Abstract
Quantum qubit commitment is a stronger version of the quantum bit commitment. It is impossible to realize unconditionally secure quantum qubit commitment in nonrelativistic domain. In this paper, we propose an unconditionally secure relativistic quantum qubit commitment protocol for the first time, which will have some unique applications in the upcoming era of quantum network.
1. Introduction
Quantum bit commitment [1,2] is a cryptographic mistrustful task between two adversarial parties, in which, the committer Alice decides the value of the bit b (b = 0 or 1) that she wants to commit to the receiver Bob, and sends him some quantum encrypted information about the bit for evidence, e.g., some quantum states, in the commit phase. Later, in the unveil phase, Alice announces the correct value of b as well as some information for decrypting the evidence, then Bob decrypts the evidence and checks whether the decryption output value of b is consistent with Alice’s announcement. If a quantum bit commitment protocol is secure against both Bob and Alice, and its security does not rely on any computational assumption, it is said to be unconditionally secure. Secure quantum bit commitment is an essential cryptographic primitive in quantum cryptography. It could be used as a building block for protocols implementing a wide range of other cryptographic tasks [3,4,5]. However, within the framework of nonrelativistic quantum mechanics, unconditionally secure quantum bit commitment is impossible since the perfect securities against Alice and Bob are incompatible, which is known as Mayers–Lo–Chau (MLC) no-go theorem [6,7]. Though there are some doubts on the generality of the theoretical model of quantum bit commitment used in the no-go proof and, new protocols attempting to evade the no-go theorem were proposed every now and then, the result of MLC no-go theorem is widely accepted nowadays, which was introduced in detail in ref. [8]. It is considered as a serious drawback in quantum cryptography, as it tells us when the rapid development of quantum computers makes the computational assumptions underlying present day classical bit commitment become distinctly vulnerable, the quantum cryptography cannot offer any compensating solution [9]. Fortunately, it was proved later that by imposing causal restrictions via relativistic quantum mechanics, unconditionally secure quantum bit commitment is possible [10,11,12,13].
Recently, quantum qubit commitment, a stronger version of the quantum bit commitment, was introduced in Ref. [14]. It was found that the quantum qubit commitment has some unique applications [15] beyond quantum bit commitment in the upcoming era of quantum network, including implementing a fair version of quantum state exchange [16] and preventing cheating in such a task that two quantum computers are demanded to generate certain quantum states independently and to be cross-checked afterward [17], in which one computer may try to delay to generate its state after the other party and cheat by learning from the other party’s state or even try to imperfectly clone the state to pretend to have high computational power. It was also pointed out [15] that secure quantum qubit commitment can break asynchronous quantum network assumption since it can effectively activate multiple quantum machines at the same time. These unique applications motivate the wide range of interest of developing unconditional security quantum qubit commitment protocols. However, it is found that, similar to quantum bit commitment, it is impossible to realize unconditionally secure quantum qubit commitment in nonrelativistic domain [14]. Naturally, as a consequence, researchers attempt to develop security quantum qubit commitment schemes via adding some additional experimental constraints or causal restrictions of relativistic quantum mechanics. In Ref. [15], a secure quantum qubit commitment scheme is proposed by using the approach of quantum one-time tables, in which a trusted third party is needed. To the best of our knowledge, however, it remains an open question whether unconditionally secure quantum qubit commitment protocol can be realized in relativistic domain. Therefore, it is both theoretically interesting and practically valuable to develop unconditional security relativistic quantum qubit commitment protocols, which must be in line with and will promote the development of the upcoming era of quantum network [18]. Stimulated by this, in this paper we focus on and, for the first time, propose an unconditionally secure relativistic quantum qubit commitment scheme.
Before giving our protocol, we first explain some details of the concepts of quantum qubit commitment and unconditional security that we used throughout this paper. In quantum qubit commitment, instead of a bit, Alice commits to a qubit from a certain set (that can potentially also contain nonorthogonal quantum states), and later unveils to Bob that she has indeed committed to that qubit [14]. The qubit set should be open, since if the qubits are prepared by a third party and are unknown to Alice, she cannot unveil the quantum state of the committed qubit in the unveil phase. The fundamental difference between quantum qubit commitment and quantum bit commitment is that a quantum qubit commitment protocol preserves the coherence of the committed quantum state, therefore, to commit to a specific qubit in the commit phase, Alice should present quantum states (obtained via appropriate unitary transformations of the committed qubit) rather than the quantum-encrypted classical information of the qubit to Bob for evidence (if she presents the quantum-encrypted classical information for evidence, it is essentially a quantum bit string commitment).
