A Multi-Objective Optimization of Secure Pull Manufacturing Systems
Abstract
:1. Introduction
2. Literature Review
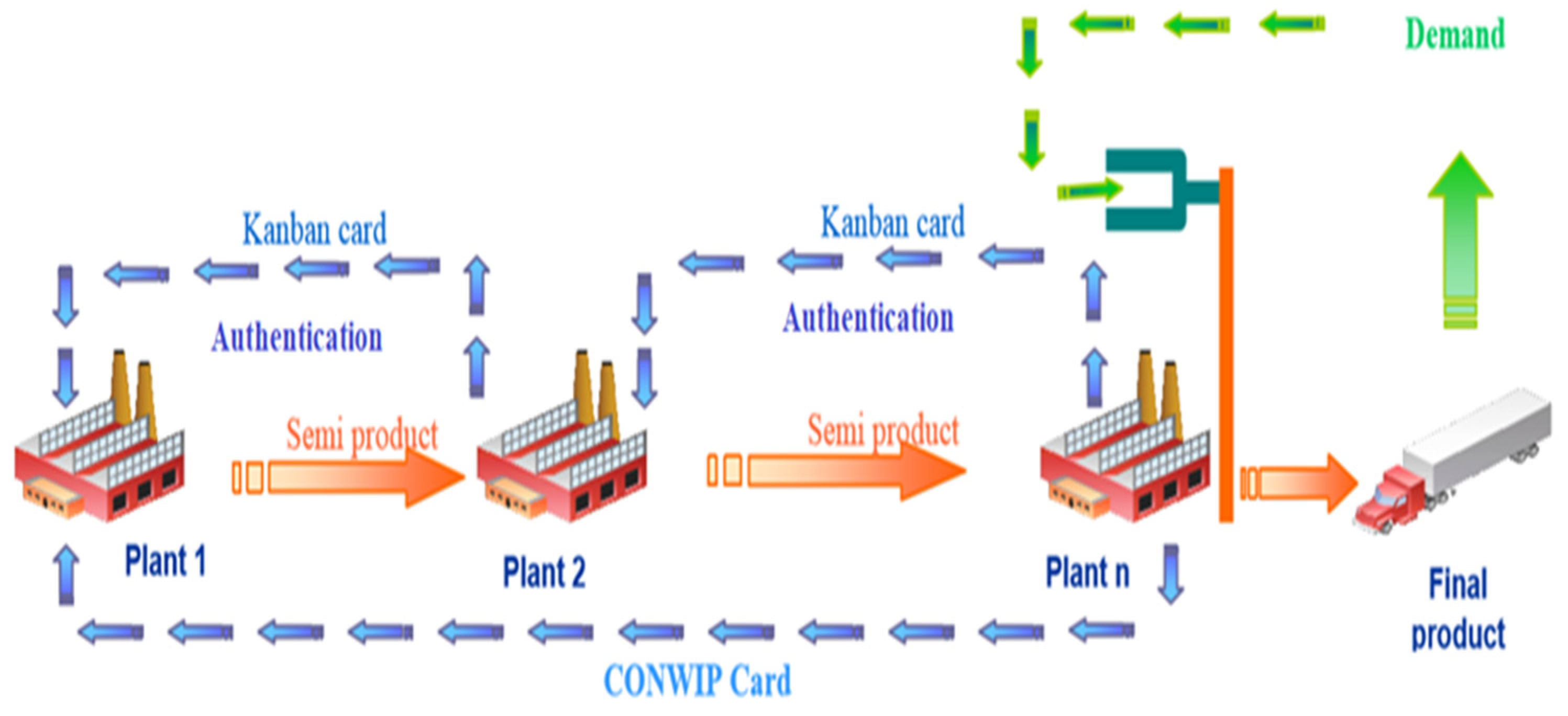
2.1. Kanban System
2.2. e-Kanban Card-Based Pull Control Systems
2.3. Security System
2.4. Flower Pollination Algorithm (FPA)
3. Methodology
3.1. BioGamal Secure Algorithm
3.1.1. BioGamal Technique
- Phase 1: Generation of key
- Create a large prime number p and primitive group where are relatively prime to p
- Generate another primitive element g and free element to produce public and private key.
