A Multiple-Swarm Particle Swarm Optimisation Scheme for Tracing Packets Back to the Attack Sources of Botnet †
Abstract
1. Introduction
- The multimodal optimisation problem was solved using the MSPSO method. Moreover, different botnet attack sources were analysed with high accuracy for the reconstructed attack path to identify the most probable attack paths. This identification was performed for assisting security managers to identify the sources of DDoS attacks.
- The optimal route-searching process of the MSPSO algorithm was improved to prevent the PSO algorithm from converging prematurely to a local suboptimal solution in a large search space.
- The accuracy of the MSPSO algorithm was obtained as 95.89% for the effects of dynamic traffic in the experimental network (number of nodes = 24) and as 94.64% for the network topology (number of nodes = 64).
- Compared to traceback accuracy with other route search algorithms such as the A* algorithm [19] and the PSO [11,12,13,14], the performance of the MSPSO-IPTBK algorithm in reconstructing attack paths provides superior performance for analysing the attack origins from multiple different data sources using ns-3 with the BRITE framework.
2. Overview of PSO Schemes and the IPTBK Problem
2.1. Existing IPTBK Techniques for DDoS Attacks
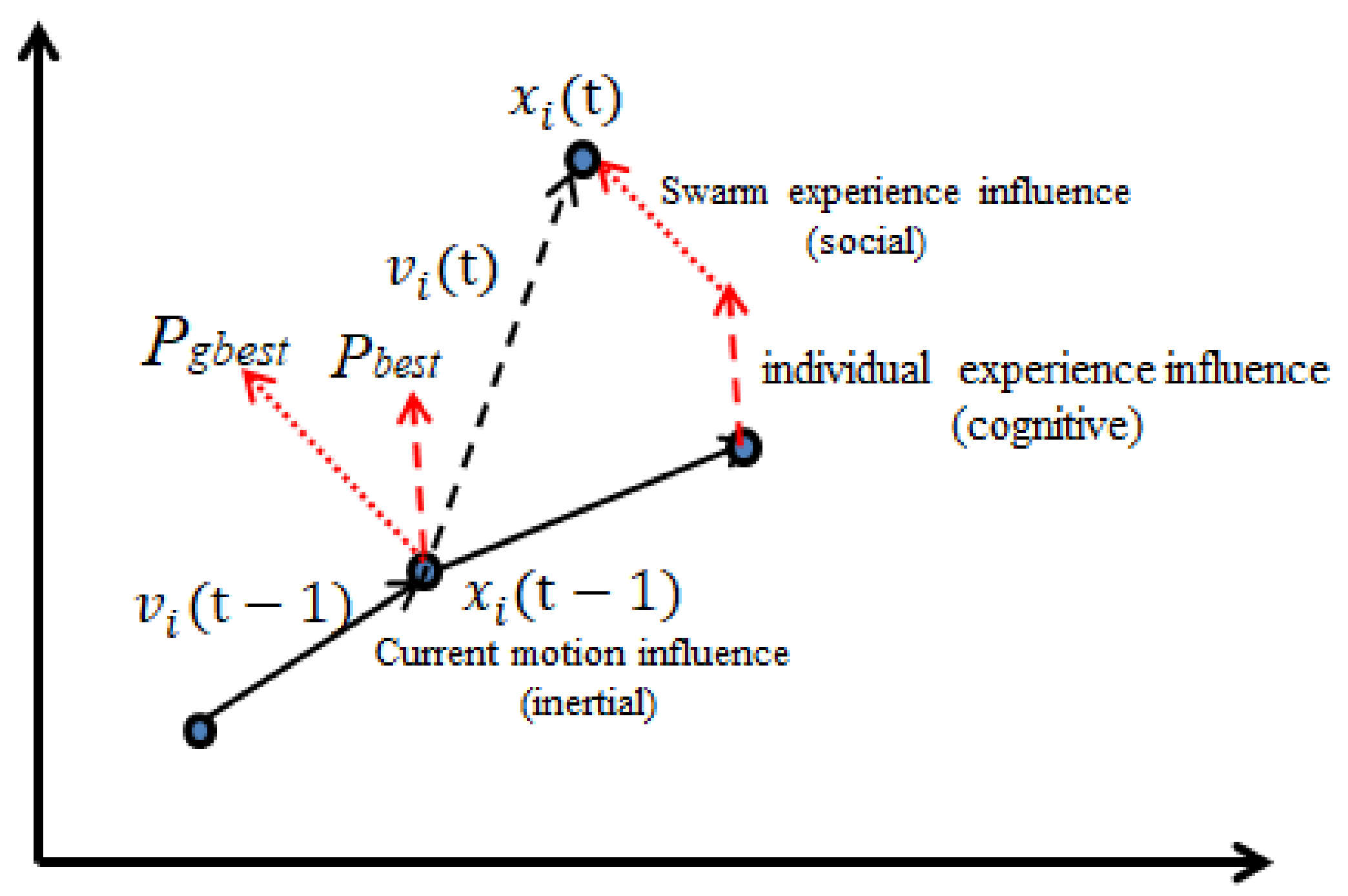
2.2. MSPSO Algorithms
2.2.1. WOSP
2.2.2. DMS-PSO
- (1)
- Local search phase: A quasi-Newton method (e.g., the Broyden–Fletcher–Goldfarb–Shanno (BFGS) algorithm) is used to speed up the search for the best position in a subswarm. Notably, the space constrained within the range is searched in this phase. The fitness value of a path is calculated by minimising the cost function of traversed paths.
- (2)
- Convergence phase: After completing the local search process, the DMS-PSO algorithm periodically regroups the particles of the subswarms into new subswarms. The new subswarms initiate the search process again with the previous particle swarms until the global best position is found.
