A Novel and Robust Hybrid Blockchain and Steganography Scheme
Abstract
:1. Introduction
2. Literature Review
3. Methodology and Proposed Method
3.1. Steganography: An Overview
3.2. Blockchain: An Overview
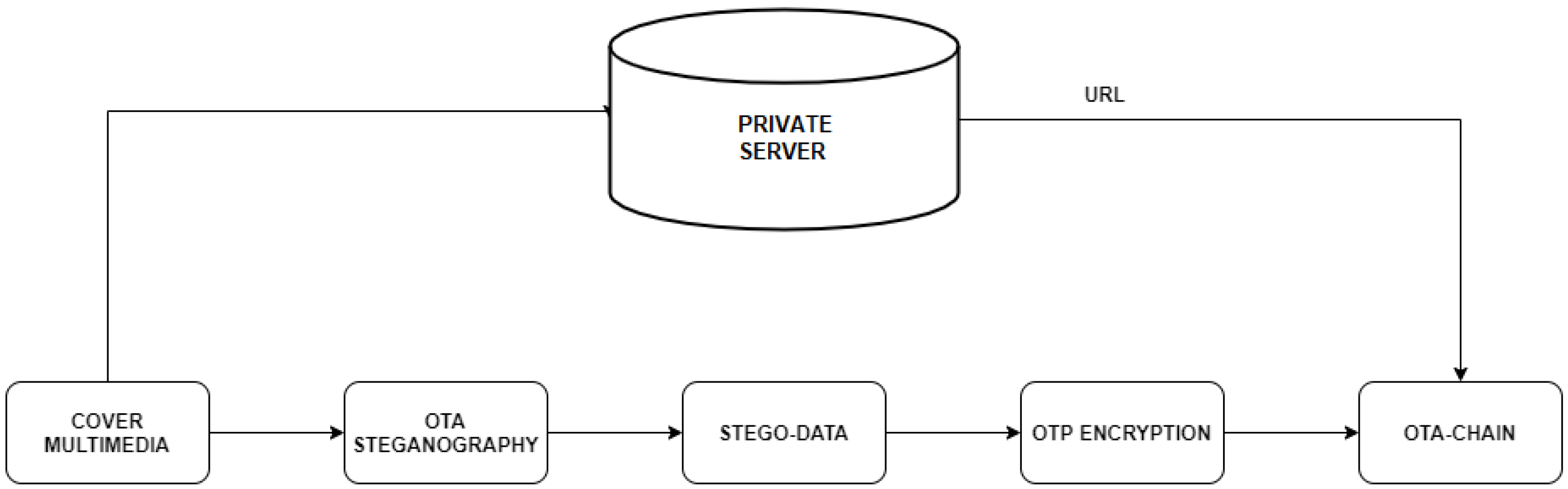
3.3. Proposed Ozyavas–Takaoglu–Ajlouni (OTA) Algorithm
3.3.1. OTA-Steganography Algorithm
| Algorithm 1. OTA-Steganography Algorithm |
| 1: let A = {A1,A2,A3,...,An} |
| 2: let B = {B1,B2,B3,...,Bn} |
| 3: upload the cover multimedia to the server and get URL |
| //for 2 bits marking |
| 4: let Ctb = { Ctb1,Ctb2,Ctb3,...,Ctbn } then |
| 5: Ctb = Ctb1 then |
| 6: if B ≠ {} then |
| 7: for A and B do |
| 8: if An == Bn do |
| 9: add An.location to Ctb then |
| 10: erase Bn from B |
| 11: if Ctb1.lenght >= 1024 then |
| 12: let Ctb = Ctbn+1 |
| 13: end if |
| 14: end if |
| 15: end for |
| 16: end if |
| //for 3 bits marking |
| 17: let Cthb = { Cthb1,Cthb2,Cthb3,...,Cthbn } then |
| 18: Cthb = Cthb1 then |
| 19: if B ≠ {} then |
| 20: for A and B do |
| 21: if An == Bn do |
| 22: add An.location to Cthb then |
| 23: erase Bn from B |
| 24: if Cthb.lenght >= 1024 then |
| 25: let Cthb = Cthb1+1 |
| 26: end if |
| 27: end if |
| 28: end for |
| 29: end if |
| //for 4 bits marking |
| 30: let Cfb = Cfb1,Cfb2,Cfb3,...,Cfbn then |
| 31: Cfb = Cfb1 then |
| 32: if B ≠ {} then |
| 33: for A and B do |
| 34: if An == Bn do |
| 35: add An.location to Cfb then |
| 36: erase Bn from B |
| 37: if Cfb.lenght >= 1024 then |
| 38: let Cfb = Cfb1+1 |
| 39: end if |
| 40: end if |
| 41: end for |
| 42: end if |
| 43: let C = {} |
| 44: select min.lenght (Ctb,Cthb,Cfb) ―>C then |
| 45: let Ci = selected (Ctb,Cthb,Cfb) information |
| //Marking part will continue to the desired bits number. In our study it’s 10 |
| //One Time Pad process |
| 46: let K |
| 47: let CSD |
| 48: generate K size of C.lenght then |
| 49: CSD = K ⊕ C |