- Public key is molded by three pair of parameters as:where, is the private key that is secret value.
- Phase 2: Encryption of message
- The algorithm uses public key and random secret integer k,
- Encrypt each character in the message using dissimilar k number.
- Compute r and t values as follow
- Cipher text achieved as (r, t).
- Phase 3: Decryption of message
- Utilize secret key and public keys to perform the decryption phase. From received cipher text (r, t), plaintext is performed as:
3.1.2. Kanban Card Secure Algorithm
- Step 1: Plant 1 read data on Kanban card where the data is divided into two parts: first, the warranty message , which include item ID, Kanban ID, supplier ID, quantity and supplier name; the second part is message M, which includes the description of semi product.
- Step 2: Apply hash function SHA-256 to the input message M as followM = “semi product that converts electrical energy into mechanical energy…”H(M) = “3f4058956969ea1ecc05b86990899847c509ec8f07b5d5a27404490deebe1edd”
- Step 3: Convert ASCII message from hashing step to binary number to apply DNA encoding as follow“0011001101100110001101000011000000110101001110000011100100110101001101100011100100110110001110010110010101100001001100010110010101100011011000110011000000101010110001000111000001101100011100100111001001100000011100000111001001110010……………………000100110010100110001011001010110010001100100”
- Step 4: Apply paring of each two bits then assign DNA digital coding for each paring as follow“ATATGCGCATGAATAAATGGATGAATGC …………………CGCA”
- Step 5: Formulate DNA sequence into DNA key combination as stated in Table 1“111111181011018111 ……… 1412”
- Step 6: Separate DNA key combination by “0” or “@”between the sequences to obtain cipher text 1C1 = “11 11 11 1 8 1 0 1 10 1 8 11 ……… 14 12”
- Step 7: Encrypt the cipher text 1 obtained from DNA encoding by using ElGamal algorithm as described in Section 3.1.1. Generate the key generation of ElGamal algorithm where the public key denoted by and the private key denoted by and H be a hash function
- Step 8: To sign the message use the secret key
- Preference a random number with unit GCD between k and p − 1
- Calculate where
- Calculate where is the concatenation of C1, r and
- Produce the pair of (r, s) as the digital signature on C1
- Step 9: Apply the decryption process, as shown in Figure 4, where Plant 2 received the signed message on the Kanban card. Then it applies the decryption ElGamal algorithm using public key and recovers the hashing value using DNA decryption algorithm.
- Step 10: Verify the signature of Plant 2
- Validate that else, he discard the signature.
- Calculate
- Agree the signature if otherwise Plant 2 discard.
3.2. Multi-Objective Flower Pollination Technique
- Pollen-carrying pollinators can fly a great distance, which obeys Lévy flights, and biotic and cross-pollination can be considered a global pollination process (Rule 1).
- Local pollination can be defined as biotic and self-pollination (Rule 2).
- Flower constancy can be equated to a reproduction chance proportional to the similarity of the two flowers in question (Rule 3).
- Local pollination and global pollination are switched on and off.
Multiobjective FPA of Secure Kanban/CONWIP
- : production cost for product type i in plant j
- : transportation cost for product type i from plant j to plant j + 1
- T: time of model replication
- : number of product type i in plant j
- : number of transported product type i from plant j to plant j + 1 at unit time
- : transportation cost for each part of final product type i to customer
- : number of final product type i
- : cost of production of final product type i
4. Simulation Results
4.1. Security Measurements
4.2. Experimental Results
4.3. Computation Analysis
5. Conclusions and Future Work
- (a)
- Using a new security BioGamal technique is better for the verification of data between different stages, especially for sensitive industries.
- (b)
- Application of FPA, to optimize the time and the cost of the overall production line, contains 8 stages, minimized by 5%, while for the 10 stages, it is optimized within 7%.
