Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks
Abstract
:1. Introduction
2. Background
2.1. IPv6 Protocol Overview
2.2. ICMPv6 Overview
2.3. ICMPv6 Flooding DDoS Attack
2.4. Deep-Learning-Based IDS
2.4.1. Recurrent Neural Networks
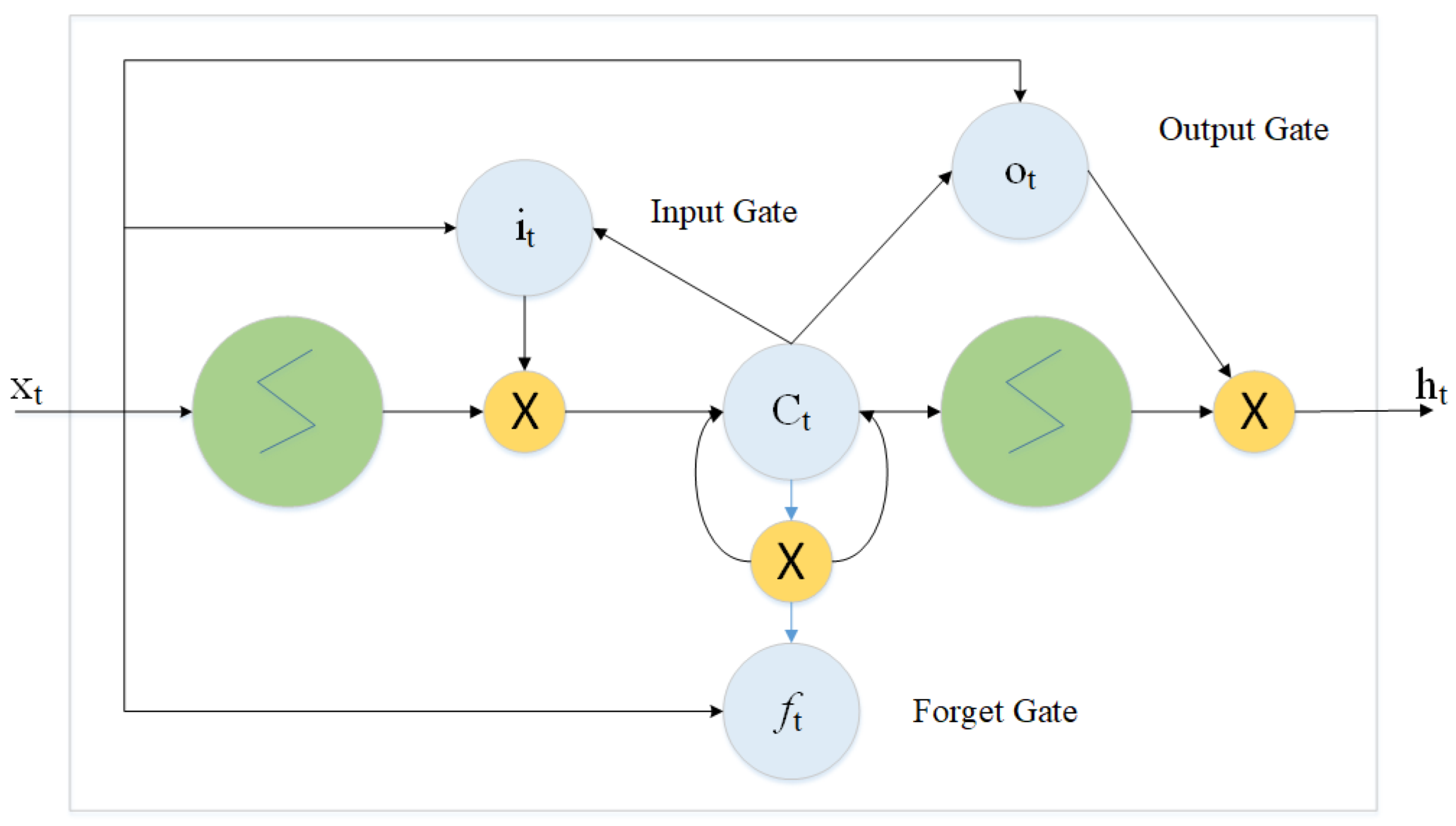
2.4.2. Long Short-Time Memory (LSTM)
2.4.3. Gated Recurrent Unit
3. Related Works
4. The Proposed Approach
4.1. Data Prepossessing
- Data cleansing step cleanses the dataset by identifying incomplete, incorrect, inaccurate, or irrelevant parts of the data for replacement, modification, or deletion. All features with empty values in the dataset are replaced with 0.
