Abstract
The connectivity of devices through the internet plays a remarkable role in our daily lives. Many network-based applications are utilized in different domains, e.g., health care, smart environments, and businesses. These applications offer a wide range of services and provide services to large groups. Therefore, the safety of network-based applications has always been an area of research interest for academia and industry alike. The evolution of deep learning has enabled us to explore new areas of research. Hackers make use of the vulnerabilities in networks and attempt to gain access to confidential systems and information. This information and access to systems can be very harmful and portray losses beyond comprehension. Therefore, detection of these network intrusions is of the utmost importance. Deep learning based techniques require minimal inputs while exploring every possible feature set in the network. Thus, in this paper, we present a one-dimensional convolutional neural network-based deep learning architecture for the detection of network intrusions. In this research, we detect four different types of network intrusions, i.e., DoS Hulk, DDoS, and DoS Goldeneye which belong to the active attack category, and PortScan, which falls in the passive attack category. For this purpose, we used the benchmark CICIDS2017 dataset for conducting the experiments and achieved an accuracy of 98.96% as demonstrated in the experimental results.
1. Introduction
In recent years many organizations have been increasingly exposed to advanced cyber threats which led to the development of the novel intrusion detection system (IDS). The invention of IDSs affects deals with both the academic community and the industry globally since it affects economic costs, damages to reputation, and legal sequences, by every cyber-attack. It is therefore of considerable importance for networks to be secured from unauthorized access, for user interaction and user data to be protected [1], and to disclose new security vulnerabilities.
An efficient security strengthening tool for detecting and protecting cyber assaults on any network or host is the IDS. IDSs are accountable for the detection of suspicious behaviors and the adequate protection of the network against attacks and the reduction in losses such as financial and functional [2].
IDSs can be classified in the literature as an anomaly [3], signature [4], or as a hybrid mix [5] of the two. Intrusion detection systems based on the signature (SIDS), which is also known as Rule IDS, conduct continuous network traffic monitoring and searches for inbound network traffic sequences or patterns that meet the signature of the attack. The signature of the attack can be recognized based on the headers of the network packets, destination addresses or the source network, data sequences corresponding to the known malware pattern, data sequences, or packet series known for a particular assault. They work with great efficiency in the identification of potential known incursions by maintaining low failure rates. Unfortunately, a database of the system must be manually updated by the admin, and SIDS can identify only those intrusions that exist in the system’s database, excluding fresh attack detection.
Anomaly-based intrusion detection systems (AIDS), or behavioral detection systems, examine the usual behavior of networks by monitoring the network deeply to detect suspicious activity. To identify new forms of intrusions, AIDS can learn using anomaly detecting algorithms or train itself with reinforcement learning algorithms. Anomaly-based systems demonstrate a substantial difference in the identification of new threats compared to signature-based ones. In addition, it is difficult for the intruders to determine which intrusion actions would not be identified to adapt the configuration profile of each system [6].
Recently, Machine Learning (ML) based AIDS enhancement (MLAIDS) algorithms have been developed [7]. These algorithms assess the network status via classification in normal or abnormal classes of the processed data. These algorithms train and test AIDS for assaults and accuracy to assess AIDS’ capabilities with various datasets. However, the majority of these datasets are severely unbalanced. The majority (98%) of these datasets are considered to be normal, while the remainder (2%) are classified as attacks [8].
A hybrid Intrusion Detection System (HIDS) can combine the benefits of both anomalies as well as signature systems and enhance the detection and erosion of known intrusion threats. Most recent hybrid IDSs are built on deep learning techniques and machines. Because of AIDS benefits in the zero-day assaults field, the newly proposed model also develops a deeply learned anomaly-based intrusion detection system.
1.1. Feature-Based Classification
IDSs employ traffic packets in network flows, by source/destination IP, source/destination port, timestamp, and protocol [9] to function correctly and identify an anomalous activity effectively [10]. In another research study [11], the authors mentioned the full-flux exchange of successive network packets between an IP address port and a port at a different IP address using a specific application protocol is a unidirectional exchange of packets. For efficient flow management, machine learning operations, and processing traffic classification is therefore necessary.
Flow technique is a recent development that can overcome various additional restrictions, such as unsaved port numbers, and encrypted packets. In the flow-based method, flow features are used as discriminators to exploit the variety of network packets and various classes [12]. In addition, due to the lack of payload, flow-based methods are preferable rather than payload methods for data protection problems. A flow-based classification of traffic uses high precision, accuracy approaches, and a vast study field.
1.2. Machine and Deep Learning Using IDS
IDSs play a significant role in cybersecurity as they monitor the network to protect it from cyber threats. Following are a few frequently used methods in the research conducted: Support Vector Machines (SVM), Random Forests (RF), Artificial Neural Networks (ANN), Self-Organizing Map (SOM), etc.
An up-to-date and elaborated dataset including numerous features and criteria was essentially required by the researchers. They were required during experiments, evaluation, and model testing on the given modern networks [13,14]. Not all datasets provided in the experiments deliver all the features provided in the literature. So thus only a few well-known datasets are referred to.
Network attacks have become common nowadays due to which datasets are continuously evaluated. The KDD 99 [15], CAIDA [16], ISCX2012 [17], and KYOTO [18] are a few datasets that were frequently used as they represented real-world network traffic. Despite their use, they are now outdated. Currently, the CICIDS2017 dataset is widely used. It is commonly used in the field of research. One of the main reasons for its popularity is that it was introduced to overcome the problems noticed in previous datasets [9] apart from this advantage it also holds numerous traffic types, furthermore, it also contains real-world network traffic. Although CICIDS2017 is an appropriate dataset there is a major issue that needs to be resolved. The consequences of this issue leads to high-class imbalance which directly misleads the classifier [13]. Although a new dataset named CIS AWS 2018 [19] has appeared, which is quite similar to CICIDS2017, its previous version is not reported yet. In this research we detect two different attacks; active and passive where DoS Hulk, DoS GoldenEye, and DDoS belong to the active attacks while PortScan belongs to the passive attacks. A detailed description of the attacks and their types has been given in Table 1.

Table 1.
Types of Attack.
