Separable Reversible Data Hiding in Encrypted AMBTC Images Using Hamming Code
Abstract
:1. Introduction
2. Related Works
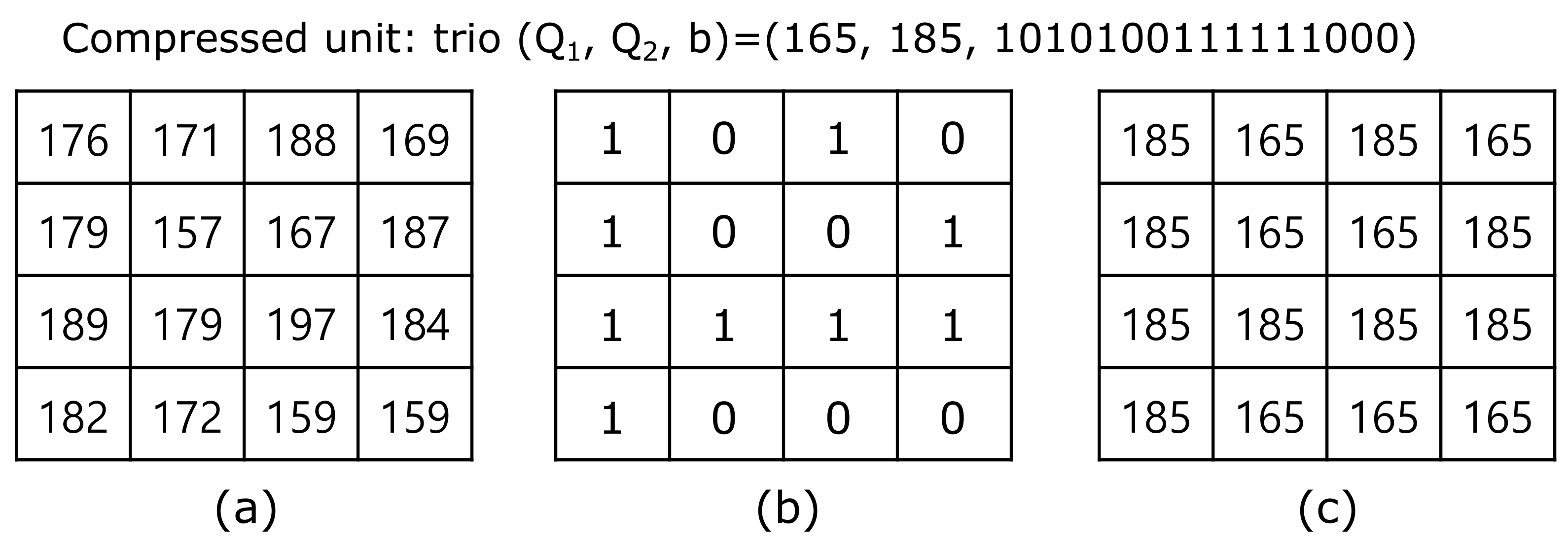
2.1. Absolute Moment Block Truncation Coding
2.2. Hamming Code
2.3. Yin et al.’s Scheme
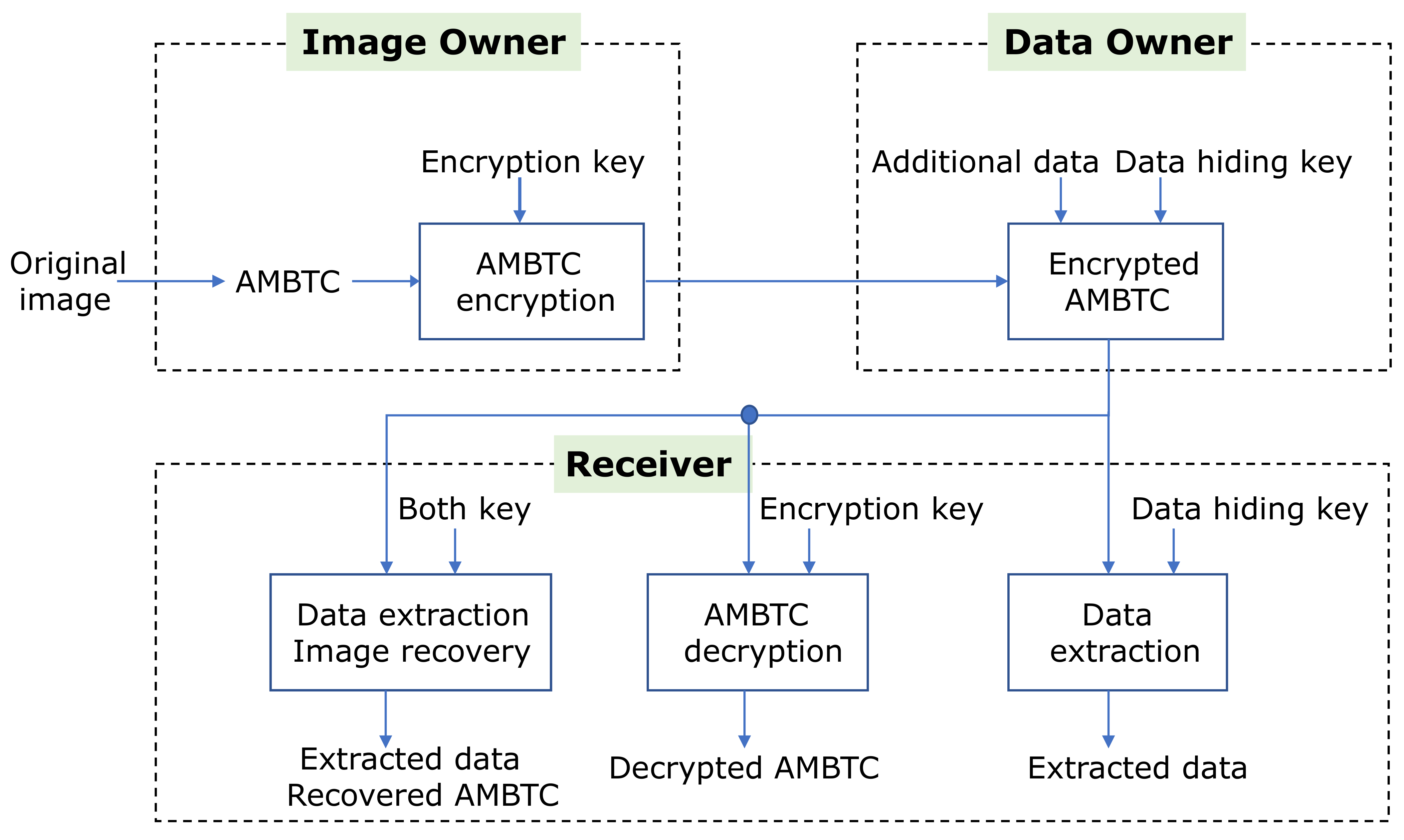
3. Proposed Scheme
3.1. AMBTC Image Encryption
- Input:
- An AMBTC cover image I and key EK.
- Output:
- An encrypted cover image I’ with size .
- Step 1:
- Read a from the cover image I, where Q1 and Q2 are the quantization levels and M is a bitmap M = (m1, m2, … , m15, m16).
- Step 2:
- The quantization levels are and , where is the Most Significant Bit (MSB) of and is the LSB of . Similarly, is MSB of and is the LSB of . is pseudo-random binary generated by the encryption key EK. Encryption for two quantization levels and is obtained by using Equations (10) and (11).Here, i is the index of the block and j is the subscript for the two quantization levels and converted into binary numbers.
- Step 3:
- For a bitmap of , a pseudo-random binary number r is generated by the image encryption key EK. An encrypted bitmap block is obtained by applying the XOR operation between the bitmap and the pseudo random bits r (Equation (12)).
- Step 4:
- If i is not the last block, it moves to Step 1 and repeats the given process. When the given procedure is completed, the encrypted AMBTC is finally generated.
3.2. Data Embedding
- Input:
- An encrypted AMBTC cover image and secret data
- Output:
- An encrypted marked image .
- Step 1:
- Read a from the encrypted AMBTC image , where and are the quantization levels and is a bitmap .
- Step 2:
- The exclusive-or operation between the secret message bits and the pseudorandom bits are calculated using Equation (13), where r is determined via DK using a standard stream cipher.
- Step 3:
- A bitmap is assigned to codeword c. For codeword c, the syndrome is obtained by employing Equation (14).
- Step 4:
- Exclusive-or operation is performed on the syndrome and the encrypted bits. That is, . If syndrome , this means no operation. Otherwise, flip the -th coordinate of c. For image restoration, the rows and columns of the changed location are obtained using Equation (15), where is the value of the row and column, and 4 bit information of is added to the last bit of . The needs to be converted to binary before it is added last to . In the formula, is first initialized to 0 and then the formula is applied.
- Step 5:
- After the operation, the codeword c is assigned to , i.e., . Add payload coordinates after bitmap . That is, .
- Step 6:
- Go to Step 1 to continue the embedding processes until all messages have been embedded in the encrypted cover image.
3.3. Data Extraction and Recovering Procedure
- Input:
- An encrypted AMBTC cover image sized , and both keys EK and DK.
