Abstract
Cloud computing has become popular in data sharing mainly because it has huge storage capacity and computing power. Securing the privacy of sensitive data for cloud-based data sharing is vital. Currently, there are various conditional proxy re-encryption (UPRE) schemes that have been proposed to resolve the privacy issue. Nevertheless, the existing UPRE schemes cannot allow the proxy (e.g., the cloud server) to transfer the outsourced encrypted data under the data owner’s public key of any homomorphic encryption scheme into the encrypted data under the data user’s public key of a homomorphic encryption scheme (possibly different from the data owner). The transformation of outsourced encrypted data between homomorphic encryption schemes is more suitable for the real data sharing in clouds. Consequently, we present the notion of universal conditional proxy re-encryption (UCPRE) to solve the issue of flexible transformation of outsourced encrypted data between homomorphic encryption schemes in cloud-based data sharing. UCPRE is lightweight in the sense that it only requires the re-encrypted key generation and re-encryption algorithms. We give the definition of UCPRE and prove that it is HRA secure without random oracle. Finally, we show that our UCPRE is efficient and rational compared to other existing CPRE schemes by instantiating our UCPRE.
1. Introduction
Cloud computing has become popular in actual applications mostly because of its massive storage capacity and computing power. Ensuring the privacy of sensitive data is a challenge in cloud computing. Public key encryption (PKE) is worth considering, as this method ensures data privacy. By the method of PKE, the data owner stores the encrypted data in clouds to guarantee the privacy of the data so that he can securely share the data with other users in a cloud environment. Data sharing in clouds is easily achieved by decrypting encrypted data and re-encrypting the data with the data user’s public key. However, the above process is not feasible, because the data owner must keep online to decrypt the encrypted data and re-encrypt the data. Therefore, there is an urgent need to find a practical solution to achieve secure and practical data sharing in clouds without exposing sensitive information.
In prior, proxy re-encryption [1] is a solution for sharing outsourced encrypted data; in this process, the proxy (e.g., cloud server) gets no information about the underlying plaintext. One might think PRE schemes can be a trivial solution to realize data sharing in a cloud environment. However, this solution is inflexible. For example, the data owner Alice encrypted the data , , and via executing the encryption algorithm of PRE, and stores the cipheretexts , , and to the cloud server, where , . In the process, the proxy has the ability to transfer all outsourced encrypted data , , and into the encrypted data , , and for data user Bob even if Alice only wants to share the data and with Bob. Alice may want to share part of the data with Bob in actual applications. The notion of conditional PRE (CPRE) is presented to solve the issue of access control about data delegation. CPRE permits the proxy to convert the ciphertexts holding a condition specified by the data owner Alice into the ciphertexts for Bob. Therefore, the CPRE scheme is a more flexible PRE scheme since it enables fine-grained delegation of decryption rights in practical scenarios.
Although the existing CPRE schemes achieve fine-grained delegation for outsourced encrypted data. However, these schemes are not suitable for real data sharing scenarios. In the actual applications, the data owner has encrypted his all data via a popular homomorphic encryption scheme (e.g., the Elgamal encryption) and stored the encrypted data in the cloud server before deciding to share the data with the data users. When conditional PRE schemes are used in the above case, the data owner needs to download the encrypted data and decrypt the ciphertext using his secret key, and re-encrypt the data using the data users’ public key. In other words, the data owner needs to keep online in actual data sharing. Therefore, the challenge is how to design a mechanism that allows the proxy to transfer the ciphertext under a homomorphic encryption scheme into the ciphertext under a (possibly different) homomorphic encryption scheme.
1.1. Motivation
The existing CPRE schemes can practically address the issues when encryption schemes and proxy re-encryption schemes are used in cloud-based data sharing. Nevertheless, the existing CPRE schemes are not applicable to support an encrypted data switching mechanism that the proxy can convert the ciphertext under a homomorphic encryption scheme into a (possibly different) homomorphic encryption scheme. This encrypted data switching mechanism is more actual situation in cloud-based data sharing because it is a common phenomenon in which the data owner has stored the encrypted data under a homomorphic encryption scheme (e.g., Elgammal encryption) before deciding to share data with someone. Therefore, securing the switching mechanisms between two homomorphic encryption schemes is meaningful in actual cloud-based data sharing.
Recently, Dottling and Nishimaki [2] proposed a universal proxy re-encryption scheme that solves the issue of ciphertext transformation from an encryption scheme to a (different) encryption scheme. However, their work does not support fine-grain access control for the ciphertext. Meanwhile, the computing cost of delegatee is related to the number of multihop. That is, the delegatee needs to undertake an enormous computation cost so that the work does not apply to the cloud-based data sharing when the data user has a weak mobile device. This motivates us to design a new ciphertext switching mechanism that the proxy transfers encrypted data under a homomorphic encryption scheme into encrypted data under a homomorphic encryption scheme effectively. In other words, the data user with weak mobile devices has low computing overhead such that our mechanism is valid to be used for data sharing in clouds. Meanwhile, our mechanism allows the proxy (e.g., the cloud server) to transfer the authorized ciphertext via the re-encrypted key. Thereform, the proxy needs to convert the ciphertext according to the will of the data owner.