3. Application of the Proposed MSPSO Algorithm to the IPTBK Problem
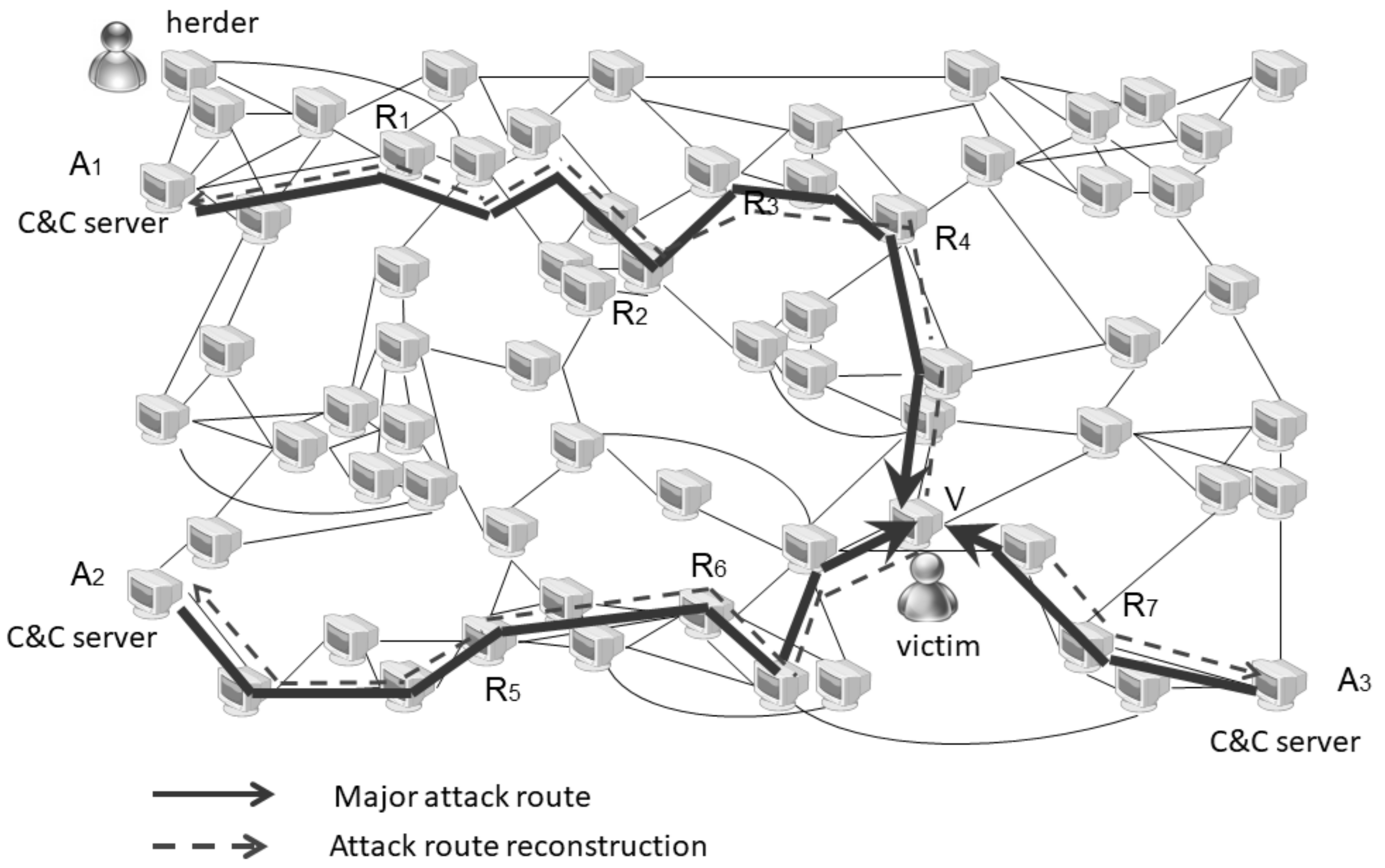
3.1. Basic Idea
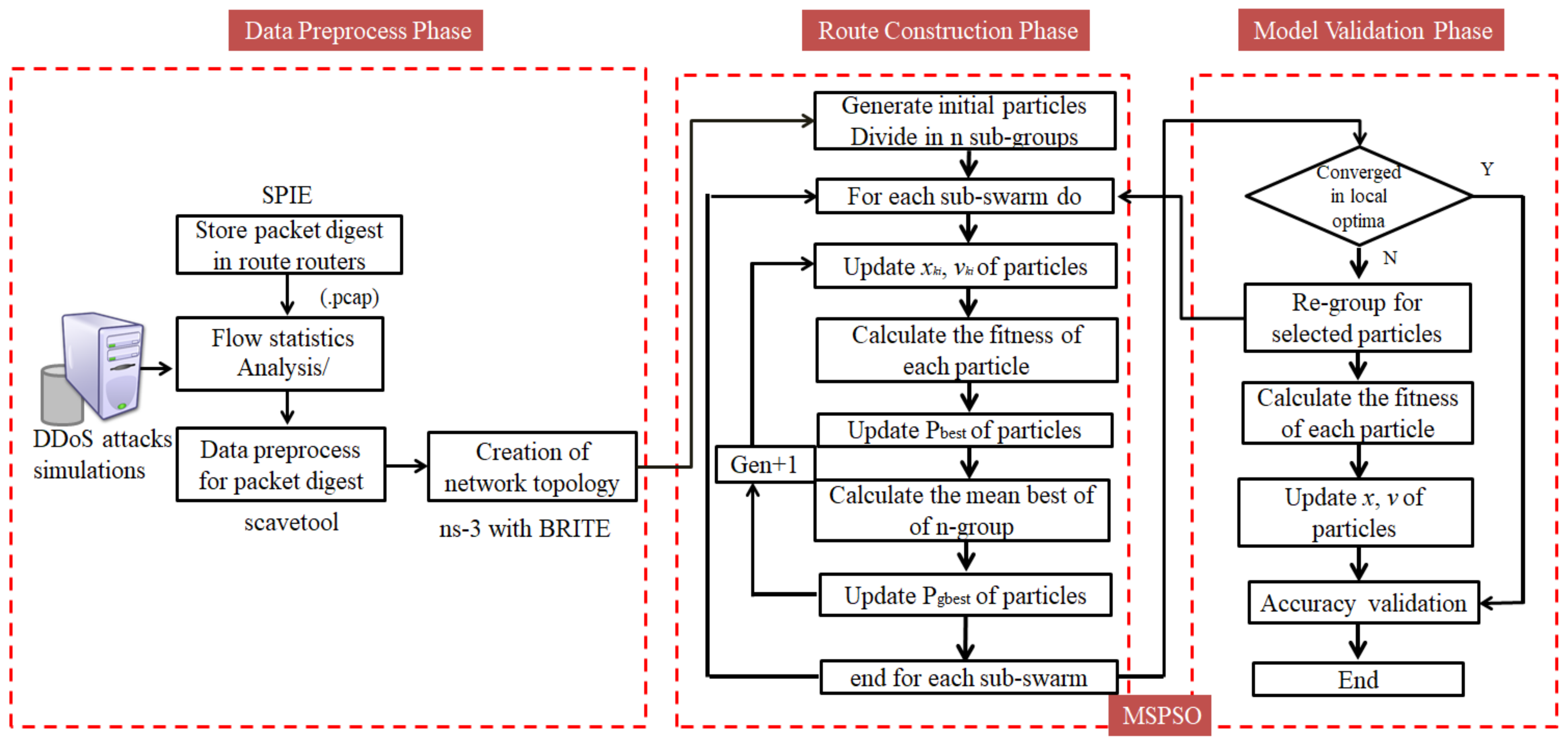
3.2. Solving the IPTBK Problem Using the MSPSO Algorithm
3.2.1. Data Pre-Processing Phase
Data Collection
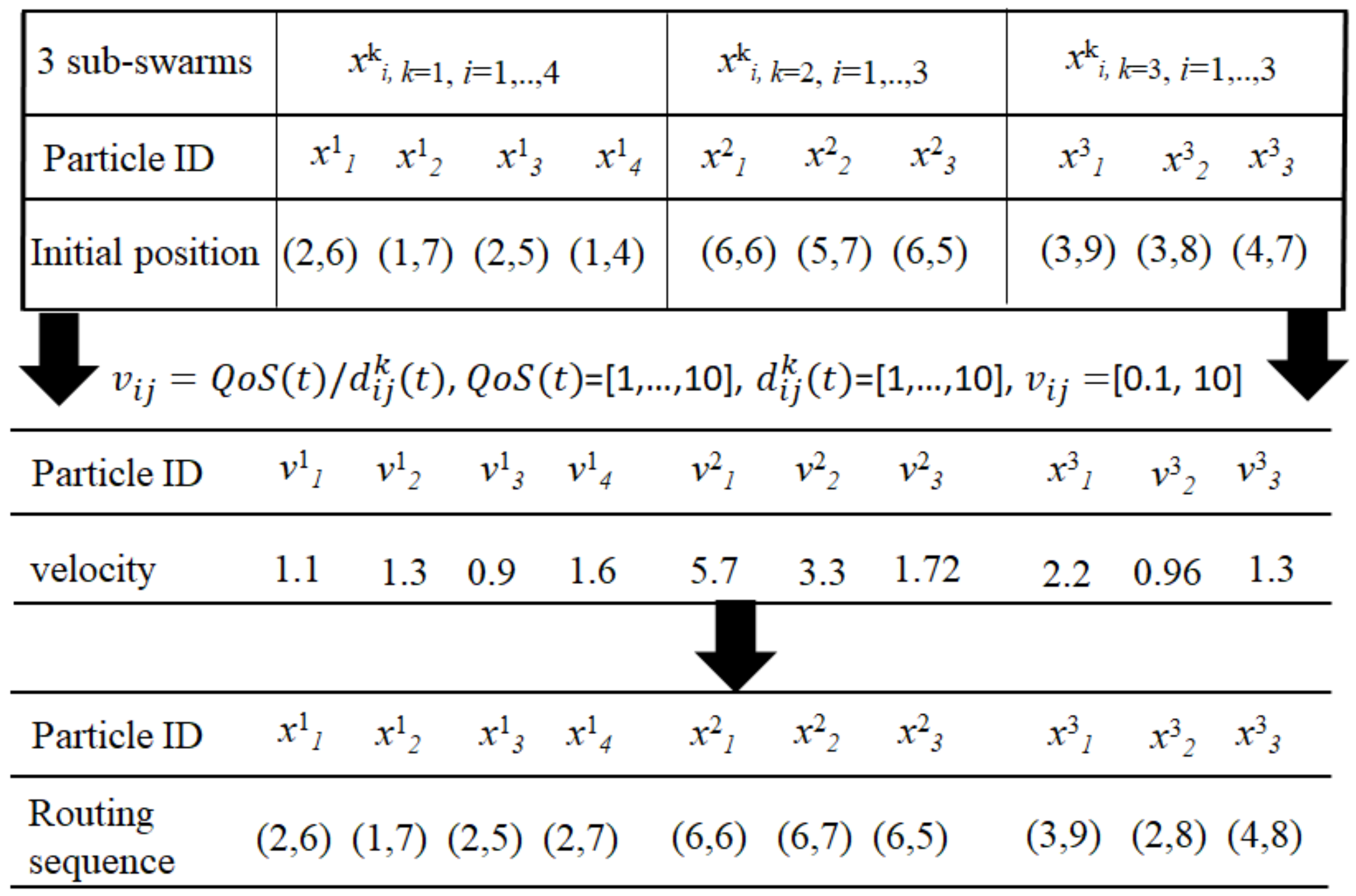
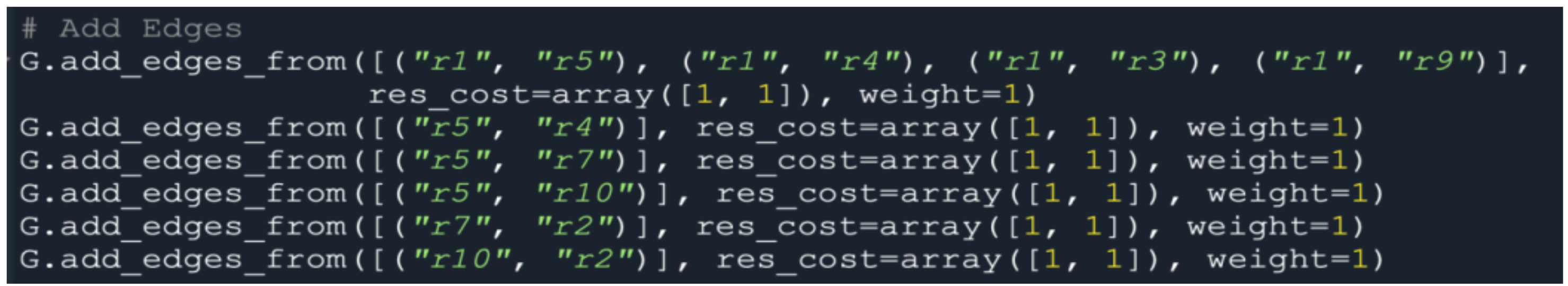
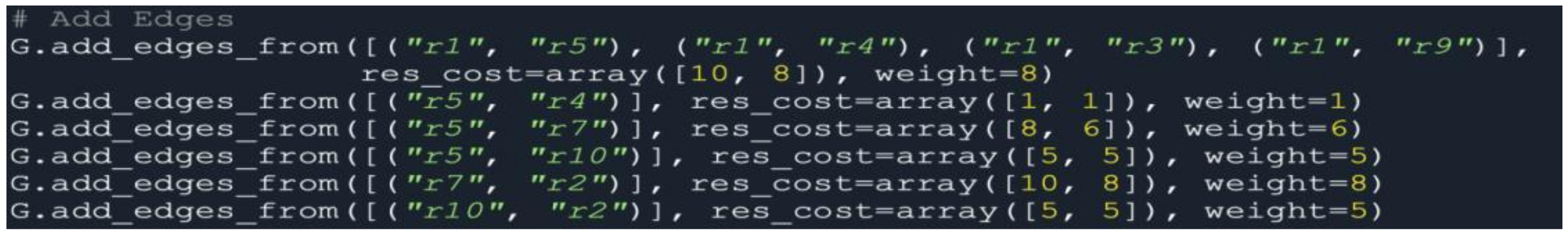
Encoding of Particles
Intelligent Reconnaissance Strategy
3.2.2. Route Construction Phase
Local Search Process
