3.1. Hierarchy for the Evaluation
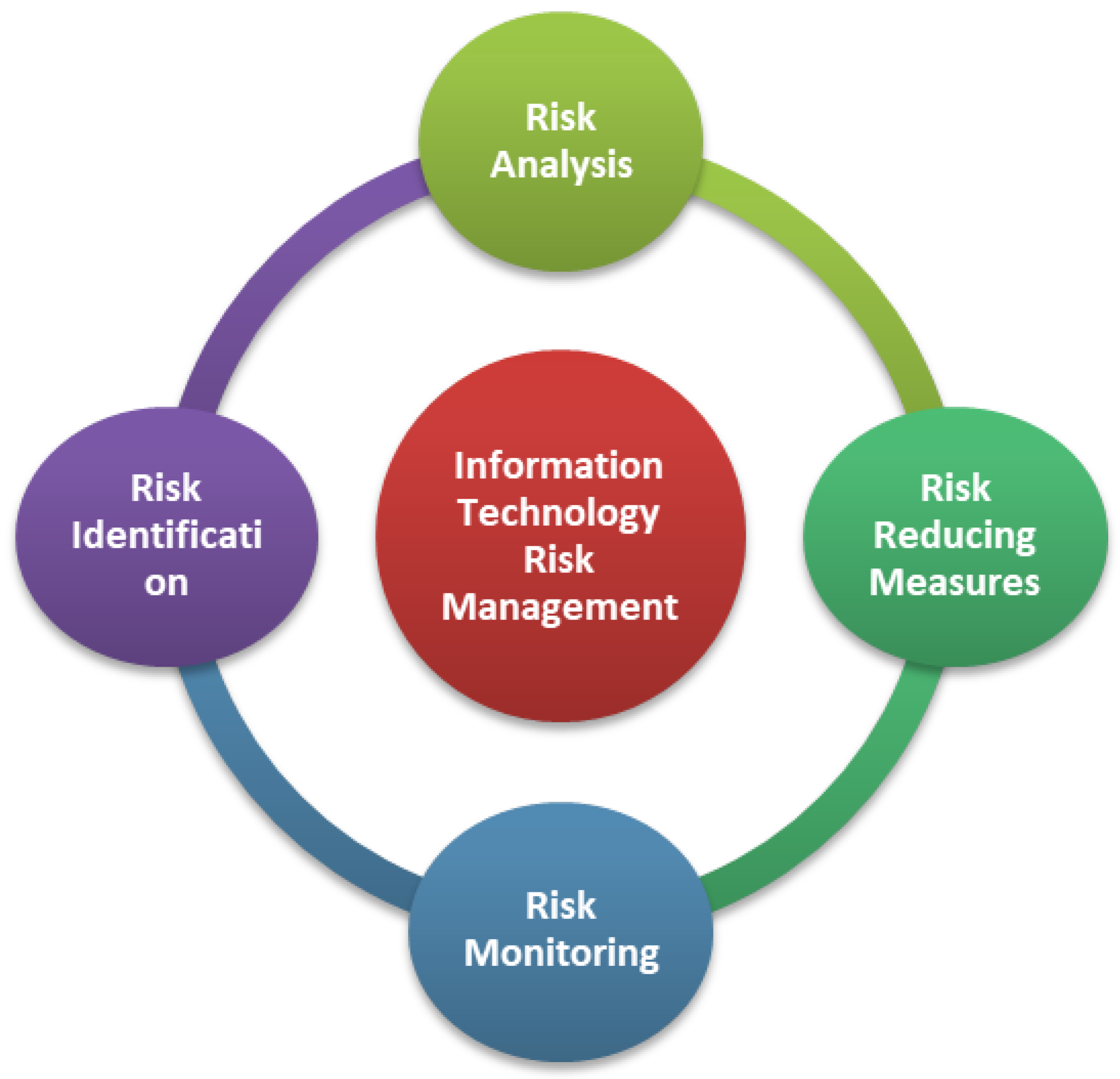
Risk implications evaluation is the method of evaluating the likelihood and consequences of possible risks if they are actually realized. In this research, a fuzzy multi-criteria decision-making method is presented for the analysis and ranking of IT risk factors in an organizational environment from 25 decision makers. There are many criteria in this issue, which has a hierarchical arrangement of criteria as well as numerous risk factors as alternatives. The findings of this study are then utilized to prioritize risk measures in order among most critical to least crucial significance. Scoring risks based on their criticality or significance informs project planning about where resources could be required to handle or mitigate the occurrence of possible risks of strongly likely consequences. Based on the literature review and expert’s suggestion, we have identified eight IT risk factors, i.e., Technology, Financial, People, Vendors, Operational, Policy and Procedures, Environmental, and Strategic, which are denoted by A1, A2, A3, A4, A5, A6, A7, and A8, respectively. To prioritize these IT risk factors we have also recognized some criteria, such as Effectiveness, Event frequency, Availability, Consequence, Adequacy, and Discoverability, that are denoted by C1, C2, C3, C4, C5, and C6, respectively.
