Spatiotemporal Road Traffic Anomaly Detection: A Tensor-Based Approach
Abstract
1. Introduction
- -
- proposed method for the spatiotemporal road traffic patterns extraction which includes STM computation,
- -
- the usage of the tensor composed of STMs to model the traffic patterns to address the spatiotemporal nature of the traffic data,
- -
- proposed anomaly detection paradigm for the road networks based on the center of mass computation which addresses the problem of averaging many speed records into one value,
- -
- the results of the anomaly detection are evaluated on the urban road network segments in a medium-sized European city.
2. Related Work
2.1. Traffic Data Modeling
2.2. Tensor-Based Anomaly Detection Approaches
2.3. Road Traffic Anomaly Detection Approaches
3. Background
3.1. Road Network Elements and Anomaly Definitions
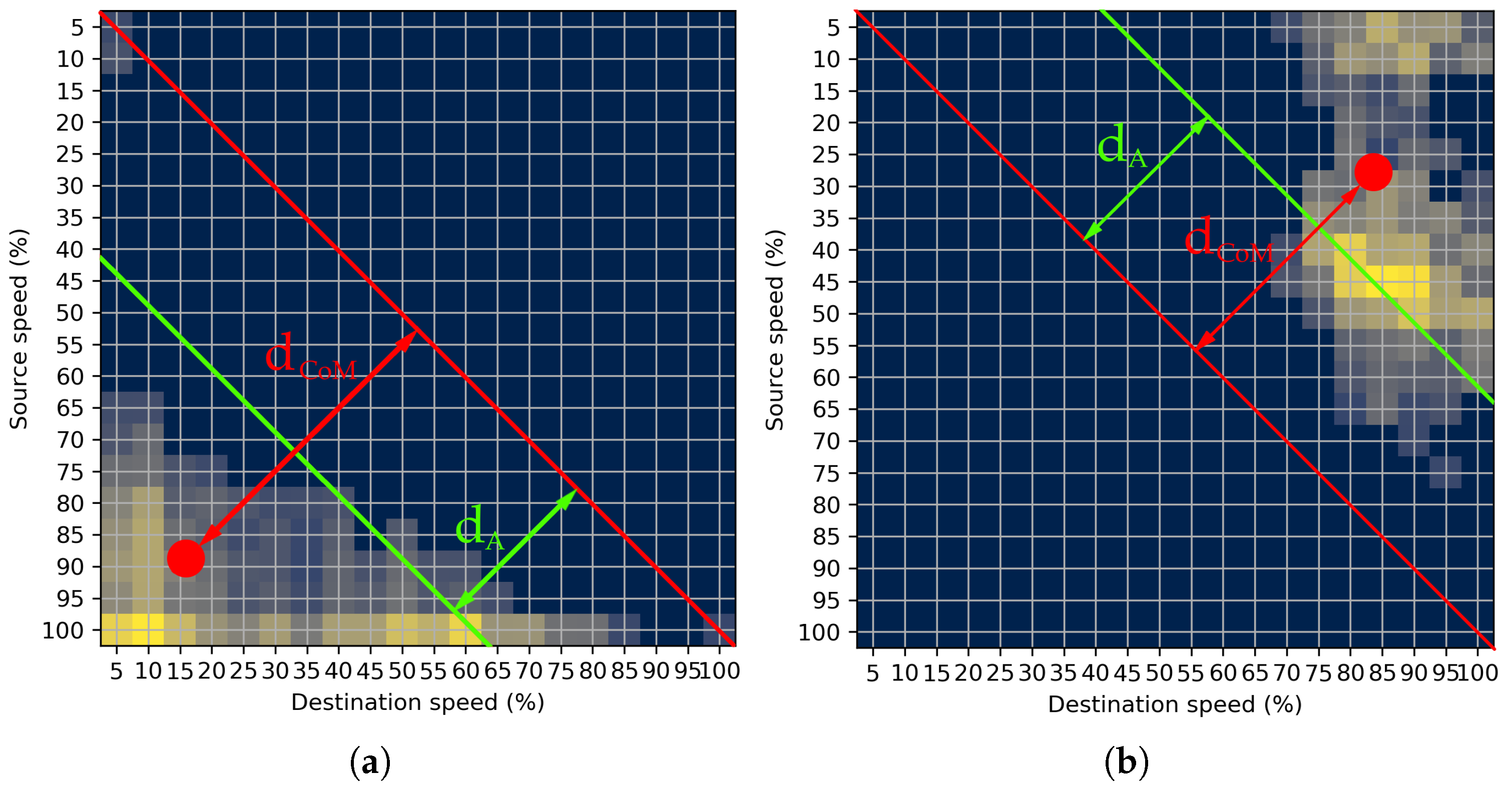
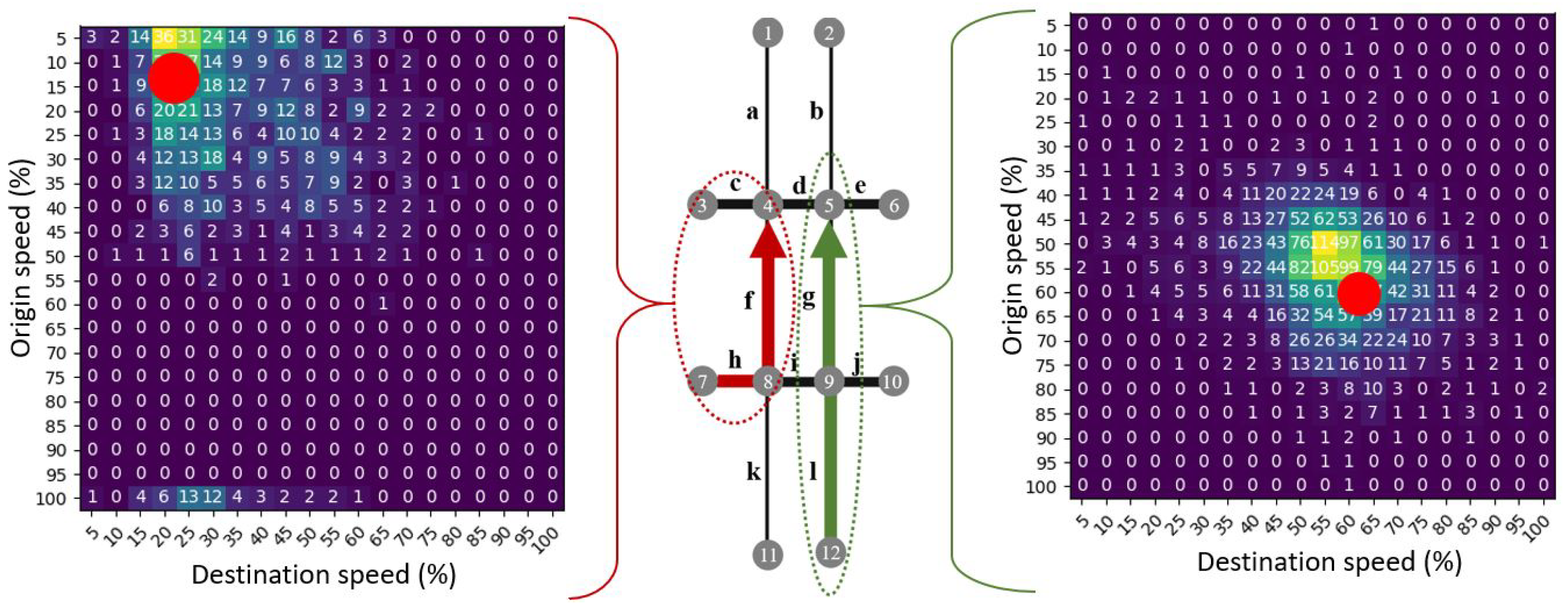
3.2. Speed Transition Matrix
3.3. Tensors
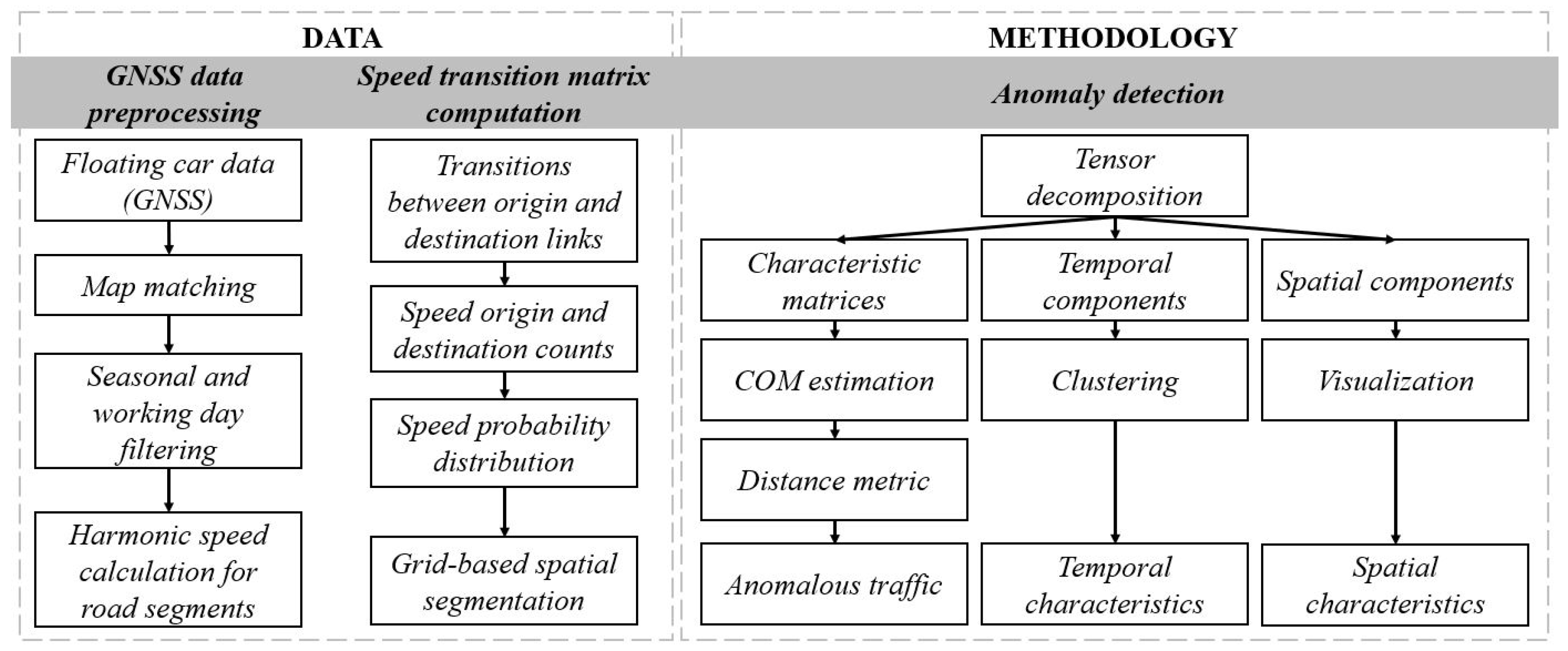
4. Methodology
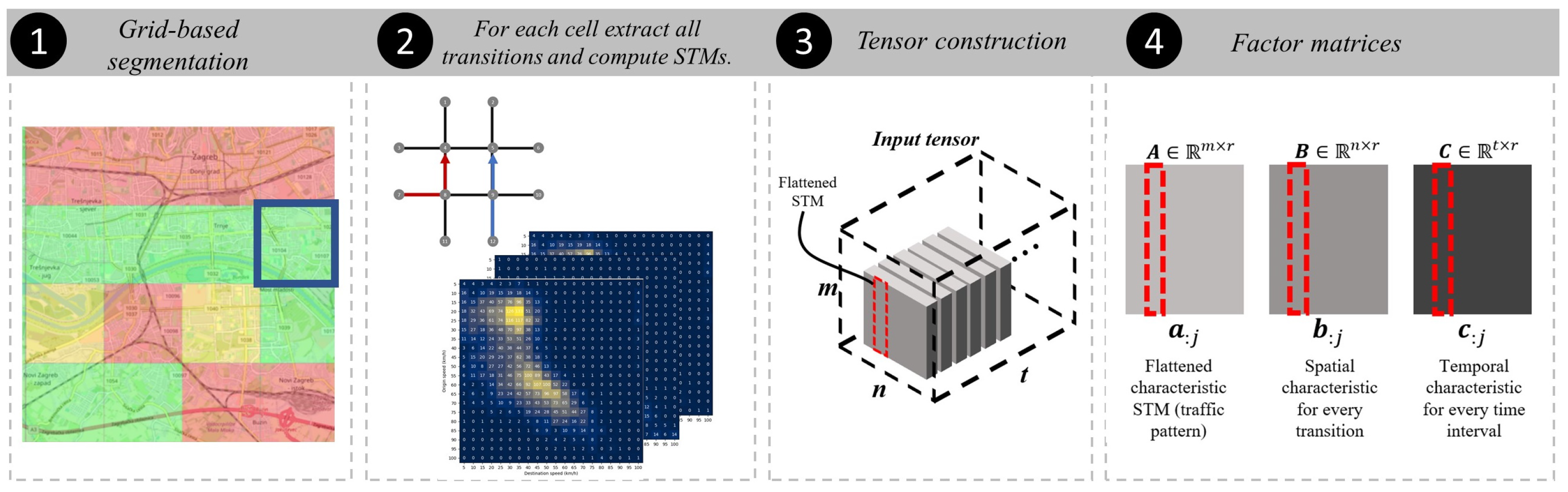
4.1. Grid-Based Map Segmentation
4.2. Tensor Construction
4.2.1. Tensor Rank Estimation
4.2.2. Factor Matrix Discussion
4.3. Anomaly Detection
| Algorithm 1 Tensor-based anomaly detection pseudo code |
Input: Spatial cells G, STMs
|
5. Results
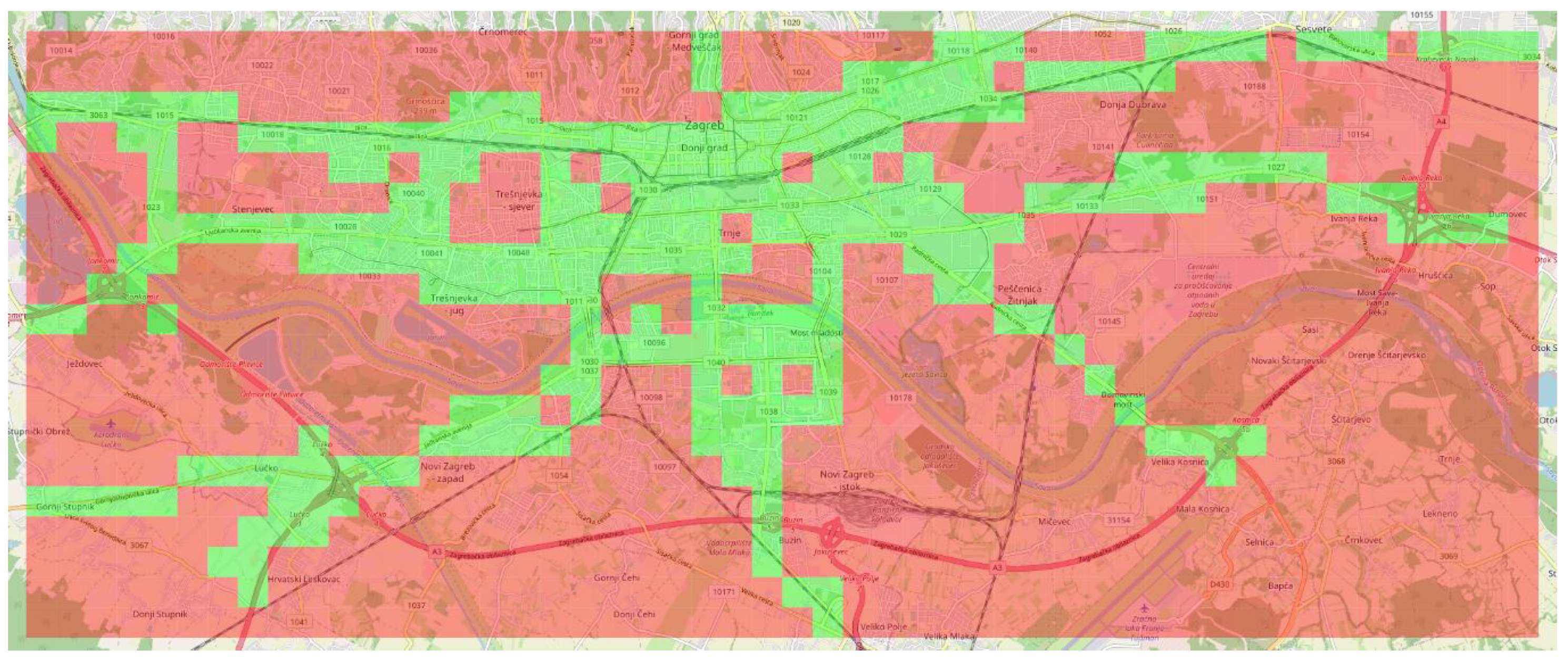
5.1. Data
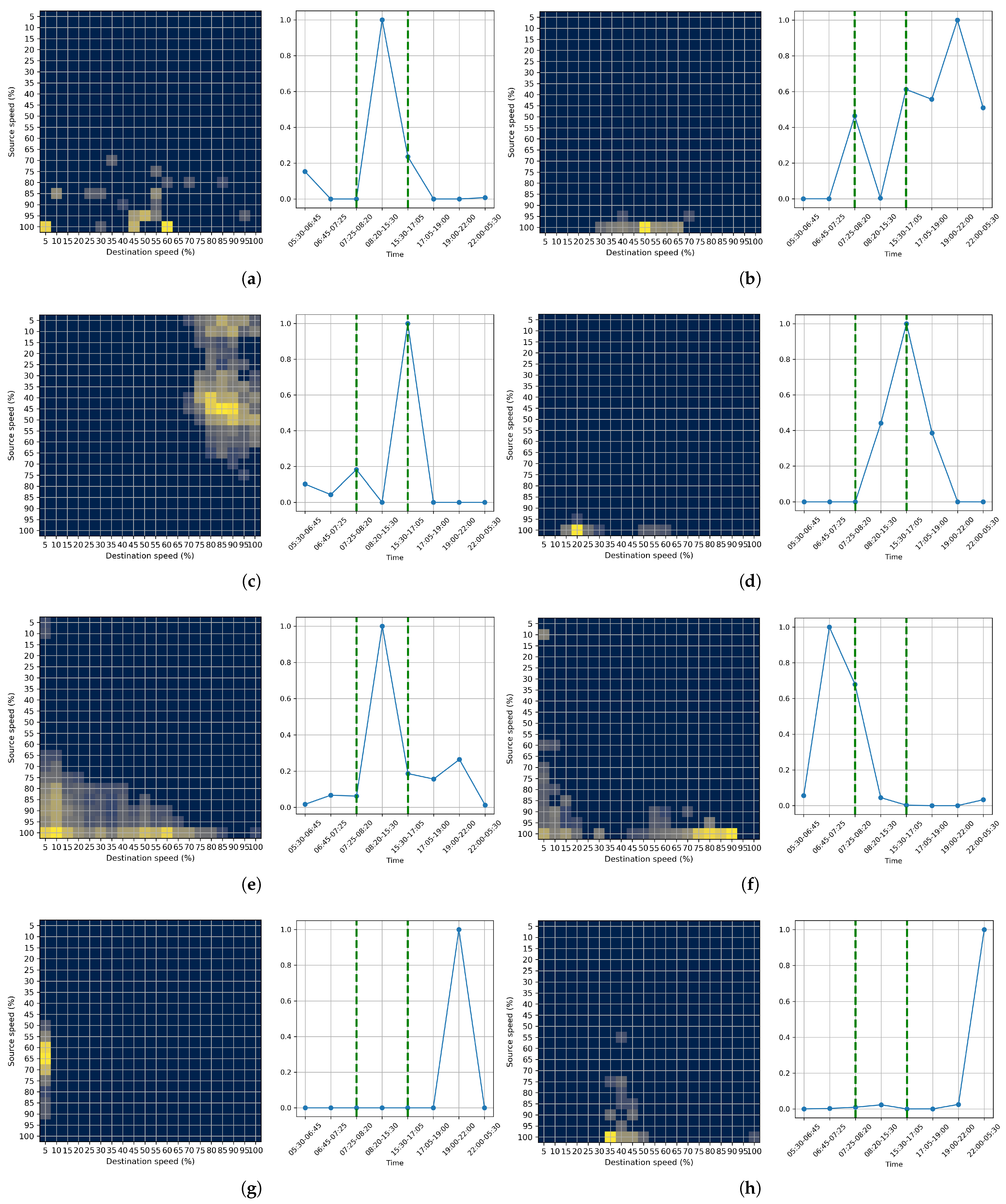
5.2. Anomalous Traffic Patterns
5.3. Domain Knowledge Validation
5.4. Comparison to Other Approaches
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| CoM | Center of Mass |
| CORCONDIA | Core Consistency Diagnostic |
| CP | CANDECOMP/PARAFAC |
| GNSS | Global Navigation Satellite System |
| HCM | Highway Capacity Manual |
