RF-Access: Barrier-Free Access Control Systems with UHF RFID
Abstract
1. Introduction
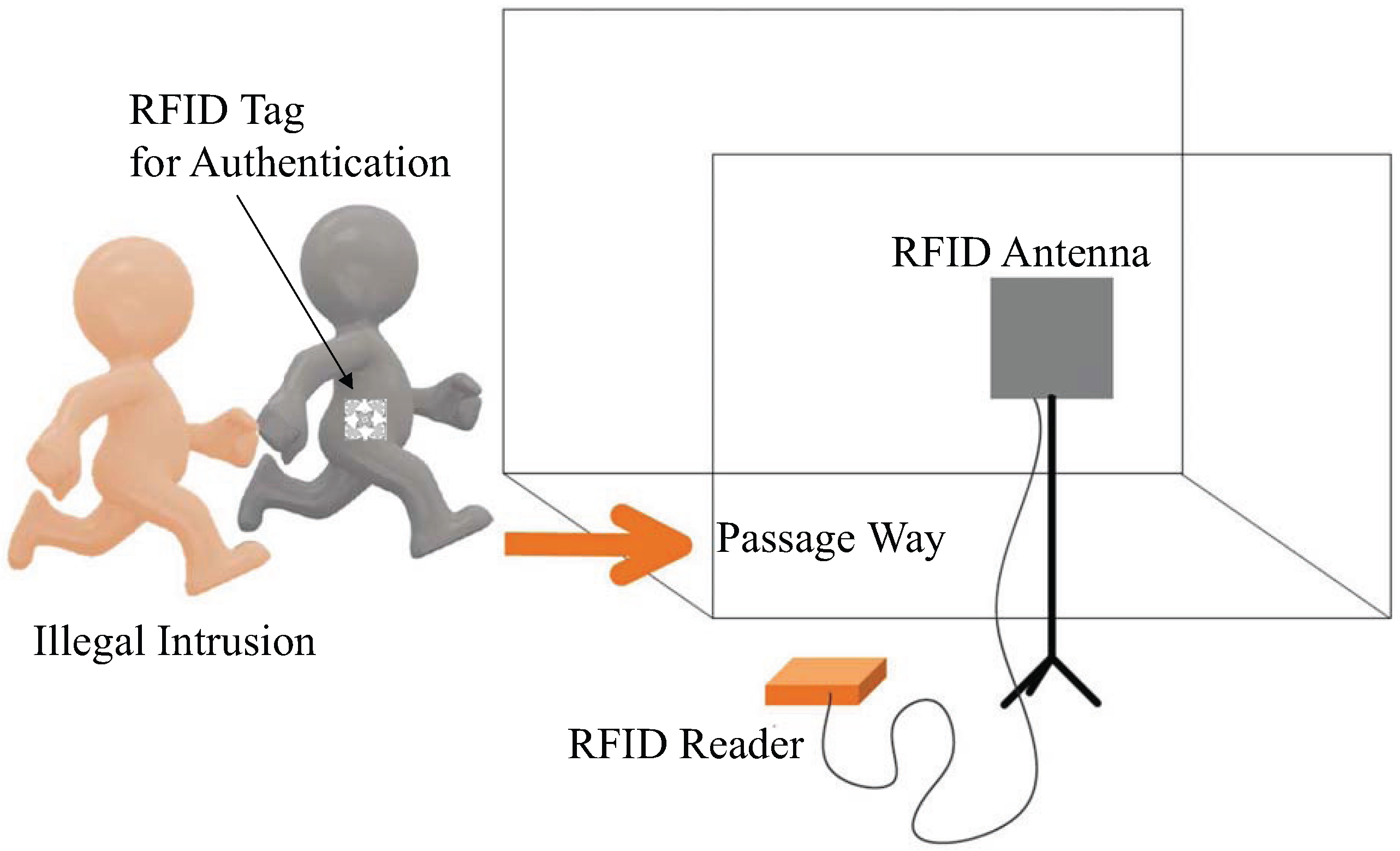
- We propose a novel barrier-free access control system (RF-Access) with UHF RFID technology. The main advantage of RF-Access is that it provides non-intrusive access control by removing flap barriers and operations of swiping the card, which greatly improves time efficiency and quality of service.
