A Location Privacy Preservation Method Based on Dummy Locations in Internet of Vehicles
Abstract
Featured Application
Abstract
1. Introduction
- We investigate the problem of vehicle location privacy preservation in IoV and propose a vehicle location privacy-preservation method based on dummy locations.
- We define the concept of effective distance to represent the characteristics of vehicle location distribution. Moreover, we improve the dummy location selection algorithm by using anonymous entropy and effective distance.
- We analyze the performance of the proposed method in terms of security, computation overhead, and communication overhead, and conduct extensive simulations to evaluate the proposed method.
2. Related Work
3. Preliminaries and Problem Formulation
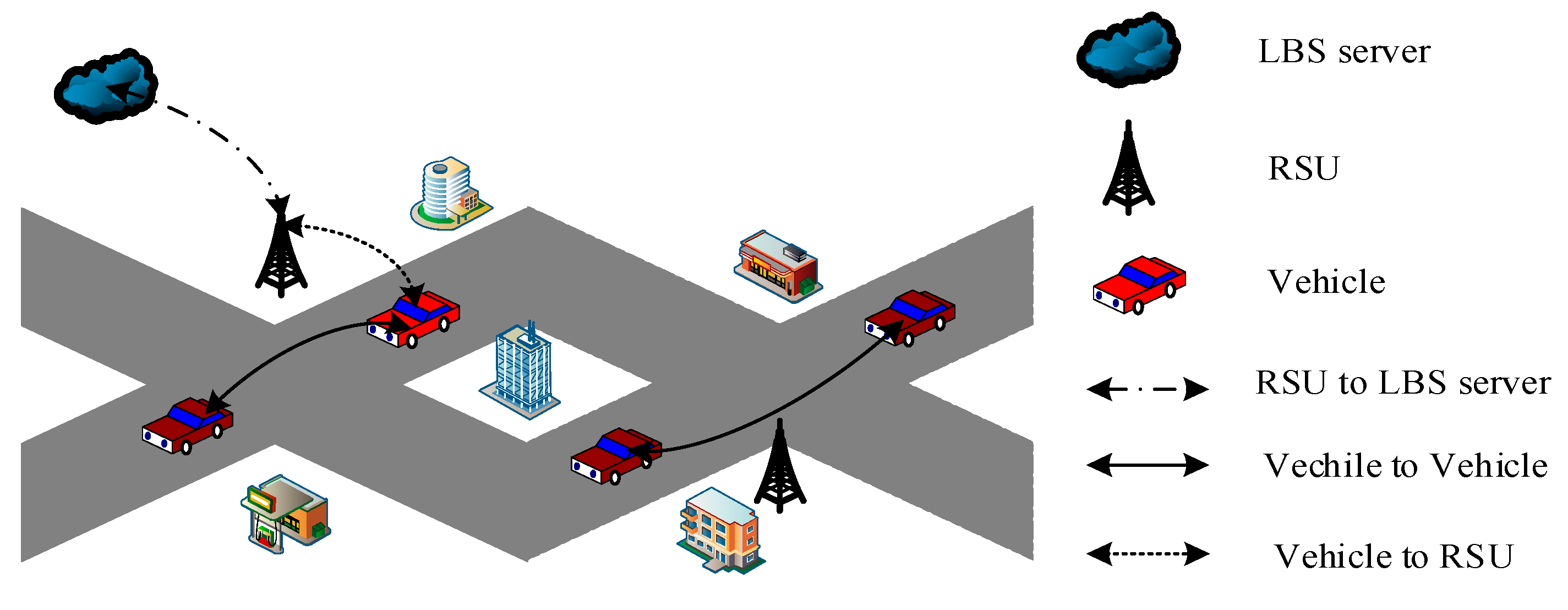
3.1. System Model
3.2. LBS Query
3.3. Service Semantics
3.4. Anonymous Entropy
3.5. Adversary Model
3.6. Problem Formulation
4. Algorithm Design
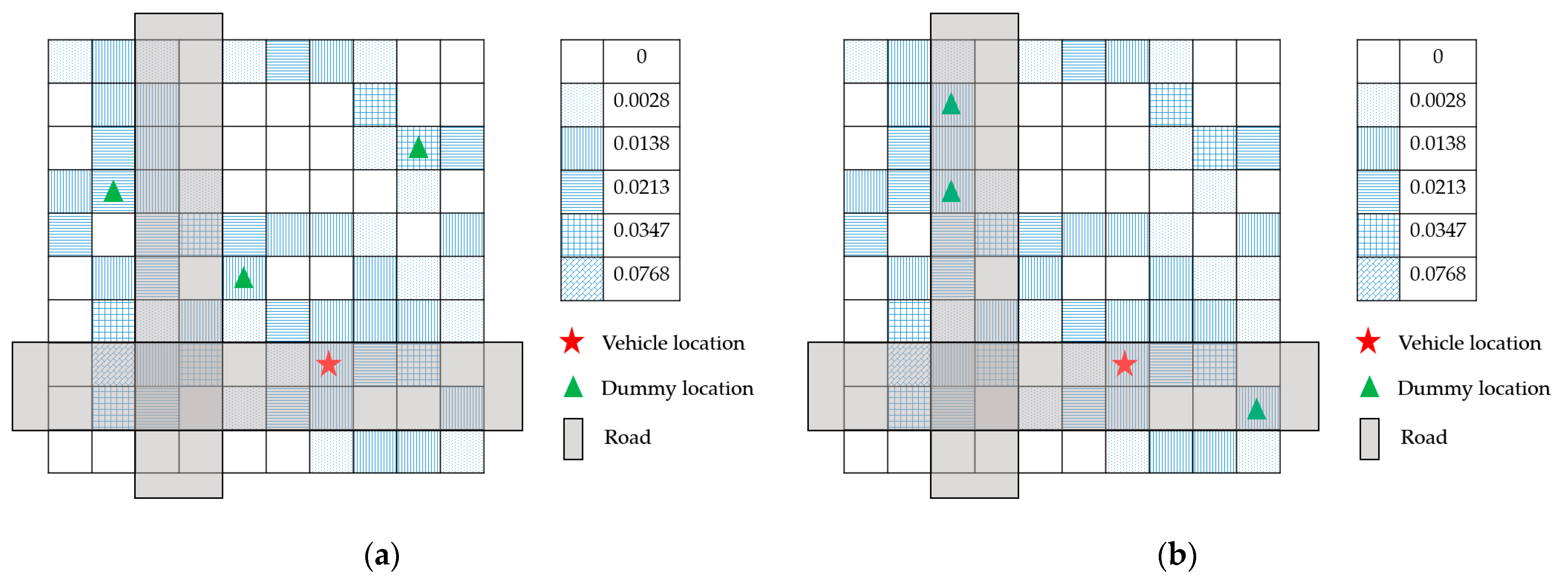
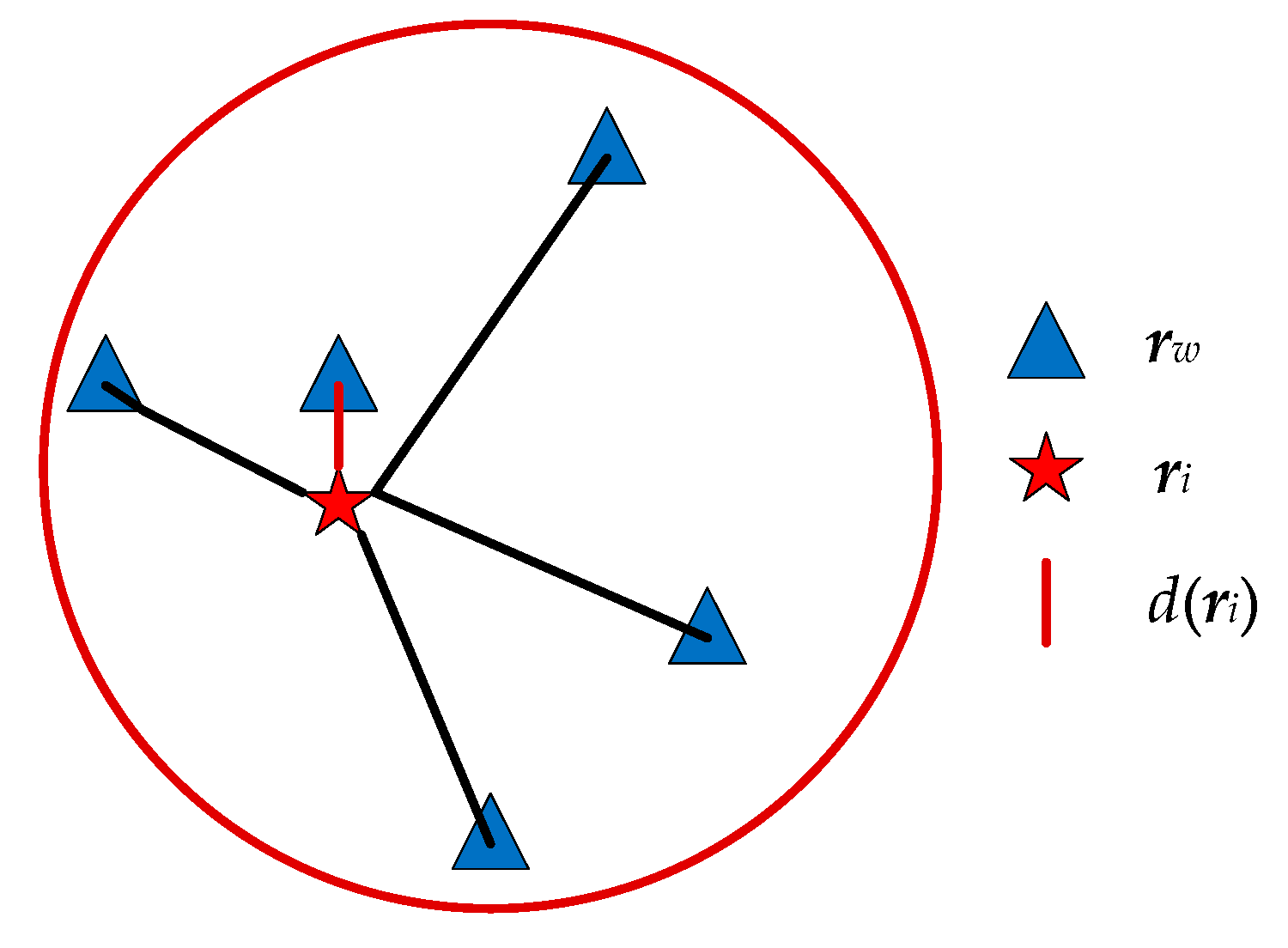
4.1. Effective Distance
4.2. Parameter Settings
