Abstract
In recent years, several hospitals have begun using health information systems to maintain electronic health records (EHRs) for each patient. Traditionally, when a patient visits a new hospital for the first time, the hospital’s help desk asks them to fill in relevant personal information on a piece of paper and verifies their identity on the spot. This patient will find that many of her personal electronic records are in many hospital’s health information systems that she visited in the past, and each EHR in these hospital’s information systems cannot be accessed or shared between these hospitals. This is inconvenient because this patient will again have to provide their personal information. This is time-consuming and not practical. Therefore, in this paper, we propose a practical and provable patient EHR fair exchange scheme for each patient. In this scheme, each patient can securely delegate the information system of a current hospital to a hospital certification authority (HCA) to apply migration evidence that can be used to transfer their EHR to another hospital. The delegated system can also establish a session key with other hospital systems for later data transmission, and each patient can protect their anonymity with the help of the HCA. Additionally, we also provide formal security proofs for forward secrecy and functional comparisons with other schemes.
1. Introduction
In recent years, many research topics have arisen to make human life more convenient. An electronic health record (EHR) is an integrated personal medical record in health information systems. Many countries implement their own health information systems to help manage each patient’s activities and keep track of their health. We can imagine a scenario in which a patient (let us call her Alice) plans to go to a new hospital and sees a doctor. In this situation, she may have to fill in her personal medical information another time when she attends a new hospital. In addition, if her doctor needs to know her medical treatment history from other hospitals, how she provides these records securely to her doctor needs to be considered. These problems are especially urgent. Our proposed scheme ensures the ease and security of data access and migration. Our approach proposes a practical and provable patient EHR fair exchange scheme with session key establishment for health information systems. Patients cannot only delegate the migration of their personal EHR to a desired hospital system from their current hospital health information system but also protect their privacy. Our mechanism provides secure data storage and the secure transfer of authorized information to a designated location. This study has two limitations. First, we assume that each patient’s EHR record is well defined and appropriate for each healthcare facility. The process of electronic health information record transmission at each hospital provider is easily done by implementing our proposed scheme for secure encrypted transmission without considering issues such as different forms or file names or a lack of formatting details. Second, each facility will transfer or link the patient’s EHR to other facilities through patient consent or under a national policy when the patient requires better care at those facilities.
Summarizing all problems, we propose a high-level practical and provable patient EHR fair exchange scheme with key agreement for health information systems. Not only could a patient delegate the health information systems of the current hospital to migrate their personal EHR to the desired hospital system, but they can also keep their privacy. Our mechanism provides data storage and the secure transfer of authorized information to designated locations. What information can be authorized is beyond the scope of this study to determine. For example, whether COVID-19 patient privacy concerning patients’ names, identities, and genetic sequences can be transmitted to different hospitals is beyond this study’s scope. The mechanism presented here could guarantee data transfer and storage safely and securely. What is more, our scheme also provides a formal security proof in a random oracle model under chosen-ciphertext security.
2. Related Works
In this section, we surveyed some articles [1,2,3,4]. In [1], the author only mentioned how EHRs are used and managed. The author also talked about the EHR format that followed the definition of HL7 [5] and that performed well-known protocols to encode each patient’s EHR from TCP/IP, MIME, HTTP(S), and SOAP.
In [2], the authors discussed several security requirements, such as EHR storage security, malicious code prevention, protected access right management, and other aspects to protect the health information system. However, they did not provide a practical scheme that would allow a patient to migrate their EHR to a health information system. We can imagine a scenario where a hospital only adopts the above simple protocols to develop its own health information system without any security mechanism. Additionally, it is not feasible for each patient to perform their own EHR exchange under this scheme.
On the other hand, in [5], the authors suggested that each patient’s health records (or files) could be portably stored on a flash disk. This idea is appealing but is currently difficult to implement. There are many security issues to be handled, including portable device security and patient medical file access rights. However, more security mechanisms are needed to solve these kinds of security issues, which are beyond the scope of this research.
In addition, various patient authentication schemes of e-health systems have been proposed [6,7,8,9,10]. In [6,7], the schemes suffered a user impersonation attack and did not offer session key establishment with a formal security proof. The authors in [8,9,10] did not provide session key establishment with a forward secrecy proof. In [11,12], the authors each proposed a framework with a patient-centric access right in a blockchain environment. However, they did not provide a practical mechanism for each patient to perform EHR migration exchange securely.
Additionally, many studies are now examining the importance of personal privacy and data authorization. For example, the prevalence of COVID-19 has made many patients reluctant to disclose information about their infection, but government healthcare units want to control the trajectory of tracking these patients. A method of providing improvements in these mechanisms is the main motivation and purpose of our study. Therefore, in this paper, we emphasize providing a secure, simple, and complete mechanism for authorizing data transfer during personal information migration and demonstrate that our approach is secure and effective in practice through a professional information security authentication model.
Hence, we summarize and list here seven kinds of security attack when a patient attempts to migrate their personal information data through a traditional authentication model:
- Replay Attack Resistance: A malicious attacker intercepts the parameters used in the mutual authentication transaction successfully. They can then forward these parameters again to impersonate one party to communicate with other parties during the mutual authentication transaction and vice versa.
- Resist User Impersonation: A malicious attacker impersonates some party by replaying the intercepted signatures or random variables to other parties engaged in the mutual authentication transaction.
- Mutual Authentication: Without mutual authentication with other e-health systems, an attacker can pretend as a fake system to let other patients register and login. Then, patient’s EHRs information cannot be stored securely in this storage location.
