Exploring the Relationship between Internal Information Security, Response Cost, and Security Intention in Container Shipping
Abstract
1. Introduction
2. Theoretical Model and Hypotheses
2.1. Conceptual Basis of Information Security Marketing
2.2. Information Security Marketing and Information Security Intention
2.3. Information Security Marketing, and Response Cost and Information Security Intention
2.4. The Moderating Effect of Information Security Awareness
2.5. The Moderating Effect of Information Security Climate
3. Methodology
3.1. Sample Selection and Data Collection
3.2. Non-Response Bias and Common-Method Variance
3.3. Measures
3.4. Analytic Method
4. Results and Empirical Approach
4.1. Exploratory Factor Analysis
4.2. Confirmatory Factor Analysis
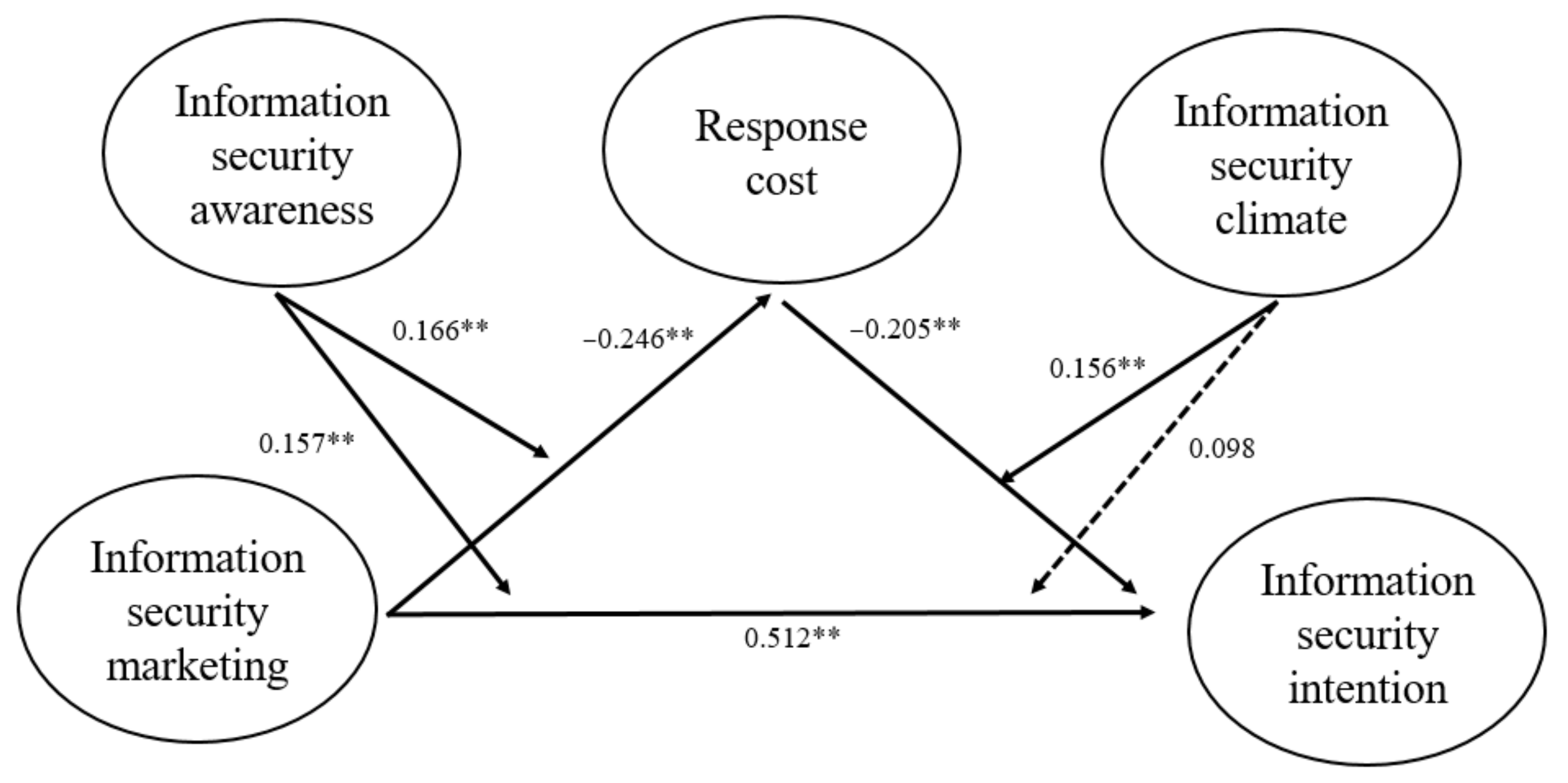
4.3. Structural Equation Modeling
4.4. Hierarchical Regression Testing
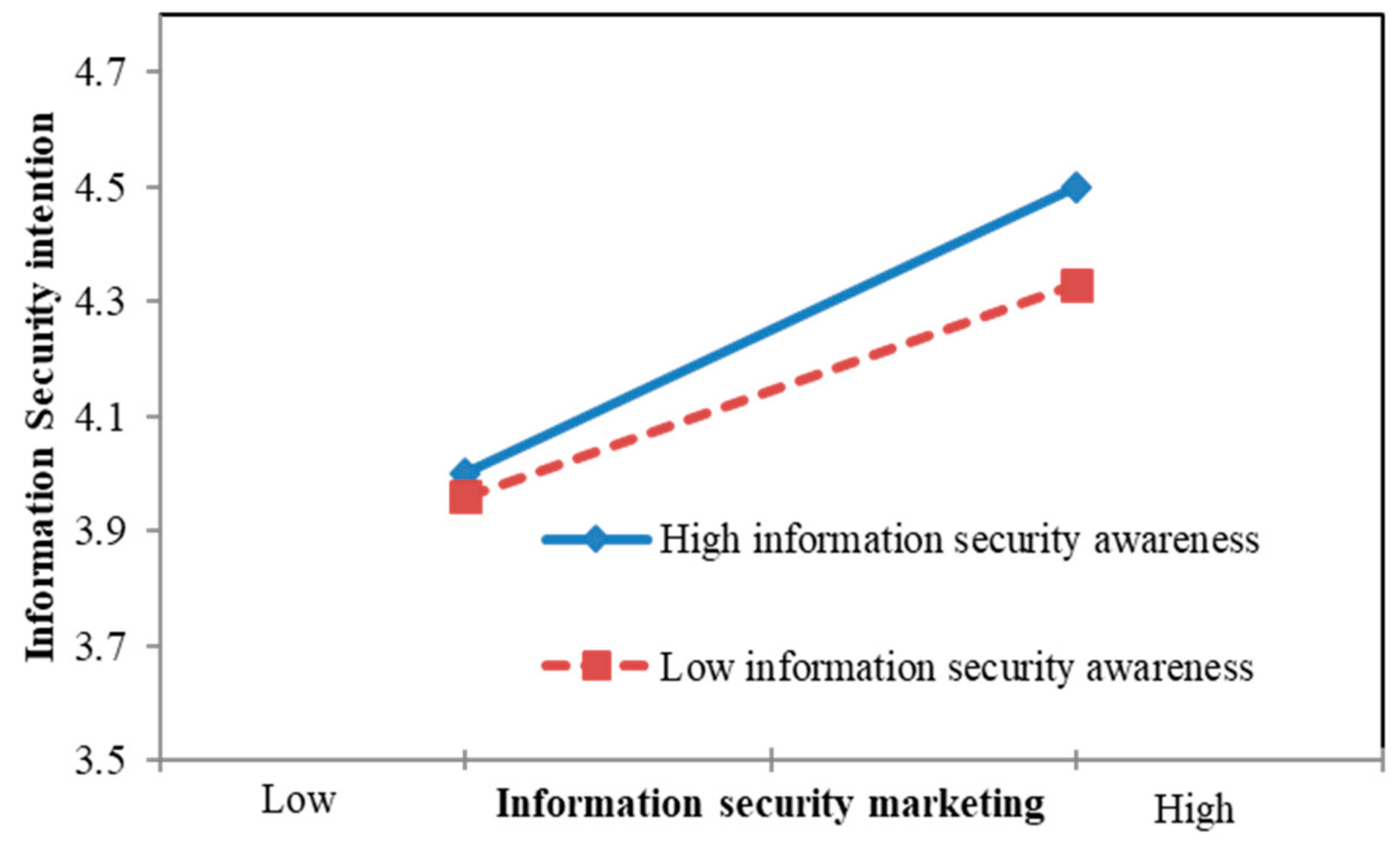
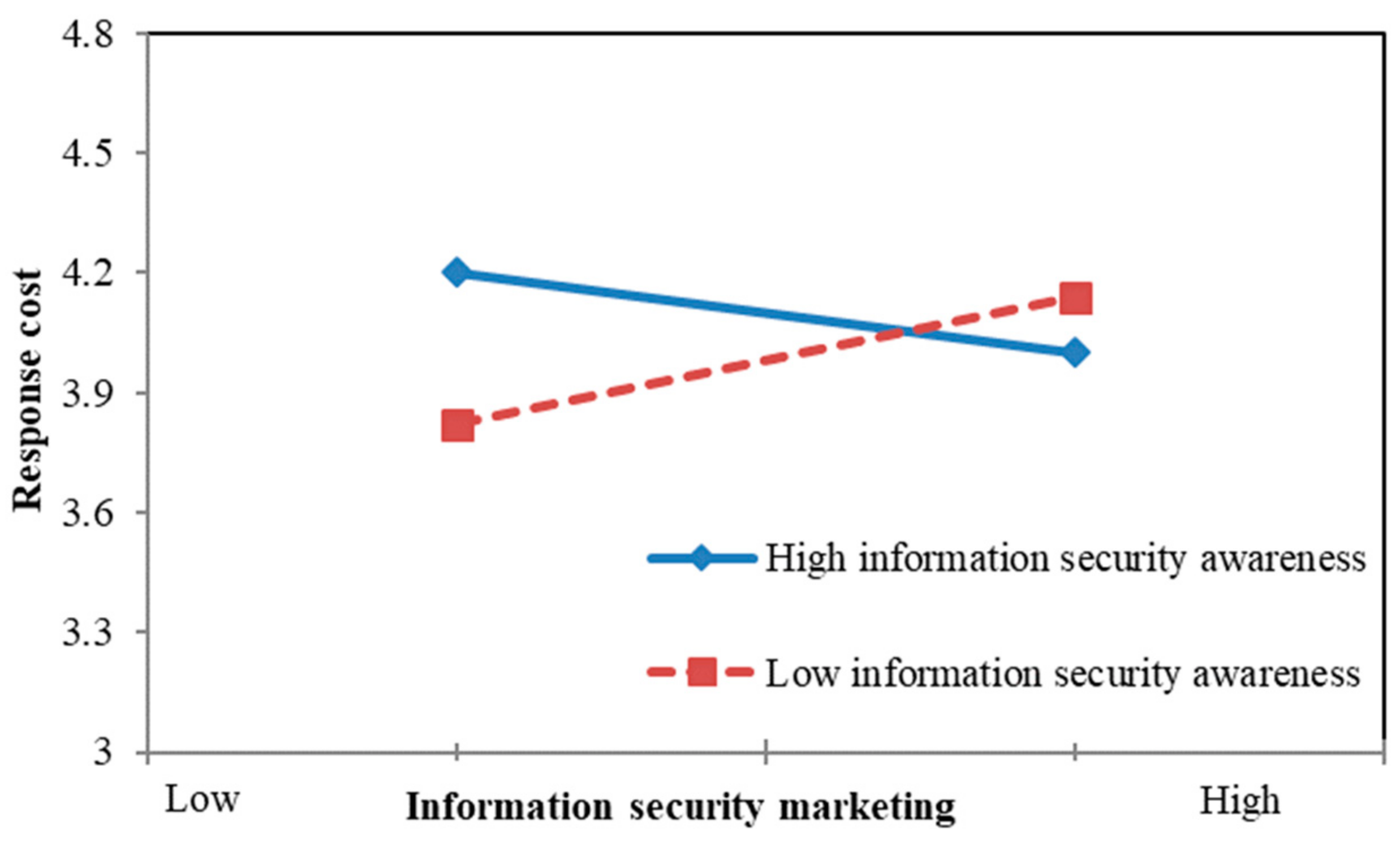
4.5. Moderated Mediating Effect Testing
5. Discussion and Implications
5.1. Discussion
5.2. Theoretical Implications
5.3. Practical Implications
5.4. Limitations and Suggestions for Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- IDC. Worldwide Semiannual Security Spending Guide. 2017. Available online: https://www.idc.com/getdoc.jsp?containerId=IDC_P33461 (accessed on 7 August 2018).
- IDG. 2018 Global State of Information Security Survey. 2018. Available online: https://zh.scribd.com/document/366302651/2018-Global-State-of-Information-Security-Survey#download&from_embed (accessed on 8 August 2018).
- Kuo, S.Z.; Lin, P.C.; Lu, C.S. The effects of dynamic capabilities, service capabilities, competitive advantage, and organizational performance in container shipping. Transp. Res. Part A 2017, 95, 356–371. [Google Scholar] [CrossRef]
- UNCTAD. Review of Maritime Transport 2018; UNCTAD/RMT/2019; UNCTAD: New York, NY, USA, 2019. [Google Scholar]
- IQPC. The Depth of This Year’s NotPetya Attack Is Now Coming to Light, and It Is Certainly No Laughing Matter—Especially for Companies’ Bottom Lines. 2017. Available online: https://www.cshub.com/attacks/news/notpetya-costs-merck-fedex-maersk-800m (accessed on 8 August 2018).