- Data transformation step changes the data by converting it from one format to another. For example, a unique numeric value replaces the text features in the dataset used. In other words, each feature’s unique values are extracted and replaced with a unique number.
- Data normalization step transforms data onto the unit sphere or translates data into the range [0, 1] (or any other range). Using Equation (11), a min–max normalization is applied to the feature vector:
- Data balancing step is a process to ensure the dataset has an equal distribution of classes, i.e., normal and attack. For example, Table 2 shows an unequal distribution of classes (43,446 normal vs. 131,859 attacks); therefore, we overcome this problem by employing the SMOTE [29] oversampling technique to bring the total number of normal classes to 131,859 samples.
4.2. Ensemble Feature Selection Technique
ICMPv6-Based Attack Detection
5. Experimental Results
5.1. Evaluation Metrics
- True positive (TP) indicates the instances where the classifier correctly classifies an attack.
- False negative (FN) indicates the instances where the classifier wrongly classifies an attack as normal.
- False positive (FP) indicates the instances where the classifier wrongly classifies a normal instance as an attack.
- True negative (TN) indicates the instances where the classifier correctly classifies normal instances.
- Precision is the proportion of attacks correctly predicted vs. all samples predicted as attacks.
- Recall, or detection rate, is the proportion of all samples correctly classified as attacks vs. all attack samples.
- False alarm rate is also known as the false positive rate and is defined as the ratio of incorrectly predicted attack samples vs. all normal samples.
- True negative rate is defined as the proportion of correctly classified normal samples vs. all normal samples.
- Accuracy, or detection accuracy, is the proportion of instances correctly classified vs. the total number of instances. However, it is only a useful performance metric when a balanced dataset is used.
- F1-measure is the harmonic mean of precision and recall. In other words, it is a statistical technique involving precision and recall for examining a system’s accuracy.
5.2. The Result of the Feature Selection Phase
5.3. Deep Learning Models Setup
5.4. Results and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Radhakrishnan, R.; Jamil, M.; Mehfuz, S.; Moinuddin, M. Security issues in IPv6. In Proceedings of the International Conference on Networking and Services (ICNS’07), Athens, Greece, 19–25 June 2007; IEEE: Piscataway, NJ, USA, 2007; p. 110. [Google Scholar]
- Caicedo, C.E.; Joshi, J.B.; Tuladhar, S.R. IPv6 security challenges. Computer 2009, 42, 36–42. [Google Scholar] [CrossRef]
- Alsadhan, A.A.; Hussain, A.; Alani, M.M. Detecting NDP distributed denial of service attacks using machine learning algorithm based on flow-based representation. In Proceedings of the 2018 11th International Conference on Developments in eSystems Engineering (DeSE), Cambridge, UK, 2–5 September 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 134–140. [Google Scholar]
- Shiranzaei, A.; Khan, R.Z. IPv6 security issues—A systematic review. Next-Gener. Netw. 2018, 638, 41–49. [Google Scholar] [CrossRef]
- Elejla, O.E.; Belaton, B.; Anbar, M.; Alnajjar, A. Intrusion detection systems of ICMPv6-based DDoS attacks. Neural Comput. Appl. 2018, 30, 45–56. [Google Scholar] [CrossRef]
- Zekri, M.; El Kafhali, S.; Aboutabit, N.; Saadi, Y. DDoS attack detection using machine learning techniques in cloud computing environments. In Proceedings of the 2017 3rd International Conference of Cloud Computing Technologies and Applications (CloudTech), Rabat, Morocco, 24–26 October 2017; pp. 1–7. [Google Scholar]
- Ahmad, Z.; Shahid Khan, A.; Wai Shiang, C.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, e4150. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, S.; Zhao, X. Intrusion Detection Algorithm Based on Convolutional Neural Network; DDEStech Transactions on Engineering and Technology Research: Lancaster, PA, USA, 2018. [Google Scholar]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Tachtatzis, C.; Atkinson, R. Shallow and deep networks intrusion detection system: A taxonomy and survey. arXiv 2017, arXiv:1701.02145. [Google Scholar]
- Alsadhan, A.; Hussain, A.; Liatsis, P.; Alani, M.; Tawfik, H.; Kendrick, P.; Francis, H. Locally weighted classifiers for detection of neighbor discovery protocol distributed denial-of-service and replayed attacks. Trans. Emerg. Telecommun. Technol. 2022, 33, e3700. [Google Scholar] [CrossRef]
- Alharbi, Y.; Alferaidi, A.; Yadav, K.; Dhiman, G.; Kautish, S. Denial-of-Service Attack Detection over IPv6 Network Based on KNN Algorithm. Wirel. Commun. Mob. Comput. 2021, 2021, 8000869. [Google Scholar] [CrossRef]
- Saad, R.M.; Anbar, M.; Manickam, S.; Alomari, E. An intelligent icmpv6 ddos flooding-attack detection framework (v6iids) using back-propagation neural network. IETE Tech. Rev. 2016, 33, 244–255. [Google Scholar] [CrossRef]
- Google. Statistics About IPv6 Connectivity Among Google Users. 2022. Available online: https://www.google.com/intl/en/ipv6/statistics.html?safe=active (accessed on 1 January 2022).