- Data Security Problem: An attacker intercepts the parameters, including ciphertext, successfully during the mutual authentication transaction, and they may then decrypt the intercepted ciphertext by adopting these intercepted parameters.
- Session Key Establishment with Forward Secrecy: Each party communicates a temporary symmetric key for data transmission after performing mutual authentication successfully. If the session key is easy to guess or derive by an attacker successfully without forward secrecy, then this attacker can derive the used session keys before the next mutual authentication phase.
- EHR Fair Exchange Problem: If there is packet loss or data loss during the EHR migration transaction, a patient’s EHR can be lost when they attended a desired hospital. At this time, without their personal EHR, the e-health system of this hospital can delay their medical treatment in this situation.
- Patient’s Anonymity Protection: During the EHR migration transaction, if a patient’s EHR identity information is not protected well, then it could be exposed and intercepted by an attacker. Additionally, the patient’s EHR information may be misused by an attacker further.
Our contribution is to offer an efficient provable and practical patient EHR fair exchange scheme so that each patient can migrate their personal EHR securely from one hospital to another and provides solutions to the above seven problems. We designed a secure patient EHR exchange protocol that can be integrated into the e-health information system of each hospital. The proposed scheme could also guarantee convenience, rapidity, and integrity. We constructed a high-level practical and provable patient EHR fair exchange scheme with key agreement for the health information system. A patient could not only delegate the current hospital’s health information systems to migrate their personal EHR to the desired hospital system, but also keep their privacy. Additionally, our scheme demonstrates a formal security proof with light-weight computation for both authentication parties.
3. The Proposed Scheme
Our proposed scheme contains three stages: the migration registration phase, the EHR migration phase, and the data recovery phase.
3.1. Preliminary
In this subsection, we provide some definitions in our proposed scheme.
- n: A large prime number that forms a finite primes field with an order less than n.
- l: A security parameter that defines the hashed messages’ length.
- V: The current medical organization.
- W: The patient’s desired medical organization.
- U: A patient making an authentication request with a server V in a health information system.
- S: A server that accepts the registration of the patient request, the login request, and the password modification request in the health information system of hospital V.
- : A patient’s real identity computed from social security numbers, where in the certification.
- : A registration local identity that can link the of user .
- , : Two secure hash functions that each maps with collision-resistance and outputs the same l-bits hash strings.
- : A initial password that is chosen by a server V when a patient U has remotely registered on the server for the first time.
- : A symmetric key encryption function for the party i under the symmetric key , where .
- : A symmetric key decryption function for the party i under the symmetric key , where .
- : An asymmetric key encryption function for the party i, where .
- : An asymmetric key decryption function for the party i, where .
- : A patient electronic health record (EHR) in one hospital organization, where .
- : A biometric information value that is chosen uniformly from the party i, where .
- : A patient EHR migration limitation date period.
- : A migration certification of the party i with registration and public keys for this , where .
- : A hospital certification authority (HCA) that helps the patient to generate the patient migration permission signature to another hospital or medical center in the public key infrastructure (PKI).
- : A patient-delegated EHR migration agreement document whereby the patient agrees that its own patient files can migrate from current hospital i to the desired one j, where .
3.2. The Migration Registration Phase
Before starting this phase, a patient (U) forwards to a hospital certification authority () for migration certification registration with a secure channel. After receiving this identity , the HCA keeps this link information and generates certification with for EHR migration and forwards this to the patient U.
When U performs this phase with the server V of the current hospital, U forwards a patient migration registration request to a server (V). After receiving this request, the server V forwards this request to the to help U obtain the permission signature from . V first prepares two hash functions: one is , and the other is , where and .
- First, U has prepared their biometric value and computed a random value with a random number , where . After the above is computed successfully, they forward their identity , which is computed from and encrypted via real identity cipher-text with public key and their certificate with their biometric information , to the server V. It also generates the applicant-delegated migration signature , where the signature is to be the with the registration identity , real identity , and EHR migration delegated agreement with final ciper-text . U then prepares the random number , where , and forwards these files to the server V with .
- After V receives these messages, it can check the with the above messages and forward the to the . When has received this message with , it can decrypt to obtain all parameters. First, it can fetch the random value and verify the signature with other parameters. If they are valid, it saves these files for data recovery usage. It then generates , which is . Finally, it returns () to the server V.
- V receives this message tuple, where one is () and the other is (), and it can verify the signature with the above parameters and compute . When the above messages are valid, V returns and forwards it back to the server . In addition, it also generates a signature as the receipt and finishes this phase after forwarding and . We demonstrate in the Figure 1.
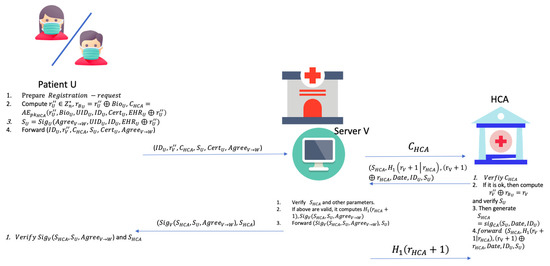 Figure 1. The migration registration phase.
Figure 1. The migration registration phase.
3.3. The EHR Migration Phase
In this phase, the server V will behave according to the delegated agreement file with the signature , and it prepares these messages as follows.
