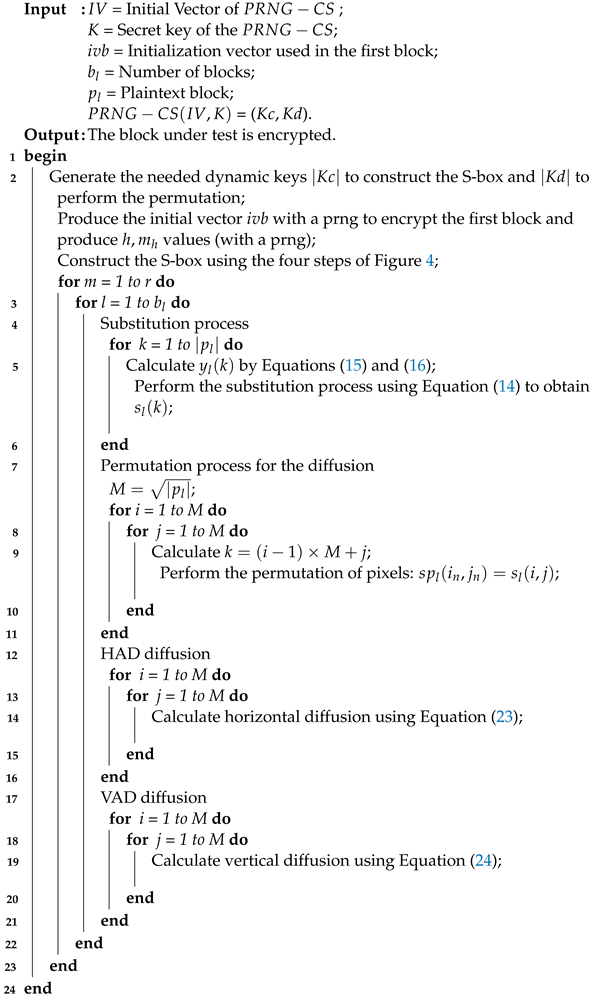
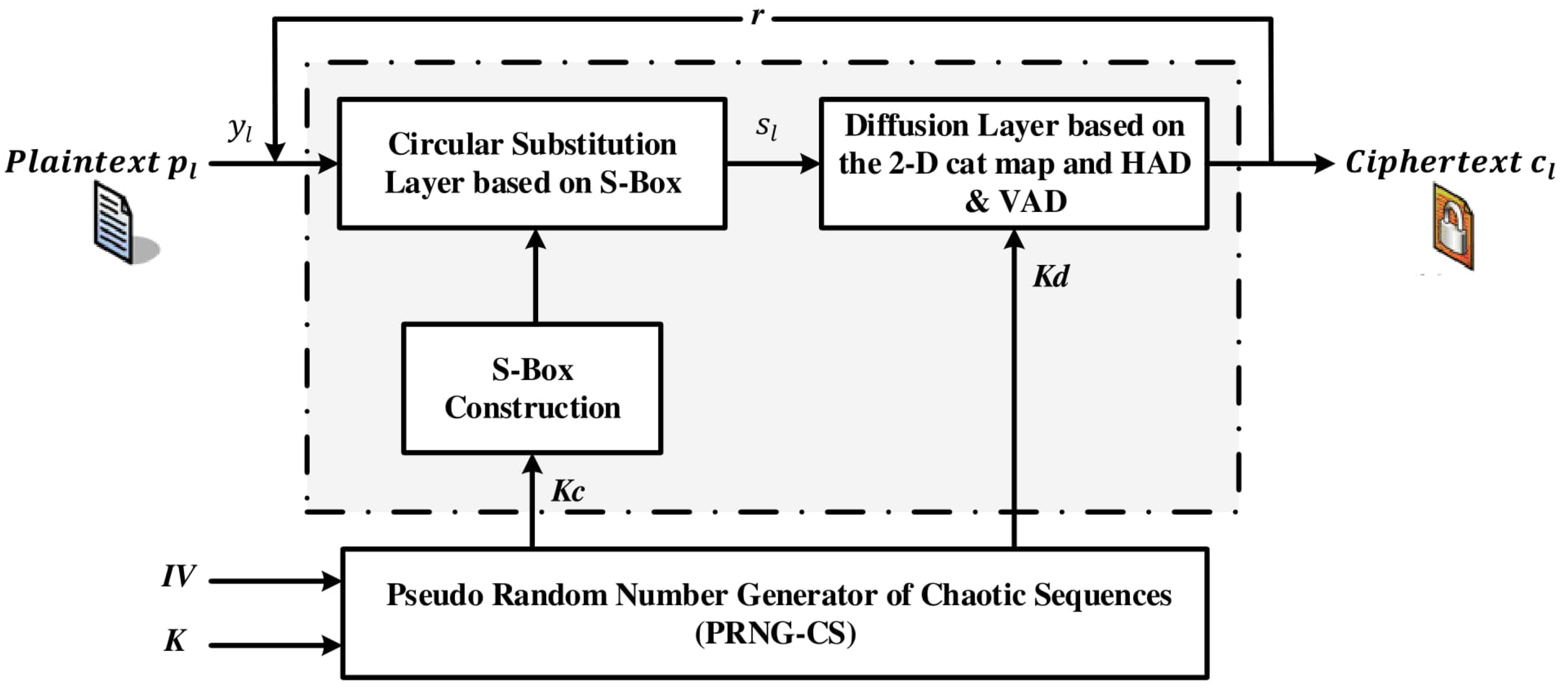
Figure 1.
Diagram of the encryption process.
Figure 1.
Diagram of the encryption process.
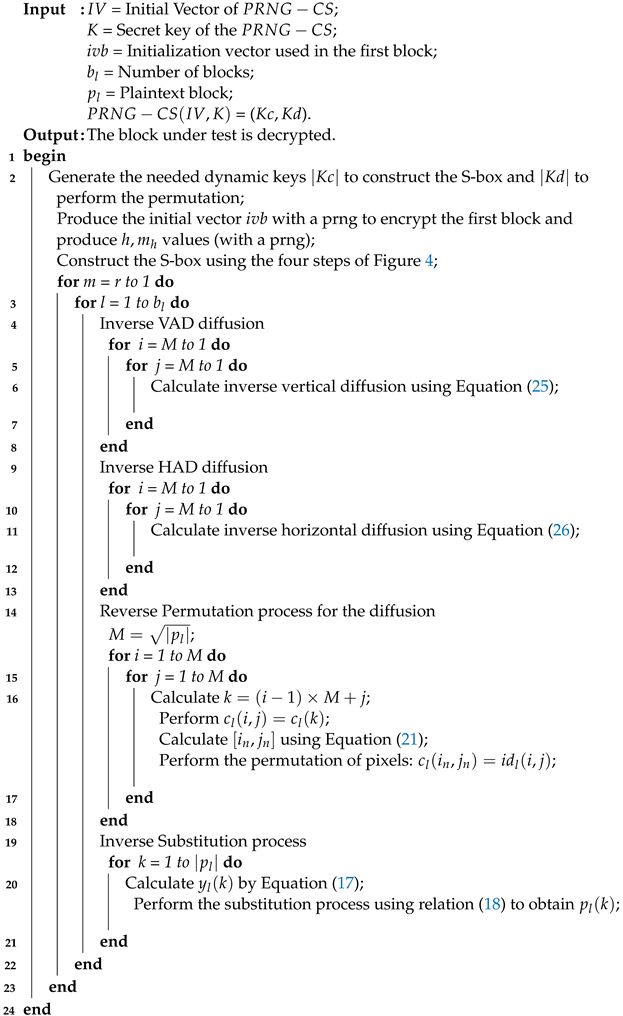
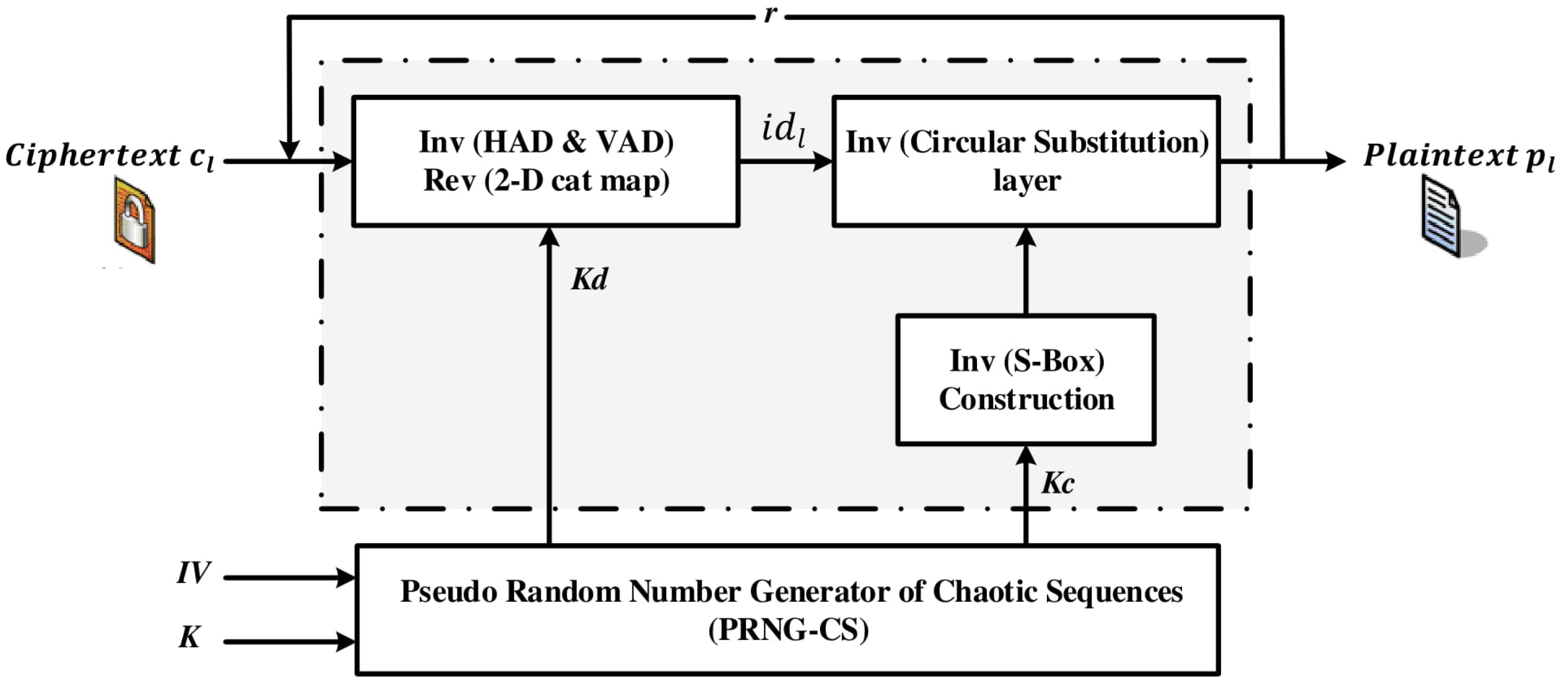
Figure 2.
