Area-Time Efficient Hardware Architecture for CRYSTALS-Kyber
Abstract
1. Introduction
- We introduce a DDF-based NTT architecture designed for Kyber. Specifically, the coefficients of the input polynomial are grouped into odd and even groups to increase the speed of the NTT operation.
- We deploy the proposed DDF-based NTT in the key generation, encryption, and decryption architectures of Kyber to accelerate these operations.
- We introduce a new architecture design for the main modules used in Kyber such as key generation, encryption, decryption, polynomial multiplication, compression, decompression, and modulo reduction in detail.
- We synthesize and implement the proposed Kyber architecture using Xilinx Vivado targeted for a Virtex-7 FPGA board. The implementation results show that the proposed Kyber architecture outperforms its predecessors in terms of area-time efficiency.
2. CRYSTALS-Kyber Algorithms
- KeyGen(): Key generation creates a public key used in the encryption process and a secret key used in the decryption processes. Noise vectors s and e are sampled from a centered binomial distribution. The public matrix is sampled from a rejection sampler. The public key and private key are obtained from formulas and , where .
- Enc(): Encryption constructs ciphertexts from the input message m, public key , and random coins . is sampled from a uniform distribution, and r, e, are obtained from a binomial sampler. Ciphertext c is computed as , where and .
- Dec(): Decryption recovers the original message m from ciphertext c using secret key . The value of m is calculated as , where u and v are obtained from c.