- Aleesa, A.; Zaidan, B.; Zaidan, A.; Sahar, N.M. Review of intrusion detection systems based on deep learning techniques: Coherent taxonomy, challenges, motivations, recommendations, substantial analysis and future directions. Neural Comput. Appl. 2020, 32, 9827–9858. [Google Scholar] [CrossRef]
- Bahashwan, A.A.; Anbar, M.; Hanshi, S.M. Overview of IPv6 based DDoS and DoS attacks detection mechanisms. In International Conference on Advances in Cyber Security; Springer: Singapore, 2019; pp. 153–167. [Google Scholar]
- Ahmed, A.S.; Hassan, R.; Othman, N.E. Secure neighbor discovery (SeND): Attacks and challenges. In Proceedings of the 2017 6th International Conference on Electrical Engineering and Informatics (ICEEI), Langkawi, Malaysia, 25–27 November 2017; pp. 1–6. [Google Scholar]
- Conta, A.; Deering, S.; Gupta, M. Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (ipv6) Specification; RFC 4443, IETF. 2006. Available online: https://datatracker.ietf.org/doc/rfc4443/bibtex/ (accessed on 27 April 2022).
- Ahmed, A.S.A.M.S.; Hassan, R.; Othman, N.E. IPv6 neighbor discovery protocol specifications, threats and countermeasures: A survey. IEEE Access 2017, 5, 18187–18210. [Google Scholar] [CrossRef]
- Mishra, P.; Varadharajan, V.; Tupakula, U.; Pilli, E.S. A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE Commun. Surv. Tutor. 2018, 21, 686–728. [Google Scholar] [CrossRef]
- Majeed, P.G.; Kumar, S. Genetic algorithms in intrusion detection systems: A survey. Int. J. Innov. Appl. Stud. 2014, 5, 233. [Google Scholar]
- Liu, X.; Xie, L.; Wang, Y.; Zou, J.; Xiong, J.; Ying, Z.; Vasilakos, A.V. Privacy and security issues in deep learning: A survey. IEEE Access 2020, 9, 4566–4593. [Google Scholar] [CrossRef]
- Sherstinsky, A. Fundamentals of recurrent neural network (RNN) and long short-term memory (LSTM) network. Phys. D Nonlinear Phenom. 2020, 404, 132306. [Google Scholar] [CrossRef] [Green Version]
- Hochreiter, S.; Schmidhuber, J. Long short-term memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef] [PubMed]
- Cho, K.; Van Merriënboer, B.; Gulcehre, C.; Bahdanau, D.; Bougares, F.; Schwenk, H.; Bengio, Y. Learning phrase representations using RNN encoder-decoder for statistical machine translation. arXiv 2014, arXiv:1406.1078. [Google Scholar]
- Anbar, M.; Abdullah, R.; Al-Tamimi, B.N.; Hussain, A. A machine learning approach to detect router advertisement flooding attacks in next-generation IPv6 networks. Cogn. Comput. 2018, 10, 201–214. [Google Scholar] [CrossRef] [Green Version]
- Zulkiflee, M.; Haniza, N.; Shahrin, S.; Ghani, M. A framework of ipv6 network attack dataset construction by using testbed environment. Int. Rev. Comput. Softw. (IRECOS) 2014, 9, 1434–1441. [Google Scholar] [CrossRef]
- Salih, A.; Ma, X.; Peytchev, E. New intelligent heuristic algorithm to mitigate security vulnerabilities in IPv6. IJIS Int. J. Inf. Secur. 2015, 4, 2382–2619. [Google Scholar]
- Elejla, O. A Reference Dataset for ICMPv6 Flooding Attacks* Omar E. Elejla," Bahari Belaton," Mohammed Anbar and “Ahmad Alnajjar" School of Computer Science, Universiti Sains Malaysia, Penang, Malaysia “National Advanced IPv6 Centre (NAv6), Universiti Sains Malaysia, Penang, Malaysia. J. Eng. Appl. Sci. 2016, 100, 476–481. [Google Scholar]
