Efficient Key Exchange Using Identity-Based Encryption in Multipath TCP Environment
Abstract
:1. Introduction
- MPTCP security threats are examined, and how threats can be used to launch session hijacking attacks is demonstrated.
- The existing solutions to the various security threats of MPTCP are analyzed.
- IBE is compared with the elliptic curve cryptosystem (ECC) in terms of performance and security.
- SKEXMTCP using IBE is proposed and evaluated in terms of security.
2. Background Study
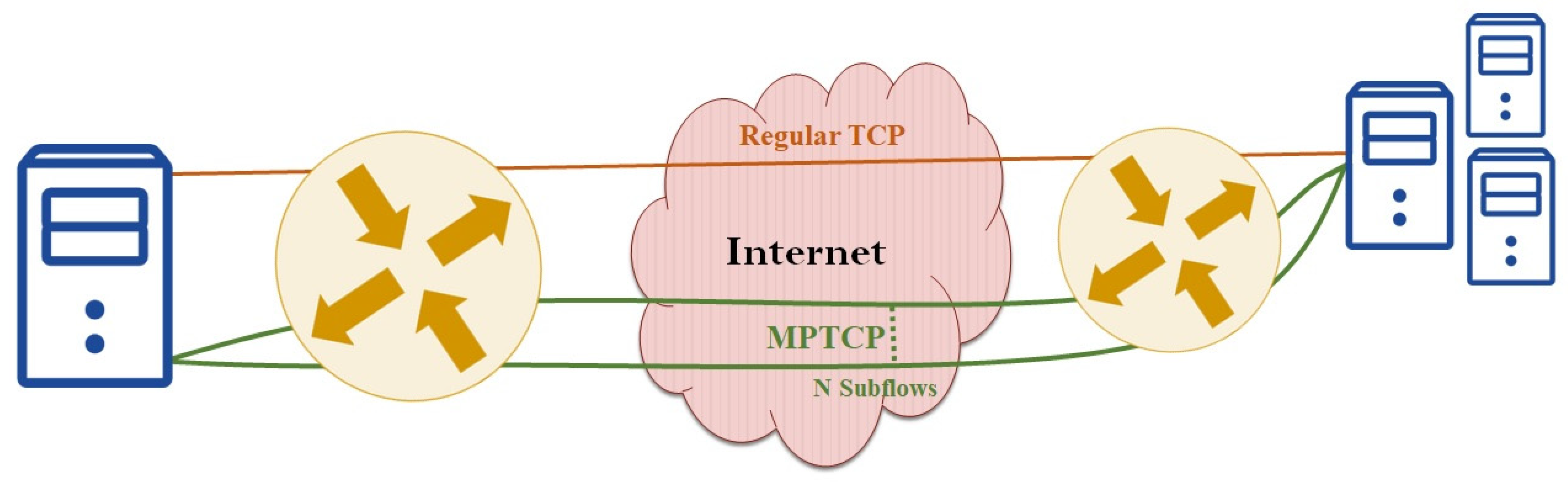
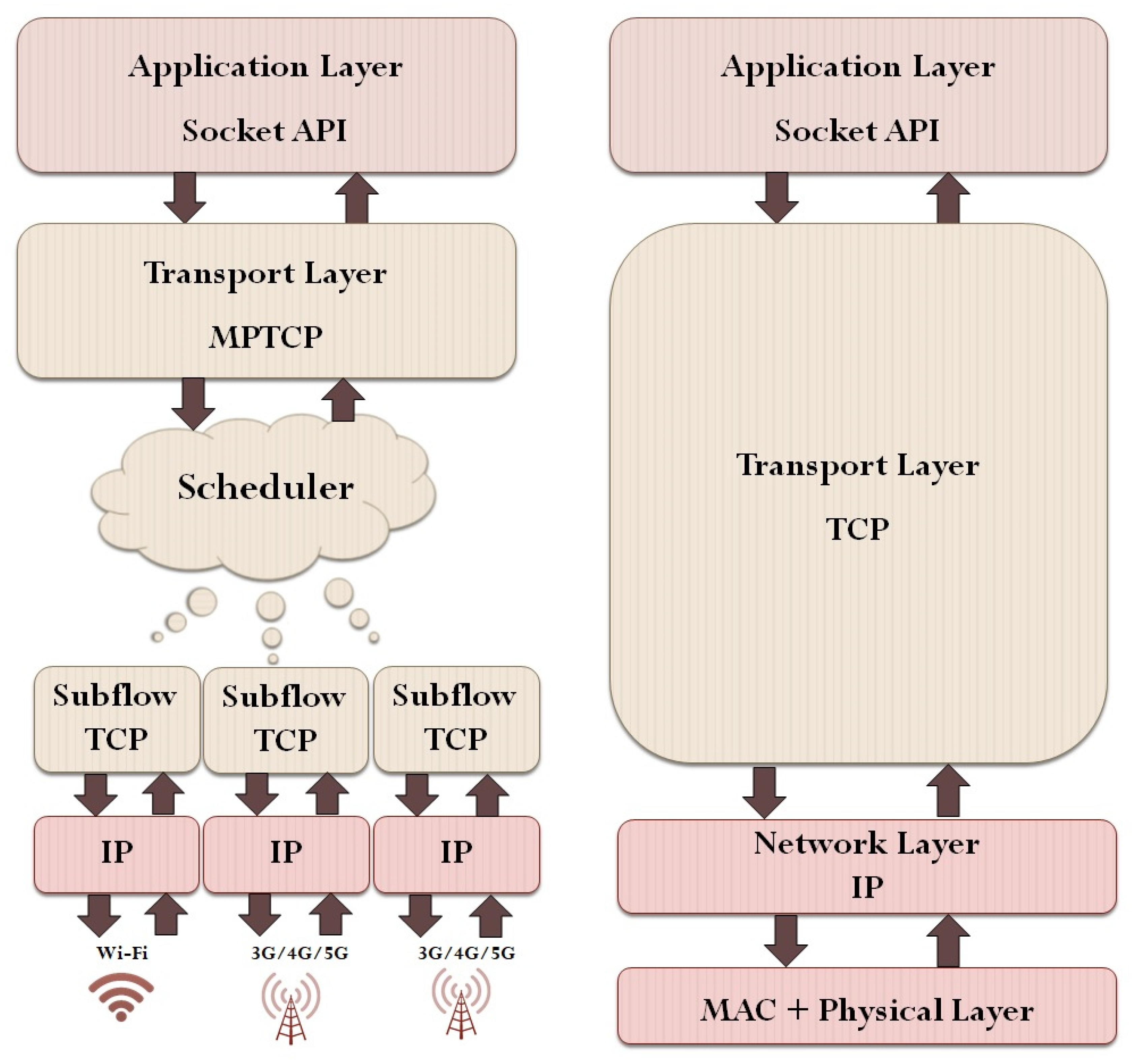
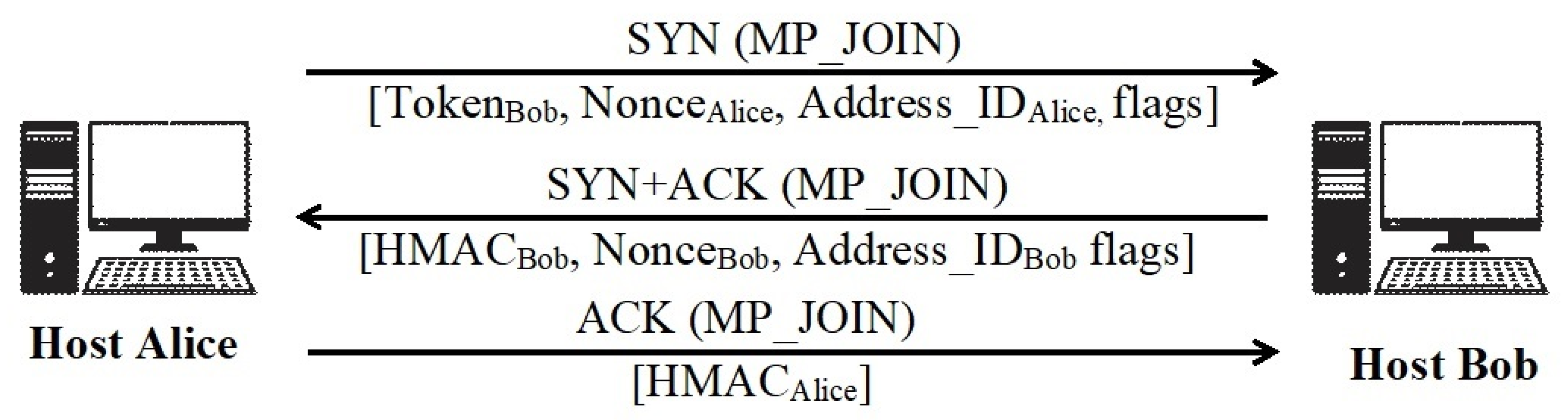
2.1. Multipath TCP (MPTCP) and Its Security Threats
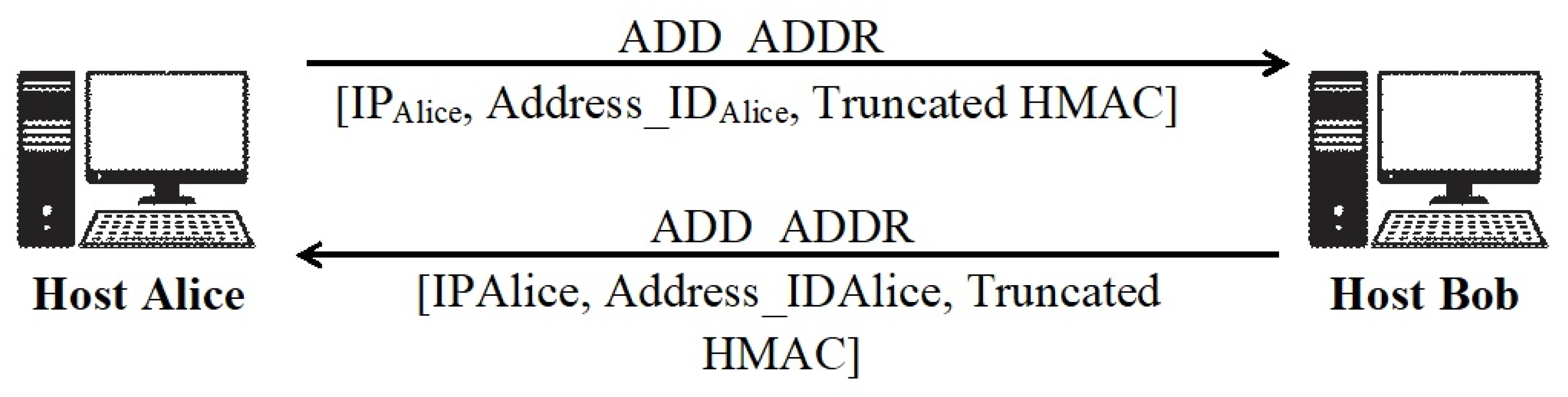
2.2. Available Solutions to Enhance the Security of MPTCP
3. Related Work: Identity-Based Encryption (IBE) and Elliptic Curve Cryptosystem (ECC)
Secure Communication between PKG and Communicating Hosts
- Alice selects the private key , which is less than The public key will be point in elliptic curve , which can be generated by using the private key and global parameter using the below equation.
- By using the same equation, PKG can select the private key and generate the public key
- Now, Alice can generate the secret key , and PKG can generate the secret key . Here, the secret key generated by Alice and PKG will be the same, which will be used for communication.
- SetUp: By using this algorithm, the PKG provides the system parameters and master-key share, which will be used to generate the private key. This algorithm takes security parameter , G1 and G2 to build a bilinear map , 2 cryptographic hash functions and and returns system parameters and master key share. Here, is the prime number, and P is the random number generator, which generates the random number to obtain the value of , where s is the master key share.
- KeyGeneration: By using this algorithm, the private key of the particular entity will be generated on request by using system parameters, master-key share, and public parameters. This algorithm uses the master key share and to generate the private key , where is a master key and
- Encryption: During the encryption, the of the receiver and system parameters will be used to encrypt a message, and ciphertext will be generated. This algorithm computes the Cipher Text using , and , is a random number and .
- Decryption: The private key generated by the KeyGeneration algorithm, system parameters generated by the SetUP algorithm, and the of the receiver will be used to decrypt the ciphertext. The Plaintext message can be computed as below: if is a cipher text encrypted using public key , compute and and . Test that If not, reject the cipher text. Here, is the decryption of .