In this study, our objective is to develop an anomalous network intrusion system based on flow-based statistics, using the CICIDS2017 dataset which detects and classifies every form of assault in a multi-categorization utilizing a high degree of accuracy. Deep learning approaches in the field of machine learning were used to accomplish flow categorization. Great success has been noted with the use of deep learning. In this research we used one dimensional convolutional neural networks (1D CNN), which works quite well on textual data in order to identify network intrusions and classify various types of threats. To identify network traffic, we created an enhanced deep neural network model based on 1D CNN. As a result, this study proposes a flow-based anomaly detection system based on deep learning. Furthermore, the main contributions are described below:
- Proposed an efficient complete system for NIDS using deep learning-based approach.
- Presented a comprehensive analysis of existing techniques based on machine learning and state-of-the-art deep learning.
- In-depth analysis of the CICIDS2017 dataset.
- Presented a detailed comparison with existing Network Intrusion Detection Systems
- Proposed one-dimensional convolution neural network-based multi-class classification technique.
The structure of this paper is organized as follows. Section 2 analyzes most of the related work of network intrusion systems utilizing deep learning and machine learning models. Section 3 discusses the dataset and its pre-processing method. Section 4 presents our proposed work utilizing deep learning techniques for network intrusion detection. The outcomes and discussion for our model are discussed in Section 5. Finally, Section 6 summarizes the findings and provides a few recommendations for future research.
2. Related Work
Machine learning is taking over the current era and is transforming the current era into a revolutionary practical world where intelligent machines complete tasks that were performed by humans in the past. Network Intrusion detection is a type of anomaly detection mechanism used to classify network anomalies. In the field of information security, network intrusion detection has become the most essential component of the infrastructure of defensive networking systems. Different machine learning techniques or approaches in NIDS are used to identify and discriminate between normal traffic, network attack, and abnormalities. K-nearest neighbor (K-NN) [1], Decision trees [2], Nave Bayes networks [3], artificial neural network (ANN) [4] and SOM [5], SVM [6], and are among these techniques where most of the researchers are using various IDS dataset, for the training and evaluation.
Siddiqui et al. [13] used the NSL-KDD dataset to investigate intrusion detection (ID), and its attributes are classified as basic, content, traffic, and host. These classifications evaluate ID based on False Alarm Rate (FAR) and Detection rate (DA) [14]. The results show that 81.2% and 72.9% of the threats were detected properly. Revolutionary energy architecture based on blockchain and deep learning for protecting the smart grid from cyber assaults named DeepCoin is presented by Ferrag et al. [16]. With deep learning being used in the block-based network, they employed the realistic Byzantine fault tolerance method recurrent neural network model (RNN). For the assessment and performance testing of their model, three distinct datasets are used: CICIDS2017, a dataset on power systems, and a dataset on web robots (Bots) the Internet of Things.
Zhang et al. [9] proposed a neural network-based anomaly detection model with the LeNet 5 convolution neural network and LSTM for feature removal. The studies were carried out utilizing binary and multi-classification using CICIDS2017 and CTU datasets. CNN, LSTM, and the hybrid combinations were performed, which resulted in improved performance in both binary and multi-classification tests. A distributed intrusion detection system for cloud settings is proposed by Idhammad et al. [20]. Firstly, the Naive Bayes Model is used to detect the anomaly and to preprocess data, and then a Random Forest classifier to determine the nature of each attack for multi-classification is used. Experiments were performed using parameters such as false-positive rate (FPR) and accuracy utilizing the CICDDS-001 dataset.
Radford et al. [21] proposed an LSTM-based deep learning model for anomaly detection sequence. To put the proposed model into operation, the authors used embedded sequences through which two bidirectional LSTM models have been passed. For evaluating the model CICIDS2017 dataset was used. The tests have been carried out using CICIDS2017 and the findings are aimed at multi-classification.
Islam et al. [22] proposed a framework based on deep learning for the identification of anomalous network traffic in the TCP/IP packets used to construct the network traffic configuration. The authors compared the performance of four different Artificial Neural Network (ANN) models using the publicly available NSLKDD network intrusion dataset. An overall accuracy of 96.74% was achieved using a particular configuration of parameters of the ANN model. Furthermore, the authors also claim that the proposed model can be effective for particularly smart factories management systems.
Hanif et al. [23] recently tried to put together an intrusion detection system for IoT devices; particularly for solving the authentication issues within IoT devices. The authors proposed the use of a supervised learning algorithm in order to detect the intrusion attacks and discard commands classified as threats at the controller level. Furthermore, ANN was used for the identification of intrusions and the UNSW-15 dataset was used for training the model. An average precision of 84% was reported while undergoing 10-fold cross validation.
Peng et al. [24] evaluated deep learning-based systems in adversarial environments for network intrusion detection. The authors aimed to analyze the resilience of Network Intrusion Detection (NID) systems based on deep learning in an adversarial environment by proposing four frameworks; Deep Neural Networks (DNN), Support Vector Machine (SVM), Random Forest (RF) and Logistic Regression (LR) using the NSL-KDD dataset. The experimental results proved that the DNN based model is more effective in detecting network intrusions.
Also, an intrusion detection method based on artificial neural networks (ANN) and fuzzy clustering were presented by Wang et al. [25]. The FC-ANN method consists of three major modules: fuzzy clustering, ANN, and fuzzy aggregation. The fluffy module for clustering divides a given collection of data into clusters. Every subset’s pattern is learned using the ANN module. The fuzzy aggregation module is used to combine the results of various ANNs and decrease detection errors. The FC-ANN method was evaluated on the KDD CUP 1999 dataset and shown to be effective against low-frequency assaults such as R2L and U2R.
A CNN based novel network intrusion detection system is presented by L. Chen et al. [26] to address the issue of malicious network traffic identification. The authors proposed a novel CNN based system for NIDS and trained their deep learning-based CNN model using raw network traffic and extracted features as well. The CICIDS 2017 dataset was used to train the model. Furthermore, the authors claim that the model trained on raw network traffic performs better when compared with the CNN model trained on the previously extracted features.