| ITS | Intelligent Transport Systems |
| NTD | Non-negative Tensor Decomposition |
| O-D | Origin-Destination |
| PCA | Principal Components Analysis |
| STM | Speed Transition Matrix |
References
- Li, D.; Yang, M.; Jin, C.J.; Ren, G.; Liu, X.; Liu, H. Multi-Modal Combined Route Choice Modeling in the MaaS Age Considering Generalized Path Overlapping Problem. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2430–2441. [Google Scholar] [CrossRef]
- Tišljarić, L.; Fernandes, S.; Carić, T.; Gama, J. Spatiotemporal Traffic Anomaly Detection on Urban Road Network Using Tensor Decomposition Method. In Discovery Science; Appice, A., Tsoumakas, G., Manolopoulos, Y., Matwin, S., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 674–688. [Google Scholar]
- Erdelić, T.; Ravlić, M.; Carić, T. Travel time prediction using speed profiles for road network of Croatia. In Proceedings of the International Symposium ELMAR, Zadar, Croatia, 12–14 September 2016; pp. 97–100. [Google Scholar] [CrossRef]
- Ma, X.; Dai, Z.; He, Z.; Ma, J.; Wang, Y.; Wang, Y. Learning traffic as images: A deep convolutional neural network for large-scale transportation network speed prediction. Sensors 2017, 17, 818. [Google Scholar] [CrossRef]
- Nguyen, H.; Liu, W.; Chen, F. Discovering Congestion Propagation Patterns in Spatio-Temporal Traffic Data. IEEE Trans. Big Data 2017, 3, 169–180. [Google Scholar] [CrossRef]
- Zhang, H.; Wu, Y.; Tan, H.; Dong, H.; Ding, F.; Ran, B. Understanding and Modeling Urban Mobility Dynamics via Disentangled Representation Learning. IEEE Trans. Intell. Transp. Syst. 2020, 1–11. [Google Scholar] [CrossRef]
