Efficient Implementation of PRESENT and GIFT on Quantum Computers
Abstract
1. Introduction
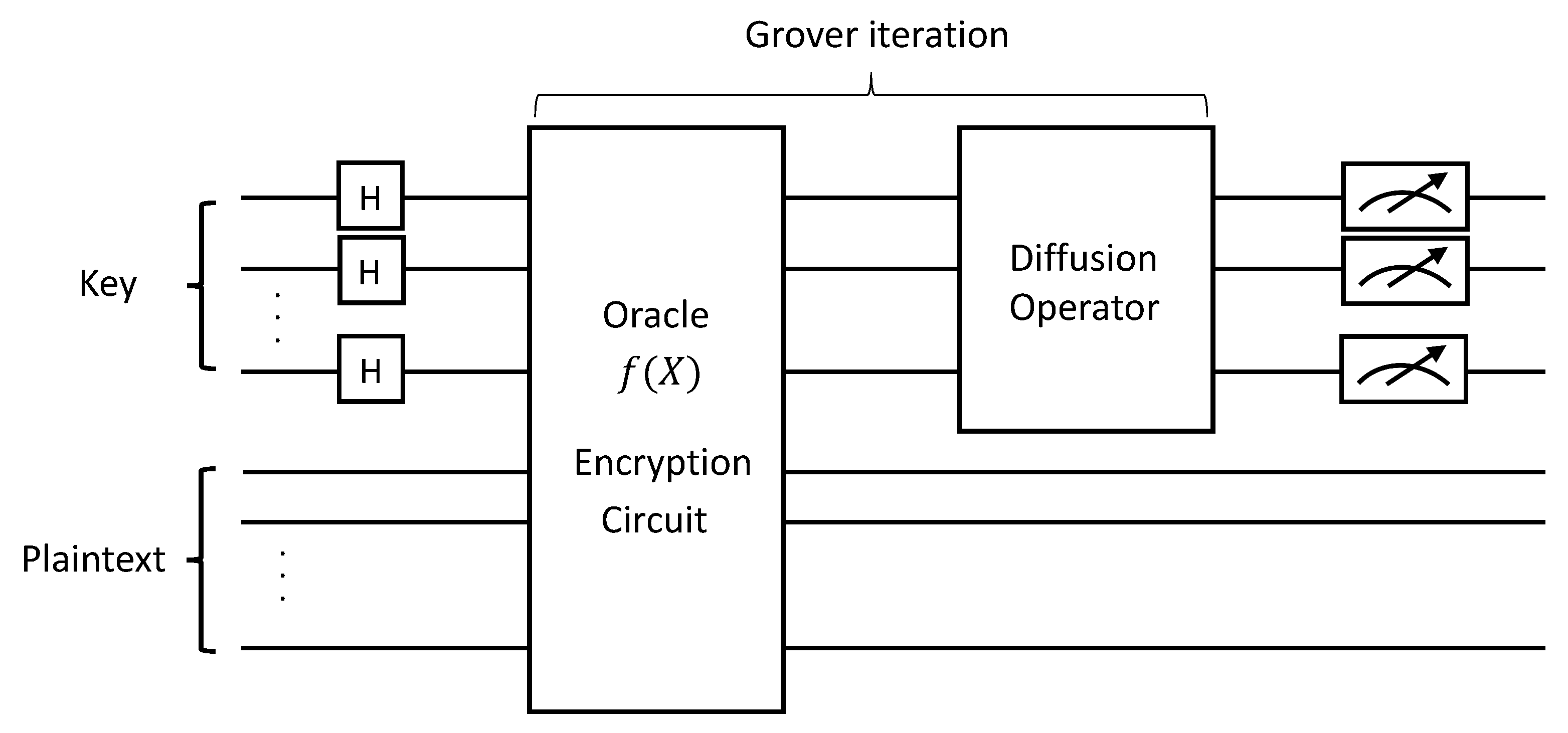
Contribution
- First design of quantum gates for PRESENT and GIFT symmetric key cryptography. As far as we know, we firstly implemented PRESENT and GIFT block ciphers as quantum circuits. We present a method of implementing PRESENT and GIFT block ciphers as quantum circuits for application to the oracle of the Grover search algorithm.
- Quantum circuits with optimized qubits for PRESENT and GIFT block ciphers. One of the most important factors when evaluating quantum circuits is optimizing the number of qubits. When designing quantum circuits, new qubits are allocated to temporal storage or new values. However, we use an on-the-fly approach to recycle the initially allocated qubits until the encryption is finished. By using efficient Sbox quantum implementation, we did not allocate qubits except for the initial key and plaintext.
- Quantum gates and circuit depth analysis for PRESENT and GIFT block ciphers. Proposed PRESENT and GIFT implementations are evaluated using the IBM ProjectQ framework, a quantum computer emulator (https://github.com/ProjectQ-Framework/ProjectQ, accessed on 10 May 2021) [14]. IBM ProjectQ uses a variety of quantum compilers that allow us to simulate quantum computers or draw quantum circuits. Among them, the resource counter compiler, which is a quantum resource estimator, measures quantum resources by analyzing qubits, quantum gates, and circuit depth. Compared with quantum implementation results of other block ciphers, we implemented low-cost PRESENT and GIFT quantum circuits.
