Cybersecurity and Privacy Risk Assessment of Point-of-Care Systems in Healthcare—A Use Case Approach
Abstract
1. Introduction
2. Proposed Use Case Overview
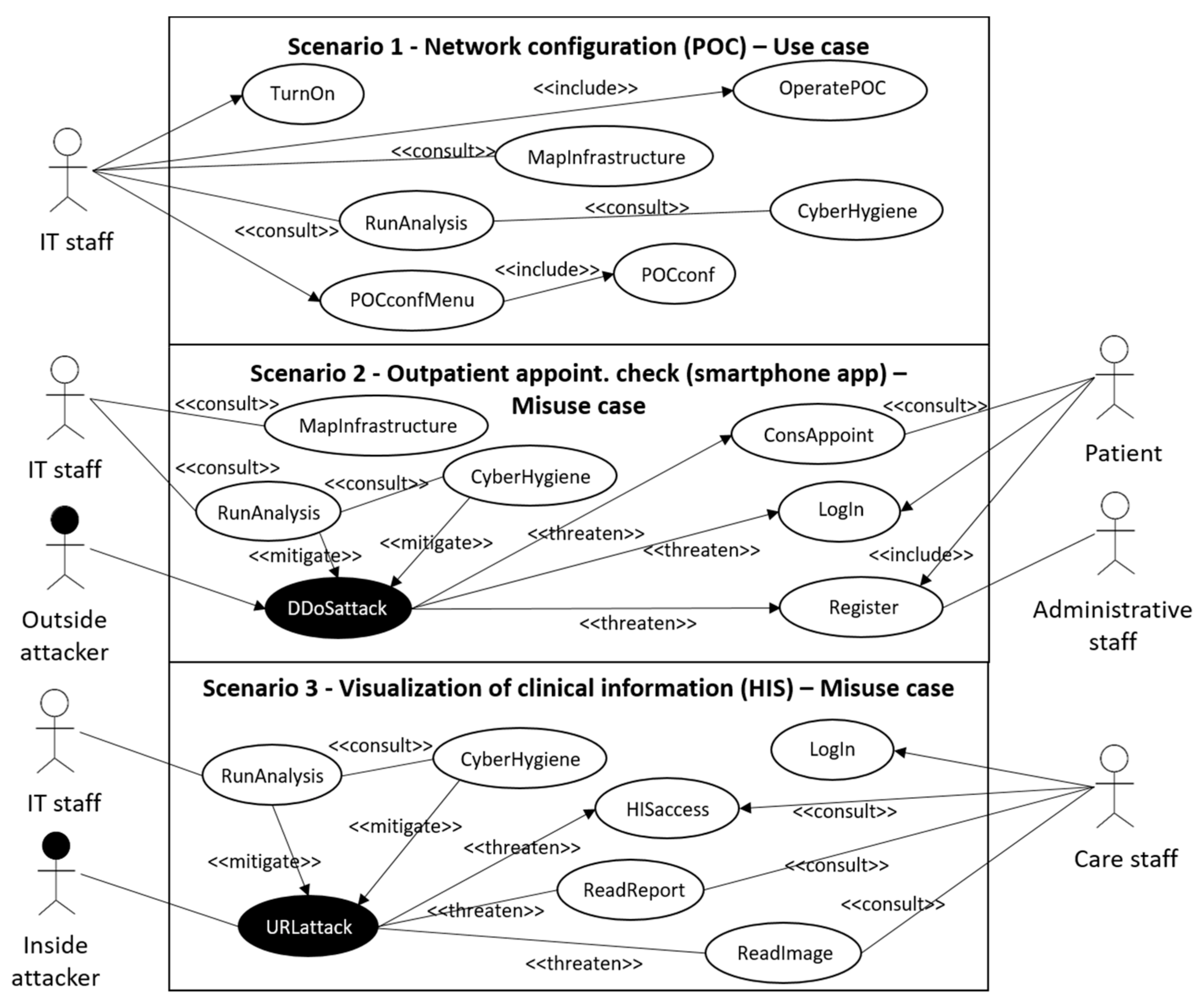
Use Case Validation Scenarios
- Scenario 1: network configuration (POC)
- Scenario 2: outpatient appointment check (smartphone app)
- Scenario 3: visualization of clinical information (HIS)
3. Develop Technical Infrastructure and CUREX Tools
CUREX Platform Solution
- ADT scans the infrastructure and identifies the entities and resources that have direct connection with the HIS [18]. A list of assets (including IP addresses, open ports, services and/or operating systems running in each asset) is generated by the ADT and shared accordingly with other CUREX tools. It is worth noting that for this particular scenario, the ADT has discovered that some workstations are running outdated versions of the operating system (OS).
- Upon reception of the asset list, VDM performs a vulnerability scanning, using as input the list of IP addresses discovered by the ADT. As a result, VDM generates a report containing a list of security vulnerabilities associated to all the hospital’s resources (assets) detected in the network’s hospital infrastructure [23]. In particular, the VDM report contains a list of critical exploitable vulnerabilities against the outdated OS, and it is initially shared with KEA for further analysis.
- Upon reception of the vulnerability report, KEA performs a machine learning analysis using the log events generated in the infrastructure in order to detect new threat patterns that could potentially harm the system [24]. New threat patterns are added to the VDM, which enriches the vulnerability report to be shared with other CUREX tools.