Imagine a data owner Alice is under the homomorphic encryption scheme (e.g., Elgammal encryption). It means that he has a pair of keys () from the Elgammal encryption so that he can encrypt his data via his public key and store encrypted data in the cloud server, where . While it is someday, Alice wants to share the data and with his friend Bob. Bob also has a pair of keys () from a homomorphic encryption scheme (e.g., Paillier encryption). Our UCPRE should satisfy the following function: The proxy has the ability to transfer the ciphertexts under the Elgammal encryption into the ciphertexts under the Paillier encryption via the re-encryption key. Figure 1 depicts the idea of our UCPRE system for data sharing in clouds. In such a UCPRE system, the data owner Alice needs to generate a re-encryption key for each data that will be shared with Bob. In other words, the proxy can share the authorized data with Bob via the re-encryption keys and form Alice, respectively. With the motivation in mind, we present an efficient and secure notion—universal conditional proxy re-encryption (UCPRE).
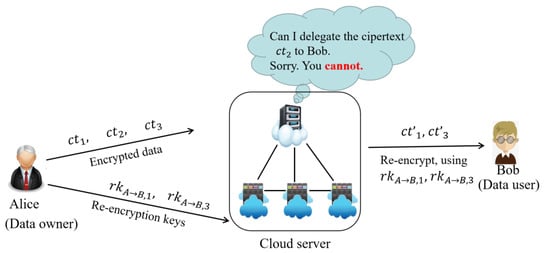
Figure 1.
UCPRE in a cloud data sharing system.
1.2. Related Work
Blaze et al. [1] proposed the notion of proxy re-encryption to achieve delegation rights from ciphertexts for Alice to ciphertexts for Bob. PRE has many real-world applications, such as outsourcing computation, distributed file storage systems, and secure email forwarding [3,4]. Since the concept of PRE was introduced by Blaze et al. [1], a rich line of works has studied the construction of PRE schemes [2,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21] with kinds of properties to satisfy different application demands. For instance, to integrate PRE into identity-based encryption (IBE) setting, Green and Ateniese [6] defined the notion of identity-based proxy re-encryption (IB-PRE). They also proposed two constructions in the random oracle model where the proxy can transfer ciphertexts from Alice’s identity to Bob’s identity. Later on, a PRE scheme with an anonymous technique designed by Liang et al. [9] has anonymous about the identity information of users and holds multisharing that the proxy can conditionally and securely share multiple times a ciphertext. Recently, Cao et al. [10] proposed a new notion of autonomous path PRE in which the delegator designates a privilege path with his predetermined multiple delegatees from high to low. In the meantime, a collusion-resistant IB-PRE scheme is designed by Paul et al. [11] that satisfies a CCA security based on the random oracle. However, the existing PRE schemes cannot support ciphertext switching between two encryption schemes. To solve this issue, Dottling and Nishimaki [2] present the notion of universal proxy re-encryption that allows the proxy to convert ciphertext into one of the possibly different encryption schemes. However, this scheme exist some disadvantages: first, it is a relaxed case that the delegator needs to execute a modified decryption algorithm to decrypt the ciphertext; second, the computing costs of the delegatee increase with the number of delegations.
Another interesting research is conditional proxy re-encryption (CPRE) which was introduced by Weng et al. [22]. CPRE is a variant of PRE, enabling the delegator to enforce fine-grained delegation of decryption rights. Later, Weng et al. [23] proposed a new CPRE scheme by reformalizing the definitions and security concepts. Subsequently, lots of CPRE schemes [24,25,26,27,28] have been proposed to improve efficiency and security. For instance, Liang et al. [26] proposed a conditional proxy re-encryption scheme based on hierarchical identity-based encryption that is efficient and achieves CCA security. Lately, an identity-based CPRE scheme with a revocable feature for secure cloud data sharing was presented by Yao et al. [27]. In the meantime, Paul et al. [28] presented an efficient CPRE scheme in which there are no pairing operations. Unfortunately, none of these works addressed the ciphertext switching issue.
1.3. Our Contributions
In this paper, we adopted the ciphertext switching mechanism between (possibly different) encryption schemes proposed for PRE [2] to add the feature of ciphertext switching for conditional PRE. Although the approach sounds straightforward, there are technical difficulties to apply ciphertext switching notion to conditional PRE because we found that the method of work in [2] cannot realize the fine-grained access control for data delegation. Meanwhile, the design of UPRE in [2] is a relaxed sense that the delegator needs to decrypt the ciphertext by the modified decryption algorithm. In this process, the delegatee in work [2] needs to undertake amounts of computing costs to recover the plaintext such that it is not applied to the cloud users with weak mobile devices. Therefore, this paper introduces a novel notion-universal conditional proxy re-encryption (UCPRE) with ciphertext switching from a homomorphic encryption scheme to a (possibly different) homomorphic encryption scheme. In our UCPRE, we achieve the fine-grained access control for the encrypted message. That is, the proxy cannot transfer the unauthorized encrypted data of the data owner by the re-encryption key. The method of our UCPRE allows the delegatee to perform the original decryption algorithm instead of the modified decryption algorithm. We also give the definition of security for our UCPRE and prove its HRA secure. Finally, the evaluation shows that our UCPRE is lightweight in terms of computing cost for each algorithm.
2. Preliminaries
This section reviews some useful definitions and operations used in the rest of the paper.