- Huang, L.; Cha, O. Examining technostress creators and role stress as potential threats to employees’ information security compliance. Comput. Hum. Behav. 2018, 81, 282–293. [Google Scholar] [CrossRef]
- Armstrong, G.; Kolter, P. Marketing: An Introduction, 14th ed.; Pearson Education: Upper Saddle River, NJ, USA, 2019. [Google Scholar]
- Ferdous, A.S.; Herington, C.; Merrilees, B. Developing an integrative model of internal and external marketing. J. Strateg. Mark. 2013, 21, 637–649. [Google Scholar] [CrossRef]
- Barry, L.L. The employee as customer. J. Retail Bank. 1981, 3, 25–28. [Google Scholar]
- Pantouvakis, A. Internal marketing and moderating role of employees: An exploratory study. Total Qual. Manag. 2012, 23, 177–195. [Google Scholar] [CrossRef]
- Rafiq, M.; Ahmed, P.K. Advances in the internal marketing concept: Definition, synthesis and extension. J. Serv. Mark. 2000, 14, 449–462. [Google Scholar] [CrossRef]
- Lu, C.S.; Kuo, S.Y.; Chiu, Y.T. Ethical leadership and ethical climate in the container shipping industry. Int. J. Shipp. Transp. Logist. 2013, 5, 591–604. [Google Scholar] [CrossRef]
- Yazdanmehr, A.; Wang, J. Employees’ information security policy compliance: A norm activation perspective. Decis. Support Syst. 2016, 92, 36–46. [Google Scholar] [CrossRef]
- Luria, G.; Yagil, D. Procedural justice, ethical climate and service outcomes in restaurants. Int. J. Hosp. Manag. 2008, 27, 276–283. [Google Scholar] [CrossRef]
- Safa, N.S.; Solms, R. An information security knowledge sharing model in organizations. Comput. Hum. Behav. 2016, 57, 442–451. [Google Scholar] [CrossRef]
- Hanus, B.; Wu, A.Y. Impact of users’ security awareness on desktop security behavior: A protection motivation theory perspective. Inf. Syst. Manag. 2016, 33, 2–16. [Google Scholar] [CrossRef]
- Adams, P.; Freitas, I.M.B.; Fontana, R. Strategic orientation, innovation performance and the moderating influence of marketing management. J. Bus. Res. 2019, 97, 129–140. [Google Scholar] [CrossRef]
- Ellram, L.M.; Murfield, M.L.U. Supply chain management in industrial marketing-relationships Matter. Ind. Mark. Manag. 2019, 79, 36–45. [Google Scholar] [CrossRef]
- Amato, F.; Moscato, V.; Picariello, A.; Sperlí, G. Diffusion Algorithms in multimedia social networks: A preliminary model. In IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 844–851. [Google Scholar]
- Chakraborty, T.; Jajodia, S.; Katz, J.; Picariello, A.; Sperli, G.; Subrahmanian, V.S. Forge: A fake online repository generation engine for cyber deception. IEEE Trans. Dependable Secur. Comput. 2021, 18, 518–533. [Google Scholar] [CrossRef]
- Hayes, A.F. Introduction to Mediation, Moderation, and Conditional Process Analysis, 2nd ed.; The Guilford Press: New York, NY, USA, 2017. [Google Scholar]
- Chen, M.; Woon, I.; Kankanhalli, A. Perceptions of information security in the workplace: Linking information security climate to compliant behavior. Int. J. Inf. Secur. Priv. 2005, 1, 18–41. [Google Scholar] [CrossRef]
- Chen, X.; Chen, L.; Wu, D. Factors that influence employees’ security policy compliance: An awareness-motivation-capability perspective. J. Comput. Inf. Syst. 2018, 58, 312–324. [Google Scholar] [CrossRef]
- Spears, J.L.; Barki, H. User participation in information systems security risk management. MIS Q. 2010, 34, 503–522. [Google Scholar] [CrossRef]
- Bansal, H.S.; Mendelson, M.B.; Sharma, B. The impact of internal marketing activities on external marketing outcomes. J. Qual. Manag. 2001, 6, 61–76. [Google Scholar] [CrossRef]
- Gyepi-Garbrah, T.F.; Asamoah, E.S. Towards a holistic internal market orientation measurement scale. J. Strateg. Mark. 2015, 23, 273–284. [Google Scholar] [CrossRef]