- Fernández, A.; Garcia, S.; Herrera, F.; Chawla, N. SMOTE for learning from imbalanced data: Progress and challenges, marking the 15-year anniversary. J. Artif. Intell. Res. 2018, 61, 863–905. [Google Scholar] [CrossRef]
- Thaseen, I.; Kumar, C. Intrusion detection model using fusion of chi-square feature selection and multi class SVM. J. King Saud Univ. Comput. Inf. Sci. 2017, 29, 462–472. [Google Scholar]
- Sahoo, K.S.; Puthal, D. SDN-assisted DDoS defense framework for the internet of multimedia things. ACM Trans. Multimed. Comput. Commun. Appl. (TOMM) 2020, 16, 1–18. [Google Scholar] [CrossRef]




| Author(s) | Techniques | IPv6 Protocol | Dataset Type | Detection Accuracy | Limitations | ||
|---|---|---|---|---|---|---|---|
| ML | DL | IPv6 | IPv4 | ||||
| Alsadhan et al. [3] | ✓ | ✗ | ✓ | ✓ | ✗ | 84.5% | This approach achieves low performance. |
| Elejla et al. [5] | ✓ | ✗ | ✓ | ✓ | ✗ | 85.83% | Achieves low detection accuracy. |
| Alsadhan et al. [10] | ✓ | ✗ | ✓ | ✓ | ✗ | 99% and 91.17% | Limited to detect NDP attacks. |
| Alharbi et al. [11] | ✓ | ✗ | ✓ | ✗ | ✓ | - | No information about detection accuracy. It was also evaluated with an IPv4 dataset. |
| Saad et al. [12] | ✓ | ✗ | ✓ | ✓ | ✗ | 98.3% | Designed to detect only ICMPv6 echo request attacks. |
| Anbar et al. [25] | ✓ | ✗ | ✓ | ✓ | ✗ | 98.55% | Designed to detect only RA DDoS. |
| Zulkiflee et al. [26] | ✓ | ✗ | ✓ | ✓ | ✗ | 99.95% | Only detects RA DDoS attacks. |
| Salih et al. [27] | ✓ | ✗ | ✓ | ✓ | ✗ | 96.46% | Still, the performance needs to be improved. |
| Total Number of Rows | 175,305 |
| Categorical Data | {normal, attack} |
| Number of Normal Packets | 131,859 |
| Number of Attack Packets | 43,446 |
| Number of Features | 19 |
| Features Names | Time, Source, Destination, Protocol, ICMPv6 type, MAC Src Addr, MAC Dst Addr, IPv6 next header, Length, Src Port, Dst Port, RA MTU, RA router lifetime, RA prefix, RA flag, NA flags, NS target, MLD flags, Class |
| Numerical Features | ICMPv6 Type, Src Port, Dst Port, RA MTU, RA router lifetime, RA prefix, RA flag, NA flags, NS target, MLD flags |
| Text Features | Time, Source, Destination, Protocol, MAC Src Addr, MAC Dst Addr, class |
| Predicted Class | ||
|---|---|---|
| Actual Class | Attack | Normal |
| True Positive | False Negative | |
| False Positive | True Negative | |
| No. | Feature | Feature Score (IGR) | Feature Score (Chi-Square) |
|---|---|---|---|
| 1 | ICMPv6 type | 4.06843988 | 1.17426781 |
| 2 | IPv6 next header | 1.51979191 | 3.72058524 |
| 3 | Length | 4.46315199 | 11.2899829 |
| 4 | RA MTU | 0.027046904 | 0.992166989 |
| 5 | RA router lifetime | 0.139719657 | 2.1899984 |
| 6 | RA prefix | 0.026007147 | 0.478028763 |
| 7 | RA flag | 0.118992257 | 2.1899984 |
| 8 | NA flags | 0.712575719 | 2.50574105 |
| 9 | NS target | 1.6334663 | 13.8955392 |
| 10 | MLD flags | 0.001439028 | 0.000998617 |
| No. | Feature | IGR (th1 = 0.1) | Chi-Square (th2 = 1) |
|---|---|---|---|
| 1 | ICMPv6 type | 4.06843988 | 1.17426781 |
| 2 | IPv6 next header | 1.51979191 | 3.72058524 |
| 3 | Length | 4.46315199 | 11.2899829 |