In Ref. [15], the authors defined that a quantum qubit commitment scheme is unconditionally secure if, without any assumption on computational power, its output is indistinguishable from the output of an instance of the ideal functionality unless the probability of the committer passing the unveil phase is lower than a certain threshold which can be made arbitrarily small by increasing the security parameters. Here we give a more straightforward mathematical description as: a quantum qubit commitment scheme is unconditionally secure if it guarantees with as , where N is the security parameter and is the probability of successfully unveiling the kth qubit of the qubit set in the unveil phase. It should be noted that is the probability of successfully unveiling the k1th qubit when Alice committed to the kth qubit in the commit phase, which can be made arbitrarily small by choosing the security parameters appropriately but cannot be zero. will reduce to be when there are only two qubits in the qubit set, which is the unconditionally secure condition of quantum bit commitment.
2. Quantum Qubit Commitment Scheme
In this section, we show our protocol. The relativistic geometry of our protocol is chosen to be same as that of Ref. [10], i.e., Alice and Bob agree on a fixed inertial reference frame with coordinates (x, y, z, t), within which the space-time point O is the origin and two points Q0 = (−x, 0, 0, x) and Q1 = (x, 0, 0, x) are lightlike separated from O (see Figure 1). Alice and Bob each have agents, separated in their own secure laboratories, adjacent to each of the points O, Q0, and Q1.
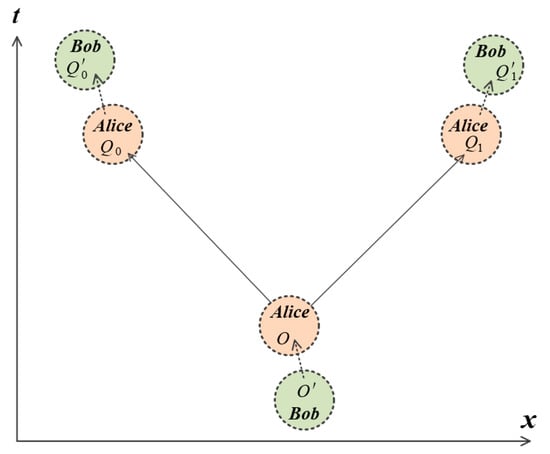
Figure 1.
A nonideal implementation of the protocol. (Not to scale.) Alice and Bob control disjoint regions of space-time, representing their respective secure laboratories. Bob generates random Bell states at and shares them (dashed arrow) to Alice at point . At point , Alice then teleports the committed qubit to Bob and transmits the teleportation measurement outcomes via secure light-speed channels (solid arrows) to her agents at the points , who relay them (dotted arrows) to Bob’s agents at the nearby points .
Before the commitment, Alice and Bob agree on a security parameter N, and a public fixed qubit set , where is an orthonormal basis in space, and are complex weight factors, and d is the number of the qubits in the set. In our protocol, the qubit set is constrained by two restrictive conditions: (1) any two of the four qubits and cannot be selected as elements of the qubit set at the same time for arbitrary and parameters; (2) any two elements, and , of the qubit set should satisfy , where is the probability of the channel errors. Any set satisfying the above two restrictive conditions can be used as a qubit set of our protocol. The second restrictive condition is related to the non-ideal case that there exist channel errors. In the following, we first present our protocol in an idealized form and ignore the second restrictive condition. In the ideal case, we assume perfect state preparations, transmissions, and measurements. We also make idealizations about the relativistic geometry and signaling speed as Ref. [10], supposing that Alice can signal at precisely light speed, all information processing is instantaneous, and the distances from both parties’ labs to the relevant points O, Q0, and Q1 are infinitesimal and can be considered to be negligible.
Commit: In the commit phase, Bob prepares securely a set of qubits independently randomly chosen from Bell states and keeps them private.