Ran et al. [27] present an ensemble-based technique for the detection of network anomalies in an intrusion detection system. This technique uses an ensemble of learning and prediction mechanisms for the multi-class classification of anomalies. Initially, researchers used ANOVA F-test as the univariate feature selection technique for determining the feature performance and the relationship between class labels and data features [28,29]. Furthermore, they used an automated machine learning model as a learning mechanism and a Kalman filter as a prediction model. They used a Bayesian optimizer as an optimization function for neural network architecture search (NAS) that selects architecture from a set of architectures list that maximizes the accuracy. This ensemble method uses a weighted voting mechanism that weights the prediction of both algorithms based on average prediction accuracy. They evaluated the performance of the proposed technique on publicly available CICIDS2017 and UNSW-NB15 datasets and achieved an accuracy of 97.02 and 98.801%, respectively.
Azizjon et al. [30] proposed a 1 Dimensional Convolution Neural Network (1D CNN) for the detection of network intrusions. In order to create an invasive Internet traffic model for the IDS, the authors serialize Transmission Control Protocol/Internet Protocol (TCP/IP) packets over a set time period. Normal and abnormal network traffic are then identified and tagged for supervised learning in the 1D-CNN.
Vinayakumar et al. [31] used a CNN algorithm built on deep learning for IDS. They created the CNN-RNN, CNN-LSTM, and CNN-GRU hybrid network models and tested them on the KDDCup 99 dataset. Their hybrid CNN-LSTM model achieves 99.7% accuracy in two-class classification and 98.7% accuracy in five-class classification.
Our literature review concluded that there is a dire need to develop a new system for network intrusion detection based on sophisticated methods such as DL. Despite some of the existing techniques achieving high accuracy, there are still some weaknesses in the detection systems, such as average or inconsistent levels of accuracy, long training period, non-existence of automatic systems, and dependence upon human operators and modified datasets. These weaknesses create the vacuum to develop new state-of-the-art systems to fill this gap. This field is preliminary, where most researchers try to experiment with different algorithms and methods to establish the most reliable and successful method for a particular dataset. We also assume that our work presented in this study would add a significant contribution to NIDS based on the DL approach.
3. Preprocessing and Data Analysis
3.1. CICIDS2017 Dataset Description and Analysis
The work conducted in the research is based on a benchmark intrusion dataset known as CICIDS-2017; this is because it holds various features and also fulfills the majority of the criteria. The dataset used is beneficial as it manages the majority of network real-world network attacks. Moreover, it contains most data network attacks. The dataset used in the research was developed by the University of New Brunswick (UNB) incorporated with the Canadian Institute of cybersecurity.
The dataset holds both normal and abnormal network traffics, where benign is normal and different categories of attacks are abnormal network traffic which is attained by capturing the data of 5 consecutive days. The acquired data was divided into 8 different files. In the captured data each day a data attack was found which contradicted the previous attack.
3.2. Data Preprocessing
Data Pre-processing is a technique used in data mining for the transformation of raw data into a format that can be utilized efficiently. It encompasses different techniques for data cleaning, data transformation, and data reduction. Data Cleaning is an essential step in pre-processing that removes the irrelevant and missing information from the dataset that could lead to the incorrect estimation of the target class.
There were a total of 8 different files that were merged into one single file and the entire work presented was relying on this file. The different types of attacks noticed are displayed in Table 2. In total, they were 2,830,743 examples included in 15 classes as shown in Table 3. On the other hand, the number of instances per class is presented in Table 4.

Table 2.
Description of CICIDS2017 Dataset.

Table 3.
CICIDS2017 Dataset characteristics.

Table 4.
Class wise Instances after Preprocessing.
Each row in the dataset contained nearly 83 features. The CICI Flow Meter is also responsible for generating bidirectional flow. In this flow, the first packet is accountable for both forward and backward directions. The forward direction is from source to direction whereas the backward direction is from destination to source. Therefore, it can be demonstrated that in total there are 83 statistical features which include both the data from back and reverse directions.
In the research, the subset of the original 83 features was utilized excluding a few features. Some of these excluded features were IPs of the source to destination, timestamp, the ID of flow, etc. As a result, nearly 79 features were left. Out of the remaining features, the last feature, i.e., the 79th feature represents the category of traffic prescribed in the present Bi-flow; this is denoted as the label.
Upon investigation, we identified that the dataset contains 135,000 values that are either missing or contain infinite floating-point values that can’t be processed. So, we removed those data instances from the dataset. The dataset used contains 83 distinct features for the classification of network activity. Table 5 shows some of the most discriminative features along with their variance ratios. From Table 3, we can analyze that the dataset is highly imbalanced, and applying the machine learning algorithms to the imbalanced dataset could lead to more bias toward the majority class [32]. So, we removed the classes that are highly imbalanced and utilized the random under-sampling technique to decrease the size of the majority class. Table 4 shows the number of class-wise instances that we are using for this research.

Table 5.
Dataset Discriminative features.
4. Methods
Deep learning is considered one of the latest achievements in machine learning. It helped the researchers to develop the solutions that could only be assumed a decade before because of the unavailability of data management, and data processing resources.
In this research, we use one-dimensional CNN (1D-CNN) for the detection of network intrusion. 1D-CNN is designed specifically to operate in 1-dimensional data. Researchers have proposed different variants of 2D-CNN to develop the solutions for one-dimensional data due to the following reasons:
- I.
- Forward propagation (FP) and Backward propagation (BP) is considered the major component of the CNN architecture. The computational complexity of 1D-CNN is reduced by a significant factor as compared to 2D-CNN due to the involvement of matrix operations.
- II.
- Shallow network architectures are easier to understand, train, and implement, and they can learn from the challenging 1D data. Conversely, 2D-CNN with deep architectures might be required to perform the task.
- III.
- 1D-CNN can train to utilize less computational resources for 1D data whereas 2D-CNN requires specialized hardware for this purpose.
1D-CNN consists of 1-dimensional convolution layers, pooling layers, dropout layers, and activation functions for handling the 1-dimensional data. 1D-CNN is configured using the following hyper-parameters: number of CNN layers, neurons in each layer, size of the filter, and subsampling factor of each layer.
The convolution layer is the basic application of the filter to an input. Utilizing the filtering operation repeated times creates a feature map, which indicates the particular attributes related to the data points. Convolution is a linear operation that involved containing the multiplication with inputs with a set of weights. For this case, inputs are multiplied with the single-dimensional array weights, known as the kernel. This operation gives a unique value for each pass and executing this operation results in multiple values, known as a feature map.