2. Related Work
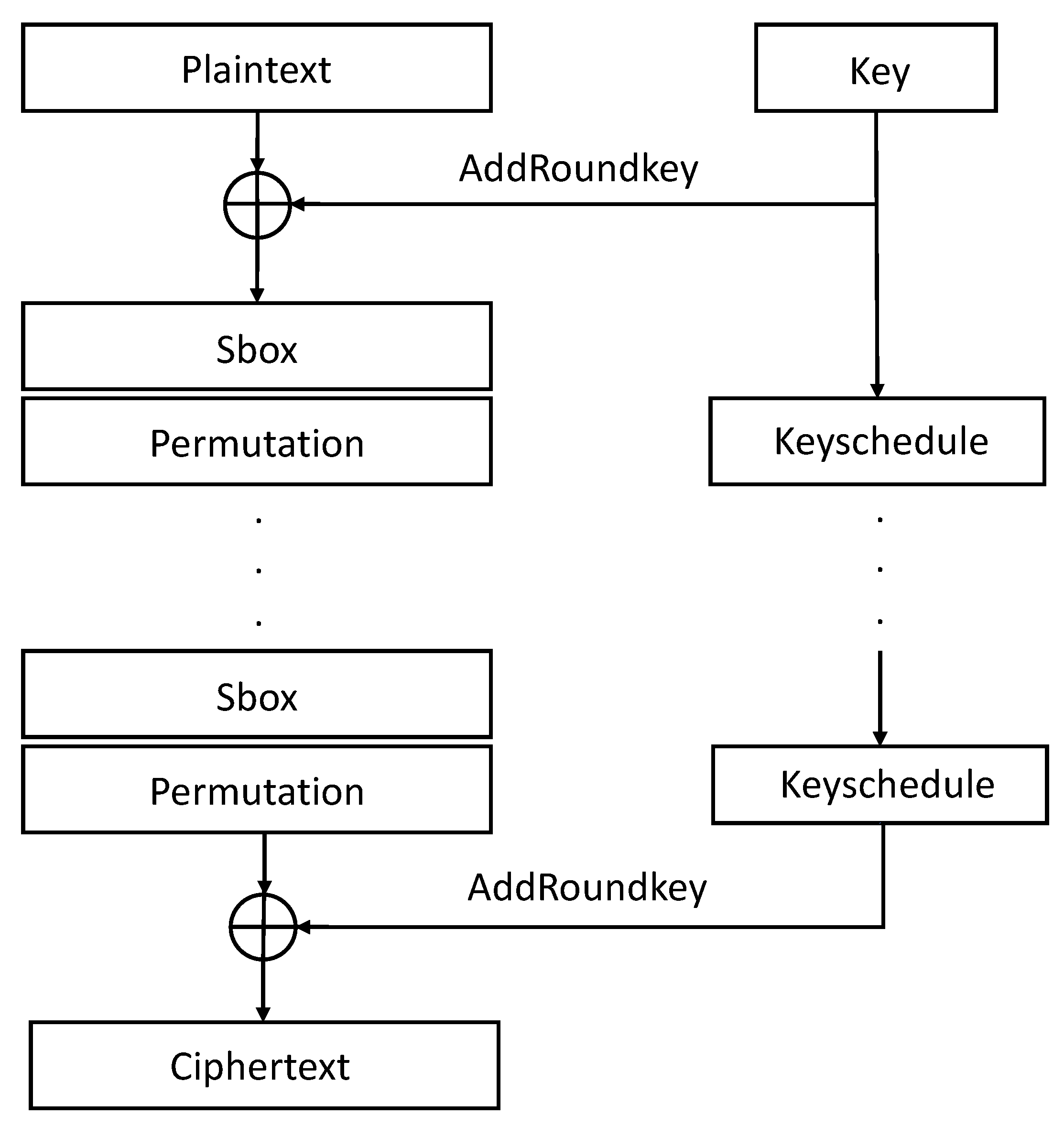
2.1. PRESENT Block Cipher
2.1.1. AddRoundkey of PRESENT Block Cipher
2.1.2. Sbox of PRESENT Block Cipher
2.1.3. Permutation of PRESENT Block Cipher
2.1.4. Keyschedule of PRESENT Block Cipher
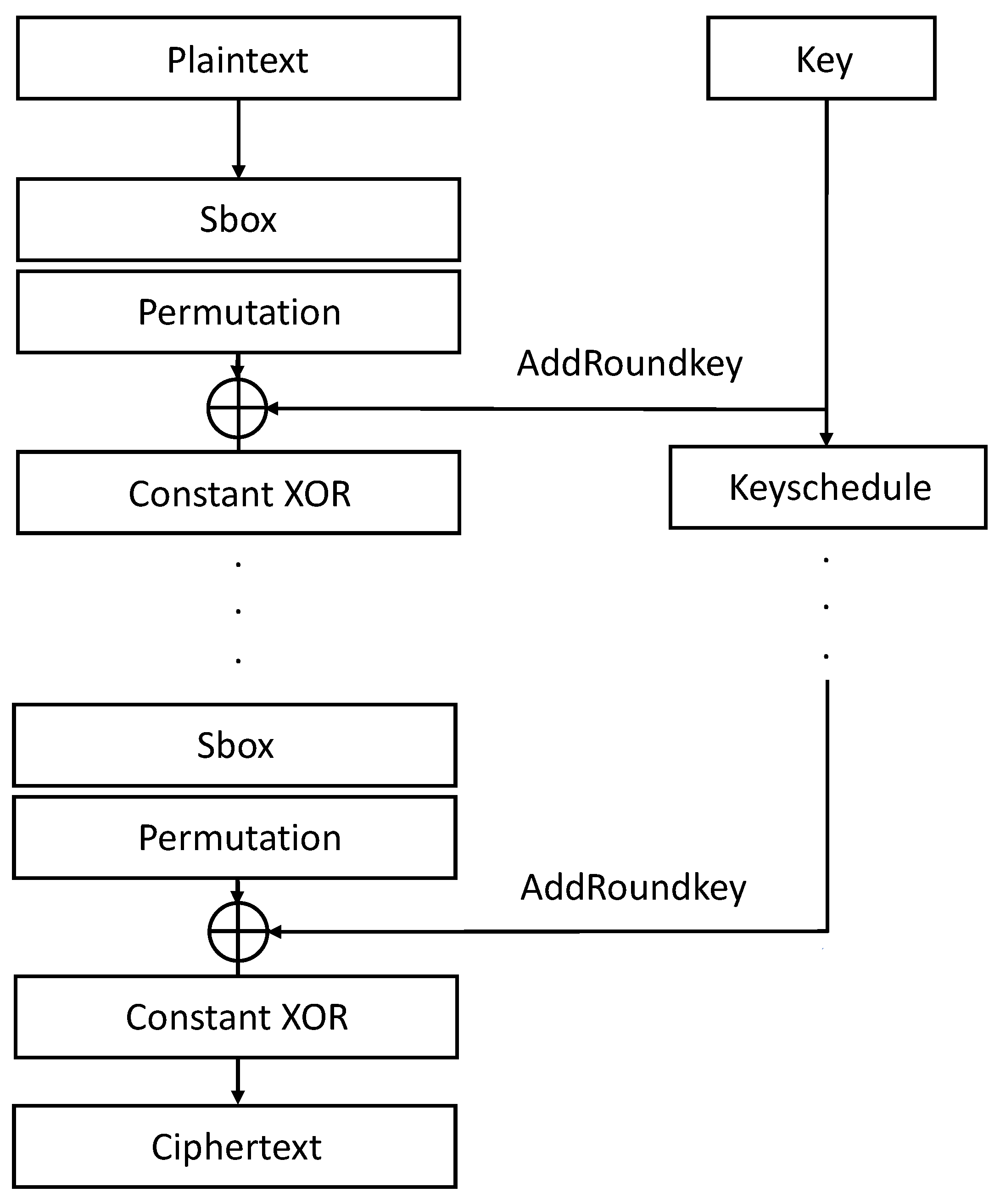
2.2. GIFT Block Cipher
2.2.1. Sbox of GIFT Block Cipher
2.2.2. Permutation of GIFT Block Cipher
2.2.3. AddRoundkey of GIFT Block Cipher
2.2.4. Constant XOR of GIFT Block Cipher
2.2.5. Keyschedule of GIFT Block Cipher
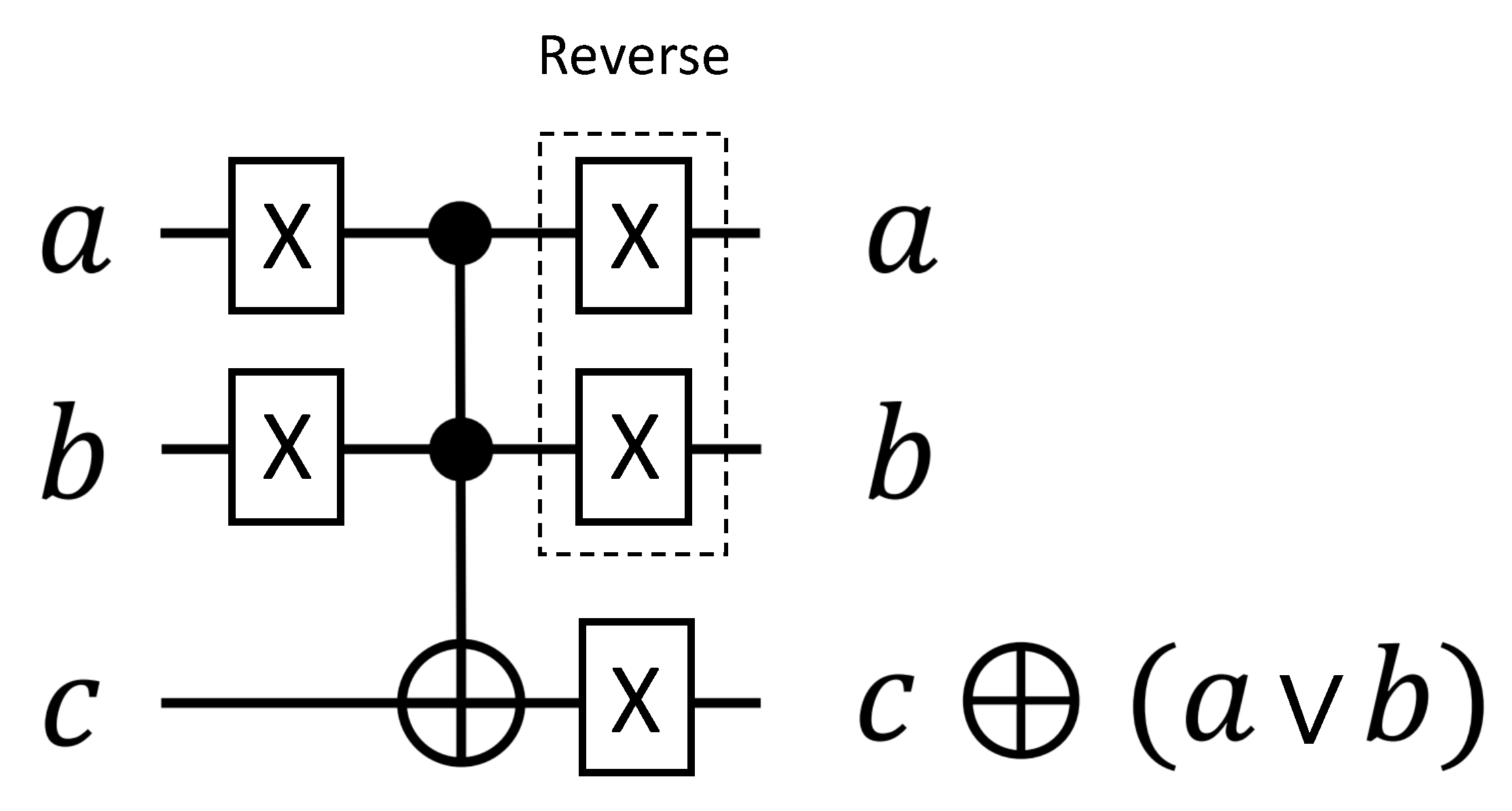
2.3. Quantum Gates and Algorithm
2.3.1. Quantum Gates
2.3.2. Grover’s Search Algorithm
2.4. LIGHTER-R
3. Proposed Method
3.1. Quantum Circuit for PRESENT Block Cipher
3.1.1. AddRoundkey of PRESENT Block Cipher
| Algorithm 1 Quantum circuit for AddRoundKey of PRESENT block cipher |
| Input: 64-qubit block 64-qubit round key ) Output: 64-qubit block after AddRoundKey 1: for to 63 do 2: CNOT 3: end for 4: return ) |
3.1.2. Sbox of PRESENT Block Cipher
| Algorithm 2 Quantum circuit using LIGHTER-R for Sbox of PRESENT block cipher |
| Input: 4-qubit input (before entering Sbox). Output: 4-qubit output (after performing Sbox). 1: CNOT () 2: Toffoli () 3: Toffoli () 4: Toffoli () 5: CNOT () 6: X () 7: CNOT () 8: CNOT () 9: CNOT () 10: X () 11: Toffoli () 12: return |
3.1.3. Permutation of PRESENT Block Cipher
3.1.4. Keyschedule of PRESENT Block Cipher
| Algorithm 3 Quantum circuits for Keyschedule of PRESENT-80 |