- Kaur, J.; Sharma, S.K. Internal marketing: Scale development and validation. J. Bus. Perspect. 2015, 19, 236–247. [Google Scholar] [CrossRef]
- Chen, Y.C.; Lin, S. Modeling internal marketing and employee loyalty: A quantitative approach. Asian Soc. Sci. 2013, 9, 99–109. [Google Scholar] [CrossRef]
- Chen, J.H.; Wu, S.I. The impact of customer relationship management and internal marketing on business performance: A comparison of lodging industries. Total Qual. Manag. 2016, 27, 17–33. [Google Scholar] [CrossRef]
- Huang, Y.T.; Rundle-Thiele, S. A holistic management tool for measuring internal marketing activities. J. Serv. Mark. 2015, 29, 571–584. [Google Scholar] [CrossRef]
- Ferdous, A.S.; Polonsky, M. The impact of frontline employees’ perceptions of internal marketing on employee outcomes. J. Strateg. Mark. 2014, 22, 300–315. [Google Scholar] [CrossRef]
- Cătălin, C.M.; Andreea, P.; Adina, C. A Holistic approach on internal marketing implementation. Bus. Manag. Dyn. 2014, 3, 9–17. [Google Scholar] [CrossRef]
- Menard, P.; Bott, G.J.; Crossler, R.E. User motivations in protecting information security: Protection motivation theory versus self-determination theory. J. Manag. Inf. Syst. 2017, 34, 1203–1230. [Google Scholar] [CrossRef]
- Chen, X.; Wu, D.; Chen, L.; Teng, J.K.L. Sanction severity and employees’ information security policy compliance: Investigating mediating, moderating, and control variables. Inf. Manag. 2018, 55, 1049–1060. [Google Scholar] [CrossRef]
- Moody, G.D.; Siponen, M.; Pahnila, S. Toward a unified model of information security policy compliance. MIS Q. 2018, 42, 185–311. [Google Scholar] [CrossRef]
- Yoon, C.; Hwang, Y.W.; Kim, R. Exploring factors that influence students’ behaviors in information security. J. Inf. Syst. Educ. 2012, 23, 407–415. [Google Scholar]
- Connolly, L.Y.; Lang, M.; Gathegi, J.; Tygar, D.J. Organizational culture, procedural countermeasures, and employee security behavior: A qualitative study. Inf. Comput. Secur. 2017, 25, 118–136. [Google Scholar] [CrossRef]
- Ortiz, J.; Chil, W.H.; Tsai, F.S. Information privacy, consumer alienation, and lurking behavior in social networking sites. Comput. Hum. Behav. 2018, 80, 143–157. [Google Scholar] [CrossRef]
- Goo, J.; Yim, M.S.; Kim, D.J. A path to successful management of employee security compliance: An empirical study of information security climate. IEEE Trans. Prof. Commun. 2014, 57, 286–308. [Google Scholar] [CrossRef]
- Armstrong, J.S.; Overton, T.S. Estimating nonresponse bias in mail surveys. J. Mark. Res. 1977, 14, 396–402. [Google Scholar] [CrossRef]
- Fuller, C.M.; Simmering, M.J.; Atinc, G.; Atinc, Y.; Babin, B.J. Common methods variance detection in business research. J. Bus. Res. 2016, 69, 3192–3198. [Google Scholar] [CrossRef]
- Iacobucci, D.; Churchill, G.A. Marketing Research: Methodological Foundation; The Dryden Press: New York, NY, USA, 2010. [Google Scholar]
- Chen, S.H.; Liu, P.Y. Effects of internal marketing, organizational commitment, job involvement and job satisfaction on work performance: A study of the elderly care institutions in Taiwan. Mark. Rev. 2012, 9, 277–302. [Google Scholar]
- Humaidi, N.; Balakrishnan, V. The moderating effect of working experience on health information system security policies compliance behaviour. Malays. J. Comput. Sci. 2015, 28, 70–92. [Google Scholar]
- Lin, C.C. Evaluating the effects of safety marketing on logistics operation in Taiwan free trade port zones. Marit. Q. 2016, 25, 1–30. [Google Scholar]
- Narteh, B.; Odoom, R. Does internal marketing influence employee loyalty? Evidence from the ghanaian banking industry. Serv. Mark. Q. 2015, 36, 112–135. [Google Scholar] [CrossRef]