| 4 | RA router lifetime | 0.139719657 | 2.1899984 |
| 5 | RA flag | 0.118992257 | 2.1899984 |
| 6 | NA flags | 0.712575719 | 2.50574105 |
| 7 | NS target | 1.6334663 | 13.8955392 |
| Layer (Type) | Output Shape | Param # |
|---|---|---|
| simple_rnn_4 (SimpleRNN) | (None, 32) | 1088.0 |
| dropout_22 (Dropout) | (None, 32) | 0 |
| batch_normalization_11 | ||
| (Batch Normalization) | (None, 32) | 128.0 |
| dropout_23 (Dropout) | (None, 32) | 0 |
| flatten_11 (Flatten) | (None, 32) | 0 |
| dense_11 (Dense) | (None, 31) | 66.0 |
| Total params: 1282.0 Trainable params: 1218.0 Non-trainable params: 64.0 | ||
| Layer (Type) | Output Shape | Param # |
|---|---|---|
| lstm_4 (LSTM) | (None, 32) | 4352.0 |
| dropout_24 (Dropout) | (None, 32) | 0 |
| batch_normalization_12 | ||
| (Batch Normalization) | (None, 32) | 128.0 |
| dropout_25 (Dropout) | (None, 32) | 0 |
| flatten_12 (Flatten) | (None, 32) | 0 |
| dense_12 (Dense) | (None, 2) | 66.0 |
| Total params: 4546.0 Trainable params: 4482.0 Non-trainable params: 64.0 | ||
| Layer (Type) | Output Shape | Param # |
|---|---|---|
| gru_3 (GRU) | (None, 32) | 3360.0 |
| dropout_26 (Dropout) | (None, 32) | 0 |
| batch_normalization_13 | ||
| (Batch Normalization) | (None, 32) | 128.0 |
| dropout_27 (Dropout) | (None, 32) | 0 |
| flatten_13 (Flatten) | (None, 32) | 0 |
| dense_13 (Dense) | (None, 2) | 66.0 |
| Total params: 3554.0 Trainable params: 3490.0 Non-trainable params: 64.0 | ||
| Actual Class | Attack | Normal |
|---|---|---|
| Confusion matrix of RNN | ||
| Attack | 25,668 | 619 |
| Normal | 3412 | 23,045 |
| Confusion matrix of LSTM | ||
| Attack | 25,598 | 689 |
| Normal | 146 | 26,311 |
| Confusion matrix of GRU | ||
| Attack | 25,631 | 656 |
| Normal | 234 | 26,223 |
| Model | TNR (%) | FNR (%) | FPR (%) | Accuracy (%) | F- Measure (%) |
|---|---|---|---|---|---|
| RNN | 87.1 | 2.3 | 12.8 | 92.3 | 92.71 |
| LSTM | 99.4 | 2.62 | 0.551 | 98.41 | 98.39 |
| GRU | 99.11 | 2.49 | 0.884 | 98.31 | 98.29 |
| Run # | RNN (Second) | LSTM (Second) | GRU (Second) |
|---|---|---|---|
| Run 1 | 5.566 | 8.311 | 8.440 |
| Run 2 | 5.421 | 8.270 | 7.860 |
| Run 3 | 5.603 | 8.431 | 8.029 |
| Average Detection Time | 5.530 | 8.337 | 8.110 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Elejla, O.E.; Anbar, M.; Hamouda, S.; Faisal, S.; Bahashwan, A.A.; Hasbullah, I.H. Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks. Appl. Sci. 2022, 12, 6150. https://doi.org/10.3390/app12126150
Elejla OE, Anbar M, Hamouda S, Faisal S, Bahashwan AA, Hasbullah IH. Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks. Applied Sciences. 2022; 12(12):6150. https://doi.org/10.3390/app12126150
Chicago/Turabian StyleElejla, Omar E., Mohammed Anbar, Shady Hamouda, Serri Faisal, Abdullah Ahmed Bahashwan, and Iznan H. Hasbullah. 2022. "Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks" Applied Sciences 12, no. 12: 6150. https://doi.org/10.3390/app12126150
APA StyleElejla, O. E., Anbar, M., Hamouda, S., Faisal, S., Bahashwan, A. A., & Hasbullah, I. H. (2022). Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks. Applied Sciences, 12(12), 6150. https://doi.org/10.3390/app12126150