At point O, Bob sends qubits A () of his Bell states to Alice and keeps qubits B () to himself. To commit to a qubit in space, Alice carries out teleportation via measuring qubits X () and A collectively in the Bell basis resulting qubits B on Bob’s side collapse to and with equal probability, and sends over secure channels to her agents at Q0 and Q1 the outcomes of the collective measurement of qubits X and A. In this stage, the collapsed states of qubits B act as the evidence of the commitment and preserve the coherence of the committed qubit; and the outcomes of the collective measurement carry the information that which specific state of each qubits B has collapsed to and determine the unitary transformations that can transform the collapsed states to the state (that is equal to the committed qubit). The outcomes can be represented by binary numbers, and it can be transmitted by using secure classical channels, which can be built by presharing one-time pads between her agent at O and those at Q0 and Q1 and sending pad-encrypted classical signals.
Unveil: Alice’s agents at Q0 and Q1 announce the classic information of the committed qubit and the outcomes of the collective measurement to adjacent Bob’s agents to unveil the commitment. Bob carries out the unitary transformations determined by the outcomes to the corresponding collapsed qubits B in his possession to transform each of them to the state and decides whether to accept the commitment and unveiling as genuine or not by comparing the announced information and checking the transformed state at somewhere in the intersection of the future light cones of Q0 and Q1. If the declared outcomes on both wings are the same and Bob’s measurement results of are consistent with the announced committed qubit, Bob accepts the commitment. Otherwise, Bob concludes that Alice cheated and rejects her commitment.
3. Security of the Protocol
In this section, we prove the unconditional security of our protocol. Since Alice does not send any quantum and classical information to Bob before the unveiling, the protocol is obviously secure against Bob. It is because no matter what strategy Bob takes (including the strategy that Bob prepares any kind of quantum state), any local measurement performed in Alice’s side does not change the reduced density matrix of the qubits in Bob’s side, so Bob cannot get any information about the committed qubit by only measuring the qubits in his side before the unveiling. From another perspective, the security against Bob is guaranteed by the theorem of impossibility of superluminal signaling. Since if Bob can learn something about the committed qubit before the unveiling, it means that an Alice in a distant location can send information to Bob simply by measuring the qubits on her side, which is essentially superluminal signaling. Hence, in our protocol, Bob can learn nothing about Alice’s choice until she chooses to unveil the qubit.
The security of this protocol against Alice should be discussed in different cases. The first case is that Alice follows the honest strategy at point O. In this case, she cannot change the collapsed states of qubits B again after O, but she is free to pretend that one original input qubit (committed qubit) from and is any one of the three remaining ones of the four qubits just by properly interchanging her results of the collective measurement of qubits X and A. For example, she can pretend that the input qubit is by interchanging her measurement results with , and with . However, because of the prior agreement that any two of the four qubits and cannot be selected as the elements of the qubit set at the same time, Alice’s cheating has no positive significance if qubit is one of the element of the qubit set. The reverse case is that Alice’s input qubit is not the element of the qubit set while she unveils the right one, such as qubit . From the perspective of the input, this is of course cheating. Although such cheating does not increase Alice’s probability of successfully revealing any correct qubit, it cannot be prohibited. However, from the perspective of the output, no matter which of the four qubits Alice inputs, the output is that qubits B on Bob’s side collapse to and with equal probability, implying the four inputs are equivalent. In the second scenario, we ask if it is possible for Alice to pretend that the input qubit is another qubit with parameters different from and , such as . If she tries to do this, she needs to pretend that the string of qubit within the collapsed qubits B is the string of . The results of Ref. [19] show that once the density matrix of the qubit string is fixed, the probabilities of Bob accepting a revelation of the string of satisfy , where can be made arbitrarily small by choosing the security parameters appropriately, therefore Alice has no successful strategy for such cheating.