2.1. Homomorphic Encryption Schemes
We will define universal conditional proxy re-encryption (UCPRE) in Section 3. Our UCPRE allows the proxy to transfer the ciphertext of the delegator under an encryption scheme into the ciphertext of the delegatee under a (possibly different) encryption scheme . In the system, the schemes and are additively homomorphic encryption or multiplicatively homomorphic encryption , respectively.
Definition 1
(Additively homomorphic encryption (AHE) [29]). We say that the encryption scheme over the message space is additively homomorphic if Setup, KeyGen, Enc, Dec, , and ScalMul are the following probabilistic polynomial time algorithms:
- : It inputs a security parameter and outputs the public parameter Par. For simplicity, Par is omitted from the input of algorithms.
- : It inputs a security parameter and outputs the secret key sk and the public key pk.
- : It inputs the public key and a message and outputs a ciphertext ct.
- : It inputs a secret key sk and a ciphertext ct and outputs a message or a symbol ⊥.
- : It inputs a public key pk and the ciphertext ct encrypting m and the ciphertext encrypting and outputs a ciphertext so that .Dec .
- : It inputs a public key pk, a ciphertext ct encrypting m and a plaintext and outputs a ciphertext such that .Dec .
Definition 2
(Multiplicatively homomorphic encryption (MHE) [29]). We say that the scheme. over the message space is multiplicatively homomorphic if Setup, KeyGen, Enc, Dec, , and ScalMul are the following algorithms:
- Setup, KeyGen, Enc and Dec algorithms are the same as the Definition 1.
- : It inputs a public key pk and the ciphertext ct encrypting m and the ciphertext encrypting and outputs a ciphertext such that .Dec .
- : It inputs a public key , a ciphertext c encrypting m and a plaintext and outputs a ciphertext such that .Dec .
Note that the above encryption schemes need to satisfy the correctness in the usual situation. In addition, we require that the schemes are indistinguishable security under the standard model of the chosen-plaintext attack (IND-CPA). The reader refers to the work [30] for more details about the standard model definition of IND-CPA.
2.2. Hidden Secret Decryption
The encryption schemes used in the UCPRE have a vital character that supports hidden secret decryption. Hidden secret decryption means that these encryption schemes are provided with a algorithm Hidden Secret denoted by , which works as follows: it inputs a secret key sk and the ciphertext ct encrypting m, and outputs a hidden secret hsk, such that the semitrusted third party (e.g., cloud server) with the hidden secret key hsk can decrypt the ciphertext ct encrypting the message m. In other words, these schemes exist an algorithm Combine denoted by if they are equipped with the algorithm Hidden Secret. The algorithm Combine works as follows: it inputs the hidden secret hsk and the ciphertext ct, and outputs the message m or a symbol ⊥. In our UCPRE, we can take the hidden secret as a condition. When the semitrusted third party holds the condition hsk about the message m, it means that the semitrusted third party can decrypt the ciphertext ct encrypting m without obtaining information about another message encrypted by the secret key sk. In UCPRE, the delegator performs the algorithm HiddenSecert to set the hidden secret key hsk and shares it with the proxy so that the proxy decrypts the ciphertext encrypting by executing the algorithm Combine. This is because, in our context, the proxy does not decrypt the plaintext because it is disguised by a random element. Encryption schemes such as Elgamal [31], the extension of Elgamal [32] or RSA [33], satisfy all these properties.
The Elgamal Encryption. The Elgamal encryption [31] is homomorphic encryption scheme that is practical and universal in actual applications. In Section 5, we will employ an additive variation of the Elgamal for small domains plaintext space. Here we show the implementation of this scheme. By executing the algorithm Setup to generate the public parameter , where a generator g of multiplicative cyclic group of prime order p. We randomly select and compute , and then set the secret key and the public key . Encryption is executed by selecting and setting , where and . Decryption of a ciphertext is performed by computing . Then, the message m is retrieved through running an exhaustive search.
The Elgamal PKE with Hidden Secret Decryption. Setup, KeyGen, and Enc algorithms are the same as the above description of the Elgamal encryption. In our system, the user generates the hidden secret by the algorithm SecretHidden and sends it to the semitrusted third party. Finally, decryption of a ciphertext is executed by computing . Then, the message m is retrieved through running an exhaustive search.
The BBS Encryption. The BBS encryption [32] is multiplicatively homomorphic encryption that can be viewed as an extension of the Elgamal encryption. In Section 5, we will instantiate our generic construction UCPRE by transferring the ciphertext under the Elgamal encryption scheme into the ciphertext under the BBS encryption scheme. Here we show the implementation of this scheme. By performing the algorithm Setup to generate the public parameter , where a generator g of a multiplicative cyclic group of prime order p. To set the secret key and the public key , we chose random and compute and , and then set and . To encrypt a message , we select and set the ciphertext to be . Decryption is executed by computing .
The BBS Encryption with Hidden Secret Decryption. Setup, KeyGen, and Enc algorithms are the same as the above description of the BBS encryption. Then, the user generates the hidden secret by the algorithm SecretHidden and sends it to the third party. Finally, decryption of the ciphertext is performed by computing .
The RSA Encryption. The RSA encryption [33] is a multiplicative homomorphic encryption scheme. In Section 5, we will instantiate our generic construction UCPRE between RSA encryption schemes. Here we show the implementation of this scheme. By executing the algorithm KeyGen to generate the public key and the secret key , we firstly choose two big prime and set , and compute . Next, we choose a random e, and generate d, where and . Finally, we set the public key and the secret key . Encryption is executed by setting the ciphertext . Decryption of a ciphertext ct is performed by computing .