3. Proposed Area-Time Efficient Hardware Architecture for Kyber
3.1. Proposed Dual-Path Delay Feedback NTT Architecture for Kyber
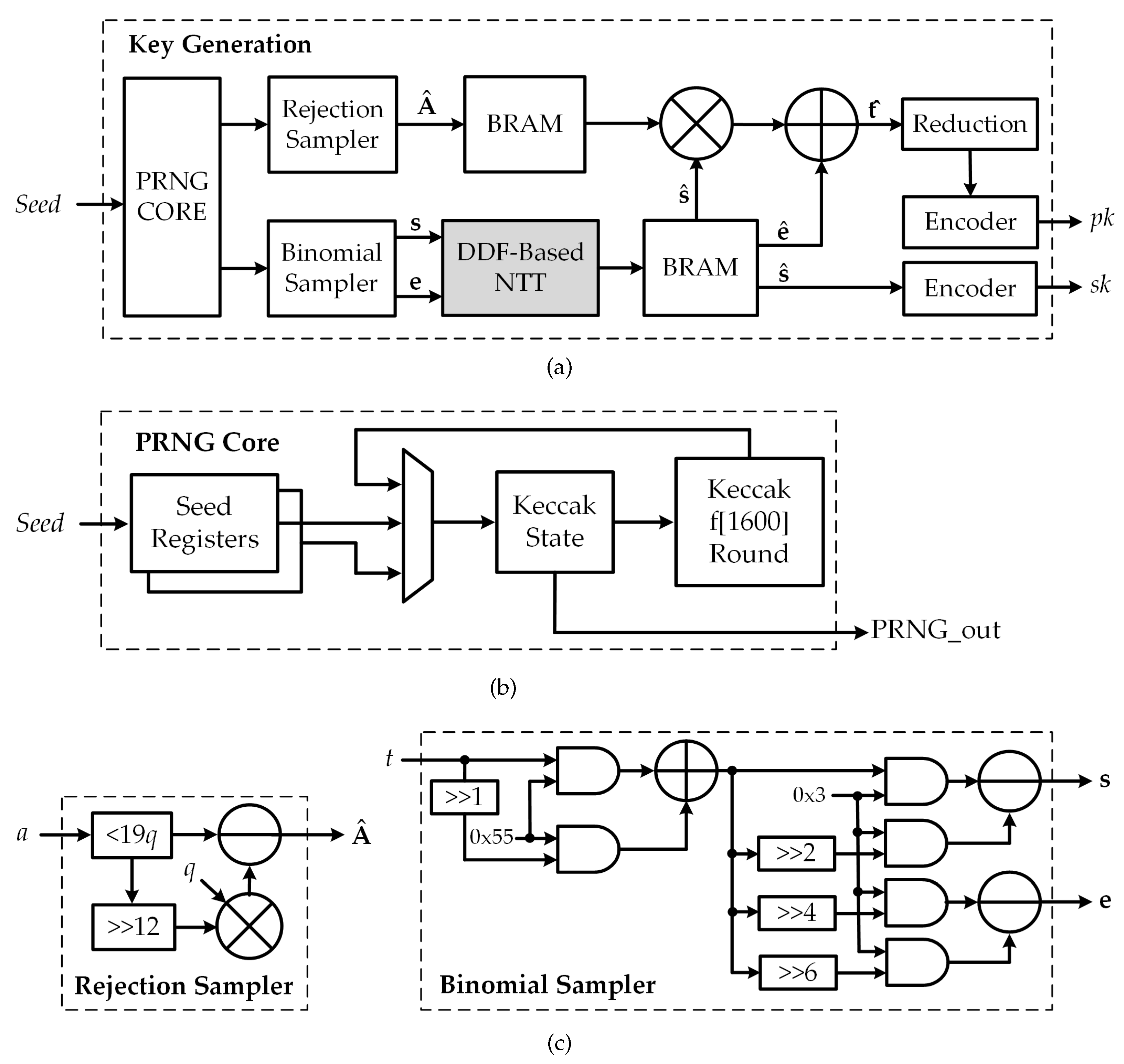
3.2. Proposed Kyber Key Generation Architecture
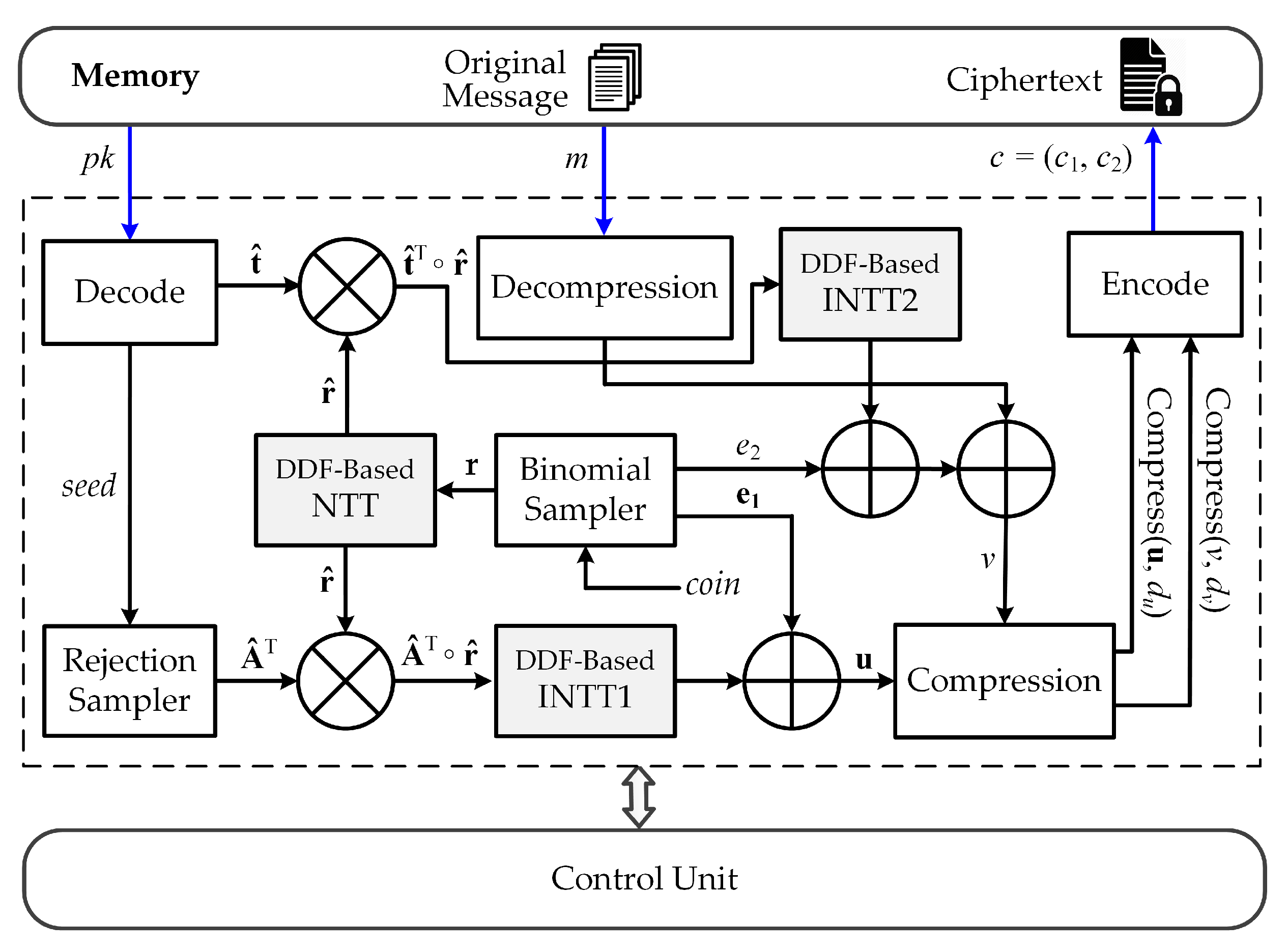
3.3. Proposed Kyber Encryption Architecture
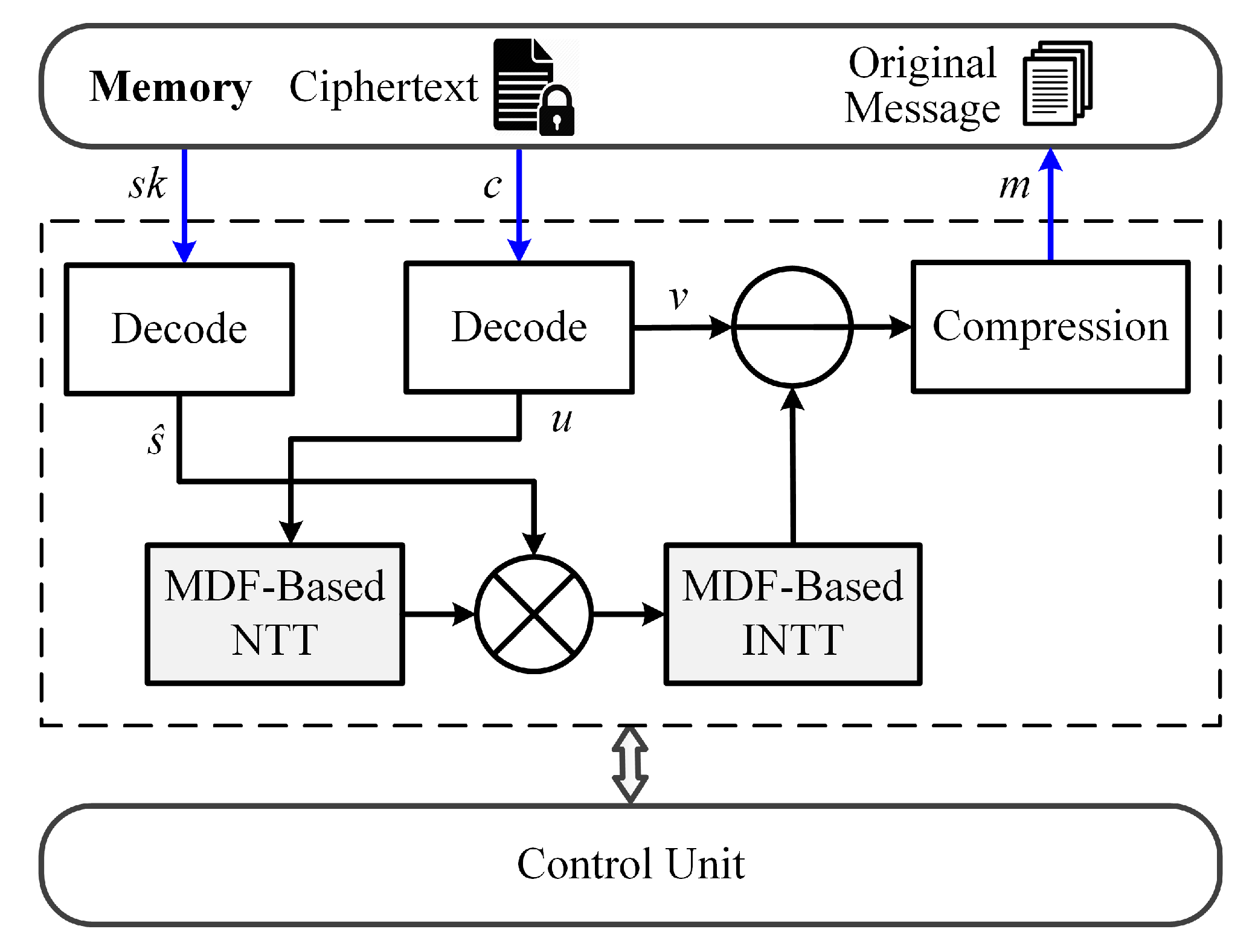
3.4. Proposed Decryption Architecture Design
4. Implementation Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Nejatollahi, H.; Dutt, N.; Ray, S.; Regazzoni, F.; Banerjee, I.; Cammarota, R. Post-Quantum Lattice-Based Cryptography Implementations: A Survey. ACM Comput. Surv. 2019, 51, 1–41. [Google Scholar] [CrossRef]
- Nguyen Tan, T.; Lee, H. High-Performance Ring-LWE Cryptography Scheme for Biometric Data Security. IEIE Trans. Smart Process. Comput. 2018, 7, 97106. [Google Scholar] [CrossRef]
- Bos, J.W.; Costello, C.; Naehrig, M.; Stebila, D. Post-Quantum Key Exchange for the TLS Protocol from the Ring Learning with Errors Problem. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–20 May 2015; pp. 553–570. [Google Scholar] [CrossRef]
- Moody, D.; Alagic, G.; Apon, D.; Cooper, D.; Dang, Q.; Kelsey, J.; Liu, Y.; Miller, C.; Peralta, R.; Perlner, R.; et al. Status Report on the Second Round of the NIST Post-Quantum Cryptography Standardization Process. In Proceedings of the NIST Interagency/Internal Report (NISTIR), National Institute of Standards and Technology, Gaithersburg, MD, USA, 22 July 2020. [Google Scholar] [CrossRef]
- Duong-Ngoc, P.; Nguyen Tan, T.; Lee, H. Efficient NewHope Cryptography Based Facial Security System on a GPU. IEEE Access 2020, 8, 108158–108168. [Google Scholar] [CrossRef]