- TIE receives the enriched vulnerability report by the VDM and in parallel, receives logs from events originated in the end-user’s infrastructure. In particular, TIE employs anomaly detection and analytics to detect intrusion and malicious activities using a variety of tools and techniques. As a result, TIE is able to generate correlated alarms indicating potential threat incidents detected in the monitored infrastructure. The generated alarms are then shared with other CUREX tools for further processing and analysis. In this example, a URL-attack is detected against one of the resources, which can potentially give uncontemplated access to the HIS database. The generated alarms are then shared with other CUREX tools for further processing and analysis.
- CAT receives a list of vulnerabilities from the VDM, and a list of events and alarms from TIE, which along with the risk pattern models and configuration configured by the infrastructure IT managers, provides the required input to perform a cybersecurity analysis. As a result, global and individual scores are generated, making it possible to identify critical events to assign priorities for their treatment. For each score, a set of mitigation measures is proposed by CAT. The generated CAT scores are stored in the PrB, and the list of mitigation measures is shared with OST [20] for its analysis and optimization. Regarded the considered example, one of the provided mitigations provided in the generated list and selected by the IT user could be “map inputs values to actual filenames/URLs, etc., and reject all other inputs”, which is highly efficient and with medium associated cost of implementation.
- In parallel, PAT also receives the vulnerability report from VDM and performs a privacy risk assessment of the organization and the platform by evaluating GDPR compliance [25]. Similar to CAT, a set of mitigation measures is proposed by PAT [26]. The generated PAT scores are stored in the PrB, and the list of mitigation measures is shared with OST for its analysis and optimization.
- OST receives in real time the CAT and PAT mitigation measures and performs an optimal safeguard analysis based on values of costs and efficacy provided by the end-user. As a result, the OST displays in its dashboard the list of mitigation measures ranked by priority. This output is also stored in the PrB.
- PrB receives on the one hand the CAT and PAT scores, and on the other hand, the mitigation measures from OST. CAT and PAT qualitative scores are merged, and a unified risk score is generated.
- After the optimal mitigation measures are applied to the systems and their infrastructure by the IT end-user, a new scan from the ADT will be performed and the process restart from Step 1 to finally end with the CAT and/or PAT results that will decrease accordingly during the new risk assessment.
4. Pilot Plan and Validation Test Steps
5. Discussion on Risk Assessment Capability
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Jalali, M.S.; Kaiser, J.P. Cybersecurity in Hospitals: A Systematic, Organizational Perspective. J. Med. Internet Res. 2018, 20, e10059. [Google Scholar] [CrossRef] [PubMed]
- Jofre, M. Holistic View of Healthcare Cybersecurity Ecosystem; Research Gate GmbH: 2020. Available online: https://www.researchgate.net/publication/343722649_Holistic_View_Of_Healthcare_Cybersecurity_Ecosystem (accessed on 21 July 2021).
- Tulasidas, S.; Mackay, R.; Hudson, C.; Balachandran, W. Security Framework for Managing Data Security within Point of Care Tests. J. Softw. Eng. Appl. 2017, 10, 2. [Google Scholar] [CrossRef][Green Version]
- Williams, P.A.; Woodward, A.J. Cybersecurity vulnerabilities in medical devices: A complex environment and multifaceted problem. Med. Devices 2015, 8, 305–316. [Google Scholar] [CrossRef] [PubMed]
- Reason, J. Human error: Models and management. BMJ 2000, 320, 768–770. [Google Scholar] [CrossRef] [PubMed]
- Sardi, A.; Rizzi, A.; Sorano, E.; Guerrieri, A. Cyber Risk in Health Facilities: A Systematic Literature Review. Sustainability 2020, 12, 7002. [Google Scholar] [CrossRef]
- Wagner, I.; Boiten, E. Privacy Risk Assessment: From Art to Science, by Metrics. In Data Privacy Management, Cryptocurrencies and Blockchain Technology; Springer: Cham, Switzerland, 2018; pp. 225–241. [Google Scholar] [CrossRef]
- Hameed, S.S.; Hassan, W.H.; Latiff, L.A.; Ghabban, F. A systematic review of security and privacy issues in the internet of medical things; the role of machine learning approaches. PeerJ Comput. Sci. 2021, 7, e414. [Google Scholar] [CrossRef] [PubMed]
- Coronado, A.J.; Wong, T.L. Healthcare Cybersecurity Risk Management: Keys to an Effective Plan. Biomed. Instrum. Technol. 2014, 48, 26–30. [Google Scholar] [CrossRef] [PubMed]
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. IoT cyber risk: A holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process. EURASIP J. Inf. Secur. 2020, 2020, 8. [Google Scholar] [CrossRef]
- Applying UML and Patterns: An Introduction to Object-Oriented Analysis and Design and Iterative Development, Third Edition [Book]. Available online: https://www.oreilly.com/library/view/applying-uml-and/0131489062/ (accessed on 26 April 2021).
