Abstract
Cloud storage services are an important application of cloud computing. An increasing number of data owners store their data on cloud platforms. Since cloud platforms are far away from users, data security and privacy protection are very important issues that need to be addressed. Identity-based broadcast encryption (IBBE) is an important method to provide security and privacy protection for cloud storage services. Because the side channel attacks may lead to the disclosure of the key information of the cryptographic system, which will damage the security of the system, this paper provides an identity-based broadcast encryption with leakage resilience by state partition (LR-SP-IBBE). By using a binary extractor to compensate for the loss in entropy of the symmetric key caused by side-channel attacks, the proposed scheme randomizes the encapsulated symmetric key. Furthermore, using a state partition technique, we split the private key into two parts, and the corresponding decryption was divided into two stages. Through the double-system encryption skill, the security and leakage-resilience were proved in the composite order group model.
1. Introduction
Cloud storage services are closely related to people’s daily production and life [1,2]. In the Internet environment, people will use cloud storage services more or less. Privacy protection is an important feature of cloud data security. Privacy protection refers to the security of user identity and data privacy. At present, privacy protection has attracted more and more attention and has become a key bottleneck for the further development of the cloud. More effective protection technologies in the cloud environment include identity-based cryptosystems [3,4], attribute-based cryptosystems [5,6,7], etc. In view of security issues, cloud server providers should only allow legitimate users to access and manipulate data.
Unfortunately, side-channel attacks [8,9,10,11,12,13] have been discovered in recent years. Through some characteristic information such as the algorithm execution time and power loss, attackers can reveal some important information of the cryptographic system, even secret information such as private keys. Thus, side-channel attacks can lead to the insecurity of the cryptographic system. As a very important type of encryption system, the identity-based broadcast encryption (IBBE) system received great attention, and many achievements of IBBE emerged. However, there are few broadcast encryption schemes that can resist side-channel attacks. This paper presents a security model of a leakage-resilient broadcast encryption scheme for cloud storage services and proposes a specific broadcast encryption scheme that can resist side-channel attacks. The safety proof and an analysis of the leakage resilience are given.
2. Related Works
In this section, we first introduce the research status of anonymous broadcast encryption. Then, the research progress of identity-based encryption with leakage resilience is introduced. Finally, our motivations and contributions are explained.
2.1. Anonymous Broadcast Encryption
For broadcast encryption (BE) schemes, the sender may send an encrypted message to many users. In a BE scheme, broadcasters usually encrypt messages by combining the public identity of the receiver and system parameters to reveal the identity of the receiver to the public and thus attract attention to user privacy. Most identity-based broadcast encryption schemes have no anonymity, so the attackers may obtain some information about those identities from that ciphertext. Fortunately, some anonymous broadcast encryption schemes have been constructed.
Libert B, et al. [14] provided the definition of anonymous BE (ANOBE) and two general constructions of ANOBE. Their first scheme came from a public key encryption (PKE) scheme. Their second scheme came from an IBE scheme whose security is weak.
The paper [15] presented the idea of an anonymous IBBE (AIBBE) on a server and proposed a concrete scheme with random oracle by pairing. Both the encryption and decryption operations were relatively easy. However, their scheme was secure against the chosen plaintext attack.
Li X, et al. [16] provided an effective anonymous IBBE scheme by a prime order bilinear group in which no attacker could obtain the receivers’ identity from the given ciphertext. Their scheme has a fixed ciphertext size. They proved the security through the assumption of an asymmetric decision bilinear Diffie Hellman exponent (DBDHE) in the standard model.
Ren Y, et al. [17] proposed a completely anonymous IBBE construction using asymmetric bilinear groups. The construction achieved adaptive security and had no random oracle. Any attacker could not obtain the receivers’ identity from the given ciphertext. Each receiver was an anonymous receiver to other receivers. Only the broadcaster knew all the receivers. This scheme could achieve both semantic security and receiver anonymity. Mandal M [18] pointed out that the construction in Ren Y, et al. [17] did not provide the security requirements of message indistinguishability for broadcast encryption. In addition, Mandal M made some improvements to the scheme and constructed a secure and anonymous IBBE.
The reference [19] proposed the first IBBE scheme that achieved both confidentiality and complete anonymity using standard assumptions. The scheme also provided two other required features. One was full collusion resistance; that is to say, even if all external recipients colluded, they could not obtain information in the plaintext. The other was statelessness; that is to say, when a user joined or left the system, other users of the system did not need to update the private key.
The authors of [20] provided a novel AIBBE and proved that their scheme had security against the chosen ciphertext attacks (CCAs) using a random oracle. Based on a comparison with the other four schemes, their scheme was the most effective one.
The reference [21] put forward a general AIBBE that provided confidentiality of information and anonymity of users against CCA. The lengths of the public key and private key were fixed. The decryption calculation was independent of the number of receivers. Therefore, regardless of the perspective, this construction was suitable for the information management system of a smart city.
Zhou Y, et al. [22] designed an updatable identity-based hash proof system (IB-HPS). They updated the private key and added some new random values to one new private key. The new private key had the same distribution as the old one. By using an updatable IB-HPS, they provided a general continual leakage-resilient IBE under a random oracle model.
The reference [23] constructed a receiver-anonymous BE for ciphertext-policy attribute-based encryption (CP-ABBE) that could protect the access structure and the description of the broadcast set related to the ciphertext. The scheme realized complete security and a constant size of the ciphertext.
Ming Y, et al. [24] presented a new anonymous IBBE scheme using asymmetric bilinear pairing. With the help of the dual pairing vector space, they proved the security using the double system encryption method.
Chen L, et al. [25] provided an effective anonymous IBBE construction and applied it to a cloud storage service. In their scheme, the ciphertext length, public parameter length, and user’s private key length were fixed.
The paper [26] put forward an IBBE that was appropriate in open networks. For their scheme, although any sender could send the encrypted information to the target users, the authorized receivers could retrieve the encrypted message. Compared with other constructions of the open network of the IBBE scheme, the decryption key of the scheme was shorter and computation and transmission costs were low.
Chen L, et al. [27] provided the concept for a personalized message BE based on anonymous certificates (ANON-CBBE-PM). They also provided an ANON-CBBE-PM construction.
Mandal M, et al. [28] introduced a BE with personalized messages (BEPM) paradigm. In addition to its adaptive security, their construction could withstand indistinguishable selective plaintext attacks without using random oracle models. Their construction had a fixed ciphertext size and was very ideal for lightweight devices.