- First, it selects a random and computes . It then forms the message tuple () for the server of the desired migration hospital W. When the system of W has received this migration agreement from V, it verifies this message tuple and decrypts to obtain the challenge random number. If all signatures and parameters are valid, it generates the response random number and returns it to the server V.
- When V receives , it decrypts it with . If it is valid, it can obtain and computes the response random number for the server of hospital W. Finally, W receives from V. It also verifies the message to check if it was returned by the real V. If true, it decrypts to obtain , computes the session key , and decrypts to fetch the patient’s EHR file with the random .
- After performing mutual authentication successfully, V can also use the session key to generate an cihper-text, such as , for the rest of the data transmission of the patient U’s EHR. Figure 2 shows the scenario of this phase.
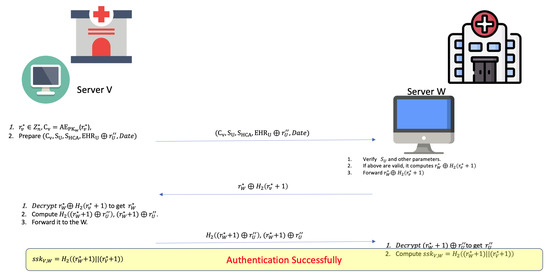 Figure 2. The EHR migration phase.
Figure 2. The EHR migration phase.
3.4. The Data Recovery Phase
In this phase, if there is some network packet loss or EHR data loss of the patient U after they have performed the EHR migration phase, then the e-health system of the hospital W cannot obtain the full U’s personal EHR, so U can ask the to deal with this situation.
- First, when a patient migrating to a hospital W that does not receive the from the server V after querying the system of hospital W, then U can ask to resolve the situation with some evidence with signatures , and . After verifying the above signatures successfully, can fetch the to the server of hospital W with .
- W can then decrypt to obtain and fetches the patient’s EHR file from the above by applying ⊕ with . At this time, this situation is solved with ’s help if needed. This phase’s scenario shows in the Figure 3.
 Figure 3. The data recovery phase.
Figure 3. The data recovery phase.
4. Security Assumptions
4.1. Secure Digital Signature
In this scheme, we define a secure digital signature. In the beginning, we have that is a signature generation function that inputs a message m with a signer’s secret key and outputs a signature . We also assert this signature function is based on the RSA factoring hard problem or the discrete logarithm problem. We can then input a signature such as with the signer’s public key into the verification function and see what the output is. If the output is 1, then we can confirm the signature is valid and signed by the signer i. In this scheme, we also assumed that the signature building block is under the RSA problem. If there is an attacker, we assume it as . If can make a forged l + 1 signature called of some user in at most lsignature queries, and this signature can pass the verification successfully with non-negligible probability , then can be used to break the RSA factoring problem. Thus,
4.2. Unforgeability
In this scheme, we define the secure digital signature scheme in the above. First, we define an attacker , whose ability is to forge a signature that can be verified successfully through the verification function with non-negligible probability . We also define a simulator that adopts ’s ability to break the underlying hard problem (such as the RSA factoring problem) in the above secure signature scheme. After is given the environment parameters , it can start the protocol simulation with . can make the signature queries to the . will also output the signature back according to the received input m from on some user i. After this simulation, if generates a forged signature , the verification result of is valid. We then have
In fact, if there is no attack that can make a forged signature pass the verification successfully with non-negligible probability , then we cannot use to solve the RSA factoring problem with non-negligible probability.
Lemma 1
(Unforgeability). First, we define , which is a secure digital signature function and equips two secure hash functions, and , which can be replaced with two random oracles functions and . In our proposed EHR scheme, we also define our proposed EHR scheme with unforgeability (Unf), which satisfies the following situations. In other words, if is and unforgeable, then
where is the maximum total experiment time, including an adversary execution time, I is an upper bound on the number of parties, at most signature oracle , and is taken over the coin flip of our EHR scheme.
4.3. Indistinguishability
We define an attacker on the experiment of our symmetric encryption/decryption functions (), which is a game controlled by the simulator . We also define two pseudo-random hash functions ( and ), which are satisfied with the property we call “indistinguishability” (), due to which the attacker can make a hash query to and on the message , which is chosen by . These functions act as real functions as our hash functions ( and ), where . The simulator also can switch this function pair to respond to each query made by during the simulation rounds of the above experiment. Finally, the simulator is given a challenge message target M chosen by the .
At this time, makes a coin flip on b. If , randomly chooses to generate the hashed value of M and return it to . Otherwise, forwards M to to ask for the hash value. ’s goal is to guess correctly the hashed value that is from or with non-negligibility probability.
Lemma 2
(Indistinguishability). In this lemma, our symmetric encryption/decryption functions satisfy the indistinguishably property if there is no attacker that can guess the hashed value from the chosen (M) with more than with negligible probability under the polynomial time bound. That is,
Therefore, we concluded that
4.4. Indistinguishable-Chosen Cipher-Text Attack (Ind-CCA)
In this scheme, we define our proposed asymmetric encryption/decryption function (), which satisfies the semantic security in the following definitions.
First, we define an attacker that can ask encryption/decryption queries in our scheme, respectively. However, the attacker can also make an encryption query to the chosen message that we define as . The attacker can then also make a decryption query to the decryption oracle, whose task is to decrypt the cipher-text sent . Next, we define , which is the simulation of our proposed scheme that can equip many different oracles, and oracles can answer back to the adversary depending on the attacker’s input messages. We also define some oracles, such as the encryption oracle with the security parameter . This encryption oracle can generate the ciphertext according to the received input , where . In addition, we also model the decryption oracle that receives the cipher-text C from the attacker and returns the final decrypted message M to the attacker . In the following, we consider two situations involving .