- RF-Access addresses two key issues of non-intrusive access control: motion direction detection and illegal intrusion detection, by using a dual-antenna tag-array system setup together with a time-slot-based model to monitor users’ moving directions.
- We implement a prototype of RF-Access with commercial RFID devices. Extensive experiments show that our system can detect the moving direction with 99.83% accuracy and detect illegal intrusion with an accuracy of 96.67%.
2. Related Work
3. RF-Access
3.1. Overview
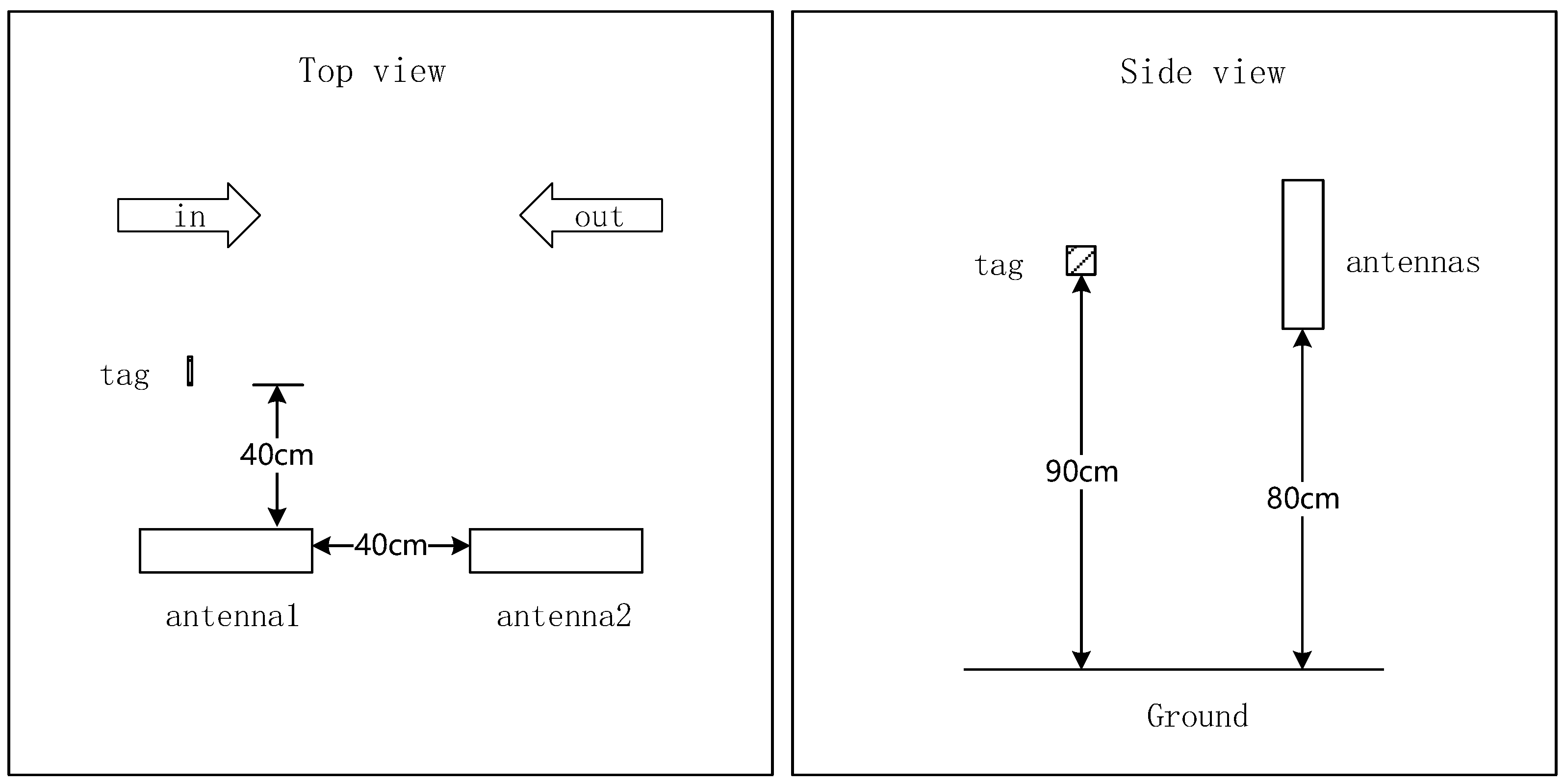
3.2. Motion Direction Detection
3.2.1. Signal-Based Sensing
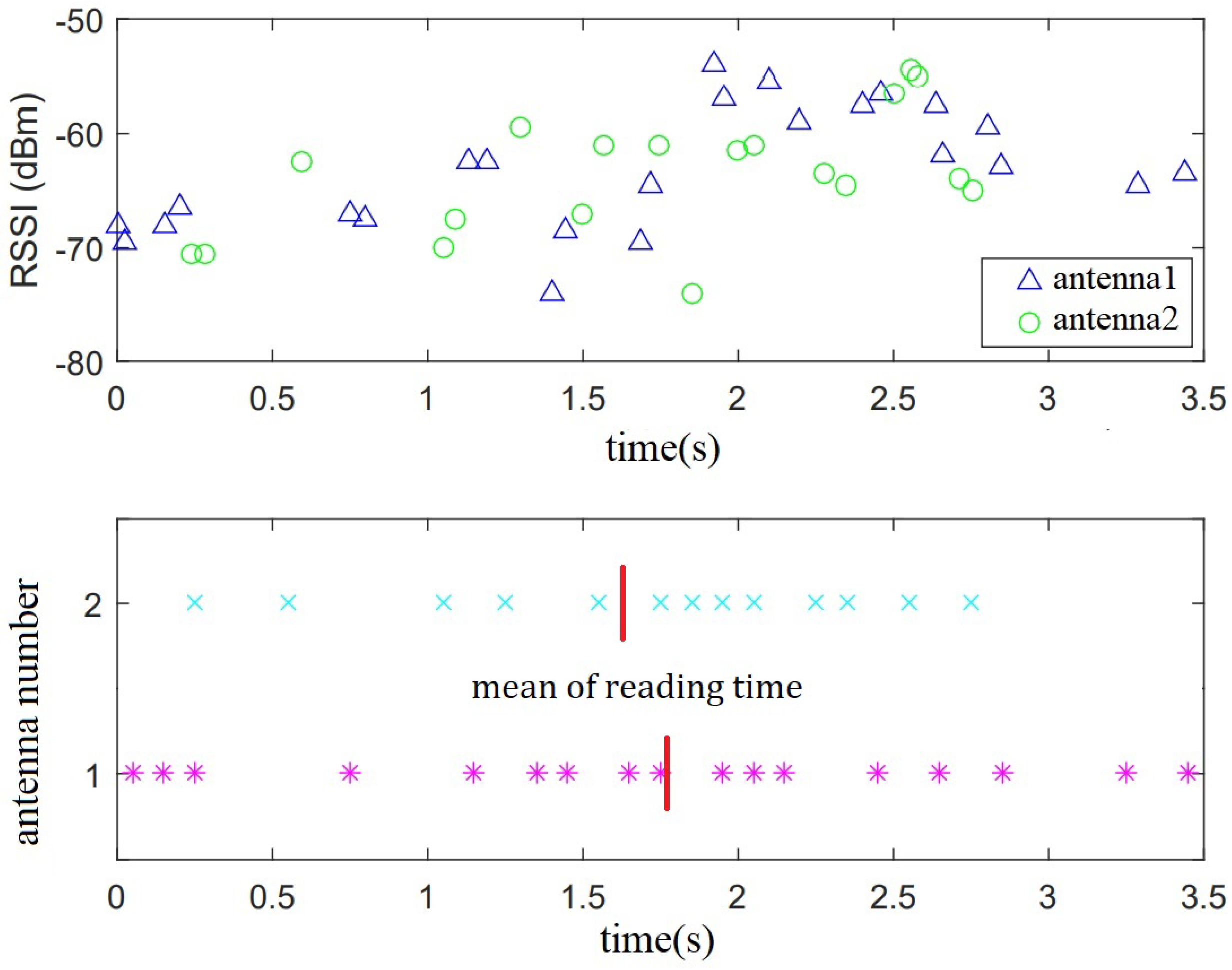
3.2.2. Time-Slot-Based Sensing
3.3. Tag-Array Based Intrusion Detection
3.4. Put Things Together
4. Evaluation
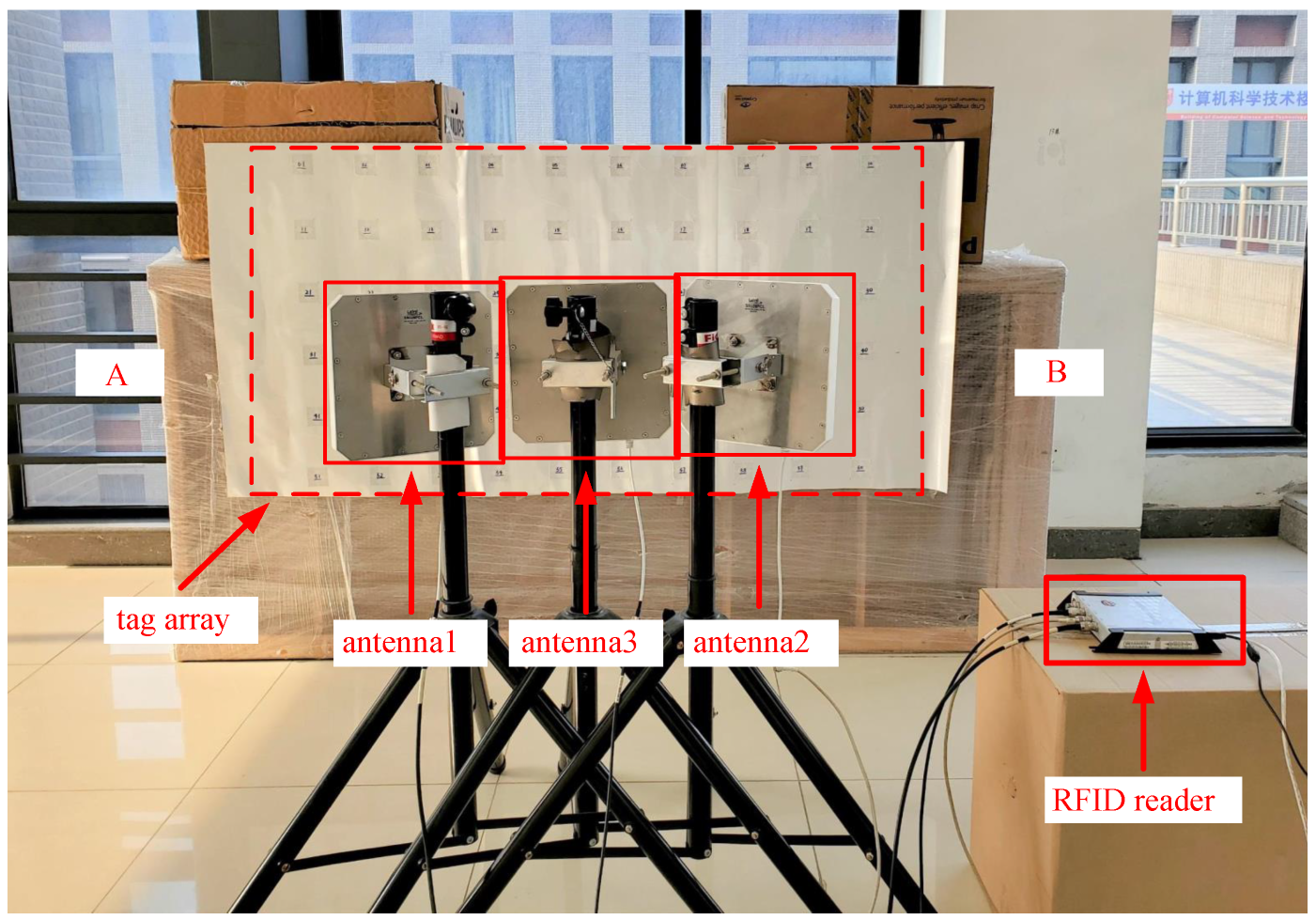
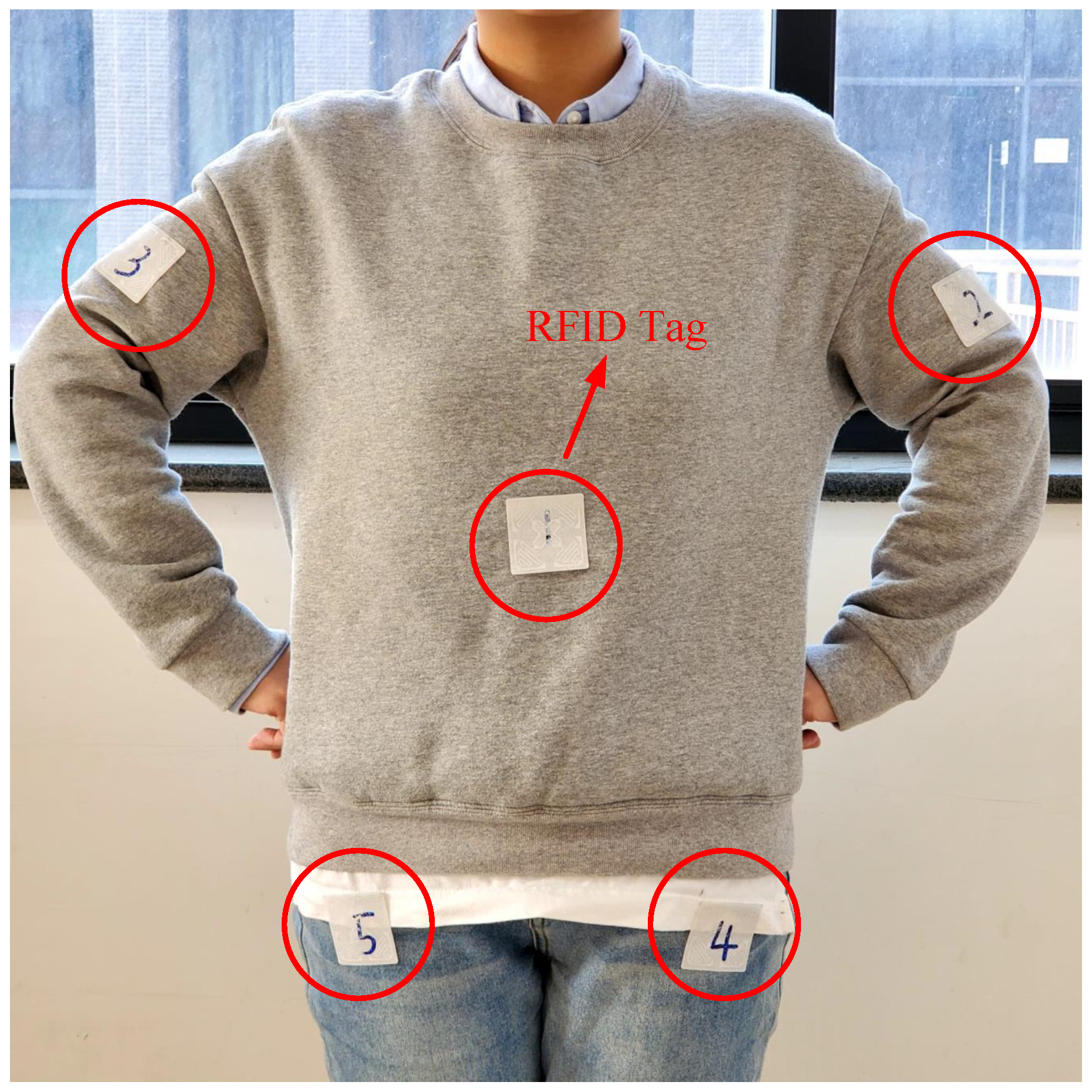