| 50: return CSD, K, Ci, URL |
| Algorithm 2. Inverse OTA-Steganography Algorithm |
| 1: get A cover multimedia from server |
| 2: get K and Ci from sender |
| 3: get CSD from OTA-chain |
| 4: let B = { B1,B2,B3,...,Bn } |
| 5: C = CSD ⊕ K then |
| //consider Ci bit information for data extracting process |
| 6: for C do |
| 7: go Ac.address then |
| 8: Bn = Ac.address |
| 9: end for |
| 10: return B |
3.3.2. OTA-Chain Algorithm
- Sender and Receiver Addresses: 256-bit unique addresses of the sending and receiving nodes in the blockchain system.
- Timestamp: This is the date and time information created when a transaction is performed.
- LastHash: In the blockchain, the hash value of the last block created, excluding the genesis block, is called lasthash. It is a 256-bit value, calculated with the SHA256 algorithm.
- Hash: 256-bit value generated using the SHA256 encryption algorithm. Each block has its own hash value and lasthash, which is the previous block’s hash value.
- Nonce: A 32-bit value randomly generated when creating the block, which stands for Number Only Used Once. The Nonce value is used for the operation of the reward system in our PoW algorithm, in which the miners in the system participate.
- Difficulty: The ease of resolution of the PoW algorithm is used to win the block writing right, and the reward is called difficulty. The difficulty level is automatically increased or decreased according to the status of participation in the system.
- URL: In the proposed OTA algorithm, cover multimedia are saved in the server for system security, and its URL is kept in the OTA-chain block, which the receiver uses to reach the cover media.
- Data: This is the field where the OTA coin information sent on the OTA-chain is kept.
- StegoData: This is the 1 kB address array OTP-ciphered stego-data sent over to and stored in blocks of OTA-chain.