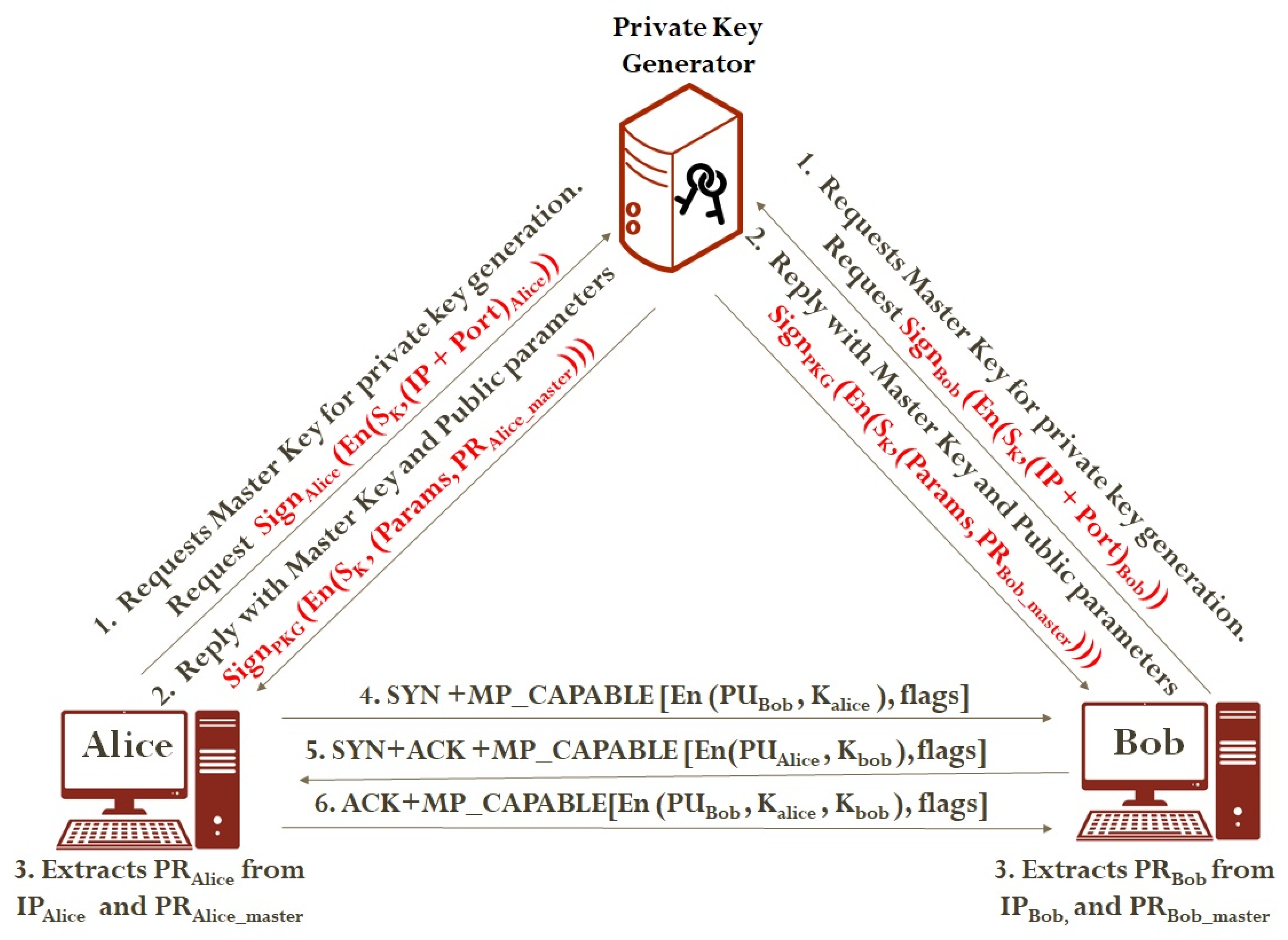
4. Proposed Work: Secure Key Exchange Model for MPTCP (SKEXMTCP) Using Identity-Based Encryption
- Module 1.
- Key Generation (KG_SKEXMTCP) using Identity-Based Encryption (IBE) Scheme:
- Step 1.
- Host Alice Key Generation
- (a)
- Here, public key of Alice PUAlice = IDAlice.It can be used by the sender to encrypt the messages for Alice.
- (b)
- Host Alice sends request to PKG with IPAlice and PortAlice as a parameter by authenticating itself using a digitally signed IP address and port combination.
- (c)
- PKG calculates the share of Alice PRAlice_master, and it will be sent back to Alice.
- (d)
- Alice can calculate the private key PRAlice from the PRAlice_master. PRAlice = Generate (PRAlice_master, IDAlice). The messages encrypted by PUAlice can be decrypted using PRAlice.
- Step 2.
- Host B Key Generation
- (a)
- Here, public key of Bob PUBob = IDBob.It can be used by sender to encrypt the messages for Bob.
- (b)
- Host Bob sends request to PKG with IPBob as a parameter by authenticating itself using digitally signed IP address and port combination.
- (c)
- PKG calculates the share of Bob PRBob_master, and it will be sent is back to Bob.
- (d)
- Bob can calculate private key PRBob from the PRBob_master. PRBob = Generate (PRBob_master, IDBob). The messages encrypted by PUBob can be decrypted using PRBob.
- Module 2.
- Initial Handshake using MP_CAPABLE with SKEXMTCP (MPC_SKEXMTCP)
- Step 1.
- SYN [MP_CAPABLE]
- (a)
- Encryption of Alice’s key KAlice. Alice encrypts the session key KAlice with public key of Bob (PUBob = IPBob) using IBE.
- (b)
- Key Transmission of Alice. Alice sends the encrypted key EKAlice = En(PUBob, KAlice) to Bob with MP_CAPABLE.
- Step 2.
- SYN+ACK [MP_CAPABLE]
- (a)
- Encryption of Bob’s key KBob. Bob encrypts the session key KBob with public key of Alice PUAlice using IBE.
- (b)
- Key transmission of Bob. Bob sends the encrypted key EKBob = En (PUAlice, KBob) to Alice with MP_CAPABLE.
- Step 3.
- ACK [MP_CAPABLE]
- (a)
- Key Echoing
5. Experimental Evaluation of Proposed Model
5.1. Security Evaluation
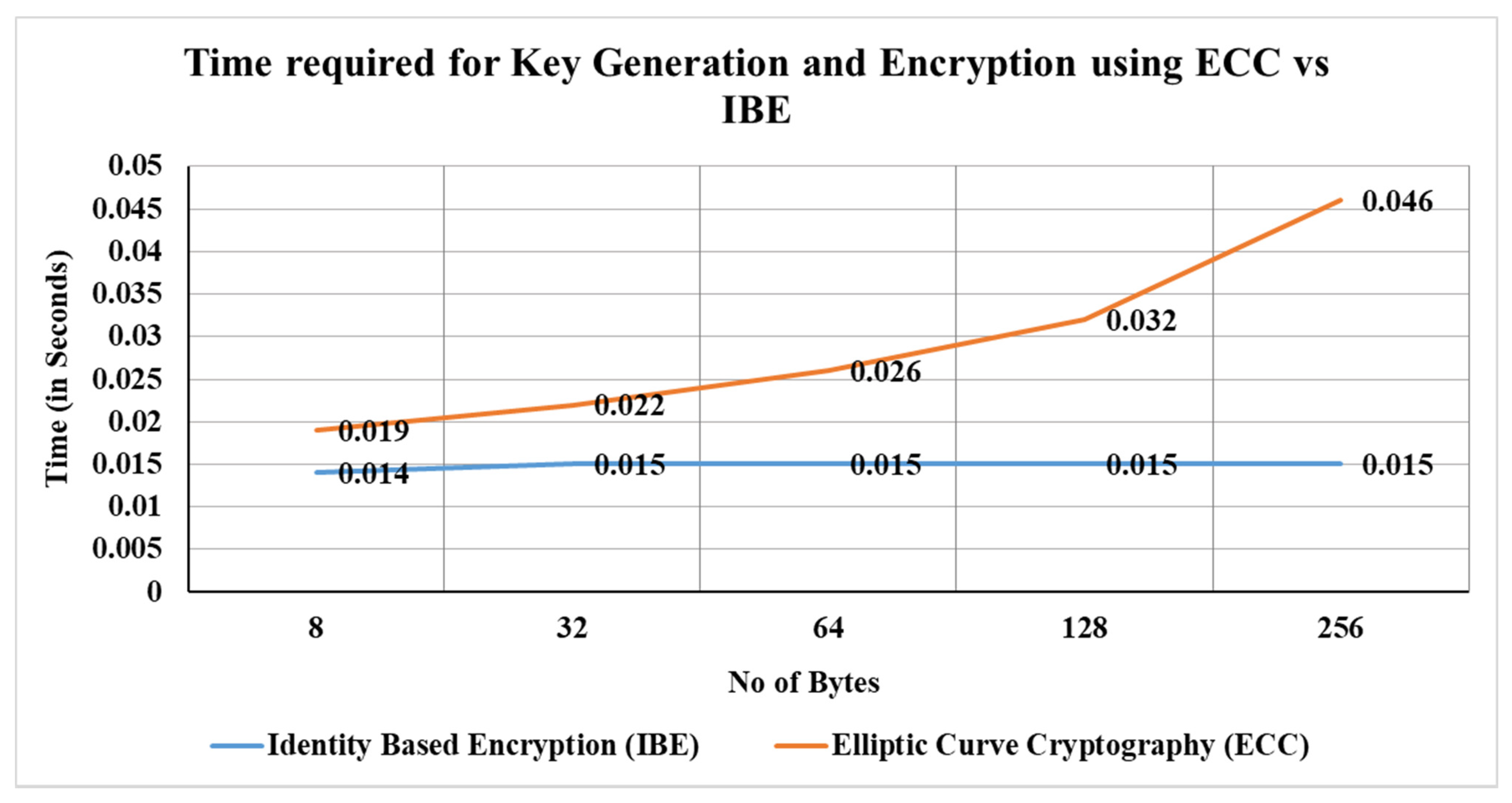
5.2. Security Complexity of IBE
5.3. Security Complexity of ECC
5.4. Performance Evaluation
- Let us assume that the cost of key generation is
- To obtain the cost of communication between the hosts and PKG, one needs to consider the cost of a request for a private key from a host to PKG and the cost of a reply from PKG to a host with a private key.
- Assume that the cost of a request for a private key from a host to PKG is and the cost of a reply from PKG to a host with a private key is .
- Thus, the cost of communication between Alice and PKG to deliver a private key to Alice is , and the cost of communication between Bob and PKG to deliver a private key to Bob is also .
- Thus, the total cost for communication between PKG and hosts is
- Now, let us calculate the cost of a three-way handshake SYN, SYN+ACK, and ACK is and respectively.
- Thus, the overall cost is
- If we consider that the overall cost of the model is , then
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Postel, J. Transmission Control Protocol, RFC 793. September 1981. Available online: https://datatracker.ietf.org/doc/html/rfc793 (accessed on 1 January 2022).