4.3. Dummy Location Selection Algorithm under Road Restriction
4.4. A Location Privacy-Preservation Method Based on Dummy Locations under Road Restriction
- (1)
- Based on the historical data of service requests, the LBS server counts the number of service requests initiated by vehicle users in each cell, and the service request probability of celli,j, i = 1, 2, …, I, j = 1, 2, …, J, , where fi,j is the number of service requests initiated by vehicle users in celli,j, and F is the number of service requests in the area. The service semantics of service u is , where f(i,j),u is the number of requests of service u initiated by vehicle users in celli,j, u = 1, 2, …, U.
- (2)
- The LBS server constructs and distributes the information matrix Q(r, q, e) within the RSU’s jurisdiction to each RSU.
- (3)
- RSU broadcasts Q(r, q, e) and R to users in its covered area.
- (4)
- According to the privacy preservation level V, the vehicle user calculates its privacy parameter k by (5).
- (5)
- The vehicle user generates k − 1 dummy locations using dummy location selection algorithm under road restriction. The details are as follows:
- (5-a)
- Let k’ = 2k. Within the locations in R, other k′ − 1 locations apart from the vehicle user’s location are selected as dummy locations by solving the problem formulated in (7). Hence, a candidate set ’ is constructed with the vehicle user’s location and k′ − 1 selected dummy locations.
- (5-b)
- Within set , other k − 1 locations apart from the vehicle user’s location are selected as dummy locations by solving the problem formulated in (8). Hence, set is constructed with the vehicle user’s location and k − 1 selected dummy locations.
- (6)
- The vehicle user generates service query Lq’ including locations in , their corresponding service contents, and the privacy preservation level, and then, Lq’ is sent to the LBS server via RSU.
- (7)
- Receiving service query Lq’, the LBS server retrieves service results according to k locations and the corresponding service contents, and then, the LBS server returns service results to the vehicle user through RSU.
- (8)
- The vehicle user selects the required result from service results according to its location.