Once the feature map is computed, each value is passed to the ReLU activation function. ReLU is a linear activation function that transforms the input as zero if it is negative, otherwise, it outputs the same input. The ReLU activation function allows the model to perform better, learn from the training data faster, and overcomes the vanishing gradient problem. It is demonstrated using Equation (1) as follows:
Here, represents the input being provided to the activation function and represents a positive output of the activation function. Convolution layers are often followed by another block of CNN—pooling layers. Internally, the Sub-Sampling technique is being used to reduce the reliance on precise positioning of the feature maps on the model; however, the feature maps should be independent of the positioning of information to avoid the model from overfitting. The computation of the architecture is dependent on the complexity and the number of parameters; pooling layers operate on the feature maps for the generation of the mapped pooled features. The selection of mapped pooled features varies based on the size of pooling filter applied, stride, and type of pooling—max pooling, average pooling. Max pooling sets the value as the maximum value of the feature for each patch whereas average pooling calculates the average value for each patch. Deep learning neural networks may likely overfit the training data, which could reduce the overall performance of the model when evaluated on the unseen data. So, we employed the use of dropout layers. It is a regularization technique that ignores some neurons that are further processing randomly. It sets the inputs to 0 at each step with the frequency of rate during the training phase for preventing the model from overfitting. Active inputs are then scaled up by a certain factor such that the sum of all the inputs remains the same using Equation (2).
Hence, this makes the training process noisy by imposing more responsibility on some nodes. It is only used during the training process. However, dropout increases the weight of the network, and scaling is required up to the chosen dropout rate. They are then followed by the dense layers, fully connected with the previous layer, and an activation function for mapping the results to the output.
Proposed Architecture
Deep learning has played a vital role in the detection of network intrusions in the current era. In this paper, we propose a state-of-the-art 1DCNN-based deep learning architecture for the detection of network intrusions. Table 2 presents the intrusion types along with their data samples.
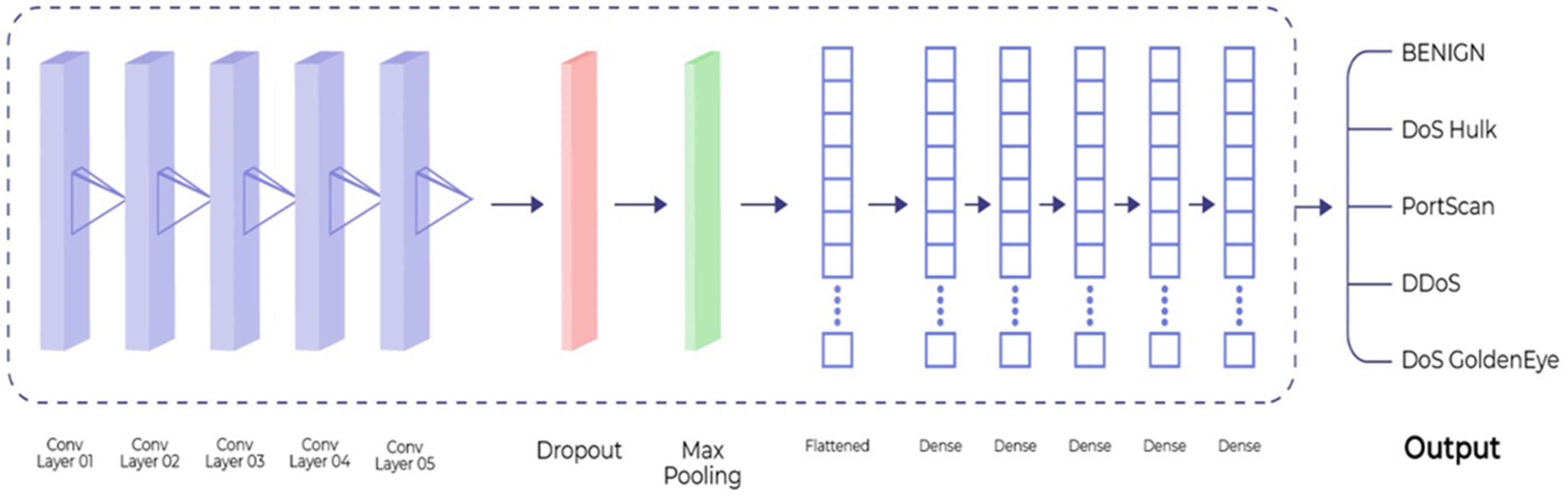
The proposed architecture consists of 5 convolution layers, a dropout layer, pooling layers, and 5 dense layers as presented in Figure 1. The first CNN layer consists of 32 filters with a kernel size of 2 along with ReLU as an activation function. This layer takes the input sample as an input and transforms the sample into a (77, 32) shape vector. It is then followed by another convolution layer consisting of 16 filters with a kernel size of 2. After five consecutive convolution layers, we added a dropout with a 0.5 rate that turns off 50% of the neurons during the training phase to avoid the model from overfitting. The dropout layer is then followed by a max-pooling having a pool size of 2. By using the max-pooling layer, the number of parameters to learn is reduced, hence, it reduces the computational cost of the model. The results are then flattened using a flattening layer that transforms the 3-dimensional vector into a single dimension. Afterward, five dense layers were employed using ReLU and SoftMax activation function for the prediction of a target variable. The summary of the model is presented in Table 6.
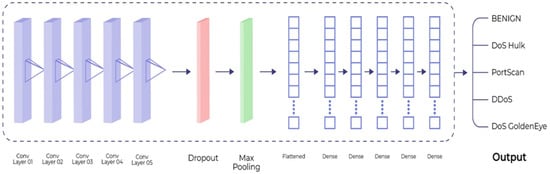
Figure 1.
Proposed 1D CNN Architecture.

Table 6.
Summary of the proposed model.
5. Experimental Results and Discussion
Deep learning is considered one of the latest achievements in machine learning. It helped the researchers to develop the solutions that could only be assumed a decade before because of the unavailability of data management, and data processing resources.
In this research, we use 1D-CNN for the detection of network intrusion. 1D-CNN is designed specifically to operate in 1-dimensional data. Previously various generic and machine learning-based approaches were used by researchers for the detection of network intrusions. Table 4 shows class wise instances after preprocessing and Table 7 depicts the number of instances used for training and testing. We divided the dataset into two sets, i.e., 75 and 25% for training and testing purposes, respectively. We evaluated the performance of the 1D-CNN classifier using different performance metrics, e.g., accuracy, precision, recall, and F1 score. These metrics are explained in Equations (3)–(6), respectively. The results of the CNN classifier are populated in Table 8.
where,
- represents the number of attacks that are correctly classified as attacks
- represents the normal data classified as an attack
- represents the normal data classified as normal
- represents the attack as normal.