4.1. Implementation
4.2. Detection of Motion Direction
4.2.1. Experimental Methods
4.2.2. Impact of Antenna Angle
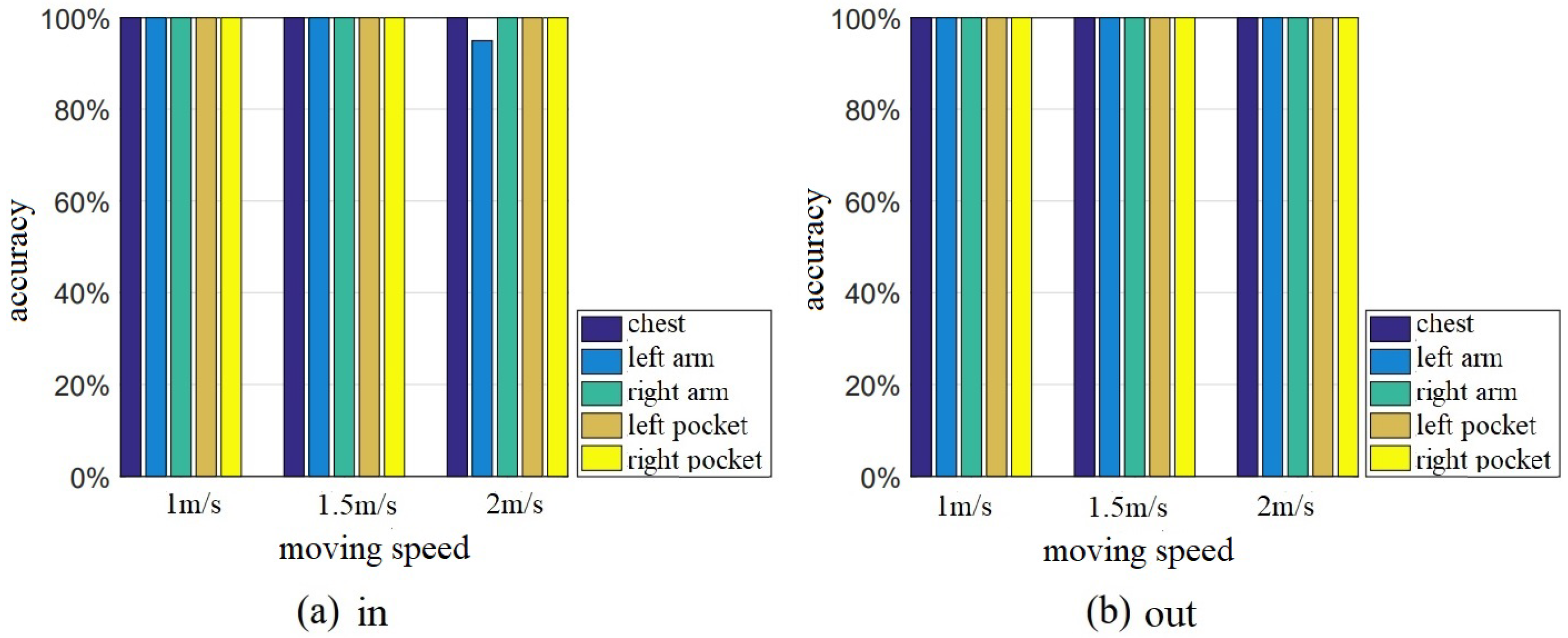
4.2.3. Impact of Antenna Distance
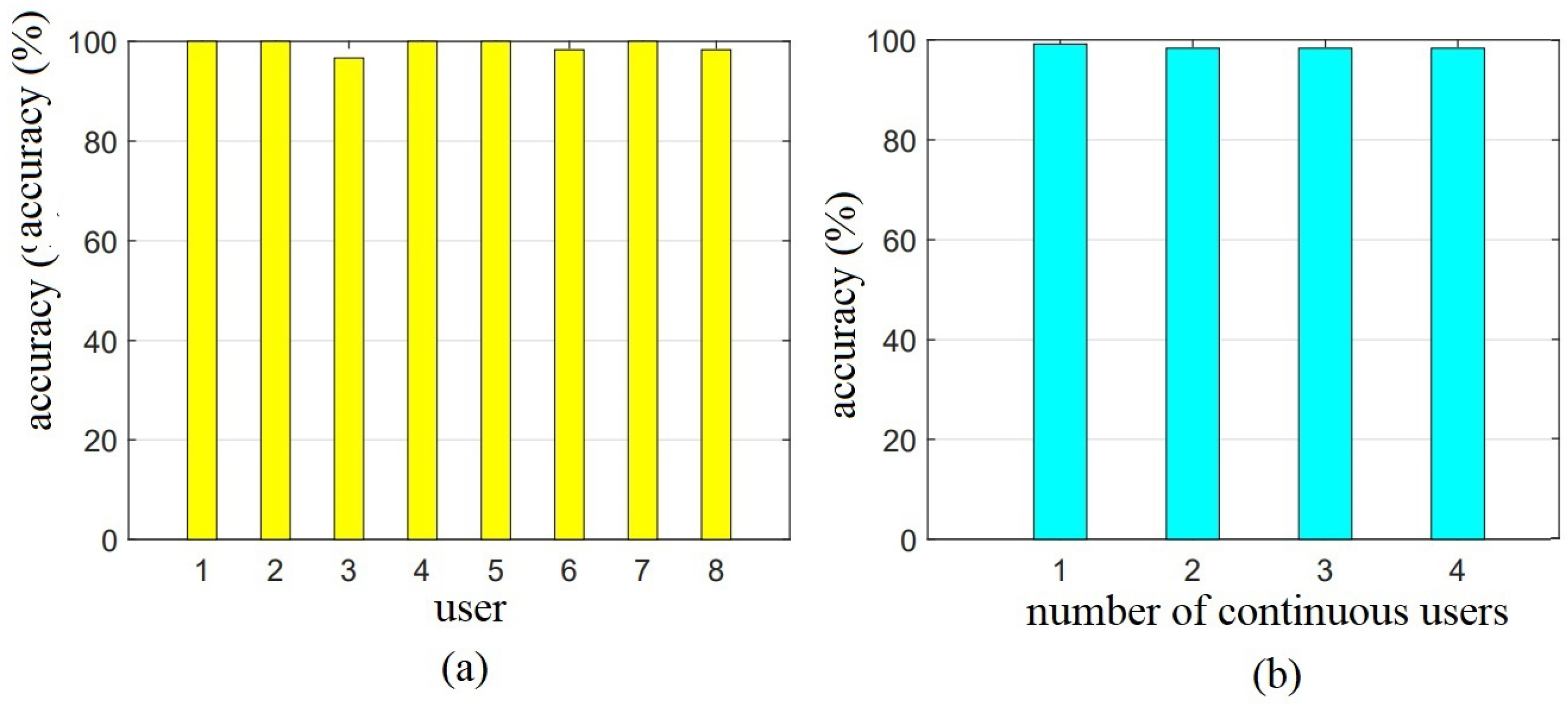
4.2.4. Impact of Different Users
4.3. Intrusion Detection
4.3.1. Experimental Methods
4.3.2. Detection Accuracy
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Choi, T.M. Coordination and Risk Analysis