5. Performance Analysis
5.1. Security Analysis
5.1.1. Collusion Attack
5.1.2. Inference Attack
5.2. Computation Overhead
5.3. Communication Overhead
6. Performance Evaluation and Discussion
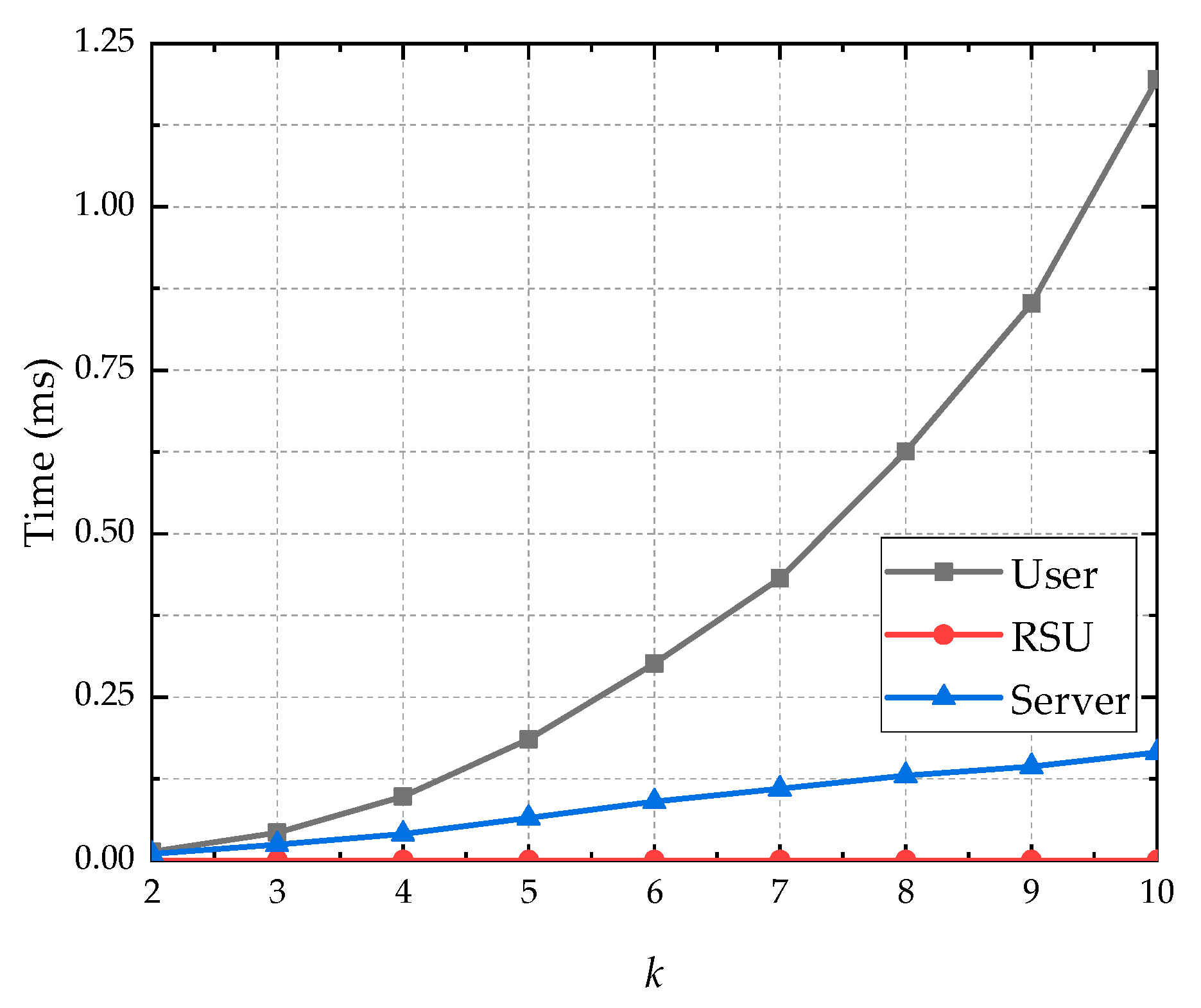
6.1. Computation Overhead
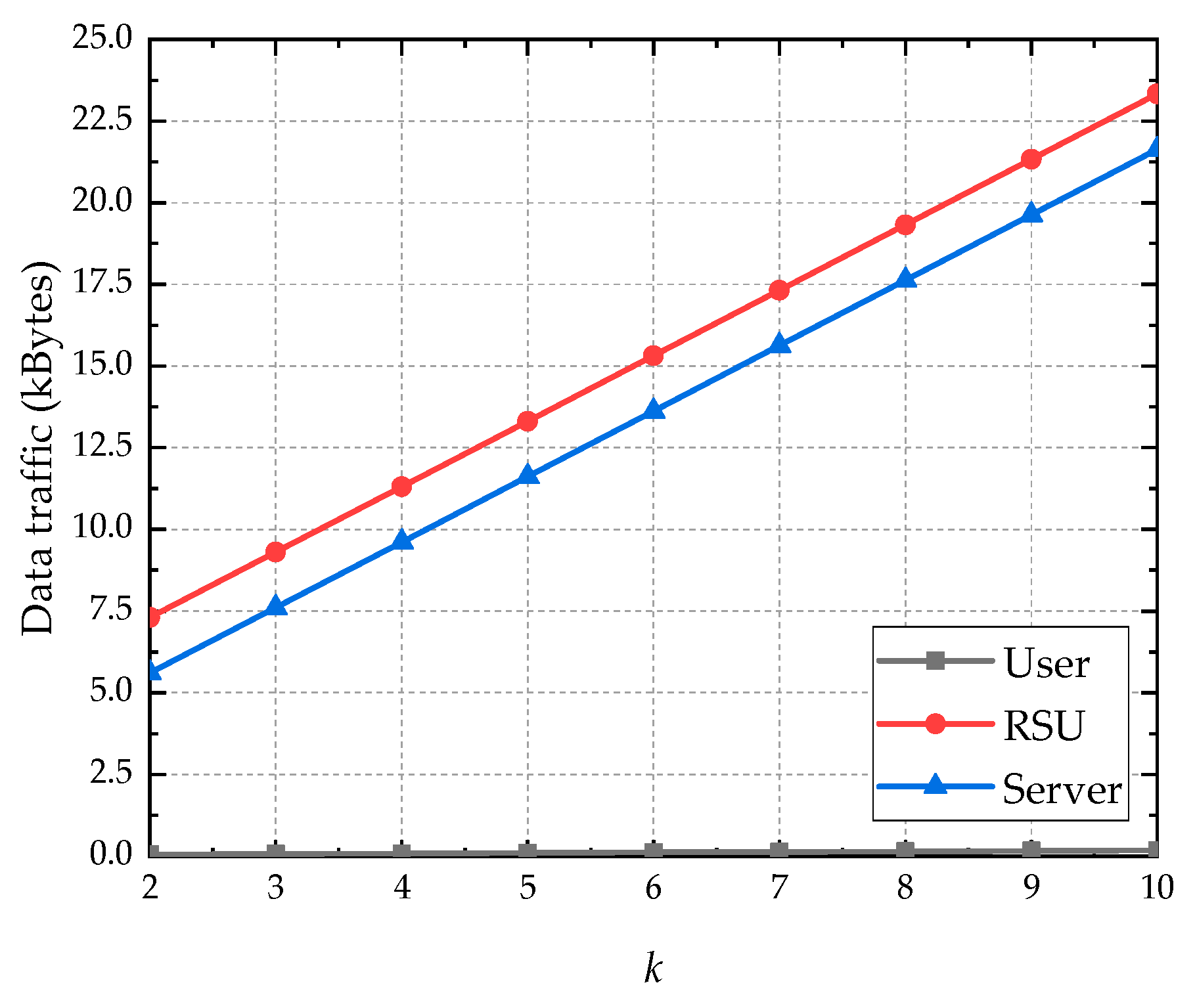
6.2. Communication Overhead
6.3. Anonymous Entropy
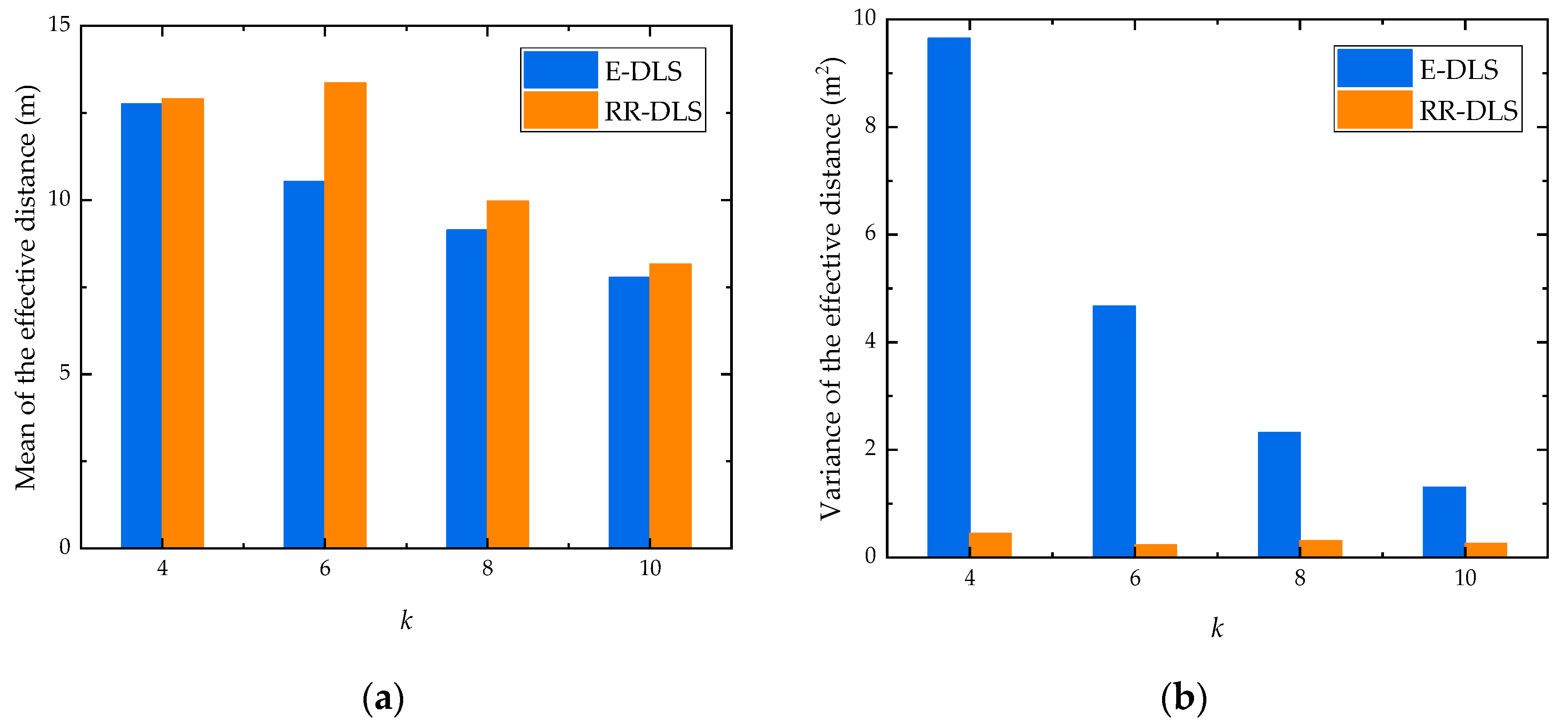
6.4. Effective Distance
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Raya, M.; Hubaux, J.-P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Zhao, L.; Song, Y.; Zhang, C.; Liu, Y.; Wang, P.; Lin, T.; Deng, M.; Li, H. T-GCN: A Temporal Graph Convolutional Network for Traffic Prediction. IEEE Trans. Intell. Transp. Syst. 2020, 21, 3848–3858. [Google Scholar] [CrossRef]
- Qiu, H.; Qiu, M.; Lu, R. Secure V2X Communication Network based on Intelligent PKI and Edge Computing. IEEE Netw. 2019, 34, 172–178. [Google Scholar] [CrossRef]
- Sun, G.; Sun, S.; Sun, J.; Yu, H.; Du, X.; Guizani, M. Security and privacy preservation in fog-based crowd sensing on the internet of vehicles. J. Netw. Comput. Appl. 2019, 134, 89–99. [Google Scholar] [CrossRef]
- Gupta, R.; Rao, U.P. An Exploration to Location Based Service and Its Privacy Preserving Techniques: A Survey. Wirel. Pers. Commun. 2017, 96, 1973–2007. [Google Scholar] [CrossRef]
- Jiang, T.; Wang, H.J.; Hu, Y.-C. Preserving location privacy in wireless lans. In MobiSys ′07: Proceedings of the 5th International Conference on Mobile Software Engineering and Systems; Association for Computing Machinery (ACM): New York, NY, USA, 2007; pp. 246–257. [Google Scholar]
- Sweeney, L. k-Anonymity: A Model for Protecting Privacy. Int. J. Uncertain. Fuzziness Knowl. Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef]