The RSA PKE with Hidden Secret Decryption. Key generation, and encrytion algorithms are the same as the above description of the RSA encryption. In our system, the user generates the hidden secret by performing the algorithm SecretHidden and sends it to the semitrusted third party secretly. Finally, decryption of a ciphertext ct is executed by computing .
3. Definition of Universal Conditional Proxy Re-Encryption
A UCPRE system includes three types of entities: the delegator, the proxy, and the delegatee. Our UCPRE allows the proxy to transfer the ciphertext of the public key (delegator) under a homomorphic encryption scheme into the ciphertext of the public key (delegatee) under a homomorphic encryption scheme that may be different from the scheme . A UCPRE scheme does not need to set setup, key generation, and decryption algorithms. That is, it generates the public parameter, key pairs, and decrypt the ciphertext by executing the existing schemes and . Therefore, UCPRE can be seen as a general construction of conditional proxy re-encryption. We give the definitions of syntax, correctness, and HAR security according to the works [2,34] (note that the notation and presentation have minor changes).
Notations. In our system, we denote separately delegator and delegatee key pairs by and and t mean “from” and “to”, respectively) if we emphasize which user is a delegator or delegatee. When we write , it mean that a key pair is generated by the key generation algorithm KeyGen of the scheme , where . When we write , it mean that the ciphertext encrypting m is generated by the key encryption algorithm Enc of the scheme . When algorithm of UCPRE take as an input (or ), we interpret it as a description of algorithms (rather than circuits or Turing machines).
3.1. Unidirectional and Multihop UCPRE
Definition 3
(UCPRE for Any Homomorphic Encryption: Syntax). A universal conditional proxy re-encryption scheme consists of two PPT lgorithms ReKeyGen and ReEnc shown as follows:
- ReKeyGen : It inputs the security parameter , a pair of homomorphic encryption schemes , a secret key and a public key of , a public key of , and and a ciphertext under of and outputs a re-encryption key .
- : It inputs a pair of homomorphic encryption schemes , a public key of , a re-encryption key , and outputs a re-encrypted ciphertextrct(note that the re-encrypted ciphertext rct be equal to the ciphertext under of .
Definition 4
(UCPRE for Any Homomorphic Encryption: Correctness). A UCPRE scheme for any homomorphic encryption is correct if for all pairs of homomorphic encryption schemes , , it holds that
where .
Security. In our UCPRE, we present the indistinguishable secure under honest re-encryption attacks (IND-HRA). This IND-HRA secure for UPRE is based on security against honest re-encryption attacks (HRA) of PRE proposed by Cohen [34]. Cohen observes that IND-CPA secure for PRE is not sufficient in actual applications. Therefore, we define IND-HRA secure for our UCPRE.
Definition 5
(UCPRE for Homomorphic Encryption: IND-HRA Secure). We define an indistinguishable experiment including three phases. The adversary is interactive with the challenger in the following indistinguishable experiment.
- Setup Phase 1: In this phase, the challenger generates all security parameters.
- –
- initializes a counternumkeys:=0, an honest indices setHon:=∅, and a corrupted indices setCor:=∅, a counter :=0, a key-value storeCt:= ∅, and a setDeriv:= ∅.
- –
- For an honest key generation query i, sets a new pair of keys ( and shares (, ) to . Moreover, the challenger needs to setHon:=Hon∪ i andnumkeys:=numkeys+1.
- –
- For an corrupted key generation query i, sets a new pair of keys ( and shares (, ) to . Moreover, the challenger needs to setCor:=Cor∪ i andnumkeys:=numkeys+1.
- Oracle Query Phase 2: In this phase, makes the following queries.
- –
- Encryption Oracle : For a query on , where numKeys, the challenger computes the ciphertext and setsnumCt:=numCt+1. Then, stores the value ct inCtwith key and return (numCt, ct).
- –
- Re-encryption Key Generation Oracle For a query on , where numKeys, outputs ⊥, if or Hon and Cor. Otherwise, the challenger returns the re-encryption key .
- –
- Challenge Oracle: For a query on , where Hon and , the challeger randomly chooses a bit b from and sets the challenge ciphertext . Meanwhile, setsnumCt:=numCt+1 and addsnumCtto the setDeriv, and stores the value inCtwith key and return (numCt, . We just do challenge query once.
- Decision Phase 3: In this phase, A outputs a bit , return win if . The advantage of is defined asWe say that our UCPRE is HRA secure if for any PPT adversary, it holds that
3.2. Re-Encryption Simulatability
Definition 6
(Re-encryption Simulatability [34]). A conditional PRE scheme is re-encryption simulatable if there exists a PPT algorithm ReEncSim with high probability over aux, for all :
where notation denotes statistical indistinguishability, and the values and are shown as follows:
When , it is special case. In other words, the scheme is re-encryption simulatable when the distribution of re-encryption ciphertexts likes the distribution of fresh ciphertexts.
Theorem 1.
If conditional PRE scheme is a CPA secure and re-encryption simulatable, then conditional PRE is HRA secure [34].