- Moody, D. Post Quantum Cryptography Standardization: Announcement and outline of NIST’s Call for Submissions. In Proceedings of the PQCrypto 2016, Fukuoka, Japan, 24–26 February 2016; Available online: https://csrc.nist.gov/Presentations/2016/Announcement-and-outline-of-NIST-s-Call-for-Submis (accessed on 27 March 2022).
- Avanzi, R.; Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehle, D. CRYSTALS-Kyber Algorithm Specifications and Supporting Documentation. Available online: https://pq-crystals.org/kyber/data/kyber-specification-round3-20210131.pdf (accessed on 27 March 2022).
- Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehle, D. CRYSTALS-Kyber: A CCA-Secure Module-Lattice-Based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar] [CrossRef]
- Gupta, N.; Jati, A.; Chauhan, A.K.; Chattopadhyay, A. PQC Acceleration Using GPUs: FrodoKEM, NewHope, and Kyber. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 575–586. [Google Scholar] [CrossRef]
- Nguyen, D.T.; Dang, V.B.; Gaj, K. A High-Level Synthesis Approach to the Software/Hardware Codesign of NTT-Based Post-Quantum Cryptography Algorithms. In Proceedings of the 2019 International Conference on Field-Programmable Technology (ICFPT), Tianjin, China, 9–13 December 2019; pp. 371–374. [Google Scholar] [CrossRef]
- Roy, S.S.; Basso, A. High-Speed Instruction-Set Coprocessor for Lattice-Based Key Encapsulation Mechanism: Saber in Hardware. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2020, 4, 443–466. [Google Scholar] [CrossRef]