Phase 1: In this phase, the attacker can make the decryption and encryption queries on a chosen message (call it ). I.e., if makes an encryption query on the input message , then returns to . At this time, can also make the decryption query on cipher-text , and the simulator will then forward this to the decryption oracle and return the final message back to the . Additionally, can also make other kinds of queries, such as a hash query to the hash oracles.
Challenge: In this phase, if has performed training on the above encryption/ decryption query many times, then, in the following challenge phase, the attacker will choose a challenge message pair for the simulator for game playing. The simulator then will toss the coin on b after it receives this message pair. If the final output b is 1, then we can have . Otherwise, we have . After the attacker has asked the cipher-text on the chosen target messages , the only restriction is that the cannot ask the decryption oracle on the target message with the input cipher-text . This query can make the simulation fail due to the simulator cannot be able to tell the answer of cipher-text . Except in the above query, can make other kinds of queries on different messages.
Lemma 3.
In this lemma, we model the above actions as the game simulation steps, which we played with the attacker .
The advantage function of the adversary that is defined as
4.5. Partner Function
In this definition, we define the partner function. We assume that there is an instance whose action is the same as player i in the k-th session, where and , where N is the number for total players. Let the partner function be the instance of player j (call it ) in the -th session, where and . At this time, the instances and believe that each side is the real player in the session, respectively. At this time, we can say that two instances and are partnered if the following statements are true:
- ’s session identity is the same as the session identity of .
- is the partner of in the session of .
- is the partner of in the session k of .
4.6. Freshness
In this definition, we define freshness. We assume that there is an instance where is “fresh” if it satisfies the following conditions.
- has not been queried the reveal query .
- There is a partner that is matched to partner by the partner function, and has not been queried the reveal query .
- The partner of is not the inside attacker during communication in the instance of the player j.
4.7. Forward Secrecy (FS)
Our proposed two factor patient authentication scheme is forward secrecy (FS) if cannot compromise the past information, even if they have sent (or ) to the player i, where .
Theorem 1.
First, we assume that is an indistinguishable-CCA (Ind-CCA) secure asymmetric encryption/decryption scheme and equips two secure hash functions, and , which we can be replaced with two random oracle (RO) functions, respectively. We also assume that our proposed patient electronic health record exchange scheme (PEHRES) that is forward secure (FS) and unforgeable (Unf) also satisfies the following situations. In other words, if our proposed scheme is secure, then
where t is the total execution time, is the maximum total experiment time including an adversary execution time, is the maximum total time to guess the real session key, I is an upper bound on the number of parties, with at most encryption queries at most decryption oracles, and is an upper bound on the number of and queries in the experiment, where ε is a negligible advantage.
5. Security Analysis
In this section, we provide security analysis and functional analysis of our proposed scheme.
5.1. Replay Attack Resistance
In this EHR migration phase, we adopt random values , , and as our authentication challenge numbers. We assume an attacker can capture authentication messages among the protocol communication and may replay these captured messages to the server W to impersonate the patient U. First, the server V will check that this message was used before in some session before communicating with the server W. Hence, the server V will also check that one of these messages , , and was used before. If one of them was used, then it would close this session and save the record as the replay attack from V.
5.2. Resist User Impersonation Attack
In this proposed scheme, the adversary cannot replay any authentication message without the user U’s biometric information , and it also cannot guess the random number successfully to impersonate the server V. Additionally, the adversary does not have the non-negligible probability to forge the patient’s signature to the server V. In addition, the server V also checks the signature to authenticate the patient U’s identity in the migration registration phase. Thus, the adversary cannot have non-negligible probability to forge U’s signature under the RSA factoring problem. Therefore, our scheme can resist user impersonation attacks.
5.3. Provide Mutual Authentication
In the EHR migration phase, a patient U can delegate the server V to perform the EHR migration exchange with the system of the desired hospital W. Server V can perform the challenge response with the server of W, and they both communicate a session key for later usage after successful authentication. During the authentication rounds, V and W can check the freshness of random numbers (, , and ). If one of them is to be replayed, V or W would find out and deny this session with the other party. Finally, it would close this phase and record that there was a replay attack in this EHR migration phase.
5.4. Provide Data Security
In the EHR migration phase, all random numbers are generated by these two parties and drop off when the authentication between them is successful. In addition, not only are , , and verified by these two parties V and W, but also they can also be response messages to confirm their respective identities.Hence, the adversary cannot have a non-negligible probability to replace each of these messages to pass the authentication process. In the data recovery phase, is used to encrypt the patient’s EHR, and the adversary does not have a non-negligible probability to obtain a patient’s EHR, under the assumption that the symmetric encryption/decryption function is indistinguishable for the adversary in a polynomial time bound.
5.5. Session Key Establishment
In the EHR migration phase, the server V and the server W can also communicate a common session key after they perform challenge-response authentication with each other successfully. Not only can this session key be used for later communication, but it can also provide for symmetric encryption/decryption usage. In the appendix, we provide a formal security proof of the session key.
5.6. Forward Secrecy Proof
In the EHR migration phase, a patient can delegate the server V to authenticate with the desired server of hospital W. They can then build the session key after successful authentication. In fact, they can use this session key to communicate with each other to transfer the patient U’s EHRs or update the patient U’s EHR. With this property, the system can reduce the communication bits and improve the efficiency of data transmission. In the appendix, we also provide a formal secrecy proof of the session key.