4. Generic Construction for UCPREA
In this section, we present our generic construction for UCPRE. Our UCPRE means that we adopted the ciphertext switching mechanism between (possibly different) encryption schemes proposed for PRE [2] to add the feature of ciphertext switching for conditional PRE. Meanwhile, our UCPRE is lightweight for the delegator and the delegatee. We also give the security proof of the UCPRE in this section.
4.1. Technical Overview
In this section, we provide a high-level overview of the techniques of our UCPRE system. To reach the ciphertext transformation mechanism between two (possibly different) homomorphic encryption schemes. A critical character of the encryption schemes used in the UCPRE is the fact that these schemes support the function of hidden secret decryption. In other words, these schemes are equipped with an algorithm HiddenSecret that is run by a delegator, which works as follows: it inputs his secret key and the ciphertext encrypting the message and outputs a hidden secret . After obtaining the hidden secret , the proxy can perform the algorithm Combine that takes as inputs the hidden secret and the ciphertext , and outputs the message . The proxy receives no information about the plaintext m because the plaintexts are masked by a random element in our context. Finally, the proxy performs the algorithm ScalMul that inputs the ciphertext encrypting the message and to generate the re-encryption ciphertext rct, where we have .
4.2. Generic Construction
Our UCPRE supports the proxy to convert the ciphertext of the delegator under an encryption scheme into the ciphertext of the delegatee under a (possibly different) encryption scheme . These schemes and are Additive homomorphism encryption scheme or Multiplicative homomorphic encryption scheme , respectively. Our generic construction for UCPRE consists of the algorithms ReKeyGen and ReEnc shown as follows:
- ReKeyGen : The delegator performs the algorithm ReKeyGen to set the re-encryption key . In the process, the delegator firstly runs the algorithm to generate ciphertext about message . Second, the delegator runs the algorithm to generate ciphertext about message . Third, the delegator executes the algorithm to generate the hidden secret key . Finally, we output the re-encryption key that includes , , and .
- (1)
- Compute : The delegator runs the algorithm in scheme to generate ciphertext about message . This algorithm inputs the public key of the delegator, a ciphertext encrypting the message m, and a message R and ouputs a ciphertext about message .
- (2)
- Compute : The delegator executes the algorithm in scheme to generate the ciphertext about message . This algorithm inputs the public key of the delegatee and a message and ouputs a ciphertext about message .
- (3)
- Compute : The delegator executes the algorithm in scheme to generate the hidden secret key about the secret key . This algorithm inputs the secret key of the delegator and a ciphertext and outputs the hidden secret key .
- (4)
- Output .
- ReEnc : The proxy parses that performs the algorithm ReEnc to set the re-encryption ciphertext . In the process, the delegator firstly runs the algorithm to recover the message . Second, the proxy runs the algorithm to generate re-encryption ciphertext rct. Finally, we output re-encryption ciphertext rct.
- (1)
- Compute : The proxy executes the algorithm in scheme to recover the message . This algorithm inputs the hidden secret key and a ciphertext encrypting the message and outputs the message .
- (2)
- Compute : The proxy executes the algorithm in scheme to generate the re-encryption ciphertext rct, where we have . This algorithm inputs the public key of the delegatee, the ciphertext , and the message and outputs the re-encryption ciphertext rct.
- (3)
- Output rct =
Correctness. We now verify the correctness of our UCPRE. In the UCPRE, we get the such that we get that by the correctness of the decryption algorithm of scheme .
Remark 1.
In our UCPRE, there are only re-encryption key generation and the re-encryption algorithm to achieve the feature of ciphertext switching between homomorphic encryption schemes. At the same time, the computing cost of delegates is not related to the number of time delegations. In addition, our UCPRE recognizes the fine-grained delegation by a new method that the re-encryption key is interrelated to the message. Our UCPRE is geared specifically for data sharing in clouds because the data owner has encrypted his all data via a popular homomorphic encryption scheme (e.g., the Elgamal encryption) and stored the encrypted data in the cloud server before deciding to share the data with the data users in the actual applications. Therefore, we design a mechanism that allows the proxy to transfer the ciphertext under a homomorphic encryption scheme into the ciphertext under a (possibly different) homomorphic encryption scheme.
4.3. Security Proof
In this section, we prove that our UCPRE is HRA secure. The proof is shown as follows.
Theorem 2.
If a homomorphic encryption scheme is CPA secure. Then UCPRE is CPA secure.
Proof.
For our UCPRE, the correctness of implies the correctness of resulting UCPRE because we have re-encrypted ciphertext rct generated by the algorithm , where . For any probabilistic and polynomial-time (PPT) adversary with advantage attack our scheme UCPRE, we can construct an efficient algorithm with advantage to attack the encryption scheme . We have because we have re-encrypted ciphertext rct generated by the algorithm , where . By the CPA secure of , the advantage is neglectable. Furthermore, the UCPRE scheme is CPA secure. ☐
Theorem 3.
If the distribution of re-encryption ciphertexts likes the distribution of fresh ciphertexts. Then our UCPRE is re-encryption simulatable.
Proof.
We prove that the UCPRE is re-encryption simulatable when We have , where is the ciphertext of the public key under the scheme . Therefore, we set the algorithm ReEncSim as such that both the algorithms ReEncSim and ReEnc are statistical indistinguishability. That is, the distribution of re-encryption ciphertexts likes the distribution of fresh ciphertexts. Consequently, the UCPRE is re-encryption simulatable. ☐
Theorem 4.
