Avoidance of Cybersecurity Threats with the Deployment of a Web-Based Blockchain-Enabled Cybersecurity Awareness System
Abstract
:1. Introduction
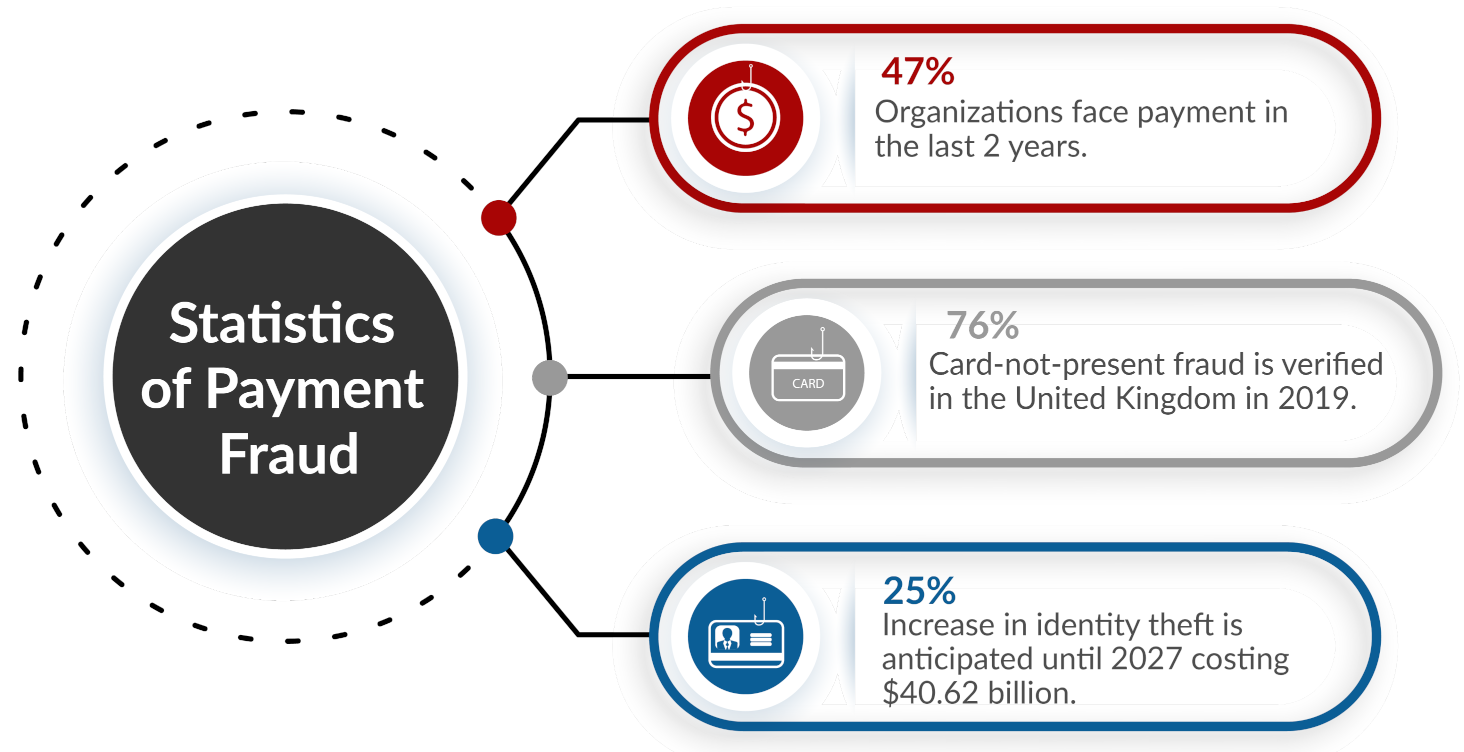
1.1. Research Problem
1.2. Research Importance
1.3. Possible Research Solutions
- The study of common mistakes individuals make, which lead to them becoming the victims of cybercriminals, and taking advantage of these experiences;
- The development of a web-based program that will test for the common behaviors of cybercriminals;
- Monitoring the impact of cybercrime and giving a new view of cybercrimes by using the advantages of much cybersecurity information;
- The creation of more cybersecurity seminars and training programs about the cybercrime world and cybersecurity hygiene;
- The analysis and usage of advice from cybersecurity professionals and modern cybersecurity trends to prevent cybercrimes.
1.4. Research Contributions and Assessment
- The developed web-based program helps many people test and improve their cybersecurity awareness levels.