5.7. EHR Fair Exchange
In the EHR migration phase, if W does not receive the U’s EHR from the V or if U’s EHR is broken, then the patient U can perform the data recovery request to the and ask the for help to solve this situation by providing the above signatures and V’s receipt to . If the above signatures are valid, performs the data recovery phase and forwards the encrypted patient’s EHR to the system of the hospital W. Finally, the server of hospital W can also obtain the patient U’s EHR under the help of .
5.8. Offline Trusted Third Party
In the proposed scheme, we assume that there is a and that it generates the patient’s EHR migrating signature with a delegation document and performs data recovery. Here we can assume that the on-line device of the can generate the signature after verifying the request party’s signature in the migration registration phase. Only if there is a request coming in the data recovery phase would the be on-line and solve this situation after verifying the request party’s evidence, including the registration signatures and the related signatures. From the above setting, our trusted third party would not stay on-line all the time and just appears when it is needed. Additionally, only the knows the link information of the patient U. Therefore, the patient can prevent their real identity from being disclosed during the EHR migration transaction.
From the above security analysis properties, we take [10] as a reference and make comparisons with schemes from [6,7,8,9,10]. In the following, we provide some security analysis definitions for security comparison (Table 1).

Table 1.
Security comparison.
5.9. Efficiency Comparisons
In this section, we evaluate our proposed scheme’s efficiency. First, we assume that our scheme’s parameter p is of 1024 bits for security consideration. We assume that H is the computation time of one hashing operation, is the computation time of one modular exponential operation in a 1024 bit module, M is the computation time of one modular multiplication in a 1024 bit module, is the computation time of a number over an elliptic curve, and is the computation time of a bilinear pairing operation of two elements over an elliptic curve in [13,14,15]. We also let , , , , and be the signature operation time, the asymmetric encryption time, the asymmetric decryption time, the symmetric encryption time, and the symmetric decryption time, respectively. We assume that our proposed scheme can be implemented on an elliptic curve over a 163-bit field and has the same security level of a 1024 bit public key crypto-system such as RSA or the Diffile-Hellman cryptosystem. We also assume that for the ARM CPU to the processor in 200 Mhz [15]. We also determine certain relations from the following: , and in [16,17,18,19,20,21,22].
Based on [23], a public key encryption/decryption operation time in an elliptic curve is approximately 1 and , respectively. Therefore, our proposed scheme total computation time cost is about . Due to the different properties of the above schemes, we omitted the efficiency comparisons and found some currently survey papers [11,24] that have the same functional properties as our proposed scheme.
In [11], the authors proposed a dynamic consent model of health data sharing using blockchain technology. They combine the consent representation models (DUO) and ADA-M [24] to let patients control their EHR sharing to match the request query with full access rights. Their method is designed for building an EHR platform but is not a practical mechanism for patients exchanging their EHRs with a formal security proof in a blockchain environment. In [12], the authors proposed an EHR with a patient-centric access right framework model by using blockchain technology. We think that this is a good idea for building health information exchange systematic modules with blockchain in the future, but they do not offer a practical solution for EHR migration currently, even in a blockchain environment. Our proposed scheme is established by the functional block such as the signature functions with other authentication functions. In future work, our proposed scheme could functionally add a smart contract function to generate a verifiable functional patient EHR block in blockchain network. Hence, our proposed scheme could be used in blockchain and non-blockchain environments.
In the efficiency evaluation of our scheme, we used a desktop with Ubuntu 20.04 with Intel(R) Core(TM) i7-8700 CPU @ 3.20 GHz CPU and 15 GB memory. The simulation experiment was carried out using GO language, and the standard “crypto/elliptic” library was used. We simulated every phase 20 times, shown in Figure 4, Figure 5 and Figure 6.
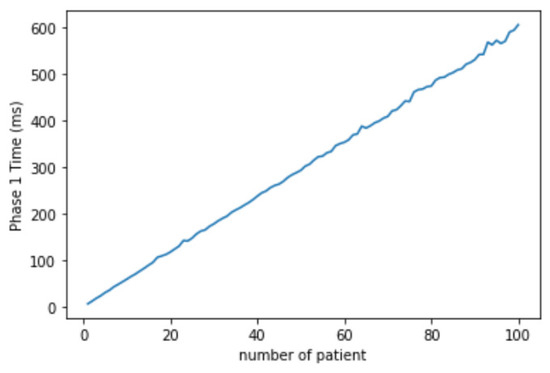
Figure 4.
The migration registration phase simulation.
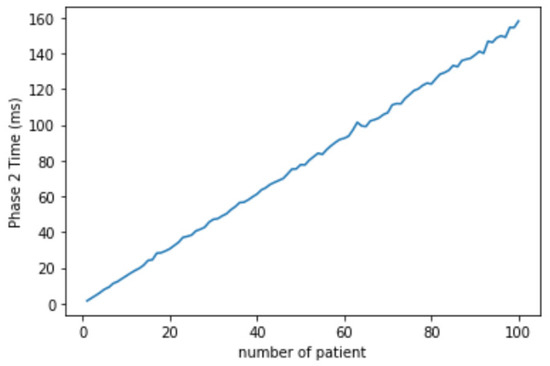
Figure 5.
The EHR migration phase simulation.
Figure 6.
The data recovery phase simulation.
In the future, we will discuss the forged HCA problem [25] and other applications such as neural network environments for COVID-19 patients [26] exchanging their EHRs. We hope to have a good solution to the above problems.