Global Search Process: Dynamic Neighbourhood
3.2.3. Model Validation Phase
4. Results
4.1. Case I: Network Performance Analysis for DDoS Attacks (24 Nodes)
4.1.1. Step 1: Data Pre-Processing Phase
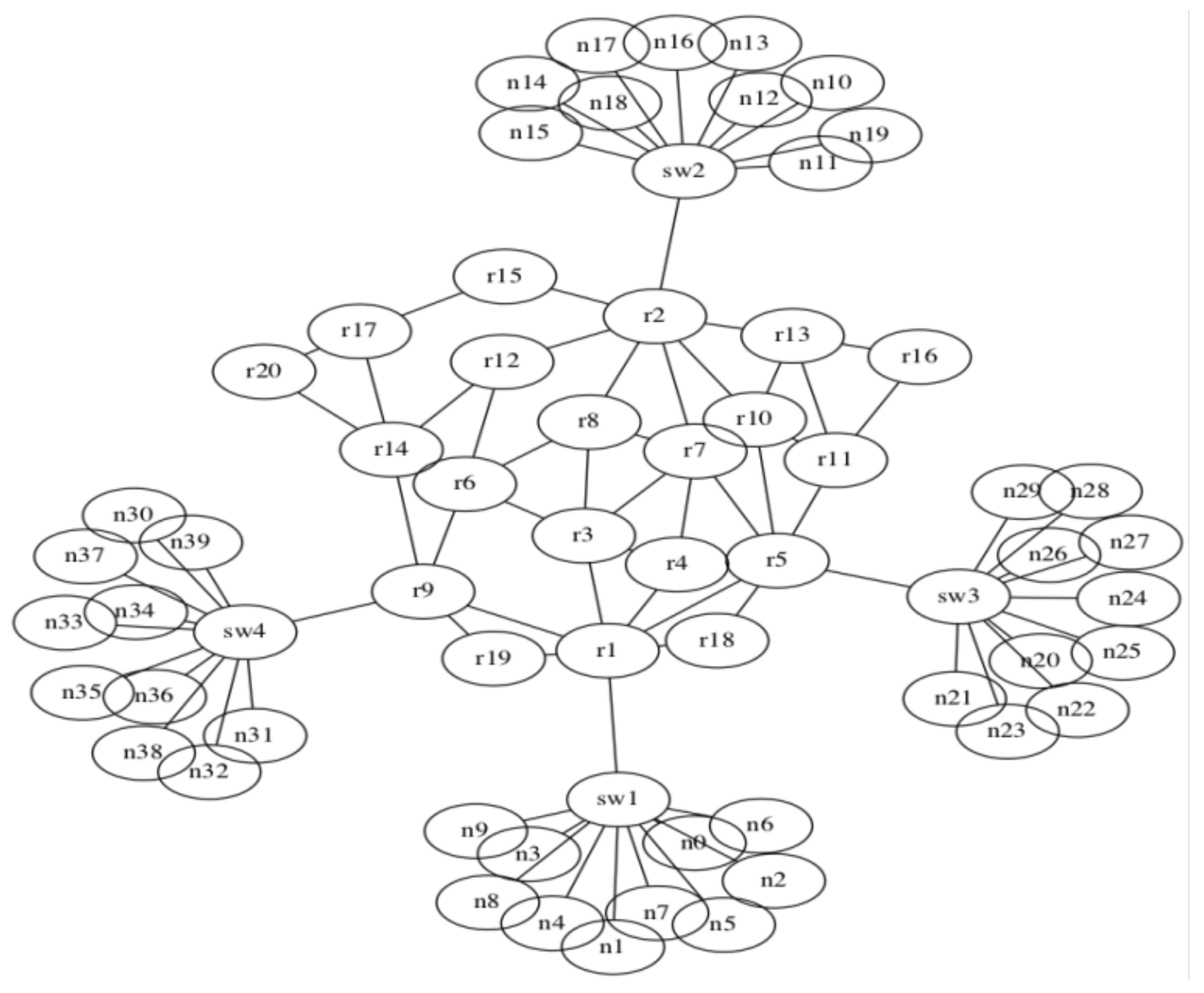
Creation of the Network Topology
4.1.2. Step 2: Route Construction Phase
4.1.3. Step 3: Model Validation Phase
4.2. Case II: Performance Analysis for a Series of DDoS Attacks (64 Nodes)
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Corero. DDoS Attack Types: Glossary of Terms. Available online: https://www.corero.com/blog/glossary/ (accessed on 12 January 2020).
- Lin, S.; Chiueh, T.C. A Survey on Solutions to Distributed Denial of Service Attacks; Technical Report; Department of Computer Science, Stony Brook University: New York, NY, USA, 2013. [Google Scholar]
- Spamhaus Malware Labs. Spamhaus Botnet Threat Report 2019. Available online: https://www.spamhaus.org/news/article/793/spamhaus-botnet-threat-report-2019 (accessed on 18 January 2020).