| Input: 80-qubit key . Output: 64-qubit round key . 1: using Swap gates 2: Sbox () 3: X () according to round i 4: return |
3.2. Quantum Circuit for GIFT Block Cipher
3.2.1. Sbox of GIFT Block Cipher
| Algorithm 4 Software-oriented implementation of GIFT Sbox |
| Input: 4-bit input (before entering Sbox). Output: 4-bit output (after performing Sbox). 1: XOR ( AND ) 2: t XOR ( AND ) 3: XOR (t OR ) 4: XOR 5: XOR 6: NOT 7: XOR (t AND ) 8: t 9: return |
| Algorithm 5 Hardware-oriented implementation of GIFT Sbox |
| Input: 4-bit input (before entering Sbox). Output: 4-bit output (after performing Sbox). 1: XNOR ( NAND ) 2: XNOR ( NAND ) 3: XNOR ( NOR ) 4: XNOR 5: XNOR 6: XNOR ( NAND ) 7: return |
| Algorithm 6 Quantum circuits for Sbox of GIFT block cipher |
| Input: 4-qubit input (before entering Sbox). Output: 4-qubit output (after performing Sbox). 1: Toffoli () 2: Toffoli () 3: X () 4: X () 5: Toffoli () 6: X () 7: X () (reverse) 8: X () (reverse) 9: CNOT () 10: X () 11: CNOT () 12: X () 13: Toffoli ( 14: return |
3.2.2. Permutaiton of GIFT Block Cipher
3.2.3. AddRoundkey of GIFT Block Cipher
| Algorithm 7 Quantum circuit for AddRoundkey of GIFT-64/128 block cipher |
| Input: 64-qubit block 32-qubit round key . Output: 64-qubit block after AddRoundKey. 1: for to 15 do 2: CNOT 3: CNOT 4: end for 5: return |
| Algorithm 8 Quantum circuits for AddRoundkey of GIFT-128/128 block cipher |
| Input: 128-qubit block 64-qubit round key . Output: 128-qubit block after AddRoundKey. 1: for to 31 do 2: CNOT 3: CNOT 4: end for 5: return |