- Chow, C.-Y.; Mokbel, M.F.; Aref, W.G. Casper*: Query processing for location services without compromising privacy. ACM Trans. Database Syst. 2009, 34, 1–48. [Google Scholar] [CrossRef]
- Liu, S.; Wang, J.H.; Wang, J.; Zhang, Q. Achieving user-defined location privacy preservation using a P2P system. IEEE Access 2020, 8, 45895–45912. [Google Scholar] [CrossRef]
- Ji, Y.; Gui, R.; Gui, X.; Liao, D.; Lin, X. Location Privacy Protection in Online Query based-on Privacy Region Replacement. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 0742–0747. [Google Scholar]
- Perazzo, P.; Skvortsov, P.; Dini, G. On Designing Resilient Location-Privacy Obfuscators. Comput. J. 2015, 58, 2649–2664. [Google Scholar] [CrossRef]
- Kachore, V.A.; Lakshmi, J.; Nandy, S. Location Obfuscation for Location Data Privacy. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; pp. 213–220. [Google Scholar]
- Qiu, C.; Squicciarini, A.C. Location Privacy Protection in Vehicle-Based Spatial Crowdsourcing Via Geo-Indistinguishability. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–9 July 2019; pp. 1061–1071. [Google Scholar]
- Parmar, D.; Rao, U.P. Towards Privacy-Preserving Dummy Generation in Location-Based Services. Procedia Comput. Sci. 2020, 171, 1323–1326. [Google Scholar] [CrossRef]
- Sun, G.; Chang, V.; Ramachandran, M.; Sun, Z.; Li, G.; Yu, H.; Liao, D. Efficient location privacy algorithm for Internet of Things (IoT) services and applications. J. Netw. Comput. Appl. 2017, 89, 3–13. [Google Scholar] [CrossRef]
- Lu, H.; Jensen, C.S.; Yiu, M.L. Pad: Privacy-area aware, dummy based location privacy in mobile services. In MobiDE ′08: Proceedings of the Seventh ACM International Workshop on Data Engineering for Wireless and Mobile Access, Vancouver, BC, Canada, 13 June 2008; Association for Computing Machinery (ACM): New York, NY, USA, 2008; pp. 16–23. [Google Scholar]