6. Security Proof
In this section, we continue to demonstrate what an adversary is and its probability. We model the , our scheme simulation steps, and the related oracle responses.
An adversary (call it ) can control all communication messages in this scheme. The adversary can obtain related information by sending oracles. A is the simulation of our proposed scheme, which can equip all kinds of oracles, and oracles can reply back according to the adversary’s questions. There is also another adversary (call it ) that controls the simulation and takes ’s ability to break the hard problem defined in the security definition.
Let be a “game”, the simulation of our scheme, where the adversary can ask queries to the oracles, and the oracles can answer back to the adversary. The following are query types that an adversary can make in the game.
- Send query (or ): this query models an adversary that can send message M to the authentication party i(or j), where in the k- (or )-th session, where k and are two different session numbers in N.
- Reveal query (or ): this query is used to model a situation that exposes a session key of to an adversary, where and in the k(or )-the session.
- Encryption query: this query is used to model that an adversary can obtain a ciphertext on the input of a chosen message .
- Decryption query: this query is used for modelling an adversary that can obtain a plain-text on the input of a cipher-text .
- Corrupt query (or ): this query is used to expose the private key of the player (or ) to the adversary, where .
- Hash query: this query depends on what the input is; the simulator then returns the related output to the attacker.
- Test query : this query is used to define the advantage of an adversary. When the adversary has finished all of the above queries to the oracle, they can make this test query on an instance (or ) to the simulator. At this time, the simulator will flip a coin b. If b is 1, then the real session key is . Otherwise, it returns a random string chosen uniformly from . The adversary is only allowed to ask for the “fresh” instance of a player in the above simulation.
Proof of Theorem 1.
First, we assume that there is an adversary that attempts to attack our patient EHR exchange scheme () in the forward secure sense. We then let be the event at which can distinguish at least one ciphertext in with non-negligible probability. At the same time, we also let be the event at which the adversary can forge the signature of our with non-negligible probability. We assume that
where b and are coin flips chosen by the simulator and the attacker , respectively.
We also assume that
where and are signatures forged by the attacker , respectively. We then use three lemmas to complete this security proof in the following.
Lemma 4.
We assume that there is no event such that the attacker can distinguish the ciphertext with non-negligible probability
in the polynomial time bound under the above Ind-CCA security definition with hash queries, at most encryption queries, and at most decryption queries, respectively.
Proof of Lemma 4.
We assume that is a non-negligible probability in the simulation game. We can then construct an attacker whose work is to distinguish the cipher-text under the Ind-CCA encryption/decryption scheme. There is also an attacker whose goal is to break the encryption/decryption of our proposed scheme . Next, we construct as the simulator that simulates the attacking environment in which can mount its attack. First, simulates an encryption oracle , where , and generates the to the attacker on the plain-texts () chosen by the attacker in the selected instance , where the partner of is . In addition, also simulates the decryption oracle to answer the decryption query issued by the attacker . We consider the following steps. First, prepares all hash functions, including and , two hash functions with collision-resistance. It also generates the instances of each player i, where . It can make the above two hash queries times, where .
Hash query
In this hash query phase, the simulator also responds to all kinds of hash queries in each stage.
- In the migration registration phase, the simulator generates the corresponding hashed value to U and V. It prepares the for the patient U as the registration token. At the same time, the simulator chooses and makes the ciphertext for .
- Next, the simulator has to simulate the signature and from the signing oracle. It then forwards (, ) to . The simulator then computes as the response receipt of the instance of player V.
- In the EHR migration phase, the simulator can simulate the hashed values and to , which forwards , , and as challenge random numbers.
Phase 1
- In the migration registration phase, the attacker can issue the encryption query on the chosen message . can then forward this to the encryption oracle and pass the final result to the .
- The attacker can issue the decryption query on the ciphertext . can then forward this to the decryption oracle and pass the final message from the oracle output to the .
- In the EHR migration phase, the attacker can ask for the encryption result and the decryption result of . can forward and to the attacker .
Challenge
- In this phase, can generate the ciphertext by querying the asymmetric encryption oracle with the coin flip b on the target message pair chosen by the attacker . If b=1, C is computed from , where . Otherwise, it returns the ciphertext to , where . The only restriction is that cannot ask for the decryption query on the ciphertext . On the other hand, we also consider that the ciphertext is the same situation. We also set up the target message pair chosen by the attacker . If =1, C is computed from , where . Otherwise, it returns the ciphertext to , where .
- We assume that this event happens with respect to the instance of the player i, where its partner player is . At this time, finally outputs its own guessing bit . Otherwise, the system stops this authentication stage and aborts this simulation.
Finally, has a set with instances of players and with total hash queries , at most encryption queries, and decryption queries. At this time, does not fail in the simulation environment with ’s correct guessing, where has non-negligible probability. The following equation will then hold:
In the ciphertext simulation game, we have the same simulation as above. Therefore, we omitted the simulation, but we also conclude that
We then can summarize the total probability as follows:
□
Lemma 5.
Before we prove this lemma, we assume that there is no attacker that can guess the real session key in the event that the ciphertext generated by the symmetric encryption (SE) functions cannot be distinguished by correctly with non-negligible probability. We then have
in the polynomial time under the random oracle (RO) assumption with total hash queries.
Proof of Lemma 5.
In this proof, we construct another simulator that also simulates the attacking environment for mounting its attack. Finally, if can guess the real session key successfully with the non-negligible property, then we can use to break the random oracle assumption.