- Sindre, G.; Opdahl, A.L. Eliciting security requirements with misuse cases. Requir. Eng. 2005, 10, 34–44. [Google Scholar] [CrossRef]
- Cockburn, A. Writing Effective Use Cases, 3rd ed.; Addison-Weley: Reading, MA, USA, 2001. [Google Scholar]
- Constantine, L.L.; Lockwood, L.A.D. Software for Use: A Practical Guide to the Models and Methods of Usage-Centered Design, 1st ed.; Addison-Wesley: Reading, MA, USA, 1999; Available online: https://www.oreilly.com/library/view/software-for-use/9780768685305/ (accessed on 26 April 2021).
- Jacobson, I.; Christerson, M. Object-Oriented Software Engineering: A Use Case Driven Approach, 1st ed.; Addison-Weley: Reading, MA, USA, 1992. [Google Scholar]
- Yue, T.; Briand, L.C.; Labiche, Y. Facilitating the transition from use case models to analysis models: Approach and experiments. ACM Trans. Softw. Eng. Methodol. 2013, 22, 1–5:38. [Google Scholar] [CrossRef]
- CUREX|Secure and Private Health Data Exchange. Available online: https://curex-project.eu/ (accessed on 26 April 2021).
- Diaz-Honrubia, A.J.; Gonzalez, A.R.; Zamorano, J.M.; Jiménez, J.R.; Gonzalez-Granadillo, G.; Diaz, R.; Konidi, M.; Papachristou, P.; Nifakos, S.; Kougka, G.; et al. An Overview of the CUREX Platform. In Proceedings of the 2019 IEEE 32nd International Symposium on Computer-Based Medical Systems (CBMS), Cordoba, Spain, 5–7 June 2019; pp. 162–167. [Google Scholar] [CrossRef]
- Mohammadi, F.; Panou, A.; Ntantogian, C.; Karapistoli, E.; Panaousis, E.; Xenakis, C. CUREX: seCUre and pRivate hEalth data eXchange. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence-Companion Volume, New York, NY, USA, 14 October 2019; pp. 263–268. [Google Scholar] [CrossRef]
- Panda, S.; Panaousis, E.; Loukas, G.; Laoudias, C. Optimizing Investments in Cyber Hygiene for Protecting Healthcare Users. January 2020. Available online: http://arxiv.org/abs/2001.03782 (accessed on 15 March 2021).
- Jofre, M. Minimum Quality Standard for Cybersecurity Training in Healthcare–SecureHospitals.eu; ResearchGate. 2020. Available online: https://www.researchgate.net/publication/343722644_Minimum_quality_standard_for_cybersecurity_training_in_healthcare_-_SecureHospitalseu (accessed on 21 July 2021).
- Fernàndez-Bayó, J.; Barbero, O.; Rubies, C.; Sentís, M.; Donoso, L. Distributing Medical Images with Internet Technologies: A DICOM Web Server and a DICOM Java Viewer. Radiographics 2000, 20, 581–590. [Google Scholar] [CrossRef] [PubMed]
- Gonzalez-Granadillo, G.; Diaz, R.; Veroni, E. A Multi-Factor Assessment Mechanism to Define Priorities on Vulnerabilities Affecting Healthcare Organizations; ITASEC 2021; p. 13. Available online: http://cgi.di.uoa.gr/~xenakis/Published/93-A%20Multi-factor%20Assessment%20Mechanism%20to%20Define%20Priorities%20on%20Vulnerabilities%20affecting%20Healthcare%20Organizations/VDM-CameraReady.pdf (accessed on 26 April 2021).
- Bellas, C.; Naskos, A.; Kougka, G.; Vlahavas, G.; Gounaris, A.; Vakali, A.; Papadopoulos, A.; Biliri, E.; Bountouni, N.; Granadillo, G.G. A Methodology for Runtime Detection and Extraction of Threat Patterns. SN Comput. Sci. 2020, 1, 238. [Google Scholar] [CrossRef]
- Data Protection. European Commission-European Commission. Available online: https://ec.europa.eu/info/law/law-topic/data-protection_en (accessed on 16 May 2021).
- Papamartzivanos, D.; Menesidou, S.A.; Gouvas, P.; Giannetsos, T. A Perfect Match: Converging and Automating Privacy and Security Impact Assessment On-the-Fly. Future Internet 2021, 13, 30. [Google Scholar] [CrossRef]
- Mai, P.X.; Goknil, A.; Shar, L.K.; Pastore, F.; Briand, L.C.; Shaame, S. Modeling Security and Privacy Requirements: A Use Case-Driven Approach. Inf. Softw. Technol. 2018, 100, 165–182. [Google Scholar] [CrossRef]
- Boeckl, K.; Fagan, M.; Fisher, W.; Lefkovitz, N.; Megas, K.N.; Nadeau, E.; O’Rourke, D.G.; Piccarreta, B.; Scarfone, K. Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks; NIST IR 8228; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019. [CrossRef]
- Lin, T.-W.; Hsu, C.-L. FAIDM for Medical Privacy Protection in 5G Telemedicine Systems. Appl. Sci. 2021, 11, 1155. [Google Scholar] [CrossRef]
- Zhang, P.; Schmidt, D.C.; White, J.; Lenz, G. Chapter One-Blockchain Technology Use Cases in Healthcare. In Advances in Computers; Raj, P., Deka, G.C., Eds.; Elsevier: Amsterdam, The Netherlands, 2018; Volume 111, pp. 1–41. [Google Scholar] [CrossRef]
- McFarland, R.J.; Olatunbosun, S.B. An Exploratory Study on the Use of Internet_of_Medical_Things (IoMT) in the Healthcare Industry and Their Associated Cybersecurity Risks; ICOMP’19 2019; p. 7. Available online: https://www.proquest.com/openview/c3d186a57f9cae20d87d6f5d5f9f92a9/1?pq-origsite=gscholar&cbl=1976348 (accessed on 20 July 2021).