The paper [29] presented an IBBE that could simultaneously achieve confidentiality and outsider anonymity under the difficulty of the learning with error (LWE) problem. Their encryption and decryption algorithms were more efficient.
2.2. Leakage Resilience of IBE
According to the ability of side-channel attacks, the leakage-resilient model is divided into the bounded-leakage case and continuous-leakage case. As for the bounded leakage case [30], the leakage amount of the secret information of the system cannot exceed a given limit. As for the continuous-leakage case [31], its private key is usually updated, and the life cycle of the cryptographic mechanism is divided into multiple time cycles by performing corresponding operations (such as key update). In each time cycle, the adversary can obtain some related context for one private key and the exposed amount for this same secret value cannot exceed the leakage parameters set by the system, but the entire execution process can have an unlimited amount of leakage. The continuous-leakage model is closer to the application requirements of the real environment.
Cryptographic researchers have done some research on the leakage resilience of some cryptosystems such as the PKE cryptosystem [32], identity-based cryptographic mechanism [33,34,35], attribute-based cryptographic mechanism [36,37], key exchange protocol [38], and signature [39]. Research on leakage resilience of cryptographic mechanisms is a hot topic in cryptography research.
At present, leakage-resilient achievements mainly occur in identity-based cryptosystems.
The work [40] proposed the first identity-based encryption (IBE) construction with leakage resilience and provided the security proof without a random oracle. Alwen J. [41] proposed an IB-HPS and provided an encryption scheme against bounded-leakage attacks under IB-HPS. Li et al. [42] designed an IBE against bounded-leak attacks. Li et al. applied hash proof technology to a variant scheme of Gentry’s IBE with CCA security and constructed a new and effective leakage-resilient IBE. The reference [43] put forward a leakage-resilient IBE by using the global hash structure. Their construction was implemented through the deterministic linear Diffie–Hellman assumption under the relative-leakage model using a random oracle. The reference [44] provided an IBE with leakage resilience with leakage parameters that were not limited by the length of the message to be encrypted. Chen et al. [45] provided several specific examples of IB-HPS.
The paper [46] pointed out that the IBE against continuous side-channel attacks had stronger practicability. In the continual-leakage-resilient circumstances, the system refreshed the private key and erased the old key periodically. In this process, the public key was unchanged. The leakage of this model only existed between key refreshes. Specifically, the leakage between two consecutive refreshes was limited, but the overall amount of leakage was unlimited. In the case that the hardware did not leak information and in the continuous-leakage model, Zhou et al. [47] proposed an IBE against continual-leakage attacks without a random oracle. Zhang et al. [48] provided a secure big data storage system that was able to resist continuous key leakage. The paper [49] pointed out that blockchain technology could be used to solve the problem of data-tampering prevention in a decentralized environment. The paper [50] provided a comprehensive review of the latest research progress on resilient and dependable management approaches. They provided seven classifications, systematically analyzed the advantages and disadvantages of the schemes, and pointed out the schemes that could be further studied.
Because the leakage circumstances for different application environments are different, the actual application requirements of different environments in reality cannot be met with a constant leakage boundary. To dynamically set the leakage boundary of an IBE mechanism according to the requirements of the application environment, the authors of [51] designed a leakage-resilient IBE mechanism with flexible changes in the leakage boundary. The upper leakage limit of the IBE mechanism could be controlled by changing the corresponding initialization parameters, which effectively achieved the on-demand design goal of the leakage limit; that is to say, the mechanism could improve the leakage-resilience ability of the mechanism by increasing the length of one private key without changing the public parameter.
2.3. Our Motivations and Contributions
Zhang et al. [52] designed a novel leakage-resilient hierarchical IBE mechanism to provide anonymity protection for recipients. Zhang et al. [53] constructed a hierarchical IBE with anonymity against leakage attacks and provided the application scenario of the scheme. The work [54] proposed an anonymous IBE using a dual-system technique. Their construction was implemented with the aid of the composite order bilinear group and was secure in the fully adaptive identity model. Sun et al. [55] designed a completely secure leakage-resilient IBE mechanism with a wildcard key derivation function. Because no anonymous IBBE against leakage attacks had been put forward, this paper constructed an anonymous IBBE scheme against side-channel attacks.
A secret sharing scheme proposed by Xiong et al. [56] could resist persistent side-channel attacks and mainly benefited from the state partitioning technology. Since then, state partitioning technology has been widely used to construct some cryptographic systems with special performance. Liu et al. [57] ensured the security of their scheme for simultaneous continuous state partition exposure and tampering attacks with the help of general reference strings, nonextensible code, and other technologies.
Fanio et al. [58] divided their code into two parts. By using the refresh process based on state partitioning, the nonextensible code could resist persistent leakage attacks. For some schemes based on state partitioning, the state is usually divided into two parts, but there are also four and eight parts [59,60].
Since the dual-system technology [61] was introduced as the security proof, a lot of work has been carried out along this main line. In the dual-system technology, the key and ciphertext appear in two states: normal and semifunctional. Normal ciphertext is correctly decrypted by any key, but semifunctional ciphertext is not correctly decrypted by the semifunctional key. The orthogonality of subgroup elements can be fully utilized to carry effective information and hide invalid information. The references [37,39,46] proved the leakage-resilient security of some schemes through dual-system encryption technology.
Among the anonymous broadcast encryption schemes, there is no leakage-resilient encryption scheme at present. On the basis of [62], this paper provides an anonymous broadcast encryption scheme against continual side-channel attacks.
We used the following two figures to illustrate the differences between this scheme and the original scheme in [62]. Figure 1 shows the encryption and decryption system of the scheme in [62]. Figure 2 shows the encryption and decryption system of our scheme. There were two main technical differences. The first was the use of extractors. The second was the use of state partitioning technology, which divided the decryption step into two stages. CSP denotes the cloud server provider. The encryption algorithm and decryption algorithm will be specified in Section 4.
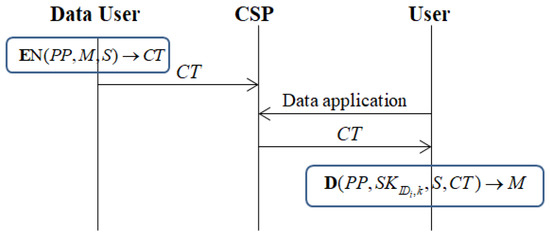
Figure 1.
The encryption and decryption system of the scheme in [62].