- Wang, P.; Lin, H.T.; Wang, T.S. An Improved Ant Colony System Algorithm for Solving the IP Traceback Problem; Information Sciences; Elsevier: Amsterdam, The Netherlands, 2016; pp. 172–187. [Google Scholar]
- Snoeren, A.C.; Partridge, C.; Sanchez, L.A.; Jones, C.E. Hash-based IP Traceback. In Proceedings of the Special Interest Group on Data Communication (SIGCOMM), San Francisco, CA, USA, 1–2 November 2001; pp. 27–31. [Google Scholar]
- Savage, S.; Wetherall, D.; Karlin, A.; Anderson, T. Network Support for IP Traceback. IEEE ACM Trans. Netw. 2001, 9, 226–237. [Google Scholar] [CrossRef]
- Song, D.X.; Perrig, A. Advanced and Authenticated Marking Schemes for IP Traceback. In Proceedings of the 20th Conference on Computer Communications, Scottsdale, AZ, USA, 15–17 October 2001; pp. 878–886. [Google Scholar]
- Paruchuri, V.; Durresi, A. On the (in) Effectiveness of Probabilistic Marking for IP Traceback Under DDoS Attacks. In Proceeding of the IEEE Global Telecommunications Conference, Washington, DC, USA, 26–30 November 2007; pp. 1965–1970. [Google Scholar]
- Bellovin, S.; Leech, M.; Taylor, T. ICMP Traceback Messages. 2001. Available online: http://tools.ietf.org/id/draft-ietf-itrace-04.txt (accessed on 29 November 2019).
- Belenky, A.; Ansari, N. IP Traceback with Deterministic Packet Marking. IEEE Commun. Lett. 2003, 7, 162–164. [Google Scholar] [CrossRef]
- Shi, Y.; Eberhart, R. A modified particle swarm optimizer. In Proceedings of the IEEE International Conference on Evolutionary Computation, Anchorage, AK, USA, 4–9 May 1998; pp. 69–73. [Google Scholar]
- Angeline, P.J. Evolutionary Optimization versus Particle Swarm Optimization: Philosophy and Performance Difference. In Proceedings of the 7th Annual Conference on Evolutionary Programming, International Conference on Evolutionary Computation Proceedings, San Diego, CA, USA, 25–27 March 1998; pp. 69–73. [Google Scholar]
- Lin, H.C.; Wang, P.; Lin, W.H. Implementation of an PSO-Based Security Defense Mechanism for Tracing the Sources of DDoS Attacks. Computers 2019, 8, 88. [Google Scholar] [CrossRef]
- Eberhart, R.C.; Shi, Y. Comparing Inertia Weights and Constriction Factors in Particle Swarm Optimization. In Proceedings of the Congress on Evolutionary Computation, La Jolla, CA, USA, 16–19 July 2000; pp. 84–88. [Google Scholar]
- Zhao, Y.W.; Wu, B.; Wang, W.L.; Ma, Y.L.; Wang, W.A.; Sun, H. Particle Swarm Optimization for Vehicle Routing Problem with Time Windows. Mater. Sci. Forum 2004, 471–472, 801–805. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.J. An Improved Routing Schema with Special Clustering Using PSO Algorithm for Heterogeneous Wireless Sensor Network. Sensors 2019, 3, 671. [Google Scholar] [CrossRef] [PubMed]
- Deng, D.; Cao, J.; He, J.; Li, S. A Novel IP Traceback Scheme to Detect DDoS. In Proceedings of the 3rd International Conference on Instrumentation, Measurement, Computer, Communication and Control (IMCCC ′13), Washington, DC, USA, 21–23 September 2013; pp. 1077–1080. [Google Scholar]
- Wikipedia, Multi-swarm Optimization. Available online: https://en.wikipedia.org/wiki/Multi-swarm_optimization (accessed on 12 January 2021).
- Wikipedia. A* Search Algorithm. Available online: https://en.wikipedia.org/wiki/A*_search_algorithm/ (accessed on 17 January 2020).
- Ye, W.; Feng, W.; Fan, S. A Novel Multi-swarm Particle Swarm Optimization with Dynamic Learning Strategy. Appl. Soft Comput. 2017, 61, 832–843. [Google Scholar] [CrossRef]
- Hendtlass, T. WoSP: A Multi-Optima Particle Swarm Algorithm. In Proceedings of the IEEE 2005 Congress on Evolutionary Computation, Edinburgh, Scotland, UK, 2–5 September 2005; pp. 727–734. [Google Scholar]
- Zhao, S.Z.; Liang, J.J.; Suganthan, P.N.; Tasgetiren, M.F. Dynamic Multi-Swarm Particle Swarm Optimizer with Local Search for Large Scale Global Optimization. In Proceedings of the IEEE 2008 Congress on Evolutionary Computation, Hong Kong, China, 1–6 June 2008; pp. 3845–3852. [Google Scholar]
- Xua, X.; Tang, Y.; Li, J.; Hua, C.; Guan, X. Dynamic Multi-swarm Particle Swarm Optimizer with Cooperative Learning Strategy. Appl. Soft Comput. 2015, 29, 169–183. [Google Scholar] [CrossRef]
- Waxman, B. Routing of Multipoint Connections. IEEE J. Sel. Areas Commun. 1988, 6, 1617–1622. [Google Scholar] [CrossRef]
- Wyld, D.C.; Zizka, J.; Nagamalai, D. Advances in Computer Science, Engineering and Applications. In Proceedings of the Second International Conference on Computer Science, Engineering and Applications, New Delhi, India, 25–27 May 2012; Volume 2, pp. 556–557. [Google Scholar]
- Gitlab, ns3-dev. Available online: https://gitlab.com/nsnam/ns-3-dev/commits/f15a942 (accessed on 25 February 2020).