- Output:
- A secret message and the cover image I sized and .
- Step 1:
- Read the i-th from the encrypted cover image , where and are the quantization levels and is a bitmap .
- Step 2:
- Assign the bitmap to codeword c, i.e., .
- Step 3:
- Calculate the syndrome for codeword c, and then assign the syndrome value to the secret bits , i.e., , . For the extracted 4-bit data, decoding is performed using r created by DK using a standard stream cipher. That is, .
- Step 4:
- Repeat Steps 1 and 3 for all blocks. Then, the secret data are recovered completely.
- Step 5:
- The original bitmap containing hidden bits can be recovered from the encrypted image by the EK. For decryption, the exclusive-or results of the encrypted bits and pseudo-random bits are calculated via Equation (16). This restores the bitmap .
- Step 6:
- In the data hiding process, the location of the codeword was changed, and to restore it during the image restoration process, the payload was attached to the back of and recorded. In this was, the bitmap M is restored. That is, after obtaining the changed matrix position(row, column) from the bitmap, the restored bitmap M is obtained using Equation (17), where is the row and is the column position of the location .
- Step 7:
- Repeat Steps 1 and 6 for all blocks. Then, all bitmaps are recovered completely.
4. Experimental Results and Discussion
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AMBTC | Absolute Moment Block Truncation Coding |
| BTC | Block Truncation Coding |
| DH | Data Hiding |
| RDH | Reversible Data Hiding |
| SRDH-EI | Separable RDH in an Encrypted Image |
| HC | Hamming Code |
| I | Cover Image |
| I′ | Encrypted Cover Image |
| I″ | Marked Image |
| g | pixel of grascale image |
| Q | quantization levels |
| M | bitmap |
| c | codeword |
| H | parity check matrix |
| m | hidden bits |
| syndrome | |
| EC | Embedding capacity |
| PSNR | Peak Signal-to-Noise Ratio |
| MSE | Mean-Squared Error |
| DE | Difference Expansion |
| HS | Histogram Shift |
References
- Bender, W.; Gruhl, D.; Morimote, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Kim, C.; Shin, D.-K.; Yang, C.-N.; Leng, L. Hybrid Data Hiding Based on AMBTC Using Enhanced Hamming Code. Appl. Sci. 2020, 10, 5336. [Google Scholar] [CrossRef]
- Yang, C.N.; Wu, S.Y.; Chou, Y.S.; Kim, C. Enhanced stego-image quality and embedding capacity for the partial reversible data hiding scheme. Multimed. Tools Appl. 2019, 78, 18595–18616. [Google Scholar] [CrossRef]
- Shi, Y.Q.; Li, X.; Zhang, X.; Wu, H.-T.; Ma, B. Reversible data hiding: Advances in the past two decades. IEEE Access 2016, 4, 3210–3237. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Wu, D.C.; Tsai, W.H. A steganographic method for images by pixel-value differencing. Pattern Recognit. Lett. 2013, 24, 1613–1626. [Google Scholar] [CrossRef]
- Alattar, A.M. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Process. 2004, 13, 1147–1156. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Tsai, P.Y.; Hu, Y.C.; Yeh, H.L. Reversible image hiding scheme using predictive coding and histogram shifting. Signal Process. 2009, 89, 1129–1143. [Google Scholar] [CrossRef]
- Abanda, Y.; Tiedeu, A. Image encryption by chaos mixing. IET Image Process. 2016, 10, 742–750. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Lü, J. Cryptanalyzing an image-scrambling encryption algorithm of pixel bits. IEEE Trans. Multimed. 2017, 24, 64–71. [Google Scholar] [CrossRef]