Diagram of the decryption process.
Figure 2.
Diagram of the decryption process.
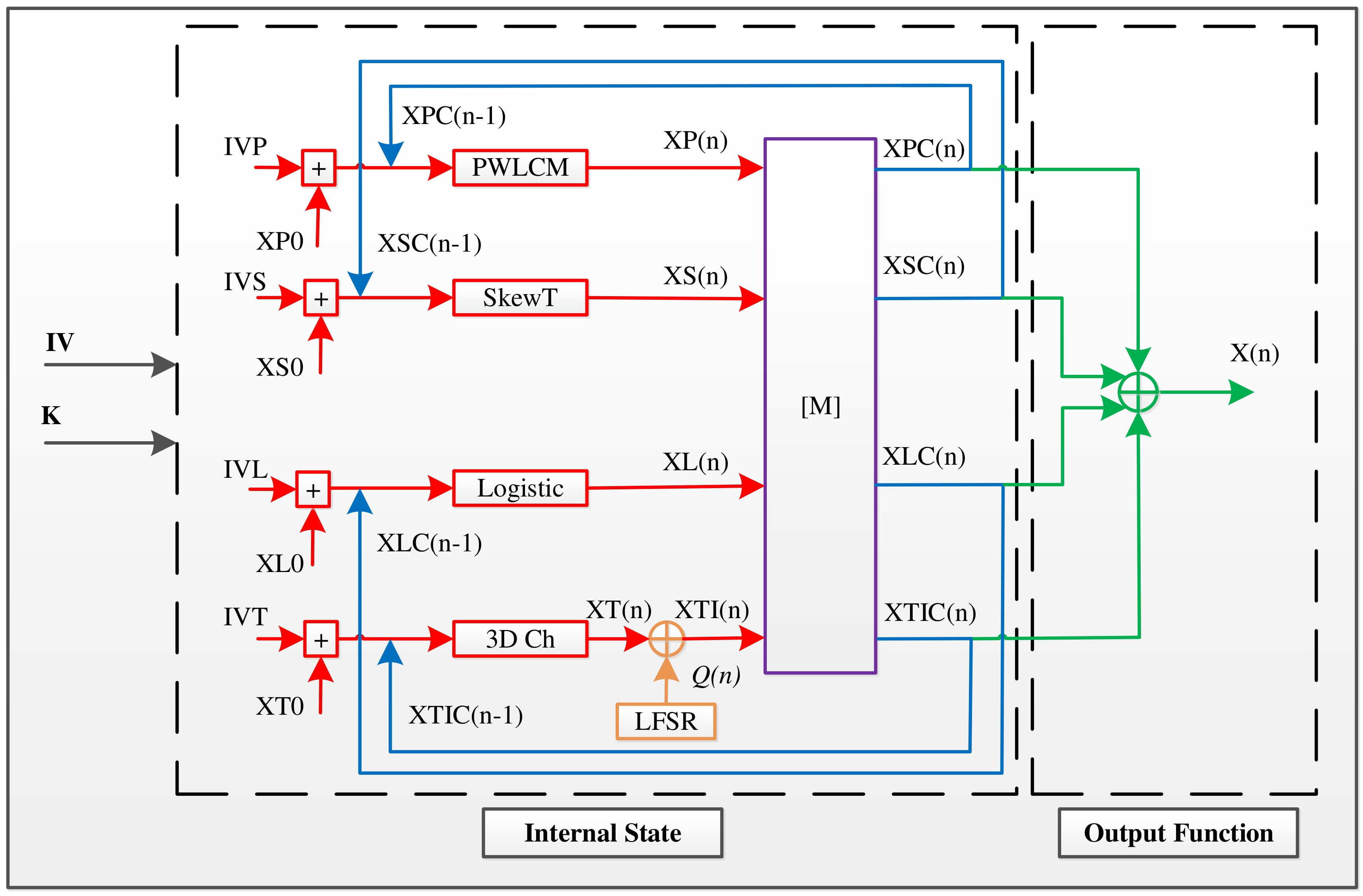
Figure 3.
The architecture of the proposed pseudorandom number generator of chaotic sequences.
Figure 3.
The architecture of the proposed pseudorandom number generator of chaotic sequences.
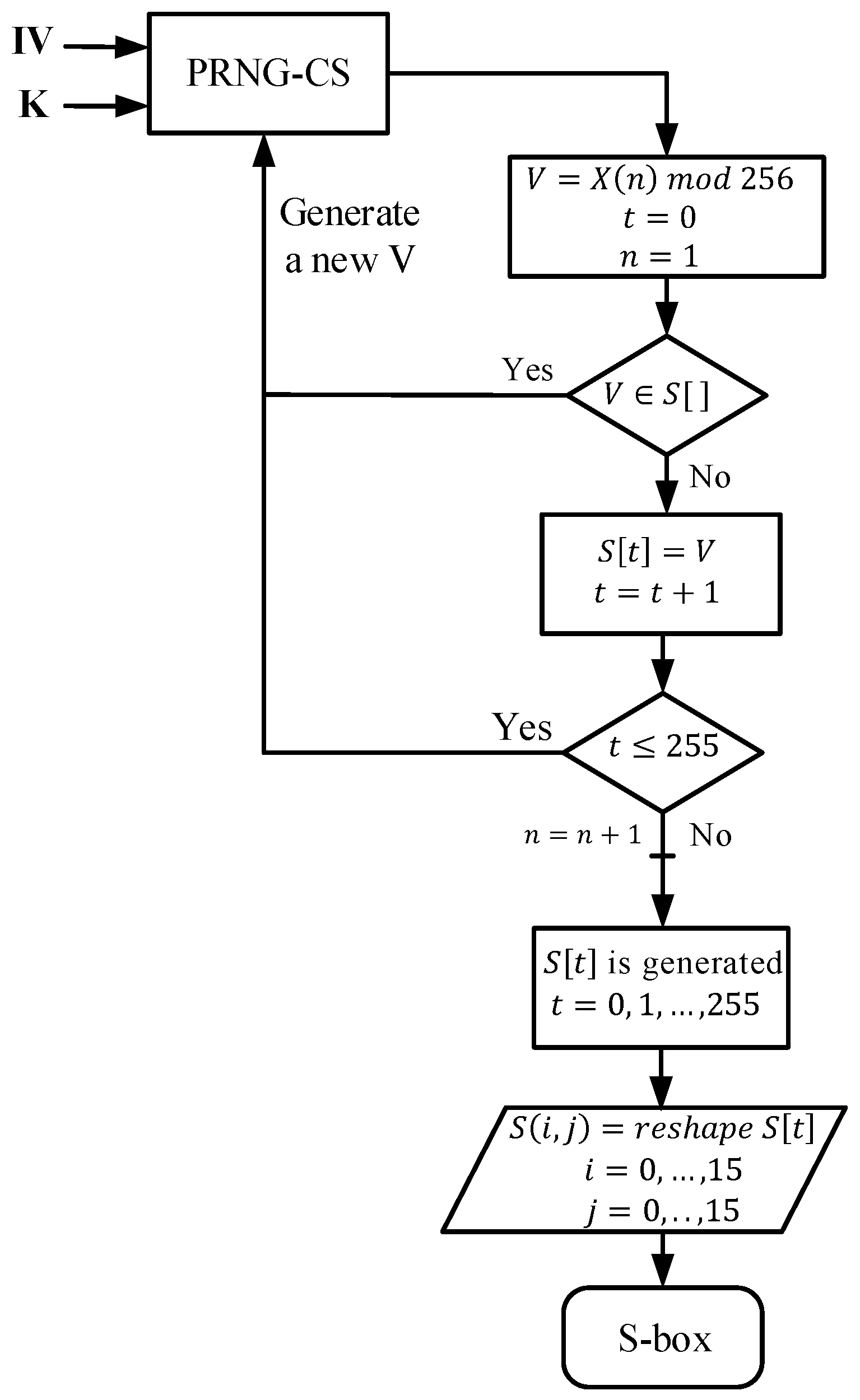
Figure 4.