- Wang, L.; Jones, R. Big Data, Cybersecurity, and Challenges in Healthcare. In Proceedings of the 2019 SoutheastCon, Huntsville, AL, USA, 11–14 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Grguric, A.; Khan, O.; Ortega-Gil, A.; Markakis, E.K.; Pozdniakov, K.; Kloukinas, C.; Medrano-Gil, A.M.; Gaeta, E.; Fico, G.; Koloutsou, K. Reference Architectures, Platforms, and Pilots for European Smart and Healthy Living—Analysis and Comparison. Electronics 2021, 10, 1616. [Google Scholar] [CrossRef]
- Anastasopoulou, K.; Mari, P.; Magkanaraki, A.; Spanakis, E.G.; Merialdo, M.; Sakkalis, V.; Magalini, S. Public and private healthcare organisations: A socio-technical model for identifying cybersecurity aspects. In Proceedings of the 13th International Conference on Theory and Practice of Electronic Governance, New York, NY, USA, 23 September 2020; pp. 168–175. [Google Scholar] [CrossRef]
- Joint Task Force Transformation Initiative. Guide for Conducting Risk Assessments. National Institute of Standards and Technology; NIST Special Publication (SP) 800-30 Rev. 1; NIST Special Publication: Gaithersburg, MD, USA, 2012. [CrossRef]
- Yannis, N. D3.3 Vulnerability Assessment as a Service v1. WP3—Cyber Security Risk Assessment & Beyond—Sphinx Intelligence. SPHINX Consortium. 2019. Available online: https://ec.europa.eu/research/participants/documents/downloadPublic?documentIds=080166e5d0ebe11a&appId=PPGMS (accessed on 16 July 2021).
- Common Vulnerability Scoring System. Wikipedia. 21 June 2021. Available online: https://en.wikipedia.org/w/index.php?title=Common_Vulnerability_Scoring_System&oldid=1029633418 (accessed on 17 July 2021).
- Agile Practice Guide|Project Management Institute. Available online: https://www.pmi.org/pmbok-guide-standards/practice-guides/agile (accessed on 17 May 2021).
- Azarm-Daigle, M.; Kuziemsky, C.; Peyton, L. A Review of Cross Organizational Healthcare Data Sharing. Procedia Comput. Sci. 2015, 63, 425–432. [Google Scholar] [CrossRef]
- Vanclay, F. International Principles for Social Impact Assessment. Impact Assess. Proj. Apprais. 2003, 21, 5–12. [Google Scholar] [CrossRef]
- Petrie, H.; Bevan, N. The Evaluation of Accessibility, Usability, and User Experience; Stepanidis, C., Ed.; CRC Press: Boca Raton, FL, USA, 2009. [Google Scholar] [CrossRef]
- Alrahbi, D.; Khan, M.; Hussain, M. Exploring the motivators of technology adoption in healthcare. Int. J. Healthc. Manag. 2021, 14, 50–63. [Google Scholar] [CrossRef]
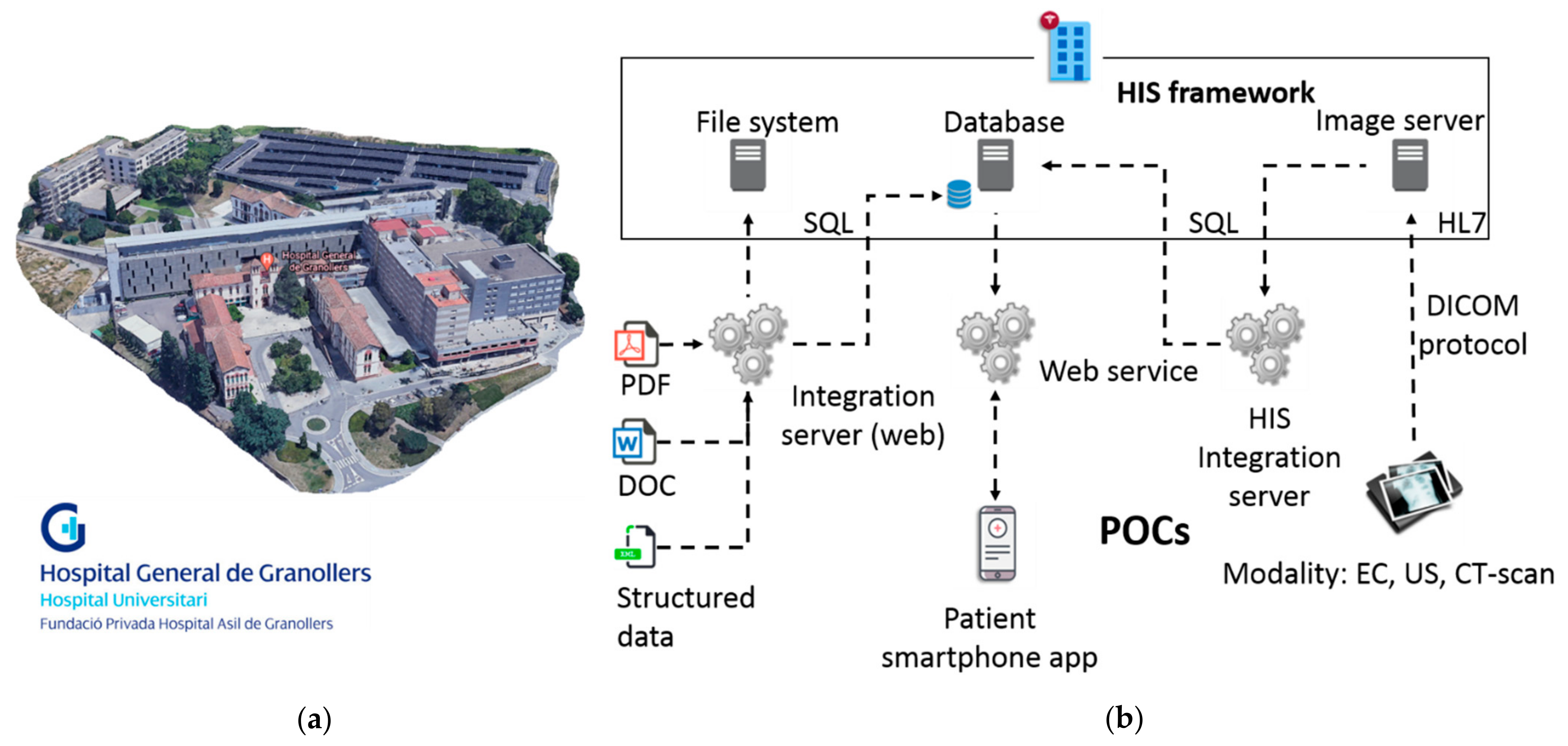
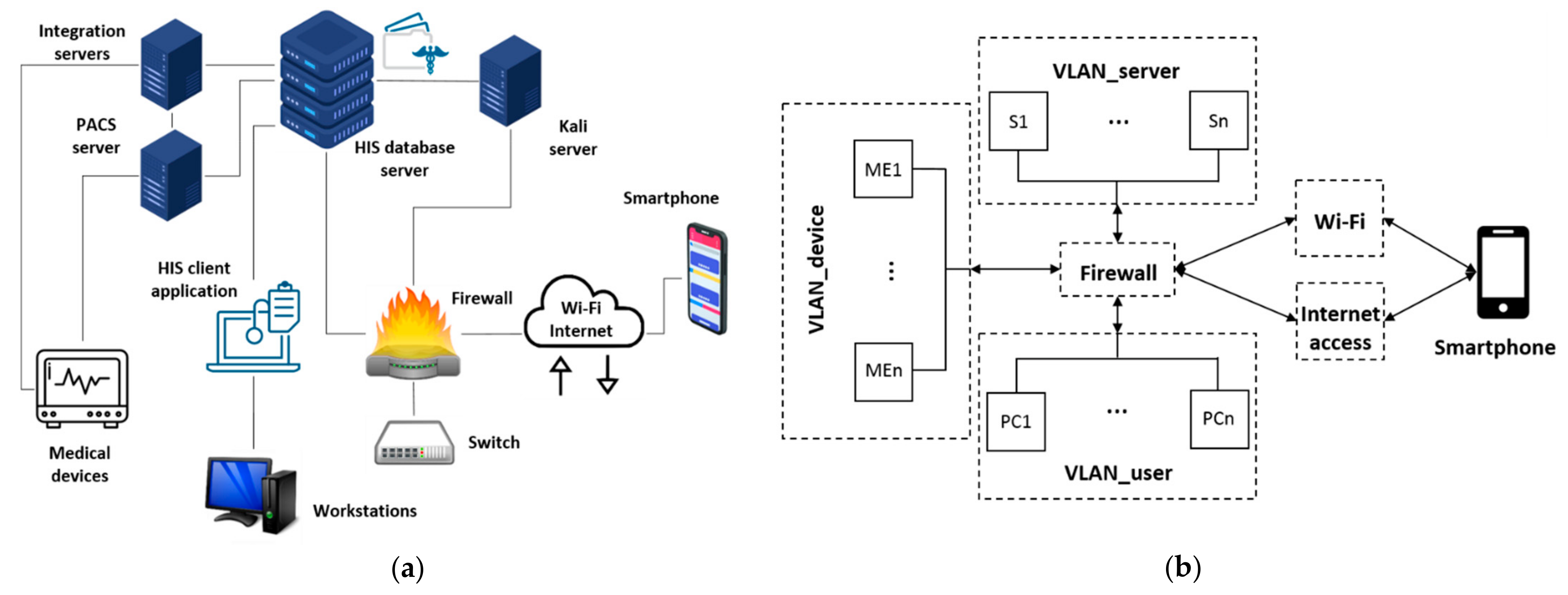

| Main Components | VLANs |
|---|---|
| HIS client application: either accessed from the CITRIX server farm or from a PC that has the client version installed locally, connects to the HIS database, which is installed in the hospital’s data center (DC). Workstations: 4 PCs are placed inside VLAN user with the basic programs together with hospital’s user credential handling procedures (credentials). HIS database server: consists of a cluster of servers that contains all the information stored. Kali Linux Server: Debian-based Linux distribution aimed at advanced penetration testing and security auditing. Firewall: The hospital’s DC is generally supervised by a firewall system in which specific rules are programmed. VLAN user, VLAN server and VLAN device are connected bi-directionally to the firewall. Switch: Dedicated 20G LACP link to the cluster of servers and a 10G LACP link to the rest of the network’s elements. PACS image server: Images are stored on a server called PACS (picture and archiving communications system). To retrieve the images, from the HIS, a call is made to a URL through a unique identifier of the patient’s image study. Integration server: Used to collect all the data and external files and integrate them into HIS, either in the database or on the file server, or by external links using identifiers. Medical equipment: Two medical devices and an emulator are placed in VLAN_device. Medical devices can be real hardware or simulated/emulated software. Smartphone: Connection through Wi-Fi (open Wi-Fi validated via capture portal), using a specific identification that the