- Vance, A.; Siponen, M.; Pahnila, S. Motivating IS security compliance: Insights from habit and protection motivation theory. Inf. Manag. 2012, 49, 190–198. [Google Scholar] [CrossRef]
- Siponen, M.; Mahmood, M.A.; Pahnila, S. Employees’ adherence to information security policies: An exploratory field study. Inf. Manag. 2014, 51, 217–224. [Google Scholar] [CrossRef]
- Hair, J.F., Jr.; Black, W.C.; Babin, B.J.; Anderson, R.E. Multivariate Data Analysis, 7th ed.; Pearson: Upper Saddle River, NJ, USA, 2013. [Google Scholar]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with un-observable and measurement Error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Lu, C.S.; Kuo, S.Y. The effects of port employees’ perceptions of tacit knowledge and transaction cost on knowledge transfer. Int. J. Shipp. Transp. Logist. 2014, 6, 46–68. [Google Scholar] [CrossRef]
- Lu, C.S.; Kuo, S.Y. The effects of job stress on self-reported safety behavior in container terminal operations: The moderating role of emotional intelligence. Transp. Res. Part F 2016, 37, 10–26. [Google Scholar] [CrossRef]
- Jeevan, J.; Othman, M.R.; Hasan, Z.R.A.; Pham, T.Q.M.; Park, G.K. Exploring the development of Malaysian seaports as a hub for tourism activities. Marit. Bus. Rev. 2019, 4, 310–327. [Google Scholar] [CrossRef]
- Martin, S.L.; Javalgi, R.G.; Cavusgil, E. Marketing capabilities, positional advantage, and performance of born global firms: Contingent effect of ambidextrous innovation. Int. Bus. Rev. 2017, 23, 527–543. [Google Scholar] [CrossRef]
- Alaghehband, F.K.; Rivard, S.; Wu, S.; Goyette, S. An assessment of the use of transaction cost theory in information technology outsourcing. J. Strateg. Inf. Syst. 2011, 20, 125–138. [Google Scholar] [CrossRef]
- Chen, Y.; Ramamurthy, K.; Wen, K.W. Organizations’ information security policy compliance: Stick or carrot approach? J. Manag. Inf. Syst. 2012, 29, 157–188. [Google Scholar] [CrossRef]
- Lee, J.S.; Keil, M.; Shalev, E. Seeing the trees or the forest? The effect of IT project managers’ mental construal on IT project risk management activities. Inf. Syst. Res. 2019, 30, 1015–1072. [Google Scholar] [CrossRef]
- Wang, M.C.; Yip, T.L. Influence of transportation infrastructure on the relationship between institutions and economic performance. Marit. Bus. Rev. 2019, 4, 395–412. [Google Scholar] [CrossRef]


| Number of Respondents | Percentage of Respondents | |
|---|---|---|
| Job title | ||
| Vice president or higher | 14 | 4.9 |
| Manager | 77 | 27.0 |
| Director | 22 | 25.3 |
| General employees | 45 | 15.8 |
| IT operators | 77 | 27.0 |
| Number of employees | ||
| 50 or fewer | 74 | 26.0 |
| 51–100 | 37 | 13.0 |
| 101–200 | 83 | 29.1 |
| 201–300 | 76 | 26.7 |
| 300 or more | 15 | 5.3 |
| Work experiences (years) | ||
| 5 years or fewer | 17 | 6.0 |
| 6–10 | 38 | 13.3 |
| 11–15 | 47 | 16.5 |
| 16–20 | 90 | 31.6 |
| 20 or more | 93 | 32.6 |
| Tenure in current company (years) | ||
| 5 or fewer | 31 | 10.9 |
| 6–10 | 50 | 17.5 |
| 11–15 | 84 | 29.5 |
| 20 or more | 120 | 42.1 |
| Length of business operations (years) | ||
| 5 or fewer | 2 | 0.7 |
| 6–10 | 10 | 3.5 |
| 11–20 | 33 | 11.6 |
| 21–30 | 96 | 33.7 |
| 30 or more | 144 | 50.5 |
| Ownership pattern | ||
| Local firm | 197 | 69.1 |
| Foreign-owned firm | 40 | 14.0 |
| Foreign local firm | 48 | 16.8 |
| Security training participation (number of training courses attended) | ||
| Never | 65 | 22.8 |
| 1 | 95 | 33.3 |
| 2 | 57 | 20.0 |
| 3 | 43 | 15.1 |
| 4 | 11 | 3.9 |
| 5 or above | 14 | 4.9 |
| Security experience | ||
| Phishing | 136 | 22.1 |
| Malware | 103 | 16.7 |
| Ransomware | 95 | 15.4 |
| Spam | 203 | 32.9 |
| Outdated security | 49 | 7.9 |
| None | 31 | 5.0 |
| Items | Mean | S.D. | F1 | F2 | F3 | F4 | F5 |