4. Results and Discussion
4.1. OTA-Steganography Results
4.2. OTA Blockchain Results
4.3. General Analysis of OTA Algorithm
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Subramanian, N.; Elharrouss, O.; Al-Maadeed, S.; Bouridane, A. Image Steganography: A Review of the Recent Advances. IEEE Access 2021, 9, 23409–23423. [Google Scholar] [CrossRef]
- Setiadi, D.R.I.M.; Rachmawanto, E.H.; Sari, C.A. Secure Image Steganography Algorithm Based on DCT with OTP Encryption. J. Appl. Intell. Syst. 2017, 2, 1–11. [Google Scholar] [CrossRef]
- Pandey, J.; Joshi, K.; Jangra, M.; Sain, M. Pixel Indicator Steganography Technique with Enhanced Capacity for RGB Images. In Proceedings of the 2019 International Conference on Intelligent Computing and Control Systems (ICCS), Madurai, India, 15–17 May 2019; pp. 738–743. [Google Scholar] [CrossRef]
- Islam, M.A.; Riad, M.A.A.K.; Pias, T.S. Enhancing Security of Image Steganography Using Visual Cryptography. In Proceedings of the ICREST 2021—2nd International Conference on Robotics, Electrical and Signal Processing Techniques, Khaka, Bangladesh, 5–7 January 2021; pp. 694–698. [Google Scholar] [CrossRef]
- Reinel, T.S.; Brayan, A.A.H.; Alejandro, B.O.M.; Alejandro, M.R.; Daniel, A.G.; Alejandro, A.G.J.; Buenaventura, B.J.A.; Simon, O.A.; Gustavo, I.; Raul, R.P. GBRAS-Net: A Convolutional Neural Network Architecture for Spatial Image Steganalysis. IEEE Access 2021, 9, 14340–14350. [Google Scholar] [CrossRef]
- Su, W.; Ni, J.; Hu, X.; Fridrich, J. Image Steganography with Symmetric Embedding Using Gaussian Markov Random Field Model. IEEE Trans. Circuits Syst. Video Technol. 2021, 31, 1001–1015. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Z.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Research on a Covert Communication Model Realized by Using Smart Contracts in Blockchain Environment. IEEE Syst. J. 2021, 1–12. [Google Scholar] [CrossRef]
- Latypov, R.; Stolov, E. A New Watermarking Method to Protect Blockchain Records Comprising Small Graphic Files. In Proceedings of the 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 1–3 July 2019; pp. 668–671. [Google Scholar] [CrossRef]
- Berg, S. The advantages and disadvantages of the inclusion of students with disabilities into regular education classrooms. In Proceedings of the 2018 IEEE 6th Workshop on Advances in Information, Electronic and Electrical Engineering, Vilnius, Lithuania, 8–10 November 2018; p. 50. [Google Scholar]
- Jnoub, N.; Klas, W. Detection of Tampered Images Using Blockchain Technology. In Proceedings of the ICBC 2019—IEEE International Conference on Blockchain and Cryptocurrency, Seoul, Korea, 14–17 May 2019; pp. 70–73. [Google Scholar] [CrossRef]
- Weber, I.; Lu, Q.; Tran, A.B.; Deshmukh, A.; Gorski, M.; Strazds, M. A Platform Architecture for Multi-Tenant Blockchain-Based Systems. In Proceedings of the 2019 IEEE International Conference on Software Architecture (ICSA), Hamburg, Germany, 25–29 March 2019; pp. 101–110. [Google Scholar] [CrossRef] [Green Version]
- Zhang, M.; Wang, S.; Zhang, P.; He, L.; Li, X.; Zhou, S. Protecting Data Privacy for Permissioned Blockchains Using Identity-Based Encryption. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 602–605. [Google Scholar] [CrossRef]
- Zhaofeng, M.; Xiaochang, W.; Jain, D.K.; Khan, H.; Hongmin, G.; Zhen, W. A Blockchain-Based Trusted Data Management Scheme in Edge Computing. IEEE Trans. Ind. Inform. 2020, 16, 2013–2021. [Google Scholar] [CrossRef]
- Ramkumar, M. A Blockchain Based Framework for Information System Integrity. China Commun. 2019, 16, 1–17. [Google Scholar] [CrossRef]
- Martens, D.; Maalej, W. ReviewChain: Untampered Product Reviews on the Blockchain. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, New York, NY, USA, 27 May 2018; pp. 40–43. [Google Scholar] [CrossRef]
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security Services Using Blockchains: A State-of-the-Art Survey. IEEE Commun. Surv. Tutor. 2019, 21, 858–880. [Google Scholar] [CrossRef] [Green Version]
- Yang, W.; Aghasian, E.; Garg, S.; Herbert, D.; Disiuta, L.; Kang, B. A Survey on Blockchain-Based Internet Service Architecture: Requirements, Challenges, Trends, and Future. IEEE Access 2019, 7, 75845–75872. [Google Scholar] [CrossRef]
- Takaoğlu, M.; Özer, Ç.; Parlak, E. Blokzinciri Teknolojisi ve Türkiye’deki Muhtemel Uygulanma Alanları. Int. J. East Anatol. Sci. Eng. Des. (IJEASED) 2019, 1, 260–295. Available online: https://dergipark.org.tr/tr/pub/ijeased/issue/47170/643683 (accessed on 21 September 2021).