- Popat, K.; Kapadia, V.V. Multipath TCP Security Issues, Challenges and Solutions. In Information, Communication and Computing Technology; Communications in Computer and Information Science; Springer: Cham, Switzerland, 2021. [Google Scholar]
- Patil, S.; Raut, R.; Jhaveri, R.; Ahanger, T.; Dhade, P.; Kathole, A.; Vhatkar, K. Robust Authentication System with Privacy preservation of Biometrics. Secur. Commun. Netw. 2022, 2022, 7857975. [Google Scholar] [CrossRef]
- Patel, C.; Joshi, D.N.; Doshi, V.A.; Jhaveri, R. An enhanced approach for three factor remote user authentication in multi-server environment. J. Intell. Fuzzy Syst. 2020, 39, 8609–8620. [Google Scholar] [CrossRef]
- Durga, R.; Poovammal, E.; Ramana, K.; Jhaveri, R.H.; Singh, S.; Yoon, B. CES Blocks—A Novel Chaotic Encryption Schemes-Based Blockchain System for an IoT Environment. IEEE Access 2022, 10, 11354–11371. [Google Scholar] [CrossRef]
- Dharmadhikari, O. 5G Link Aggregation with Multipath TCP (MPTCP); CableLabs. 2019. Available online: https://www.cablelabs.com/blog/5g-link-aggregation-mptcp (accessed on 1 January 2022).
- 5G & Wi-Fi: From Coexistence to Convergence. Tessares. Available online: https://www.tessares.net/solutions/5g-atsss-solution/ (accessed on 1 January 2022).
- Bonaventure, O. The First Multipath TCP Enabled Smartphones. Multipath-TCP. 2018. Available online: http://blog.multipath-tcp.org/blog/html/2018/12/10/the_first_multipath_tcp_enabled_smartphones.html (accessed on 1 January 2022).
- Bonaventure, O. Important Milestone for Multipath TCP. Tessares. 10 April 2020. Available online: https://www.tessares.net/important-milestone-for-multipath-tcp/ (accessed on 1 January 2022).
- Opening the Way to 4G/5G Wi-Fi Convergence (NEW). Tessares. 2020. Available online: https://www.tessares.net/new-white-paper-opening-the-way-to-5g-convergence-september-2020/ (accessed on 1 January 2022).
- Use Multipath TCP to Create Backup Connections for IOS. Apple. 2017. Available online: https://support.apple.com/en-in/HT201373 (accessed on 1 January 2022).
- Detal, G.; Barré, S.; Peirens, B.; Bonaventure, O. Leveraging Multipath TCP to Create Hybrid Access Networks; ACM SIGCOMM: Los Angeles, CA, USA, 2017; Available online: https://conferences.sigcomm.org/sigcomm/2017/files/program-industrial-demos/sigcomm17industrialdemos-paper4.pdf (accessed on 1 January 2022).
- Chao, L.; Wu, C.; Yoshinaga, T.; Bao, W.; Ji, Y. A Brief Review of Multipath TCP for Vehicular Networks. Sensors 2021, 21, 2793. [Google Scholar] [CrossRef]
- Bonaventure, O. Multipath TCP in the Datacenter. 2018. Available online: http://blog.multipath-tcp.org/blog/html/2018/12/11/multipath_tcp_in_the_datacenter.html (accessed on 1 January 2022).
- Zhao, Q.; Du, P.; Mena, J.; Gerla, M. A Multi-path TCP Solution for Software-Defined Military Heterogeneous Network. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Zhao, Q.; Du, P.; Mena, J.; Gerla, M. Software Defined Multi-Path TCP Solution for Mobile Wireless Tactical Networks. In Proceedings of the 2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018. [Google Scholar]
- Ford, A.; Raiciu, C.; Handley, M.; Bonaventure, O.; Paasch, C. TCP Extensions for Multipath Operation with Multiple Addresses RFC6824(if approved); draft-ietf-mptcp-rfc6824bis-12. 2018. Available online: https://datatracker.ietf.org/doc/pdf/draft-ietf-mptcp-rfc6824bis-12 (accessed on 1 January 2022).