- Liu, X.; Liu, K.; Guo, L.; Li, X.; Fang, Y. A game-theoretic approach for achieving k-anonymity in Location Based Services. In Proceedings of the IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 2985–2993. [Google Scholar]
- Niu, B.; Li, Q.; Zhu, X.; Cao, G.; Li, H. Achieving k-anonymity in privacy-aware location-based services. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 754–762. [Google Scholar]
- Liao, D.; Huang, X.; Anand, V.; Sun, G.; Yu, H. k-DLCA: An efficient approach for location privacy preservation in location-based services. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Pingley, A.; Zhang, N.; Fu, X.; Choi, H.-A.; Subramaniam, S.; Zhao, W. Protection of query privacy for continuous location based services. In Proceedings of the IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1710–1718. [Google Scholar]
- Liu, J.; Jiang, X.; Zhang, S.; Wang, H.; Dou, W. FADBM: Frequency-Aware Dummy-Based Method in Long-Term Location Privacy Protection. In Proceedings of the 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), Tianjin, China, 4–6 December 2019; pp. 384–391. [Google Scholar]
- Niu, J.; Zhu, X.; Shi, L.; Ma, J. Time-Aware Dummy-Based Privacy Protection for Continuous LBSs. In Proceedings of the 2019 International Conference on Networking and Network Applications (NaNA), Daegu, Korea, 10–13 October 2019; pp. 15–20. [Google Scholar]
- Yang, X.; Gao, L.; Zheng, J.; Wei, W. Location Privacy Preservation Mechanism for Location-Based Service with Incomplete Location Data. IEEE Access 2020, 8, 95843–95854. [Google Scholar] [CrossRef]
- Sun, G.; Cai, S.; Yu, H.; Maharjan, S.; Chang, V.; Du, X.; Guizani, M. Location Privacy Preservation for Mobile Users in Location-Based Services. IEEE Access 2019, 7, 87425–87438. [Google Scholar] [CrossRef]
