Enabling Blockchain Based SCM Systems with a Real Time Event Monitoring Function for Preemptive Risk Management
Abstract
:1. Introduction
- (1)
- Building a resilient blockchain approach for achieving intelligent supply chain management.
- (2)
- Incorporating an event-monitoring system model to share emergent information by detecting real-time events at the early stage for preemptive management in supply chains.
2. Related Work
3. System Model
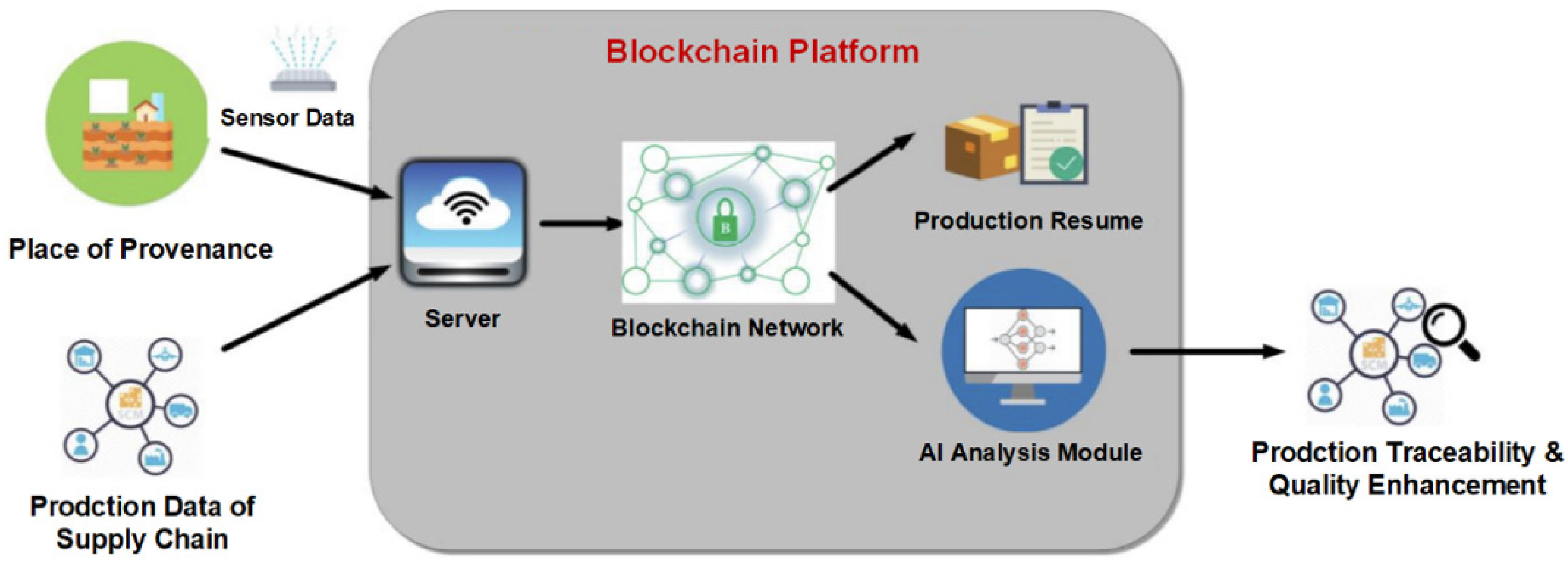
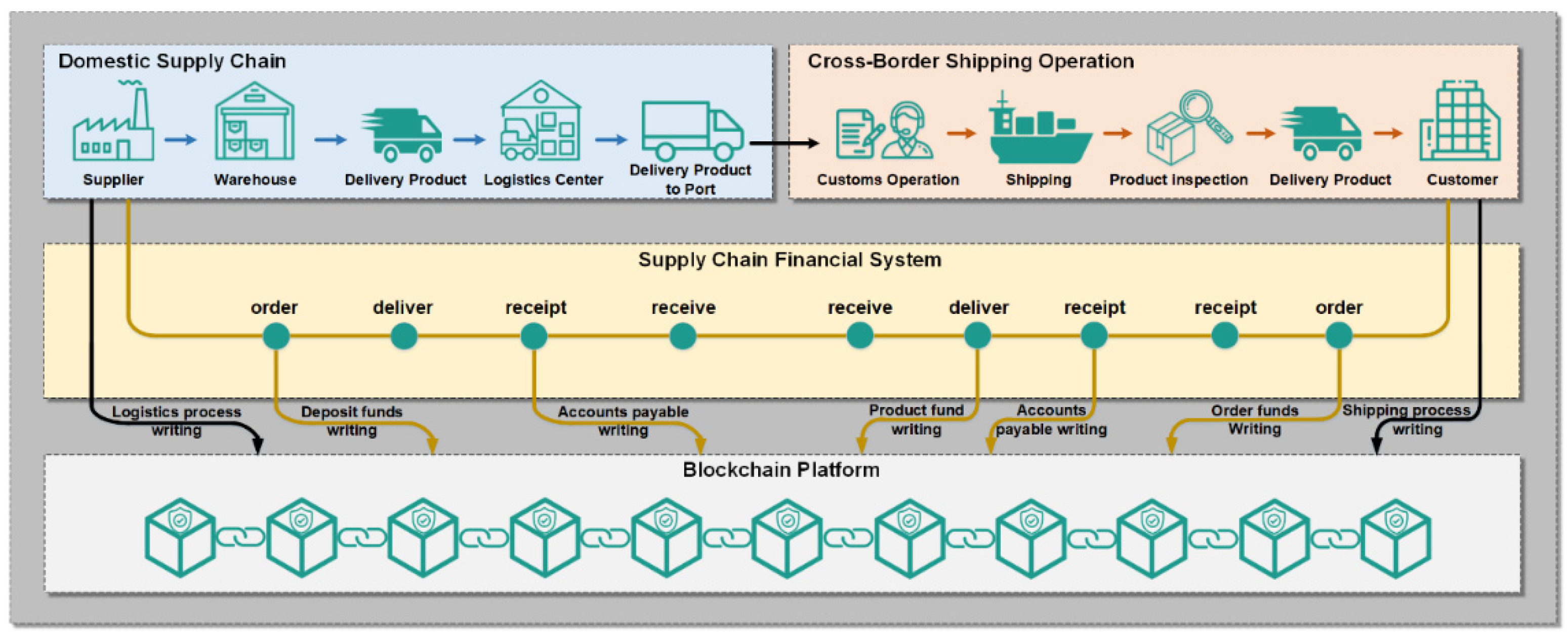
3.1. A Blockchain Based Information Sharing System for the Supply Chains
3.2. System Framework
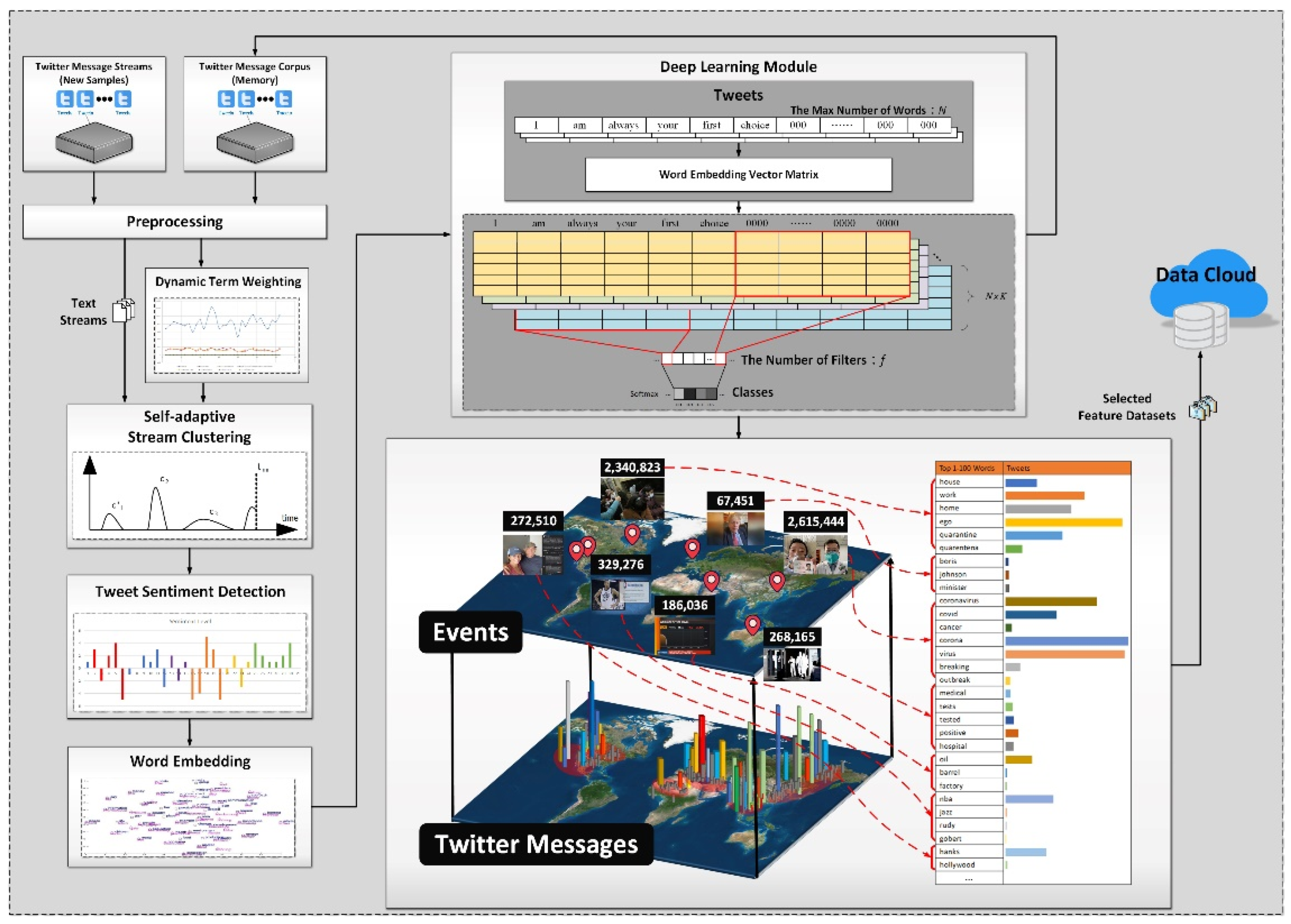
4. A Twitter-Based Event Detection Method for Monitoring Emergency Events
4.1. A Twitter-Based Real-Time Event Detection Method
Event Modelling Using Twitter Text Streams
4.2. Event Monitoring Using the Developed Twitter Based Real-Time Event Detection Method
4.3. Twitter Sentiment as an Early Warning Indicator for Event Monitoring of Emergency Events
5. Case Study and Experiments
5.1. Experimented with Event Related Index and Indictor for Event Monitoring of a Real World Case (COVID-19 Epidemic Outbreaks)
Case Study: “COVID-19 Spread on the Global Supply Chain on 2020” Event
- Jan 25: Production stop at suppliers in China;
- Feb 11: Port operations stop in China;
- Feb 25: Shortage in distribution centers worldwide;
- March 11: Re-start production in China;
- March 13: Extended quarantine measures in Europe and the USA.