firewall allows it to be visible and operating for this use case scenario; and/or using internet access (back-bone connection or mobile connection 3G/4G). | The firewall is configured to sectorize the use case in four virtual networks and controls the visibility of the three VLANs, the Wi-Fi and internet access to allow connecting the smartphone to the pre-production infrastructure. User, server and device VLANs are connected bi-directionally to the firewall. PCs in VLAN_user with the basic programs and user credential handling procedures. Servers in VLAN_server with: integration engines, HIS, image server, and service integrators. Medical devices in VLAN_device with real hardware preferably; otherwise simulated/emulated. Smartphone in Wi-Fi (open Wi-Fi validated via captive portal) with app test version installed. |
| IP | Host | Notes | System | Domain | Name | IP/Port Number | |
|---|---|---|---|---|---|---|---|
| 172.21.40.2 | DEVCUREXSAVAC | HIS server CUREX | Centos 7.7, BBDD Oracle 11.2.0.4.0 | 40 | CUREX_SERVER | 172.21.40.0/24 | |
| 172.21.40.3 | PREPACS | Preproduction PACS server CUREX | Windows 2016, IIS. Ports DICOM 1010, 1011 and 104 | 41 | CUREX_USER | 172.21.41.0/24 | |
| 172.21.40.4 | PREPACSSQL | Preproduction PACS SQL server CUREX | Windows 2016, SQL Server | 42 | CUREX_ME | 172.21.42.0/24 | |
| 172.21.40.5 | DEVCUREXSAVI05 | Integration HIS sever CUREX | Windows 2012, Apache Tomcat | ||||
| 172.21.40.6 | DEVCUREXSAVIFS | HIS Template server CUREX | Windows 2012, File server | ||||
| 172.21.40.7 | DEVCURESSAVIFS1 | HIS Reports server CUREX | Windows 2012, File server | IP | Host | Mask | System |
| 172.21.40.8 | DEVCUREXXASVC01 | Virtualisation server CUREX | Windows 2012R2 Citrix Server | 172.21.41.2 | pccurex01 | 255.255.255.0 | Windows 10 |
| 172.21.40.9/24 | DEVCUREXADT01 | Asset Discovery server Curex_Server | OVA | 172.21.41.3 | pccurex02 | 255.255.255.0 | Windows 10 |
| 172.21.41.5/24 | DEVCUREXADT02 | Asset Discovery server Curex_User | OVA | 172.21.41.4 | pccurex03 | 255.255.255.0 | Windows 10 |
| Information Sharing Capacity | POC Medical Devices and Emulated Devices | Smartphone Addresable Information |
|---|---|---|
| Implemented 3 sectorizations (VLANs) of the IT infrastructure (managed by the general Firewall). Mounted and configured 8 servers. 3 working stations/PCs. Two hardware medical devices and one software emulator device. HIS mounted and capacity to generate simulated data in several formats (word documents, pdfs, etc.). Smartphone test application and server with access to the use case infrastructure. | Medical Device 1: Ultrasound Siemens Acuson Antares. Medical Device 2: Electrocardiogram RDPC Technic Assistance heart tablet. Emulated Medical Device 1: professional modality simulator (mounted in the infrastructure and configured). X-ray machine RAÏM modality simulator. | When the smartphone is connected to the infrastructure: the connection is via Wi-Fi (or other internet access proxies). It is relevant to monitor the app server, and less relevant the app terminal itself. The app server is configured to support a test app. The app server is a regular server, but also configured for the test app for the use case. The app server provides simulated data to the SAVAC_CUREX (HIS). |
| Item | Description |
|---|---|
| Involved Partners | The use case pilot is executed involving participants at the hospital facilities. It is convenient for the execution of the pilot because the participants will use computers enabled to run the steps of the defined validations on the develop infrastructure. Furthermore, the preamble presentations and interview/focus groups are hosted as well at the piloting premises with the involvement of the participants and use case managers. |
| Participants | IT staff. It is the group composed of professionals belonging to the IT department of the hospital. They have experience with the technical aspects of the HIS, medical devices and cybersecurity. Assistance staff. It is the group composed of medical doctors and nurses, who may belong to different medical specialties. These professionals have knowledge and experience in consulting clinical information in the HIS. Administrative outpatient staff. It is the group composed of professionals belonging to the hospital outpatient administrative staff. These professionals have knowledge and regularly plan the appointments for the patients of the hospital. |