- (c)
- The percentage of cost and time reduction for 14 stages is higher than the percentage of cost and time reduction for 8 and 10 stages: within 2.5% difference rate.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- ISO/IEC 27002; Information Technology—Security Techniques—Code of Practice for Information Security Management. ISO: Geneva, Switzerland, 2005.
- Kumar, C.S.; Panneerselvam, R. Literature review of JIT-KANBAN system. Int. J. Adv. Manuf. Technol. 2006, 32, 393–408. [Google Scholar] [CrossRef]
- González-R, P.L.; Framinan, J.M.; Pierreval, H. Token-based pull production control systems: An introductory overview. J. Intell. Manuf. 2012, 23, 5–22. [Google Scholar] [CrossRef]
- Prakash, J.; Chin, J. Modified CONWIP systems: A review and classification. Prod. Plan. Control. 2015, 26, 296–307. [Google Scholar] [CrossRef]
- Junior, M.L.; Filho, M.G. Variations of the kanban system: Literature review and classification. Int. J. Prod. Econ. 2010, 125, 13–21. [Google Scholar] [CrossRef]
- Pierreval, H.; Daures, A.; Both, T.; Szimczak, S.; Gonzalez, P.; Framinan, J. A simulation optimization approach for reactive ConWIP systems. In Proceedings of the 2013 8th EUROSIM Congress on Modelling and Simulation (EU-ROSIM), Cardiff, UK, 10–13 September 2013; pp. 415–420. [Google Scholar]
- Zhang, Y.; Jiang, P.; Huang, G. RFID-based smart Kanbans for Just-In-Time manufacturing. Int. J. Mater. Prod. Technol. 2008, 33, 170–184. [Google Scholar] [CrossRef]
- Belisário, L.S.; Azouz, N.; Pierreval, H. Adaptive conwip: Analyzing the impact of changing the number of cards. In Proceedings of the 2015 International Conference on Industrial Engineering and Systems Management, Seville, Spain, 21–23 October 2015. [Google Scholar]
- Houti, M.; El Abbadi, L.; Abouabdellah, A. E-Kanban the new generation of traditional Kanban system, and the impact of its implementation in the enterprise. In Proceedings of the International Conference on Industrial Engineering and Operations Management, Rabat, Morocco, 11–13 April 2017. [Google Scholar]
- Fathy, A. A Reliable Methodology Based On Mine Blast Optimization Algorithm For Optimal Sizing Of Hybrid PV-Wind-FC System For Remote Area In Egypt. Renew. Energy 2016, 95, 367–380. [Google Scholar] [CrossRef]
- Zahhafi, L.; Khadir, O. An ElGamal-Like Digital Signature Based on Elliptic Curves. In Mobile, Secure, and Programmable Networking; Renault, É., Boumerdassi, S., Leghris, C., Bouzefrane, S., Eds.; MSPN 2019. Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11557. [Google Scholar] [CrossRef]
- Mohamed, H.G.; ElKamchouchi, D.H.; Moussa, K.H. A Novel Color Image Encryption Algorithm Based on Hyperchaotic Maps and Mitochondrial DNA Sequences. Entropy 2020, 22, 158. [Google Scholar] [CrossRef] [PubMed]
- ElKamchouchi, D.H.; Mohamed, H.G.; Moussa, K.H. A Bijective Image Encryption System Based on Hybrid Chaotic Map Diffusion and DNA Confusion. Entropy 2020, 22, 180. [Google Scholar] [CrossRef]
- Kasodhan, R.; Gupta, N. A New Approach of Digital Signature Verification based on BioGamal Algorithm. In Proceedings of the 2019 3rd International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 27–29 March 2019; pp. 10–15. [Google Scholar] [CrossRef]
- Azouz, N.; Pierreval, H. Adaptive smart card-based pull control systems in context-aware manufacturing systems: Training a neural network through multi-objective simulation optimization. Appl. Soft Comput. 2019, 75, 46–57. [Google Scholar] [CrossRef]