5.2. Experimented with Designed Smart Contracts for Adaptive Supply Chain Management
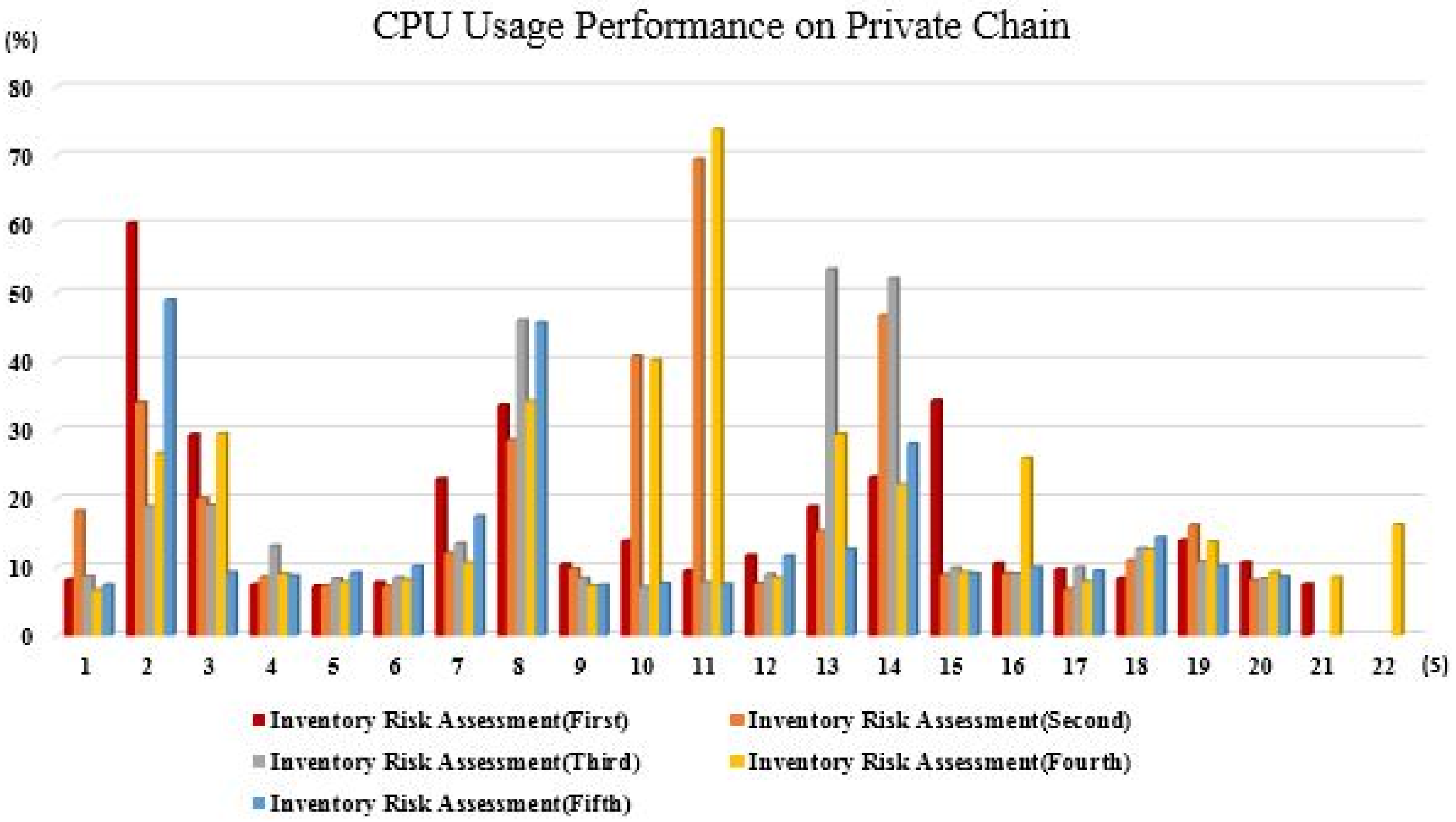
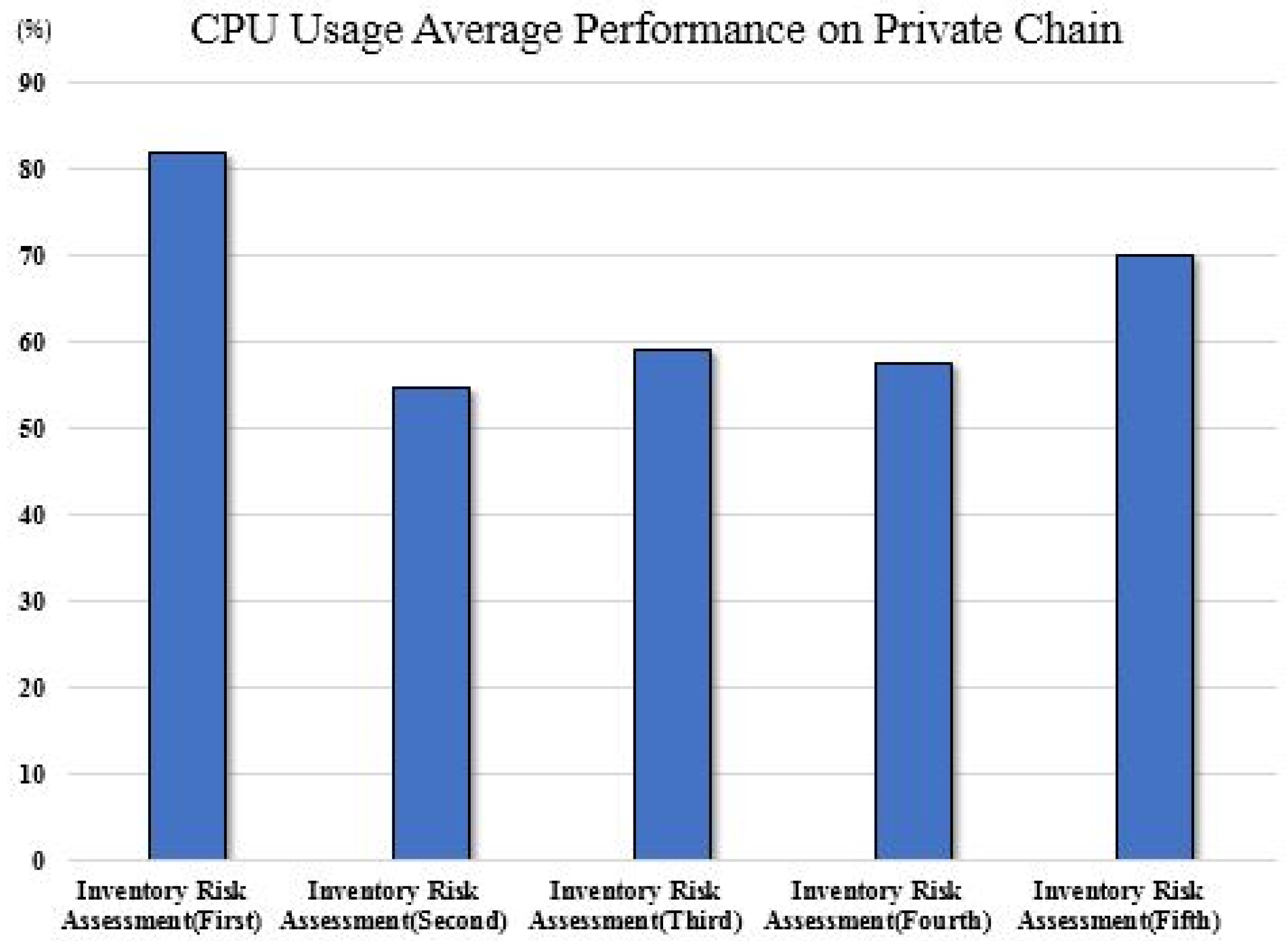
5.3. Simulation Results
6. Discussion
- (1)
- The experimental results demonstrated that the total cost of using our system is very low, and the implemented system is very simple to apply.
