Anomaly Detection Using Deep Neural Network for IoT Architecture
Abstract
1. Introduction
2. Related Work
3. Proposed Methodology
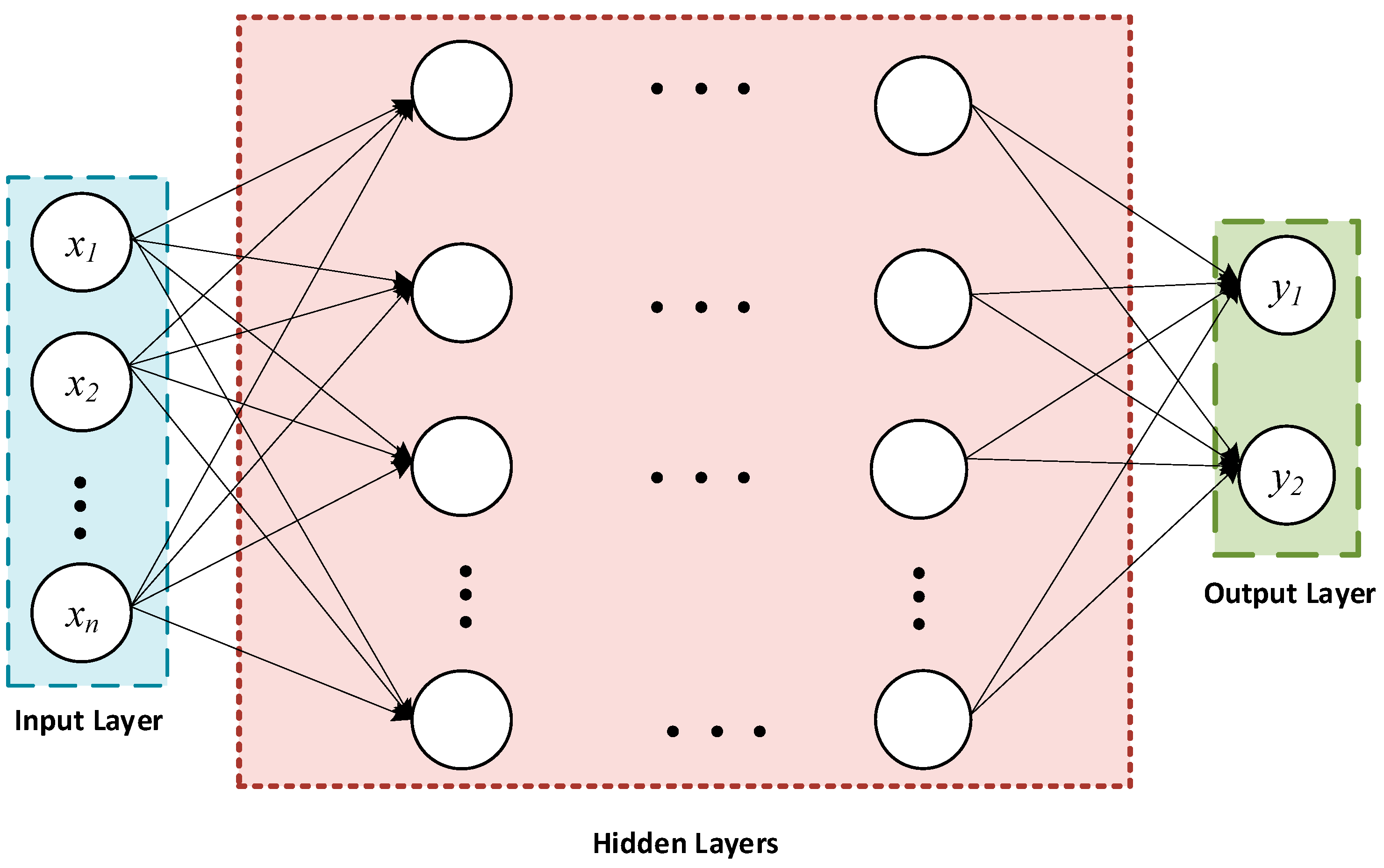
3.1. Deep Neural Network (DNN)
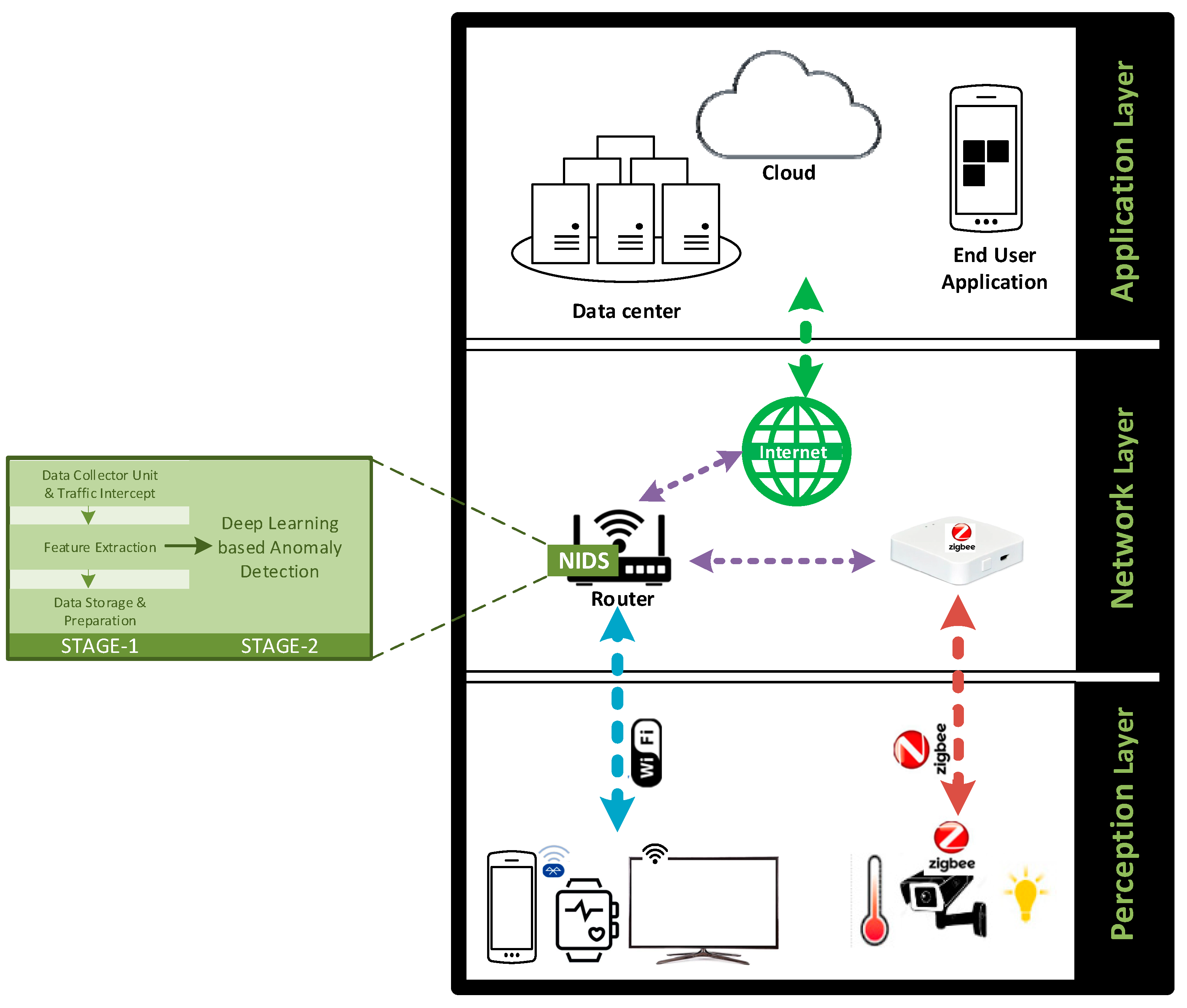
3.2. IoT Architecture
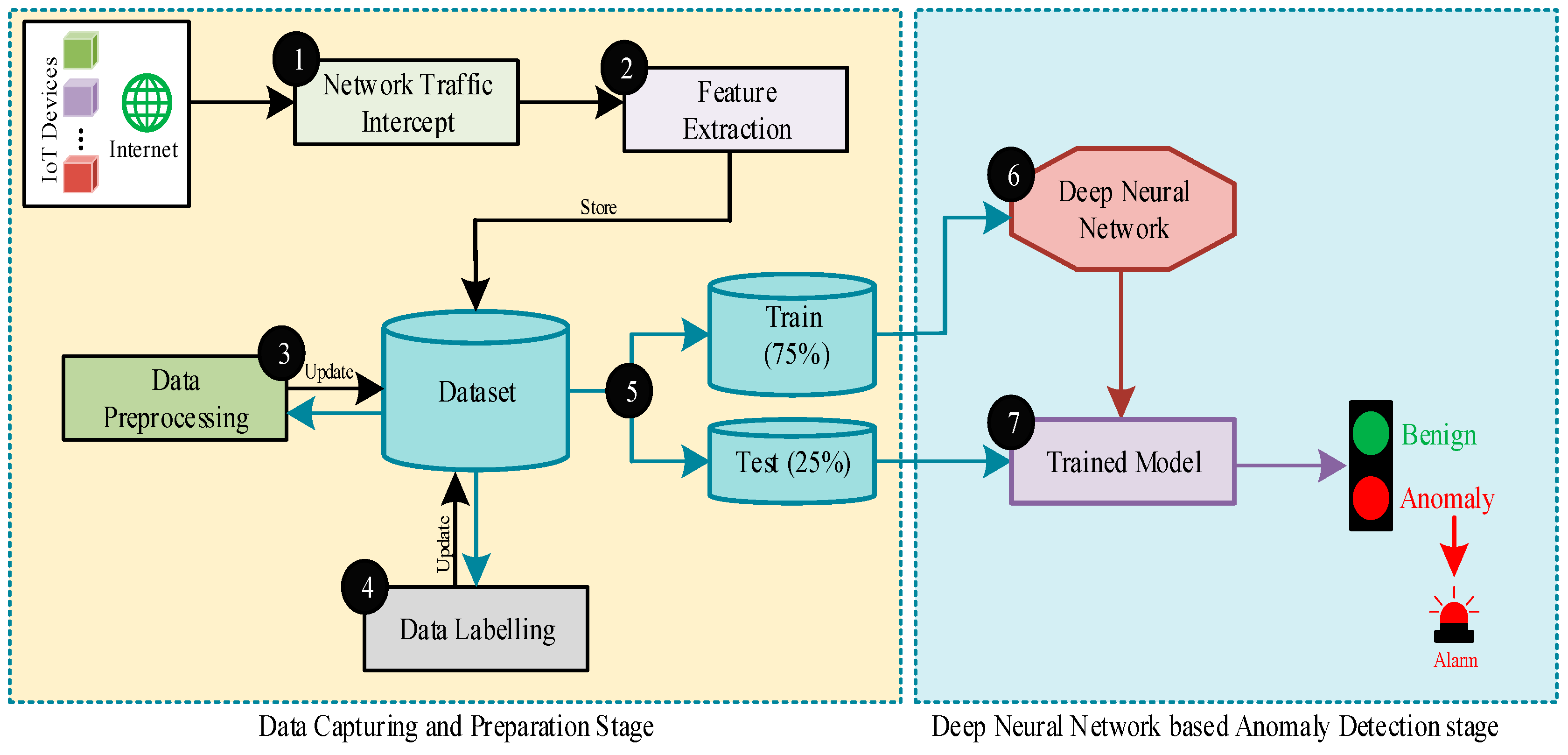
3.3. Methodology
- Step-1:
- Step-2:
- The features are being extracted from the network packets and are stored in a dataset.
- Step-3:
- The extracted features are then preprocessed to remove the redundant flows, normalize the continuous features, and encode the categorical features using one-hot encoding.
- Step-4:
- The dataset is labeled as the Benign record and Anomaly record to prepare for the binary classification scenarios.
- Step-5:
- The dataset is then split into 75% Train dataset and 25% Test dataset.
- Step-6:
- The DNN is then trained on the Train dataset by selecting the Benign and Anomaly Labels as target features utilizing the binary classification. This step results in a trained DNN model.
- Step-7:
- The trained model is then tested using the Test dataset to predict the records as either Benign or Anomaly flows. If the Benign traffic is predicted, it was allowed to pass through without taking any action. While on the other hand, if an Anomaly is predicted, an alarm signal is given to the network administrator to take further actions.
4. Experimental Results and Analysis
4.1. Dataset Description
4.2. Evaluation Metrics
4.3. Experimental Setup
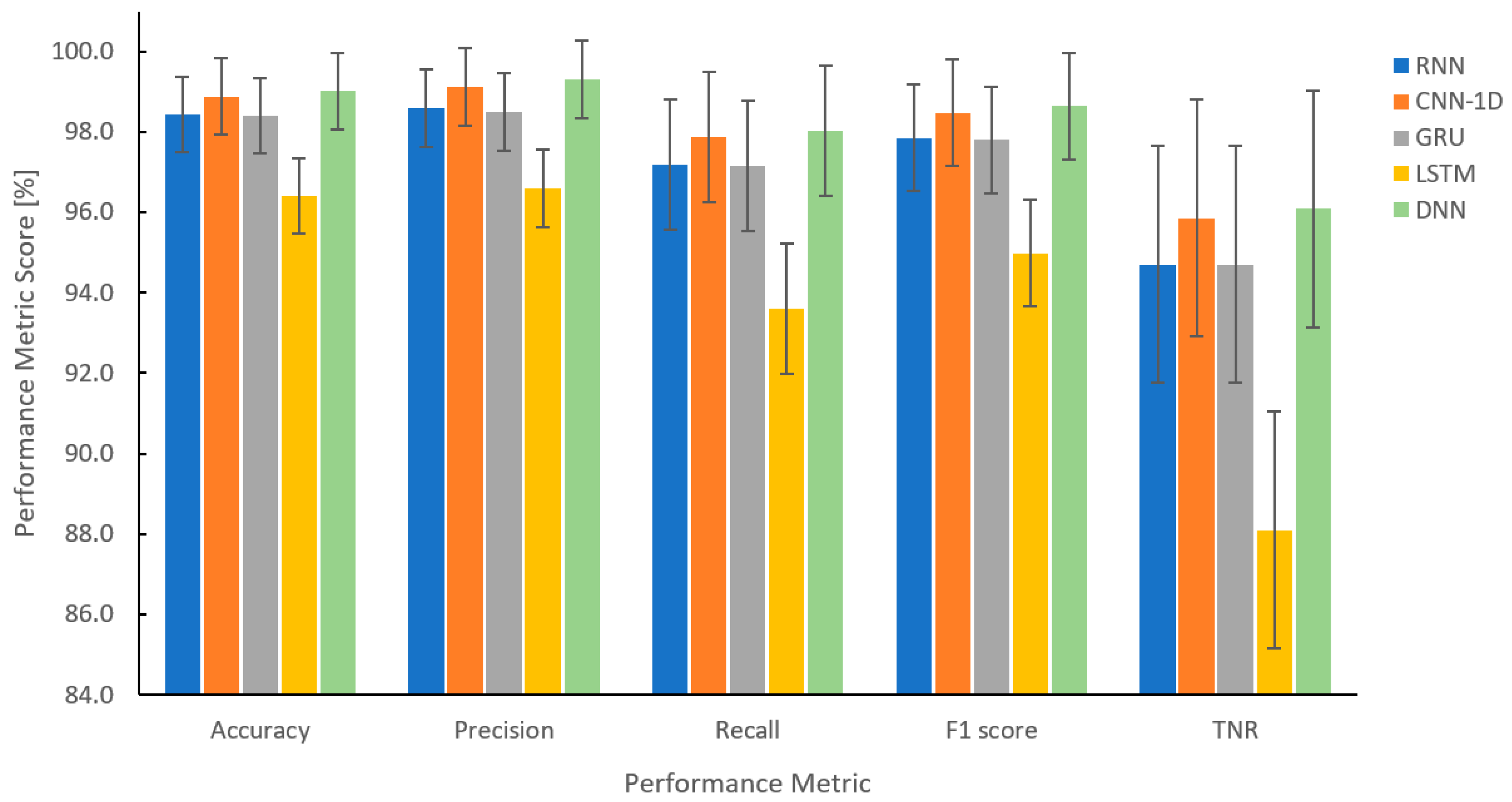
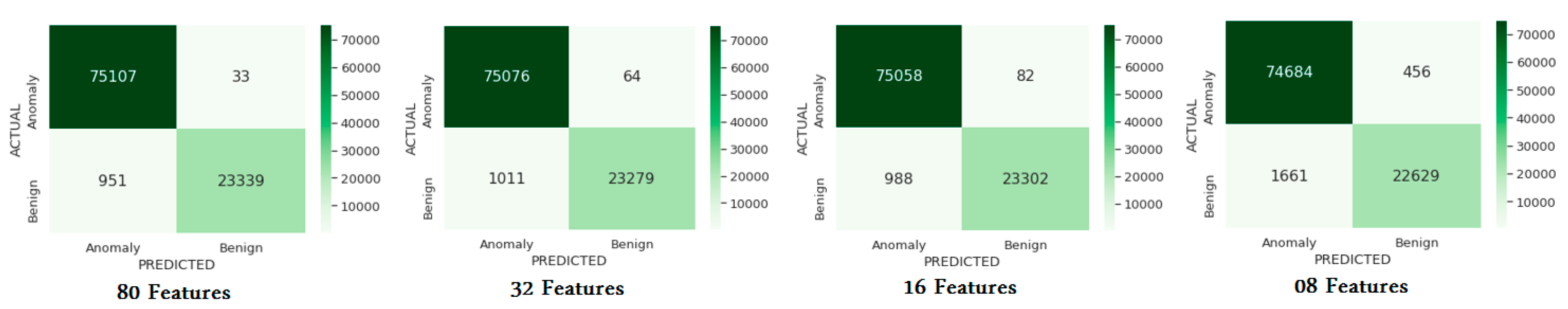
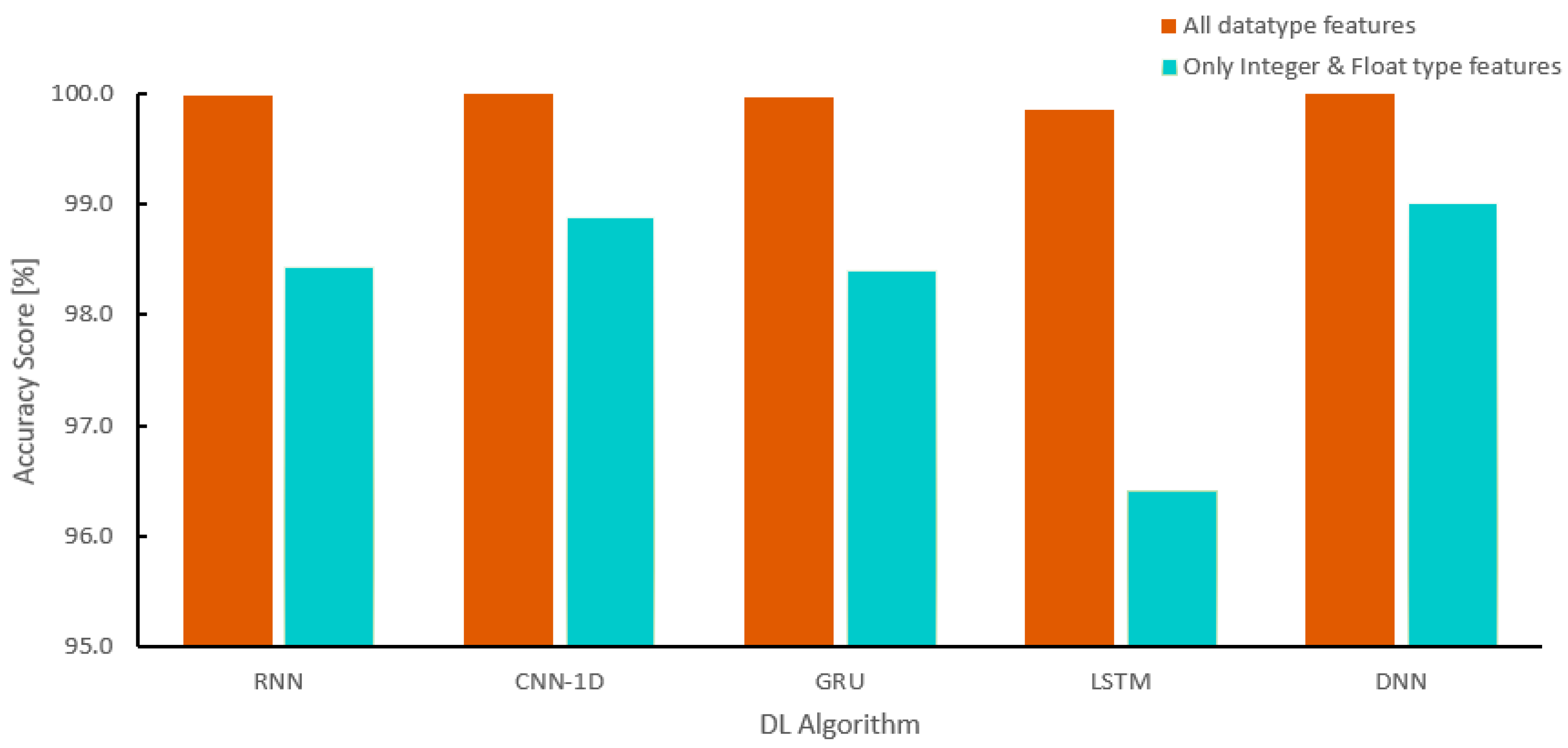
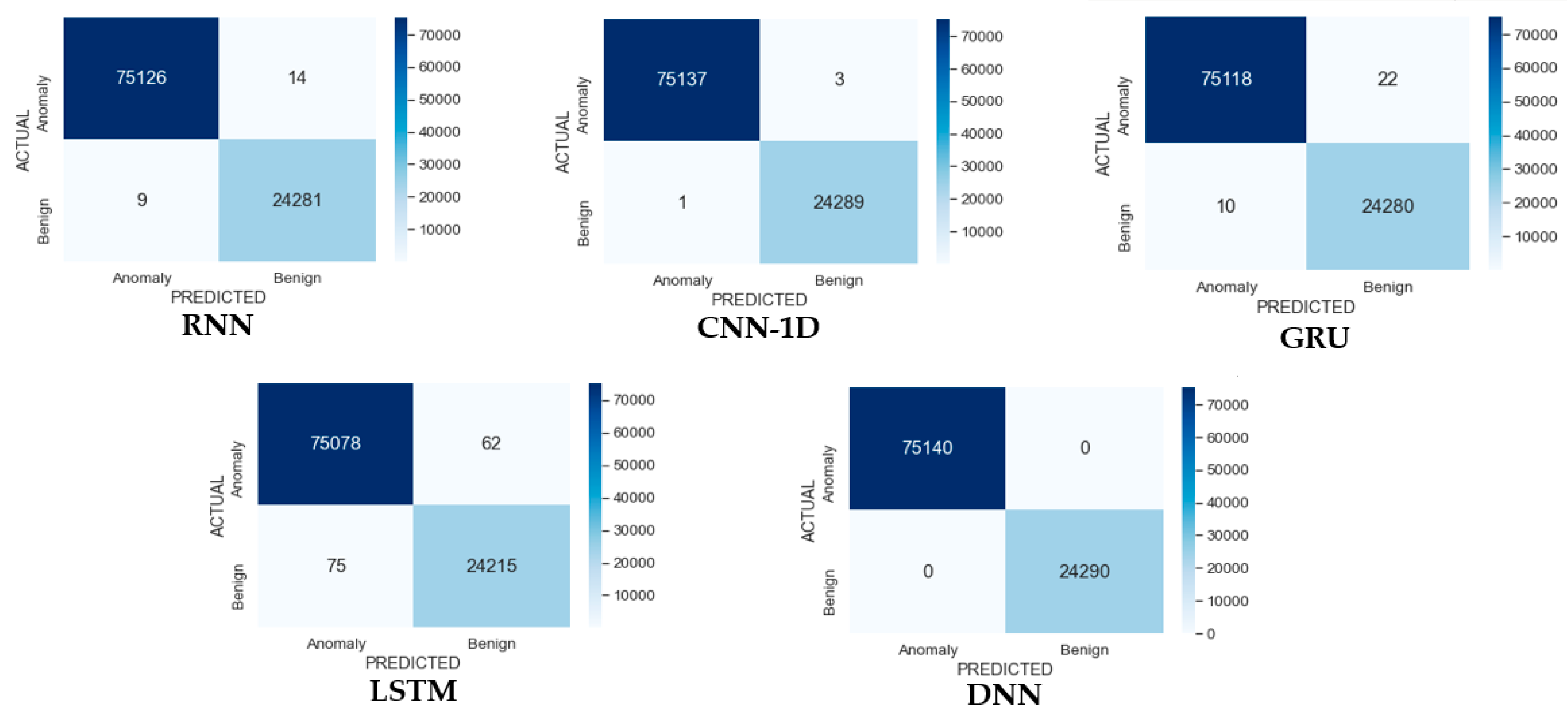
4.4. Results and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Harb, H.; Mansour, A.; Nasser, A.; Cruz, E.M.; Diez, I.D.L.T. A Sensor-Based Data Analytics for Patient Monitoring in Connected Healthcare Applications. IEEE Sens. J. 2021, 21, 974–984. [Google Scholar] [CrossRef]
- Haider, I.; Khan, K.B.; Haider, M.A.; Saeed, A.; Nisar, K. Automated Robotic System for Assistance of Isolated Patients of Coronavirus (COVID-19). In Proceedings of the 2020 IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–6. [Google Scholar]
- Hovav, S.; Tsadikovich, D. A network flow model for inventory management and distribution of influenza vaccines through a healthcare supply chain. Oper. Res. Health Care 2015, 5, 49–62. [Google Scholar] [CrossRef]
- Sarkar, N.I.; Kuang, A.X.-M.; Nisar, K.; Amphawan, A.; Sarkar, N.I. Performance Studies of Integrated Network Scenarios in a Hospital Environment. Int. J. Inf. Commun. Technol. Hum. Dev. 2014, 6, 35–68. [Google Scholar] [CrossRef]
- Sarkar, N.I.; Kuang, A.X.-M.; Nisar, K.; Amphawan, A.; Sarkar, N.I. Hospital Environment Scenarios using WLAN over OPNET Simulation Tool. Int. J. Inf. Commun. Technol. Hum. Dev. 2014, 6, 69–90. [Google Scholar] [CrossRef]