Block diagram of the proposed chaos-based S-box construction.
Figure 4.
Block diagram of the proposed chaos-based S-box construction.
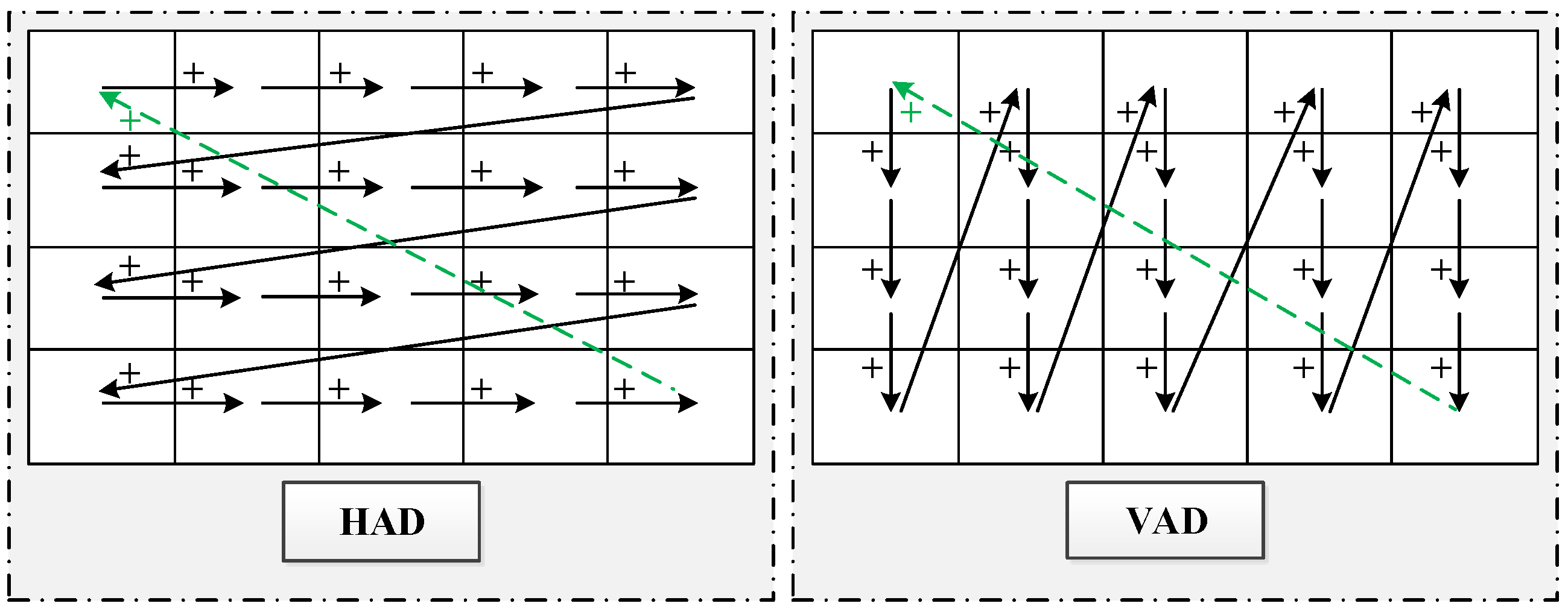
Figure 5.
Horizontal and vertical addition diffusion.
Figure 5.
Horizontal and vertical addition diffusion.
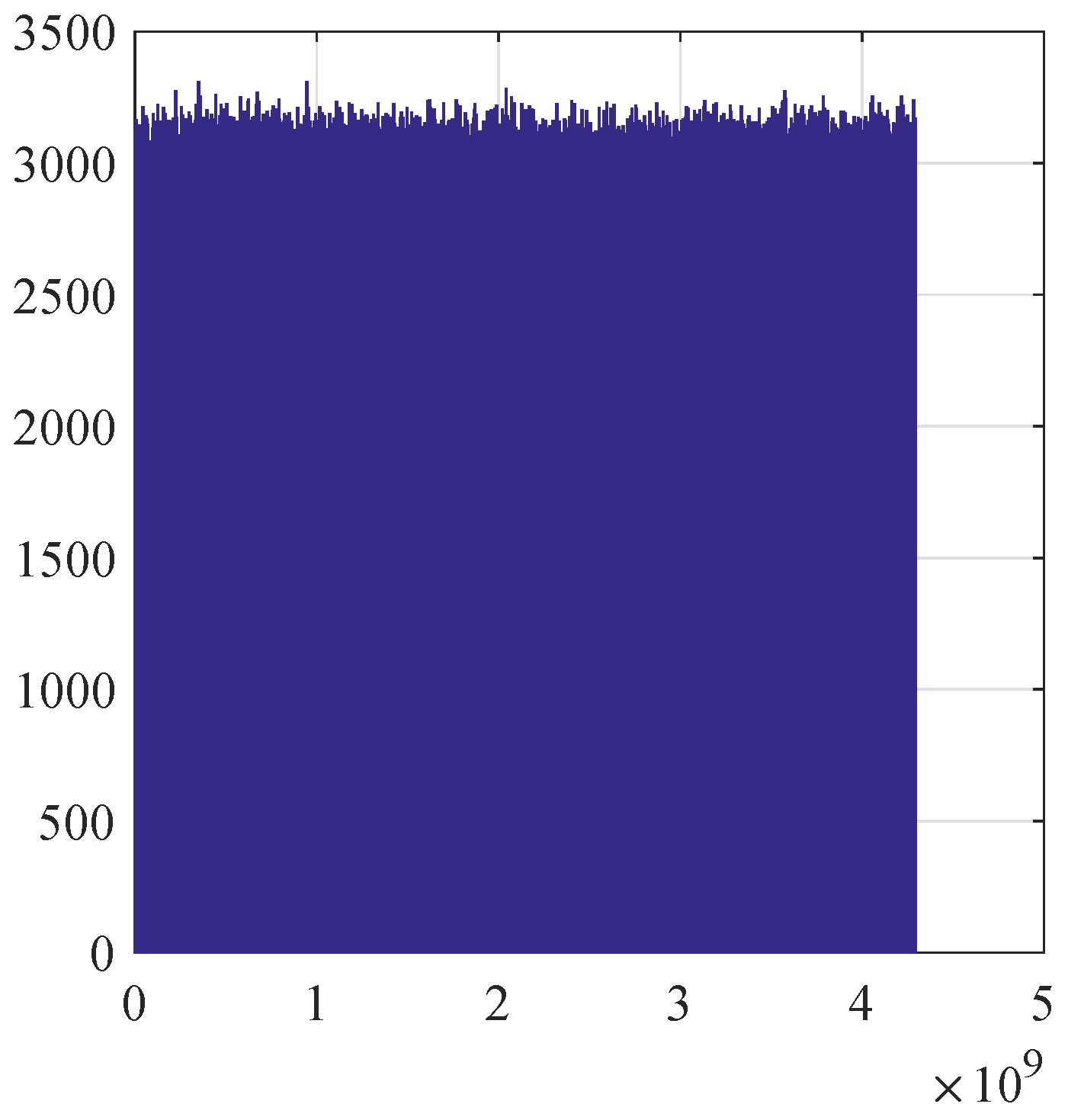
Figure 6.
An example of a histogram of a generated sequence .
Figure 6.
An example of a histogram of a generated sequence .
