter, C.; Franke, K. Extracting cyber threat intelligence from hacker forums: Support vector machines versus convolutional neural networks. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; IEEE: Piscataway, NJ, USA, 2017. [Google Scholar] [CrossRef]
- Kadoguchi, M.; Hayashi, S.; Hashimoto, M.; Otsuka, A. Exploring the Dark Web for Cyber Threat Intelligence using Machine Leaning. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; IEEE: Piscataway, NJ, USA, 2019. [Google Scholar] [CrossRef]
- Zhang, H.; Shen, G.; Guo, C.; Cui, Y.; Jiang, C. EX-Action: Automatically Extracting Threat Actions from Cyber Threat Intelligence Report Based on Multimodal Learning. Secur. Commun. Netw. 2021, 2021, 5586335. [Google Scholar] [CrossRef]
- Li, K.; Wen, H.; Li, H.; Zhu, H.; Sun, L. Security OSIF: Toward Automatic Discovery and Analysis of Event Based Cyber Threat Intelligence. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Zhu, Z.; Dumitras, T. ChainSmith: Automatically Learning the Semantics of Malicious Campaigns by Mining Threat Intelligence Reports. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Husari, G.; Niu, X.; Chu, B.; Al-Shaer, E. Using Entropy and Mutual Information to Extract Threat Actions from Cyber Threat Intelligence. In Proceedings of the 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, FL, USA, 9–11 November 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Ghazi, Y.; Anwar, Z.; Mumtaz, R.; Saleem, S.; Tahir, A. A Supervised Machine Learning Based Approach for Automatically Extracting High-Level Threat Intelligence from Unstructured Sources. In Proceedings of the 2018 International Conference on Frontiers of Information Technology (FIT), Islamabad, Pakistan, 17–19 December 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Wang, X.; Chen, R.; Song, B.; Yang, J.; Jiang, Z.; Zhang, X.; Li, X.; Ao, S. A Method for Extracting Unstructured Threat Intelligence Based on Dictionary Template and Reinforcement Learning. In Proceedings of the 2021 IEEE 24th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Dalian, China, 5–7 May 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Wagner, T.D.; Mahbub, K.; Palomar, E.; Abdallah, A.E. Cyber threat intelligence sharing: Survey and research directions. Comput. Secur. 2019, 87, 101589. [Google Scholar] [CrossRef]
- Wagner, C.; Dulaunoy, A.; Wagener, G.; Iklody, A. MISP: The Design and Implementation of a Collaborative Threat Intelligence Sharing Platform. In Proceedings of the 2016 ACM on Workshop on Information Sharing and Collaborative Security, WISCS ’16, Vienna, Austria, 24 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 49–56. [Google Scholar] [CrossRef]
- Gao, P.; Liu, X.; Choi, E.; Soman, B.; Mishra, C.; Farris, K.; Song, D. A System for Automated Open-Source Threat Intelligence Gathering and Management. In Proceedings of the 2021 International Conference on Management of Data, Online, China, 20–25 June 2021; ACM: New York, NY, USA, 2021. [Google Scholar] [CrossRef]
- Connolly, J.; Davidson, M.; Schmidt, C. The Trusted Automated eXchange of Indicator Information (TAXII). Mitre Corp. 2014. Available online: https://taxii.mitre.org/about/documents/Introduction_to_TAXII_White_Paper_May_2014.pdf (accessed on 12 October 2022).