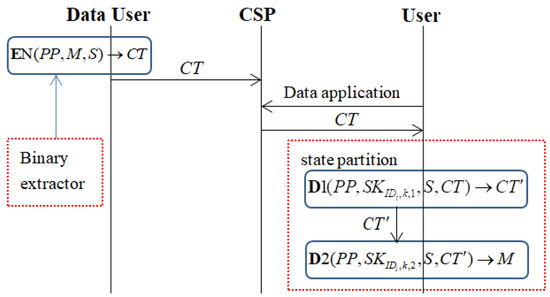
Figure 2.
The encryption and decryption system of our scheme.
First, we divided a private key into two states through the state partitioning technology. The private key had a fixed size, which was an important index to be considered in the broadcast encryption scheme. This was different from some current leakage-resilient encryption schemes. Some current encryption schemes obtain certain entropy through lengthening of the private key. This private key has sufficient redundancy to ensure that the security of the private key can be maintained in case of leakage in side-channel attacks.
Secondly, because the key for encrypting the plaintext was the encapsulated symmetric key, the symmetric key was subject to leakage-resilient processing through the extractor technology. Thus, the symmetric key could resist side-channel attacks, and the relative leakage ratio for the private key could almost reach 1.
Thirdly, the scheme given in this paper was anonymous. The presented scheme could effectively provide privacy protection for the receiver. In the IBBE scheme, the anonymity of users was related to its privacy protection.
Figure 3 shows the system structure of our anonymous IBBE against leakage attacks. There were three roles in the system: private key generator (PKG), cloud server provider (CSP), and user. Users were divided into data owners and data users. The private key generation center produced the private key and public key for every user. The data owner encrypted one piece of information according to the identity of some selected users and then transmitted the ciphertext to the CSP. The authorized users correctly decrypted the ciphertext that was downloaded from the CSP, while unauthorized users were not able to decrypt the ciphertext. In addition, onlookers could not obtain some identity information about the users from the ciphertext.
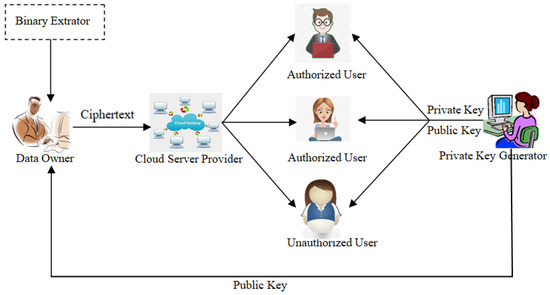
Figure 3.
The entire structure of our anonymous IBBE scheme against leakage attack.
3. Preliminary Knowledge
This section provides the basic concepts that are used in this paper such as bilinear mapping, binary extractor, etc. In addition, this section also lists several basic assumptions that had to be used in the safety proof of our scheme.
3.1. Bilinear Map
Definition 1.
Letanddenote two different multiplicative cyclic groups. Letdenote a generator forand let the bilinear map satisfy the next three conditions:
- (a)
- Computability: ,can be computed effectively.
- (b)
- Nondegeneration: .
- (c)
- Bilinearity: and;.
3.2. Minimum Entropy
Definition 2.
The statistical distance of a random variable and another variable is expressed as .
Definition 3.
The minimum entropy of one variable is expressed by ; this is a measure of the uncertainty of this variable. The conditional mean minimum entropy for one variable with respect to is expressed by , which is the measure of uncertainty of the variable under the condition that exists.
Conclusion 1
([63]). If ,, and are three random variables and has values, .
3.3. Binary Extractor
Definition 4.
A binary function is called a strong extractor [64] if the following clause holds: is the uniform distribution over ; is the uniform distribution over ; and as long as and , there is ( can be ignored).
3.4. General Subgroup Decision Hypothesis
The paper [65] introduced the concept of a bilinear group with a composite order. We used to represent a bilinear group generation algorithm for the composite order. inputs safety parameters and outputs the formalization of the bilinear group with the composite order , where , , and are three different primes that are bits in length (that is to say, ). is a cyclic group with order , as is . : is one bilinear map. is determined by the safety parameter.
, and are used to represent subgroups of order , , and , respectively. The subgroups of order in the group are represented by . If an element is expressed by the product of a member of and a member of , these two parts are called the part of and the part of . Assuming and (), we obtain = 1. So, and are orthogonal. For example, this shows how and are orthogonal. Suppose can generate , can generate , can generate , and can generate . It can then be obtained that . Therefore, and are orthogonal.
The following three hypotheses given in references [61,66,67] will be used in our proof. For , it was assumed that is the generator of .
Hypothesis 1.
Consider that the algorithm generates a bilinear group with composite order. Given the following distribution:
Any attack does not distinguish between and .
The advantage that the adversary destroys Hypothesis 1 is expressed by .
If it is negligible for every PPT adversary, Hypothesis 1 is said to be true.
Hypothesis 2.
Consider that the algorithm generates a bilinear group with composite order. Given the following distribution:
Any attack does not distinguish between and
The advantage that the adversary destroys Hypothesis 2 is expressed by .
If it is negligible for every PPT adversary, Hypothesis 2 is said to be true.
Hypothesis 3.
Consider that the algorithm generates a bilinear group with composite order. Given the following distribution:
Any attack does not distinguish between and
The advantage that the adversary destroys Hypothesis 3 is expressed by .
If it is negligible for every PPT adversary, Hypothesis 3 is said to be true.
4. Syntax about LR-SP-IBBE
This section provides the formal description and security semantics of identity-based broadcast encryption with leakage resilience by state partition (LR-SP-IBBE).
Figure 4 gives the relations of the algorithms; the specific algorithms will be detailed in Section 4.1.
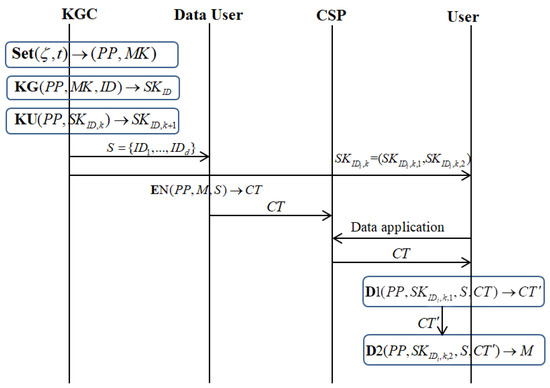
Figure 4.
The relations of the algorithms of the proposed scheme.