3.2.4. Constant XOR of GIFT Block Cipher
| Algorithm 9 Quantum circuits for constant XOR of GIFT-n/128 block cipher |
| Input: of n-bit block B. Output: of n-bit block B after Constant XOR. 1: X () according to round constant C () 2: X () 3: return |
3.2.5. Keyschedule of GIFT Block Cipher
4. Evaluation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Biryukov, A.; Perrin, L.P. State of the Art in Lightweight Symmetric Cryptography. 2017. Available online: https://eprint.iacr.org/2017/511 (accessed on 10 May 2021).
- Bogdanov, A.; Knudsen, L.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.; Seurin, Y.; Vikkelsoe, C. PRESENT: An ultra-lightweight block cipher. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4727, pp. 450–466. [Google Scholar] [CrossRef]
- Banik, S.; Peyrin, T.; Sasaki, Y.; Sim, S.M.; Todo, Y. GIFT: A Small Present. In Proceedings of the International Conference on Cryptographic Hardware and Embedded Systems, Taipei, Taiwan, 25–28 September 2017; pp. 321–345. [Google Scholar] [CrossRef]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Grassl, M.; Langenberg, B.; Roetteler, M.; Steinwandt, R. Applying Grover’s algorithm to AES: Quantum resource estimates. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2016; pp. 29–43. [Google Scholar]
- Langenberg, B.; Pham, H.; Steinwandt, R. Reducing the Cost of Implementing AES as a Quantum Circuit; Technical Report; Cryptology ePrint Archive, Report 2019/854. 2019. Available online: https://eprint.iacr.org/2019/854 (accessed on 10 May 2021).