- (2)
- In many reported use cases [64], in blockchain-based supply chain systems, on-chain records and off-chain repositories can interoperate as needed. As stated previously, in this work, we have developed a blockchain-based platform and decentralized applications to provide users with an assessment of global market conditions based on real-world conditions and status updates in the blockchain. As blockchain has limited storage, the data has been stored on-chain and off-chain. The system monitors the situation in the external world (off-chain) and the blockchain world (on-chain). The connection between the on-chain and off-chain world can be fulfilled by the automatic execution mechanism of a smart contract on the platform. This allows the original SCM system and the blockchain system to work at the same time, regardless of whether they work together or separately, without reducing the performance of the existing SCM system.
- (3)
- “Smart contract” is employed in this work as an automatic execution and control tool for the supply chain management. In the developed blockchain system, when the conditions meet the set conditions, the scripts as contracts will be triggered automatically by the distributed blockchain system. Using the functionality of blockchain, there is no central power that has the right to change a smart contract unless every node on the blockchain system comes to a consensus.
- (4)
- In our experiments, once the impact of an external event (i.e., the values of selected external indicators or indexes) reaches the smart contract setting value, the corresponding function will be executed. The set value represents the emergency state in the real world. When the system detects certain unsafe event-related status, it will automatically execute the previously set supply chain response function. In our experiments, once an abnormal event situation from the event-monitoring system is found, the smart contracts start to work. Therefore, in our case on the smart contracts, the company can set the threshold as a risk level based on the VIX index under actual conditions. In the real world, with the help of blockchain smart contracts, all necessary supply chain transaction functions can be automatically enforced in an emergency. Therefore, in the early stage of an emergency, the preemptive supply chain management measures will be taken for the purpose of avoiding risks.
- (5)
- In this work, the proposed system model has not yet completed the function of the “predictive monitoring” paradigm for forecasting event development. This is due to the large amount of relevant data required and the complexity of some unknown events. For some very challenging cases, such as the COVID-19 pandemic, the prediction of the future development of the pandemic is fundamentally challenged by the inherent uncertainty of many “unknown unknowns,” not only with the infectious virus itself, but also intertwined with human, social, and political factors, which develop together and keep the pandemic’s future boundless. These unknown unknowns mislead accuracy-oriented predictions [65]. However, the main contribution of our work is to utilize the proposed system to help us detect and track real-time events at an early stage. We need such a system to monitor the development of emergency events to activate appropriate supply chain actions to cope with possible supply chain disruption.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Caridi, M.; Moretto, A.; Perego, A.; Tumino, A. The benefits of supply chain visibility: A value assessment model. Int. J. Prod. Econ. 2014, 151, 1–19. [Google Scholar] [CrossRef]
- Anner, M. Worker resistance in global supply chains: Wildcat strikes, international accords and transnational campaigns. Int. J. Labour Res. 2015, 7, 17–34. [Google Scholar]
- Handfield, R.B.; Graham, G.; Burns, L. Coronavirus, Tariffs, Trade Wars and Supply Chain Evolutionary Design. Int. J. Oper. Prod. Manag. 2020, 40, 1649–1660. [Google Scholar] [CrossRef]