- The developed web-based program is guaranteed to determine the cybersecurity bottlenecks of the tested users.
- The program results can be analyzed to train the tested users on advanced cybersecurity topics to preserve their high cybersecurity awareness.
- Blockchain technology is used to protect the WBCA program from any potential malicious threats. As a result, only legitimate users can successfully be entertained.
1.5. Research Structure
2. Related Work
2.1. General Detection/Prevention Approaches
2.2. Approaches Based on Emerging Technologies
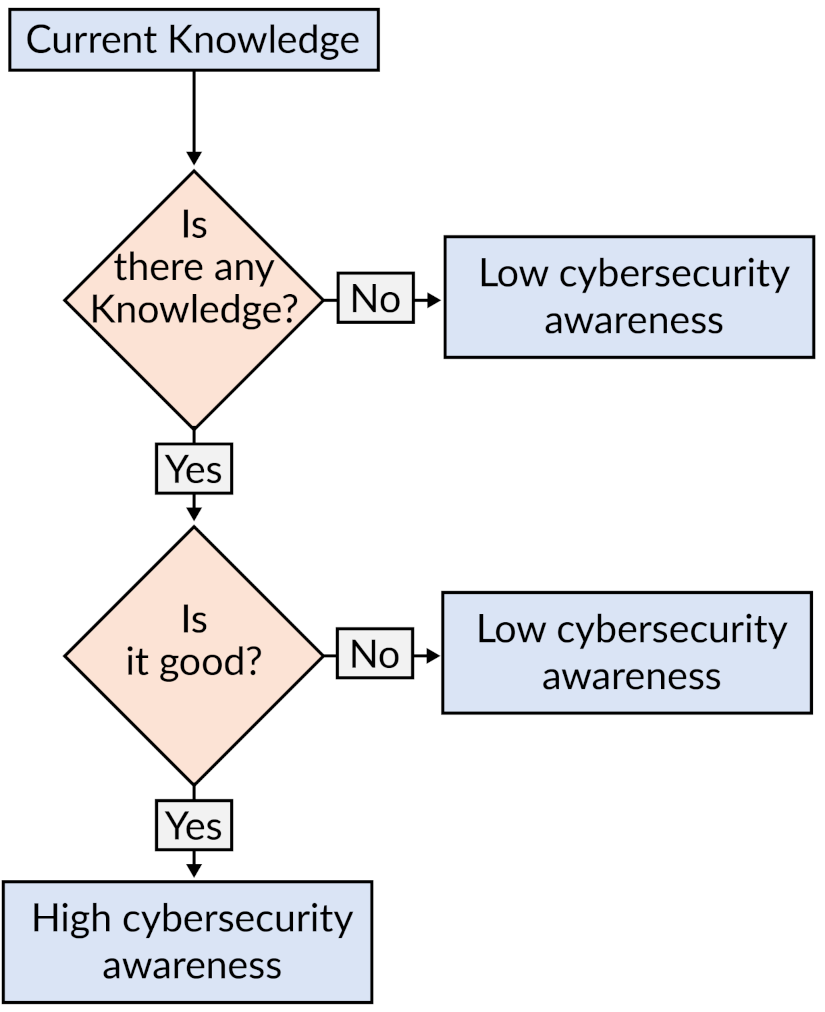
3. System Model
- An initial knowledge-check
- A lower cybersecurity awareness module
- An advanced knowledge check
- A high cybersecurity awareness module
4. Proposed Blockchain-Enabled Cybersecurity Awareness Process
- Counter Sorting Process
- Cybersecurity Awareness Assessment Process
- Blockchain-Enabled Susceptibility Detection Process
4.1. Counter Sorting Process
4.2. Cybersecurity Awareness Assessment Process
| Algorithm 1 Cybersecurity awareness assessment process |
| Input: in Output: out
|
4.3. Blockchain-Enabled Susceptibility Detection Process
| Algorithm 2 Blockchain susceptibility detection process of defining the user’s vulnerability |
| Input: in Output: out
|
5. Experimental Results
5.1. Experimental Setup
5.2. Performance Metrics
- Consistency
- Quality Ratio
- User Response Time
- Solution Efficiency
- Threat Avoidance Capacity
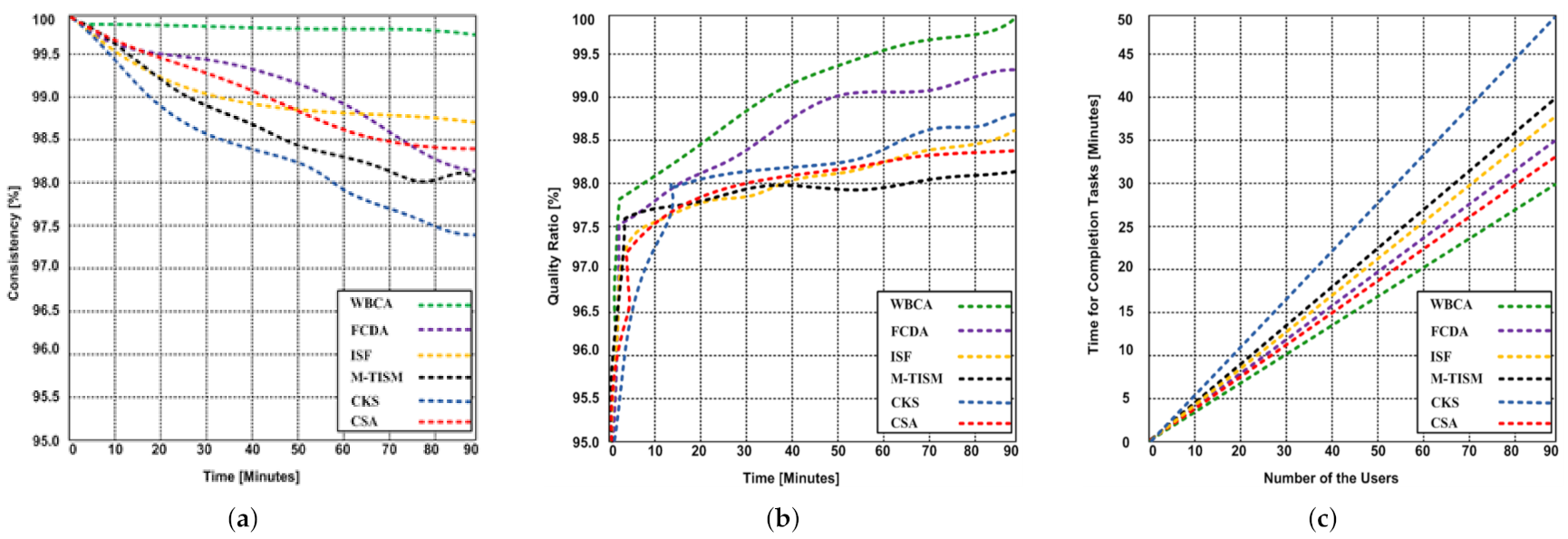
5.2.1. Consistency
5.2.2. Quality Ratio
5.2.3. User Response Time
5.2.4. Solution Efficiency
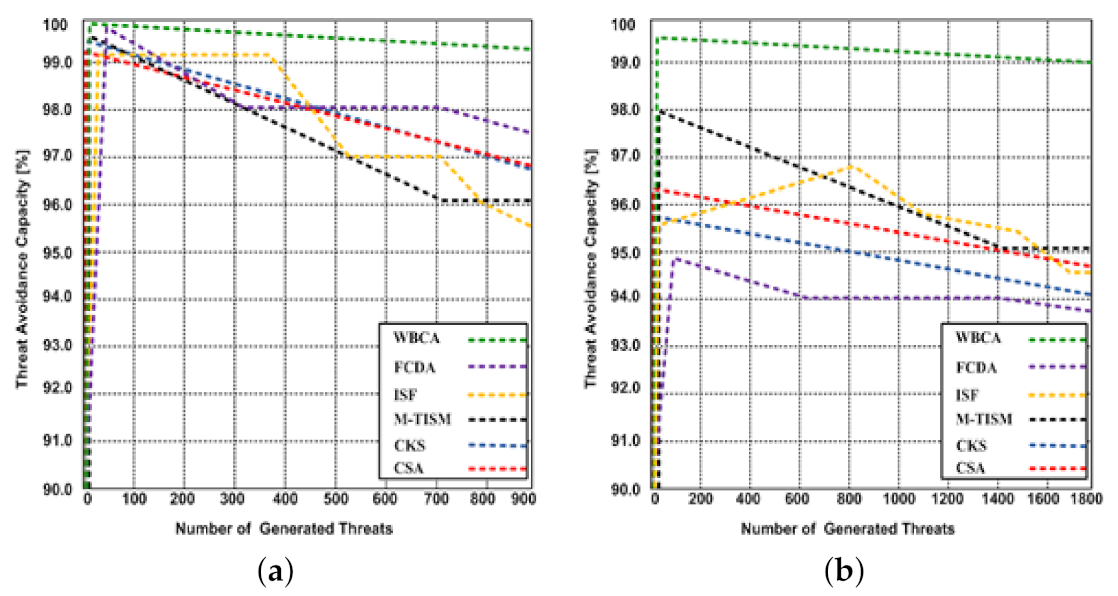
5.2.5. Threat Avoidance Capacity