Table 7.
Dataset Distribution.
Table 7.
Dataset Distribution.
| Instances | Value |
|---|---|
| Training | 101,250 |
| Testing | 33,750 |

Table 8.
Model Performance.
Table 8.
Model Performance.
| Precision (%) | Recall (%) | F1 Score (%) | Accuracy (%) | |
|---|---|---|---|---|
| Training | 99.2 | 99.5 | 99.34 | 99.32 |
| Validation | 98.7 | 99.2 | 98.94 | 98.96 |
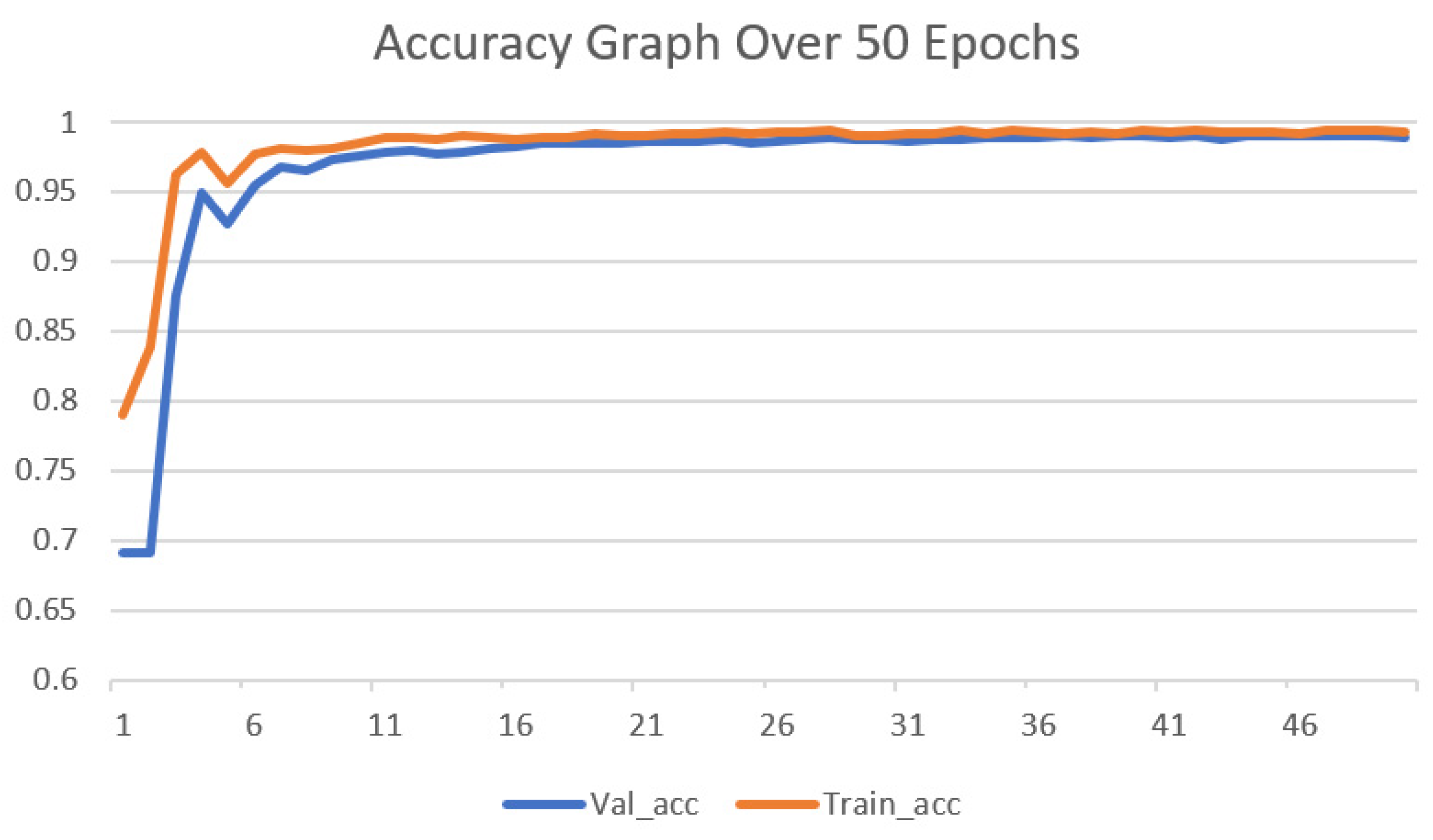
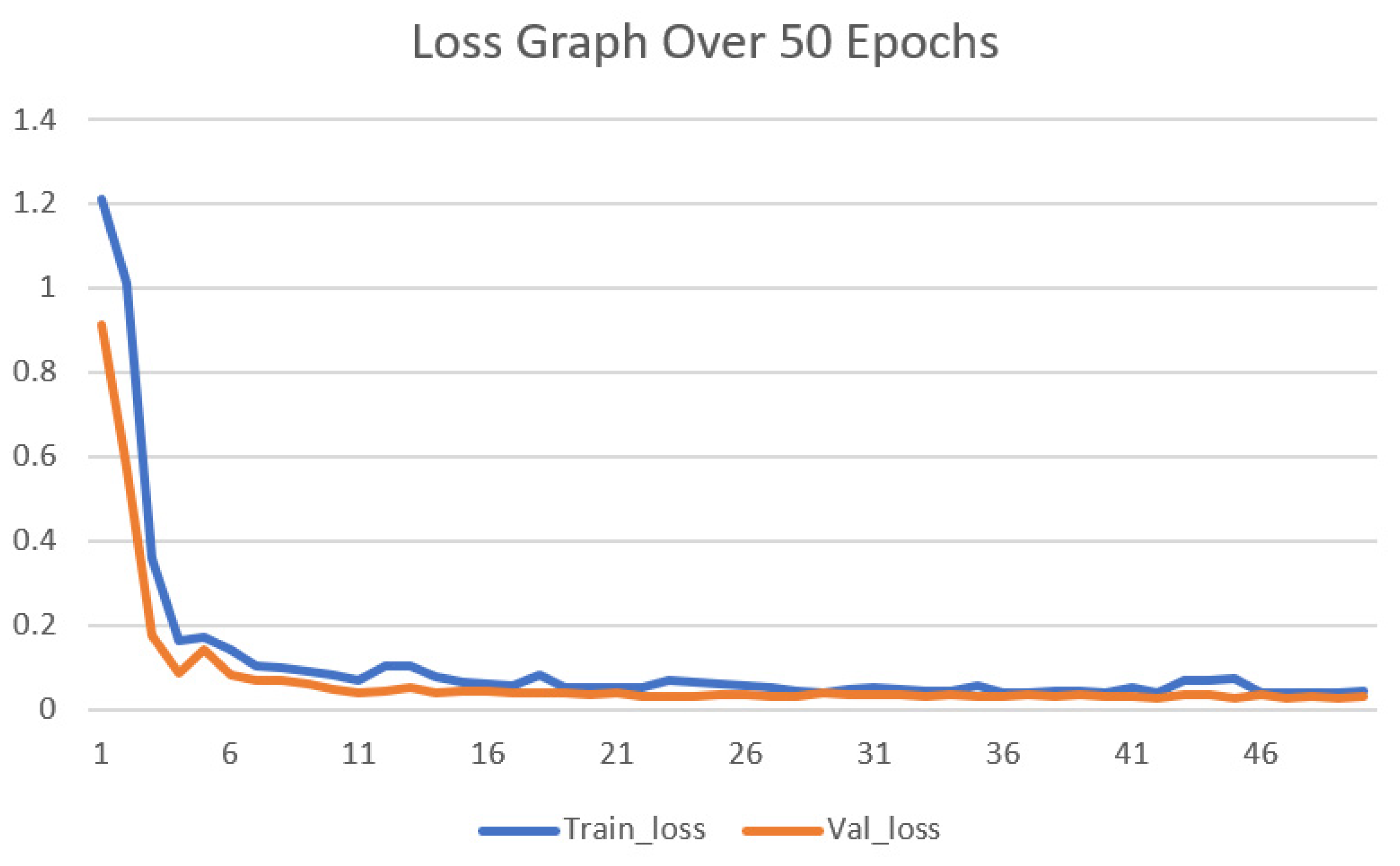
The optimal parameters used by our 1D-CNN classifier are presented in Table 9. After detailed experimentation, the parameters presented in Table 9 were selected. From Table 8, it is evident that we achieved a training accuracy of 99.32%, a precision of 99.2%, a recall of 99.5% and an F1 score of 99.34% was obtained over 50 epochs. Testing accuracy of 98.96%, the precision of 98.7%, recall of 99.2%, and F1 score of 98.94% were obtained by the proposed 1D-CNN- based methodology. Furthermore, we also present a detailed comparison of our methodology with existing techniques; most of the researchers have used generic machine learning techniques along with a handful of researchers using ANN, deep learning, and CNN as their main architectures. A detailed comparison is presented in Table 10 which shows the architecture, dataset that is used and the accuracy obtained. Figure 2 presents the overall model performance over 50 epochs. We also report the loss of the model during training and validation in Figure 3.

Table 9.
1D-CNN Parameters.

Table 10.
Comparison with Existing Approaches.
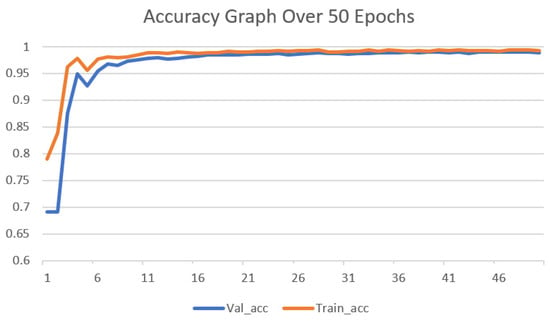
Figure 2.
Accuracy Graph over 50 Epochs.
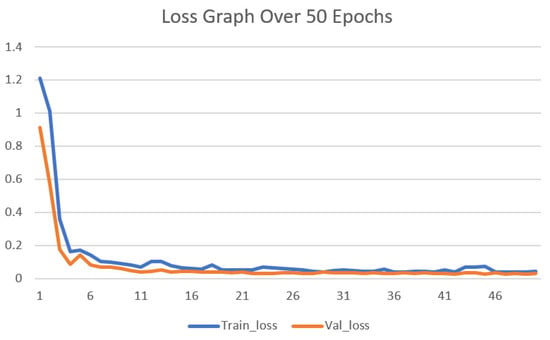
Figure 3.
Loss Graph over 50 Epochs.