- Hara, T.; Suzuki, A.; Iwata, M.; Arase, Y.; Xie, X. Dummy-Based User Location Anonymization under Real-World Constraints. IEEE Access 2016, 4, 673–687. [Google Scholar] [CrossRef]
- Luo, C.; Liu, X.; Xue, W.; Shen, Y.; Li, J.; Hu, W.; Liu, A.X. Predictable Privacy-Preserving Mobile Crowd Sensing: A Tale of Two Roles. IEEE/ACM Trans. Netw. 2019, 27, 361–374. [Google Scholar] [CrossRef]
- Zhou, L.; Yu, L.; Du, S.; Zhu, H.; Chen, C. Achieving Differentially Private Location Privacy in Edge-Assistant Connected Vehicles. IEEE Internet Things J. 2019, 6, 4472–4481. [Google Scholar] [CrossRef]
- Lin, X.; Lu, R. Pseudonym-changing strategy for location privacy. In Vehicular Ad Hoc Network Security and Privacy; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA; John Wiley & Sons: Hoboken, NJ, USA, 2015; Volume 1, pp. 71–90. [Google Scholar]
- Guo, N.; Ma, L.; Gao, T. Independent Mix Zone for Location Privacy in Vehicular Networks. IEEE Access 2018, 6, 16842–16850. [Google Scholar] [CrossRef]
- Al-Anwar, A.; Shoukry, Y.; Chakraborty, S.; Balaji, B.; Martin, P.; Tabuada, P.; Srivastava, M.B. PrOLoc: Resilient localization with private observers using partial homomorphic encryption. In Proceedings of the 16th ACM/IEEE International Conference on Information Processing in Sensor Networks, Pittsburgh, PA, USA, 18–21 April 2017; Association for Computing Machinery (ACM): New York, NY, USA, 2017; pp. 257–258. [Google Scholar]
- Negi, D.; Ray, S.; Lu, R. Pystin: Enabling Secure LBS in Smart Cities with Privacy-Preserving Top-k Spatial–Textual Query. IEEE Internet Things J. 2019, 6, 7788–7799. [Google Scholar] [CrossRef]