- Kukkala, V.K.; Thiruloga, S.V.; Pasricha, S. Roadmap for Cybersecurity in Autonomous Vehicles. IEEE Consum. Electron. Mag. 2022, 11, 13–23. [Google Scholar] [CrossRef]
- He, H.; Gray, J.; Cangelosi, A.; Meng, Q.; McGinnity, T.; Mehnen, J. The challenges and opportunities of artificial intelligence in implementing trustworthy robotics and autonomous systems. In Proceedings of the 3rd International Conference on Intelligent Robotic and Control Engineering, Oxford, UK, 10–12 August 2020. [Google Scholar]
- Panda, S.; Rass, S.; Moschoyiannis, S.; Liang, K.; Loukas, G.; Panaousis, E. HoneyCar: A Framework to Configure Honeypot Vulnerabilities on the Internet of Vehicles. arXiv 2021, arXiv:2111.02364. [Google Scholar] [CrossRef]
- Basnet, M.; Ali, M. A Deep Learning Perspective on Connected Automated Vehicle (CAV) Cybersecurity and Threat Intelligence. arXiv 2021, arXiv:2109.10763. [Google Scholar]
- Ali, E.S.; Hasan, M.K.; Hassan, R.; Saeed, R.A.; Hassan, M.B.; Islam, S.; Nafi, N.S.; Bevinakoppa, S. Machine learning technologies for secure vehicular communication in internet of vehicles: Recent advances and applications. Secur. Commun. Netw. 2021, 2021, 8868355. [Google Scholar] [CrossRef]
- Liu, W.; Xu, X.; Qi, L.; Zhang, X.; Dou, W. GoDeep: Intelligent IoV Service Deployment and Execution with Privacy Preservation in Cloud-edge Computing. In Proceedings of the 2021 IEEE International Conference on Web Services (ICWS), Chicago, IL, USA, 5–10 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 579–587. [Google Scholar]
- Mohseni, S.; Pitale, M.; Singh, V.; Wang, Z. Practical solutions for machine learning safety in autonomous vehicles. arXiv 2019, arXiv:1912.09630. [Google Scholar]
- Kumar, P.; Gupta, G.P.; Tripathi, R.; Garg, S.; Hassan, M.M. DLTIF: Deep Learning-Driven Cyber Threat Intelligence Modeling and Identification Framework in IoT-Enabled Maritime Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2021. [Google Scholar] [CrossRef]
- Alexakos, C.; Katsini, C.; Votis, K.; Lalas, A.; Tzovaras, D.; Serpanos, D. Enabling Digital Forensics Readiness for Internet of Vehicles. Transp. Res. Procedia 2021, 52, 339–346. [Google Scholar] [CrossRef]
- Katsini, C.; Raptis, G.E.; Alexakos, C.; Serpanos, D. FoRePlan: Supporting Digital Forensics Readiness Planning for Internet of Vehicles. In Proceedings of the 25th Pan-Hellenic Conference on Informatics, PCI 2021, Volos, Greece, 26–28 November 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 369–374. [Google Scholar] [CrossRef]
- Raptis, G.E.; Katsini, C.; Alexakos, C. Towards Automated Matching of Cyber Threat Intelligence Reports based on Cluster Analysis in an Internet-of-Vehicles Environment. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Pedregosa, F.; Varoquaux, G.; Gramfort, A.; Michel, V.; Thirion, B.; Grisel, O.; Blondel, M.; Prettenhofer, P.; Weiss, R.; Dubourg, V.; et al. Scikit-learn: Machine Learning in Python. J. Mach. Learn. Res. 2011, 12, 2825–2830. [Google Scholar]
- Ester, M.; Kriegel, H.P.; Sander, J.; Xu, X. A density-based algorithm for discovering clusters in large spatial databases with noise. In Proceedings of the Kdd, Portland, OR, USA, 2–4 August 1996; Volume 96, pp. 226–231. [Google Scholar]
- Rousseeuw, P.J. Silhouettes: A graphical aid to the interpretation and validation of cluster analysis. J. Comput. Appl. Math. 1987, 20, 53–65. [Google Scholar] [CrossRef]
- Caliński, T.; Harabasz, J. A dendrite method for cluster analysis. Commun. Stat.-Theory Methods 1974, 3, 1. [Google Scholar] [CrossRef]
- Davies, D.L.; Bouldin, D.W. A cluster separation measure. IEEE Trans. Pattern Anal. Mach. Intell. 1979, PAMI-1, 224–227. [Google Scholar] [CrossRef]
- Schubert, E.; Sander, J.; Ester, M.; Kriegel, H.P.; Xu, X. DBSCAN Revisited, Revisited: Why and How You Should (Still) Use DBSCAN. ACM Trans. Database Syst. 2017, 42, 19:1–19:21. [Google Scholar] [CrossRef]