Second, in the case that Alice does not follow the honest strategy at point O, we can suppose that some operations are carried out at this point, but they leave her significantly uncommitted and retain as much freedom as possible in her choice of which qubit to unveil. We then further suppose that in the causal future of O, all the strategies that the agent on the line segment can follow form a set and the probabilities of successfully unveiling the qubit when the agent on the line segment performs the strategy while the other agent on the line segment performs is . Similar to the discussion in the case that Alice follows the honest strategy at point O, by the results of Ref. [19] again, when the two agents follow and strategies, once the qubits B collapse to the states corresponding to the committed qubit , there should exist no cheating strategy for Alice to successfully unveil any other qubit unless the probability of passing the unveil phase is lower than a certain threshold which can be made arbitrarily small by increasing the security parameters, therefore the sum of the probabilities of successfully unveiling all the qubits of the public fixed qubit set except when the two agents follow and strategies must be less than , resulting in . Moreover, by Minkowksi causality, any operations carried out on the half-open line segment cannot affect the operations carried out on the half-open line segment , and vice versa. The agent at can only guess the strategy that the agent at follows with probability , which must be agreed by the two agents at or before O or decided by the agent at Q1 alone, hence satisfies . Therefore, the probability of successfully unveiling the qubit in the unveil phase is , where is the probability of the agent at following when the agent at follows , which must satisfy . Combining the three conditions , , and , we have . This is consistent with our above mathematical definition of unconditionally secure of a quantum qubit commitment.
4. Discussion of Qubit Certification
Classical certification [20,21] is a well-known constraint that a quantum cryptographic protocol guarantees to all the other parties that one party is restricted so that, to avoid being detected as cheating, his quantum inputs must take the form of pure states of the basis elements of a public fixed basis of the appropriate d-dimensional input space. Here, as the qubit set in the quantum qubit commitment is not always a set of orthonormal bases in space, we define qubit certification, a new constraint similar to classical certification, that a protocol guarantees to all the other parties that one party is restricted so that his quantum inputs must be a specific qubit of the public fixed set, which can be described as, in a quantum qubit commitment, that any unveiled qubit commitments necessarily have a definite committed qubit choosing from the public set. Like all technologically unconstrained quantum bit commitment protocols, [9,12] do not force Alice to commit to a specific bit, the protocol here does not force to commit to a specific qubit, as it does not prevent Alice from preparing states in entangled with other system with the form , where is a set of orthonormal bases. In the commitment, Alice can choose to keep the states in quantum entanglement, and input as the committed qubit and store the entangled state and then measure it in the computational basis until unveiling. In this case there is a definite committed qubit without being detected cheating, but from Alice’s perspective the unveiled qubit remains unknown with subjective probabilities obeying . It does not rule out the case that Alice’s measurement result of qubit C is but she successfully unveils qubit , or even the case that she prepares states entangling the subset of () with , i.e., satisfying , but successfully unveils a qubit , with a probability , which can be made arbitrarily small by choosing the security parameters appropriately as there is no any measurement result that could act as an evidence to support Alice to obtain a successful probability of unveiling this qubit higher than the successful probability of just guessing by chance. Hence, we say a quantum qubit commitment protocol with a security parameter N is unconditionally secure when it guarantees with as . It is the complete mathematical definition of unconditionally secure of a quantum qubit commitment that we presented above.
5. The Non-Ideal Case in Practical Application
The protocol proposed above is idealized with some ideal assumptions. In this section, we discuss the non-ideal case in practical application. Realistically, it is not possible for Alice and Bob to have secure access to precisely the same space–time point to exchange a qubit; Alice cannot signal at precisely light speed; and information cannot be processed instantaneously. In a realistic implementation, all the corrections about the idealized assumptions of these aspects will introduce time delays at various stages of the protocol. The effects of these time delays can be discussed same as the other relativistic protocols [9,12]. If the corrections are small, the protocol remains secure and the only significant effect is that Alice can only persuade Bob that her commitment is binding from some point in the near causal future of O, rather than from O itself [9,12].