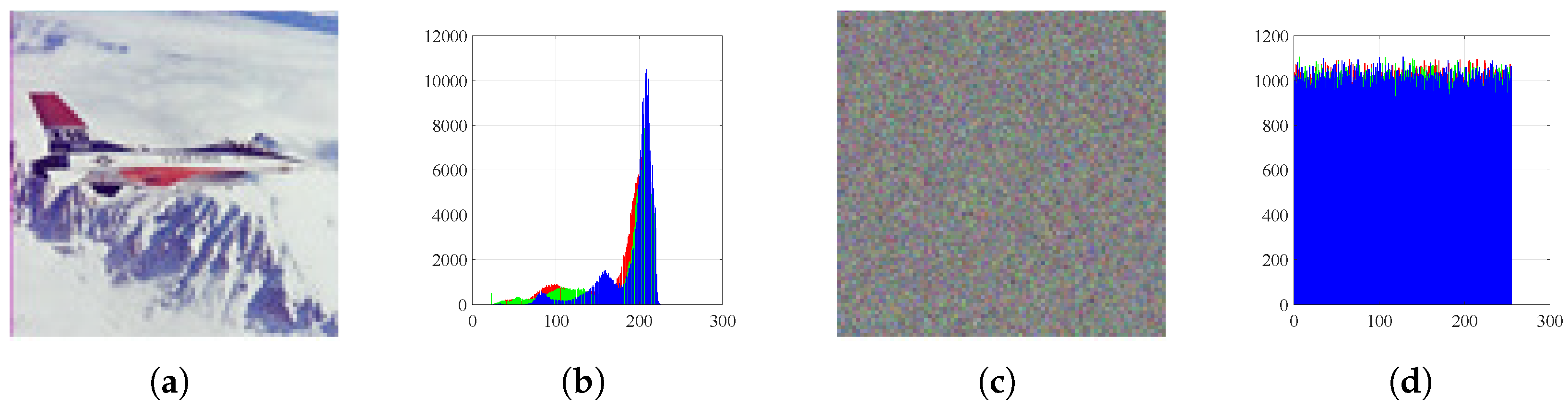
Figure 7.
Histograms: (a) Airplane image, (b) histogram of plain Airplane, (c) encrypted Airplane, and (d) histogram of encrypted Airplane.
Figure 7.
Histograms: (a) Airplane image, (b) histogram of plain Airplane, (c) encrypted Airplane, and (d) histogram of encrypted Airplane.
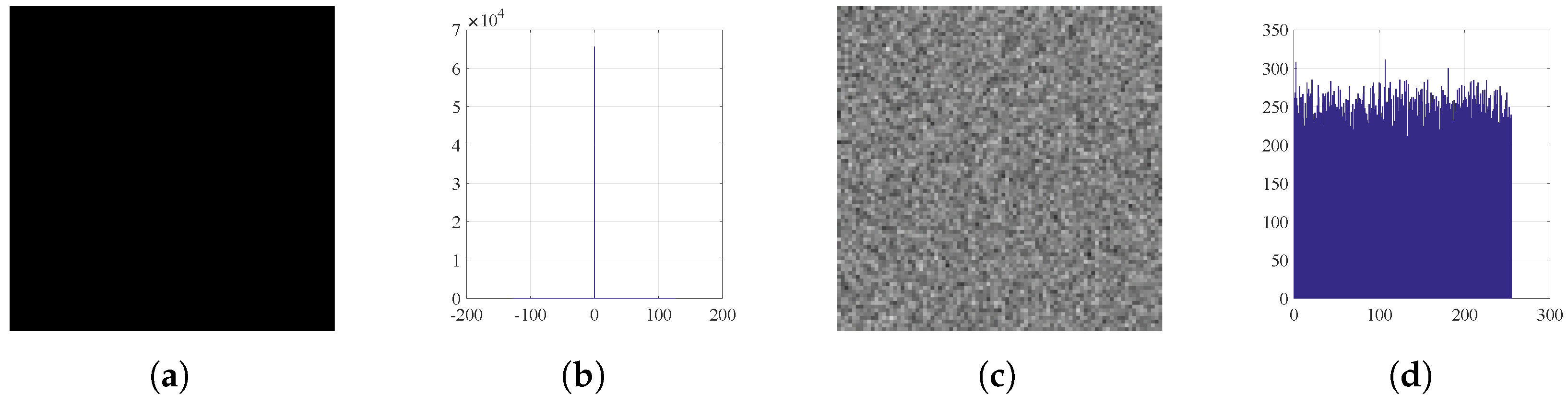
Figure 8.
Histograms: (a) Black image, (b) histogram of plain Black, (c) encrypted Black, and (d) histogram of encrypted Black.
Figure 8.
Histograms: (a) Black image, (b) histogram of plain Black, (c) encrypted Black, and (d) histogram of encrypted Black.
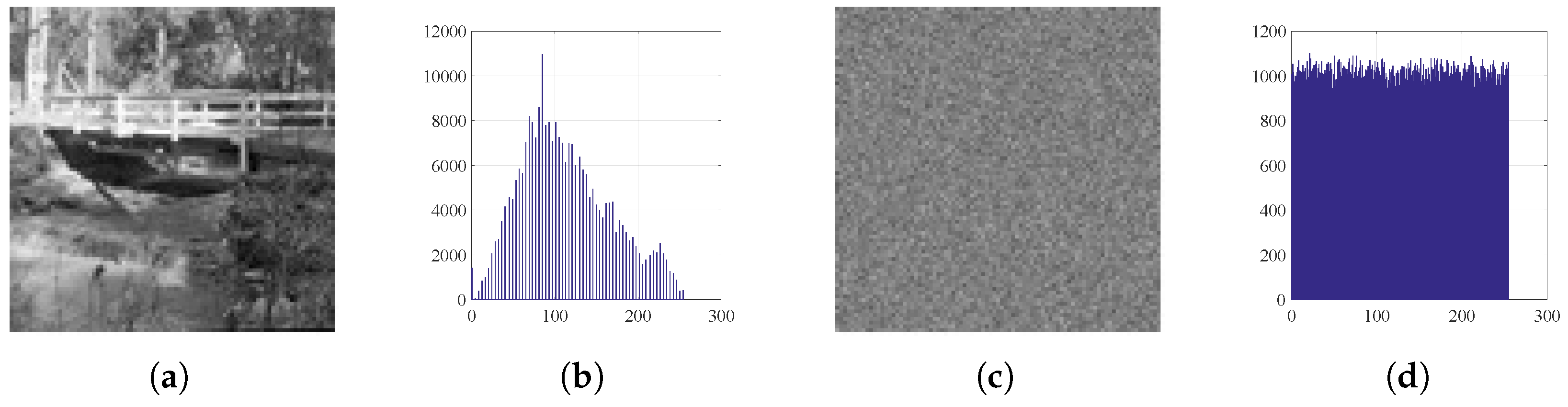
Figure 9.
Histograms: (a) Bridge image, (b) histogram of plain Bridge, (c) encrypted Bridge, and (d) histogram of encrypted Bridge.
Figure 9.
Histograms: (a) Bridge image, (b) histogram of plain Bridge, (c) encrypted Bridge, and (d) histogram of encrypted Bridge.
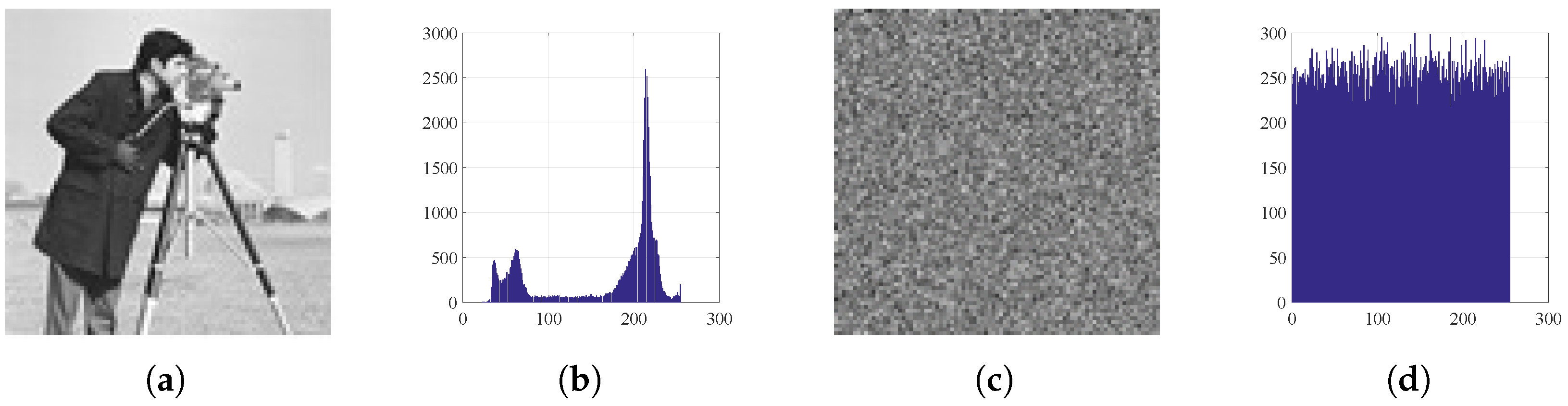
Figure 10.
Histograms: (a) Cameraman image, (b) histogram of plain Cameraman, (c) encrypted Cameraman, and (d) histogram of encrypted Cameraman.
Figure 10.
Histograms: (a) Cameraman image, (b) histogram of plain Cameraman, (c) encrypted Cameraman, and (d) histogram of encrypted Cameraman.
Figure 11.