- Jaques, S.; Naehrig, M.; Roetteler, M.; Virdia, F. Implementing Grover oracles for quantum key search on AES and LowMC. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 10–14 May 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 280–310. [Google Scholar]
- Anand, R.; Maitra, A.; Mukhopadhyay, S. Grover on SIMON. Quantum Inf. Process. 2020, 19, 1–17. [Google Scholar] [CrossRef]
- Jang, K.; Choi, S.; Kwon, H.; Seo, H. Grover on SPECK: Quantum Resource Estimates. Cryptology ePrint Archive, Report 2020/640. 2020. Available online: https://eprint.iacr.org/2020/640 (accessed on 10 May 2021).
- Schlieper, L. In-place implementation of Quantum-Gimli. arXiv 2020, arXiv:2007.06319. [Google Scholar]
- Jang, K.; Choi, S.; Kwon, H.; Kim, H.; Park, J.; Seo, H. Grover on Korean Block Ciphers. Appl. Sci. 2020, 10, 6407. [Google Scholar] [CrossRef]
- Dasu, V.A.; Baksi, A.; Sarkar, S.; Chattopadhyay, A. LIGHTER-R: Optimized Reversible Circuit Implementation For SBoxes. In Proceedings of the 2019 32nd IEEE International System-on-Chip Conference (SOCC), Singapore, 3–6 September 2019; pp. 260–265. [Google Scholar] [CrossRef]
- Steiger, D.S.; Häner, T.; Troyer, M. ProjectQ: An open source software framework for quantum computing. Quantum 2018, 2, 49. [Google Scholar] [CrossRef]
- Yang, G.; Zhu, B.; Suder, V.; Aagaard, M.; Gong, G. The SIMECK Family of Lightweight Block Ciphers. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2015; pp. 307–329. [Google Scholar] [CrossRef]
- Jean, J.; Peyrin, T.; Sim, S.M.; Tourteaux, J. Optimizing Implementations of Lightweight Building Blocks. IACR Trans. Symmetric Cryptol. 2017, 2017, 130–168. [Google Scholar] [CrossRef]