5.3. Result Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mittal, A.; Gupta, M.P.; Chaturvedi, M.; Chansarkar, S.R.; Gupta, S. Cybersecurity Enhancement through Blockchain Training (CEBT)—A serious game approach. Int. J. Inf. Manag. Data Insights 2021, 1, 100001. [Google Scholar]
- Razaque, A.; Amsaad, F.; Khan, M.J.; Hariri, S.; Chen, S.; Siting, C.; Ji, X. Survey: Cybersecurity vulnerabilities, attacks and solutions in the medical domain. IEEE Access 2019, 7, 168774–168797. [Google Scholar] [CrossRef]
- Kaur, J.; Ram Kumar, K.R. The Recent Trends in CyberSecurity: A Review. J. King Saud Univ. Comput. Inf. Sci. 2021, in press. [Google Scholar]
- Oad, A.; Razaque, A.; Tolemyssov, A.; Alotaibi, M.; Alotaibi, B.; Zhao, C. Blockchain-Enabled Transaction Scanning Method for Money Laundering Detection. Electronics 2021, 10, 1766. [Google Scholar] [CrossRef]
- Palmieri, M.; Shortl, N.; McGarry, P. Personality and online deviance: The role of reinforcement sensitivity theory in cybercrime. Comput. Hum. Behav. 2021, 120, 106745. [Google Scholar] [CrossRef]
- Borkovich, D.J.; Skovira, R.J. Cybersecurity Intertia and Social Engineering: Who’S Worse, Employees or Hackers? Issues Inf. Syst. 2019, 20, 139–150. [Google Scholar]
- Frank, M.L.; Grenier, J.H.; Pyzoha, J.S. Board liability for cyberattacks: The effects of a prior attack and implementing the AICPA’s cybersecurity framework. J. Account. Public Policy 2021, 106860. [Google Scholar] [CrossRef]
- Button, M.; Whittaker, J. Exploring the voluntary response to cyber-fraud: From vigilantism to responsibilisation. Int. J. Law Crime Justice 2021, 66, 100482. [Google Scholar] [CrossRef]
- Almiani, M.; AbuGhazleh, A.; Al-Rahayfeh, A.; Atiewi, S.; Razaque, A. Deep recurrent neural network for IoT intrusion detection system. Simul. Model. Pract. Theory 2020, 101, 102031. [Google Scholar] [CrossRef]