Histograms: (a) Flowers image, (b) histogram of plain Flowers, (c) encrypted Flowers, and (d) histogram of encrypted Flowers.
Figure 11.
Histograms: (a) Flowers image, (b) histogram of plain Flowers, (c) encrypted Flowers, and (d) histogram of encrypted Flowers.
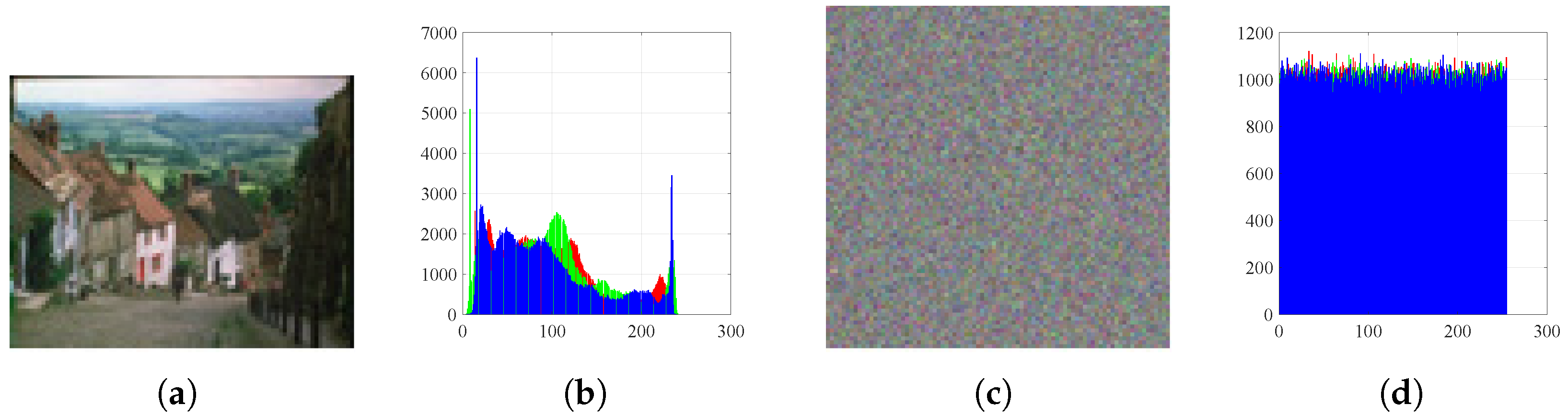
Figure 12.
Histograms: (a) Goldhill image, (b) histogram of plain Goldhill, (c) encrypted Goldhill, and (d) histogram of encrypted Goldhill.
Figure 12.
Histograms: (a) Goldhill image, (b) histogram of plain Goldhill, (c) encrypted Goldhill, and (d) histogram of encrypted Goldhill.
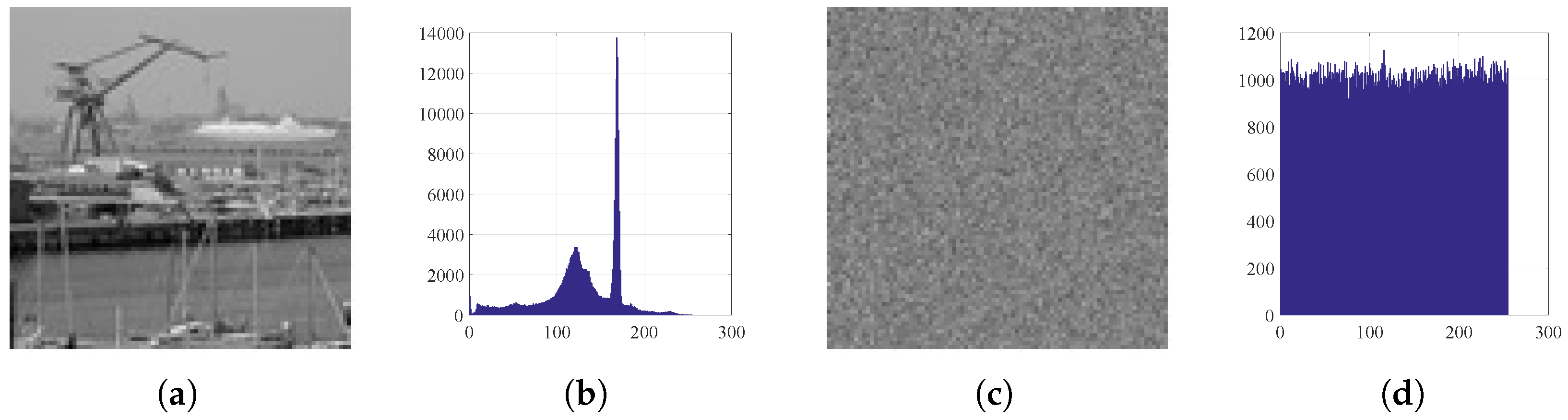
Figure 13.
Histograms: (a) Kiel image, (b) histogram of plain Kiel, (c) encrypted Kiel, and (d) histogram of encrypted Kiel.
Figure 13.
Histograms: (a) Kiel image, (b) histogram of plain Kiel, (c) encrypted Kiel, and (d) histogram of encrypted Kiel.
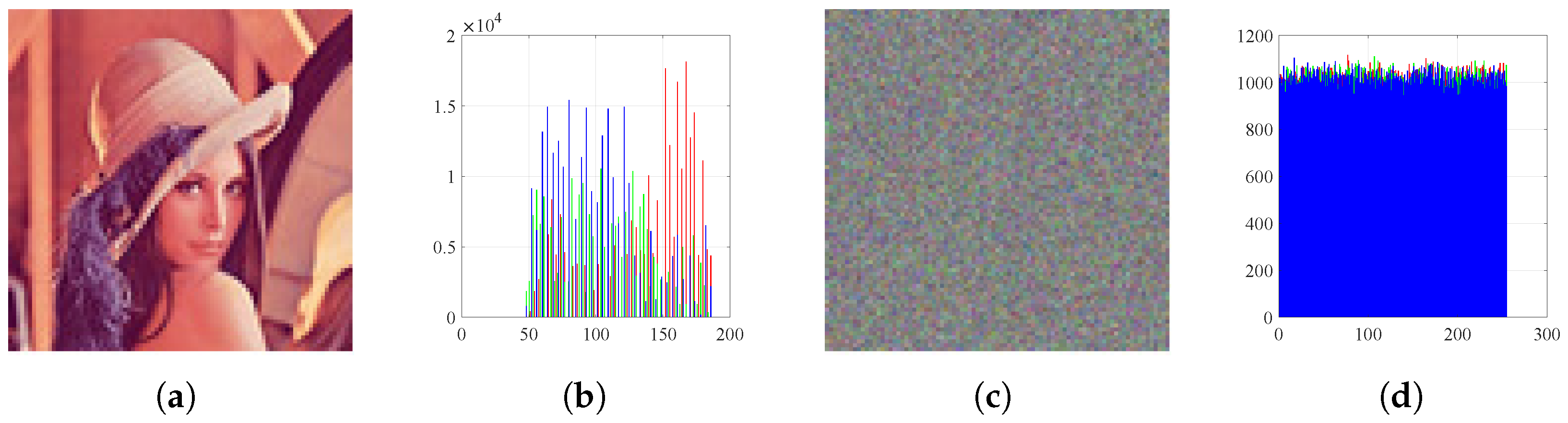
Figure 14.
Histograms: (a) Lena image, (b) histogram of plain Lena, (c) encrypted Lena, and (d) histogram of encrypted Lena.
Figure 14.
Histograms: (a) Lena image, (b) histogram of plain Lena, (c) encrypted Lena, and (d) histogram of encrypted Lena.
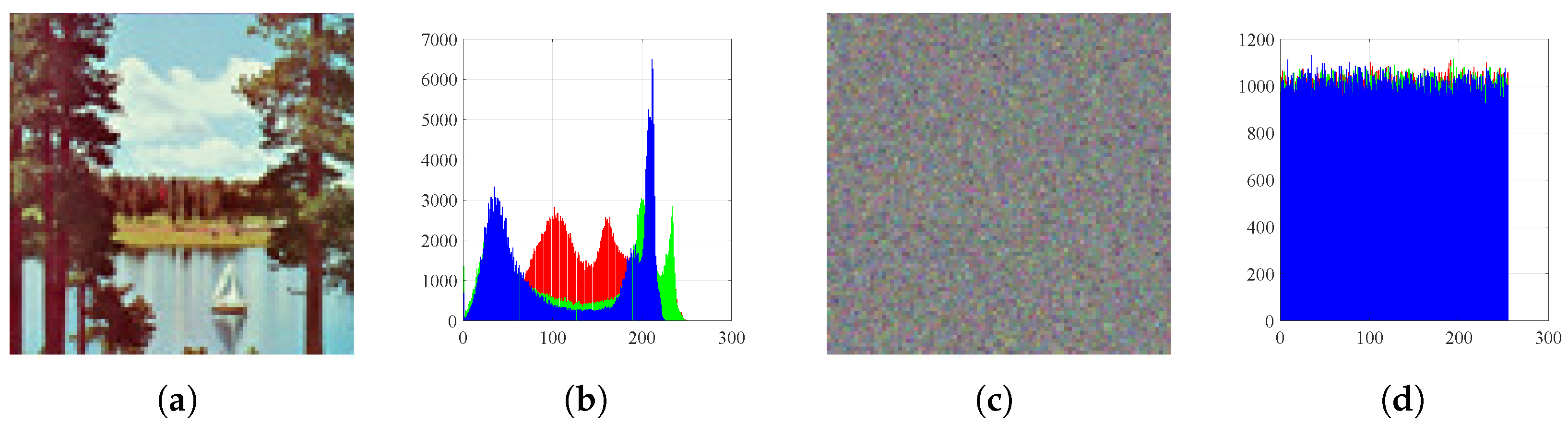
Figure 15.