- Bhattacharjee, D.; Chattopadhyay, A. Depth-Optimal Quantum Circuit Placement for Arbitrary Topologies. arXiv 2017, arXiv:1703.08540. [Google Scholar]
- Amento-Adelmann, B.; Grassl, M.; Langenberg, B.; Liu, Y.K.; Schoute, E.; Steinwandt, R. Quantum cryptanalysis of block ciphers: A case study. In Proceedings of the Poster at Quantum Information Processing QIP, Delft, The Netherlands, 15–19 January 2018. [Google Scholar]
- Langenberg, B.; Pham, H.; Steinwandt, R. Reducing the Cost of Implementing the Advanced Encryption Standard as a Quantum Circuit. IEEE Trans. Quantum Eng. 2020, 1, 1–12. [Google Scholar] [CrossRef]
- Dinu, D.; Biryukov, A.; Großschädl, J.; Khovratovich, D.; Le Corre, Y.; Perrin, L. FELICS—Fair evaluation of lightweight cryptographic systems. In Proceedings of the NIST Workshop on Lightweight Cryptography, Gaithersburg, MD, USA, 20–21 July 2015; Volume 128. [Google Scholar]
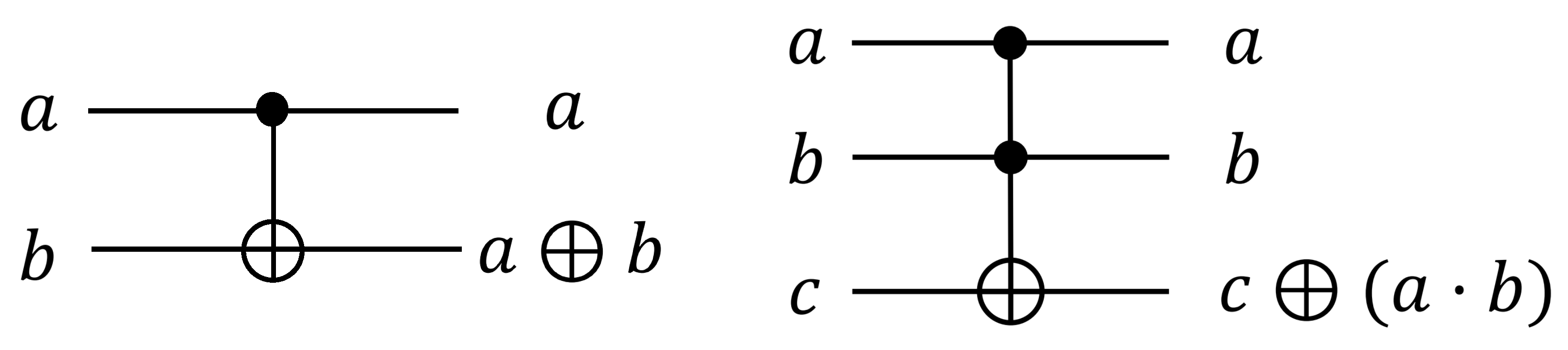
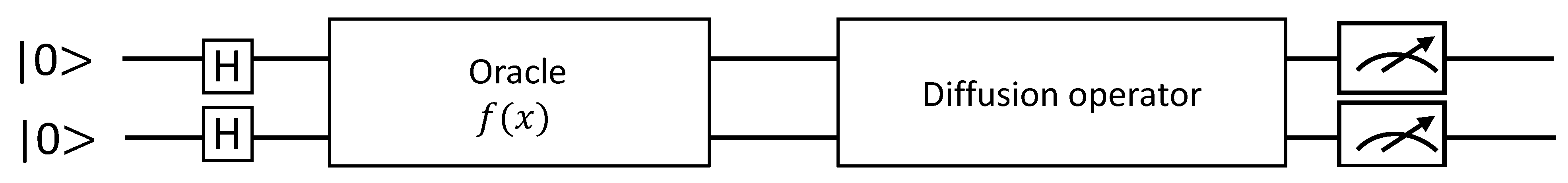
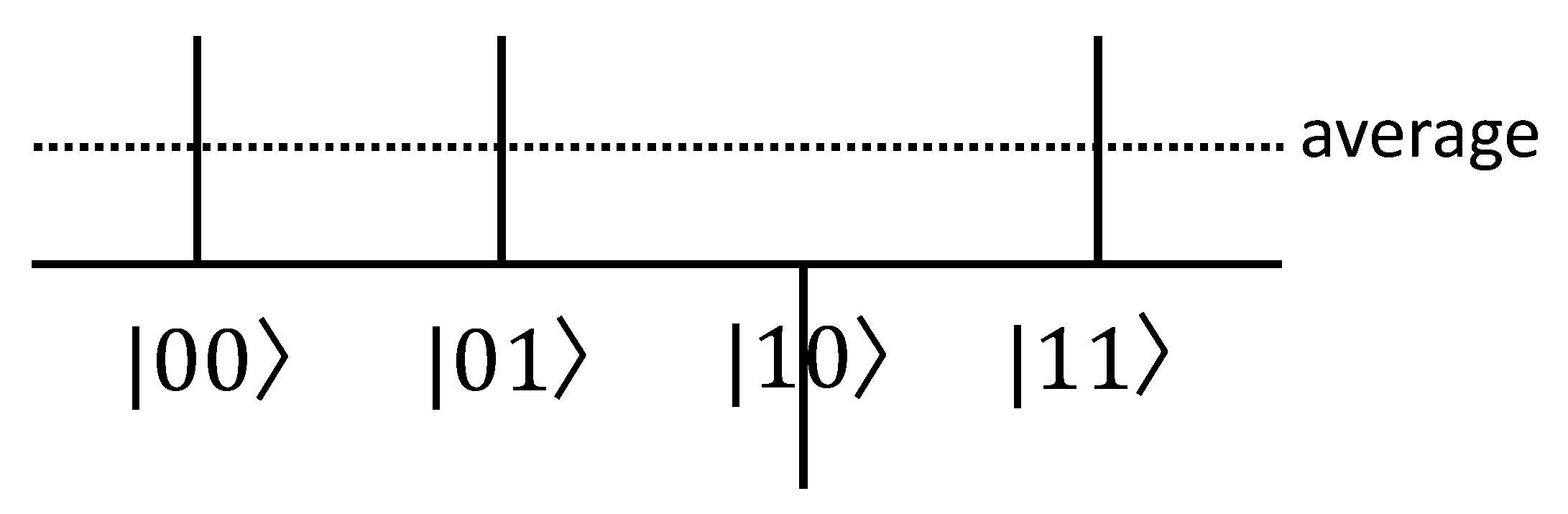
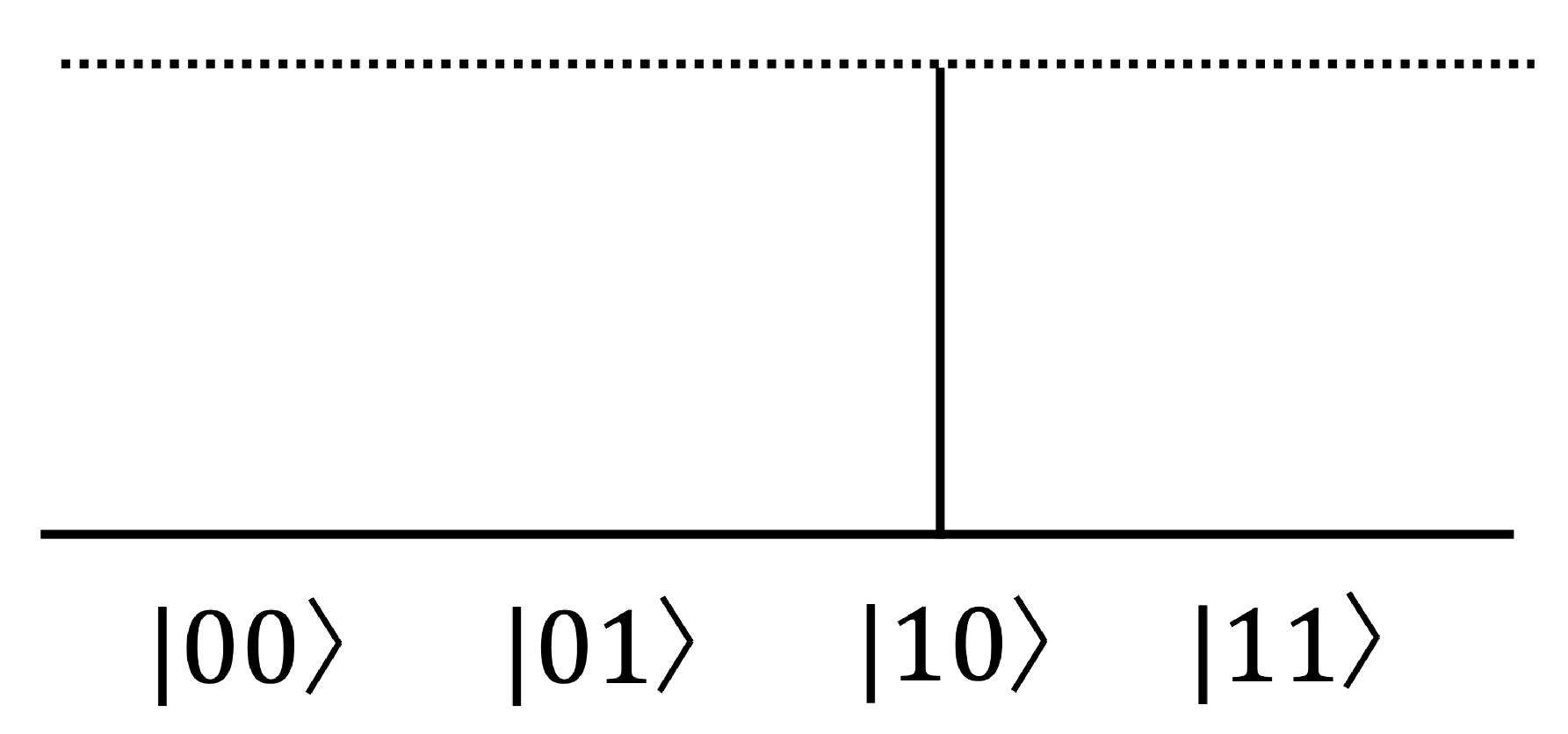
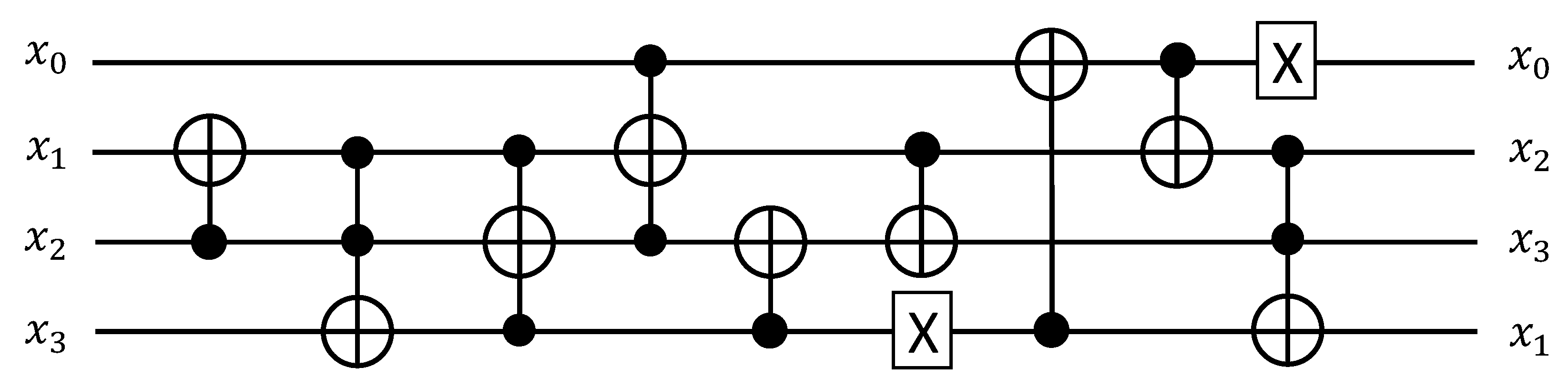
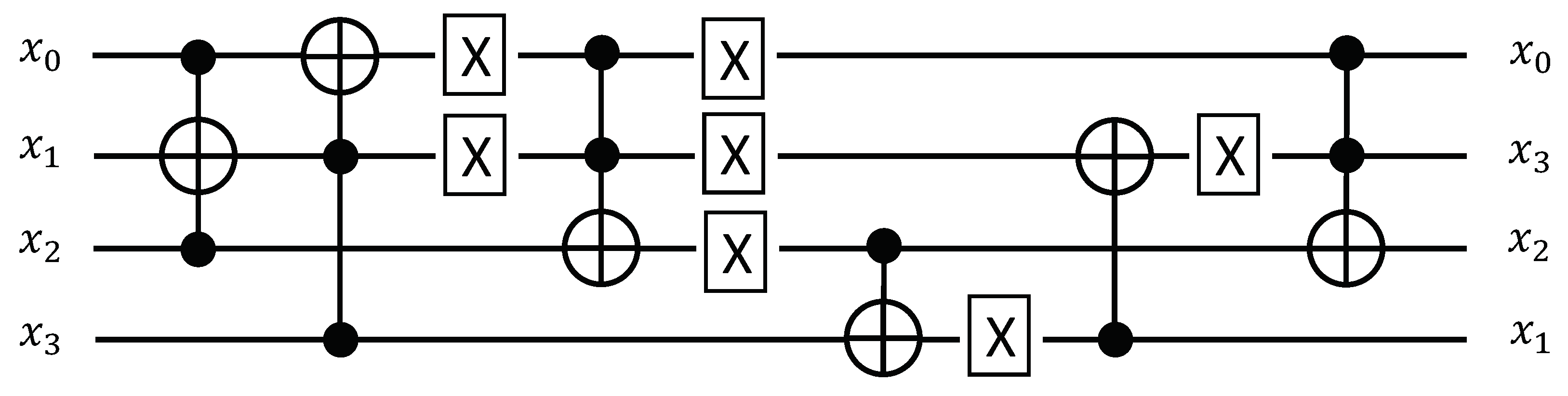
| x | 0 1 2 3 4 5 6 7 8 9 a b c d e f |
| Sbox(x) | c 5 6 b 9 0 a d 3 e f 8 4 7 1 2 |
| i | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 0 | 16 | 32 | 48 | 1 | 17 | 33 | 49 | 2 | 18 | 34 | 50 | 3 | 19 | 35 | 51 | |
| i | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
| 4 | 20 | 36 | 52 | 5 | 21 | 37 | 53 | 6 | 22 | 38 | 54 | 7 | 23 | 39 | 55 | |