- Wang, X.; Xu, Y. An improved index for clustering validation based on Silhouette index and Calinski-Harabasz index. In Proceedings of the IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2019; Volume 569, p. 052024. [Google Scholar]
- Grelot, F.; Larinier, S.; Salmon, M. Automation of Binary Analysis: From Open Source Collection to Threat Intelligence. In Proceedings of the 28th C&ESAR, Rennes, France, 16–17 November 2021; CEUR-WS: Aachen, Germany, 2021; pp. 41–56. [Google Scholar]
- Nayak, S.; Nadig, D.; Ramamurthy, B. Analyzing Malicious URLs using a Threat Intelligence System. In Proceedings of the 2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, 16–19 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–4. [Google Scholar]
- Wu, Y.; Huang, C.; Zhang, X.; Zhou, H. GroupTracer: Automatic attacker TTP profile extraction and group cluster in Internet of things. Secur. Commun. Netw. 2020, 2020, 8842539. [Google Scholar] [CrossRef]
- Ramírez Sánchez, J.; Campo-Archbold, A.; Zapata Rozo, A.; Díaz-López, D.; Pastor-Galindo, J.; Gómez Mármol, F.; Aponte Díaz, J. Uncovering cybercrimes in social media through natural language processing. Complexity 2021, 2021, 7955637. [Google Scholar] [CrossRef]
- Rodriguez, A.; Okamura, K. Enhancing data quality in real-time threat intelligence systems using machine learning. Soc. Netw. Anal. Min. 2020, 10, 91. [Google Scholar] [CrossRef]
- Smiti, A.; Elouedi, Z. Dbscan-gm: An improved clustering method based on gaussian means and dbscan techniques. In Proceedings of the 2012 IEEE 16th International Conference on Intelligent Engineering Systems (INES), Lisbon, Portugal, 13–15 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 573–578. [Google Scholar]
- Mustakim; Fauzi, M.Z.; Mustafa; Abdullah, A.; Rohayati. Clustering of Public Opinion on Natural Disasters in Indonesia Using DBSCAN and K-Medoids Algorithms. J. Phys. Conf. Ser. 2021, 1783, 012016. [Google Scholar]
- Sarma, A.; Goyal, P.; Kumari, S.; Wani, A.; Challa, J.S.; Islam, S.; Goyal, N. μDBSCAN: An exact scalable DBSCAN algorithm for big data exploiting spatial locality. In Proceedings of the 2019 IEEE International Conference on Cluster Computing (CLUSTER), Albuquerque, NM, USA, 23–26 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–11. [Google Scholar]




| Work | Reason(s) for Adopting Machine Learning Techniques | Application Domain |
|---|---|---|
| Landauer et al. [15] | extract CTI from raw log data | generic |
| Zhao et al. [16] | extract CTI from social data | domain-specific |
| Deliu et al. [17] | classify CTI content (forum posts) | social media |
| Zhang et al. [19] | extract CTI actions through semantic analysis | generic, text mining |
| Li et al. [20] | collect and analyze CTI events (semantic analysis of articles) | generic, text mining |
| Zhu et al. [21] | collect and analyze CTI malicious campaigns (semantic analysis of articles) | generic, text mining |
| Husari et al. [22] | extract CTI actions through semantic analysis | generic, text mining |
| Ghazi et al. [23] | extract high-level CTI IOCs | generic, text mining |
| Wang et al. [24] | extract high-level CTI IOCs | generic, text mining |
| Gao et al. [27] | search, collect, and manage CTI | generic |
| He et al. [30] | analyze huge CTI volume | IoV |
| Panda et al. [31] | collect and analyze CTI for honeypot configuration | IoV |
| Basnet et al. [32] | detect cyber-attacks in CAVs | IoV |
| Ali et al. [33] | ensure secure vehicular communication | IoV |
| Liu et al. [34] | deploy and execute privacy preservation services in cloud-edge computing | IoV |
| Mohseni et al. [35] | complement engineering safety for IoV software based on machine learning | IoV |
| Attack | Description |
|---|---|