- Hamza, A.; Lali, M.I.; Javid, F.; Din, M.U. Study of MPTCP with Transport Layer Security. In Proceedings of the 3rd International Conference on Engineering & Emerging Technologies (ICEET), Superior University, Lahore, Pakistan, 7–8 April 2016. [Google Scholar]
- Bittau, A.; Boneh, D.; Hamburg, M.; Handley, M.; Mazieres, D.; Slack, Q. Cryptographic Protection of TCP Streams (Tcpcrypt); Internet-Draft draft-ietf-tcpinc-tcpcrypt-03. 2014. Available online: https://datatracker.ietf.org/doc/html/rfc8548 (accessed on 1 January 2022).
- Díez, J.; Bagnulo, M.; Valera, F.; Vidal, I. Security for multipath TCP: A constructive approach. Int. J. Internet Protoc. Technol. 2011, 6, 146–155. [Google Scholar] [CrossRef]
- Krishnan, A.; Amritha, P.P.; Sethumadhavan, M. Sum Chain Based Approach against Session Hijacking in MPTCP. In Proceedings of the 7th International Conference on Advances in Computing & Communications, ICACC-2017, Cochin, India, 19–22 September 2017. [Google Scholar]
- Melki, R.; Hussein, A.; Chehab, A. Enhancing Multipath TCP Security Through Software Defined Networking. In Proceedings of the 2019 Sixth International Conference on Software Defined Systems (SDS), Rome, Italy, 10–13 June 2019. [Google Scholar]
- Noh, G.; Park, H.; Roh, H.; Lee, W. Secure and Lightweight Subflow Establishment of Multipath-TCP. IEEE Access 2019, 7, 177438–177448. [Google Scholar] [CrossRef]
- Kim, D.-Y.; Choi, H.-K. Efficient design for secure multipath TCP against eavesdropper in initial handshake. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef] [Green Version]
- Ford, A.; Raiciu, C.; Handley, M.; Bonaventure, O. Extensions for Multipath Operation with Multiple Addresses; RFC 6824 TCP. 2013. Available online: https://datatracker.ietf.org/doc/html/rfc6824 (accessed on 1 January 2022).
- Ford, A.; Raiciu, C.; Handley, M.; Bonaventure, O. Architectural Guidelines for Multipath TCP Development (RFC6182); Internet Engineering Task Force (IETF): Fremont, CA, USA, 2011. [Google Scholar]
- Popat, K.J.; Raval, J.; Johnson, S.; Patel, B. Experimental Evaluation of Multipath TCP with MPI. In Proceedings of the Third International Symposium on Women in Computing and Informatics, Kochi, India, 10–13 August 2015. [Google Scholar]
- Popat, K.; Kapadia, D.V. Recent Trends in Security Threats in Multi-Homing Transport Layer Solutions. Int. J. Adv. Sci. Technol. 2020, 29, 5641–5648. [Google Scholar]
- Raiciu, C.; Handley, M.; Wischik, D. Coupled Congestion Control for Multipath Transport Protocols (RFC 6356); Internet Engineering Task Force (IETF): Fremont, CA, USA, 2011. [Google Scholar]
- Khalili, R.; Gast, N.; Popovic, M. Opportunistic Linked-Increases Congestion Control Algorithm for MPTCP. 2013. Available online: https://datatracker.ietf.org/doc/html/draft-khalili-mptcp-congestion-control-05 (accessed on 1 January 2022).
- Cao, Y.; Xu, M.; Fu, X. Delay-based congestion control for multipath TCP. In Proceedings of the 2012 20th IEEE International Conference on Network Protocols (ICNP), Austin, TX, USA, 30 October–2 November 2012. [Google Scholar]
- Chaturvedi, R.K.; Chand, S. Multipath TCP security over different attacks. Trans. Emerg. Telecommun. Technol. 2020, 31, 4081. [Google Scholar] [CrossRef]
- Bagnulo, M.; Paasch, C.; Gont, F.; Bonaventure, O.; Raiciu, C. Analysis of Residual Threats and Possible Fixes for Multipath TCP (Mptcp); (No. RFC 7430). 2015. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc7430.txt.pdf (accessed on 1 January 2022).
- Demaria, F. Security Evaluation of Multipath TCP, Analyzing and Fixing Multipath TCP Vulnerabilities, Contributing to the Linux Kernel Implementation of the New Version of the Protocol. Ph.D. Thesis, Master of Science in Engineering-Information and Communication Technology. KTH Royal Institute of Technology, Stockholm, Sweden, March 2016. [Google Scholar]
- Munir, A.; Qian, Z.; Shafiq, Z.; Liu, A.; Le, F. Multipath TCP traffic diversion attacks and countermeasures. In Proceedings of the IEEE 25th International Conference on Network Protocols (ICNP), Toronto, ON, Canada, 10–13 October 2017. [Google Scholar]
- Shafiq, M.Z.; Le, F.; Srivatsa, M.; Liu, A.X. Cross-path inference attacks on multipath tcp. In Proceedings of the Twelfth ACM Workshop on Hot Topics in Networks, College Park, MA, USA, 21–22 November 2013; Association for Computing Machinery: New York, NY, USA, 2013. [Google Scholar]
- Kumar, V.A.; Das, D.; Senior Member IEEE. Data sequence signal manipulation in multipath TCP (MPTCP): The vulnerability, attack and its detection. Comput. Secur. 2021, 103, 102180. [Google Scholar] [CrossRef]
- Jadin, M.; Tihon, G.; Pereira, O.; Bonaventure, O. Securing multipath TCP: Design & implementation. In Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017. [Google Scholar]
- Bonaventure, O. MPTLS: Making TLS and Multipath TCP Stronger Together. 2015. Available online: https://datatracker.ietf.org/doc/html/draft-bonaventure-mptcp-tls-00 (accessed on 1 January 2022).
- Kato, T.; Cheng, S.; Yamamoto, R.; Ohzahata, S.; Suzuki, N. Protecting Eavesdropping over Multipath TCP Communication Based on Not-Every-Not-Any Protection. In Proceedings of the SECURWARE 2017: The Eleventh International Conference on Emerging Security Information, Systems and Technologies, Rome, Italy, 10–14 September 2017. [Google Scholar]
- Pandya, V.; Saiyed, A.; Patel, K. Recent Advancement in Fine-Grained Access Control and Secure Data Sharing Scheme for Distributed Environment. In Emerging Technologies for Computing, Communication and Smart Cities; Springer: Singapore, 2022. [Google Scholar]
- Mallouli, F.; Hellal, A.; Saeed, N.S.; Alzahrani, F.A. A Survey on Cryptography: Comparative Study between RSA vs ECC Algorithms, and RSA vs El-Gamal Algorithms. In Proceedings of the 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Paris, France, 21–23 June 2019. [Google Scholar]
- Stallings, W. Cryptography and Network Security, 4/E; Pearson Education Inc.: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Forouzan, B.; Mukhopadhyay, A.D. Cryptography and Network Security; Mc Graw Hill Education (India) Private Limited: New York, NY, USA, 2015. [Google Scholar]
- Bagnulo, M. Secure MPTCP, Draft-Bagnulo-Mptcp-Secure-00; ietf-bagnulo-mptcp-secure-00. 2014. Available online: https://datatracker.ietf.org/doc/html/draft-bagnulo-mptcp-secure-00 (accessed on 1 January 2022).