| i | 32 | 33 | 34 | 35 | 36 | 37 | 38 | 39 | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 |
| 8 | 24 | 40 | 56 | 9 | 25 | 41 | 57 | 10 | 26 | 42 | 58 | 11 | 27 | 43 | 59 | |
| i | 48 | 49 | 50 | 51 | 52 | 53 | 54 | 55 | 56 | 57 | 58 | 59 | 60 | 61 | 62 | 63 |
| 12 | 28 | 44 | 60 | 13 | 29 | 45 | 61 | 14 | 30 | 46 | 62 | 15 | 31 | 47 | 63 |
| x | 0 1 2 3 4 5 6 7 8 9 a b c d e f |
| Sbox(x) | 1 a 4 c 6 f 3 9 2 d b 7 5 0 8 e |
| i | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 0 | 17 | 34 | 51 | 48 | 1 | 18 | 35 | 23 | 49 | 2 | 19 | 16 | 33 | 50 | 3 | |
| i | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
| 4 | 21 | 38 | 55 | 52 | 5 | 22 | 39 | 36 | 53 | 6 | 23 | 20 | 37 | 54 | 7 | |
| i | 32 | 33 | 34 | 35 | 36 | 37 | 38 | 39 | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 |
| 8 | 25 | 42 | 59 | 56 | 9 | 26 | 43 | 40 | 57 | 10 | 27 | 24 | 41 | 58 | 11 | |
| i | 48 | 49 | 50 | 51 | 52 | 53 | 54 | 55 | 56 | 57 | 58 | 59 | 60 | 61 | 62 | 63 |
| 12 | 29 | 46 | 63 | 60 | 13 | 30 | 47 | 44 | 61 | 14 | 31 | 28 | 45 | 62 | 15 |
| Rounds | Constants C | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 to 16 | 01 | 03 | 07 | 0F | 1F | 3E | 3D | 3B | 37 | 2F | 1E | 3C | 39 | 33 | 27 | 0E |
| 17 to 32 | 1D | 3A | 35 | 2B | 16 | 2C | 18 | 30 | 21 | 02 | 05 | 0B | 17 | 2E | 1C | 38 |
| 33 to 48 | 31 | 23 | 06 | 0D | 1B | 36 | 2D | 1A | 34 | 29 | 12 | 24 | 08 | 11 | 22 | 04 |
| Quantum Circuit | Qubits | Toffoli Gates | CNOT Gates | X Gates | Circuit Depth |
|---|---|---|---|---|---|
| PRESENT-64/80 (This work) | 144 | 2108 | 4683 | 1118 | 311 |
| PRESENT-64/128 (This work) | 192 | 2232 | 4838 | 1164 | 311 |