|---|---|---|---|---|---|---|---|
| Information security marketing | |||||||
| S7 Information security threats are always alerted to all employees through messages or emails in my organization. | 4.13 | 0.72 | 0.77 | ||||
| S4 My organization always provides specific training on information security regularly. | 4.17 | 0.78 | 0.75 | ||||
| S3 My organization takes information security into account when running the business. | 4.31 | 0.77 | 0.73 | ||||
| S6 Any changes related to information security policies are always alerted to all employees through messages or emails in my organization. | 4.18 | 0.68 | 0.70 | ||||
| S5 My organization encourages me to attend information security campaigns. | 4.14 | 0.69 | 0.69 | ||||
| S8 My company communicates clear information on security policies to employees. | 4.04 | 0.74 | 0.68 | ||||
| S1 My organization always seeks improvements related to information security policies. | 4.20 | 0.69 | 0.66 | ||||
| S2 My organization is confident that compliance with information security policies is important. | 4.29 | 0.74 | 0.66 | ||||
| Information security climate | |||||||
| C5 My supervisor discusses information security issues with me and my colleagues. | 3.97 | 0.86 | 0.88 | ||||
| C1 I believe that other employees comply with the information security policies of my organization. | 4.09 | 0.84 | 0.85 | ||||
| C2 The majority of other employees take the information security of my organization into account to help protect the organization’s information systems. | 4.12 | 0.78 | 0.85 | ||||
| C4 Employees discuss information security threats with each other in my organization. | 3.86 | 0.84 | 0.79 | ||||
| C3 My supervisor and colleagues support me when I adopt proper information security practices. | 3.77 | 0.90 | 0.79 | ||||
| Information security intention | |||||||
| T5 When I access the information system, I consider the organization’s information security policies. | 4.38 | 0.70 | 0.80 | ||||
| T3 I remind others to take care with information security issues. | 4.22 | 0.81 | 0.78 | ||||
| T4 I assist others in complying with information security policies. | 4.35 | 0.69 | 0.77 | ||||
| T1 I am likely to follow information security policies. | 4.34 | 0.73 | 0.77 | ||||
| T2 I consider information security practices when performing my daily work. | 4.34 | 0.68 | 0.76 | ||||
| Security response cost | |||||||
| R4 Having to learn how to adopt information security behavior would result in a significant loss of my work time. | 2.84 | 0.93 | 0.87 | ||||
| R3 Complying with information security policies is costly for me (e.g., learning cost or time cost). | 2.95 | 0.97 | 0.87 | ||||
| R2 Complying with information security procedures inconveniences my work. | 2.99 | 0.95 | 0.82 | ||||
| R1 Complying with information security procedures is time-consuming. | 3.01 | 0.95 | 0.78 | ||||
| Information security awareness | |||||||
| A3 I believe that violations of the organization’s information security policies would cause serious damage to the organization. | 4.12 | 0.87 | 0.87 | ||||
| A4 I am aware that if I do not adopt information security behavior adequately, it will cause security incidents. | 4.02 | 0.85 | 0.85 | ||||
| A2 An information security breach in my organization would be a serious problem for my organization. | 3.93 | 0.88 | 0.84 | ||||
| A1 I understand the potential security threats, risks, and negative consequences. | 3.89 | 0.85 | 0.83 | ||||
| Eigenvalues | 4.40 | 3.60 | 3.36 | 3.05 | 2.96 | ||
| Cumulative percentage variance (%) | 16.93 | 30.76 | 43.77 | 55.39 | 66.77 |
| Latent Variable Items | Standardized Loading | Standard Error a | Critical Ratio b | R2 | Mean | S.D. | Item-Total Correlation | Cronbach’s Alpha |