If a homomorphic encryption scheme is CPA secure and UCPRE is re-encryption simulatable. Then UCPRE is HRA secure.
Proof.
Here we first prove that the UCPRE is CPA secure if a homomorphic encryption scheme is CPA secure by the Theorem 2. Then, we prove that the UCPRE is re-encryption simulatable by the Theorem 3. Finally, by Theorem 1, we prove the UCPRE is HRA secure because UCPRE is CPA secure and UCPRE is re-encryption simulatable. ☐
5. Instantiation of Our Generic Construction
In this section we provide two kinds of instantiations of our generic construction. First, we provide an Instantiation 1 in which the proxy can transfer the ciphertext under an additively homomorphic encryption scheme (the Elgamal encryption [31]) into the ciphertext under a multiplicatively homomorphic one (the BBS encryption [32]-the extension of Elgamal). Then, we provide an Instantiation 2 by describing ciphertext transformation between the RSA encryption schemes [33]. Note that, the description of Elgamal, extension of Elgamal, and RSA encryption schemes in Section 2.2.
5.1. Instantiation 1
We suppose that the delegator is under the Elgamal encryptin scheme denoted by . That is, the delegator obtains a pair of keys throught the algorithm of , we randomly choose and set have and the public key . Meanwhile, the delegator generates the ciphertext encrypting the plaintext m via excuting the algorithm of , where and . Suppose that the delegatee is under the BBS encryption scheme denoted by . In other words, the delegatee gets a pair of keys via the algorithm of , we set and where , , . In our system, the proxy can transfer the ciphertext encrypting the plaintext m under the Elgamal encryption scheme into the ciphertext under the BBS encryption scheme, as described in the following procedure.
- ReKeyGen : The delegator performs the algorithm to set the re-encryption key from the delegator to the delegatee, where . First, the delegator sets the ciphertext encrypting the message by performing the algorithm of . For the algorithm , randomly choose and set , and , and returns . Second, the delegator generates the ciphertext encrypting the message by excuting the algorithm of . For the algorithm , randomly pick , and compute , , and , and return . Third, we generate a hidden secret by excuting the algorithm of . For the algorithm , we set and return . Finally, output .
- ReEnc : The proxy performs the algorithm to generate re-encryption ciphertext rct, where . First, the proxy decrypts the ciphertext by excuting the algorithm of . For the algorithm , the proxy sets . Then, the message is retrieved through running an exhaustive search. Second, the proxy obtains the ciphertext by excuting the algorithm of . For the algorithm , we compute , , and via encrypting , where . Next, we compute , , , and return .
5.2. Instantiation 2
We suppose that the delegator is under a RSA encryptin scheme denoted by . That is, the delegator obtains a pair of keys throught the algorithm of , we set the public key and the secret key . Meanwhile, The delegator generates the ciphertext encrypting the plaintext m via excuting the algorithm of , where . Suppose that the delegatee is under a RSA encryptin scheme denoted by . In other words, the delegatee gets a pair of keys throught the algorithm of , we set the public key and the secret key . In our system, the proxy can transfer the ciphertext encrypting the plaintext m under a RSA encryption scheme into the ciphertext under a RSA encryption scheme, as described in the following procedure.
- ReKeyGen : The delegator performs the algorithm to set the re-encryption key from the delegator to the delegatee, where . First, the delegator sets the ciphertext encrypting the message by performing the algorithm of . For the algorithm , the delegator choose a random R and sets , where . Second, the delegator generates the ciphertext encrypting the message by excuting the algorithm of . For the algorithm , the delagator computes . Third, the delegator generates a hidden secret by excuting the algorithm of . For the algorithm , we set and return . Finally, the algorithm outputs .
- ReEnc : The proxy performs the algorithm to generate re-encryption ciphertext rct, where . First, the proxy decrypts the ciphertext by excuting the algorithm of . For the algorithm , the proxy sets . Second, the proxy obtains the ciphertext by excuting the algorithm ScalMul of . For the algorithm , we compute via encrypting . Next, we compute , where we have Finally, return .
We can fully understand how our UCPRE realizes ciphertext transformation from a homomorphic encryption scheme to a (different) homomorphic encryption scheme throught the above Instantiation 1 and Instantiation 2.
6. Efficiency Analysis
We first define the notations used in Table 1. Notations and , and denote the times consumed for a pairing operation, and a modular exponentiation in , and a modular exponentiation in , separately. Notations Dec(Or) and Dec(Re) denote the decryption execution for the original ciphertext and the re-encryption ciphertext, respectively. Here, we omit the computing time of addition, multiplication, and hash function operations because these operations are much less modular exponentiation and pairing operations. As shown in Table 1, the computation overhead of the instantiation scheme for UCPRE in each algorithm is compared to other works.

Table 1.
Computing cost comparison.
- Enc. The instantiation scheme for UCPRE has lower computing cost to set the original ciphertext. Nevertheless, the delegator in works [24,25,26,27] have to undertake the amount of computing overhead in the encryption phase. For exzample, the delegator in work [27] needs to undertake 8 modular exponentiation operations in and a pairing operation for setting ciphertext.
- RKeyGen. Table 1 shows that scheme [27] and our scheme have lower computation overhead to generate the re-encryption key. However, the delegator in work [26] needs abundant computing overhead to set the re-encryption key.