- Pekarcikova, M.; Trebuna, P.; Kliment, M.; Rosocha, L. Material Flow Optimization through E-Kanban System Simulation. Int. J. Simul. Model. 2020, 19, 243–254. [Google Scholar] [CrossRef]
- Monden, Y. The Toyota Production System; Industrial Engineering and Management Press: Norcross, GA, USA, 1983. [Google Scholar]
- Rees, L.P.; Philipoom, P.R.; Taylor, B.W.; Huang, P.Y. Dynamically adjusting the number of kanbans in a just-in-time production system using estimated values of lead time. IIE Trans. 1987, 19, 199–207. [Google Scholar] [CrossRef]
- Co, H.C.; Sharafali, M. Overplanning factor in Toyota′s formula for computing the number of kanban. IIE Trans. 1997, 29, 409–415. [Google Scholar] [CrossRef]
- Wang, S.; Sarker, B.R. Optimal models for a multi-stage supply chain system controlled by kanban under just-in-time philosophy. Eur. J. Oper. Res. 2006, 172, 179–200. [Google Scholar] [CrossRef]
- Yusoff, N.; Jaffar, A.; Abdul, H.; Nurul, H. Implementation of Just in Time Production through Kanban System. 2019. Available online: https://www.researchgate.net/publication/331274310_Implementation_of_Just_in_Time_Production_through_Kanban_System (accessed on 1 February 2019).
- Belisário, L.S.; Pierreval, H. Using genetic programming and simulation to learn how to dynamically adapt the number of cards in reactive pull systems. Expert Syst. Appl. 2015, 42, 3129–3141. [Google Scholar] [CrossRef]
- Thürer, M.; Stevenson, M.; Protzman, C.W. Card-based production control: A review of the control mechanisms underpinning Kanban, ConWIP, POLCA and COBACABANA systems. Prod. Plan. Control. 2016, 27, 1143–1157. [Google Scholar]
- Xanthopoulos, A.; Koulouriotis, D.; Gasteratos, A. Adaptive card-based production control policies. Comput. Ind. Eng. 2017, 103, 131–144. [Google Scholar] [CrossRef]
- Hopp, W.J.; Roof, M. Setting WIP levels with statistical throughput control (STC) in CONWIP production lines. Int. J. Prod. Res. 1998, 36, 867–882. [Google Scholar] [CrossRef]
- Framinan, J.M.; González, P.L.; Ruiz-Usano, R. Dynamic card controlling in a Conwip system. Int. J. Prod. Econ. 2006, 99, 102–116. [Google Scholar] [CrossRef]
- Gonzalez-R, P.L.; Framinan, J.M.; Usano, R.R. A response surface methodology for parameter setting in a dynamic Conwip production control system. Int. J. Manuf. Technol. Manag. 2011, 23, 16. [Google Scholar] [CrossRef]
- Liu, Q.; Huang, D. Dynamic card number adjusting strategy in card-based production system. Int. J. Prod. Res. 2009, 47, 6037–6050. [Google Scholar] [CrossRef]
- Ghofar, A.; Hardi, M.; Firdaus, M.N.; Shidik, G.F. Digital Signature Based on PlayGamal Algorithm. In Proceedings of the International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 7–8 October 2017; pp. 58–65. [Google Scholar]
- Utama, K.D.B.; Al-Ghazali, Q.M.R.; Mahendra, L.I.B.; Shidik, G.F. Digital Signature using MAC Address based AES128 and SHA-2 256-bit. In Proceedings of the International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 7–8 October 2017; pp. 72–78. [Google Scholar]
- Chernyi, S.G.; Ali, A.A.; Veselkov, V.V.; Titov, I.L.; Budnik, V.Y. Security of Electronic Digital Signature in Maritime Industry. In Proceedings of the IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow and St. Petersburg, Russia, 29 January–1 February 2018; pp. 29–32. [Google Scholar]