| GNSS signals spoofing | The attacker emits a fake GNSS signal (i.e., providing false positioning and timing data) to the area that the CAV is moving through. The CAV receives this signal and processes false vehicle location. As a result, the moving CAV gets disoriented, demonstrating unexpected and dangerous behavior. |
| GNSS signals jamming | The attacker attempts to disrupt GNSS communications by jamming GNSS signals. As GNSS signals are vulnerable to intentional interference, the attacker uses a specific device (e.g., Software Defined Radio (SDR) hardware) to overpower GNSS signals so that they cannot be acquired and tracked by the GNSS receiver. |
| CAN DoS attack | The attacker floods the CAN bus (i.e., the control area network of the CAV that implements a message-based protocol, which enables communication between the in-vehicle components, such as micro-controllers and devices) with messages with high priority. As a result, the CAN bus becomes unresponsive, and thus, there is no control over the CAV, which demonstrates unexpected and dangerous behavior. |
| Alteration of CAN messages | The attacker tries to manipulate the CAN frames. Data manipulation can be defined as the insertion of an unauthorized CAN frame into the network. Since the CAN protocol does not have an authorization mechanism, a malicious node can attach to the network and inject malicious data. An attacker exploits this vulnerability and sends a CAN message to activate emergency brakes while the vehicle is moving. |
| Alteration of camera stream | The attacker attempts to alter the video transmitted over the Ethernet network of the CAV. They intercept the video stream and tamper with it. Next, they send it to the supervision center that monitors the CAVs. This results in image elements not being identified by the supervision center correctly. As a result, the supervision center cannot identify the actual situation of the CAV through the internal camera. |
| False sensor reading | The attacker manipulates the speedometer (i.e., the gauge that measures the instantaneous speed of the CAV) readings to trick the CAV into making bad decisions. The attacker replaces the existing speedometer with a malicious one. Therefore, the control module receives an erroneous value on the speed of the new device, which leads the CAV to make bad decisions and demonstrate unexpected and dangerous behavior. |
| Malware/Ransomware | The attacker attempts to penetrate and infect the vehicle with malware (e.g., ransomware). They use a Trojan disguised as a legitimate file to trick the end-users into downloading or installing it on a vehicle. The malware encrypts the vehicle’s files, making them inaccessible and the vehicle inoperable, and demands a ransom payment to decrypt them. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Raptis, G.E.; Katsini, C.; Alexakos, C.; Kalogeras, A.; Serpanos, D. CAVeCTIR: Matching Cyber Threat Intelligence Reports on Connected and Autonomous Vehicles Using Machine Learning. Appl. Sci. 2022, 12, 11631. https://doi.org/10.3390/app122211631
Raptis GE, Katsini C, Alexakos C, Kalogeras A, Serpanos D. CAVeCTIR: Matching Cyber Threat Intelligence Reports on Connected and Autonomous Vehicles Using Machine Learning. Applied Sciences. 2022; 12(22):11631. https://doi.org/10.3390/app122211631
Chicago/Turabian StyleRaptis, George E., Christina Katsini, Christos Alexakos, Athanasios Kalogeras, and Dimitrios Serpanos. 2022. "CAVeCTIR: Matching Cyber Threat Intelligence Reports on Connected and Autonomous Vehicles Using Machine Learning" Applied Sciences 12, no. 22: 11631. https://doi.org/10.3390/app122211631
APA StyleRaptis, G. E., Katsini, C., Alexakos, C., Kalogeras, A., & Serpanos, D. (2022). CAVeCTIR: Matching Cyber Threat Intelligence Reports on Connected and Autonomous Vehicles Using Machine Learning. Applied Sciences, 12(22), 11631. https://doi.org/10.3390/app122211631