- Dasaklis, T.K.; Pappis, C.P.; Rachaniotis, N.P. Epidemics control and logistics operations: A review. Int. J. Prod. Econ. 2012, 139, 393–410. [Google Scholar] [CrossRef]
- Ivanov, D. Predicting the impacts of epidemic outbreaks on global supply chains: A simulation-based analysis on the coronavirus outbreak (COVID-19/SARS-CoV-2) case. J. Transp. Res. Part E Logist. Transp. Rev. 2020, 136, 101922. [Google Scholar] [CrossRef] [PubMed]
- Ponomarov, S.Y.; Holcomb, M.C. Understanding the concept of supply chain resilience. Int. J. Logist. Manag. 2009, 20, 124–143. [Google Scholar] [CrossRef]
- Ribeiro, J.P.; Barbosa-Povoa, A. Supply Chain Resilience: Definitions and quantitative modelling approaches—A literature review. J. Comput. Ind. Eng. 2018, 115, 109–122. [Google Scholar] [CrossRef]
- Li, S.; Ragu-Nathan, B.; Ragu-Nathan, T.S.; Rao, S.S. The impact of supply chain management practices on competitive advantage and organizational performance. J. Omega 2006, 34, 107–124. [Google Scholar] [CrossRef]
- Fiala, P. Information sharing in supply chains. J. Omega 2005, 33, 419–423. [Google Scholar] [CrossRef]
- Wu, L.; Chuang, C.H.; Hsu, C.H. Information sharing and collaborative behaviors in enabling supply chain performance: A social exchange perspective. Int. J. Prod. Econ. 2014, 148, 122–132. [Google Scholar] [CrossRef]
- Dominguez, R.; Cannella, S.; Barbosa-Póvoa, A.P.; Framinan, J.M. Information sharing in supply chains with heterogeneous retailers. J. Omega 2018, 79, 116–132. [Google Scholar] [CrossRef]
- Scholten, K.; Schilder, S. The role of collaboration in supply chain resilience. Supply Chain Manag. Int. J. 2015, 20, 471–484. [Google Scholar] [CrossRef]
- Jain, V.; Kumar, S.; Soni, U.; Chandra, C. Supply chain resilience: Model development and empirical analysis. Int. J. Prod. Res. 2017, 55, 6779–6800. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Khan, M.K.; Kumar, N. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Queiroz, M.M.; Wamba, S.F. Blockchain adoption challenges in supply chain: An empirical investigation of the main drivers in India and the USA. Int. J. Inf. Manag. 2019, 46, 70–82. [Google Scholar] [CrossRef]
- Tian, F. A supply chain traceability system for food safety based on HACCP, blockchain & Internet of things. In Proceedings of the IEEE 2017 International Conference on Service Systems and Service Management, Dalian, China, 16–18 June 2017; pp. 1–6. [Google Scholar]
- Caro, M.P.; Ali, M.S.; Vecchio, M.; Giaffreda, R. Blockchain-based traceability in Agri-Food supply chain management: A practical implementation. In Proceedings of the IEEE 2018 IoT Vertical and Topical Summit on Agriculture-Tuscany (IOT Tuscany), Tuscany, Italy, 8–9 May 2018; pp. 1–4. [Google Scholar]
- Perboli, G.; Musso, S.; Rosano, M. Blockchain in logistics and supply chain: A lean approach for designing real-world use cases. J. IEEE Access 2018, 6, 62018–62028. [Google Scholar] [CrossRef]
- Kshetri, N. 1 Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inf. Manag. 2018, 39, 80–89. [Google Scholar] [CrossRef] [Green Version]
- Leng, K.; Bi, Y.; Jing, L.; Fu, H.C.; Van Nieuwenhuyse, I. Research on agricultural supply chain system with double chain architecture based on blockchain technology. J. Future Gener. Comput. Syst. 2018, 86, 641–649. [Google Scholar] [CrossRef]
- Mao, D.; Wang, F.; Hao, Z.; Li, H. Credit evaluation system based on blockchain for multiple stakeholders in the food supply chain. Int. J. Environ. Res. Public Health 2018, 15, 1627. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chang, S.E.; Chen, Y.C.; Lu, M.F. Supply chain re-engineering using blockchain technology: A case of smart contract based tracking process. J. Technol. Forecast. Soc. Chang. 2019, 144, 1–11. [Google Scholar] [CrossRef]
- Zhang, D.; Sheng, Z.; Du, J.; Jin, S. A study of emergency management of supply chain under supply disruption. Neural Comput. Appl. 2014, 24, 13–20. [Google Scholar] [CrossRef]