- Zhang, B.; Chen, S.; Ma, Y.; Li, T.; Tang, K. Analysis on spatiotemporal urban mobility based on online car-hailing data. J. Transp. Geogr. 2020, 82, 102568. [Google Scholar] [CrossRef]
- Wang, Z.; Hu, K.; Xu, K.; Yin, B.; Dong, X. Structural analysis of network traffic matrix via relaxed principal component pursuit. Comput. Netw. 2012, 56, 2049–2067. [Google Scholar] [CrossRef][Green Version]
- Fanaee-T, H.; Gama, J. Event detection from traffic tensors: A hybrid model. Neurocomputing 2016, 203, 22–33. [Google Scholar] [CrossRef]
- Xu, G.; Khan, S.; Zhu, H.; Han, L.; Ng, M.K.; Yan, H. Discriminative tracking via supervised tensor learning. Neurocomputing 2018, 315, 33–47. [Google Scholar] [CrossRef]
- Rendle, S. Factorization Machines with LibFM. ACM Trans. Intell. Syst. Technol. 2012, 3, 57. [Google Scholar] [CrossRef]
- Prada, M.A.; Dominguez, M.; Barrientos, P.; Garcia, S. Dimensionality Reduction for Damage Detection in Engineering Structures. Int. J. Mod. Phys. B 2012, 26, 1246004. [Google Scholar] [CrossRef]
- Tian, X.; Zhang, X.; Deng, X.; Chen, S. Multiway kernel independent component analysis based on feature samples for batch process monitoring. Neurocomputing 2009, 72, 1584–1596. [Google Scholar] [CrossRef]
- Fanaee-T, H.; Gama, J. EigenEvent: An Algorithm for Event Detection from Complex Data Streams in Syndromic Surveillance. Intell. Data Anal. 2015, 19, 597–616. [Google Scholar] [CrossRef]
- Gauvin, L.; Panisson, A.; Cattuto, C. Detecting the Community Structure and Activity Patterns of Temporal Networks: A Non-Negative Tensor Factorization Approach. PLoS ONE 2014, 9, e86028. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Gao, F.; Cui, P.; Li, C.; Xiong, Z. Discovering Urban Spatio-temporal Structure from Time-Evolving Traffic Networks. In Web Technologies and Applications; Chen, L., Jia, Y., Sellis, T., Liu, G., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 93–104. [Google Scholar]