The following
Figure 3 shows the graphical representation of the hierarchical structure used for the evaluation of IT risk factors using fuzzy TOPSIS-based approach.
3.2. Fuzzy TOPSIS Method
The fuzzy TOPSIS tactic is an approach that was developed from the TOPSIS core principle to address a wide range of MCDM challenges in an uncertain setting. Chen and Hwang established the fuzzy TOPSIS procedure in 1992 by applying fuzzy values to the TOPSIS procedure [
27]. Chen introduced a vertex process to calculate the distance among two TFNs in 2000 [
28]. TFNs would then portray the decision makers’ perspectives on characteristics as well as alternatives in this strategy. The alternatives would then be ranked depending on the distance closest to ideal solutions, and the ranking consequence would be used to make the selection. The fuzzy TOPSIS process works on the same principles as the TOPSIS method, and yet in a more ambiguous setting. There are numerous benefits to using the fuzzy TOPSIS approach for solving MCDM challenges. To begin, the fuzzy TOPSIS procedure was introduced to resolve the ambiguity that frequently emerges in information derived from human decision. Let
X1 = (
x1,
x2,
x3) and
Y1 = (
y1,
y2,
y3) be two triangular fuzzy numbers (TFNs); therefore, the following Equation (1) could be used to calculate the distance between the two TFNs.
Furthermore, we have discovered numerous uncertain circumstances that have been predicted using TFNs to produce an improved result when solving MCDM major issues. Moreover, the fuzzy TOPSIS strategy is simple and straightforward for tackling MCDM challenges with imprecise information. According to a review of relevant literature [
29,
30,
31,
32,
33], this process could be used as a separate strategy to solving MCDM challenges such as assessing various websites as well as examining the variables that assist to enhance the comparative benefit of those targeted online platforms.
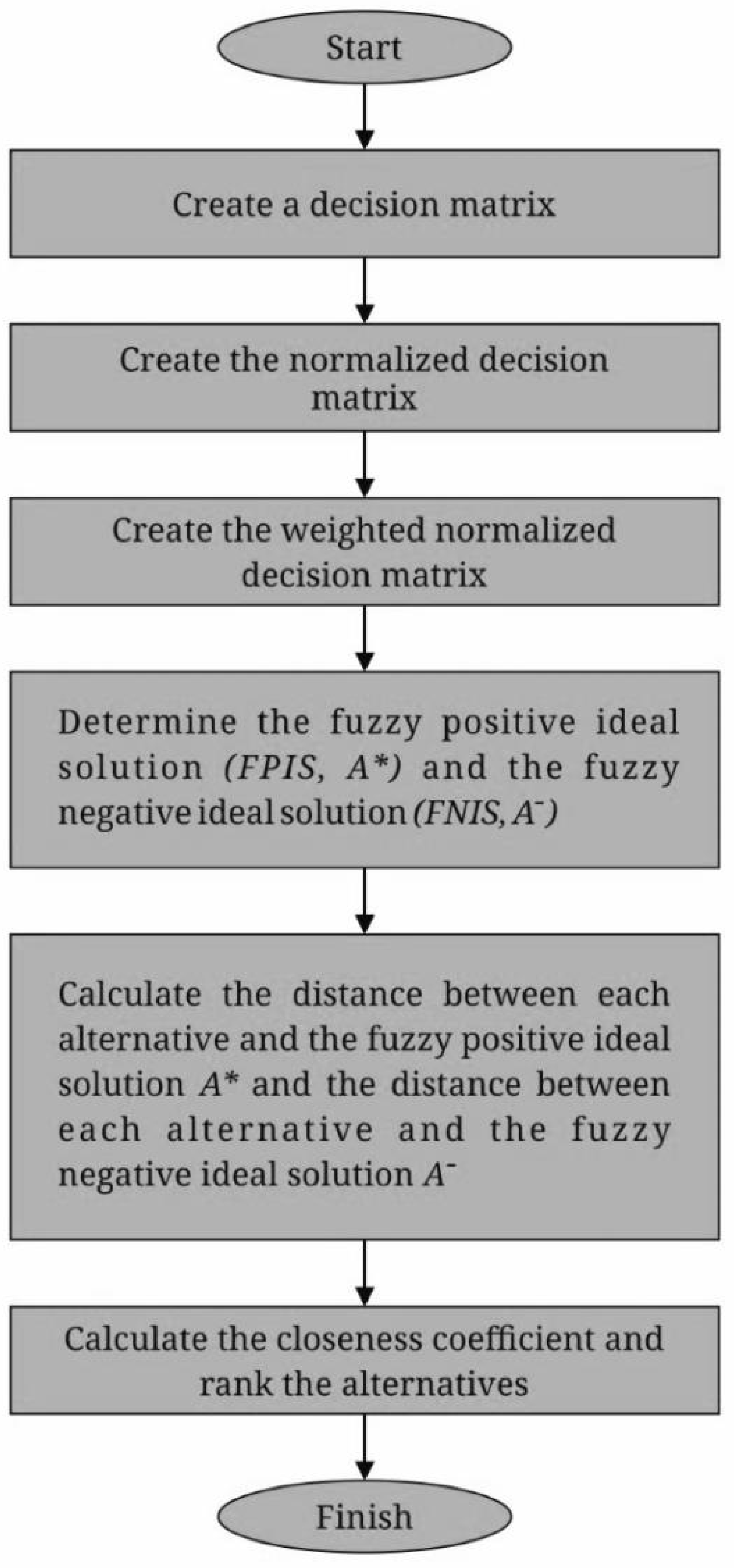
Figure 4 shows the sequential steps of the fuzzy TOPSIS method.