- Chowdhry, B.; Shah, A.A.; Harris, N.; Hussain, T.; Nisar, K. Development of a Smart Instrumentation for Analyzing Railway Track Health Monitoring Using Forced Vibration. In Proceedings of the 2020 IEEE 14th International Conference on Application of Information and Communication Technologies (AICT), Tashkent, Uzbekistan, 7–9 October 2020; pp. 1–5. [Google Scholar]
- Nisar, K. Smart Home: Multisensor Information Fusion Towards Better Healthcare. Adv. Sci. Lett. 2018, 24, 1896–1901. [Google Scholar] [CrossRef]
- Patel, R.; Longini, I.M.; Halloran, M.E. Finding optimal vaccination strategies for pandemic influenza using genetic algorithms. J. Theor. Biol. 2005, 234, 201–212. [Google Scholar] [CrossRef] [PubMed]
- Haque, M.R.; Tan, S.C.; Yusoff, Z.; Nisar, K.; Lee, C.K.; Chowdhry, B.; Ali, S.; Memona, S.K.; Kaspin, R. SDN Architecture for UAVs and EVs using Satellite: A Hypothetical Model and New Challenges for Future. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; pp. 1–6. [Google Scholar]
- Ahmad, F.; Ahmad, Z.; Kerrache, C.A.; Kurugollu, F.; Adnane, A.; Barka, E. Blockchain in Internet-of-Things: Architecture, Applications and Research Directions. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS), Aljouf, Saudi Arabia, 3–4 April 2019; pp. 1–6. [Google Scholar]
- Mehmood, Y.; Ahmad, F.; Yaqoob, I.; Adnane, A.; Imran, M.; Guizani, S. Internet-of-Things-Based Smart Cities: Recent Advances and Challenges. IEEE Commun. Mag. 2017, 55, 16–24. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, 4150. [Google Scholar] [CrossRef]
- Apruzzese, G.; Andreolini, M.; Marchetti, M.; Colacino, V.G.; Russo, G. AppCon: Mitigating Evasion Attacks to ML Cyber Detectors. Symmetry 2020, 12, 653. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Moschoyiannis, S.; Janicke, H. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. J. Inf. Secur. Appl. 2020, 50, 102419. [Google Scholar] [CrossRef]
- Xiaolong, H.; Huiqi, Z.; Lunchao, Z.; Nazir, S.; Jun, D.; Shahid Khan, A. Soft Computing and Decision Support System for Software Process Improvement: A Systematic Literature Review. Sci. Program. 2021, 2021, 7295627. [Google Scholar]
- Maikol, S.O.; Khan, A.S.; Javed, Y.; Bunsu, A.L.; Petrus, C.; George, H.; Jau, S. A novel authentication and key agreement scheme for countering MITM and impersonation attack in medical facilities. Int. J. Integr. Eng. 2020, 13, 127–135. [Google Scholar]
- Nisar, K.; Sabir, Z.; Raja, M.; Ibrahim, A.; Rodrigues, J.; Khan, A.; Gupta, M.; Kamal, A.; Rawat, D. Evolutionary Integrated Heuristic with Gudermannian Neural Networks for Second Kind of Lane–Emden Nonlinear Singular Models. Appl. Sci. 2021, 11, 4725. [Google Scholar] [CrossRef]
- Haque, M.R.; Tan, S.C.; Yusoff, Z.; Nisar, K.; Kwang, L.C.; Kaspin, R.; Chowdhry, B.S.; Buyya, R.; Majumder, S.P.; Gupta, M.; et al. Automated Controller Placement for Software-Defined Networks to Resist DDoS Attacks. Comput. Mater. Contin. 2021, 68, 3147–3165. [Google Scholar] [CrossRef]
- Haque, M.R.; Tan, S.C.; Yusoff, Z.; Lee, C.K.; Kaspin, R. DDoS Attack Monitoring using Smart Controller Placement in Software Defined Networking Architecture. In Lecture Notes in Electrical Engineering; Springer Science and Business Media LLC: Singapore, 2018; Volume 481, pp. 195–203. [Google Scholar]