| GIFT-64/128 (This work) | 192 | 1792 | 1792 | 3261 | 308 |
| GIFT-128/128 (This work) | 256 | 6144 | 6144 | 10,953 | 528 |
| SIMON-64/128 [9] | 192 | 1408 | 7396 | 1216 | 2643 |
| SIMON-128/128 [9] | 256 | 4352 | 17,152 | 4224 | 8427 |
| SPECK-64/128 [12] | 193 | 3286 | 9238 | 57 | - |
| SPECK-128/128 [12] | 257 | 7942 | 22,086 | 75 | - |
| CHAM-64/128 [12] | 196 | 2400 | 12,285 | 240 | - |
| CHAM-128/128 [12] | 268 | 4960 | 26,885 | 240 | - |
| Symmetric Key Cryptography | Qubits | Toffoli Gates | CNOT Gates | X Gates |
|---|---|---|---|---|
| PRESENT-64/80 | 289 | 8432 | 18,892 | 4472 |
| PRESENT-64/128 | 385 | 8928 | 19,608 | 4656 |
| GIFT-64/128 | 385 | 7168 | 7424 | 13,044 |
| GIFT-128/128 | 257 | 12,288 | 12,288 | 21,906 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jang, K.; Song, G.; Kim, H.; Kwon, H.; Kim, H.; Seo, H. Efficient Implementation of PRESENT and GIFT on Quantum Computers. Appl. Sci. 2021, 11, 4776. https://doi.org/10.3390/app11114776
Jang K, Song G, Kim H, Kwon H, Kim H, Seo H. Efficient Implementation of PRESENT and GIFT on Quantum Computers. Applied Sciences. 2021; 11(11):4776. https://doi.org/10.3390/app11114776
Chicago/Turabian StyleJang, Kyungbae, Gyeongju Song, Hyunjun Kim, Hyeokdong Kwon, Hyunji Kim, and Hwajeong Seo. 2021. "Efficient Implementation of PRESENT and GIFT on Quantum Computers" Applied Sciences 11, no. 11: 4776. https://doi.org/10.3390/app11114776
APA StyleJang, K., Song, G., Kim, H., Kwon, H., Kim, H., & Seo, H. (2021). Efficient Implementation of PRESENT and GIFT on Quantum Computers. Applied Sciences, 11(11), 4776. https://doi.org/10.3390/app11114776