- Alam, S.; Jamil, A.; Saldhi, A.; Ahmad, M. Digital Image Authentication and Encryption using Digital Signature. In Proceedings of the International Conference on Advances in Computer Engineering and Applications (ICACEA), Ghaziabad, India, 19–20 March 2015; pp. 332–336. [Google Scholar]
- Gerić, S.; Vidačić, T. XML Digital Signature and its Role in Information System Security. In Proceedings of the 35th International Convention MIPRO, Opatija, Croatia, 21–25 May 2012. [Google Scholar]
- Xuan, Z.; Du, Z.; Chen, R. Comparison Research on Digital Signature Algorithms in Mobile Web Services. In Proceedings of the International Conference on Management and Service Science, Beijing, China, 20–22 September 2009. [Google Scholar]
- Deng, J.; Cheng, X.; Gui, Q. Design of Hyper Elliptic Curve Digital Signature. In Proceedings of the International Conference on Information Technology and Computer Science, Kiev, Ukraine, 25–26 July 2009; pp. 45–47. [Google Scholar]
- Can, X.; Lin, Y. A New Conic Curve Digital Signature Scheme. In Proceedings of the 2009 Fifth International Conference on Information Assurance and Security, Xi’an, China, 18–20 August 2009; pp. 623–626. [Google Scholar]
- Yang, X.-S. Flower pollination algorithm for global optimization. In Unconventional Computation and Natural Computation; Springer: Berlin/Heidelberg, Germany, 2012; pp. 240–249. [Google Scholar]
- Alam, D.F.; Yousri, D.A.; Eteiba, M.B. Flower Pollination Algorithm based solar PV parameter estimation. Energy Convers. Manag. 2015, 101, 410–422. [Google Scholar] [CrossRef]
- Ram, J.P.; Babu, T.S. A new hybrid bee pollinator flower pollination algorithm for solar PV parameter estimation. Energy Convers Manag. 2017, 135, 463–476. [Google Scholar] [CrossRef]
- Rodrigues, D.; Silva, G.F.; Papa, J.P.; Marana, A.N.; Yang, X.-S. Eeg-based person identification through binary flower pollination algorithm. Expert Syst. Appl. 2016, 62, 81–90. [Google Scholar] [CrossRef]
- Sharawi, M.; Emary, E.; Saroit, I.A.; El-Mahdy, H. Flower pollination optimization algorithm for wireless sensor network lifetime global optimization. Int. J. Soft Comput. Eng. 2014, 4, 54–59. [Google Scholar]
- Zawbaa, H.M.; Emary, E. Applications of flower pollination algorithm in feature selection and knapsack problems. In Nature-Inspired Algorithms and Applied Optimization; Yang, X.-S., Ed.; Springer: Berlin/Heidelberg, Germany, 2018; pp. 217–243. [Google Scholar] [CrossRef]
- Abdel-Raouf, O.; El-Henawy, I.; Abdel-Baset, M. A novel hybrid flower pollination algorithm with chaotic harmony search for solving sudoku puzzles. Int. J. Mod. Educ. Comput. Sci. 2014, 6, 38–44. [Google Scholar] [CrossRef]
- Nigdeli, S.M.; Bekdaş, G.; Yang, X.-S. Application of the flower pollination algorithm in structural engineering. In Metaheuristics and Optimization in Civil Engineering; Springer: Berlin/Heidelberg, Germany, 2016; pp. 25–42. [Google Scholar]
- Köchel, P.; Nieländer, U. Kanban optimization by simulation and evolution. Prod. Plan. Control. 2002, 13, 725–734. [Google Scholar] [CrossRef]
- Yang, X.-S. Multi-Objective Flower Pollination Algorithm (MOFPA). 2019. Available online: https://www.researchgate.net/publication/340279071_Multi-objective_Flower_Pollination_Algorithm_MOFPA (accessed on 8 May 2022).