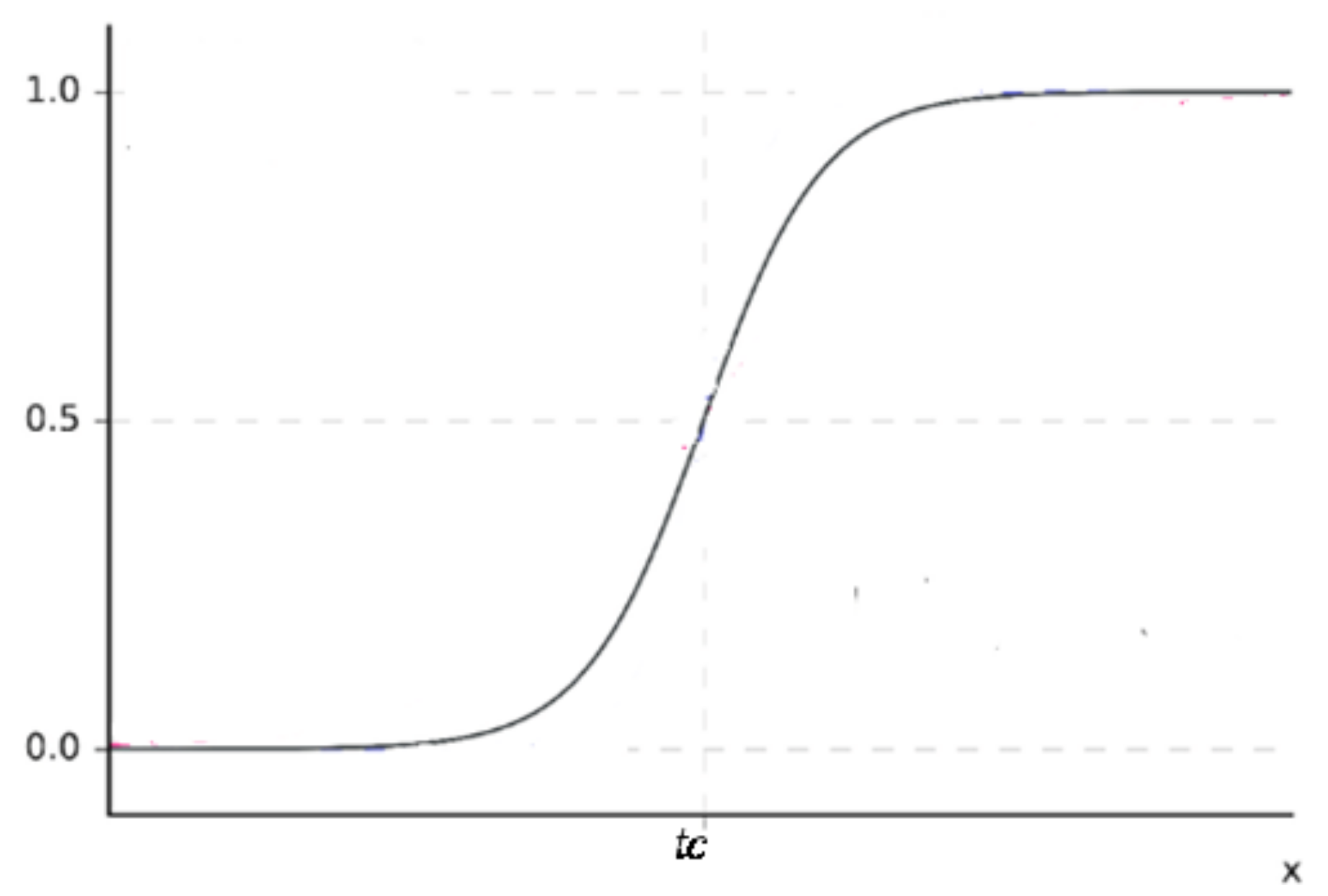
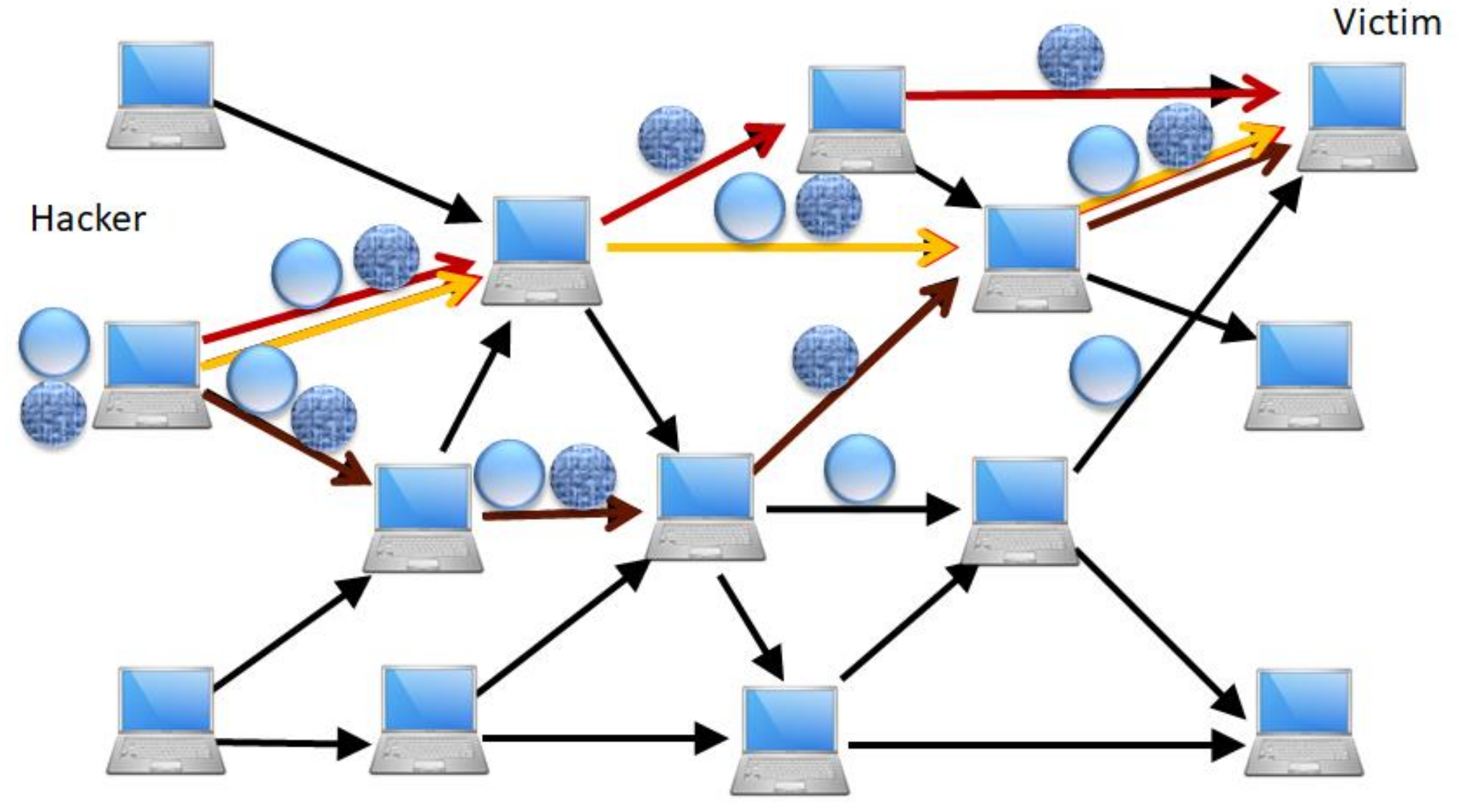



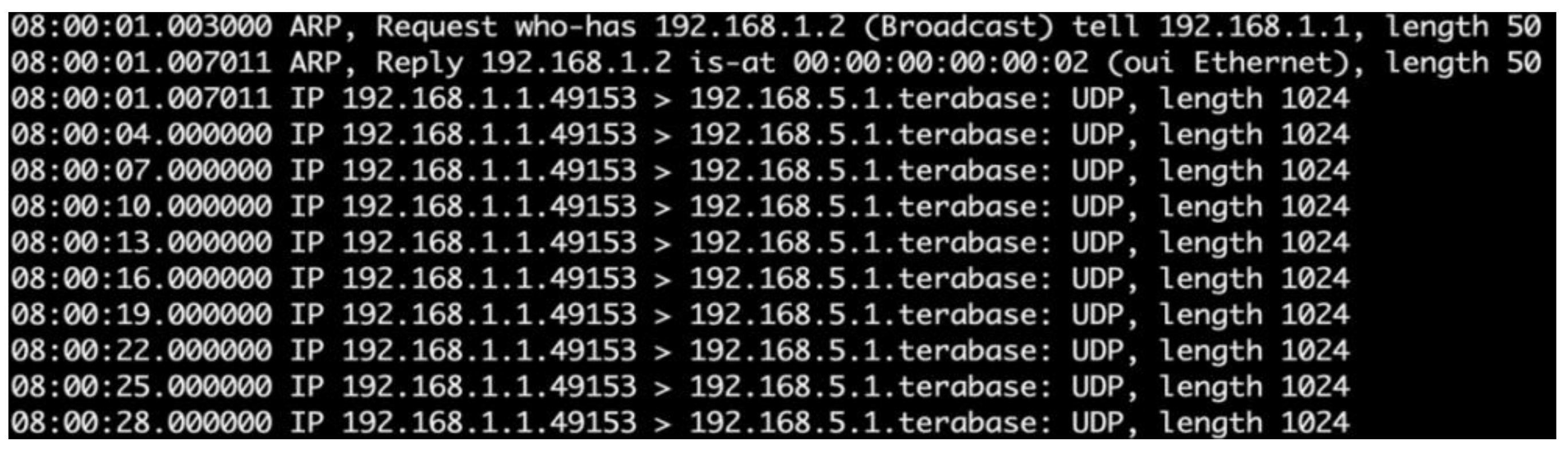
| Features | Limitations | ||
|---|---|---|---|
| Data Collection | Route Reconstruction | ||
| ingress filtering [5] | Each router marks all traversing packets for information flows (heavy loading) |
| When IP addresses are used through a proxy or a spoofed IP address, which does not identify a specific user within that pool of users. |
| PPM [6,7,8] | Each router marks packets with some probability p for information flows to reduce the consumption of computational resources |
|
|
| iTrace * [9] | When forwarding packets, routers can generate a Traceback message based on icmp command that is sent along to the destination with a low probability. With enough traceback messages from enough routers along the path, the traffic source and path can be determined. | The attack path reconstruction is based on traceback messages, which recursively repeat until the true of attack source is located based on traversing IPs. | Multiple attack sources will generate multiple attack paths that make traceback more difficult to locate the original attack sources. |
| DPM [10] | Using an advanced marking mechanism with ingress edge routers and traversing routers. | The same as that of PPM | DPM is sensitive to router subversion because it is critical that marks, once placed in packets, are not over written. |
| Scheme | Feature | Advantage | Limitation |
|---|---|---|---|
| WOSP [21] | When particles get too close, they are expelled by a short range force into new subswarms, thus avoiding a complete convergence. | WOSP is especially fitted for the optimisation on multimodal problems using the SRF where multiple local optima exist. | Sometimes, it may generate loop iterations in the searching process to discover the optimal solution. |