- Farouk, F.; Alkady, Y.; Rizk, R. Efficient Privacy-Preserving Scheme for Location Based Services in VANET System. IEEE Access 2020, 8, 60101–60116. [Google Scholar] [CrossRef]
- Ni, L.; Tian, F.; Ni, Q.; Yan, Y.; Zhang, J. An anonymous entropy-based location privacy protection scheme in mobile social networks. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 93. [Google Scholar] [CrossRef]
- Ying, B.; Makrakis, D. Protecting Location Privacy with Clustering Anonymization in vehicular networks. In Proceedings of the 2014 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 27 April–2 May 2014; pp. 305–310. [Google Scholar]
- Frejinger, E. Route Choice Analysis: Data, Models, Algorithms and Applications. Ph.D. Dissertation, Linköping University, Lausanne, Sweden, 30 April 2008. [Google Scholar]


| Entity | Computation Overhead | Communication Overhead |
|---|---|---|
| Vehicle user | O(k2 + IJU) | O(k) |
| RSU | O(1) | O(IJU + kn + k) |
| LBS Server | O(kn) | O(IJU + kn) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, X.; Chen, H.; Xie, L. A Location Privacy Preservation Method Based on Dummy Locations in Internet of Vehicles. Appl. Sci. 2021, 11, 4594. https://doi.org/10.3390/app11104594
Xu X, Chen H, Xie L. A Location Privacy Preservation Method Based on Dummy Locations in Internet of Vehicles. Applied Sciences. 2021; 11(10):4594. https://doi.org/10.3390/app11104594
Chicago/Turabian StyleXu, Xianyun, Huifang Chen, and Lei Xie. 2021. "A Location Privacy Preservation Method Based on Dummy Locations in Internet of Vehicles" Applied Sciences 11, no. 10: 4594. https://doi.org/10.3390/app11104594
APA StyleXu, X., Chen, H., & Xie, L. (2021). A Location Privacy Preservation Method Based on Dummy Locations in Internet of Vehicles. Applied Sciences, 11(10), 4594. https://doi.org/10.3390/app11104594