- Pradeepkumar, D.S.; Singi, K.; Kaulgud, V.; Podder, S. Evaluating Complexity and Digitizability of Regulations and Contracts for a Blockchain Application Design. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 25–29. [Google Scholar] [CrossRef]
- Tabares-Soto, R.; Arteaga-Arteaga, H.B.; Mora-Rubio, A.; Bravo-Ortíz, M.A.; Arias-Garzón, D.; Grisales, J.A.A.; Jacome, A.B.; Orozco-Arias, S.; Isaza, G.; Pollan, R.R. Strategy to Improve the Accuracy of Convolutional Neural Network Architectures Applied to Digital Image Steganalysis in the Spatial Domain. PeerJ Comput. Sci. 2021, 7, 1–21. [Google Scholar] [CrossRef]
- Xie, G.; Ren, J.; Marshall, S.; Zhao, H.; Li, H. A New Cost Function for Spatial Image Steganography Based on 2D-SSA and WMF. IEEE Access 2021, 9, 30604–30614. [Google Scholar] [CrossRef]
- Sarkar, P.; Ghosal, S.K.; Sarkar, M. Stego-Chain: A Framework to Mine Encoded Stego-Block in a Decentralized Network. J. King Saud Univ. Comput. Inf. Sci. 2020, 16, 25–29. [Google Scholar] [CrossRef]
- Mohsin, A.H.; Zaidan, A.A.; Zaidan, B.B.; Mohammed, K.I.; Albahri, O.S.; Albahri, A.S.; Alsalem, M.A. PSO–Blockchain-Based Image Steganography: Towards a New Method to Secure Updating and Sharing COVID-19 Data in Decentralised Hospitals Intelligence Architecture. Multimed. Tools Appl. 2021, 80, 14137–14161. [Google Scholar] [CrossRef] [PubMed]
- Basuki, A.I.; Rosiyadi, D. Joint Transaction-Image Steganography for High Capacity Covert Communication. In Proceedings of the 2019 International Conference on Computer, Control, Informatics and its Applications (IC3INA), Tangerang, Indonesia, 23–24 October 2019; pp. 41–46. [Google Scholar] [CrossRef]
- Partala, J. Provably Secure Covert Communication on Blockchain. Cryptography 2018, 2, 18. [Google Scholar] [CrossRef] [Green Version]
- Horng, J.H.; Chang, C.C.; Li, G.L.; Lee, W.K.; Hwang, S.O. Blockchain-Based Reversible Data Hiding for Securing Medical Images. J. Healthc. Eng. 2021, 2021. [Google Scholar] [CrossRef] [PubMed]
- Xu, M.; Wu, H.; Geng, G.; Zhang, X.; Ding, F. Broadcasting steganography in the blockchain. In International Workshop on Digital Watermarking; Springer: Berlin/Heidelberg, Germany, 2019; pp. 256–267. [Google Scholar]
- Matzutt, R.; Hiller, J.; Henze, M.; Ziegeldorf, J.H.; Müllmann, D.; Hohlfeld, O.; Wehrle, K. A Quantitative Analysis of the Impact of Arbitrary Blockchain Content on Bitcoin. In Financial Cryptography and Data Security; Meiklejohn, S., Sako, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2018; pp. 420–438. [Google Scholar]
- Giron, A.A.; Martina, J.E.; Custódio, R. Steganographic Analysis of Blockchains. Sensors 2021, 21, 4078. [Google Scholar] [CrossRef]
- Hassaballah, M.; Hameed, M.A.; Awad, A.I.; Muhammad, K. A Novel Image Steganography Method for Industrial Internet of Things Security. IEEE Trans. Ind. Inform. 2021, 17, 7743–7751. [Google Scholar] [CrossRef]
- Onuma, K.; Miyata, S. A Proposal for Correlation-Based Steganography Using Shamir’s Secret Sharing Scheme and DCT Domain. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 255–260. [Google Scholar] [CrossRef]