| DMS-PSO [22,23] | DMS-PSO periodically regroups the particles of the subswarms after they have converged into new subswarms, and the new swarms are started with particles from previous swarms. | DMS-PSO can achieve a good balance between the exploration and exploitation abilities in multimodal problems. | DMS-PSO separates the optimal solution searching process into distinct phases, which could weaken both mechanisms of the search process. |
| n0-Switch1-router1-router5-router4-router3-router8-router7-router10-router2-Switch2-n11 |
| n0-Switch 1-router1-router5-router4-router3-router8-router7-router2- Switch2-n11 |
| n0-Switch 1-router1-router5-router4-router3-router8- router2- Switch2-n11 |
| n0-Switch 1-router1-router9-router6-router8-router2- Switch 2-n11 |
| Attack Path | Packets Collected | Coverage Percentage (%) |
|---|---|---|
| n0-switch1-router1-router5-router7-router2-switch2-n11 | 500 | 41.67% |
| n0-switch1-router1-router4-router7-router2-switch2-n11 | 500 | 41.67% |
| n0-switch1-router1-router3-router8-router2-switch2-n11 | 170 | 14.17% |
| Total | 1200 | 100.0% |
| Attack Path | Packets Collected | Coverage Percentage (%) |
|---|---|---|
| n0-switch1-router1-router5-router7-router2-switch2-n11 | 500 | 41.67% |
| n0-switch1-router1-router4-router7-router2-switch2-n11 | 500 | 41.67% |
| n0-switch1-router1-router3-router8-router2-switch2-n11 | 150 | 12.50% |
| n0-switch1-router1-router9-router3-router8-router2-switch2-n11 | 20 | 1.67% |
| Total | 1200 | 100.0% |
| Attack Path | Packets Collected | Coverage Percentage (%) |
|---|---|---|
| n0-switch1-router1-router5-router7-router2-switch2-n11 | 200 | 16.67% |
| n0-switch1-router1-router4-router7-router2-switch2-n11 | 200 | 16.67% |
| n0-switch1-router1-router3-router8-router2-switch2-n11 | 20 | 1.67% |
| n0-switch1-router1-router9- router3-router8-router2-switch2-n11 | 20 | 1.67% |