- (1)
Step 1: Create a decision matrix.
In this research, six criteria and eight alternatives are consistently rated using the Fuzzy TOPSIS procedure. In classic multiple-criteria decision-making (MCDM) processes, the weights of characteristics illustrate correlative significance in the decision-making process. We cannot assume that each and every evaluation criterion is equally important because evaluating criteria includes a variety of perspectives and interpretations [
29]. Subjective and objective strategies to weighing are the two types of weighing methods. Weight values are primarily generated using subjective strategies predicated on decision makers’ choices or decisions. A decision matrix is a set of values in columns and rows that is used to clearly compare different solutions through weighing parameters according to their importance.
Table 1 below summarizes the criterion form as well as weight allocated to every set of criteria. The type represents the category of different criteria. The researchers used the standard fuzzy scale (that can be seen in
Table 2) as well as Equations (1)–(10) to collect and analyze the data. The strategies are evaluated using a variety of criteria, and the results of the decision matrix are demonstrated in the following table. The arithmetic mean of all 25 decision makers’ opinions is provided in
Table 3’s preference matrix.
The letters L, M, or U are used to demonstrate a triangular fuzzy number (TFN). The indicators L, M, as well as U, respectively, represent the least preferred, most preferred, and highest preferred significance. The fuzzy scale used in the model is shown in
Table 2.
The alternatives are assessed in aspects of different criteria, as well as the decision matrix consequences demonstrated below in
Table 3. It should be noted that if more than one expert participates in the estimation, the matrix below actually reflects the arithmetic average of all specialists.
- (2)
Step 2: Make a normalized decision matrix.
A normalized decision matrix could be computed using the following relevance predicated on the positive as well as negative ideal options:
The normalized decision matrix is presented in the following
Table 4.
- (3)
Step 3: Make a weighted normalized decision matrix.
The weighted normalized decision matrix could be computed by multiplying the criteria weights in the normalized fuzzy decision problem by the following equations, taking into account the distinct weights of every criterion.
where
signifies weight of criterion
.
The weighted normalized decision matrix can be seen in
Table 5 below.
- (4)
Step 4: Control the fuzzy positive ideal solution (FPIS, A*) as well as the fuzzy negative ideal solution (). The FPIS and the FNIS of the alternatives can be defined as follows:
The alternative solutions’ FPIS and FNIS could be demarcated as presented below: Where is the highest amount of i for all the alternatives, and is the lowest amount of i for all the alternatives options. B and C signify the positive as well as negative ideal solutions, correspondingly.
The positive as well as negative ideal solutions are presented in the following
Table 6.
- (5)
Step 5: Determine the difference in range among each alternative and the fuzzy positive ideal alternative solution , and the range among every alternative and the fuzzy negative ideal solution .
The range among every alternative and FPIS as well as among every alternative and FNIS is calculated by using the following:
d is the range among two fuzzy figures, when assumed two triangular fuzzy numbers (
) and (
), e distance among the two can be estimated as follows:
Note that and are crisp numbers.
The range from positive as well as negative ideal solutions is shown in the following
Table 7.
- (6)
Step 6: Determine the closeness coefficient as well as rating the options.
Every alternative’s closeness coefficient can be determined as described in the following:
The best option is nearest to the FPIS as well as farthest away from the FNIS. The following
Table 8 shows the closeness coefficient and the priority order of every alternative solution.
The graph below depicts the closeness coefficient of every alternative solution.
According to the research results in
Table 8 and
Figure 5, one of most significant IT risk factors is alternative A1, which really is Technology, followed by Strategic, Financial, Policy and Procedures, Environmental, Operational, Vendors, and People.