- Sengupta, A.; Rathor, M. Crypto-Based Dual-Phase Hardware Steganography for Securing IP Cores. IEEE Lett. Comput. Soc. 2019, 2, 32–35. [Google Scholar] [CrossRef]
- Ghosal, S.K.; Mukhopadhyay, S.; Hossain, S.; Sarkar, R. Exploiting Laguerre Transform in Image Steganography. Comput. Electr. Eng. 2021, 89, 106964. [Google Scholar] [CrossRef]
- Wahab, O.F.A.; Khalaf, A.A.M.; Hussein, A.I.; Hamed, H.F.A. Hiding Data Using Efficient Combination of RSA Cryptography, and Compression Steganography Techniques. IEEE Access 2021, 9, 31805–31815. [Google Scholar] [CrossRef]
- Kasapbasi, M.C. A New Chaotic Image Steganography Technique Based on Huffman Compression of Turkish Texts and Fractal Encryption with Post-Quantum Security. IEEE Access 2019, 7, 148495–148510. [Google Scholar] [CrossRef]
- Saad, A.H.S.; Mohamed, M.S.; Hafez, E.H. Coverless Image Steganography Based on Optical Mark Recognition and Machine Learning. IEEE Access 2021, 9, 16522–16531. [Google Scholar] [CrossRef]
- Sharifzadeh, M.; Aloraini, M.; Schonfeld, D. Adaptive Batch Size Image Merging Steganography and Quantized Gaussian Image Steganography. IEEE Trans. Inf. Forensics Secur. 2020, 15, 867–879. [Google Scholar] [CrossRef]
- Kordov, K.; Zhelezov, S. Steganography in Color Images with Random Order of Pixel Selection and Encrypted Text Message Embedding. PeerJ Comput. Sci. 2021, 7, 1–21. [Google Scholar] [CrossRef]
- Rodriguez-Garcia, M.; Sicilia, M.A.; Dodero, J.M. A Privacy-Preserving Design for Sharing Demand-Driven Patient Datasets over Permissioned Blockchains and P2P Secure Transfer. PeerJ Comput. Sci. 2021, 7, 1–25. [Google Scholar] [CrossRef]
- Lian, W.; Li, Z.; Guo, C.; Wei, Z.; Peng, X. FRChain: A Blockchain-Based Flow-Rules-Oriented Data Forwarding Security Scheme in SDN. KSII Trans. Internet Inf. Syst. 2021, 15, 264–284. [Google Scholar] [CrossRef]
- Ali, A.; Ahmed, M.; Khan, A.; Anjum, A.; Ilyas, M.; Helfert, M. VisTAS: Blockchain-Based Visible and Trusted Remote Authentication System. PeerJ Comput. Sci. 2021, 7, 1–26. [Google Scholar] [CrossRef]
- Akhtar, M.M.; Khan, M.Z.; Ahad, M.A.; Noorwali, A.; Rizvi, D.R.; Chakraborty, C. Distributed Ledger Technology Based Robust Access Control and Real-Time Synchronization for Consumer Electronics. PeerJ Comput. Sci. 2021, 7, 1–16. [Google Scholar] [CrossRef]
- Shrestha, A.K.; Vassileva, J.; Joshi, S.; Just, J. Augmenting the Technology Acceptance Model with Trust Model for the Initial Adoption of a Blockchain-Based System. PeerJ Comput. Sci. 2021, 7, 1–38. [Google Scholar] [CrossRef]
- Yu, B.; Li, X.; Zhao, H. PoW-BC: A PoW Consensus Protocol Based on Block Compression. KSII Trans. Internet Inf. Syst. 2021, 15, 1389–1408. [Google Scholar] [CrossRef]
- Pranto, T.H.; Noman, A.A.; Mahmud, A.; Haque, A.B. Blockchain and Smart Contract for IoT Enabled Smart Agriculture. PeerJ Comput. Sci. 2021, 7, 1–29. [Google Scholar] [CrossRef] [PubMed]
- International Business Machines Corporation. Why New Off-Chain Storage Is Required for Blockchains. Available online: https://www.ibm.com/downloads/cas/RXOVXAPM#:~:text=Because%20non-transaction%20data%2C%20such,off-chain%20data%20is%20unstructured (accessed on 23 September 2021).