Realistically, too, perfect state preparations, transmissions, and measurements are impossible with unavoidable channel losses and errors. A low possibility of losses does not affect the security since the security parameter N of the protocol implies essentially committing N copies of the qubit, hence Bob can always be able to receive enough evidence qubits to finally check Alice’s unveiling. To deal with the channel errors, we consider that the two qubits and are two arbitrary elements of the public qubit set . If Alice attempts to cheat to pretend that the committed qubit is in a concrete implementation, she needs to persuade Bob that the strings of and within the collapsed qubits B are the strings of and , respectively. Let be the probability of Bob accepting a revelation of for the ith . We have , and the probability that Alice is detected cheating in unveiling is . If the probability of the channel errors is bigger than , Alice can always claim that the error was due to channel errors, even if she did cheat. Therefore, Bob can be guaranteed that Alice’s commitment is binding only when . Since it can be found that in our protocol, it finally becomes , which gives, to counter the channel errors, a definite constraint in determining the qubit set. When this constraint condition is satisfied, the channel errors make no essential difference as long as they are small and Bob needs only to check that Alice’s revelation is statistically consistent with the output corresponding to the unveiled qubit and statistically inconsistent with the other. In practical application, we think that is good enough to implement our protocol. To illustrate this constraint more visually, we suppose that and are two qubits in the qubit set and in a practical application, hence we have . In this case, the constraint requires , i.e., the angle is not smaller than .
6. Conclusions and Discussion
Quantum qubit commitment is a rather new concept, which was first proposed in 2018 [14]. It was pointed out in 2021 [15] that the quantum qubit commitment has some unique and important applications beyond quantum bit commitment in the upcoming era of quantum network. Therefore, it is both theoretically interesting and practically valuable to develop unconditional secure quantum qubit commitment protocols. In this paper, we proposed an unconditionally secure relativistic quantum qubit commitment protocol for the first time. Comparing to the existed quantum bit commitment, our protocol does not destroy the coherence of the committed qubit (the collapsed states of qubits B preserve the coherence of the committed qubit). This is the fundamental difference between quantum qubit commitment and quantum bit commitment.
Since quantum qubit commitment is a stronger version of the quantum bit commitment, our quantum qubit commitment protocol of course can be used to fulfill quantum bit commitment. However, to preserve the coherence of the committed qubit, when our protocol is used to execute a quantum bit commitment, it needs more quantum resources (quantum entanglement in our protocol) than the dedicated quantum bit commitment protocols [9,10,12]. This is the limitation of our protocol.
In the last two decades, relativistic quantum cryptography has become an important branch of quantum physics. Numerous researchers have carried out a great deal of research in this field, including revealing information causality as a physical principle in quantum physics [22] as well as developing relativistic quantum protocols with wide range of important applications, such as quantum tokens [23] and quantum tagging [24]. As our proposed protocol is the first unconditionally secure relativistic quantum qubit commitment scheme, we think that it comes timely in the rapid development of relativistic quantum cryptography and will help stimulate further interest in the theory and practical implementation of this field.
Author Contributions
Conceptualization, H.L. and L.Y.; funding acquisition, H.L. and L.Y.; investigation, H.L.; writing—original draft, H.L.; writing—review and editing, H.L. and L.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Key Research and Development Program of China (Grant No. 2019YFB2203903), the National Natural Science Foundations of China (Grant No. 62065006), the Natural Science Foundation of Guangxi (Grants No. 2019GXNSFAA245024 and No. 2020GXNSFBA159059), the Science and Technology Project of Guangxi (Grant No. AD19245064), Guangxi Key Laboratory Project of Optoelectronic Information Processing (Grant No. GD20103), and Guangxi Key Laboratory Project of Automatic Detection Technology and Instrument (Grant No. YQ20103).