The artificial neural networks were used for the detection of anomaly-based intrusions by Zhang et al. [33] where they used unsupervised outlier detection along with ANN using the UNSW-NB-15 dataset. The authors achieved an accuracy of 84%. Furthermore, we compare some of the existing approaches for network intrusion detection in various domains using the CICIDS 2017, NSL-KDD, UNSW-NB15 and RedIRIS datasets. We focus on deep learning-based techniques employed to detect network intrusions in different settings [37,43,44,45], presented the use of CNN, and RNN-based methodologies whereas the detailed comparison are presented in Table 10. Most of the researchers detect DDoS attacks while multi class classification is conducted by Sanchit et al. [42] using RNN-LSTM algorithm which was tested on the CICIDS 2017 dataset, whereas Sivamohan et al. [41] used Bi-directional LSTM on the CICIDS 2017 dataset for intrusion detection. Federated learning and CNN-LSTM based methodologies were also adopted for the detection of network intrusions [34,45].
6. Conclusions and Future Work
In this study, we present a One-Dimensional Convolution Neural Network (1D-CNN) based methodology for the detection of normal and four different types of malicious network traffic. While undergoing data analysis at the preprocessing stage, we were able to determine four different types of most common network intrusions, namely: DoS Hulk, DDoS, and DoS GoldenEye belonging to the active attack types, and PortScan which belongs to the passive attacks. We were also able to detect features with missing data and inconsistencies in the data. To overcome the class imbalance problem, we applied under sampling on the dataset.