of VMI Supply Chains With RFID Technology. IEEE Trans. Ind. Inform. 2011, 7, 497–504. [Google Scholar] [CrossRef]
- Chen, X.; Liu, J.; Wang, X.; Liu, H.; Jiang, D.; Chen, L. Eingerprint: Robust Energy-related Fingerprinting for Passive RFID Tags. In Proceedings of the USENIX NSDI, Santa Clara, CA, USA, 25–27 February 2020; pp. 1101–1113. [Google Scholar]
- Fyhn, K.; Jacobsen, R.M.; Popovski, P.; Larsen, T. Fast Capture-Recapture Approach for Mitigating the Problem of Missing RFID Tags. IEEE Trans. Mob. Comput. 2012, 11, 518–528. [Google Scholar] [CrossRef]
- Liu, J.; Zhu, F.; Wang, Y.; Wang, X.; Pan, Q.; Chen, L. RF-scanner: Shelf scanning with robot-assisted RFID systems. In Proceedings of the IEEE INFOCOM, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Shangguan, L.; Zhou, Z.; Zheng, X.; Yang, L.; Liu, Y.; Han, J. ShopMiner: Mining Customer Shopping Behavior in Physical Clothing Stores with COTS RFID Devices. In Proceedings of the ACM SenSys, Seoul, Korea, 1–4 November 2015; pp. 113–126. [Google Scholar]
- Liu, J.; Chen, S.; Chen, M.; Xiao, Q.; Chen, L. Pose Sensing with a Single RFID Tag. IEEE/ACM Trans. Netw. 2020, 28, 2023–2036. [Google Scholar] [CrossRef]
- IEE: A Sense for Innovation. Available online: https://iee-sensing.com (accessed on 11 October 2022).