Histograms: (a) Sailboat image, (b) histogram of plain Sailboat, (c) encrypted Sailboat, and (d) histogram of encrypted Sailboat.
Figure 15.
Histograms: (a) Sailboat image, (b) histogram of plain Sailboat, (c) encrypted Sailboat, and (d) histogram of encrypted Sailboat.
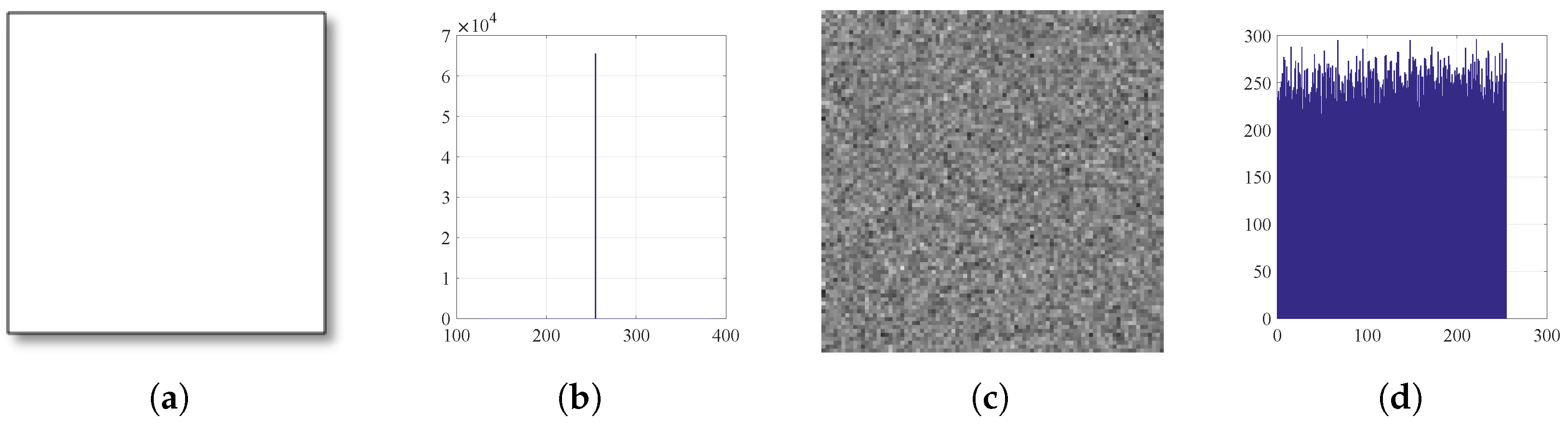
Figure 16.
Histograms: (a) White image, (b) histogram of plain White, (c) encrypted White, and (d) histogram of encrypted White.
Figure 16.
Histograms: (a) White image, (b) histogram of plain White, (c) encrypted White, and (d) histogram of encrypted White.
Figure 17.
Distribution of adjacent pixels in the plain and encrypted images of Goldhill in the three directions: horizontal, vertical, and diagonal, respectively.
Figure 17.
Distribution of adjacent pixels in the plain and encrypted images of Goldhill in the three directions: horizontal, vertical, and diagonal, respectively.
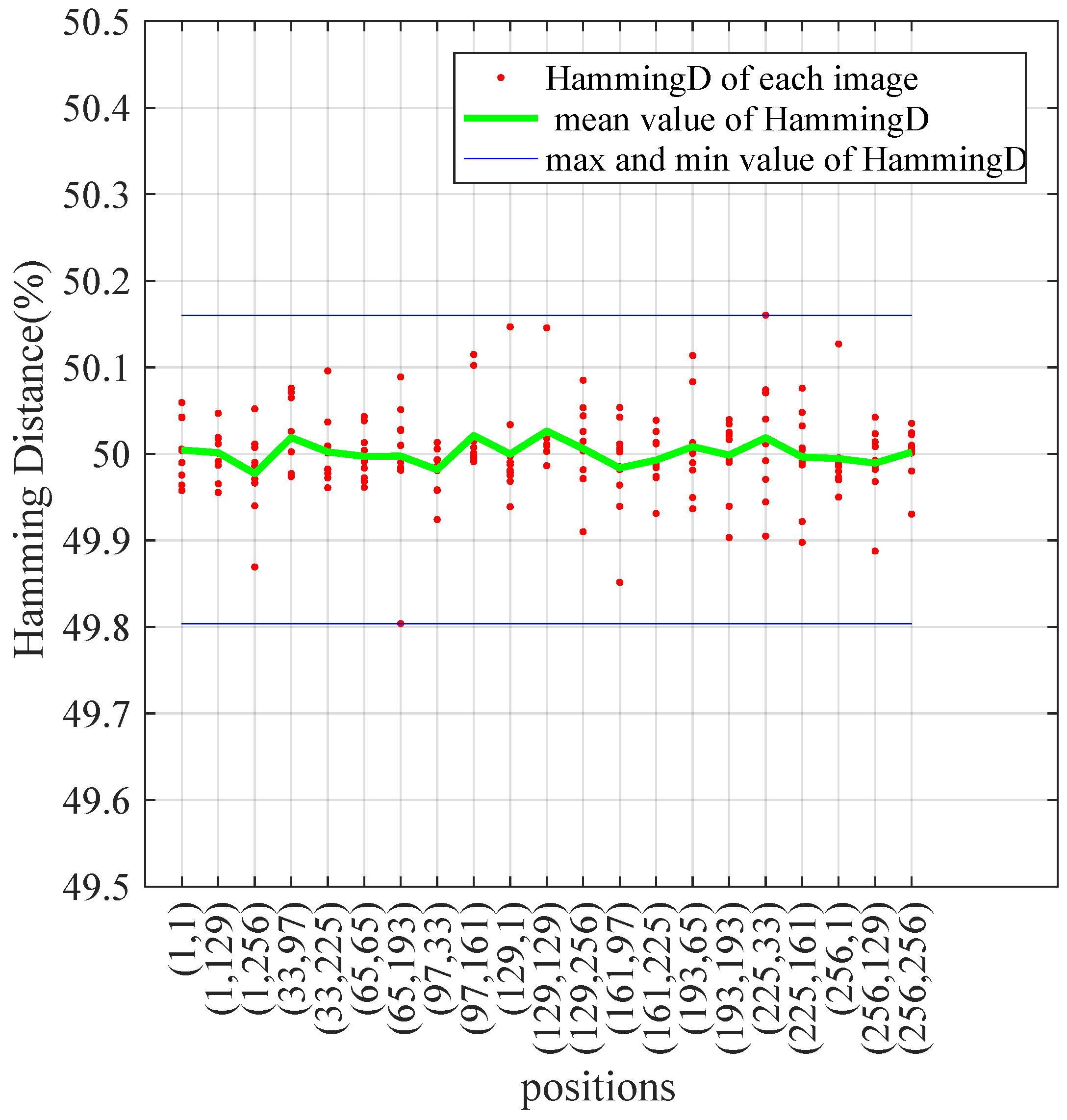
Figure 18.
Plaintext sensitivity test evaluated by the Hamming distance.
Figure 18.
Plaintext sensitivity test evaluated by the Hamming distance.