- Aberbach, J.D.; Christensen, T. Academic autonomy and freedom under pressure: Severely limited, or alive and kicking? Public Organ. Rev. 2018, 18, 487–506. [Google Scholar] [CrossRef] [Green Version]
- Rahim, N.H.A.; Hamid, S.; Kiah, M.L.M.; Shamshirband, S.; Furnell, S. A systematic review of approaches to assessing cybersecurity awareness. Kybernetes 2015, 44, 606–622. [Google Scholar] [CrossRef]
- George, J.J.; Leidner, D.E. From clicktivism to hacktivism: Understanding digital activism. Inf. Organ. 2019, 29, 100249. [Google Scholar] [CrossRef]
- Delcher, P. Are we losing the fight against cybercrime? Comput. Fraud. Secur. 2021, 2021, 18–19. [Google Scholar] [CrossRef]
- Yar, M.; Steinmetz, K.F. Cybercrime and Society; SAGE: London, UK, 2019. [Google Scholar]
- Lane, B.R.; Salmon, P.M.; Desmond, D.; Cherney, A.; Carley, A.; Hulme, A.; Stanton, N.A. Out of control? Using STAMP to model the control and feedback mechanisms surrounding identity crime in darknet marketplaces. Appl. Ergon. 2020, 89, 103223. [Google Scholar] [CrossRef]
- Umanailo, M.C.B.; Fachruddin, I.; Mayasari, D.; Kurniawan, R.; Agustin, D.N.; Ganefwati, R.; Daulay, P.; Meifilina, A.; Alamin, T.; Fitriana, R.; et al. Cybercrime Case as Impact Development of Communication Technology That Troubling Society. Int. J. Sci. Technol. Res. 2021, 8, 1224–1228. [Google Scholar]
- Bello, M.; Griffiths, M. Routine activity theory and cybercrime investigation in Nigeria: How capable are law enforcement agencies. In Rethinking Cybercrime; Springer: Cham, Switzerland, 2021; pp. 213–235. [Google Scholar]
- Shuftipro. Available online: https://shuftipro.com/blog/how-age-verification-protects-the-e-commerce-industry-from-potential-risks/ (accessed on 3 July 2021).