4.1. Formalization of LR-SP-IBBE
Based on the work in [62,68], the formal definition of LR-SP-IBBE is given below. The LR-SP-IBBE was composed of the following algorithms:
Initialization.. This inputs the security parameters and the upper bound of users. The algorithm produces the public parameter and the master private key . is open to all users. is kept as a secret.
Private key generation.. The algorithm inputs the public parameters , the master private key , and one user’s identity . It generates one private key: .
Private key update.. This inputs and and outputs the updated private key .
Encryption. . This takes and one identity set () as the input and outputs , where is the headers and is a symmetric key that is used to encrypt the plaintext . If the broadcaster is about to send the ciphertext corresponding to the plaintext , they encrypts with , which generates the ciphertext and broadcasts .
Decryption1.. This inputs , private keys , user identity sets , and ciphertext . First, it divides into . If , the algorithm calculates the part plaintext of .
Decryption2.. This inputs , private keys , user identity sets , and ciphertext . First, it divides into . If , the algorithm uses to calculate the symmetric key . Then, the plaintext message is recovered by .
Semifunctional private key generation. . The algorithm inputs , , and one identity . It generates the semifunctional private key .
Semifunctional encryption. . This inputs , , and . It gains the semifunctional ciphertext .
The first three algorithms were run by the key generation center (KGC), and the other algorithms were run by the user. The last two algorithms were only used for the security proof.
4.2. Security Descriptions for LR-SP-IBBE
The security for the LR-SP-IBBE scheme could be achieved through an interactive game that was executed by one challenger and one adversary . This scheme obtained the security against the chosen ciphertext attack.
The security for LR-SP-IBBE was described through the game . In , the challenger maintained a table,
, where , , , , and are the handles’ space, identities’ space, symmetric keys’ space, private keys’ space, and the leakage amount’s space, respectively. Assume
and .
:
Initialization: By running the initialization algorithm, the challenger produced the public parameters and the master private key . gives to , then keeps in secret.
Stage 1: the adversary conducted the following inquires.
. Given one identity , searched for the item corresponding to in the list . In the event that the corresponding item was found in the list , the challenger ended the operation. Otherwise, obtained one private key by running the private key generation algorithm and updated . The challenger put in .
. Given the identity , chose one arbitrary leak function . input the symmetric key. sent the outcome of to the adversary . The limitation was that the output could not extend a bound. The information obtained from the output of this leakage function was related to the one encapsulated symmetric key .
Specifically, sought an item for the handle in the table provided that was found. determined whether or not, where is the maximum value that allowed private key disclosure. If , the challenger sent to and updated with . Otherwise, the challenger would output ⊥.
. inquired about one private key of the handle . looked for an item corresponding to the handle in the table . In the event that was found, gave to the adversary.
. inquired about the updating of the private key corresponding to the handle . looked for one item corresponding to the handle in . Provided that was found, ran the updating algorithm to obtain the new private key . The challenger then gave the new private key and updated to .
. The adversary inquired about the plaintext of , and the challenger looked up the list and found the private key . invoked the decryption algorithm . If , the challenger calculated the part of plaintext and sent it to .
. inquired about the plaintext of , and the challenger looked up the list and found the private key . invoked the decryption algorithm . First, it divided into . If , the challenger used to calculate the symmetric key . Then, the plaintext message was recovered by and was sent to .
Challenge. offered the message and with an equal length. randomly selected . Then, input the public parameters and user set () and output . The challenger obtained by encrypting with . The ciphertext was . The challenger broadcasted .
Stage 2. could ask for , , , and . The basic limitations were the same as those in Stage 1. Other restrictions were that the adversary could not inquire about and . In addition, a leakage inquiry was not allowed, Because if it were allowed, could win the game in an ordinary way.
Guess. provided a conjecture . If , wins . The advantage of winning the game was defined as .
Supposing every adversary only achieved negligible advantages in the game , our LR-SP-IBBE scheme had leakage-resilience.
5. Specific Construction of LR-SP-IBBE
We used to represent a bilinear group generation algorithm for the composite order. input safety parameters and output the formalization of the bilinear group with the composite order , where , , and are three different primes with a bit length (that is to say, ). was a cyclic group with order , as was . : is one bilinear map. was determined by the safety parameter.
It was assumed that any identity information was a member of and any message was a member of . Suppose that , and are the generators of the subgroups , and . The first subgroup carried some primary information for the plaintext and every user’s private key. offered the semifunctionality that was used in the security proof. randomized the private key.
Initialization. was used to represent the maximum number of users. It randomly selected ,, and . It selected a strong binary extractor .
The public parameter was .
The master private key was .
Private key generation. For an identity where , () is the target users. The algorithm input , , and one user’s identity . It randomly selected , , , and . It set and generated the private key , where and .
Private key update. This input and and produced one new private key . For , where and , it randomly selected and generated one new private key , where and .
Since were all random, and were also random. The private keys and had the same distribution. Without losing generality, the original was used for convenience.
Encryption. This took the message and an identity set of the receivers as input. It randomly selected and . Then, it calculated the ciphertext .
The symmetric encryption key was . was sent to the receivers.
Decryption1. If one receiver belongs to , it split into two parts . This receiver ran the decryption algorithm . This receiver calculated the part of the plaintext using .
First, the receiver used to compute , where and .
Decryption2.. This receiver input , private key , identity sets , and ciphertexts . Suppose ; this receiver first calculated . The plaintext message was recovered by decrypting using .
First, it used to compute:
Semifunctional private key generation. For the private keys , where and , it randomly selected and generated the semifunctional private key , where and .
Semifunctional encryption. By revoking the normal encryption algorithm, it gained the general ciphertext .
Then, it randomly selected and generated the semifunctional ciphertext .
The first three algorithms were run by the key generation center (KGC); the other algorithms were run by the user.
6. Safety Proof
The scheme was safe in the standard model.
Theorem 1.
Considering that the symmetric key hasbits leakage, if Hypothesis 1, Hypothesis 2, and Hypothesis 3 hold, the presented LR-SP-IBBE scheme has CCA security under the standard model.
The proof was finished through a number of games. These games were modified versions of the real security game. For the last game, the opponent’s advantage was 0. The first game was a real one. We proved the indiscernibility of any two consecutive games. Therefore, the security of this scheme could be obtained. indicates the number of private key queries in one game.
The definition of these games is given below:.
. This is the real interactive game for LR-SP-IBBE that is played by the challenger and the attacker.
. This is very similar to , but the only difference is that in , the challenger generates semifunctional ciphertext.
(). The ciphertext appears in a semifunctional form. The previous private key responses are also semifunctional and the subsequent private key responses are normal. Especially for , all private key responses are semifunctional.