- Fernandes, S.; Fanaee-T, H.; Gama, J.; Tišljarić, L.; Šmuc, T. WINTENDED: WINdowed TENsor decomposition for Densification Event Detection in time-evolving networks. Mach. Learn. 2020. [Google Scholar] [CrossRef]
- Wang, X.; Fagette, A.; Sartelet, P.; Sun, L. A Probabilistic Tensor Factorization Approach to Detect Anomalies in Spatiotemporal Traffic Activities. In Proceedings of the IEEE Intelligent Transportation Systems Conference, Auckland, New Zealand, 27–30 October 2019; pp. 1658–1663. [Google Scholar] [CrossRef]
- Tang, K.; Chen, S.; Liu, Z. Citywide spatial-temporal travel time estimation using big and sparse trajectories. IEEE Trans. Intell. Transp. Syst. 2018, 19, 4023–4034. [Google Scholar] [CrossRef]
- Tan, H.; Yang, Z.; Feng, G.; Wang, W.; Ran, B. Correlation Analysis for Tensor-based Traffic Data Imputation Method. Procedia Soc. Behav. Sci. 2013, 96, 2611–2620. [Google Scholar] [CrossRef]
- Tan, H.; Wu, Y.; Shen, B.; Jin, P.J.; Ran, B. Short-Term Traffic Prediction Based on Dynamic Tensor Completion. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2123–2133. [Google Scholar] [CrossRef]
- Pan, P.; Wang, H.; Li, L.; Wang, Y.; Jin, Y. Peak-Hour Subway Passenger Flow Forecasting: A Tensor Based Approach. In Proceedings of the 21st International Conference on Intelligent Transportation Systems, Maui, HI, USA, 4–7 November 2018; pp. 3730–3735. [Google Scholar] [CrossRef]
- Chen, X.; He, Z.; Chen, Y.; Lu, Y.; Wang, J. Missing traffic data imputation and pattern discovery with a Bayesian augmented tensor factorization model. Transp. Res. Part Emerg. Technol. 2019, 104, 66–77. [Google Scholar] [CrossRef]