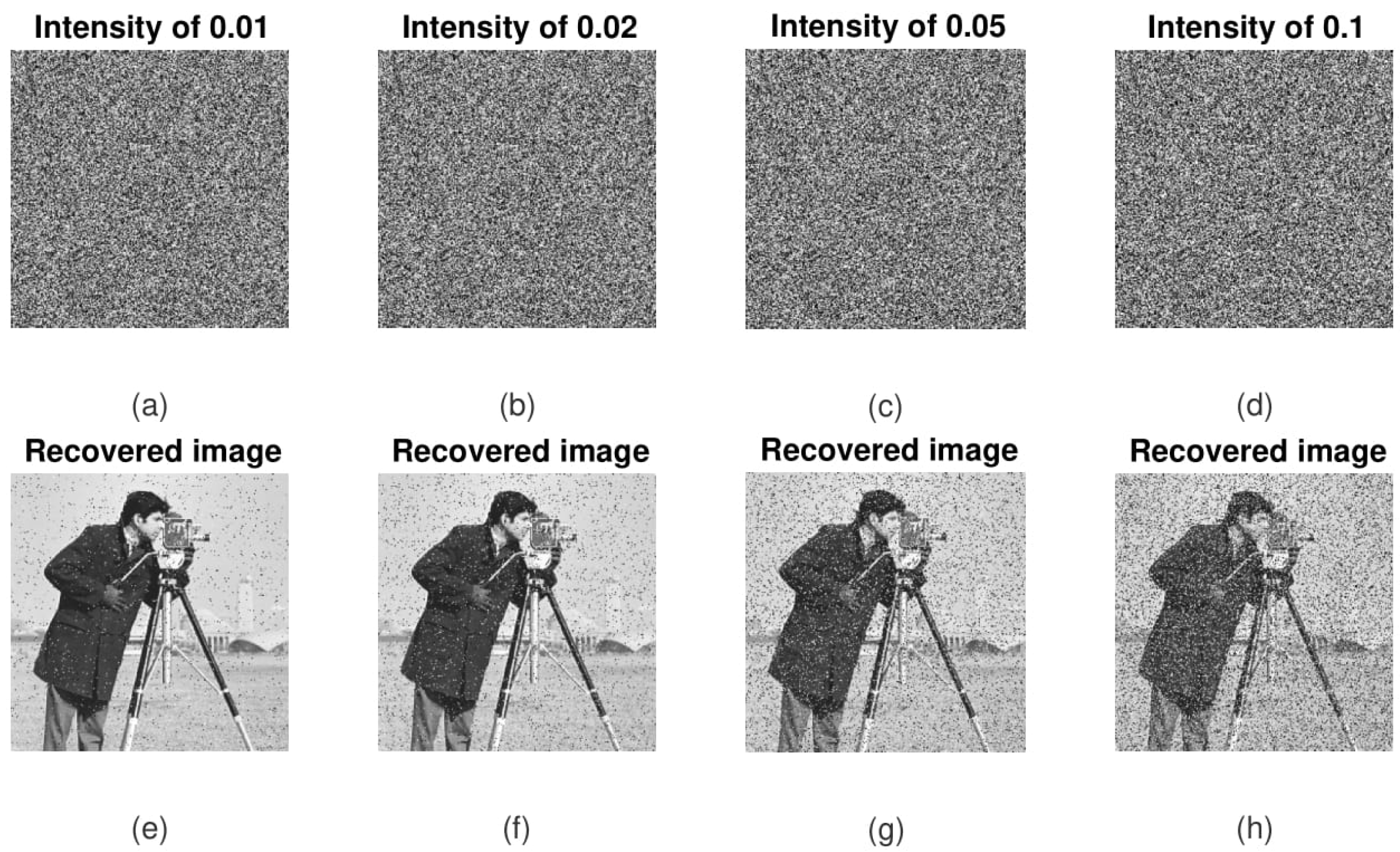
Figure 19.
Robustness against salt and pepper noise.
Figure 19.
Robustness against salt and pepper noise.
Figure 20.
Robustness against occlusion attack.
Figure 20.
Robustness against occlusion attack.
Table 1.
Initial conditions and parameters that form the secret key.
Table 1.
Initial conditions and parameters that form the secret key.
| Symbol | Definition |
|---|
| , , , and | Initial conditions of the four chaotic maps: PWLCM, skew tent, logistic, and 3-D Chebyshev in . |
| PWLCM map control parameter in . |
| Skew tent map control parameter in . |
| Coupling matrix M parameters in with . |
| Q0 | The initial value of the used LFSR is defined by: |
| The transient phase of 10 bits. |
Table 2.
An example of an S-box is obtained by the proposed algorithm.
Table 2.
An example of an S-box is obtained by the proposed algorithm.
| | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|
| 0 | 2E | 3E | 5D | 03 | 7C | B7 | AD | 9B | E0 | 62 | 67 | 50 | 95 | BC | 24 | 83 |
| 1 | A6 | CB | DD | F5 | BE | 39 | 9A | C3 | 2C | 64 | EA | EC | 05 | 3B | 26 | 2A |
| 2 | F8 | B4 | D0 | C5 | 30 | FD | E6 | 69 | 70 | 74 | 7A | 77 | F7 | 1A | E5 | DF |
| 3 | 15 | 7F | 8B | 32 | 51 | F1 | C9 | 93 | 40 | 5C | 48 | 8E | 2F | 65 | E2 | CC |
| 4 | FB | D8 | BD | 04 | C7 | 0B | E1 | 06 | 90 | B6 | A1 | EF | 14 | 2B | D5 | 82 |
| 5 | 4B | D1 | B8 | 59 | 92 | E3 | CD | B9 | 38 | 1F | 71 | 73 | EE | F9 | 46 | 45 |
| 6 | C0 | A8 | 00 | 6E | 9C | 6A | 9F | A9 | 78 | 6F | 87 | 5E | D9 | BA | 47 | 42 |
| 7 | 68 | DA | F0 | 53 | 58 | 31 | D3 | 36 | 34 | 20 | 33 | 8D | D4 | 8C | 4C | 3D |
| 8 | 1D | 4E | 61 | E9 | 5A | 5F | 4D | 6B | AA | C4 | 91 | 3F | 4A | 1E | 02 | 0F |
| 9 | 09 | 72 | 88 | CA | F2 | 85 | 99 | 9D | FF | CF | B2 | 2D | 52 | 23 | E4 | 3C |
| A | C8 | EB | AF | 81 | 1C | FE | 9E | B5 | 7B | 55 | ED | 07 | 41 | 89 | 94 | 7E |
| B | 12 | 11 | D7 | 49 | AB | 4F | 21 | DE | 0C | D6 | 17 | BF | 56 | 6D | F3 | 01 |
| C | 1B | A5 | 3A | 8A | 27 | E7 | 8F | 0E | A3 | 75 | BB | 84 | 76 | CE | 25 | B1 |
| D | FA | DB | 18 | B0 | A0 | C1 | 44 | 54 | A7 | 28 | 43 | 13 | 22 | A2 | 35 | FC |
| E | C6 | C2 | 66 | 63 | AC | A4 | 7D | F6 | 96 | 29 | 10 | 86 | 16 | D2 | 37 | 6C |
| F | 79 | 08 | 97 | E8 | DC | 0A | 19 | 0D | B3 | 98 | 80 | AE | F4 | 57 | 5B | 60 |
Table 3.
HD versus the round times in the encryption process.
Table 3.
HD versus the round times in the encryption process.
| Image | Size | HD (%) | | |
|---|
| | |
|---|
| Airplane | 512 × 512 × 3 | 50.0010 | 49.9974 | 49.9998 |
| Black | 256 × 256 × 1 | 50.0027 | 50.0050 | 49.9977 |
| Bridge | 512 × 512 × 1 | 50.0039 | 49.9962 | 50.0021 |
| Cameraman | 256 × 256 × 1 | 49.9936 | 50.0018 | 50.0000 |
| Flowers | 256 × 256 × 3 | 49.9993 | 50.0034 | 49.9955 |
| Goldhill | 512 × 512 × 3 | 49.9999 | 49.9988 | 49.9996 |
| Kiel | 512 × 512 × 1 | 50.0010 | 49.9989 | 50.0036 |
| Lena | 512 × 512 × 3 | 50.0001 | 49.9997 | 49.9972 |
| Sailboat | 512 × 512 × 3 | 49.9961 | 50.0050 | 50.0000 |
| White | 256 × 256 × 1 | 50.0107 | 49.9948 | 50.0009 |
Table 4.
Chi-square results on the tested histograms.
Table 4.
Chi-square results on the tested histograms.
| Chi-Square Test | PRNG-CS |
|---|
| 967.700 |
| (1000, 0.05) | 1073.642 |
Table 5.
P-values and proportion results of NIST tests.
Table 5.
P-values and proportion results of NIST tests.
| Test | p-Value | Proportion (%) |
|---|
| Frequency test | 0.494 | 98.000 |
| Block-frequency test | 0.514 | 99.000 |
| Cumulative sums test | 0.504 | 98.000 |
| Runs test | 0.494 | 99.000 |
| Longest-run test | 0.262 | 97.000 |
| Rank test | 0.868 | 99.000 |
| FFT test | 0.384 | 99.000 |
| Nonperiodic templates | 0.482 | 99.061 |
| Overlapping templates | 0.596 | 98.000 |
| Universal | 0.946 | 99.000 |
| Approximate entropy | 0.419 | 100.000 |
| Random excursions | 0.439 | 98.214 |
| Random excursion variant | 0.488 | 98.651 |
| Serial test | 0.415 | 100.000 |
| Linear complexity | 0.817 | 97.000 |
Table 6.
Performance comparison of different S-boxes.
Table 6.