- First, we assume that is given the system parameters . It starts to choose public key/secret key pairs for all parties except for and . Next, selects other protocol parameters such as ( and . At this time, we also let the target identities and be the instances of the patient U and the system V, respectively.
- After the above environment is set up completely, starts to simulate the following oracle queries and related hash functions.
- First, sets parameters , where are two random numbers, and , are these two collision-resistance hash functions. In addition, adopts as the security parameter. First, prepares two nonce challenge numbers and in the -th and -th session, respectively.
- During this simulation, for each query issued from , answers it as follows:
- It takes as its input and responds to each query in the instance in the k-th session on the message M, where and are two pseudo-random functions with the same length of the hash oracles and , respectively.
□
Hash Query
In this hash query phase, the simulator can answer all kinds of harsh queries in each stage, as follows:
- In the migration registration phase, the simulator also computes the initial biometric information value () for the patient U and keeps them in the oracle simulation database. If the makes the hash query on () and , also forwards them to the hash oracle and returns the response hashed value to .
- In the EHR migration phase, asks for the , , and hash values of the function, and also forwards them to the hash oracle and lets the hash oracle generate the corresponding hash values to .
- If receives the query, then it returns the private key to . If receives the query, it checks if or , then computes the session key , where and are chosen from and functions, respectively. On the other hand, if , , and , then computes as the session key and delays this key in the response in the query.
- If the adversary has finished the above queries, it can make the query to . At this time, will check the instance session and player to see if and , and then tosses a coin b to answer the session key. If b=0, then it computes . Otherwise, it computes from the random pseudo-random function.
Finally, if answers the query for and by using , and does not fail in guessing , then answers the session key depending on its coin flip . We can have -4.6cm0cm
Finally, we could conclude that
Lemma 6.
Before we prove Lemma 1, we assume that there is no event such that the attacker can forge the signature of patient U with non-negligible probability
in the polynomial time bound under the above Ind-CCA security definition with hash queries, at most encryption queries, and at most decryption queries, respectively.
Proof of Lemma 6.
In this lemma proof, we start to prove our above Lemma 1 (*lm1). To start the proof of Lemma 1 (*lm1), we defined the Game as the simulation game that runs as the proposed protocol controlled by the simulator . We define Game as follows.
We first define the simulator as the simulator that is given in the RSA factoring problem, and we assume there is an attacker whose goal is to forge a valid signature on the function block.
The simulator first chooses the security parameter l with the message space . The also selects two collision-resistance hash functions that map from and two hash oracles and , respectively. After setting up the system parameter, the simulates each phase in the proposed EHR scheme. In the migration registration phase, the attacker can impersonate the patient U to ask for U’s signature request on the desired message. When has received this request, it takes the message as input and outputs the signature with the help of the above secure digital signature function . It then returns this back to the . The can also continue to ask the hospital certification center ’s signature on the received signature of patient P. It also receives the message tuple and outputs the signature back to . In addition, it is the same situation when asks the signature of V. The also returns back to .
In these phases, the will make the signature request in the above situation. The starts the Challenge phase and forwards the message , where . The can forge l+1 signatures , where , where and after l signature queries. Finally, this forged signature also passes the verification successfully. We then can use ’s ability to find a solution to the RSA factoring problem. Thus, we have
Finally, we could conclude that
□
After summarizing the above three lemmas, we can conclude that .
7. Conclusions
We propose a practical and provable patient EHR fair exchange scheme with key agreement for e-health information systems. Not only does our scheme offer a solution for the seven problems described in Section 2, when a patient attempts to migrate their personal information data to another hospital, but they can also maintain their anonymity during the data migration transaction. In addition, Table 1 shows a security and functional comparison with other related papers. It is obvious that our proposed scheme guarantees convenience, rapidity, and integrity.
Our mechanism provides secure data storage and the secure transfer of authorized information to designated locations. What information can be authorized, for example, whether COVID-19 patient privacy concerning patients’ names, identities, and genetic sequences can be transmitted to different hospitals, is beyond this study’s scope. This study guarantees secure data transfer and storage. Our scheme also provides a formal security proof in the random oracle model under chosen-ciphertext security. Our approach focuses on the security and privacy protection of patient EHRs rather than on the design of electronic health systems. It not only serves as a high-level functional module for integrity but also provides an efficient and contactless data transfer method that allows for medical data aggregation and protects patient anonymity, especially relevant in the context of the global COVID-19 pandemic. In the future, we will extend our scheme to be applicable for COVID-19 patient EHR exchange in a neural network environment.
Author Contributions
Conceptualization, M.-T.C.; Formal analysis, M.-T.C. and T.-H.L.; Methodology, M.-T.C. and T.-H.L.; Writing—original draft, M.-T.C.; Writing—review & editing, T.-H.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Acknowledgments
This study was supported in part by grants from the Ministry of Science and Technology of the Republic of China (Grant No. MOST 109-2221-E-167-028-MY2).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Saranummi, N. In the spotlight: health information systems. PHR Value Based Healthc. 2011, 2, 15–17. [Google Scholar] [CrossRef] [PubMed]
- Chiuchisan, I.; Balan, D.G.; Geman, O.; Chiuchisan, I.; Gordin, I. A Security Approach for Health Care Information Systems. In Proceedings of the E-Health and Bioengineering Conference (EHB), Sinaia, Romania, 22–24 June 2017; pp. 721–724. [Google Scholar]
- Appari, A.; Johnson, M. Information security and privacy in healthcare: Current state of research. Int. J. Internet Enterp. Manag. 2010, 4, 279–284. [Google Scholar] [CrossRef]
- Mahmoud, A.M.; Zeki, A.M. Security issues with health care information technology. Int. J. Sci. Res. (IJSR) 2015, 12, 1021–1024. [Google Scholar]
- Health Level Seven. Available online: http://www.hl7.org/implement/standards/ansiapproved.cfm (accessed on 21 December 2020).