- Thomas, V.A.; Mahanty, B. Assessment of emergency sourcing strategy of a supply chain through dynamic simulation approach. J. Ind. Prod. Eng. 2020, 37, 56–69. [Google Scholar] [CrossRef]
- Trkman, P.; McCormack, K. Supply chain risk in turbulent environments—A conceptual model for managing supply chain network risk. Int. J. Prod. Econ. 2009, 119, 247–258. [Google Scholar] [CrossRef]
- Vishnubhotla, A.K.; Pati, R.K.; Padhi, S.S. Can Projects on Blockchain Reduce Risks in Supply Chain Management?: An Oil Company Case Study. J. SAGE 2020, 9, 189–201. [Google Scholar] [CrossRef]
- Layaq, M.W.; Goudz, A.; Noche, B.; Atif, M. Blockchain Technology as a Risk Mitigation Tool in Supply Chain. Int. J. Transp. Eng. Technol. 2019, 5, 49–56. [Google Scholar]
- Yoon, J.; Talluri, S.; Yildiz, H.; Sheu, C. The value of Blockchain technology implementation in international trades under demand volatility risk. Int. J. Prod. Res. 2020, 58, 2163–2183. [Google Scholar] [CrossRef]
- Garvey, M.D.; Carnovale, S.; Yeniyurt, S. An analytical framework for supply network risk propagation: A Bayesian network approach. Eur. J. Oper. Res. 2015, 243, 618–627. [Google Scholar] [CrossRef]
- Ghadge, A.; Wurtmann, H.; Seuring, S. Managing climate change risks in global supply chains: A review and research agenda. Int. J. Prod. Res. 2020, 58, 44–64. [Google Scholar] [CrossRef]
- Queiroz, M.; Ivanov, D.; Dolgui, A.; Wamba, S.F. Impacts of epidemic outbreaks on supply chains: Mapping a research agenda amid the COVID-19 pandemic through a structured literature review. Ann. Oper. Res. 2020, 1–38. [Google Scholar] [CrossRef]
- Ivanov, D.; Dolgui, A. A digital supply chain twin for managing the disruption risks and resilience in the era of Industry 4.0. Prod. Plan. Control 2020, 1–14. [Google Scholar] [CrossRef]
- Singh, N.P.; Singh, S. Building supply chain risk resilience. Int. J. Benchmarking 2019, 26, 2318–2342. [Google Scholar] [CrossRef]
- Ivanov, D.; Dolgui, A.; Sokolov, B.; Ivanova, M. Literature review on disruption recovery in the supply chain. Int. J. Prod. Res. 2017, 55, 6158–6174. [Google Scholar] [CrossRef]
- Zsidisin, G.A. A grounded definition of supply risk. J. Purch. Supply Manag. 2003, 9, 217–224. [Google Scholar] [CrossRef]
- Shao, X.F.; Dong, M. Supply disruption and reactive strategies in an assemble-to-order supply chain with time-sensitive demand. IEEE Trans. Eng. Manag. 2010, 59, 201–212. [Google Scholar] [CrossRef]
- Bueno-Solano, A.; Cedillo-Campos, M.G. Dynamic impact on global supply chains performance of disruptions propagation produced by terrorist acts. Transp. Res. Part E Logist. Transp. Rev. 2014, 61, 1–12. [Google Scholar] [CrossRef]
- Oh, B.; Jun, T.J.; Yoon, W.; Lee, Y.; Kim, S.; Kim, D. Enhancing Trust of Supply Chain Using Blockchain Platform with Robust Data Model and Verification Mechanisms. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics (SMC), Bari, Italy, 6–9 October 2019; pp. 3504–3511. [Google Scholar]
- Min, H. Blockchain technology for enhancing supply chain resilience. Bus. Horiz. 2019, 62, 35–45. [Google Scholar] [CrossRef]
- Choi, T.M.; Wen, X.; Sun, X.; Chung, S.H. The mean-variance approach for global supply chain risk analysis with air logistics in the blockchain technology era. Transp. Res. Part E Logist. Transp. Rev. 2019, 127, 178–191. [Google Scholar] [CrossRef]
- Moberg, C.R.; Cutler, B.D.; Gross, A.; Speh, T.W. Identifying antecedents of information exchange within supply chains. Int. J. Phys. Distrib. Logist. Manag. 2002, 32, 755–770. [Google Scholar] [CrossRef]
- Lau, J.S.; Huang, G.Q.; Mak, K.L. Impact of information sharing on inventory replenishment in divergent supply chains. Int. J. Prod. Res. 2004, 42, 919–941. [Google Scholar] [CrossRef]