- Bada, M.; Sasse, A.M.; Nurse, J.R. Cyber security awareness campaigns: Why do they fail to change behaviour? arXiv 2019, arXiv:1901.02672. [Google Scholar]
- Newhouse, W.; Keith, S.; Scribner, B.; Witte, G. National initiative for cybersecurity education (NICE) cybersecurity workforce framework. NIST Spec. Publ. 2017, 800. [Google Scholar] [CrossRef]
- Pessim, P.S.P.; Lacerda, M.J. State-feedback control for cyber-physical LPV systems under DoS attacks. IEEE Control Syst. Lett. 2020, 5, 1043–1048. [Google Scholar] [CrossRef]
- Talukder, M.A.I.; Shahriar, H.; Haddad, H. Point-of-sale device attacks and mitigation approaches for cyber-physical systems. In Cybersecurity and Privacy in Cyber-Physical Systems; CRC Press: Boca Raton, FL, USA, 2019; pp. 367–391. [Google Scholar]
- Dreyfuss, R.C. TRIPS-Round II: Should Users Strike Back. In The Regulation of Services and Intellectual Property; Routledge: London, UK, 2017; pp. 397–411. [Google Scholar]
- Eskandari, S.; Leoutsarakos, A.; Mursch, T.; Clark, J. A first look at browser-based cryptojacking. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), London, UK, 23–27 April 2018; pp. 58–66. [Google Scholar]
- Burlison, J.D.; Scott, S.D.; Browne, E.K.; Thompson, S.G.; Hoffman, J.M. The second victim experience and support tool (SVEST): Validation of an organizational resource for assessing second victim effects and the quality of support resources. J. Patient Saf. 2017, 13, 93. [Google Scholar] [CrossRef]
- Cascavilla, G.; Tamburri, D.A.; Heuvel, W.-J.V.D. Cybercrime Threat Intelligence: A Systematic Multi-Vocal Literature Review. Comput. Secur. 2021, 105, 102258. [Google Scholar] [CrossRef]
- Tsakalidis, G.; Vergidis, K. A systematic approach toward description and classification of cybercrime incidents. IEEE Trans. Syst. Man Cybern. Syst. 2017, 49, 710–729. [Google Scholar] [CrossRef]
- Senarak, C. Port cybersecurity and threat: A structural model for prevention and policy development. Asian J. Shipp. Logist. 2021, 37, 20–36. [Google Scholar] [CrossRef]
- Gallo, L.; Maiello, A.; Botta, A.; Ventre, G. 2 Years in the anti-phishing group of a large company. Comput. Secur. 2021, 105, 102259. [Google Scholar] [CrossRef]
- D’Hooge, L.; Wauters, T.; Volckaert, B.; De Turck, F. In-depth comparative evaluation of supervised machine learning approaches for detection of cybersecurity threats. In Proceedings of the 4th International Conference on Internet of Things, Big Data and Security (IoTBDS), Crete, Greece, 2–4 May 2019; pp. 125–136. [Google Scholar]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y.; Ma, M.D.; He, J. Blochie: A blockchain-based platform for healthcare information exchange. In Proceedings of the IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Italy, 18–20 June 2018; pp. 49–56. [Google Scholar]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y. Fairness-based packing of industrial IoT data in permissioned blockchains. IEEE Trans. Ind. Inform. 2021, 17, 7639–7649. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; McCann, J.A.; Yang, Y.; Liu, Y.; Wang, X.; Deng, Y. Privacy-preserving and efficient multi-keyword search over encrypted data on blockchain. In Proceedings of the IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 405–410. [Google Scholar]
- Brilingaitė, A.; Bukauskas, L.; Juozapavičius, A. A framework for competence development and assessment in hybrid cybersecurity exercises. Comput. Secur. 2020, 88, 101607. [Google Scholar] [CrossRef]