- Das, A.K.; Goswami, A. A secure and efficient uniqueness- and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 2013, 3, 9948. [Google Scholar] [CrossRef] [PubMed]
- He, D.; Kumar, N.; Chen, J.; Lee, C.C.; Chilamkurti, N.; Yeo, S.S. Robust anonymous authentication protocol for health- care applications using wireless medical sensor networks. Multimed. Syst. 2015, 1, 49–60. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Y.; Tang, S.; Luo, H. Privacy protection for e-health systems by means of dynamic authentication and three-factor key agreement. IEEE Trans. Ind. Electron. 2017, 65, 2795–2805. [Google Scholar] [CrossRef]
- Kaul, S.D.; Murty, V.K.; Hatzinakos, D. Secure and privacy preserving biometric based user authentication with data access control system in the healthcare environment. In Proceedings of the 2020 International Conference on Cyberworlds (CW), Caen, France, 29 Septemeber–1 October 2020; pp. 249–256. [Google Scholar]
- Jaiman, V.; Urovi, V. A Consent Model for Blockchain-Based Health Data Sharing Platforms. IEEE Access 2020, 8, 143734–143745. [Google Scholar] [CrossRef]
- Zhuang, Y.; Sheets, L.R.; Chen, Y.W.; Shae, Z.Y.; Tsai, J.J.P.; Shyu, C.R. A Patient-Centric Health Information Exchange Framework Using Blockchain Technology. IEEE J. Biomed. Health Inform. 2020, 24, 2169–2176. [Google Scholar] [CrossRef] [PubMed]
- Jurisic, A.; Menezes, A.J. Elliptic Curves and Cryptography. pp. 1–13. Available online: http://http://www.cs.nthu.edu.tw/~cchen/CS4351/jurisic.pdf (accessed on 22 December 2020).
- Koblitz, N.; Menezes, A.; Vanstone, S. The state of Elliptic curve cryptography. Des. Codes Cryptgography 2000, 19, 173–193. [Google Scholar] [CrossRef]
- Lauter, K. The Advantages of Elliptic curve cryptography for wireless security. IEEE Wirel. Commun. 2004, 11, 62–67. [Google Scholar] [CrossRef]
- LI, Z.; Higgins, J.; Clement, M. Performance of Finite Field Arithmetic in an Elliptic Curve Cryptosystem. In Proceedings of the 9th IEEE International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunications Systems (MASCOTS’01), Cincinnati, OH, USA, 15–18 August 2001; pp. 249–256. [Google Scholar]
- Ramachanfdran, A.; Zhou, Z.; Huang, D. Computing cryptography algorithm in Portable and embedded devices. In Proceedings of the IEEE International Conference on Portable Information Devices, Orlando, FL, USA, 25–29 May 2007; pp. 1–7. [Google Scholar]
- Schneier, B. Applied Cryptography, 2nd ed.; John Wiley & Sons: Hoboken, NJ, USA, 1996. [Google Scholar]
- Takashima, K. Scaling Security of Elliptic Curves with Fast Pairing Using Efficient Endomorphisms. IEICE Trans. Fundam. 2007, E90-A, 152–159. [Google Scholar] [CrossRef]
- Bertinoi, G.; Breveglieri, L.; Chen, L.; Fragneto, P.; Harrison, K.; Pelosi, G. A pairing SW implementation for smart cards. J. Syst. Softw. 2008, 81, 1240–1247. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A.; Scott, M. Software Implementation of pairings. Identity-Based Cryptogr. Cryptol. Inf. Secur. 2008, 2. [Google Scholar] [CrossRef]
- Hohenberger, S. Advances in Signatures, Encryption, and E-cash from Bilnear Groups. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2006. [Google Scholar]
- Juang, W.S.; Lei, C.L.; Liaw, H.T.; Nien, W.K. Robust and Efficient Three-party User Authentication and key agreement Using Bilinear pairings. Int. J. Innov. Comput. Inf. Control. 2010, 6, 763–772. [Google Scholar]
- Woolley, J.P.; Kirby, E.; Leslie, J.; Jeanson, F.; Cabili, M.N.; Rushton, G.; Hazard, J.G.; Ladas, V.; Veal, C.D.; Gibson, S.J.; et al. Responsible sharing of biomedical data and biospecimens via the automatable discovery and access Matrix (ADA-M). NPJ Genom. Med. 2018, 3, 7. [Google Scholar] [CrossRef] [PubMed]
- Chakraborty, T.; Jajodia, S.; Katz, J.; Picariello, A.; Sperli, G.; Subrahmanian, V.S. FORGE: A fake online repository generation engine for cyber deception. IEEE Trans. Dependable Secur. Comput. 2019. [Google Scholar] [CrossRef]
- La Gatta, V.; Moscato, V.; Postiglione, M.; Sperli, G. An epidemiological neural network exploiting dynamic graph structured data applied to the COVID-19 outbreak. IEEE Trans. Big Data. 2020, 7, 45–55. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).