- Casado-Vara, R.; González-Briones, A.; Prieto, J.; Corchado, J.M. Smart Contract for Monitoring and Control of Logistics Activities: Pharmaceutical Utilities Case Study. In Advances in Intelligent Systems and Computing, Proceedings of the 13th International Conference on Soft Computing Models in Industrial and Environmental Applications, San Sebastian, Spain, 6–8 June 2018; Springer: Cham, Switzerland, 2018; Volume 771, pp. 509–517. [Google Scholar]
- Liao, D.Y.; Wang, X.H. Applications of Blockchain Technology to Logistics Management in Integrated Casinos and Entertainment. Informatics 2018, 5, 44. [Google Scholar] [CrossRef] [Green Version]
- Hofman, W.J.; Brewster, C. The Applicability of Blockchain Technology in the Mobility and Logistics Domain. In Towards User-Centric Transport in Europe; Springer: Cham, Switzerland, 2018; pp. 185–201. [Google Scholar]
- Bai, C.; Sarkis, J. A supply chain transparency and sustainability technology appraisal model for blockchain technology. Int. J. Prod. Res. 2020, 58, 2142–2162. [Google Scholar] [CrossRef]
- Casino, F.; Kanakaris, V.; Dasaklis, T.K.; Moschuris, S.; Stachtiaris, S.; Pagoni, M.; Rachaniotis, N.P. Blockchain-based food supply chain traceability: A case study in the dairy sector. Int. J. Prod. Res. 2020, 1–13. [Google Scholar] [CrossRef]
- She, W.; Liu, Q.; Tian, Z.; Chen, J.S.; Wang, B.; Liu, W. Blockchain trust model for malicious node detection in wireless sensor networks. J. IEEE Access 2019, 7, 38947–38956. [Google Scholar] [CrossRef]
- Fu, Y.; Zhu, J. Big production enterprise supply chain endogenous risk management based on blockchain. J. IEEE Access 2019, 7, 15310–15319. [Google Scholar] [CrossRef]
- Baryannis, G.; Dani, S.; Antoniou, G. Predicting supply chain risks using machine learning: The trade-off between performance and interpretability. Future Gener. Comput. Syst. 2019, 101, 993–1004. [Google Scholar] [CrossRef]
- Stefanovic, N. Proactive supply chain performance management with predictive analytics. J. Sci. World 2014, 2014, 528917. [Google Scholar] [CrossRef] [Green Version]
- Baryannis, G.; Validi, S.; Dani, S.; Antoniou, G. Supply chain risk management and artificial intelligence: State of the art and future research directions. Int. J. Prod. Res. 2019, 57, 2179–2202. [Google Scholar] [CrossRef]
- Calatayud, A.; Mangan, J.; Christopher, M. The self-thinking supply chain. Int. J. Supply Chain Manag. 2019, 24, 22–38. [Google Scholar] [CrossRef]
- Ivanov, D.; Dolgui, A.; Sokolov, B. The impact of digital technology and Industry 4.0 on the ripple effect and supply chain risk analytics. Int. J. Prod. Res. 2019, 57, 829–846. [Google Scholar] [CrossRef]
- Mani, V.; Delgado, C.; Hazen, B.T.; Patel, P. Mitigating supply chain risk via sustainability using big data analytics: Evidence from the manufacturing supply chain. Sustainability 2017, 9, 608. [Google Scholar] [CrossRef] [Green Version]
- Bodendorf, F.; Zimmermann, R. Proactive supply-chain event management with agent technology. Int. J. Electron. Commer. 2005, 9, 58–89. [Google Scholar] [CrossRef]
- Liu, R.; Kumar, A.; Van Der Aalst, W. A formal modeling approach for supply chain event management. J. Decis. Support Syst. 2007, 43, 761–778. [Google Scholar] [CrossRef]
- Bearzotti, L.A.; Salomone, E.; Chiotti, O.J. An autonomous multi-agent approach to supply chain event management. Int. J. Prod. Econ. 2012, 135, 468–478. [Google Scholar] [CrossRef]
- Fernández, E.; Salomone, E.; Chiotti, O. A model driven development approach based on a reference model for predicting disruptive events in a supply process. J. Comput. Ind. 2012, 63, 482–499. [Google Scholar] [CrossRef]
- Fernández, E.; Toledo, C.M.; Galli, M.R.; Salomone, E.; Chiotti, O. Agent-based monitoring service for management of disruptive events in supply chains. J. Comput. Ind. 2015, 70, 89–101. [Google Scholar] [CrossRef]
- Brintrup, A.; Pak, J.; Ratiney, D.; Pearce, T.; Wichmann, P.; Woodall, P.; McFarlane, D. Supply chain data analytics for predicting supplier disruptions: A case study in complex asset manufacturing. Int. J. Prod. Res. 2020, 58, 3330–3341. [Google Scholar] [CrossRef]