- Huang, Y.; Huang, M.; Lei, Z.; Wu, J. A Pure Hardware Implementation of CRYSTALS-KYBER PQC Algorithm through Resource Reuse. IEICE Electron. Express 2020, 17, 20200234. [Google Scholar] [CrossRef]
- Bisheh-Niasar, M.; Azarderakhsh, R.; Mozaffari-Kermani, M. Instruction-Set Accelerated Implementation of CRYSTALS-Kyber. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 4648–4659. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Nguyen, T.T.B.; Lee, H. An Analysis of Hardware Design of MLWE-Based Public-Key Encryption and Key-Establishment Algorithms. Electronics 2022, 11, 891. [Google Scholar] [CrossRef]
- He, S.; Torkelson, M. Designing Pipeline FFT Processor for OFDM (De)modulation. In Proceedings of the 1998 URSI International Symposium on Signals, Systems, and Electronics, Pisa, Italy, 2 October 1998; pp. 257–262. [Google Scholar] [CrossRef]
- Nguyen, T.T.B.; Lee, H. High-throughput low-complexity mixed-radix FFT processor using a dual-path shared complex constant multiplier. J. Semicond. Technol. Sci. 2017, 17, 101–109. [Google Scholar] [CrossRef][Green Version]
- Barrett, P. Implementing the Rivest Shamir and Adleman Public Key Encryption Algorithm on a Standard Digital Signal Processor. Adv. Cryptol.–CRYPTO’86 1987, 263, 311–323. [Google Scholar]
- Montgomery, P.L. Modular Multiplication without Trial Division. Math. Comput. 1985, 44, 519–521. [Google Scholar] [CrossRef]
- Bertoni, G.; Daemen, J.; Peeters, M.; Assche, G.V. Keccak and the SHA-3 Standardization. NIST, Gaithersburg, MD, USA, 6 February 2013. Available online: https://csrc.nist.gov/csrc/media/projects/hash-functions/documents/keccak-slides-at-nist.pdf (accessed on 27 March 2022).