- Aasch, C.A.O.B. Securing the MultiPath TCP Handshake with External Keys; Work in Progress; draft-paasch-mptcp-ssl-00. 2012. Available online: https://tools.ietf.org/id/draft-paasch-mptcp-ssl-00.html (accessed on 1 January 2022).
- Elliptic-Curve Cryptography. Available online: https://en.wikipedia.org/wiki/Elliptic-curve_cryptography (accessed on 1 April 2022).





| Cryptographic Technique | References | Working with MPTCP | Limitations |
|---|---|---|---|
| Elliptic curve cryptography | [24] | The points required to plot the Elliptic curve are shared during initial four-way handshake in clear format. | One extra packet is required to share all four points to generate the keys. Vulnerable to time-shift attack. |
| Hash Chain-based Encryption | [20] | During the initial handshake, the random value will be exchanges, which will be used to generate the chain of hash by applying hash function for the authentication during addition of subflows and advertisement of new Internet Protocol (IP) Address (network interface). | Vulnerable to session hijacking using ADD_ADDR Attack. |
| Sum Chain-based encryption | [21] | Uses mathematical equation to create a chain instead of normal hash function. | Vulnerable to eavesdroppers in initial handshake attack. |
| Asymmetric Key cryptography | [18,19] | Public key cryptography can be used to avoid the key exchange during the initial handshake. Tcpcrypt and TLS uses asymmetric key cryptography. | Computational cost increases the overhead of MPTCP. Moreover, the TCP header option size is also limited. |
| Authentication using Hash based Message Authentication Code (HMAC) | [17] | The keys are exchanged during the initial handshake of MPTCP. The truncated HMAC calculated from the keys will be used to authenticate the user during ADD_ADDR and MP_JOIN. | Vulnerable to eavesdroppers in initial handshake. |
| Attack | Category * | Active/ Passive | References | Security Goals Impacted # | Remarks |
|---|---|---|---|---|---|
| Eavesdropper in initial handshake | P | Active | [34] | C | During the three-way handshake, the session keys are exchanged in clear format, which can be used in the future to initiate a SYN+MP_JOIN DoS attack or an ADD_ADDR attack. |
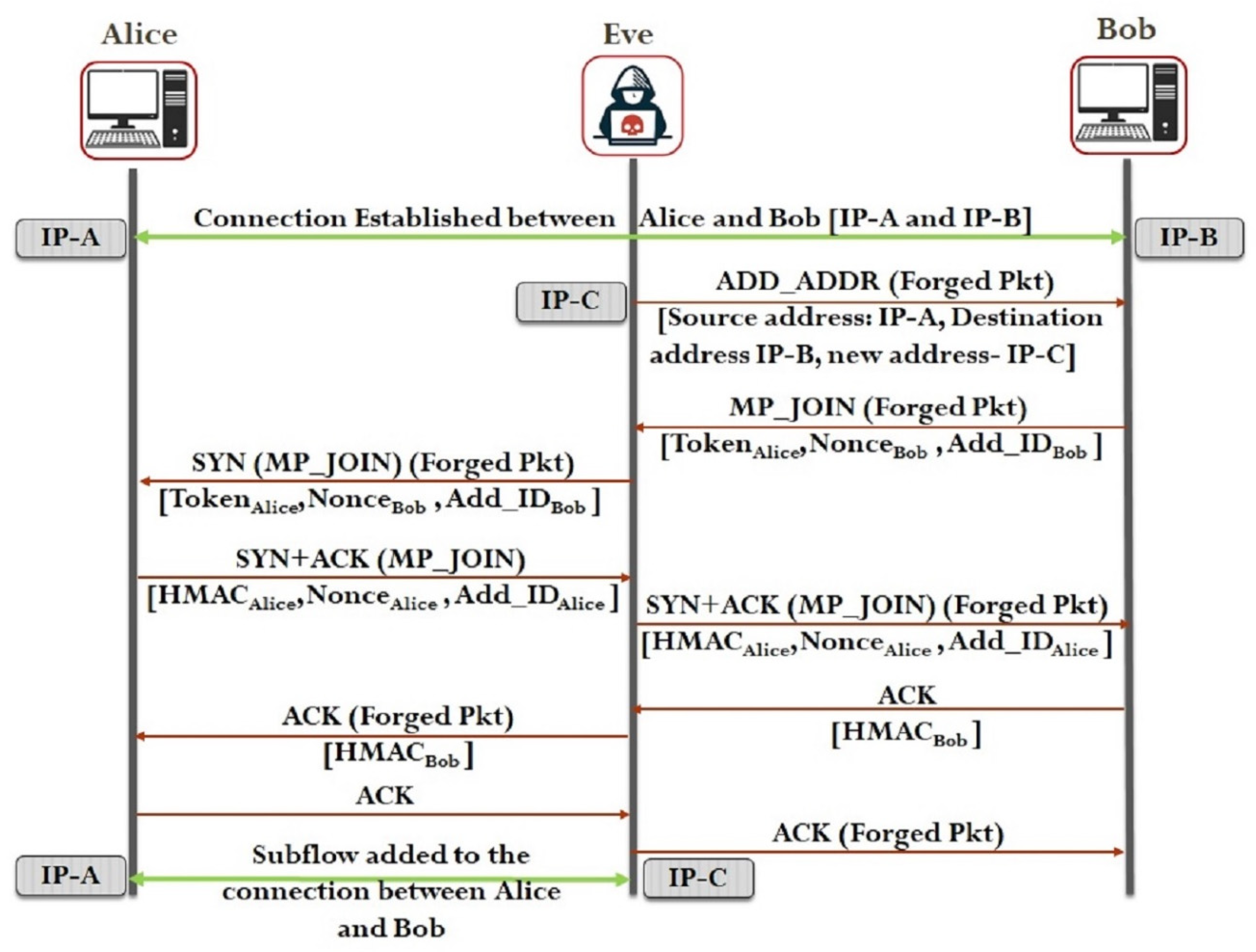
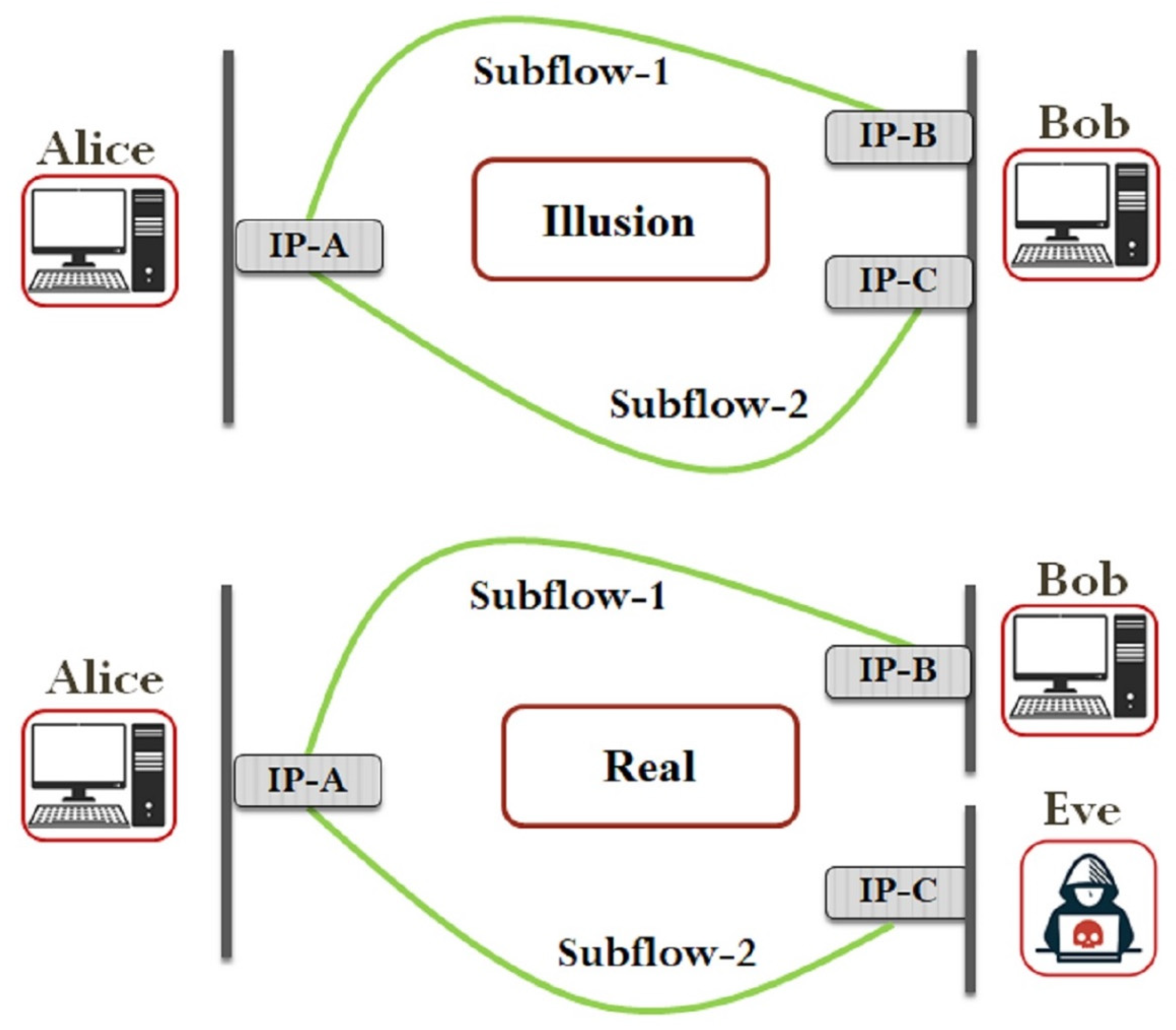
| ADD_ADDR attack | F | Active | [34,35] | C, I, A | By packet forging, an attacker can send the spoofed packet to the legitimate user and add the attacker’s address as a legitimate address to add subflow between the authenticated host and the attacker over a legitimate connection. |
| ADD_ADDR2 attack | F | Active | [2] | C, I | The eavesdropper in the initial handshake can gather the keys exchanged between communicating hosts and use those keys to perform this attack by using the keys to find out the HMAC. |