.This game is similar to except that in the game , the broadcaster encrypts a random message and in the game , the broadcaster selects any of the two challenge messages and encrypts it.
Proof.
We will finish the proof through the games , (), and and three lemmas. Through these three lemmas, we prove the indiscernibility of these games. In addition, the adversary has no advantage in . In this way, the security proof is finished. □
Table 1 illustrates some differences between the adversary advantages in two consecutive games. Here, we provide the conclusion on these three lemmas. Specific proofs of the three lemmas will be presented later. or was used to indicate the superiority achieved by over . We used or to indicate the superiority achieved by over (. We used or to indicate the advantage obtained by over .

Table 1.
The differences between the adversary’ advantages in two consecutive games.
From Table 1, we obtain:
So, . In addition, . We obtain . Thus, Theorem 1 is completed.
Lemma 1.
Considering that the symmetric key has bits of leakage, if there is an adversary such that , the challenger can destroy Hypothesis 1 with advantage
Proof.
Given the challenger , an instance , , and the challenge
( or ), and interacts as follows:
Initialization. Let indicate the maximum number of users. randomly selects , , and . sets up . selects a strong binary extractor .
The public parameters are .
The master private key is .
sends to .
Stage 1. asks for the private key of , where () is the set of users who can decrypt the ciphertext. randomly selects and and . Then, generates the private key: , where and .
responds to with the private key .
Challenge. gives the challenger an identity set and two messages and of the same size. randomly selects and . Then, calculates the ciphertext: .
Stage 2. continues to ask for the private key, but it requires that .
Guess. provides a guess about . If , wins the game.
Probability analysis. When ( and are randomly selected), properly simulates the game . When ( is randomly selected), properly simulates the game .
The joint distribution of all variables is represented by symbols . When there was no leakage, [65] showed that . Thus, the probability that the adversary received the invalid ciphertext in every decryption query was . When the symmetric key exposed bits of information, we obtained . Thus, the superiority that the adversary obtained in every decryption query was .
Therefore, the advantage of solving the difficult Hypothesis 1 using is . That is to say, if could distinguish and over advantage , the challenger could destroy Hypothesis 1 with the advantage . This contradicts Hypothesis 1. So, . □
Lemma 2.
Considering that the symmetric key hasbits of leakage, if there is an adversary such that (), the challenger destroys Hypothesis 2 with the advantage .
Proof.
Given the challenger , an instance and ( or ). interacts with as follows:
Initialization. Let indicate the maximum number of users. randomly selects , , and . sets up . selects a strong binary extractor .
The public parameters are .
The master private key is .
sends to .
Stage 1. makes a private key inquiry for , where . responds in the following three ways:
- (1)
- For , responds with the semifunctional key. randomly chooses and generates the semifunctional private key: where and .
- (2)
- For , produces a normal private key in response.
- (3)
- For , randomly selects , , and . Then, generates a private key: , where and .
If , this private key has a normal form, correctly plays the game .
If , the private key has a semifunctional form, correctly plays the game .
Challenge. sends one challenge identity group and two equal-length challenge messages and to . randomly selects and calculates the ciphertext: .
Stage 2. continues to make a private key inquiry for . The condition that needs to be met is .
Guess. outputs the guess about . If , wins the game.
Probability analysis. When , correctly simulates the game . When , correctly simulates the game . The joint distribution of all variables is represented by the symbol . When there is no leakage, the paper [65] shows that . Thus, the probability that the adversary receives the invalid ciphertext in every decryption query is . When the symmetric key exposes bits of information, we obtain that . Thus, the probability that the adversary receives the invalid ciphertext in every decryption query is .
Therefore, the advantage of solving the difficult Hypothesis 2 using is . That is to say, if can distinguish and over advantage , the challenger can destroy Hypothesis 2 with the advantage . This contradicts Hypothesis 2. So, .
By the same token, for to , we obtain ,…, . Therefore,
In addition, (the proof will be given in Lemma 3). In this way, we can obtain:
This indicates that the advantage of can be ignored in . Lemma 2 is proved. □
Lemma 3.
Considering that the symmetric key has bits of leakage, if there is an adversary such that , the challenger destroys Hypothesis 3 with the advantage .
Proof.
Given the challenger , an instance and a challenge item ( or ). interacts with as follows.
Initialization. Let indicate the maximum number of users. randomly selects , , and . sets up . selects a strong binary extractor .
The public parameters are .
The master private key is .
sends to .
Stage 1. asks for the private key of , where () is the intended receivers’ collection. randomly selects . Then, generates the semifunctional private key: , where and .
responds to with the private key .
Challenge. sends one challenge identity group and two equal-length challenge messages and to . randomly selects and calculates the ciphertext: .
Stage 2. continues to make a private key inquiry for . The conditions that need to be met are .
Guess. outputs a guess about . If , wins the game.
Probability analysis. If , correctly simulates the game . When , correctly simulates the game . The joint distribution of all variables is represented by the symbol . When there is no leakage, [69] shows that . Thus, the probability that the adversary receives the invalid ciphertext in every decryption query is . When the symmetric key exposes bits of information, we obtain . Thus, the probability that the adversary receives the invalid ciphertext in every decryption query is .
Therefore, the advantage of solving the difficult Hypothesis 3 using is . That is to say, if can distinguish and over advantage , the challenger can destroy Hypothesis 3 with the advantage . This contradicts Hypothesis 3. So, . Lemma 3 is proved. □
Theorem 2.
The LR-SP-IBBE scheme has the performance of continuous leakage resilience.
Proof.
Similar to [35], the given scheme LR-SP-IBBE obtains continuous leakage resilience by refreshing the private key periodically. The update algorithm inputs and public parameters and achieves one update secret key . In the update procedure, an additional value is added to the random value of the original exponent of one private key. Since the newly added value is randomly selected from , the distribution of this new private key is the same as that of the original one. After the private key update algorithm ran, we obtained one fresh private key. Thus, the proposed scheme had continuous leakage resilience. □
Theorem 3.
The relative leakage rate of the symmetric key of LR-SP-IBBE is
Proof.