Performance comparison of different S-boxes.
| S-Box | Nonlinearity | SAC | BIC-SAC | BIC Nonlinearity | DP | LP |
|---|
| Min | Avg | Max | Min | Avg | Max |
|---|
| Proposed S-box | 102 | 104 | 108 | 0.4375 | 0.4948 | 0.5625 | 0.4991 | 103.4286 | 10 | 0.1094 |
| Çavuşoğlu et al. [42] | 104 | 106 | 110 | 0.4218 | 0.5039 | 0.5937 | 0.5058 | 103.40 | 10 | 0.1406 |
| Lambić et al. [43] | 106 | 106.75 | 108 | - | 0.5034 | - | 0.5014 | 103.78 | 10 | 0.1328 |
| Ahmed et al. [44] | 106 | 107.5 | 108 | - | 0.4943 | - | 0.4982 | 104.35 | 10 | 0.1250 |
| Lai et al. [49] | 104 | 105 | 110 | 0.3906 | 0.5014 | 0.5937 | 0.5028 | 102.75 | 10 | 0.1250 |
| Al Solami et al. [50] | 106 | 108.5 | 110 | - | 0.5017 | - | 0.5026 | 104 | 10 | 0.1094 |
Table 7.
Chi-square test.
Table 7.
Chi-square test.
| Image | Size | Chi-Square Test |
|---|
| Airplane | 512 × 512 × 3 | 256.7715 |
| Black | 256 × 256 × 1 | 234.0391 |
| Bridge | 512 × 512 × 1 | 256.6113 |
| Cameraman | 256 × 256 × 1 | 275.5625 |
| Flowers | 256 × 256 × 3 | 236.6458 |
| Goldhill | 512 × 512 × 3 | 239.6576 |
| Kiel | 512 × 512 × 1 | 243.4629 |
| Lena | 512 × 512 × 3 | 249.1270 |
| Sailboat | 512 × 512 × 3 | 242.1380 |
| White | 256 × 256 × 1 | 273.6641 |
Table 8.
The correlation coefficient of 8000 pairs of two adjacent pixels of the plain and ciphered images.
Table 8.
The correlation coefficient of 8000 pairs of two adjacent pixels of the plain and ciphered images.
| Image | Size | | Plain Image | Encrypted Image |
|---|
| HC | VC | DC | HC | VC | DC |
|---|
| Airplane | 512 × 512 × 3 | R | 0.97191 | 0.96051 | 0.93848 | 0.00006 | −0.00153 | 0.00024 |
| | | G | 0.95150 | 0.96915 | 0.92863 | −0.00154 | −0.00041 | −0.00098 |
| | | B | 0.96226 | 0.94538 | 0.92419 | −0.00033 | −0.00056 | −0.00004 |
| Black | 256 × 256 × 1 | | - | - | - | −0.00167 | −0.00044 | −0.00074 |
| Bridge | 512 × 512 × 1 | | 0.93981 | 0.92720 | 0.89716 | −0.00130 | 0.00172 | 0.00084 |
| Cameraman | 256 × 256 × 1 | | 0.92013 | 0.95496 | 0.89590 | 0.00110 | 0.00193 | 0.00028 |
| Flowers | 256 × 256 × 3 | R | 0.95049 | 0.96800 | 0.93340 | 0.00197 | −0.00128 | 0.00153 |
| | | G | 0.91532 | 0.94200 | 0.88863 | −0.00082 | −0.00019 | 0.00071 |
| | | B | 0.92085 | 0.94834 | 0.89510 | −0.00092 | 0.00009 | 0.00182 |
| Goldhill | 512 × 512 × 3 | R | 0.97767 | 0.97649 | 0.95975 | 0.00039 | 0.00052 | −0.00058 |
| | | G | 0.98180 | 0.98496 | 0.96998 | −0.00047 | 0.00028 | 0.00148 |
| | | B | 0.98453 | 0.98641 | 0.97339 | −0.00140 | 0.00084 | −0.00024 |
| Kiel | 512 × 512 × 1 | | 0.90591 | 0.82571 | 0.78020 | 0.00168 | −0.00127 | −0.00044 |
| Lena | 512 × 512 × 3 | R | 0.97529 | 0.98540 | 0.96464 | 0.00055 | −0.00041 | 0.00001 |
| | | G | 0.96666 | 0.98011 | 0.95321 | −0.00162 | 0.00049 | −0.00023 |
| | | B | 0.93357 | 0.95552 | 0.91819 | 0.00077 | −0.00006 | 0.00042 |
| Sailboat | 512 × 512 × 3 | R | 0.95595 | 0.95302 | 0.94030 | −0.00041 | 0.00070 | −0.00001 |
| | | G | 0.97088 | 0.96404 | 0.95027 | −0.00096 | 0.00038 | −0.00015 |
| | | B | 0.97054 | 0.96872 | 0.95208 | −0.00164 | 0.00048 | −0.00018 |
| White | 256 × 256 × 1 | | - | - | - | −0.00165 | 0.00025 | 0.00036 |
Table 9.
Entropy test results.
Table 9.
Entropy test results.
| Image | Size | Plain | Encrypted |
|---|
| Airplane | 512 × 512 × 3 | 6.6639 | 7.9997 |
| Black | 256 × 256 × 1 | 0.0000 | 7.9974 |
| Bridge | 512 × 512 × 1 | 5.7056 | 7.9992 |
| Cameraman | 256 × 256 × 1 | 6.9046 | 7.9977 |
| Flowers | 256 × 256 × 3 | 7.5434 | 7.9991 |
| Goldhill | 512 × 512 × 3 | 7.6220 | 7.9997 |
| Kiel | 512 × 512 × 1 | 6.9589 | 7.9994 |
| Lena | 512 × 512 × 3 | 5.6822 | 7.9998 |
| Sailboat | 512 × 512 × 3 | 7.7632 | 7.9998 |
| White | 256 × 256 × 1 | 0.0000 | 7.9968 |
Table 10.
Average NPCR, UACI, and HD key sensitivity tests.
Table 10.
Average NPCR, UACI, and HD key sensitivity tests.
| Image | Size | Key Sensitivity Test |
|---|
| NPCR (%) | UACI (%) | HD (%) |
|---|
| Airplane | 512 × 512 × 3 | 99.6065 | 33.4666 | 50.0052 |
| Black | 256 × 256 × 1 | 99.6099 | 33.4323 | 50.0094 |
| Bridge | 512 × 512 × 1 | 99.6098 | 33.5052 | 50.0019 |
| Cameraman | 256 × 256 × 1 | 99.5992 | 33.4234 | 49.9844 |
| Flowers | 256 × 256 × 3 | 99.6040 | 33.4772 | 49.9941 |
| Goldhill | 512 × 512 × 3 | 99.6069 | 33.4464 | 49.9942 |
| Kiel | 512 × 512 × 1 | 99.6042 | 33.4650 | 49.9976 |
| Lena | 512 × 512 × 3 | 99.6088 | 33.4664 | 49.9907 |
| Sailboat | 512 × 512 × 3 | 99.6077 | 33.4680 | 50.0090 |
| White | 256 × 256 × 1 | 99.6231 | 33.5524 | 50.0000 |
Table 11.
NPCR, UACI, and HD of the plaintext sensitivity test.
Table 11.
NPCR, UACI, and HD of the plaintext sensitivity test.
| Image | Size | Plaintext Sensitivity |
|---|
| NPCR (%) | UACI (%) | HD (%) |
|---|
| Airplane | 512 × 512 × 3 | 99.6102 | 33.4659 | 49.9972 |
| Black | 256 × 256 × 1 | 99.6067 | 33.4840 | 50.0143 |
| Bridge | 512 × 512 × 1 | 99.6114 | 33.4960 | 50.0060 |
| Cameraman | 256 × 256 × 1 | 99.6068 | 33.4616 | 49.9907 |
| Flowers | 256 × 256 × 3 | 99.6016 | 33.4563 | 49.9954 |
| Goldhill | 512 × 512 × 3 | 99.6081 | 33.4460 | 50.0003 |
| Kiel | 512 × 512 × 1 | 99.6075 | 33.4658 | 49.9974 |
| Lena | 512 × 512 × 3 | 99.6092 | 33.4669 | 50.0028 |
| Sailboat | 512 × 512 × 3 | 99.6058 | 33.4837 | 50.0062 |
| White | 256 × 256 × 1 | 99.6008 | 33.5139 | 49.9981 |
Table 12.
The proposed encryption system’s computing performance.
Table 12.
The proposed encryption system’s computing performance.
| Image | Size | Encryption Time (Milliseconds) | ET (Mbps) | NCpB (Cycles/Byte) |
|---|
| Cameraman | 256 × 256 × 1 | 39.3 | 1.589 | 1501 |
| Flowers | 256 × 256 × 3 | 119.2 | 1.5726 | 1516 |
| Kiel | 512 × 512 × 1 | 163.9 | 1.5249 | 1564 |
| Lena | 512 × 512 × 3 | 602.3 | 1.2451 | 1915 |
Table 13.
Comparison of NCpBs from different encryption schemes.
Table 13.
Comparison of NCpBs from different encryption schemes.
| Cryptosystem | NCpB |
|---|
| Proposed | 1568 |
| Qiao et al. [25] | 77,386 |
| Luo et al. [52] | 95,368 |
| Huang et al. [53] | 15,642 |