|---|---|---|---|---|---|---|---|---|
| ISM | 4.18 | 0.53 | 0.62–0.67 | 0.88 | ||||
| SM1 | 0.68 | 0.10 | 9.63 | 0.46 | ||||
| SM2 | 0.70 | 0.10 | 10.22 | 0.49 | ||||
| SM3 | 0.72 | 0.11 | 10.52 | 0.52 | ||||
| SM4 | 0.69 | 0.11 | 10.16 | 0.48 | ||||
| SM5 | 0.68 | 0.10 | 9.98 | 0.46 | ||||
| SM6 | 0.66 | 0.09 | 9.77 | 0.44 | ||||
| SM7 | 0.72 | 0.10 | 10.44 | 0.51 | ||||
| SM8 | 0.80 | - c | - c | 0.44 | ||||
| RSC | 2.95 | 0.99 | 0.68–0.80 | 0.88 | ||||
| RS1 | 0.71 | 0.05 | 13.57 | 0.51 | ||||
| RS2 | 0.80 | 0.05 | 16.18 | 0.64 | ||||
| RS3 | 0.83 | 0.05 | 17.04 | 0.69 | ||||
| RS4 | 0.88 | - c | - c | 0.77 | ||||
| ISI | 4.33 | 0.53 | 0.68–0.73 | 0.88 | ||||
| IT1 | 0.74 | 0.08 | 12.99 | 0.55 | ||||
| IT2 | 0.77 | 0.70 | 13.47 | 0.59 | ||||
| IT3 | 0.77 | 0.08 | 13.55 | 0.60 | ||||
| IT4 | 0.77 | 0.07 | 13.57 | 0.59 | ||||
| IT5 | 0.79 | -c | -c | 0.63 | ||||
| ISA | 3.99 | 0.74 | 0.70–0.76 | 0.87 | ||||
| IA1 | 0.76 | 0.07 | 13.43 | 0.58 | ||||
| IA2 | 0.77 | 0.07 | 13.56 | 0.59 | ||||
| IA3 | 0.84 | 0.07 | 14.90 | 0.71 | ||||
| IA4 | 0.81 | - c | - c | 0.65 | ||||
| ISC | 3.96 | 0.71 | 0.71–0.82 | 0.90 | ||||
| IC1 | 0.82 | 0.08 | 12.99 | 0.68 | ||||
| IC2 | 0.78 | 0.07 | 13.47 | 0.61 | ||||
| IC3 | 0.78 | 0.08 | 13.55 | 0.61 | ||||
| IC4 | 0.75 | 0.07 | 13.57 | 0.56 | ||||
| IC5 | 0.88 | - c | - c | 0.77 |
| Measure | AVE a | Construct Reliability b | SMC | RSC | ISI | ISA | ISC |
|---|---|---|---|---|---|---|---|
| ISM | 0.50 | 0.89 | 1 c | ||||
| RSC | 0.65 | 0.88 | −0.22 ** | 1 | |||
| ISI | 0.59 | 0.88 | 0.50 ** | −0.30 ** | 1 | ||
| ISA | 0.63 | 0.87 | 0.07 ** | −0.13 ** | 0.00 ** | 1 | |
| ISC | 0.65 | 0.90 | 0.27 ** | 0.11 | 0.12 ** | 0.21 ** | 1 |
| RSC Model 1 | RSC Model 2 | RSC Model 3 | ISI Model 4 | ISI Model 5 | ISI Model 6 | ISI Model 7 | ISI Model 8 | |
|---|---|---|---|---|---|---|---|---|
| Control variables | ||||||||
| Sex | −0.096 | −0.098 | −0.081 | −0.060 | −0.072 | −0.053 | −0.066 | −0.063 |
| Age | 0.045 | 0.049 | 0.043 | 0.052 | 0.123 ** | 0.069 | 0.080 | 0.068 |
| Main effects | ||||||||
| ISM | −0.217 *** | −0.175 ** | 0.438 *** | 0.482 *** | 0.474 *** | 0.413 *** | ||
| RSC | −0.238 *** | −0.246 *** | −0.234 *** | −0.220 *** | ||||
| ISA | −0.116 ** | −0.101 | −0.064 | −0.049 | −0.068 | −0.061 | ||
| ISC | 0.021 | 0.013 | 0.019 | 0.027 | ||||
| Moderating effects | ||||||||
| ISM x ISA | 0.166 ** | 0.157 ** | ||||||
| ISM x ISC | 0.098 | |||||||
| RSC x ISC | 0.156 ** | |||||||
| F-value | 1.592 | 5.707 *** | 6.238 *** | 0.884 | 17.640 *** | 18.652 *** | 17.543 *** | 18.779 *** |
| Adjust R2 | 0.004 | 0.062 | 0.084 | −0.001 | 0.289 | 0.303 | 0.290 | 0.305 |
| Durbin-Watson | 0.840 | 0.877 | 0.882 | 1.696 | 1.576 | 1.602 | 1.551 | 1.642 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, H.-W.; Kuo, S.-Y.; Chen, L.-B. Exploring the Relationship between Internal Information Security, Response Cost, and Security Intention in Container Shipping. Appl. Sci. 2021, 11, 2609. https://doi.org/10.3390/app11062609
Wang H-W, Kuo S-Y, Chen L-B. Exploring the Relationship between Internal Information Security, Response Cost, and Security Intention in Container Shipping. Applied Sciences. 2021; 11(6):2609. https://doi.org/10.3390/app11062609
Chicago/Turabian StyleWang, Hsin-Wei, Szu-Yu Kuo, and Liang-Bi Chen. 2021. "Exploring the Relationship between Internal Information Security, Response Cost, and Security Intention in Container Shipping" Applied Sciences 11, no. 6: 2609. https://doi.org/10.3390/app11062609
APA StyleWang, H.-W., Kuo, S.-Y., & Chen, L.-B. (2021). Exploring the Relationship between Internal Information Security, Response Cost, and Security Intention in Container Shipping. Applied Sciences, 11(6), 2609. https://doi.org/10.3390/app11062609