- Chandola, V. Anomaly Detection: A Survey. ACM Comput. Surv. 2009, 41, 15. [Google Scholar] [CrossRef]
- Schubert, E.; Zimek, A.; Kriegel, H.P. Local outlier detection reconsidered: A generalized view on locality with applications to spatial, video, and network outlier detection. Data Min. Knowl. Discov. 2014, 28, 190–237. [Google Scholar] [CrossRef]
- Feng, Z.; Zhu, Y. A Survey on Trajectory Data Mining: Techniques and Applications. IEEE Access 2016, 4, 2056–2067. [Google Scholar] [CrossRef]
- Zheng, Y. Trajectory Data Mining: An Overview. ACM Trans. Intell. Syst. Technol. 2015, 6, 29:1–29:41. [Google Scholar] [CrossRef]
- Gupta, M.; Gao, J.; Aggarwal, C.C.; Han, J. Outlier Detection for Temporal Data: A Survey. IEEE Trans. Knowl. Data Eng. 2014, 26, 2250–2267. [Google Scholar] [CrossRef]
- Djenouri, Y.; Belhadi, A.; Lin, J.C.w.; Djenouri, D.; Cano, A. A Survey on Urban Traffic Anomalies Detection Algorithms. IEEE Access 2019, 7, 12192–12205. [Google Scholar] [CrossRef]
- Tan, P.N.; Steinbach, M.; Kumar, V. Anomaly Detection. In Introduction to Data Mining, 2nd ed.; Pearson Addison Wesley: Boston, MA, USA, 2006; pp. 651–684. [Google Scholar]
- Guo, J.; Huang, W.; Williams, B.M. Real time traffic flow outlier detection using short-term traffic conditional variance prediction. Transp. Res. Part C Emerg. Technol. 2014, 50, 160–172. [Google Scholar] [CrossRef]
- Pan, B.; Zheng, Y.; Wilkie, D.; Shahabi, C. Crowd Sensing of Traffic Anomalies Based on Human Mobility and Social Media. In Proceedings of the 21st ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems, Orlando, FL, USA, 5–8 November 2013; pp. 344–353. [Google Scholar] [CrossRef]