- Apruzzese, G.; Colajanni, M.; Ferretti, L.; Guido, A.; Marchetti, M. On the effectiveness of machine and deep learning for cyber security. In Proceedings of the 2018 10th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 30 May–1 June 2018; pp. 371–390. [Google Scholar]
- Waseem, Q.; Alshamrani, S.S.; Nisar, K.; Wan Din, W.I.S.; Alghamdi, A.S. Future Technology: Software-Defined Network (SDN) Forensic. Symmetry 2021, 13, 767. [Google Scholar] [CrossRef]
- Nisar, K.; Jimson, E.R.; Hijazi, M.H.A.; Memon, S.K. A survey: Architecture, security threats and application of SDN. J. Ind. Electron. Technol. Appl. 2019, 2, 64–69. [Google Scholar]
- Kas, K.N.; Hijazi, M.H.A.; Chen, G.; Sarrafzadeh, A. A Review: Software Defined Networks Management. Proc. Asia Pac. Adv. Netw. 2015, 39, 20. [Google Scholar] [CrossRef][Green Version]
- Ali, N.F.; Said, A.M.; Nisar, K.; Aziz, I.A. A survey on software defined network approaches for achieving energy efficiency in wireless sensor network. In Proceedings of the 2017 IEEE Conference on Wireless Sensors (ICWiSe), Miri, Malaysia, 13–14 November 2017; pp. 1–6. [Google Scholar]
- Bovenzi, G.; Aceto, G.; Ciuonzo, D.; Persico, V.; Pescape, A. A Hierarchical Hybrid Intrusion Detection Approach in IoT Scenarios. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–7. [Google Scholar]
- Khan, A.S.; Javed, Y.; Abdullah, J.; Zen, K. Trust-based lightweight security protocol for device to device multihop cellular communication (TLwS). J. Ambient. Intell. Humaniz. Comput. 2021, 12, 1–18. [Google Scholar] [CrossRef]
- Haque, M.R.; Tan, S.C.; Lee, C.K.; Yusoff, Z.; Ali, S.; Kaspin, I.R.; Ziri, S.R. Analysis of DDoS Attack-Aware Software-Defined Networking Controller Placement in Malaysia. In Recent Trends in Computer Applications; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2018; pp. 175–188. [Google Scholar]
- Jimson, E.R.; Nisar, K.; Hijazi, M.H.A. The State of the Art of Software Defined Networking (SDN) Issues in Current Network Architecture and a Solution for Network Management Using the SDN. Int. J. Technol. Diffus. 2019, 10, 33–48. [Google Scholar] [CrossRef]
- Ibrahim, A.A.A.; Nisar, K. Future internet and named data networking hourglass, packet and node architecture. J. Ind. Inf. Technol. Appl. 2018, 2, 115–123. [Google Scholar]
- Khan, A.S.; Balan, K.; Javed, Y.; Abdullah, J.; Tarmizi, S. Secure trust-based blockchain architecture to prevent attacks in VANET. Sensors 2019, 19, 4954. [Google Scholar] [CrossRef]
- Harada, S.; Yan, Z.; Park, Y.-J.; Nisar, K.; Ibrahim, A.A.A. Data aggregation in named data networking. In Proceedings of the TENCON 2017—2017 IEEE Region 10 Conference, Penang, Malaysia, 5–8 November 2017; pp. 1839–1842. [Google Scholar]
- Abbasi, I.A.; Khan, A.S.; Ali, S. A Reliable Path Selection and Packet Forwarding Routing Protocol for Vehicular Ad hoc Networks. EURASIP J. Wirel. Commun. Netw. 2018, 236, 1–19. [Google Scholar] [CrossRef]