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bengalore, India, 9–12 December 1984; IEEE: New York, NY, USA, 1984; pp. 175–179. [Google Scholar]
- Brassard, G.; Crepeau, C.; Jozsa, R.; Langlois, D. A quantum bit commitment scheme provably unbreakable by both parties. In Proceedings of the IEEE 34th Annual Foundations of Computer Science, Palo Alto, CA, USA, 3–5 November 1993; pp. 362–371. [Google Scholar]
- Bennett, C.H.; Brassard, G.; Crépeau, C.; Skubiszewska, M.-H. Practical Quantum Oblivious Transfer. In CRYPTO ’91: Proceedings of the 11th Annual International Cryptology Conference on Advances in Cryptology; Springer: Berlin/Heidelberg, Germany, 1992; pp. 351–366. [Google Scholar]
- Kent, A. Location-oblivious data transfer with flying entangled qudits. Phys. Rev. A 2011, 84, 012328. [Google Scholar] [CrossRef]
- Molina-Terriza, G.; Vaziri, A.; Ursin, R.; Zeilinger, A. Experimental Quantum Coin Tossing. Phys. Rev. Lett. 2005, 94, 040501. [Google Scholar] [CrossRef] [PubMed]
- Lo, H.-K.; Chau, H.F. Is Quantum Bit Commitment Really Possible? Phys. Rev. Lett. 1997, 78, 3410–3413. [Google Scholar] [CrossRef]
- Mayers, D. Unconditionally Secure Quantum Bit Commitment is Impossible. Phys. Rev. Lett. 1997, 78, 3414–3417. [Google Scholar] [CrossRef]
- He, G.P. Quantum key distribution based on orthogonal states allows secure quantum bit commitment. J. Phys. A Math. Theor. 2011, 44, 445305. [Google Scholar] [CrossRef]
- Kent, A. Unconditionally Secure Bit Commitment. Phys. Rev. Lett. 1999, 83, 1447–1450. [Google Scholar] [CrossRef]
- Kent, A. Unconditionally Secure Bit Commitment by Transmitting Measurement Outcomes. Phys. Rev. Lett. 2012, 109, 130501. [Google Scholar] [CrossRef] [PubMed]
- Liu, Y.; Cao, Y.; Curty, M.; Liao, S.-K.; Wang, J.; Cui, K.; Li, Y.-H.; Lin, Z.-H.; Sun, Q.-C.; Li, D.-D.; et al. Experimental Unconditionally Secure Bit Commitment. Phys. Rev. Lett. 2014, 112, 010504. [Google Scholar] [CrossRef] [PubMed]
- Kent, A. Unconditionally secure bit commitment with flying qudits. New J. Phys. 2011, 13, 113015. [Google Scholar] [CrossRef]
- Lunghi, T.; Kaniewski, J.; Bussières, F.; Houlmann, R.; Tomamichel, M.; Kent, A.; Gisin, N.; Wehner, S.; Zbinden, H. Experi-mental bit commitment based on quantum communication and special relativity. Phys. Rev. Lett. 2013, 111, 180504. [Google Scholar] [CrossRef] [PubMed]
- Modi, K.; Pati, A.K.; Sen, A.; Sen, U. Masking Quantum Information is Impossible. Phys. Rev. Lett. 2018, 120, 230501. [Google Scholar] [CrossRef] [PubMed]
- Lie, S.H.; Kwon, H.; Kim, M.S.; Jeong, H. Quantum one-time tables for unconditionally secure qubit-commitment. Quantum 2021, 5, 405. [Google Scholar] [CrossRef]
- Lee, Y.; Takagi, R.; Yamasaki, H.; Adesso, G.; Lee, S. State Exchange with Quantum Side Information. Phys. Rev. Lett. 2019, 122, 010502. [Google Scholar] [CrossRef]
- Elben, A.; Vermersch, B.; van Bijnen, R.; Kokail, C.; Brydges, T.; Maier, C.; Joshi, M.K.; Blatt, R.; Roos, C.F.; Zoller, P. Cross-Platform Verification of Intermediate Scale Quantum Devices. Phys. Rev. Lett. 2020, 124, 010504. [Google Scholar] [CrossRef]
- Kimble, H.J. The quantum internet. Nature 2008, 453, 1023–1030. [Google Scholar] [CrossRef]
- Kent, A. Quantum Bit String Commitment. Phys. Rev. Lett. 2003, 90, 237901. [Google Scholar] [CrossRef]
- Kent, A. Impossibility of unconditionally secure commitment of a certified classical bit. Phys. Rev. A 2000, 61, 042301. [Google Scholar] [CrossRef]
- Kent, A. Why classical certification is impossible in a quantum world. Quantum Inf. Process. 2011, 11, 493–499. [Google Scholar] [CrossRef][Green Version]
- Pawłowski, M.; Paterek, T.; Kaszlikowski, D.; Scarani, V.; Winter, A.; Żukowski, M. Information causality as a physical prin-ciple. Nature 2009, 461, 1101. [Google Scholar] [CrossRef]
- Kent, A.; Pitalúa-García, D. Flexible quantum tokens in spacetime. Phys. Rev. A 2020, 101, 022309. [Google Scholar] [CrossRef]
- Kent, A. Quantum tagging for tags containing secret classical data. Phys. Rev. A 2011, 84, 022335. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).