- Chen, S.; Wang, W.; Zuylen, H.V. A comparison of outlier detection algorithms for ITS data. Expert Syst. Appl. 2010, 37, 1169–1178. [Google Scholar] [CrossRef]
- Tišljarić, L.; Ivanjko, E.; Kavran, Z.; Carić, T. Fuzzy Inference System for Congestion Index Estimation Based on Speed Probability Distributions. Trans. Res. Proc. 2021, 55, 2021. [Google Scholar] [CrossRef]
- Kolda, T.G.; Bader, B.W. Tensor decompositions and applications. SIAM Rev. 2009, 51, 455–500. [Google Scholar] [CrossRef]
- Bro, R.; Kiers, H.A.L. A new efficient method for determining the number of components in PARAFAC models. J. Chemom. 2003, 17, 274–286. [Google Scholar] [CrossRef]
- Carić, T.; Fosin, J. Using Congestion Zones for Solving the Time Dependent Vehicle Routing Problem. Promet-Traffic Transp. 2020, 32, 25–38. [Google Scholar] [CrossRef]
- Papalexakis, E.E. Automatic Unsupervised Tensor Mining with Quality Assessment. In Proceedings of the International Conference on Data Mining, Miami, FL, USA, 5–7 May 2016; pp. 711–719. [Google Scholar] [CrossRef]
- Qi, G.; Huang, A.; Guan, W.; Fan, L. Analysis and Prediction of Regional Mobility Patterns of Bus Travellers Using Smart Card Data and Points of Interest Data. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1197–1214. [Google Scholar] [CrossRef]
- Tišljarić, L.; Carić, T.; Abramović, B.; Fratrović, T. Traffic State Estimation and Classification on Citywide Scale Using Speed Transition Matrices. Sustainability 2020, 12, 7278. [Google Scholar] [CrossRef]
- Jordaan, I.J. Decisions under Uncertainty: Probabilistic Analysis for Engineering Decisions; Cambridge University Press: Cambridge, UK, 2005; pp. 127–144. [Google Scholar]