| n20-switch3- router5-router7-router2-switch2-n11 | 280 | 23.33% |
| n20-switch3-router5-router4-router7-router2-switch2-n11 | 280 | 23.33% |
| n20-switch3-router5-router11-router10-router2-switch2-n11 | 140 | 11.67% |
| n30-switch4-router9-router3-router8-router2-switch2-n11 | 20 | 1.67% |
| n30-switch4-router9-router6-router8-router2-switch2-n11 | 20 | 1.67% |
| Total | 4071 | 100.0% |
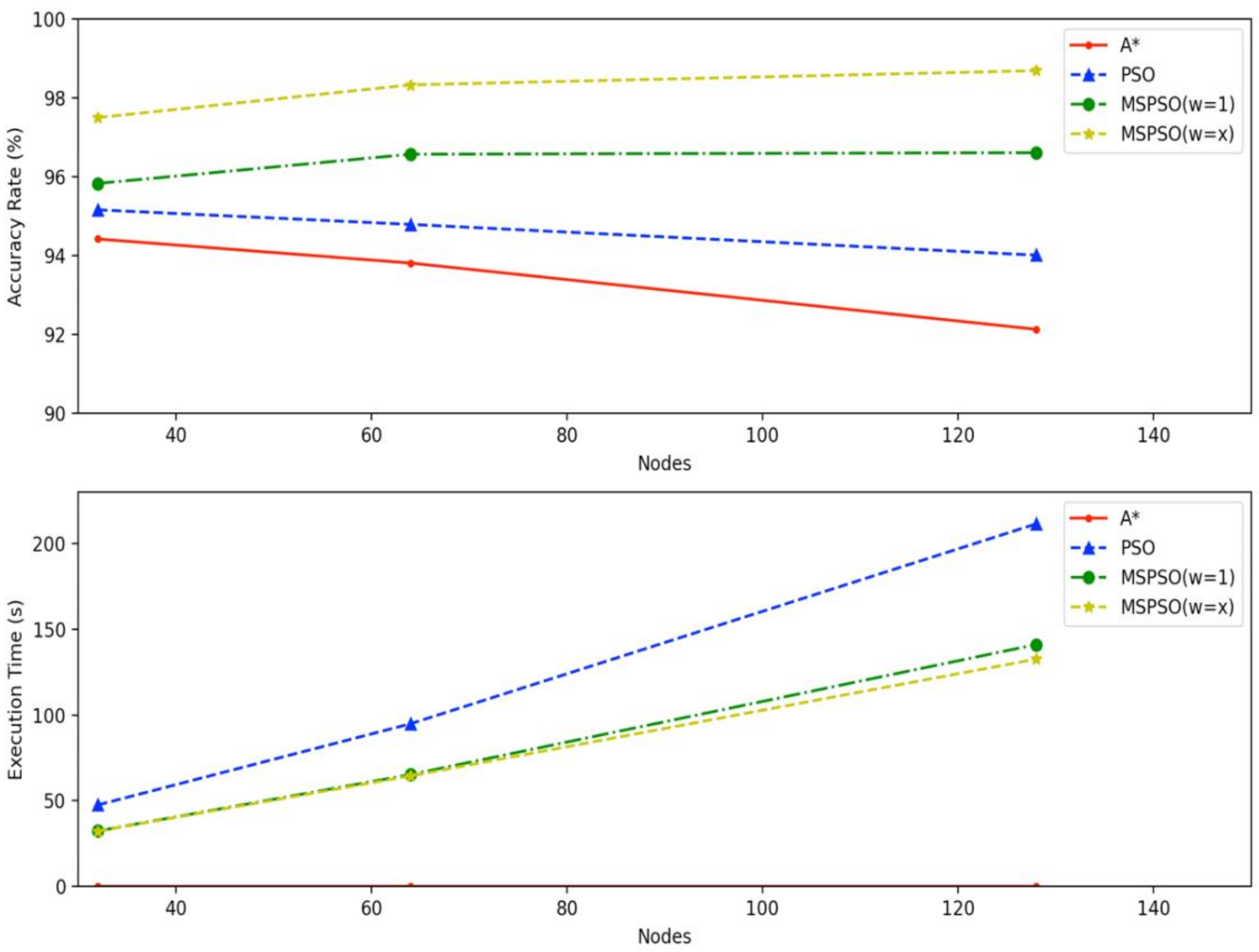
| Topology | n = 32 Nodes | n = 64 Nodes | n = 128 Nodes | |
|---|---|---|---|---|
| Scheme | ||||
| A* search algorithm | 94.42%/0.95 msec | 93.81%/4.64 msec | 92.13%/9.98 msec | |
| PSO | 95.16%/47,482.19 msec | 94.79%/396.17 msec | 94.01%/211,453.41 msec | |
| MSPSO (w = 1) | 95.83%/32,125.30 msec | 96.57%/65,209.73 msec | 96.61%/141,071.80 msec | |
| MSPSO (w = x) | 97.50%/32,202.44 msec | 98.33%/64,434.63 msec | 98.69%/132,566.52 msec | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, H.-C.; Wang, P.; Lin, W.-H.; Huang, Y.-H. A Multiple-Swarm Particle Swarm Optimisation Scheme for Tracing Packets Back to the Attack Sources of Botnet. Appl. Sci. 2021, 11, 1139. https://doi.org/10.3390/app11031139
Lin H-C, Wang P, Lin W-H, Huang Y-H. A Multiple-Swarm Particle Swarm Optimisation Scheme for Tracing Packets Back to the Attack Sources of Botnet. Applied Sciences. 2021; 11(3):1139. https://doi.org/10.3390/app11031139
Chicago/Turabian StyleLin, Hsiao-Chung, Ping Wang, Wen-Hui Lin, and Yu-Hsiang Huang. 2021. "A Multiple-Swarm Particle Swarm Optimisation Scheme for Tracing Packets Back to the Attack Sources of Botnet" Applied Sciences 11, no. 3: 1139. https://doi.org/10.3390/app11031139
APA StyleLin, H.-C., Wang, P., Lin, W.-H., & Huang, Y.-H. (2021). A Multiple-Swarm Particle Swarm Optimisation Scheme for Tracing Packets Back to the Attack Sources of Botnet. Applied Sciences, 11(3), 1139. https://doi.org/10.3390/app11031139