- Kam, H.-J.; Menard, P.; Ormond, D.; Crossler, R.E. Cultivating cybersecurity learning: An integration of self-determination and flow. Comput. Secur. 2021, 96, 101875. [Google Scholar] [CrossRef]
- Rajan, R.; Rana, N.P.; Parameswar, N.; Dhir, S.; Dwivedi, Y.K. Developing a modified total interpretive structural model (M-TISM) for organizational strategic cybersecurity management. Technol. Forecast. Soc. Chang. 2021, 170, 120872. [Google Scholar] [CrossRef]
- Švábenský, V.; Čeleda, P.; Vykopal, J.; Brišáková, S. Cybersecurity knowledge and skills taught in capture the flag challenges. Comput. Secur. 2021, 102, 102154. [Google Scholar] [CrossRef]
- Hart, S.; Margheri, A.; Paci, F.; Sassone, V. Riskio: A serious game for cyber security awareness and education. Comput. Secur. 2020, 95, 101827. [Google Scholar] [CrossRef]


| Components | Version/The Name of the System |
|---|---|
| Personal computer | x64 |
| Operating system | Linux CentOS 7 |
| Java version | 1.8.271u |
| Recommended screen resolution | |
| Processor | Intel(R) Core (TM) i3-6100H |
| Maker | Intel Xeon |
| RAM | 4096 MB |
| Video memory | 16 MB |
| Hard drive | 50 GB (/dev/sda1) |
| CPU | 2.300 GHz |
| Cache size | 8192 KB |
| Programs | Consistency | Quality Ratio | User Response Time in Minutes (Basic Task) | User Response Time in Minutes (Advanced Task) | Efficiency (Basic Task) | Efficiency (Advanced Task) | Threat Avoidance (900 Threats) | Threat Avoidance (1800 Threats) |
|---|---|---|---|---|---|---|---|---|
| M-TISM | 98.0% | 98.08% | 39.58 | 42.05 | 99.26% | 97.01% | 96.06% | 95.04% |
| ISF | 98.75% | 98.61% | 37.31 | 45.01 | 99.65% | 98.12% | 95.52% | 98.17% |
| FDCA | 98.17% | 99.38% | 37.31 | 51.09 | 98.88% | 97.85% | 97.72% | 93.81% |
| CSA | 98.37% | 98.39% | 32.41 | 39.03 | 98.52% | 96.11% | 96.92% | 96.16% |
| CKS | 97.4% | 98.78% | 49.59 | 57.23 | 98.06% | 95.48% | 96.92% | 95.54% |
| WBCA | 99.76% | 99.97% | 29.58 | 33.01 | 100 % | 99.34% | 99.32% | 99.11% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Razaque, A.; Al Ajlan, A.; Melaoune, N.; Alotaibi, M.; Alotaibi, B.; Dias, I.; Oad, A.; Hariri, S.; Zhao, C. Avoidance of Cybersecurity Threats with the Deployment of a Web-Based Blockchain-Enabled Cybersecurity Awareness System. Appl. Sci. 2021, 11, 7880. https://doi.org/10.3390/app11177880
Razaque A, Al Ajlan A, Melaoune N, Alotaibi M, Alotaibi B, Dias I, Oad A, Hariri S, Zhao C. Avoidance of Cybersecurity Threats with the Deployment of a Web-Based Blockchain-Enabled Cybersecurity Awareness System. Applied Sciences. 2021; 11(17):7880. https://doi.org/10.3390/app11177880
Chicago/Turabian StyleRazaque, Abdul, Abrar Al Ajlan, Noussaiba Melaoune, Munif Alotaibi, Bandar Alotaibi, Issabekov Dias, Ammar Oad, Salim Hariri, and Chenglin Zhao. 2021. "Avoidance of Cybersecurity Threats with the Deployment of a Web-Based Blockchain-Enabled Cybersecurity Awareness System" Applied Sciences 11, no. 17: 7880. https://doi.org/10.3390/app11177880
APA StyleRazaque, A., Al Ajlan, A., Melaoune, N., Alotaibi, M., Alotaibi, B., Dias, I., Oad, A., Hariri, S., & Zhao, C. (2021). Avoidance of Cybersecurity Threats with the Deployment of a Web-Based Blockchain-Enabled Cybersecurity Awareness System. Applied Sciences, 11(17), 7880. https://doi.org/10.3390/app11177880