- Lee, C.H. Mining Spatio-temporal Information on Microblogging Streams Using a Density-based Online Clustering Method. Expert Syst. Appl. 2012, 39, 9623–9641. [Google Scholar] [CrossRef]
- Lee, C.H.; Chien, T.F. Leveraging Microblogging Big Data with a Modified Density-based Clustering Approach for Event Awareness and Topic Ranking. J. Inf. Sci. 2013, 39, 520–540. [Google Scholar] [CrossRef]
- Xu, X.; Pautasso, C.; Zhu, L.; Gramoli, V.; Ponomarev, A.; Tran, A.B.; Chen, S. The blockchain as a software connector. In Proceedings of the 2016 13th Working IEEE/IFIP Conference on Software Architecture (WICSA2016), Venice, Italy, 5–8 April 2016; pp. 182–191. [Google Scholar]
- Luo, J. Forecasting COVID-19 pandemic: Unknown unknowns and predictive monitoring. J. Technol. Forecast. Soc. Chang. 2021, 166, 120602–120605. [Google Scholar] [CrossRef]
- Park, Y.; Hong, P.; Roh, J.J. Supply chain lessons from the catastrophic natural disaster in Japan. J. Bus. Horiz. 2013, 56, 75–85. [Google Scholar] [CrossRef]









| Network | Network ID | Consensus | Mining | Block Time | Status |
|---|---|---|---|---|---|
| Ethereum Main | 1 | PoW | Yes | 15 s | Available |
| Morden | 2 | PoW | Yes | 15 s | Stop |
| Ropsten | 3 | PoW | Yes | 15 s | Available |
| Rinkeby | 4 | PoA | No | 15 s | Available |
| Kovan | 42 | PoA | No | 4 s | Available |
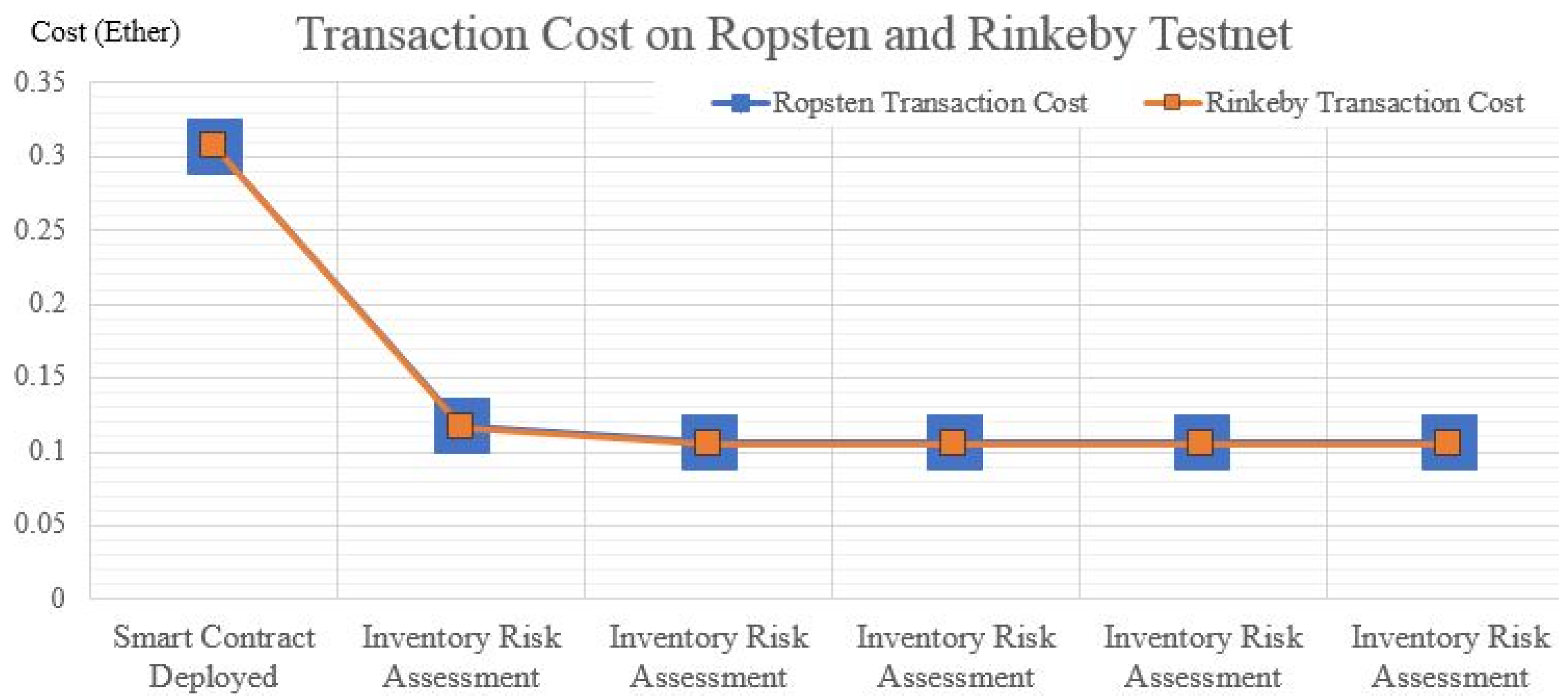
| Testnet | Action | Oraclize Callback (Time) | Transaction Gas | Gas Price (Ether) | Oraclize Fee (Ether) | Transation Cost (Ether) | USD ($) |
|---|---|---|---|---|---|---|---|
| RINKEBY | Smart Contract Deployed | - | 2,872,997 | 0.000000107 | 0 | 0.307410679 | 121.5563307 |
| Inventory Risk Assessment | 45 s | 526,838 | 0.06 | 0.116371666 | 46.01568417 | ||
| 45 s | 422,840 | 0.10524388 | 41.61553503 | ||||
| 45 s | 422,840 | 0.10524388 | 41.61553503 | ||||
| 45 s | 422,840 | 0.10524388 | 41.61553503 | ||||
| 45 s | 422,840 | 0.10524388 | 41.61553503 | ||||
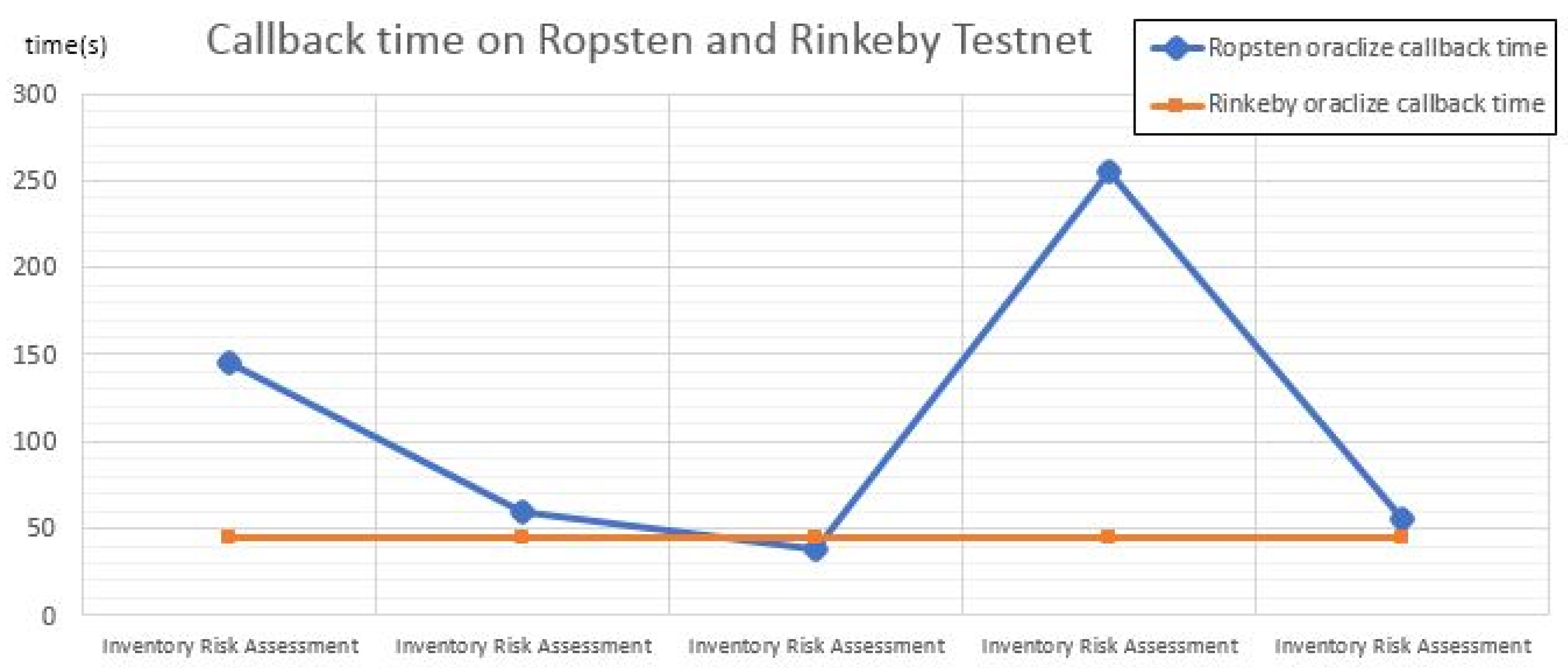
| ROPSTEN | Smart Contract Deployed | - | 2,872,997 | 0 | 0.307410679 | 121.5563307 | |
| Inventory Risk Assessment | 145 s | 536,572 | 0.06 | 0.117413204 | 46.42752913 | ||
| 59 s | 436,172 | 0.106670404 | 42.17981115 | ||||
| 38 s | 436,172 | 0.106670404 | 42.17981115 | ||||
| 255 s | 436,172 | 0.106670404 | 42.17981115 | ||||
| 55 s | 436,172 | 0.106670404 | 42.17981115 |
| Testnet | Action | Oraclize Callback (Time) | Transaction Gas | Gas Prince (Ether) | Oraclize Fee (Ether) | Transaction Cost (Ether) | USD ($) |
|---|---|---|---|---|---|---|---|
| Private Chain | Smart Contract Deployed | - | 3,505,517 | 0.000000107 | 0 | 0.375090319 | 148.3182139 |
| Inventory Risk Assessment | 23 s | 473,074 | 0.06 | 0.110618918 | 43.74093256 | ||
| 21 s | 414,180 | 0.10431726 | 41.24913095 | ||||
| 20 s | 414,180 | 0.10431726 | 41.24913095 | ||||
| 20 s | 414,180 | 0.10431726 | 41.24913095 | ||||
| 19 s | 414,180 | 0.10431726 | 41.24913095 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, C.-H.; Yang, H.-C.; Wei, Y.-C.; Hsu, W.-K. Enabling Blockchain Based SCM Systems with a Real Time Event Monitoring Function for Preemptive Risk Management. Appl. Sci. 2021, 11, 4811. https://doi.org/10.3390/app11114811
Lee C-H, Yang H-C, Wei Y-C, Hsu W-K. Enabling Blockchain Based SCM Systems with a Real Time Event Monitoring Function for Preemptive Risk Management. Applied Sciences. 2021; 11(11):4811. https://doi.org/10.3390/app11114811
Chicago/Turabian StyleLee, Chung-Hong, Hsin-Chang Yang, Yu-Chen Wei, and Wen-Kai Hsu. 2021. "Enabling Blockchain Based SCM Systems with a Real Time Event Monitoring Function for Preemptive Risk Management" Applied Sciences 11, no. 11: 4811. https://doi.org/10.3390/app11114811
APA StyleLee, C.-H., Yang, H.-C., Wei, Y.-C., & Hsu, W.-K. (2021). Enabling Blockchain Based SCM Systems with a Real Time Event Monitoring Function for Preemptive Risk Management. Applied Sciences, 11(11), 4811. https://doi.org/10.3390/app11114811