| Short Description | The hospital IT department has raised concerns about the cybersecurity issues that may emerge from the operation and the communication of the clinical data. Indeed, since the data contains highly sensitive personal information, it must be ensured that the hospitals’ information systems are properly maintained, and any vulnerabilities are identified and timely patched. In addition, since the hospital has the technical capability of generating data reports and exchanging them with third parties, the platform must ensure that proper cybersecurity and privacy safeguards are in place in order to protect the integrity of the data and—most importantly—the patient safety. Consequently, the hospital decides to adopt the CUREX platform in order to address these issues immediately. In conjunction with optimal recommended safeguards, CUREX will deliver targeted measures for raising the cyber hygiene of healthcare organizations through the recommendation of strategies and methodologies for training and raising awareness activities, targeted towards healthcare employees (administration, medical, and IT personnel) on cybersecurity and privacy risks incurred during data exchange. Training will involve the development of cybersecurity defending skills, e.g., empowering social engineering de-fences. In this way, healthcare employees will feel more confident in handling and ex-changing sensitive data and improve their capabilities to perform their daily professional tasks effectively and in a secure fashion. |
| Timeline | The pilot execution will consist of two phases, following the Agile Flow Review methodology, in order to provide feedback to the tool owners and means of validation. Enough participants are involved in the pilots to collect sufficient result in order to generate relevant outcomes. Therefore, more than one session with different participants is executed. In general, each session will last 4 h, consisting of the preamble presentation, running the relevant scenarios of the pilot and conducting the interviews/focus group. Given that three working stations are available in the mounted infrastructure, each session can consist of six participants covering the three different types described above. Around four sessions in the timeframe of the first phase of the pilot can be executed. Depending on the outcome of the first stage of the pilot, the second phase of the pilot can be arranged as explained before, or adjustments of the planning can be arranged. |
| Preconditions | The CUREX framework has modelled, monitored and assessed the HIS infrastructure. As a result, the CUREX framework is able to provide assessment scores and give a proper set of cybersecurity and privacy recommendations to the hospital in the form of reports and manuals dictating possible best practices to correct issues identified in the infrastructure. Furthermore, the involved CUREX tools have been properly configured. |
| Preamble | A preamble PowerPoint presentation will be given and explained to each participant for them to better understand the use case and CUREX solution in general. |
| Step # | Description of Tasks | Step to Execute | Expected Results |
|---|---|---|---|
| Scenario 1—Network Configuration (POC)—Use Case Scenario | |||
| 1 | Turn on medical devices and emulators | IT participant presses turn-on buttons of the two medical devices and initiate the emulator | Medical devices and emulator operating |
| 2 | Mapping of original IT infrastructure | IT participant executes CUREX ADT tool | Map the IT infrastructure with servers and devices present |
| 3 | Operating medical devices and emulator | IT participant capture information for the two medical devices and display CT image from emulator | Confirmation of the proper operation of the medical devices and emulator |