- Nisar, K.; Amphawan, A.; Hassan, S.; Sarkar, N.I. A comprehensive survey on scheduler for VoIP over WLAN. J. Netw. Comput. Appl. 2013, 36, 933–948. [Google Scholar] [CrossRef]
- Sattar, F.; Hussain, M.; Nisar, K. A secure architecture for open source VoIP solutions. In Proceedings of the 2011 International Conference on Information and Communication Technologies, Karachi, Pakistan, 23–24 July 2011; pp. 1–6. [Google Scholar]
- Nisar, K.; Said, A.M.; Hasbullah, H. Enhanced performance of packet transmission using system model over VoIP network. In Proceedings of the 2010 International Symposium on Information Technology, Kuala Lumpur, Malaysia, 15–17 June 2010; pp. 1005–1008. [Google Scholar] [CrossRef]
- Sarkar, N.; Nisar, K.; Babbage, L. Performance Studies on Campus-Wide Focus on FTP, Video and VoIP Ethernet Network. Int. J. Adv. Pervasive Ubiquitous Comput. 2012, 4, 49–59. [Google Scholar] [CrossRef]
- Chaudhary, S.; Amphawan, A.; Nisar, K. Realization of free space optics with OFDM under atmospheric turbulence. Optik 2014, 125, 5196–5198. [Google Scholar] [CrossRef]
- Amphawan, A.; Mishra, V.; Nisar, K.; Nedniyom, B. Real-time holographic backlighting positioning sensor for enhanced power coupling efficiency into selective launches in multimode fiber. J. Mod. Opt. 2012, 59, 1745–1752. [Google Scholar] [CrossRef]
- Abbasi, I.A.; Khan, A.S.; Ali, S. Dynamic Multiple Junction Selection Based Routing protocol for VANETs in city environment. Appl. Sci. 2018, 8, 687. [Google Scholar] [CrossRef]
- Khan, A.S.; Lenando, H.; Abdullah, J.; Fisal, N. Secure authentication and key management protocols for mobile multihop WiMAX networks. Jurnal Teknologi 2015, 73, 75–81. [Google Scholar] [CrossRef][Green Version]
- Lawal, I.A.; Said, A.M.; Nisar, K.; Mu’azu, A.A. A distributed QoS-oriented model to improve network performance for fixed WiMAX. Int. J. Recent Trends Eng. Technol. ACEEE 2014, 10, 186–202. [Google Scholar]
- Lawal, I.A.; Said, A.M.; Nisar, K.; Shah, P.A.; Mu’azu, A.r.A. Throughput performance improvement for VoIP applications in fixed WiMAX network using client–server model. J. Sci. Int. 2014, 26, 999–1002. [Google Scholar]
- Khan, A.S.; Ahmad, Z.; Abdullah, J.; Ahmad, F. A Spectrogram Image-Based Network Anomaly Detection System Using Deep Convolutional Neural Network. IEEE Access 2021, 9, 87079–87093. [Google Scholar] [CrossRef]
- Haque, M.R.; Tan, S.C.; Yusoff, Z.; Nisar, K.; Lee, C.K.; Kaspin, R.; Chowdhry, B.; Ali, S.; Memon, S. A Novel DDoS Attack-aware Smart Backup Controller Placement in SDN Design. Ann. Emerg. Technol. Comput. 2020, 4, 75–92. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network Intrusion Detection for IoT Security Based on Learning Techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Verwoerd, T.; Hunt, R. Intrusion detection techniques and approaches. Comput. Commun. 2002, 25, 1356–1365. [Google Scholar] [CrossRef]