- Zhang, X. Reversible data hiding in encrypted image. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Ma, K.; Zhang, W.; Zhao, X.; Yu, N.; Li, F. Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans. Inf. Forensics Secur. 2013, 8, 553–562. [Google Scholar] [CrossRef]
- Zhang, W.; Ma, K.; Yu, N. Reversibility improved data hiding in encrypted images. Signal Process. 2014, 94, 118–127. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.S.; Wu, H.Y. An improved reversible data hiding in encrypted images using side match. IEEE Signal Process. Lett. 2012, 19, 199–202. [Google Scholar] [CrossRef]
- Liao, X.; Shu, C. Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J. Vis. Commun. Image Represent. 2015, 28, 21–27. [Google Scholar] [CrossRef]
- Wu, X.; Sun, W. High-capacity reversible data hiding in encrypted images by prediction error. Signal Process. 2014, 104, 387–400. [Google Scholar] [CrossRef]
- Yin, Z.; Abel, A.; Zhang, X.; Luo, B. Reversible data hiding encrypted image based on block histogram shifting. In Proceedings of the 2016 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Shanghai, China, 20–25 March 2016; pp. 2129–2133. [Google Scholar]
- Zhang, X. Separable reversible data hiding in encrypted image. IEEE Trans. Inf. Forensics Secur. 2012, 7, 826–832. [Google Scholar] [CrossRef]
- Qian, Z.; Han, X.; Zhang, X. Separable reversible data hiding in encrypted images by n-nary histogram modification. In Proceedings of the 3rd International Conference on Multimedia Technology (ICMT-13), Guangzhou, China, 29 November–1 December 2013; pp. 869–876. [Google Scholar]
- Yin, Z.; Luo, B.; Hong, W. Separable and error-free reversible data hiding in encrypted image with high payload. Sci. World J. 2014, 2014, 604876. [Google Scholar] [CrossRef]
- Yin, Z.; Niu, X.; Zhang, X.; Tang, J.; Luo, B. Reversible data hiding in encrypted AMBTC images. Multimed. Tools Appl. 2018, 77, 18067–18083. [Google Scholar] [CrossRef]
- Wang, H.Y.; Lin, H.J.; Gao, X.Y.; Cheng, W.H.; Chen, Y.Y. Reversible AMBTC-based data hiding with security improvement by chaotic encryption. IEEE Access 2019, 7, 38337–38347. [Google Scholar] [CrossRef]
- Su, G.; Chang, C.; Lin, C. A high capacity reversible data hiding in encrypted AMBTC-compressed images. IEEE Access 2020, 8, 26984–27000. [Google Scholar] [CrossRef]
- Delp, E.; Mitchell, O. Image compression using block truncation coding. IEEE Trans. Commun. 1979, 27, 1335–1342. [Google Scholar] [CrossRef]
- Lema, M.D.; Mitchell, O.R. Absolute moment block truncation coding and its application to color images. IEEE Trans. Commun. 1984, 32, 1148–1157. [Google Scholar] [CrossRef]
- Chuang, J.C.; Chang, C.C. Using a simple and fast image compression algorithm to hide secret information. Int. J. Comput. Appl. 2006, 28, 329–333. [Google Scholar]
- Ou, D.; Sun, W. High payload image steganography with minimum distortion based on absolute moment block truncation coding. Multimed. Tools Appl. 2015, 74, 9117–9139. [Google Scholar] [CrossRef]
- Chen, J.; Hong, W.; Chen, T.S.; Shiu, C.W. Steganography for BTC compressed images using no distortion technique. Imaging Sci. J. 2013, 58, 177–185. [Google Scholar] [CrossRef]
- Rurik, W.; Mazumdar, A. Hamming codes as error-reducing codes. In Proceedings of the 2016 IEEE Information Theory Workshop (ITW), Cambridge, UK, 11–14 September 2016; pp. 404–408. [Google Scholar]
- Moon, T.K. Error Correction Coding–Mathematical Methods and Algorithms; John Wiley and Sons: Hoboken, NJ, USA, 2005; pp. 2001–2006. [Google Scholar]
- Image Databases. Available online: https://www.imageprocessingplace.com/root_files_V3/image_databases.htm (accessed on 10 August 2022).