| 4 | Access to medical device configuration section | IT participant operates the configuration menu of one of the medical devices (with user and password) | Access (possible risk of default password) |
| 5 | Modify the network configuration data and modify roles and permissions on the firewall | IT participant introduces new IP address link for the medical device and the firewall | Modified original emitter details for the medical device and firewall |
| 6 | Mapping of updated IT infrastructure | IT participant executes CUREX ADT tool | CUREX detect different correlation between IP and MAC address |
| 7 | Operating medical devices and emulator | IT participant captures information for the two medical devices and display CT image from emulator | Confirmation of the proper operation of the medical devices and emulator |
| 8 | Execution of CUREX platform | IT participant runs CUREX analysis and annotates score from the CVT. Both IT participant and participant perform the feasible recommendations if needed | Score should be low, then participant performs the feasible recommendations given by CUREX to improve the resilience on cyber-security, privacy and cyber hygiene on the items related to this Test |
| Scenario 2—Outpatient Appointment Check (Smartphone App)—Misuse Case Scenario | |||
| 1 | Mapping of original IT infrastructure | IT participant executes CUREX ADT tool | Map the IT infrastructure with servers and devices present |
| 2 | Simulate registering at front desk (private part of the test app) | IT participants creates and stores new user and credentials in the test app | Simulated administrative staff provides credentials |
| 3 | Participant logs in with new credentials | User participant opens app using the mobile phone and log in with PIN | Access to the private/confidential section of the test app |
| 4 | Participant consults the pending appointments | User participant clicks on the appointments section of the app | Webservice is launched and receives response of the appointments listed in the HIS |
| 5 | The test app is turned off (simulating DoS attack) | IT participant turns down the app test configuration (potentially it can be simulated with Kali Linux server as a DoS attack) | No petitions are served |
| 6 | Mapping of original IT infrastructure | IT participant executes CUREX ADT tool | Map of the IT infrastructure with servers and devices present |
| 7 | Participants checks the detailed information of a specific appointment | User participant click on a specific appointment | Out-of-service message is received |
| 8 | Execution of CUREX platform | IT participant runs CUREX analysis and annotates score from the CVT. Both IT participant and user participant perform the feasible recommendations if needed | Score should be medium, then participant performs the feasible recommendations given by CUREX to re-establish the score to low and to improve the resilience on cyber-security, privacy and cyber hygiene on the items related to this test |
| Scenario 3—Visualization of Clinical Information (HIS)—Misuse Case Scenario | |||
| 1 | Login to Windows sessions | User participant introduces credentials | Log in against active directory. |
| 2 | Login to CITRIX | User participant validates that the credential displayed in CITRIX are the same as Windows | Credential pass-through to CITRIX that will present the icons of those applications that the user has configured |
| 3 | Login to HIS | User participant clicks on HIS client icon and introduce credentials | Access to HIS |
| 4 | Access to clinical history | User participant searches and clicks on “Visión Global” of the specific simulated patient | Structured data of HIS |
| 5 | Selection of report | User participant clicks on specific simulated report “informat” | Access to report |
| 6 | Selection radiological procedure (image) | User participant clicks on specific simulated CT image “RX button” | Open image in an external DICOM viewer through URL call, with a specific identifying unique number |
| 7 | Capture of image URL before pop-up Windows auto-closes (minimum and only security protection) | User participant clicks on specific simulated CT image “RX button” and copies the url from the web browser | Capture of the url call |