- Li, J.; Qu, Y.; Chao, F.; Shum, H.P.H.; Ho, E.S.L.; Yang, L. Machine Learning Algorithms for Network Intrusion Detection. In Intelligent Systems Reference Library; Springer: Berlin/Heidelberg, Germany, 2018; pp. 151–179. [Google Scholar] [CrossRef]
- Prasad, R.; Rohokale, V. Artificial Intelligence and Machine Learning in Cyber Security. In Industrial Internet of Things; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2019; pp. 231–247. [Google Scholar]
- Chan, K.Y.; Abdullah, J.; Khan, A.S. A framework for traceable and transparent supply chain management for agri-food sector in malaysia using blockchain technology. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 149–156. [Google Scholar] [CrossRef]
- Balan, K.; Khan, A.S.; Julaihi, A.A.; Tarmizi, S.; Pillay, K.S.; Abdulrazak, L.F.; Sallehudin, H. RSSI and Public Key Infrastructure based Secure Communication in Autonomous Vehicular Networks. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2018, 9, 298–304. [Google Scholar] [CrossRef]
- Ali, M.H.; Al Mohammed, B.A.D.; Ismail, A.; Zolkipli, M.F. A New Intrusion Detection System Based on Fast Learning Network and Particle Swarm Optimization. IEEE Access 2018, 6, 20255–20261. [Google Scholar] [CrossRef]
- Khan, N.; Abdullah, J.; Khan, A.S. Defending malicious script attacks using machine learning classifiers. Wirel. Commun. Mob. Comput. 2017, 2017. [Google Scholar] [CrossRef]
- Yao, H.; Fu, D.; Zhang, P.; Li, M.; Liu, Y. MSML: A Novel Multilevel Semi-Supervised Machine Learning Framework for Intrusion Detection System. IEEE Internet Things J. 2019, 6, 1949–1959. [Google Scholar] [CrossRef]
- Shone, N.; Ngoc, T.N.; Phai, V.D.; Shi, Q. A Deep Learning Approach to Network Intrusion Detection. IEEE Trans. Emerg. Top. Comput. Intell. 2018, 2, 41–50. [Google Scholar] [CrossRef]
- Khan, N.; Abdullah, J.; Khan, A.S. A dynamic method of detecting malicious scripts using classifiers. Adv. Sci. Lett. 2017, 23, 5352–5355. [Google Scholar] [CrossRef]
- Marir, N.; Wang, H.; Feng, G.; Li, B.; Jia, M. Distributed Abnormal Behavior Detection Approach Based on Deep Belief Network and Ensemble SVM Using Spark. IEEE Access 2018, 6, 59657–59671. [Google Scholar] [CrossRef]
- Zubair, S.; Fisal, N.; Abazeed, M.B.; Salihu, B.A.; Shahid Khan, A. Lightweight distributed geographical: A lightweight distributed protocol for virtual clustering in geographical forwarding cognitive radio sensor networks. Int. J. Commun. Syst. 2015, 28, 1–18. [Google Scholar] [CrossRef]
- Kerrache, C.A.; Ahmad, F.; Ahmad, Z.; Lagraa, N.; Kurugollu, F.; Benamar, N. Towards an Efficient Vehicular Clouds using Mobile Brokers. In Proceedings of the International Conference on Computer and Information Sciences (ICCIS), Aljouf, Saudi Arabia, 3–4 April 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Nisar, K.; Sabir, Z.; Raja, M.A.; Ibrahim, A.A.; Erdogan, F.; Haque, M.R.; Rodrigues, J.J.; Rawat, D.B. Design of morlet wavelet neural network for solving a class of singular pantograph nonlinear differential models. IEEE Access 2021. [Google Scholar] [CrossRef]