We made use of the state-of-the-art deep learning methodologies by employing a 1D-CNN based architecture and achieved very promising results while performing multi-class classification. The proposed model architecture is simple and less computationally expensive. We achieved an overall accuracy of 98.96% with this approach.
In future work, we aim to perform further analysis on the reduction in input features using various techniques such as Principal Component Analysis (PCA), Independent Component Analysis (ICA), Autoencoders, etc. We also plan to retrain our model to detect even more types of network attacks. Lastly, we also consider the use of RNN, LSTM, and GRU-based architectures in future research.
Author Contributions
Conceptualization, E.U.H.Q., A.A. and T.Z.; data curation, E.U.H.Q., A.A. and T.Z.; formal analysis, E.U.H.Q., A.A. and T.Z.; funding acquisition, A.A.; methodology. E.U.H.Q.; project administration, A.A. and T.Z.; resources, A.A.; software, E.U.H.Q.; supervision, A.A. and T.Z.; validation, E.U.H.Q., A.A. and T.Z.; visualization, E.U.H.Q.; writing—original draft, E.U.H.Q.; writing—review and editing. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Security Research Center at Naif Arab University for Security Sciences (Project No. SRC-PR2-02).
Acknowledgments
The author would like to express their deep thanks to the Vice Presidency for Scientific Research at Naif Arab University for Security Sciences for their kind encouragement of this work.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liao, Y.; Vemuri, V.R. Use of K-nearest neighbor classifier for intrusion detection. Comput. Secur. 2002, 21, 439–448. [Google Scholar] [CrossRef]
- Kim, G.; Lee, S.; Kim, S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst. Appl. 2014, 41, 1690–1700. [Google Scholar] [CrossRef]
- De la Hoz, E.; De La Hoz, E.; Ortiz, A.; Ortega, J.; Prieto, B. PCA filtering and probabilistic SOM for network intrusion detection. Neurocomputing 2015, 164, 71–81. [Google Scholar] [CrossRef]
- Sen, R.; Chattopadhyay, M.; Sen, N. An efficient approach to develop an intrusion detection system based on multi-layer backpropagation neural network algorithm: IDS using BPNN algorithm. In Proceedings of the 2015 ACM SIGMIS Conference on Computers and People Research, Newport Beach, CA, USA, 4–6 June 2015; pp. 105–108. [Google Scholar]
- Koc, L.; Mazzuchi, T.A.; Sarkani, S. A network intrusion detection system based on a hidden Naïve Bayes multiclass classifer. Expert Syst. Appl. 2012, 39, 13492–13500. [Google Scholar] [CrossRef]
- De la Hoz, E.; De La Hoz, E.; Ortiz, A.; Ortega, J.; Martínez-Álvarez, A. Feature selection by multi-objective optimisation: Application to network anomaly detection by hierarchical self-organising maps. Knowl.-Based Syst. 2014, 71, 322–338. [Google Scholar] [CrossRef]
- Ahmad, I.; Basheri, M.; Iqbal, M.J.; Rahim, A. Performance comparison of support vector machine, random forest, and extreme learning machine for intrusion detection. IEEE Access 2018, 6, 33789–33795. [Google Scholar] [CrossRef]
- Soheily-Khah, S.; Marteau, P.F.; Béchet, N. Intrusion detection in network systems through hybrid supervised and unsupervised machine learning process: A case study on the ISCX dataset. In Proceedings of the 2018 1st International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 8–10 April 2018; pp. 219–226. [Google Scholar]
- Zhang, Y.; Chen, X.; Jin, L.; Wang, X.; Guo, D. Network Intrusion Detection: Based on Deep Hierarchical Network and Original Flow Data. IEEE Access 2019, 7, 37004–37016. [Google Scholar] [CrossRef]
- Zhang, J.; Chen, C.; Xiang, Y.; Zhou, W.; Xiang, Y. Internet traffic classification by aggregating correlated naive bayes predictions. IEEE Trans. Inf. Forensics Secur. 2013, 8, 5–15. [Google Scholar] [CrossRef]
- Cisco Systems. Cisco IOS NetFlow. 2012. Available online: www.cisco.com/go/netflow (accessed on 5 June 2022).
- Sperotto, A.; Schaffrath, G.; Sadre, R.; Morariu, C.; Pras, A.; Stiller, B. An overview of ip flow-based intrusion detection. IEEE Commun. Surv. Tutor. 2010, 12, 343–356. [Google Scholar] [CrossRef] [Green Version]
- Siddiqui, M.K.; Naahid, S. Analysis of KDD CUP 99 dataset using clustering-based data mining. Int. J. Database Theory Appl. 2013, 6, 23–34. [Google Scholar] [CrossRef]
- Aggarwal, P.; Sharma, S.K. Analysis of KDD dataset attributes-class wise for intrusion detection. Procedia Comput. Sci. 2015, 57, 842–851. [Google Scholar] [CrossRef] [Green Version]
- Vijayanand, R.; Devaraj, D.; Kannapiran, B. Intrusion detection system for wireless mesh network using multiple support vector machine classifiers with genetic-algorithm-based feature selection. Comput. Secur. 2018, 77, 304–314. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L. Deepcoin: A novel deep learning and blockchain-based energy exchange framework for smart grids. IEEE Trans. Eng. Manag. 2019, 67, 1285–1297. [Google Scholar] [CrossRef] [Green Version]
- Song, J.; Zhao, W.; Liu, Q.; Wang, X. Hybrid feature selection for supporting lightweight intrusion detection systems. J. Phys. Conf. Ser. 2017, 887, 012031. [Google Scholar] [CrossRef]
- Wang, W.; He, Y.; Liu, J.; Gombault, S. Constructing important features from massive network traffic for lightweight intrusion detection. IET Inf. Secur. 2015, 9, 374–379. [Google Scholar] [CrossRef]
- Aydın, M.A.; Zaim, A.H.; Ceylan, K.G. A hybrid intrusion detection system design for computer network security. Comput. Electr. Eng. 2009, 35, 517–526. [Google Scholar] [CrossRef]
- Idhammad, M.; Afdel, K.; Belouch, M. Distributed intrusion detection system for cloud environments based on data mining techniques. Procedia Comput. Sci. 2018, 127, 35–41. [Google Scholar] [CrossRef]