When the symmetric key is not disclosed,, where represents the adversary and represents the joint distribution of all variables. The adversary can obtain the bits of information for the symmetric key by a side-channel attack. This indicates that the variable is bits in length. By means of conclusion 1, . In this way, if the extractor is selected, , where represents a uniform distribution. Thus, when is close to zero, the leakage is close to . Then, and uniform distribution are indistinguishable. Therefore, the relative leakage rate is: . □
7. Performance Analysis
We will now provide the comparisons of our scheme and some other classical schemes regarding security and storage efficiency. Table 2 shows the safety comparison. STD stands for standard model, ROM stands for random oracle model, FS stands for full security, GSD stands for general subgroup decision assumption, DBDH means the decisional bilinear Diffie–Hellman assumption, DBDHE indicates the asymmetric DBDH exponent assumption, and n-BDHE indicates the decision n-bilinear Deffie–Hellman exponent problem.

Table 2.
Security comparisons of some related schemes.
The model column indicates whether the scheme achieved security under the standard model (STD) or the random oracle model (ROM). The assumption column describes the difficult problem assumption on which the scheme depended. Anonymity indicates whether the scheme was anonymous. Leakage-resilience indicates whether the scheme had the feature of resisting private key disclosure. Table 2 shows that our scheme had security, anonymity, and leakage resilience under STD. This is the best security at present.
Table 3 shows the storage efficiency comparisons. is used to represent the number of all users, is the number of the intended receivers, represents the length of the elements in group (others are similar), and is a value that can be changed and is related to the leakage rate.

Table 3.
Comparisons of Storage Efficiency.
Table 3 indicates that our scheme had the shortest ciphertext length, like that in [62]. Compared with the same type of schemes [35,62] and based on a composite order group, our scheme also had the shortest public key length. Because the schemes in [19,21] were constructed using a prime order group, their public key was relatively short. In terms of the private key length, our scheme adopted state partitioning technology, so the private key length was twice that of [62], on which ours was based.
8. Conclusions
This paper provided the syntax expression and security formulation of LR-SP-IBBE and proposed an LR-SP-IBBE construction. The proposed construction had continual leakage resilience. Based on the general subgroup decision hypothesis, our proved to be secure under STD. By comparing the efficiency of our proposed scheme and relevant ones, our scheme had a better performance. The relative leakage ratio could almost reach 1. The scheme had the following advantages.
The scheme had a continuous leakage-resilient performance, which can better reflect real application scenarios. In real applications, adversaries generally have a long-term attack capability.
The scheme had a good leakage-resilient performance, and the almost complete disclosure of the encapsulated symmetric key could also ensure the security of the scheme, which benefited from the use of the extractor. The entropy lost by the symmetric key could be supplemented through the extractor so that the symmetric key had enough entropy to continue to maintain confidentiality.
The scheme had anonymity that well protected the privacy of users. Users are very sensitive to privacy. They all want to effectively protect their privacy while also making cloud storage convenient. Therefore, the scheme proposed in this paper is very suitable for applications such as cloud storage services.
In a health diagnosis system, patient data are very large and usually needs to be stored on a cloud platform. In light of personal privacy, the data need to be secure and anonymous. This system is very suitable for such application scenarios.
Generally speaking, the computational efficiency of schemes in prime order groups is better than that in composite order groups. A method for constructing an anonymous broadcast encryption scheme in a prime order group is a subject we will study in the future.
Author Contributions
Conceptualization and methodology, Q.Y. and J.L.; formal analysis, Q.Y. and S.J.; writing—original draft preparation, Q.Y.; writing—review and editing, Q.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (grant Numbers: 62172292, 62072104, 61972095, and U21A20465).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Mohiyuddin, A.; Javed, A.R.; Chakraborty, C.; Rizwan, M.; Shabbir, M.; Nebhen, J. Secure cloud storage for medical IoT data using adaptive neuro-fuzzy inference system. Int. J. Fuzzy Syst. 2022, 24, 1203–1215. [Google Scholar] [CrossRef]
- Yuan, Y.; Zhang, J.; Xu, W.; Li, Z. Identity-based public data integrity verification scheme in cloud storage system via blockchain. J. Supercomput. 2022, 78, 8509–8530. [Google Scholar] [CrossRef]
- Yang, Y.; Chen, Y.; Chen, F.; Chen, J. An efficient identity-based provable data possession protocol with compressed cloud storage. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1359–1371. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Role based access control using identity and broadcast based encryption for securing cloud data. J. Comput. Virol. Hacking 2022, 18, 171–182. [Google Scholar] [CrossRef]
- Chinnasamy, P.; Deepalakshmi, P.; Dutta, A.K.; You, J.; Joshi, G.P. Ciphertext-policy attribute-based encryption for cloud storage: Toward data privacy and authentication in AI-enabled IoT system. Mathematics 2021, 10, 68. [Google Scholar] [CrossRef]
- Xue, Y.; Xue, K.; Gai, N.; Hong, J.; Wei, D.S.L.; Hong, P. An attribute-based controlled collaborative access control scheme for public cloud storage. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2927–2942. [Google Scholar] [CrossRef]
- Chen, L.; Li, J.; Lu, Y.; Zhang, Y. Adaptively secure certificate-based broadcast encryption and its application to cloud storage service. Inf. Sci. 2020, 538, 273–289. [Google Scholar] [CrossRef]