- Hubert, M.; Vandervieren, E. An adjusted boxplot for skewed distributions. Comput. Stat. Data Anal. 2008, 52, 5186–5201. [Google Scholar] [CrossRef]
- Erdelić, T.; Ravlić, M. SORDITO—System for Route Optimization in Dynamic Transport Environment. Promet-Traffic Transp. 2016, 28, 193–194. [Google Scholar] [CrossRef][Green Version]
- Capparuccini, D.M.; Faghri, A.; Polus, A.; Suarez, R.E. Fluctuation and Seasonality of Hourly Traffic and Accuracy of Design Hourly Volume Estimates. Transp. Res. Rec. 2008, 2049, 63–70. [Google Scholar] [CrossRef]
- HCM2010. Highway Capacity Manual; Transportation Research Board, National Research Council: Washington, DC, USA, 2010. [Google Scholar]
- Lin, C.; Zhu, Q.; Guo, S.; Jin, Z.; Lin, Y.R.; Cao, N. Anomaly detection in spatiotemporal data via regularized non-negative tensor analysis. Data Min. Knowl. Discov. 2018, 32, 1056–1073. [Google Scholar] [CrossRef]
- Lykov, S.; Asakura, Y. Anomalous Traffic Pattern Detection in Large Urban Areas: Tensor-Based Approach with Continuum Modeling of Traffic Flow. Int. J. Intell. Transp. Syst. Res. 2018, 18, 13–21. [Google Scholar] [CrossRef]
- Chen, L.; Jakubowicz, J.; Yang, D.; Zhang, D.; Pan, G. Fine-Grained Urban Event Detection and Characterization Based on Tensor Cofactorization. IEEE Trans. Hum.-Mach. Syst. 2017, 47, 380–391. [Google Scholar] [CrossRef]
- Vrbanić, F.; Ivanjko, E.; Kušić, K.; Čakija, D. Variable Speed Limit and Ramp Metering for Mixed Traffic Flows: A Review and Open Questions. Appl. Sci. 2021, 11, 2574. [Google Scholar] [CrossRef]
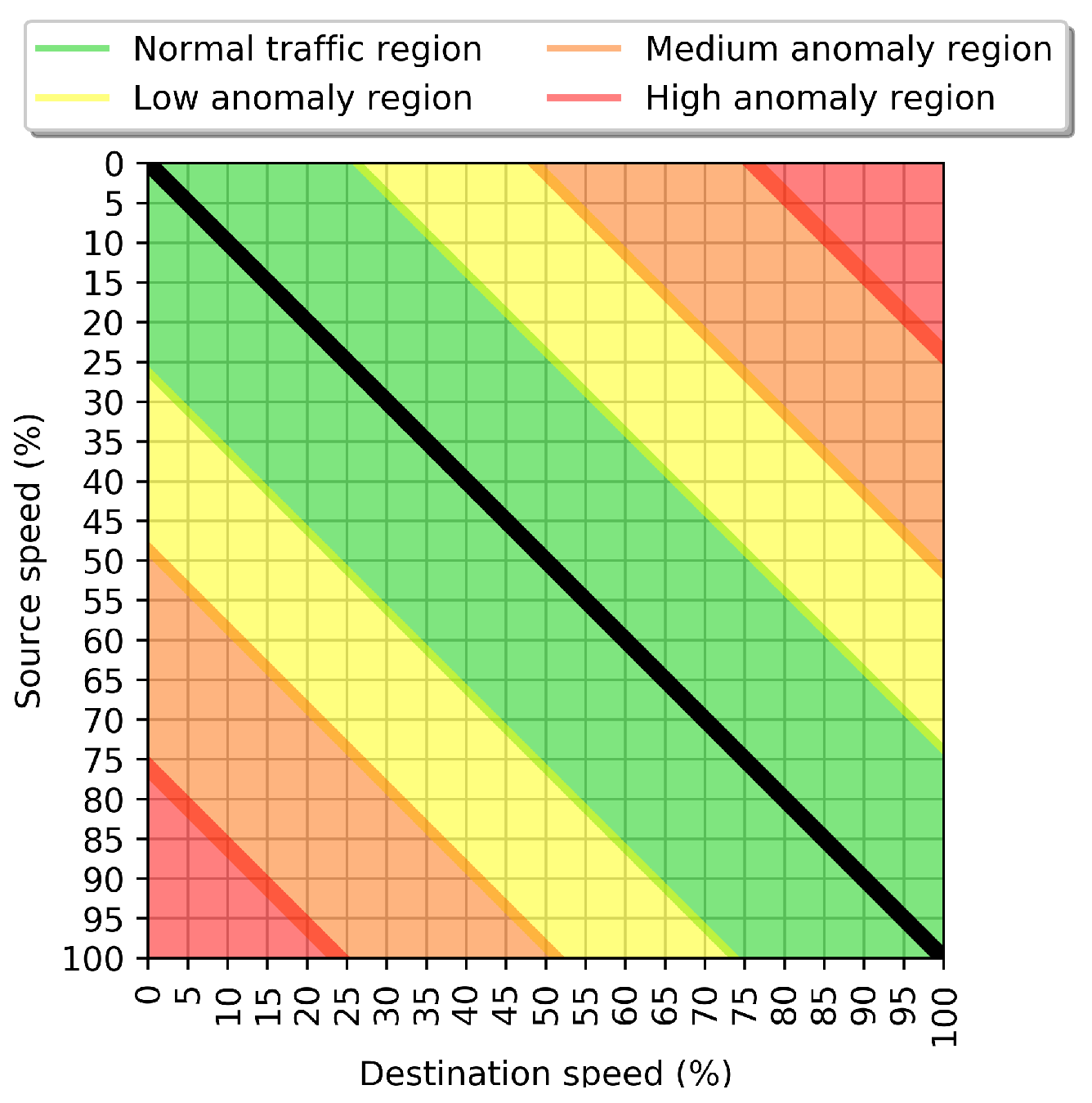
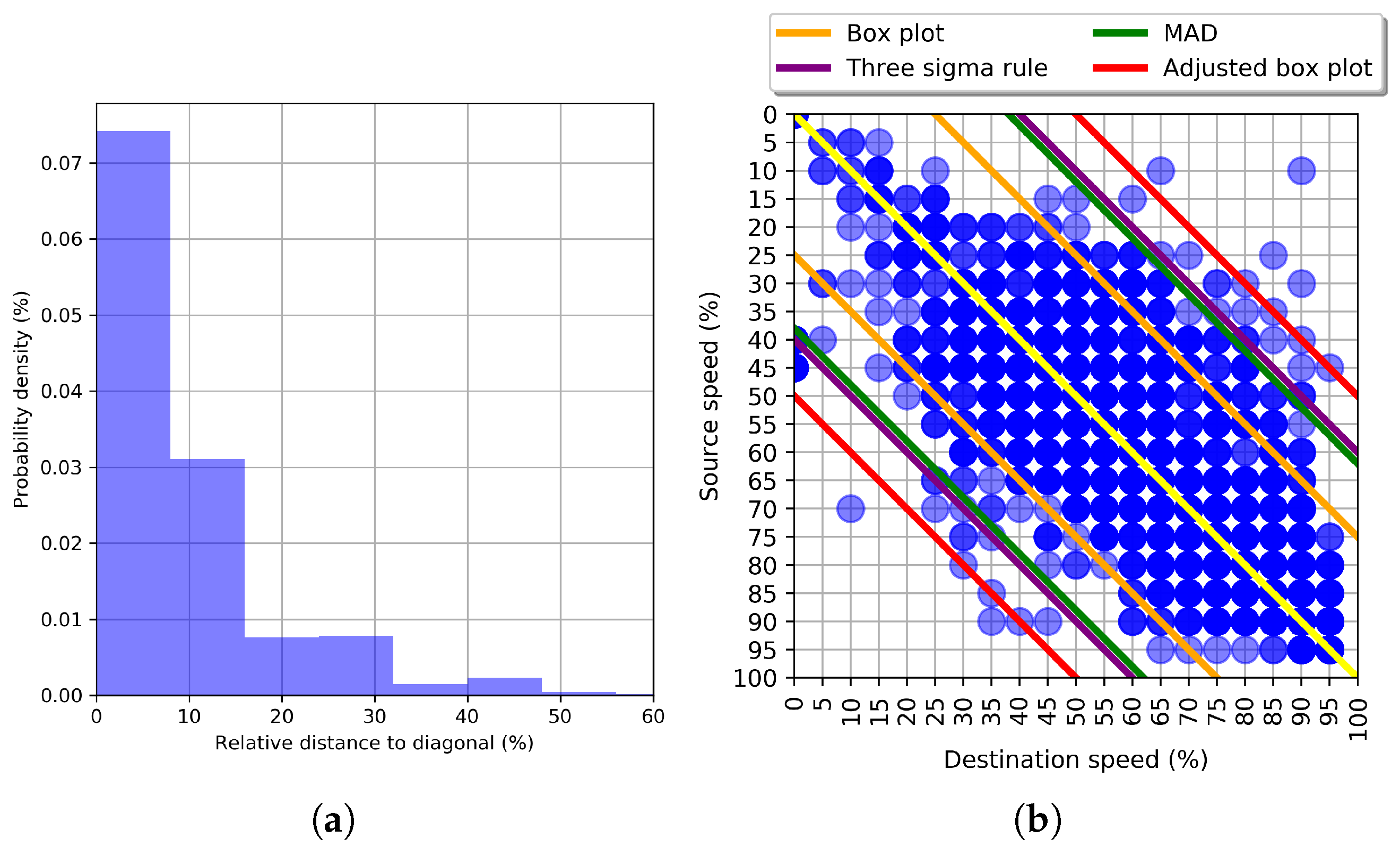

| Method | N. Anomalies Detected | Bounds |
|---|---|---|
| Box plot | 261 | |
| Three sigma rule | 58 | |
| MAD | 58 | |