- Xu, C.; Shen, J.; Du, X.; Zhang, F. An Intrusion Detection System Using a Deep Neural Network with Gated Recurrent Units. IEEE Access 2018, 6, 48697–48707. [Google Scholar] [CrossRef]
- Xiao, Y.; Xing, C.; Zhang, T.; Zhao, Z. An Intrusion Detection Model Based on Feature Reduction and Convolutional Neural Networks. IEEE Access 2019, 7, 42210–42219. [Google Scholar] [CrossRef]
- Jiang, K.; Wang, W.; Wang, A.; Wu, H. Network Intrusion Detection Combined Hybrid Sampling with Deep Hierarchical Network. IEEE Access 2020, 8, 32464–32476. [Google Scholar] [CrossRef]
- Khan, A.; Johari, A.; Khan, N.; Julahi, A.; Tarmizi, S. Quantum-Elliptic curve Cryptography for Multihop Communication in 5G Networks. Int. J. Comput. Sci. Netw. Secur. 2017, 17, 357–365. [Google Scholar]
- Wang, Z. Deep Learning-Based Intrusion Detection with Adversaries. IEEE Access 2018, 6, 38367–38384. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Alazab, M.; Soman, K.P.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep Learning Approach for Intelligent Intrusion Detection System. IEEE Access 2019, 7, 41525–41550. [Google Scholar] [CrossRef]
- Gu, S.; Rigazio, L. Towards deep neural network architectures robust to adversarial examples. arXiv 2014, arXiv:1412.5068. [Google Scholar]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J.; Alazab, A. A novel Ensemble of Hybrid Intrusion Detection System for Detecting Internet of Things Attacks. Electronics 2019, 8, 1210. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A Two-Level Flow-Based Anomalous Activity Detection System for IoT Networks. Electronics 2020, 9, 530. [Google Scholar] [CrossRef]
- Goyal, P.; Goyal, A. Comparative study of two most popular packet sniffing tools-Tcpdump and Wireshark. In Proceedings of the 2017 9th International Conference on Computational Intelligence and Communication Networks (CICN), Girne, Cyprus, 16–17 September 2017; pp. 77–81. [Google Scholar]
- Hoque, N.; Bhuyan, M.H.; Baishya, R.; Bhattacharyya, D.; Kalita, J. Network attacks: Taxonomy, tools and systems. J. Netw. Comput. Appl. 2014, 40, 307–324. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A Technique for Generating a Botnet Dataset for Anomalous Activity Detection in IoT Networks. In Proceedings of the 2020 IEEE International Conference on Systems, Man, and Cybernetics SMC, Toronto, ON, Canada, 11–14 October 2020; pp. 134–140. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Ambusaidi, M.A.; He, X.; Nanda, P.; Tan, Z. Building an Intrusion Detection System Using a Filter-Based Feature Selection Algorithm. IEEE Trans. Comput. 2016, 65, 2986–2998. [Google Scholar] [CrossRef]
- Saleem, M.A.; Alyas, T.; Asfandayar; Ahmad, R.; Farooq, A.; Ali, K.; Idrees, M.; Khan, A.S. Systematic literature review of identifying issues in software cost estimation techniques. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 341–346. [Google Scholar] [CrossRef]
- Usman, M.; Zubair, M.; Ahmad, Z.; Zaidi, M.; Ijyas, T.; Parayangat, M.; Wajid, M.; Shiblee, M.; Ali, S.J. Heart rate detection and classification from speech spectral features using machine learning. Arch. Acoust. 2021, 46, 41–53. [Google Scholar] [CrossRef]