| Images | Cover AMBTC | Encrypted AMBTC | Decrypted AMBTC | |||
|---|---|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | PSNR | SSIM | |
| Barboon | 26.9765 | 0.8872 | 9.5038 | 0.0147 | 26.9757 | 0.887 |
| Barbara | 27.0756 | 0.9248 | 7.8847 | 0.0140 | 27.0702 | 0.923 |
| Boat | 31.5700 | 0.9388 | 8.9932 | 0.0146 | 31.5444 | 0.9355 |
| Goldhill | 32.8360 | 0.9208 | 9.0695 | 0.0159 | 32.8207 | 0.9196 |
| Airplane | 32.0372 | 0.9504 | 8.7070 | 0.0150 | 32.0017 | 0.9462 |
| Lena | 33.6556 | 0.9468 | 9.3058 | 0.0167 | 33.599 | 0.9423 |
| Pepper | 34.0968 | 0.9395 | 9.1550 | 0.0147 | 34.0397 | 0.9356 |
| Tiffany | 35.6576 | 0.9473 | 6.8659 | 0.0140 | 35.5651 | 0.9426 |
| Zelda | 36.6537 | 0.9476 | 8.8716 | 0.0140 | 36.5378 | 0.9432 |
| Average | 32.3736 | 0.9337 | 8.6421 | 0.0153 | 32.2394 | 0.9306 |
| Images | T = 5 | T = 10 | T = 15 | T = 20 | ||||
|---|---|---|---|---|---|---|---|---|
| EC (Bits) | PSNR | EC (Bits) | PSNR | EC (Bits) | PSNR | EC (Bits) | PSNR | |
| Baboon | 1113 | 26.9757 | 10121 | 26.9571 | 18,649 | 26.9161 | 24,557 | 26.8607 |
| Barbara | 14,889 | 27.0702 | 26,493 | 27.0485 | 32,125 | 27.0208 | 35,153 | 26.9922 |
| Boat | 28,217 | 31.5444 | 36,133 | 31.5034 | 42,313 | 31.4161 | 47,357 | 31.2857 |
| Goldhill | 9385 | 32.8207 | 27,769 | 32.6851 | 41,445 | 32.4429 | 48,965 | 32.1992 |
| Airplane | 34,549 | 32.0017 | 44,637 | 31.9485 | 49,469 | 31.8705 | 52,657 | 31.7764 |
| Lena | 29,677 | 33.599 | 44,217 | 33.4861 | 50,637 | 33.3503 | 54,329 | 33.2079 |
| Pepper | 21,149 | 34.0397 | 45,997 | 33.8319 | 52,921 | 33.6764 | 56,149 | 33.5425 |
| Tiffany | 29,381 | 35.5651 | 45,457 | 35.3734 | 52,609 | 35.1416 | 56,497 | 34.9002 |
| Zelda | 23,301 | 36.5378 | 49,093 | 36.1607 | 55,857 | 35.9139 | 59,365 | 35.6629 |
| Average | 21,295 | 32.2393 | 36,657 | 32.1105 | 44,002 | 31.9720 | 48,336 | 29.0427 |
| Images | Cover Images | Yin et al.’s [22] | Proposed Method | ||||
|---|---|---|---|---|---|---|---|
| PSNR | Payload | PSNR | PSNR2 | Payload | PSNR1 | PSNR2 | |
| Baboon | 26.9765 | 141 | 23.66 | 1113 | 26.9757 | ||
| Boat | 31.57 | 554 | 30.32 | 28,217 | 31.5444 | ||
| Airplane | 32.0372 | 1458 | 30.40 | 34,549 | 32.0017 | ||
| Lena | 33.6556 | 1213 | 33.00 | 29,677 | 33.5990 | ||
| Tiffany | 35.6576 | 1687 | 29.81 | 29,381 | 35.5651 | ||
| Average | 31.9793 | 1010 | 27.93 | 24,587 | 31.9371 | ||
| Images | Yin et al.’s (2018) [22] | Wang et al. (2019) [23] | Su et al.’s (2020) [24] | Proposed |
|---|---|---|---|---|
| Baboon | 273 | - | 14,976 | 64,881 |
| Boat | 932 | 22,050 | 29,382 | 65,369 |
| Airplane | 1365 | 23,610 | 34,564 | 65,013 |
| Lena | 1270 | 22,287 | 36,418 | 65,329 |
| Barbara | 524 | - | 13,644 | 62,945 |
| Peppers | 926 | 22,142 | 41,080 | 64,929 |
| Average | 881 | 22,522 | 28,344 | 64,744 |
| Method | Criterion | |||
|---|---|---|---|---|
| Separable | Error in Extracted Data | Error in Reconstructed Cover Image | Embedding Efficiency | |
| Ma et al.’s [13] | O | X | X | Mid |
| Zhang’s [12] | X | X | O | Low |
| Zhang et al.’s [19] | O | X | X | Low |
| Yin et al.’s [22] | O | X | O | High |
| Wang et al.’s [23] | O | X | O | High |
| Su et al.’s [24] | O | X | O | High |
| Proposed | O | X | O | High |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, C. Separable Reversible Data Hiding in Encrypted AMBTC Images Using Hamming Code. Appl. Sci. 2022, 12, 8225. https://doi.org/10.3390/app12168225
Kim C. Separable Reversible Data Hiding in Encrypted AMBTC Images Using Hamming Code. Applied Sciences. 2022; 12(16):8225. https://doi.org/10.3390/app12168225
Chicago/Turabian StyleKim, Cheonshik. 2022. "Separable Reversible Data Hiding in Encrypted AMBTC Images Using Hamming Code" Applied Sciences 12, no. 16: 8225. https://doi.org/10.3390/app12168225
APA StyleKim, C. (2022). Separable Reversible Data Hiding in Encrypted AMBTC Images Using Hamming Code. Applied Sciences, 12(16), 8225. https://doi.org/10.3390/app12168225