- Kundu, K.; Rossini, M.; Portioli-Staudacher, A. A study of a kanban based assembly line feeding system through integration of simulation and particle swarm optimization. Int. J. Ind. Eng. Comput. 2019, 10, 421–442. [Google Scholar] [CrossRef]
- Alweshah, M.; Qadoura, M.A.; Hammouri, A.I.; Azmi, M.S.; AlKhalaileh, S. Flower Pollination Algorithm for Solving Classification Problems. Int. J. Adv. Soft Compu. Appl. 2020, 12, 15–34. [Google Scholar]
- Abdelaziz, A.Y.; Ali, E.S.; Abd Elazim, S.M. Flower Pollination Algorithm and Loss Sensitivity Factors For Optimal Sizing and Placement of Capacitors in Radial Distribution Systems. Int. J. Electr. Power Energy Syst. 2016, 78, 207–214. [Google Scholar] [CrossRef]
- Abdelaziz, A.; Ali, E.; Abd-Elazim, S. Implementation of flower pollination algorithm for solving economic load dispatch and combined economic emission dispatch problems in power systems. Energy 2016, 101, 506–518. [Google Scholar] [CrossRef]
- Yang, X.S.; Karamanoglu, M.; He, X. Flower pollination algorithm: A novel approach for multiobjective optimization. Eng. Optim. 2014, 46, 1222–1237. [Google Scholar] [CrossRef]









| Pattern | Key Combination | Value |
|---|---|---|
| 0000 | AA | 0 |
| 0001 | AT | 1 |
| 0010 | AG | 2 |
| 0011 | AC | 3 |
| 0100 | TA | 4 |
| 0101 | TT | 5 |
| 0011 | TG | 6 |
| 0111 | TC | 7 |
| 1000 | GA | 8 |
| 1001 | GT | 9 |
| 1010 | GG | 10 |
| 1011 | GC | 11 |
| 1100 | CA | 12 |
| 1101 | CT | 13 |
| 1110 | CG | 14 |
| 1111 | CC | 15 |
| Security Measurements | Performance Analysis |
|---|---|
| Verification | Plant 2 can check the signature by the following verification equation If hold, then he accept the semi product from Plant 1 |
| Unforgeability | In proposed algorithm, the signature is made with Plant 1’s secret key α. Nobody (as well as Plant 1) can develop the digital signature without having the information on the secret key α. Getting the secret key by some other gathering is as difficult as breaking BioGamal algorithm. In addition, the verification of the signed Kanban card keeps the forged party from the production of fabricated digital signatures. Subsequently, any tip including the Plant 1 can’t counterfeit a valid signature and hence the proposed system fulfills the unforgeability property |
| Identification | The verification process of the proposed scheme requires Plant 1 public key β and warrant . Any verifier can decide the identity of Plant 1 from the signed message, because the signed message is which contains the warranty data that include the identites of end users. Along these lines, from the first security process any verifier can be sure from the identity of the Plant 1 from . |
| Undeniability | From digital signature of the proposed system, the warrant and the combination of the public keys β and r in the verification process dictate the contributions of both Plant 1 and Plant 2. Hence, Plant 1 and Plant 2 cannot deny their association in an authenticated digital signature. In this way, the system fulfills the undeniability property. |
| Algorithms | Encryption Process | Decryption Process | ||||
|---|---|---|---|---|---|---|
| Stages | 8 Stages | 10 Stages | 14 Stages | 8 Stages | 10 Stages | 14 Stages |
| Time with FPA | 0.1415 | 0.0236 | 0.0042 | 0.1336 | 0.0475 | 0.0039 |
| Time without FPA | 1.5289 | 1.3759 | 1.1706 | 1.4729 | 1.2470 | 1.1657 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Elattar, S.; Mohamed, H.G.; Hussien, S.A. A Multi-Objective Optimization of Secure Pull Manufacturing Systems. Appl. Sci. 2022, 12, 5937. https://doi.org/10.3390/app12125937
Elattar S, Mohamed HG, Hussien SA. A Multi-Objective Optimization of Secure Pull Manufacturing Systems. Applied Sciences. 2022; 12(12):5937. https://doi.org/10.3390/app12125937
Chicago/Turabian StyleElattar, Samia, Heba G. Mohamed, and Shimaa A. Hussien. 2022. "A Multi-Objective Optimization of Secure Pull Manufacturing Systems" Applied Sciences 12, no. 12: 5937. https://doi.org/10.3390/app12125937