- Usman, M.; Ahmad, Z.; Wajid, M. Dataset of Raw and Pre-processed Speech Signals, Mel Frequency Cepstral Coefficients of Speech and Heart Rate Measurements. In Proceedings of the 5th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 10–12 October 2019; pp. 376–379. [Google Scholar] [CrossRef]
- Bisong, E. Google Colaboratory. In Building Machine Learning and Deep Learning Models on Google Cloud Platform; Apress: Berkeley, CA, USA, 2019; pp. 59–64. [Google Scholar]
- Dildar, M.S.; Khan, N.; Abdullah, J.B.; Khan, A.S. Effective way to defend the hypervisor attacks in cloud computing. In Proceedings of the 2nd International Conference on Anti-Cyber Crimes, ICACC, Abha, Saudi Arabia, 26–27 March 2017; pp. 154–159. [Google Scholar]
- Google Research Colaboratory. 2021. Available online: https://colab.research.google.com (accessed on 10 July 2021).


| Category | IoT-Botnet Dataset | This Study | ||
|---|---|---|---|---|
| No. of Records | No. of Records | Train [75%] | Test [25%] | |
| Benign | 97197 | 97197 | 72,907 | 24,290 |
| Anomaly | 1843192 | 300520 | 225,380 | 75,140 |
| Total Samples | 1940389 | 397717 | 298,287 | 99,430 |
| Feature | Data Type | Feature | Data Type | Feature | Data Type | Feature | Data Type |
|---|---|---|---|---|---|---|---|
| Flow_ID | Categorical | Flow_IAT_Mean | Float | Pkt_Len_Max | Float | Subflow_Fwd_Pkts | Integer |
| Src_IP | Categorical | Flow_IAT_Std, | Float | Pkt_Len_Mean | Float | Subflow_Fwd_Byts | Integer |
| Src_Port | Integer | Flow_IAT_Max | Float | Pkt_Len_Std | Float | Subflow_Bwd_Pkts | Integer |
| Dst_IP | Categorical | Flow_IAT_Min | Float | Pkt_Len_Var | Float | Subflow_Bwd_Byts | Integer |
| Dst_Port | Integer | Fwd_IAT_Tot | Float | FIN_Flag_Cnt | Integer | Init_Fwd_Win_Byts | Integer |
| Protocol | Integer | Fwd_IAT_Mean | Float | SYN_Flag_Cnt | Integer | Init_Bwd_Win_Byts | Integer |
| Timestamp | Categorical | Bwd_IAT_Mean | Float | RST_Flag_Cnt | Integer | Fwd_Act_Data_Pkts | Integer |
| Flow_Duration | Integer | Fwd_IAT_Max | Float | PSH_Flag_Cnt | Integer | Fwd_Seg_Size_Min | Integer |
| Tot_Fwd_Pkts | Integer | Fwd_IAT_Min | Float | ACK_Flag_Cnt | Integer | Active_Mean | Float |
| Tot_Bwd_Pkts | Integer | Bwd_IAT_Tot | Float | URG_Flag_Cnt | Integer | Active_Std | Float |
| TotLen_Fwd_Pkts | Float | Bwd_IAT_Mean.1 | Float | CWE_Flag_Count | Integer | Active_Max | Float |
| TotLen_Bwd_Pkts | Float | Bwd_IAT_Std | Float | ECE_Flag_Cnt | Integer | Active_Min | Float |
| Fwd_Pkt_Len_Max | Float | Bwd_IAT_Max | Float | Down/Up_Ratio | Float | Idle_Mean | Float |
| Fwd_Pkt_Len_Min | Float | Bwd_IAT_Min | Float | Pkt_Size_Avg | Float | Idle_Std | Float |
| Fwd_Pkt_Len_Mean | Float | Fwd_PSH_Flags | Integer | Fwd_Seg_Size_Avg | Float | Idle_Max | Float |
| Fwd Pkt Len Std | Float | Bwd_PSH_Flags | Integer | Bwd_Seg_Size_Avg | Float | Idle_Min | Float |
| Bwd Pkt Len Max | Float | Fwd_URG_Flags | Integer | Fwd_Byts/b_Avg | Float | Label | Integer |