| DoS attack on MP_JOIN | F | Active | [34] | A | The legitimate users will not be able to create new subflows by sending fake SYN+MP_JOIN requests, which will make the server busy; thus, the server will not be able to handle the requests of legitimate users. |
| SYN Flooding attack | F | Active | [34] | A | By using the SYN packet, the server will be exhausted; thus, the client will not be served. |
| Traffic diversion attack | F | Active | [36] | C, A | By cross-path inference, an attacker can monitor one of the subflows, and by using a forged MP_PRIO packet, all the traffic can be redirected to the compromised subflow. |
| Cross path inferences attack | F | Active | [37] | C, A | Attackers can infer the properties and sensitive information of an unmonitored path through side channels to create a negative impact on the design goals of MPTCP. |
| SYN/JOIN attack | P | Active | [34] | C, I, A | If the attacker is on the path during the initial SYN/JOIN message exchange, the attacker will be able to add any of the addresses to establish a new subflow over the connection. |
| Data Sequence signal manipulation | F | Active | [38] | A | The connection level ACK is manipulated on the top of the TCP optimistic ACKing, which will lead to a powerful attack scenario such as DoS, flood, etc. |
| References | Year | Solution | Remarks |
|---|---|---|---|
| [20] | 2011 | Hash chain-based solution | It does not offer security against on-path active attackers. |
| [19] | 2014 | Tcpcrypt | It does not authenticate the public key and is vulnerable to man-in-the middle attacks. |
| [18] | 2016 | Multipath Transport Layer Security (MPTLS) | Computation overhead during initial handshake. Need to modify the packet sequence. |
| [40] | 2015 | ||
| [24] | 2016 | Modified initial handshake | During initial handshake, the values of the points are communicated in a clear format, which can be used in the future to initiate time-shifted attack. |
| [21] | 2017 | Sum chain-based solution | Vulnerable to time-shifted attack. |
| [41] | 2017 | Data Scrambling technique for privacy | The proposed model only focuses on the eavesdropper on untrusted paths and does not work in a strict sense. Moreover, integrity of the data is not guaranteed. |
| [17] | 2018 | ADD_ADDR2 | Vulnerable to time-shifted attack. |
| [22] | 2019 | Key exchange through SDN | Single point of failure. |
| [33] | 2020 | Secure connection Multipath TCP (SCMTCP) | For each new connection request, it generates the unique key for each option, which increases the computational overhead. |
| [23] | 2019 | Secure and lightweight connection establishment scheme | Increases the packet overhead every time, confirming the new address and does not offer security against an eavesdropper in the initial handshake. |
| Term | Significance/ Meaning | Generation |
|---|---|---|