| Adjusted Box plot | 8 |
| Number of GNSS traces | 6.55 billion |
| Sampling rate | 100 m/5 min |
| Time-span | August 2008–October 2014 |
| Number of vehicles | 4200 |
| Number of road segments (Croatia) | 2,000,000 |
| Number of road segments (Zagreb) | 86,900 |
| Anomalous STMs | Normal STMs | Precision | Recall | F-1 |
|---|---|---|---|---|
| 500 | 500 | 90.14% |
| Literature | Data Type | Traffic Parameter | Anomaly Detection |
|---|---|---|---|
| Fanaee et al. [9] | O-D matrices (car) | Traffic volume | Traffic flow or topology |
| Wang et al. [18] | O-D matrices (car) | Traffic volume | Traffic Flow |
| Lin et al. [46] | O-D matrices (car) | Traffic volume | Event detection |
| Chen et al. [48] | GNSS (bicycle) | Traffic volume | Event detection |
| Lykov et al. [47] | Simulation (car) | Traffic speed | Traffic patterns |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tišljarić, L.; Fernandes, S.; Carić, T.; Gama, J. Spatiotemporal Road Traffic Anomaly Detection: A Tensor-Based Approach. Appl. Sci. 2021, 11, 12017. https://doi.org/10.3390/app112412017
Tišljarić L, Fernandes S, Carić T, Gama J. Spatiotemporal Road Traffic Anomaly Detection: A Tensor-Based Approach. Applied Sciences. 2021; 11(24):12017. https://doi.org/10.3390/app112412017
Chicago/Turabian StyleTišljarić, Leo, Sofia Fernandes, Tonči Carić, and João Gama. 2021. "Spatiotemporal Road Traffic Anomaly Detection: A Tensor-Based Approach" Applied Sciences 11, no. 24: 12017. https://doi.org/10.3390/app112412017
APA StyleTišljarić, L., Fernandes, S., Carić, T., & Gama, J. (2021). Spatiotemporal Road Traffic Anomaly Detection: A Tensor-Based Approach. Applied Sciences, 11(24), 12017. https://doi.org/10.3390/app112412017