| Bwd Pkt Len Min | Float | Bwd_URG_Flags | Integer | Fwd_Pkts/b_Avg | Integer | Cat | Categorical |
| Bwd Pkt Len Mean | Float | Bwd_Header_Len | Integer | Fwd_Blk_Rate_Avg | Integer | Sub_Cat | Categorical |
| Bwd_Pkt_Len_Std | Float | Fwd_Pkts/s | Float | Bwd_Byts/b_Avg | Integer | ||
| Flow_Byts/s | Float | Bwd_Pkts/s | Float | Bwd_Pkts/b_Avg | Integer | ||
| Flow_Pkts/s | Float | Pkt_Len_Min | Float | Bwd_Blk_Rate_Avg | Integer |
| PREDICTED CLASS | |||
|---|---|---|---|
| ANOMALY | BENIGN | ||
| ACTUAL CLASS | ANOMALY | True Positive () | False Negative () |
| BENIGN | False Positive () | True Negative () | |
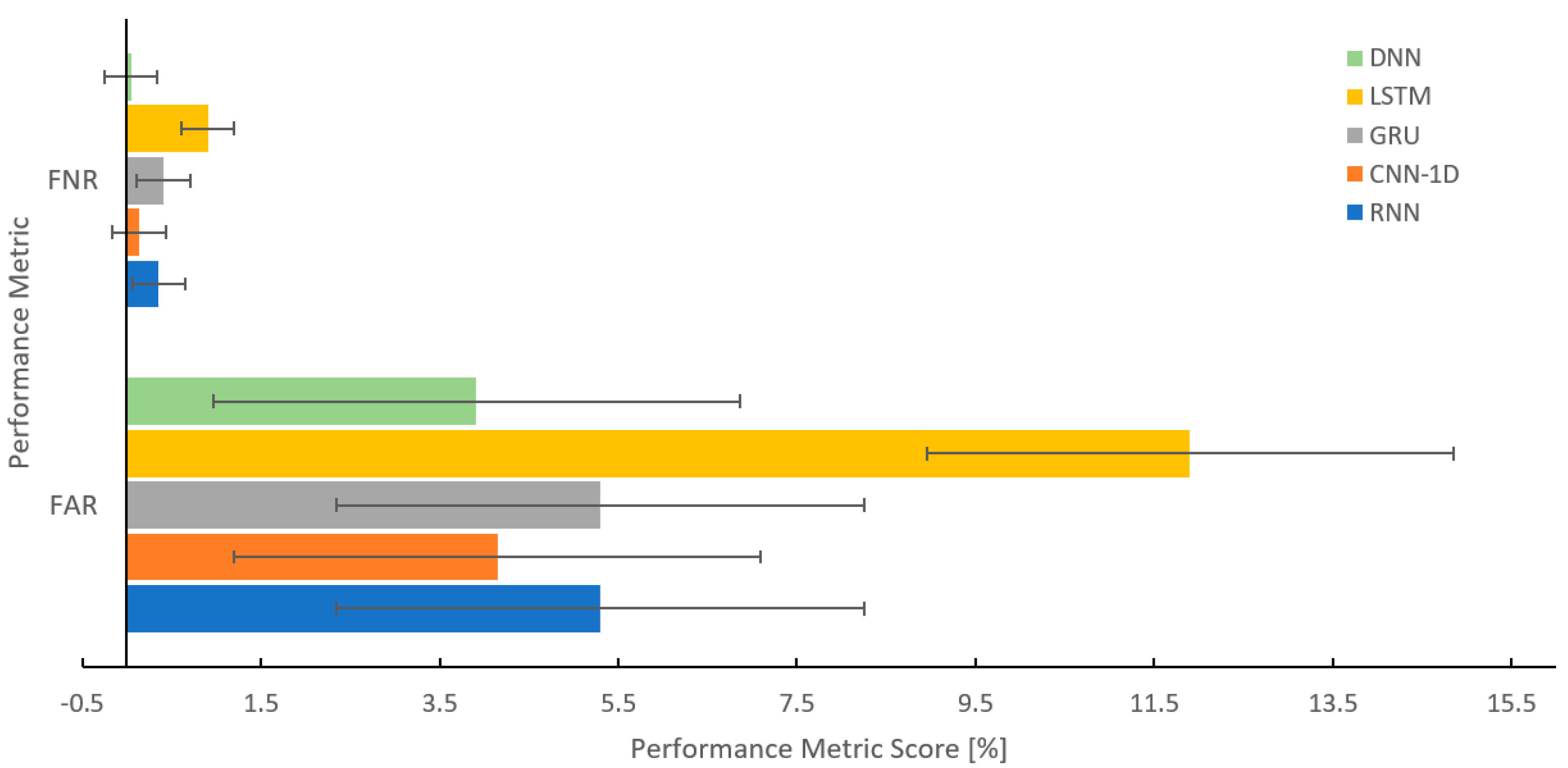
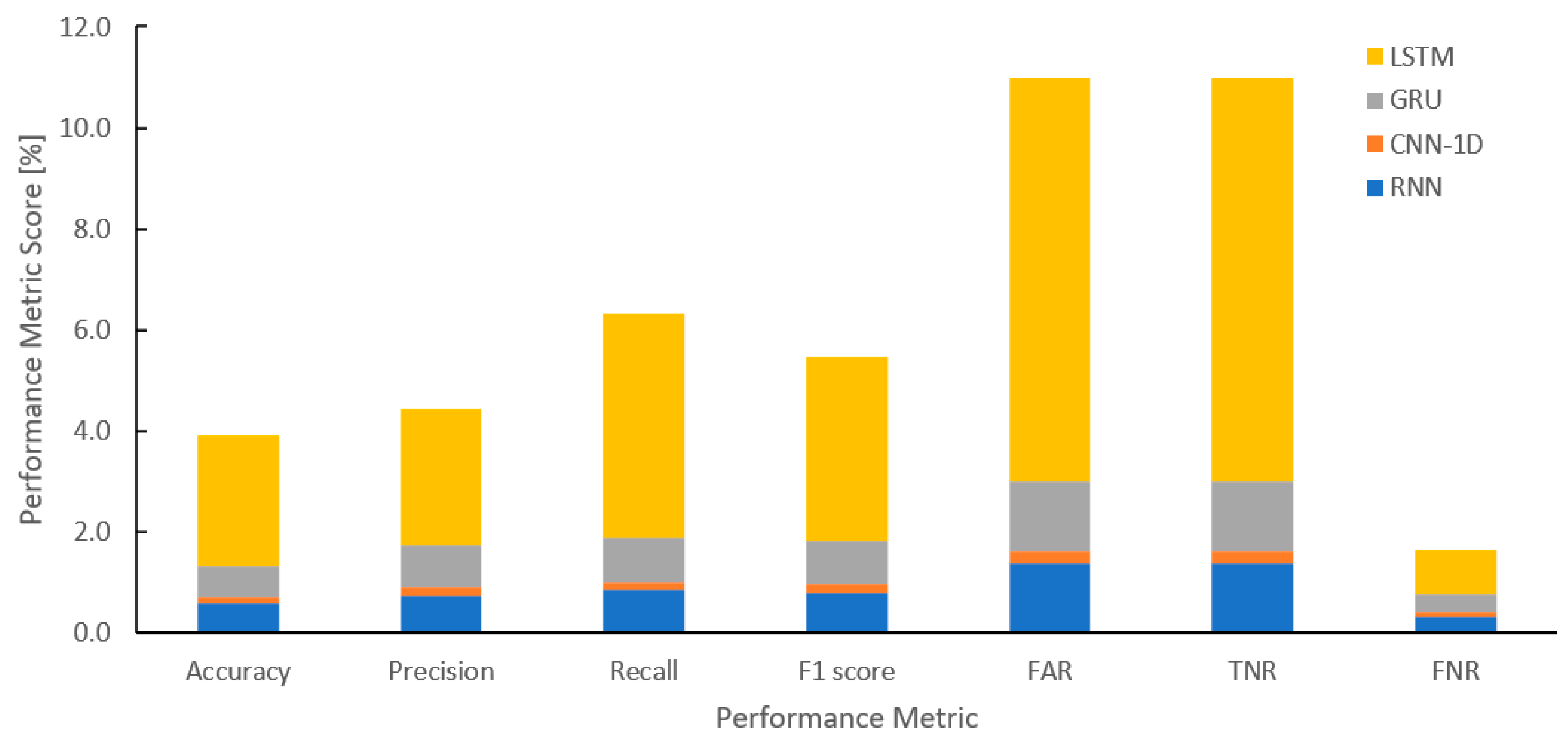
| DL Algorithms | Accuracy | Precision | Recall | F1 Score | FAR | TNR | FNR |
|---|---|---|---|---|---|---|---|
| RNN | 98.435 | 98.579 | 97.170 | 97.850 | 5.303 | 94.697 | 0.357 |
| CNN-1D | 98.882 | 99.113 | 97.857 | 98.466 | 4.146 | 95.854 | 0.140 |
| GRU | 98.394 | 98.491 | 97.143 | 97.795 | 5.303 | 94.697 | 0.411 |
| LSTM | 96.410 | 96.594 | 93.597 | 94.980 | 11.902 | 88.098 | 0.904 |
| DNN | 99.010 | 99.304 | 98.020 | 98.642 | 3.915 | 96.085 | 0.044 |
| DL Algorithms | Anomaly | Benign | ||||
|---|---|---|---|---|---|---|
| Precision | Recall | F1-Score | Precision | Recall | F1-Score | |
| RNN | 98.309 | 99.643 | 98.972 | 98.848 | 94.697 | 96.728 |
| CNN-1D | 98.676 | 99.860 | 99.265 | 99.551 | 95.854 | 97.668 |
| GRU | 98.308 | 99.589 | 98.944 | 98.674 | 94.697 | 96.645 |
| LSTM | 96.263 | 99.096 | 97.659 | 96.925 | 88.098 | 92.301 |
| DNN | 98.750 | 99.956 | 99.349 | 99.859 | 96.085 | 97.936 |
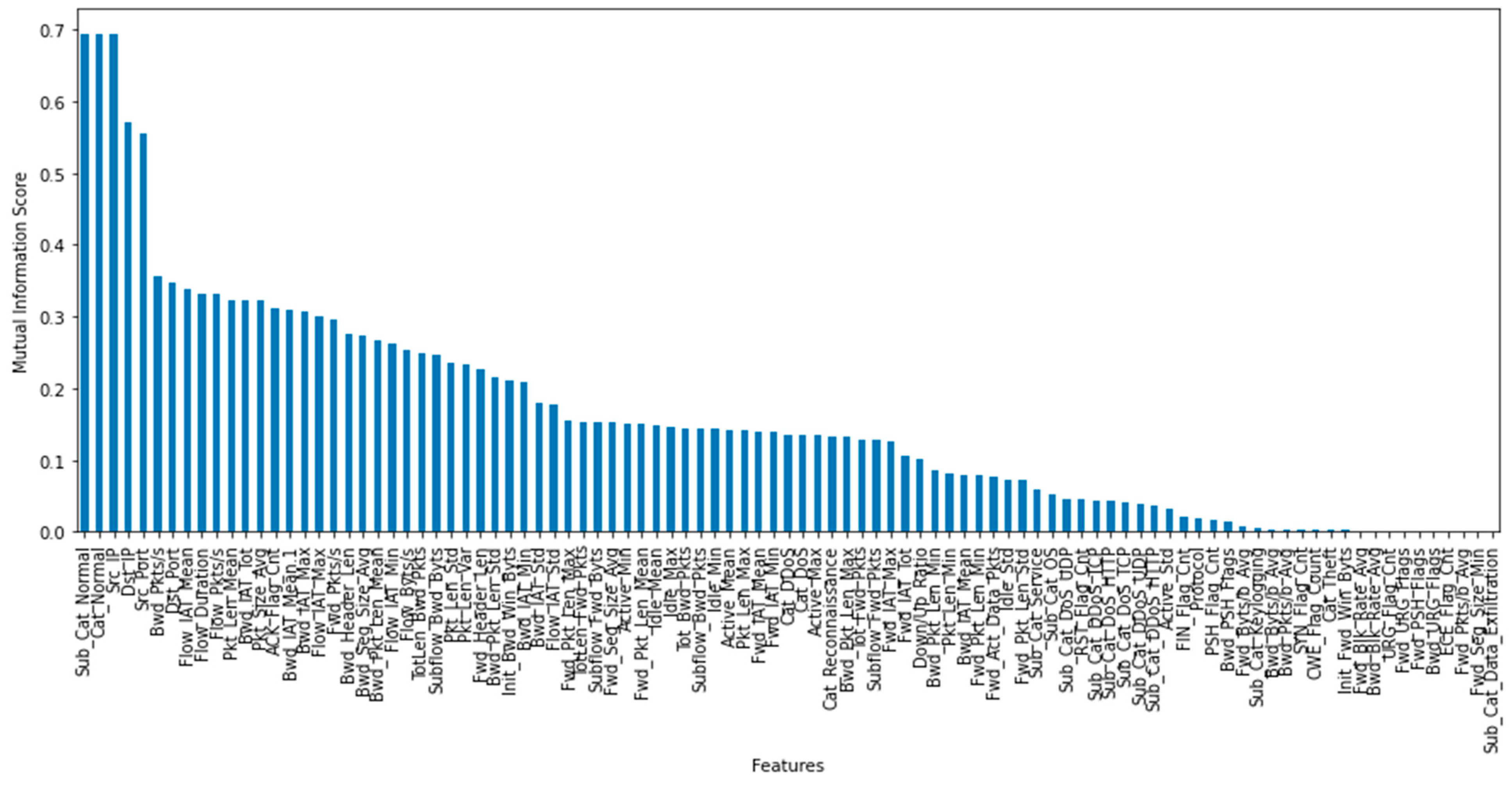
| Feature | MI Score | Feature | MI Score | Feature | MI Score |
|---|---|---|---|---|---|
| Cat_Normal | 0.694397 | Sub_Cat_Normal | 0.693928 | Src_IP | 0.693317 |
| Dst_IP | 0.573648 | Src_Port | 0.559126 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmad, Z.; Shahid Khan, A.; Nisar, K.; Haider, I.; Hassan, R.; Haque, M.R.; Tarmizi, S.; Rodrigues, J.J.P.C. Anomaly Detection Using Deep Neural Network for IoT Architecture. Appl. Sci. 2021, 11, 7050. https://doi.org/10.3390/app11157050
Ahmad Z, Shahid Khan A, Nisar K, Haider I, Hassan R, Haque MR, Tarmizi S, Rodrigues JJPC. Anomaly Detection Using Deep Neural Network for IoT Architecture. Applied Sciences. 2021; 11(15):7050. https://doi.org/10.3390/app11157050
Chicago/Turabian StyleAhmad, Zeeshan, Adnan Shahid Khan, Kashif Nisar, Iram Haider, Rosilah Hassan, Muhammad Reazul Haque, Seleviawati Tarmizi, and Joel J. P. C. Rodrigues. 2021. "Anomaly Detection Using Deep Neural Network for IoT Architecture" Applied Sciences 11, no. 15: 7050. https://doi.org/10.3390/app11157050
APA StyleAhmad, Z., Shahid Khan, A., Nisar, K., Haider, I., Hassan, R., Haque, M. R., Tarmizi, S., & Rodrigues, J. J. P. C. (2021). Anomaly Detection Using Deep Neural Network for IoT Architecture. Applied Sciences, 11(15), 7050. https://doi.org/10.3390/app11157050