- Nguyen, B.M.; Dao, T.C.; Do, B.L. Towards a Blockchain-Based Certificate Authentication System in Vietnam. PeerJ Comput. Sci. 2020, 2020. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Xu, X.; Pautasso, C.; Zhu, L.; Lu, Q.; Weber, I. A pattern collection for blockchain-based applications. In Proceedings of the ACM International Conference Proceeding Series, Irsee, Germany, 4–8 July 2018. [Google Scholar] [CrossRef]





| 128 Byte | 256 Byte | 512 Byte | 1 kB | 4 kB | |
|---|---|---|---|---|---|
| 4-bit pattern | ~100% | ~100% | ~100% | ~100% | ~100% |
| 6-bit pattern | 99.99% | ~100% | ~100% | ~100% | ~100% |
| 8-bit pattern | 98.34% | 99.97% | 99.99% | ~100% | ~100% |
| 10-bit pattern | 63.30% | 86.62% | 98.22% | 99.96% | ~100% |
| Embeded Data Size | 1 kB | 5 kB | 10 kB | 20 kB | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bit Block Size | 2 Bits | 4 Bits | 6 Bits | 8 Bits | 10 Bits | 2 Bits | 4 Bits | 6 Bits | 8 Bits | 10 Bits | 2 Bits | 4 Bits | 6 Bits | 8 Bits | 10 Bits | 2 Bits | 4 Bits | 6 Bits | 8 Bits | 10 Bits |
| Encoding time (ms) | 3 | 2 | 6 | 22 | 6645 | 6 | 7 | 24 | 4895 | 28,073 | 11 | 14 | 28 | 69 | 30,330 | 26 | 25 | 45 | 89 | 30,217 |
| Array size | 3916 | 1958 | 1306 | 979 | 784 | 19,580 | 9790 | 6527 | 4895 | 3916 | 39,160 | 19,580 | 13,054 | 9790 | 7832 | 80,524 | 40,262 | 26,842 | 20,131 | 16,105 |
| No of arrays required | 4 | 2 | 2 | 1 | 1 | 20 | 10 | 7 | 5 | 4 | 39 | 20 | 13 | 10 | 8 | 79 | 40 | 27 | 20 | 16 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Takaoğlu, M.; Özyavaş, A.; Ajlouni, N.; Alshahrani, A.; Alkasasbeh, B. A Novel and Robust Hybrid Blockchain and Steganography Scheme. Appl. Sci. 2021, 11, 10698. https://doi.org/10.3390/app112210698
Takaoğlu M, Özyavaş A, Ajlouni N, Alshahrani A, Alkasasbeh B. A Novel and Robust Hybrid Blockchain and Steganography Scheme. Applied Sciences. 2021; 11(22):10698. https://doi.org/10.3390/app112210698
Chicago/Turabian StyleTakaoğlu, Mustafa, Adem Özyavaş, Naim Ajlouni, Ali Alshahrani, and Basil Alkasasbeh. 2021. "A Novel and Robust Hybrid Blockchain and Steganography Scheme" Applied Sciences 11, no. 22: 10698. https://doi.org/10.3390/app112210698
APA StyleTakaoğlu, M., Özyavaş, A., Ajlouni, N., Alshahrani, A., & Alkasasbeh, B. (2021). A Novel and Robust Hybrid Blockchain and Steganography Scheme. Applied Sciences, 11(22), 10698. https://doi.org/10.3390/app112210698