| 8 | Open web browser and manipulate iteratively the URL (simulating URL hacking attack) | User participant captures the url for the image call in the web browser and changes the last number of the line (potentially done automatically with Kali Linux server with a man-in-the-middle attack) | Access to different images |
| 9 | Execution of CUREX platform | IT participant runs CUREX analysis and annotates score from the CVT. Both IT participant and user participant perform the feasible recommendations if needed | Score should be high, then IT participant implements the feasible recommendations given by CUREX to re-establish the score to low and to improve the resilience on cyber-security, privacy and cyber hygiene on the items related to this test |
| Cybersecurity and Privacy Requirements | Priority/Domain | Description |
| Securing integrity information regarding risk assessment and interactions with the infrastructure | Mandatory/Cybersecurity | The complete monitoring and assessment flow must be reflected in the private blockchain contents providing support for the fact that end components can connect and disconnect without prior notice. |
| Check credentials match from previous steps | Optional/Cybersecurity | Credentials must be passed between steps, from the medical staff, which informs them on the system, to the SAVAC system. Each step must get and pass the credentials through the next step. The CUREX system should monitor, as an important part of its risk assessment phase whether these holds. |
| Verify/check that registration number and patient ID are not correlated | Optional/Privacy | The patient must provide a valid identification number to the medical staff in order to search for his/her history. The system needs a way to correlate the patient history number with a European unique patient history number. |
| Database and communication channel assessment | Mandatory/Cybersecurity | Data must travel safely between database and front-end HIS application. Communication network must ensure no data sniffing or data loss, and no third party can change the data between the database and the front-end. Patient data is involved. |
| Assessments/safeguards regarding prevention of URL headers from being hacked | Optional/Cybersecurity and Privacy | Application headers are formatted text that can be modified. If this occurs, an attacker could see image from another patient and/or the image can be saved in another patient record history. |
| Cyber hygiene level of target groups | Mandatory/Cybersecurity and Privacy | Targeting different groups (e.g., care staff, IT staff, administrative staff) cyber hygiene strategies should increase awareness on cyber security and the new GDPR. |
| User friendly interface of tools and applications | Mandatory/Cybersecurity and Privacy | Targets digital infrastructures, but is meant to be operated to a significant extent by non-IT experts. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jofre, M.; Navarro-Llobet, D.; Agulló, R.; Puig, J.; Gonzalez-Granadillo, G.; Mora Zamorano, J.; Romeu, R. Cybersecurity and Privacy Risk Assessment of Point-of-Care Systems in Healthcare—A Use Case Approach. Appl. Sci. 2021, 11, 6699. https://doi.org/10.3390/app11156699
Jofre M, Navarro-Llobet D, Agulló R, Puig J, Gonzalez-Granadillo G, Mora Zamorano J, Romeu R. Cybersecurity and Privacy Risk Assessment of Point-of-Care Systems in Healthcare—A Use Case Approach. Applied Sciences. 2021; 11(15):6699. https://doi.org/10.3390/app11156699
Chicago/Turabian StyleJofre, Marc, Diana Navarro-Llobet, Ramon Agulló, Jordi Puig, Gustavo Gonzalez-Granadillo, Juan Mora Zamorano, and Ramon Romeu. 2021. "Cybersecurity and Privacy Risk Assessment of Point-of-Care Systems in Healthcare—A Use Case Approach" Applied Sciences 11, no. 15: 6699. https://doi.org/10.3390/app11156699
APA StyleJofre, M., Navarro-Llobet, D., Agulló, R., Puig, J., Gonzalez-Granadillo, G., Mora Zamorano, J., & Romeu, R. (2021). Cybersecurity and Privacy Risk Assessment of Point-of-Care Systems in Healthcare—A Use Case Approach. Applied Sciences, 11(15), 6699. https://doi.org/10.3390/app11156699