- FIPS PUB 202–SHA3 Standard; Permutation-Based Hash and Extendable-Output Function. Federal Information Processing Standards Publication: Gaithersburg, MD, USA, August 2015. [CrossRef]
- Elkhatib, R.; Azarderakhsh, R.; Mozaffari-Kermani, M. Highly Optimized Montgomery Multiplier for SIKE Primes on FPGA. In Proceedings of the 2020 IEEE 27th Symposium on Computer Arithmetic (ARITH), Portland, OR, USA, 7–10 June 2020; pp. 64–71. [Google Scholar] [CrossRef]




| Algorithm | NIST Security Level | Parameters | ||
|---|---|---|---|---|
| Kyber-512 | 1 | 256 | 2 | 3329 |
| Kyber-768 | 3 | 256 | 3 | 3329 |
| Kyber-1024 | 5 | 256 | 4 | 3329 |
| Parameters | This Work |
|---|---|
| Devices | Virtex-7 |
| LUTs | 22K |
| FFs | 12K |
| DSPs | 21 |
| BRAMs | 4.5 |
| Frequency (MHz) | 217 |
| Time (μs) | 39 |
| Area × Time (LUTs × s) | 0.86 |
| Parameters | This Work | [14] | [12] | [13] | [22] |
|---|---|---|---|---|---|
| Devices | Virtex-7 | Virtex-7 | UltraScale+ | Virtex-7 | Virtex-7 |
| Protocol | Kyber-1024 | Kyber-1024 | Kyber-1024 | Kyber-1024 | SIKEp751 |
| LUTs | 29,718 | 16,000 | 23,868 | 252,107 | 20,207 |
| FFs | 22,556 | 6000 | 9805 | 335,125 | 39,339 |
| DSPs | 71 | 12 | 0 | 584 | 452 |
| BRAMs | 11 | 17 | 2 | 402.5 | 41.5 |
| Frequency (MHz) | 226 | 156 | 150 | 192 | 233 |
| Time (μs) | 57.5 | 205 | 153 | 1264 | 25,500 |
| Area × Time (LUTs × s) | 1.68 | 3.28 | 3.62 | 318.66 | 515.28 |
| Norm. Area × Time | 1.00 | 1.95 | 2.15 | 189.68 | 306.71 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nguyen, T.T.; Kim, S.; Eom, Y.; Lee, H. Area-Time Efficient Hardware Architecture for CRYSTALS-Kyber. Appl. Sci. 2022, 12, 5305. https://doi.org/10.3390/app12115305
Nguyen TT, Kim S, Eom Y, Lee H. Area-Time Efficient Hardware Architecture for CRYSTALS-Kyber. Applied Sciences. 2022; 12(11):5305. https://doi.org/10.3390/app12115305
Chicago/Turabian StyleNguyen, Tuy Tan, Sungjae Kim, Yongjun Eom, and Hanho Lee. 2022. "Area-Time Efficient Hardware Architecture for CRYSTALS-Kyber" Applied Sciences 12, no. 11: 5305. https://doi.org/10.3390/app12115305
APA StyleNguyen, T. T., Kim, S., Eom, Y., & Lee, H. (2022). Area-Time Efficient Hardware Architecture for CRYSTALS-Kyber. Applied Sciences, 12(11), 5305. https://doi.org/10.3390/app12115305