| PUAlice | Public key of Alice | IP address of the Alice will be used as a Public Key. |
| PRAlice_Master | Shared key used to generate the private key of Alice | Generated by PKG and shared with Alice. |
| PRAlice | Private Key of Alice | It can be generated by using PRAlice_Master and PUAlice. |
| PUBob | Public key of Bob | IP address of the Bob will be used as a Public Key. |
| PRBob_master | Shared key used to generate the private key of Bob | The key will be generated by PKG and shared with Alice. |
| PRBob | Private Key of Bob | It can be generated by using PRBob_Master and PUBob. |
| IDAlice | ID used as a Public key of Alice | IPAlice + PortAlice Combination. |
| IDBob | ID used as a Public key of Bob | IPBob + PortBob Combination. |
| Attack | Type | Proposed Solution | SCMTCP [33] | Secure and Lightweight Subflow Scheme [23] | Secure MPTCP (SMPTCP) [46] | MPTLS [47] | Hash Chain [20] | MPTCP [17] |
|---|---|---|---|---|---|---|---|---|
| Session hijacking using ADD_ADDR Vulnerability | Off Path Active attack/Partial Time on Path Active attack | Y | Y | Y | Y | Y | N | N |
| Eavesdropper in the initial handshake | On Path Attack | Y | Y | N | Y | Y | N | N |
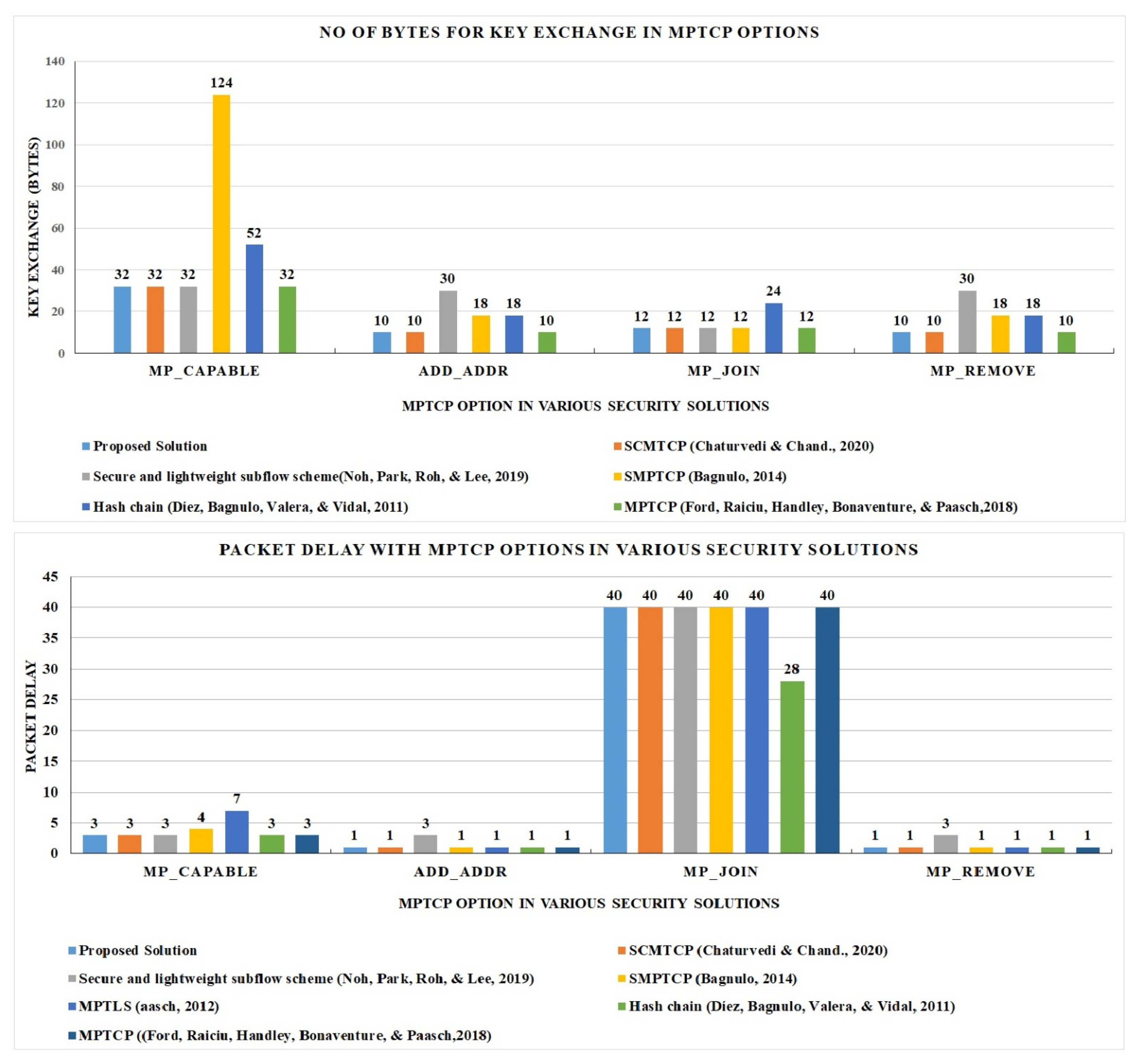
| Proposed Solution | SCMTCP [33] | Secure and Lightweight Subflow Scheme [23] | SMPTCP [46] | MPTLS [47] | Hash Chain [20] | MPTCP [17] | |
|---|---|---|---|---|---|---|---|
| MP_CAPABLE | |||||||
| 32 | 32 | 32 | 124 | 7468 | 52 | 32 |
| 3 | 3 | 3 | 4 | 7 | 3 | 3 |
| ADD_ADDR | |||||||
| 10 | 10 | 30 | 18 | 18 | 18 | 10 |
| 1 | 1 | 3 | 1 | 1 | 1 | 1 |
| MP_JOIN | |||||||
| 12 | 12 | 12 | 12 | 12 | 24 | 12 |
| 40 | 40 | 40 | 40 | 40 | 28 | 40 |
| MP_REMOVE | |||||||
| 10 | 10 | 30 | 18 | 18 | 18 | 10 |
| 1 | 1 | 3 | 1 | 1 | 1 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almuflih, A.S.; Popat, K.; Kapdia, V.V.; Qureshi, M.R.N.M.; Almakayeel, N.; Mamlook, R.E.A. Efficient Key Exchange Using Identity-Based Encryption in Multipath TCP Environment. Appl. Sci. 2022, 12, 7575. https://doi.org/10.3390/app12157575
Almuflih AS, Popat K, Kapdia VV, Qureshi MRNM, Almakayeel N, Mamlook REA. Efficient Key Exchange Using Identity-Based Encryption in Multipath TCP Environment. Applied Sciences. 2022; 12(15):7575. https://doi.org/10.3390/app12157575
Chicago/Turabian StyleAlmuflih, Ali Saeed, Khushi Popat, Viral V. Kapdia, Mohamed Rafik Noor Mohamed Qureshi, Naif Almakayeel, and Rabia Emhamed Al Mamlook. 2022. "Efficient Key Exchange Using Identity-Based Encryption in Multipath TCP Environment" Applied Sciences 12, no. 15: 7575. https://doi.org/10.3390/app12157575
APA StyleAlmuflih, A. S., Popat, K., Kapdia, V. V., Qureshi, M. R. N. M., Almakayeel, N., & Mamlook, R. E. A. (2022). Efficient Key Exchange Using Identity-Based Encryption in Multipath TCP Environment. Applied Sciences, 12(15), 7575. https://doi.org/10.3390/app12157575