- Kumar, S.; Dasu, V.A.; Baksi, A.; Sarkar, S.; Jap, D.; Breier, J.; Bhasin, S. Side channel attack on stream ciphers: A three-step approach to state/key recovery. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2022, 2022, 166–191. [Google Scholar] [CrossRef]
- Das, D.; Ghosh, S.; Raychowdhury, A.; Sen, S. EM/power side-channel attack: White-box modeling and signature attenuation countermeasures. IEEE Des. Test 2021, 38, 67–75. [Google Scholar] [CrossRef]
- Won, Y.S.; Chatterjee, S.; Jap, D.; Bhasin, S.; Basu, A. Time to leak: Cross-device timing attack on edge deep learning accelerator. In Proceedings of the 2021 International Conference on Electronics, Information, and Communication (ICEIC), Jeju, Korea, 31 January–3 February 2021. [Google Scholar]
- Chen, C.S.; Wang, T.; Tian, J. Improving timing attack on RSA-CRT via error detection and correction strategy. Inf. Sci. 2013, 232, 464–474. [Google Scholar] [CrossRef]
- Halderman, J.A.; Schoen, S.D.; Heninger, N.; Clarkson, W.; Paul, W.; Calandrino, J.A.; Feldman, A.J.; Appelbaum, J.; Felten, E.W. Lest we remember: Cold-Boot attacks on encryption keys. Commun. ACM 2009, 52, 91–98. [Google Scholar] [CrossRef]
- Lipp, M.; Schwarz, M.; Gruss, D.; Prescher, T.; Haas, W.; Horn, J.; Mangard, S.; Kocher, P.; Genkin, D.; Yarom, Y.; et al. Meltdown: Reading kernel memory from user space. Commun. ACM 2020, 63, 46–56. [Google Scholar] [CrossRef]
- Libert, B.; Paterson, K.G.; Quaglia, E.A. Anonymous broadcast encryption: Adaptive security and efficient constructions in the standard model. In Proceedings of the 15th International Conference on Practice and Theory in Public Key Cryptography, Darmstadt, Germany, 21–23 May 2012. [Google Scholar]
- Cui, H.; Mu, Y.; Guo, F. Server-aided identity-based anonymous broadcast encryption. Int. J. Secur. Netw. 2013, 8, 29–39. [Google Scholar] [CrossRef]
- Xie, L.; Ren, Y. Efficient anonymous identity-based broadcast encryption without random oracles. Int. J. Digit. Crime Forensics 2014, 6, 40–51. [Google Scholar]
- Ren, Y.; Niu, Z.; Zhang, X. Fully anonymous identity-based broadcast encryption without random oracles. Int. J. Netw. Secur. 2014, 16, 256–264. [Google Scholar]
- Mandal, M. Cryptanalysis of RNZ, an identity-based fully anonymous broadcast encryption. ICT Express 2020, 6, 316–319. [Google Scholar] [CrossRef]
- He, K.; Weng, J.; Liu, J.N.; Liu, J.K.; Liu, W.; Deng, R.H. Anonymous identity-based broadcast encryption with chosen-ciphertext security. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016. [Google Scholar]
- Zhang, J.; Mao, J. Anonymous multi-receiver broadcast encryption scheme with strong security. Int. J. Embed. Syst. 2017, 9, 177–187. [Google Scholar] [CrossRef]
- He, K.; Weng, J.; Mao, Y.; Yuan, H. Anonymous identity-based broadcast encryption technology for smart city information system. Pers. Ubiquitous Comput. 2017, 21, 841–853. [Google Scholar] [CrossRef]
- Zhou, Y.; Yang, B.; Xia, Z.; Mu, Y.; Wang, T. Anonymous and updatable identity-based hash proof system. IEEE Syst. J. 2018, 13, 2818–2829. [Google Scholar] [CrossRef]
- Zhang, L.; Yin, H. Recipient anonymous ciphertext-policy attribute-based broadcast encryption. Int. J. Netw. Secur. 2018, 20, 168–176. [Google Scholar]
- Ming, Y.; Yuan, H. Fully secure anonymous identity based broadcast encryption with group of prime order. Int. J. Netw. Secur. 2019, 21, 7–16. [Google Scholar]
- Chen, L.; Li, J.; Zhang, Y. Adaptively secure anonymous identity-based broadcast encryption for data access control in cloud storage service. KSII Trans. Internet Inf. Syst. 2019, 13, 1523–1545. [Google Scholar]
- Mishra, P.; Verma, V. Identity based broadcast encryption scheme with shorter decryption keys for open networks. Wirel. Pers. Commun. 2020, 115, 961–969. [Google Scholar] [CrossRef]
- Chen, L.; Li, J.; Zhang, Y. Anonymous certificate-based broadcast encryption with personalized messages. IEEE Trans. Broadcast. 2020, 66, 867–881. [Google Scholar] [CrossRef]
- Mandal, M.; Nuida, K. Identity-based outsider anonymous broadcast encryption with simultaneous individual messaging. In Proceedings of the 14th International Conference on Network and System Security, Melbourne, VIC, Australia, 25–27 November 2020. [Google Scholar]
- He, K.; Liu, X.; Liu, J.N.; Liu, W. Efficient identity-based broadcast encryption scheme on lattices for the Internet of Things. Secur. Commun. Netw. 2021, 2021, 2847731. [Google Scholar] [CrossRef]
- Naor, M.; Segev, G. Public-key cryptosystems resilient to key leakage. In Proceedings of the 29th Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2009. [Google Scholar]
- Dodis, Y.; Haralambiev, K.; Lopez-Alt, A.; Wichs, D. Cryptography against continuous memory attacks. In Proceedings of the 51st Annual Symposium on Foundations of Computer Science, Las Vegas, NV, USA, 23–26 October 2010. [Google Scholar]
- Huang, M.; Yang, B.; Zhou, Y.; Hu, X. Continual leakage-resilient hedged public-key encryption. Comput. J. 2022, 65, 1574–1585. [Google Scholar] [CrossRef]
- Zhou, Y.; Yang, B.; Xia, Z.; Zhang, M.; Mu, Y. Identity-based encryption with leakage-amplified chosen-ciphertext attacks security. Theor. Comput. Sci. 2020, 809, 277–295. [Google Scholar] [CrossRef]
- Hou, H.; Yang, B.; Zhang, M.; Zhou, Y.; Huang, M. Fully secure wicked identity-based encryption resilient to continual auxiliary-inputs leakage. J. Inf. Secur. Appl. 2020, 53, 102521. [Google Scholar] [CrossRef]
- Li, J.; Yu, Q.; Zhang, Y. Identity-based broadcast encryption with continuous leakage resilience. Inf. Sci. 2018, 429, 177–193. [Google Scholar] [CrossRef]
- Tomita, T.; Ogata, W.; Kurosawa, K. Boosting CPA to CCA2 for leakage-resilient attribute-based encryption by using new QA-NIZK. IEICE Trans. Fundam. Electron. 2022, 105, 143–159. [Google Scholar] [CrossRef]
- Li, J.; Yu, Q.; Zhang, Y. Hierarchical attribute based encryption with continuous leakage-resilience. Inf. Sci. 2019, 484, 113–134. [Google Scholar] [CrossRef]
- Alawatugoda, J.; Okamoto, T. Standard model leakage-resilient authenticated key exchange using inner-product extractors. Des. Code Cryptogr. 2022, 90, 1059–1079. [Google Scholar] [CrossRef]
- Yu, Q.; Li, J.; Ji, S. Fully secure ID-based signature sheme with continuous leakage-resilience. Secur. Commun. Netw. 2022, 2022, 8220259. [Google Scholar]