- ReEnc. Table 1 shows that our instantiation scheme has less computing cost to execute the re-encryption algorithm for setting re-encryption ciphertext compared with the works [24,26]. While our scheme is less efficinet comparied with works [25,27] in the re-encryption phase. However, it cannot support the ciphertext switching functionality.
- Dec(Or). In the decryption algorithm for the original ciphertext, the delegator in our instantiation scheme and work [27] only executes lower computing costs to decrypt the original ciphertext. However, there are heavy computing overhead in works [24,25,26].
- Dec(Re). Table 1 shows that our instantiation scheme has less computing cost to execute the decryption algorithm for the re-encryption ciphertext compared with CPRE schemes [24,25,26,27].
The comparison results displayed in Table 1 clearly show that our UCPRE has the least computation overhead compared to related works. Meanwhile, our construction UCPRE adds the property of ciphertext transformation between two (different) homormorphic encryption schemes compared with conditional proxy re-encryption schemes. This function is important for a CPRE scheme that may be used in actual applications (e.g., data sharing in clouds).
7. Conclusions
We present a generic construction UCPRE named universal conditional proxy re-encryption in this article. Our solution supports fineness access control for sensitive data compared to the design of UPRE. In particular, our UCPRE is more applied in the real data sharing in clouds because it supports the flexible transformation of outsourced encrypted data between the (possibly different) homomorphic encryption schemes efficiently. Furthermore, our UCPRE is simple and efficient compared to the existing CPRE scheme via instantiating our generic construction. While this work achieves ciphertext switching between homomorphic encryption schemes for data sharing, it inspires some interesting open problems such as designing a UCPRE scheme to support the flexible transformation of ciphertext between any encryption schemes.
Author Contributions
Conceptualization, H.H., Y.Z., Z.C. and X.D.; methodology, H.H.; software, Y.Z.; validation, H.H.; formal analysis, H.H.; investigation, H.H.; resources, H.H.; data curation, H.H.; writing—original draft preparation, H.H.; writing—review and editing, H.H. and Y.Z.; visualization, Y.Z.; supervision, Z.C. and X.D.; project administration, Z.C.; funding acquisition, Z.C. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Key Research and Development Program of China (Grant No. 2020YFA0712300), in part by the National Natural Science Foundation of China (Grant No. 62132005, 62172162).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; pp. 127–144. [Google Scholar]
- Döttling, N.; Nishimaki, R. Universal Proxy Re-Encryption. In Proceedings of the Public-Key Cryptography—PKC 2021—24th IACR International Conference on Practice and Theory of Public Key Cryptography, Virtual Event, 10–13 May 2021; pp. 512–542. [Google Scholar]
- Liang, K.; Liu, J.K.; Wong, D.S.; Susilo, W. An efficient cloud-based revocable identity-based proxy re-encryption scheme for public clouds data sharing. In Proceedings of the European Symposium on Research in Computer Security, Wroclaw, Poland, 7–11 September 2014; pp. 257–272. [Google Scholar]
- Sun, M.; Ge, C.; Fang, L.; Wang, J. A proxy broadcast re-encryption for cloud data sharing. Multimed. Tools Appl. 2018, 77, 10455–10469. [Google Scholar] [CrossRef]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. 2006, 9, 1–30. [Google Scholar] [CrossRef]
- Green, M.; Ateniese, G. Identity-based proxy re-encryption. In Proceedings of the 14th International Conference on Applied Cryptography and Network Security, Zhuhai, China, 5–8 June 2007; pp. 288–306. [Google Scholar]
- Tang, Q.; Hartel, P.; Jonker, W. Inter-domain identity-based proxy re-encryption. In Proceedings of the International Conference on Information Security and Cryptology, Beijing, China, 14–17 December 2008; pp. 332–347. [Google Scholar]
- Matsuo, T. Proxy re-encryption systems for identity-based encryption. In Proceedings of the International Conference on Pairing-Based Cryptography, Tokyo, Japan, 2–4 July 2007; pp. 247–267. [Google Scholar]
- Liang, K.; Susilo, W.; Liu, J.K. Privacy-preserving ciphertext multi-sharing control for big data storage. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1578–1589. [Google Scholar] [CrossRef]
- Cao, Z.; Wang, H.; Zhao, Y. AP-PRE: Autonomous path proxy re-encryption and its applications. IEEE Trans. Depend. Secur. Comput. 2017, 16, 833–842. [Google Scholar] [CrossRef]
- Paul, A.; Srinivasavaradhan, V.; Selvi, S.S.D.; Rangan, C.P. A CCA-secure collusion-resistant identity-based proxy re-encryption scheme. In Proceedings of the International Conference on Provable Security, Jeju, Korea, 25–28 October 2018; pp. 111–128. [Google Scholar]