- Xu, X. Application and Innovation of Eight Integrated Technologies of Intelligent Access Card System. China Secur. Prot. 2014, 8, 52–54. [Google Scholar]
- Yang, L.; Chen, Y.; Li, X.Y.; Xiao, C.; Li, M.; Liu, Y. Tagoram: Real-time tracking of mobile RFID tags to high precision using COTS devices. In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking, Maui Hawaii USA, 7–11 September 2014; pp. 237–248. [Google Scholar]
- Stefaniak, P.; Jachnik, B.; Koperska, W.; Skoczylas, A. Localization of LHD Machines in Underground Conditions Using IMU Sensors and DTW Algorithm. Appl. Sci. 2021, 11, 6751. [Google Scholar] [CrossRef]
- Mai, A.; Wei, Z.; Gao, M. An access control and positioning security management system based on RFID. In Proceedings of the 7th International Conference on Intelligent Human-Machine Systems and Cybernetics, Hangzhou, China, 26–27 August 2015; Volume 2, pp. 537–540. [Google Scholar]
- Wang, Y. Open Trouble-Free Guard Management System Based on RFID Technology. Master’s Thesis, Ocean University of China, Qingdao, China, 2008. [Google Scholar]
- Fan, J. Research and Design of Student Apartments Barrier-Free Access Management System Based on RFID Technology. Master’s Thesis, Harbin Engineering University, Harbin, China, 2015. [Google Scholar]
- He, S.P.; Li, A.G.; Zhang, X. Design of Removable Intelligenct Barrier-free Access Control System Based on Mobile Technique. Meas. Control Technol. 2017, 36, 72–75. [Google Scholar]
- Impinj Inc. Available online: http://www.impinj.com (accessed on 11 October 2022).
- atlasRFIDstore. Available online: https://www.atlasrfidstore.com/impinj-xspan-gateway-rfid-reader (accessed on 11 October 2022).
- Griffin, J.D.; Durgin, G.D. Complete Link Budgets for Backscatter-Radio and RFID Systems. IEEE Antennas Propag. Mag. 2009, 51, 11–25. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Vayyar. Available online: https://vayyar.com/technology/ (accessed on 11 October 2022).
- Laird Inc. Available online: https://www.lairdconnect.com/rf-antennas/rfid-antennas/s902-series-rfid-antenna (accessed on 11 October 2022).










| Number | Visitor Quantity | Legal Visitor Quantity | Illegal Visitor Quantity |
|---|---|---|---|
| 1 | 1 | 1 | 0 |
| 2 | 2 | 2 | 0 |
| 3 | 2 | 1 | 1 |
| 4 | 3 | 3 | 0 |
| 5 | 3 | 2 | 1 |
| 6 | 3 | 1 | 2 |
| True Value | Estimated Value | |||
|---|---|---|---|---|
| 0 Visitor | 1 Visitor | 2 Visitors | 3 Visitors | |
| 0 visitor | 1 | 0 | 0 | 0 |
| 1 visitor | 0 | 0.98 | 0.02 | 0 |
| 2 visitors | 0 | 0.02 | 0.95 | 0.03 |
| 3 visitors | 0 | 0.007 | 0.04 | 0.953 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.; Wang, X.; Yan, Y.; Liu, J.; Zhao, Z. RF-Access: Barrier-Free Access Control Systems with UHF RFID. Appl. Sci. 2022, 12, 11592. https://doi.org/10.3390/app122211592
Wang X, Wang X, Yan Y, Liu J, Zhao Z. RF-Access: Barrier-Free Access Control Systems with UHF RFID. Applied Sciences. 2022; 12(22):11592. https://doi.org/10.3390/app122211592
Chicago/Turabian StyleWang, Xuan, Xia Wang, Yingli Yan, Jia Liu, and Zhihong Zhao. 2022. "RF-Access: Barrier-Free Access Control Systems with UHF RFID" Applied Sciences 12, no. 22: 11592. https://doi.org/10.3390/app122211592
APA StyleWang, X., Wang, X., Yan, Y., Liu, J., & Zhao, Z. (2022). RF-Access: Barrier-Free Access Control Systems with UHF RFID. Applied Sciences, 12(22), 11592. https://doi.org/10.3390/app122211592