- Alwen, J.; Dodis, Y.; Naor, M.; Segev, G.; Walfish, S.; Wichs, D. Public-key encryption in the bounded-retrieval model. In Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Riviera, France, 30 May–3 June 2010. [Google Scholar]
- Alwen, J.; Dodis, Y.; Wichs, D. Leakage-resilient public-key cryptography in the bounded-retrieval model. In Proceedings of the 29th Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, CA, USA, 16–20 August 2009. [Google Scholar]
- Li, J.; Teng, M.; Zhang, Y.; Yu, Q. A leakage-resilient CCA-secure identity-based encryption scheme. Comput. J. 2016, 59, 1066–1075. [Google Scholar] [CrossRef]
- Chen, Y.; Luo, S.; Chen, Z. A new leakage-resilient IBE scheme in the relative leakage model. In Proceedings of the 25th Annual IFIP WG 11.3 Conference on Data and Applications Security and Privacy, Richmond, VA, USA, 11–13 July 2011. [Google Scholar]
- Sun S, F.; Gu, D.; Liu, S. Efficient chosen ciphertext secure identity-based encryption against key leakage attacks. Secur. Commun. Netw. 2016, 9, 1417–1434. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, Z.; Lin, D.; Cao, Z. Generalized (identity-based) hash proof system and its applications. Secur. Commun. Netw. 2016, 9, 1698–1716. [Google Scholar] [CrossRef]
- Lewko, A.; Rouselakis, Y.; Waters, B. Achieving leakage resilience through dual system encryption. In Proceedings of the 8th Theory of Cryptography Conference on Theory of Cryptography, Providence, RI, USA, 28–30 March 2011. [Google Scholar]
- Zhou, Y.; Yang, B.; Mu, Y. Continuous leakage-resilient identity-based encryption without random oracles. Comput. J. 2018, 61, 586–600. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, M.; Zheng, D.; Lang, P.; Wu, A.; Chen, C. Efficient and secure big data storage system with leakage resilience in cloud computing. Soft Comput. 2018, 22, 7763–7772. [Google Scholar] [CrossRef]
- Gardas, B.B.; Heidari, A.; Navimipour, N.J.; Unal, M. A fuzzy-based method for objects selection in blockchain-enabled edge-IoT platforms using a hybrid multi-criteria decision-making model. Appl. Sci. 2022, 12, 8906. [Google Scholar] [CrossRef]
- Amiri, Z.; Heidari, A.; Navimipour, N.J.; Unal, M. Resilient and dependability management in distributed environments: A systematic and comprehensive literature review. Cluster Comput. 2022. [Google Scholar] [CrossRef]
- Zhou, Y.; Yang, B.; Mu, Y. Continuous leakage-resilient identity-based encryption with leakage amplification. Des. Code Cryptgr. 2019, 87, 2061–2090. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, M.; Zheng, D.; Zhang, T.; Guo, R.; Ren, F. Leakage-resilient hierarchical identity-based encryption with recipient anonymity. Int. J. Found. Comput. S. 2019, 30, 665–681. [Google Scholar] [CrossRef]
- Zhang, M.; Yang, B.; Wang, C.; Takagi, T. Unbounded anonymous hierarchical IBE with continual-key-leakage tolerance. Secur. Commun. Netw. 2014, 7, 1974–1987. [Google Scholar] [CrossRef]
- Liu, P.; Hu, C.; Guo, S.; Wang, Y. Anonymous identity-based encryption with bounded leakage resilience. In Proceedings of the IEEE 29th International Conference on Advanced Information Networking and Applications Workshops, Gwangju, Korea, 24–27 March 2015. [Google Scholar]
- Sun, S.F.; Gu, D.; Huang, Z. Fully secure wicked identity-based encryption against key leakage attacks. Comput. J. 2015, 58, 2520–2536. [Google Scholar] [CrossRef]
- Xiong, H.; Zhang, C.; Yuen, T.H.; Zhang, E.P.; Yiu, S.M.; Qing, S. Continual leakage-resilient dynamic secret sharing in the split-state model. In Proceedings of the 14th International Conference on Information and Communications Security, Hong Kong, China, 29–31 October 2012. [Google Scholar]
- Liu, F.H.; Lysyanskaya, A. Tamper and leakage resilience in the split-state model. In Proceedings of the 32nd Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012. [Google Scholar]
- Faonio, A.; Nielsen, J.B.; Simkin, M.; Venturi, D. Continuously non-malleable codes with split-state refresh. Theor. Comput. Sci. 2019, 759, 98–132. [Google Scholar] [CrossRef]
- Kanukurthi, B.; Obbattu, S.L.B.; Sekar, S. Four-state non-malleable codes with explicit constant rate. Comput. J. 2020, 33, 1044–1079. [Google Scholar] [CrossRef]
- Aggarwal, D.; Dottling, N.; Nielsen, J.B.; Obremski, M.; Purwanto, E. Continuous non-malleable codes in the 8-split-state model. In Proceedings of the 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019. [Google Scholar]
- Waters, B. Dual system encryption: Realizing fully secure IBE and HIBE under simple assumptions. In Proceedings of the 29th Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, CA, USA, 16–20 August 2009. [Google Scholar]
- Ming, Y.; Yuan, H.; Sun, B.; Qiao, Z. Efficient identity-based anonymous broadcast encryption scheme in standard model. J. Comput. Appl. 2016, 36, 2762–2766. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. SIAM J. Comput. 2008, 38, 97–139. [Google Scholar] [CrossRef]
- Nisan, N.; Zuckerman, D. Randomness is linear in space. J. Comput. Syst. Sci. 1996, 52, 43–52. [Google Scholar] [CrossRef]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF formulas on ciphertexts. In Proceedings of the Second Theory of Cryptography Conference, Cambridge, MA, USA, 10–12 February 2005. [Google Scholar]
- Xiong, H.; Yuen, T.H.; Zhang, C.; Yiu, S.M.; He, Y.J. Leakage-resilient certificateless public key encryption. In Proceedings of the 8th ACM Symposium on Information, Computer and Communications Security, Hangzhou, China, 8 May 2013. [Google Scholar]
- Lewko, A.; Waters, B. New techniques for dual system encryption and fully secure hibe with short ciphertexts. In Proceedings of the 7th Theory of Cryptography Conference, Zurich, Switzerland, 9–11 February 2010. [Google Scholar]
- Kim, J.; Susilo, W.; Au, H.; Seberry, J. Adaptively secure identity-based broadcast encryption with a constant-sized ciphertext. IEEE Trans. Inf. Forensics Secur. 2015, 10, 679–693. [Google Scholar]
- Gentry, C. Practical identity-based encryption without random oracles. In Proceedings of the 25th International Conference on the Theory and Applications of Cryptographic Techniques, St. Petersburg, Russia, 28 May–1 June 2006. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).