- Chung, P.S.; Liu, C.W.; Hwang, M.S. A Study of Attribute-based Proxy Re-encryption Scheme in Cloud Environments. IJ Netw. Secur. 2014, 16, 1–13. [Google Scholar]
- Liang, X.; Cao, Z.; Lin, H.; Shao, J. Attribute based proxy re-encryption with delegating capabilities. In Proceedings of the 4th International Symposium on Information, Computer, and Communications Security, Sydney, Australia, 10–12 March 2009; pp. 276–286. [Google Scholar]
- Li, K.; Zhang, Y.; Ma, H. Key policy attribute-based proxy re-encryption with matrix access structure. In Proceedings of the 2013 5th International Conference on Intelligent Networking and Collaborative Systems, Xi’an, China, 9–11 September 2013; pp. 46–50. [Google Scholar]
- Li, K.; Wang, J.; Zhang, Y.; Ma, H. Key Policy Attribute-based Proxy Re-encryption and RCCA Secure Scheme. J. Internet Serv. Inf. Secur. 2014, 4, 70–82. [Google Scholar]
- Ge, C.; Susilo, W.; Wang, J.; Huang, Z.; Fang, L.; Ren, Y. A key-policy attribute-based proxy re-encryption without random oracles. J. Cryptol. 2016, 59, 970–982. [Google Scholar] [CrossRef]
- Ge, C.; Susilo, W.; Fang, L.; Wang, J.; Shi, Y. A CCA-secure key-policy attribute-based proxy re-encryption in the adaptive corruption model for dropbox data sharing system. Design. Code. Cryptogr. 2018, 86, 2587–2603. [Google Scholar] [CrossRef]
- Paul, A.; Selvi, S.S.D.; Rangan, C.P. Efficient Attribute-Based Proxy Re-Encryption with Constant Size Ciphertexts. In Proceedings of the International Conference on Cryptology in India, Bangalore, India, 13–16 December 2020; pp. 644–665. [Google Scholar]
- Chu, C.K.; Weng, J.; Chow, S.S.; Zhou, J.; Deng, R.H. Conditional proxy broadcast re-encryption. In Proceedings of the Australasian Conference on Information Security and Privacy, Brisbane, Australia, 1–3 July 2009; pp. 327–342. [Google Scholar]
- Xu, P.; Jiao, T.; Wu, Q.; Wang, W.; Jin, H. Conditional identity-based broadcast proxy re-encryption and its application to cloud email. IEEE Trans. Comput. 2015, 65, 66–79. [Google Scholar] [CrossRef]
- Maiti, S.; Misra, S. P2B: Privacy preserving identity-based broadcast proxy re-encryption. IEEE Trans. Veh. Technol. 2020, 69, 5610–5617. [Google Scholar] [CrossRef]
- Weng, J.; Deng, R.H.; Ding, X.; Chu, C.; Lai, J. Conditional proxy re-encryption secure against chosen-ciphertext attack. In Proceedings of the 2009 ACM Symposium on Information, Computer and Communications Security, ASIACCS 2009, Sydney, Australia, 10–12 March 2009; pp. 322–332. [Google Scholar]
- Weng, J.; Yang, Y.; Tang, Q.; Deng, R.H.; Bao, F. Efficient Conditional Proxy Re-encryption with Chosen-Ciphertext Security. In Proceedings of the Information Security, 12th International Conference, ISC 2009, Pisa, Italy, 7–9 September 2009; pp. 151–166. [Google Scholar]
- Fang, L.; Susilo, W.; Ge, C.; Wang, J. Chosen-ciphertext secure anonymous conditional proxy re-encryption with keyword search. Theor. Comput. Sci. 2012, 462, 39–58. [Google Scholar] [CrossRef]
- Seo, J.W.; Yum, D.H.; Lee, P.J. Proxy-invisible CCA-secure type-based proxy re-encryption without random oracles. Theor. Comput. Sci. 2013, 491, 83–93. [Google Scholar] [CrossRef]
- Liang, K.; Susilo, W.; Liu, J.K.; Wong, D.S. Efficient and Fully CCA Secure Conditional Proxy Re-Encryption from Hierarchical Identity-Based Encryption. Comput. J. 2015, 58, 2778–2792. [Google Scholar] [CrossRef]
- Yao, S.; Dayot, R.V.J.; Kim, H.; Ra, I. A Novel Revocable and Identity-Based Conditional Proxy Re-Encryption Scheme with Ciphertext Evolution for Secure Cloud Data Sharing. IEEE Access 2021, 9, 42801–42816. [Google Scholar] [CrossRef]
- Paul, A.; Selvi, S.S.D.; Rangan, C.P. A Provably Secure Conditional Proxy Re-Encryption Scheme without Pairing. J. Internet Serv. Inf. Secur. 2021, 11, 1–21. [Google Scholar]
- Castagnos, G.; Imbert, L.; Laguillaumie, F. Encryption Switching Protocols Revisited: Switching Modulo p. In Proceedings of the Advances in Cryptology—CRYPTO 2017—37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; pp. 255–287. [Google Scholar]
- Katz, J.; Lindell, Y. Introduction to Modern Cryptography, 2nd ed.; CRC Press: Boca Raton, FL, USA, 2014. [Google Scholar]
- Gamal, T.E. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar]
- Boneh, D.; Boyen, X.; Shacham, H. Short Group Signatures. In Proceedings of the Advances in Cryptology—CRYPTO 2004, 24th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2004; pp. 41–55. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L.M. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Cohen, A. What About Bob? The Inadequacy of CPA Security for Proxy Reencryption. In Proceedings of the Public-Key Cryptography—PKC 2019—22nd IACR International Conference on Practice and Theory of Public-Key Cryptography, Beijing, China, 14–17 April 2019; pp. 287–316. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).