- Radford, B.J.; Richardson, B.D.; Davis, S.E. Sequence aggregation rules for anomaly detection in computer network traffic. arXiv 2018, arXiv:1805.03735. [Google Scholar] [CrossRef]
- Islam, F.B.; Akter, R.; Kim, D.S.; Lee, J.M. Deep Learning Based Network Intrusion Detection for Industrial Internet of Things. In Proceedings of the Korea Telecommunications Society Conference, Online, 14–17 June 2020; pp. 418–421. [Google Scholar]
- Hanif, S.; Ilyas, T.; Zeeshan, M. Intrusion Detection in IoT Using Artificial Neural Networks on UNSW-15 Dataset. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019; pp. 152–156. [Google Scholar] [CrossRef]
- Peng, Y.; Su, J.; Shi, X.; Zhao, B. Evaluating Deep Learning Based Network Intrusion Detection System in Adversarial Environment. In Proceedings of the 2019 IEEE 9th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 12–14 July 2019; pp. 61–66. [Google Scholar] [CrossRef]
- Wang, G.; Hao, J.; Ma, J.; Huang, L. A new approach to intrusion detection using artificial neural networks and fuzzy clustering. Expert Syst. Appl. 2010, 37, 6225–6232. [Google Scholar] [CrossRef]
- Chen, L.; Kuang, X.; Xu, A.; Suo, S.; Yang, Y. A Novel Network Intrusion Detection System Based on CNN. In Proceedings of the 2020 Eighth International Conference on Advanced Cloud and Big Data (CBD), Taiyuan, China, 19–20 September 2020; pp. 243–247. [Google Scholar] [CrossRef]
- Jamil, F.; Kim, D. An Ensemble of Prediction and Learning Mechanism for Improving Accuracy of Anomaly Detection in Network Intrusion Environments. Sustainability 2021, 13, 10057. [Google Scholar] [CrossRef]
- Biney, G.; Okyere, G.; Alhassan, A. Adaptive scheme for ANOVA models. J. Adv. Math. Comput. Sci. 2020, 35, 12–23. [Google Scholar] [CrossRef]
- Feir-Walsh, B.J.; Toothaker, L.E. An empirical comparison of the ANOVA F-test, normal scores test and Kruskal–Wallis test under violation of assumptions. Educ. Psychol. Meas. 1974, 34, 789–799. [Google Scholar] [CrossRef] [Green Version]
- Azizjon, M.; Jumabek, A.; Kim, W. 1D CNN based network intrusion detection with normalization on imbalanced data. In Proceedings of the 2020 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Fukuoka, Japan, 19–21 February 2020; pp. 218–224. [Google Scholar] [CrossRef] [Green Version]
- Vinayakumar, R.; Soman, K.P.; Poornachandran, P. Applying convolutional neural network for network intrusion detection. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Udupi, India, 13–16 September 2017; pp. 1222–1228. [Google Scholar]
- Panigrahi, R.; Borah, S. A detailed analysis of CICIDS2017 dataset for designing Intrusion Detection Systems. Int. J. Eng. Technol. 2018, 73, 479–482. [Google Scholar]
- Zhang, J.; Zulkernine, M. Anomaly based network intrusion detection with unsupervised outlier detection. In Proceedings of the 2006 IEEE International Conference on Communications, Istanbul, Turkey, 11–15 June 2006; Volume 5, pp. 2388–2393. [Google Scholar]
- Roopak, M.; Tian, G.Y.; Chambers, J. Deep learning models for cyber security in IoT networks. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 452–457. [Google Scholar] [CrossRef]
- Lee, J.; Kim, J.; Kim, I.; Han, K. Cyber threat detection based on artificial neural networks using event profiles. IEEE Access 2019, 7, 165607–165626. [Google Scholar] [CrossRef]
- Atefi, K.; Hashim, H.; Khodadadi, T. A hybrid anomaly classification with deep learning (DL) and binary algorithms (BA) as optimizer in the intrusion detection system (IDS). In Proceedings of the 2020 16th IEEE International Colloquium on SIGNAL Processing & Its Applications (CSPA), Langkawi, Malaysia, 28–29 February 2020; pp. 29–34. [Google Scholar] [CrossRef]
- Naseer, S.; Saleem, Y. Enhanced network intrusion detection using deep convolutional neural networks. KSII Trans. Internet Inf. Syst. (TIIS) 2018, 12, 5159–5178. [Google Scholar] [CrossRef]
- Bhardwaj, A.; Mangat, V.; Vig, R. Hyperband tuned deep neural network with well posed stacked sparse autoencoder for detection of DDoS attacks in cloud. IEEE Access 2020, 8, 181916–181929. [Google Scholar] [CrossRef]
- Asad, M.; Asim, M.; Javed, T.; Beg, M.O.; Mujtaba, H.; Abbas, S. Deepdetect: Detection of distributed denial of service attacks using deep learning. Comput. J. 2020, 63, 983–994. [Google Scholar] [CrossRef]
- Albelwi, S.A. An Intrusion Detection System for Identifying Simultaneous Attacks using Multi-Task Learning and Deep Learning. In Proceedings of the 2022 2nd International Conference on Computing and Information Technology (ICCIT), Tabuk, Saudi Arabia, 25–27 January 2022; pp. 349–353. [Google Scholar] [CrossRef]
- Sivamohan, S.; Sridhar, S.S.; Krishnaveni, S. An Effective Recurrent Neural Network (RNN) based Intrusion Detection via Bi-directional Long Short-Term Memory. In Proceedings of the 2021 International Conference on Intelligent Technologies (CONIT), Karnataka, India, 25–27 June 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Nayyar, S.; Arora, S.; Singh, M. Recurrent neural network based intrusion detection system. In Proceedings of the 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; pp. 136–140. [Google Scholar] [CrossRef]
- Lopez-Martin, M.; Carro, B.; Sanchez-Esguevillas, A.; Lloret, J. Network traffic classifier with convolutional and recurrent neural networks for Internet of Things. IEEE Access 2017, 5, 18042–18050. [Google Scholar] [CrossRef]
- Teyou, D.; Kamdem, G.; Ziazet, J. Convolutional neural network for intrusion detection system in cyber physical systems. arXiv 2019, arXiv:1905.03168. [Google Scholar]
- Ayed, M.A.; Talhi, C. Federated learning for anomaly-based intrusion detection. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October–2 November 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 2018, 1, 108–116. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).