A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning
Abstract
1. Introduction
- Revisiting state-of-the-art anti-ransomware technologies, particularly those assisted by machine learners to highlight the issues that they have overlooked in ransomware detection.
- Deploying an informative compact set of static and dynamic traits to holistically characterize the ransomware versions of both crypto and locker families.
- Enhancing numeral and statistic metrics to attribute a ransomware version to its ancestor family, and to fuse ransomware versions of multi- descent families, respectively.
- Proposing a machine learner that unearths the 0-Day versions of ransomware into a generalized class model.
- Designing a multi-tier streaming analytics model to implement in a realistic environment and operate on manifold platforms by integrating the compact set of traits, the numeral and statistic metrics, and the proposed machine learner.
- Significance of our proposals is manifested through testing, evaluating, and benchmarking on a big dataset consisting of 35,000 ransomware versions of 14 families, 500 versions of 10 malware, and 500 good-ware apps aggregated at a different time from different data archives.
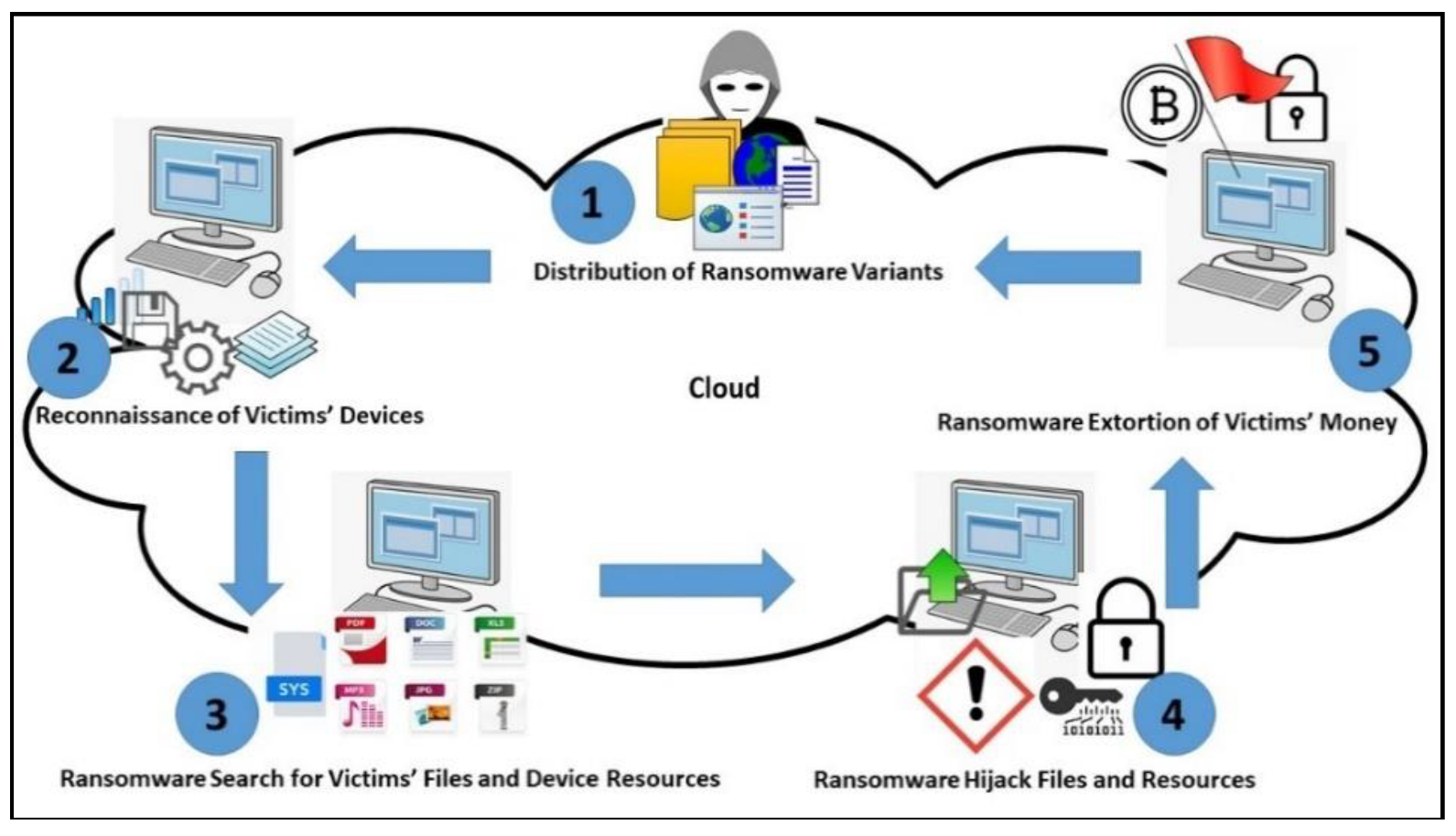
2. Ransomware Versions and Ransomware Families
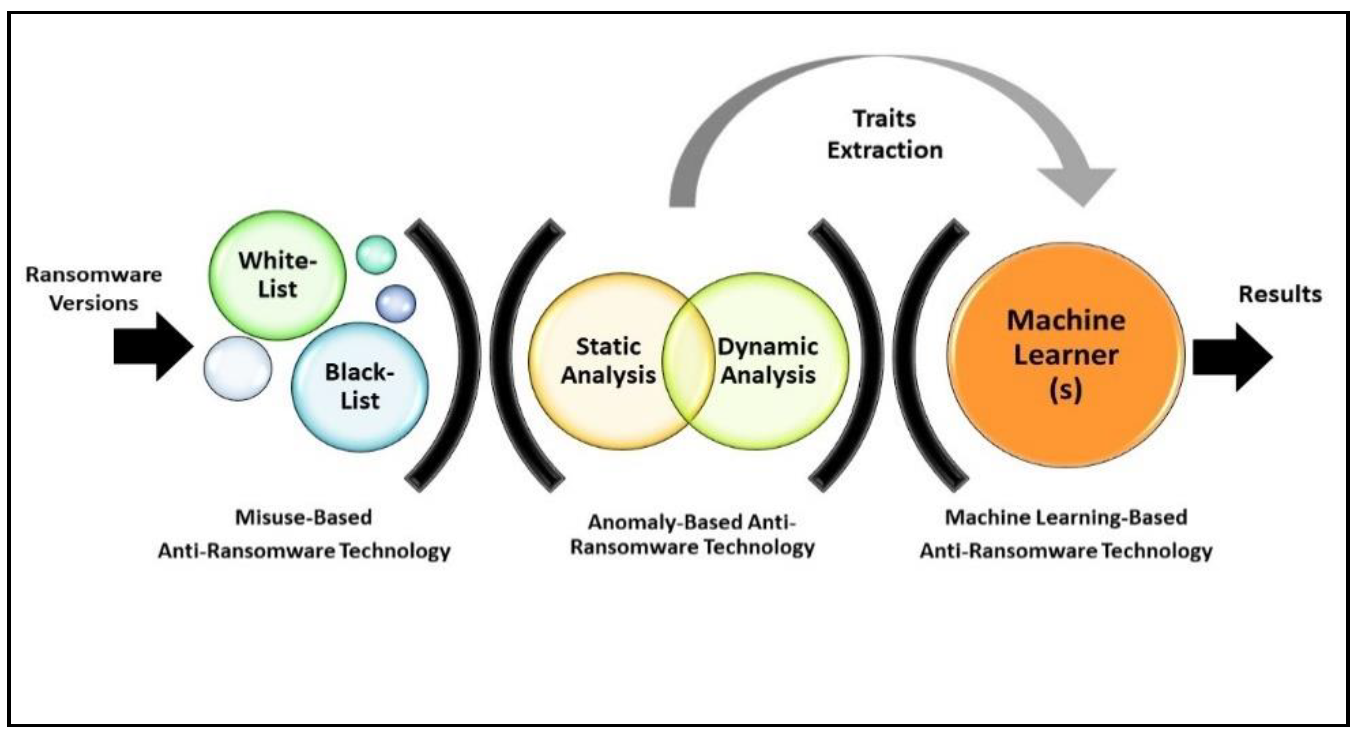
3. The State-of-The-Art of Anti-Ransomware Technology
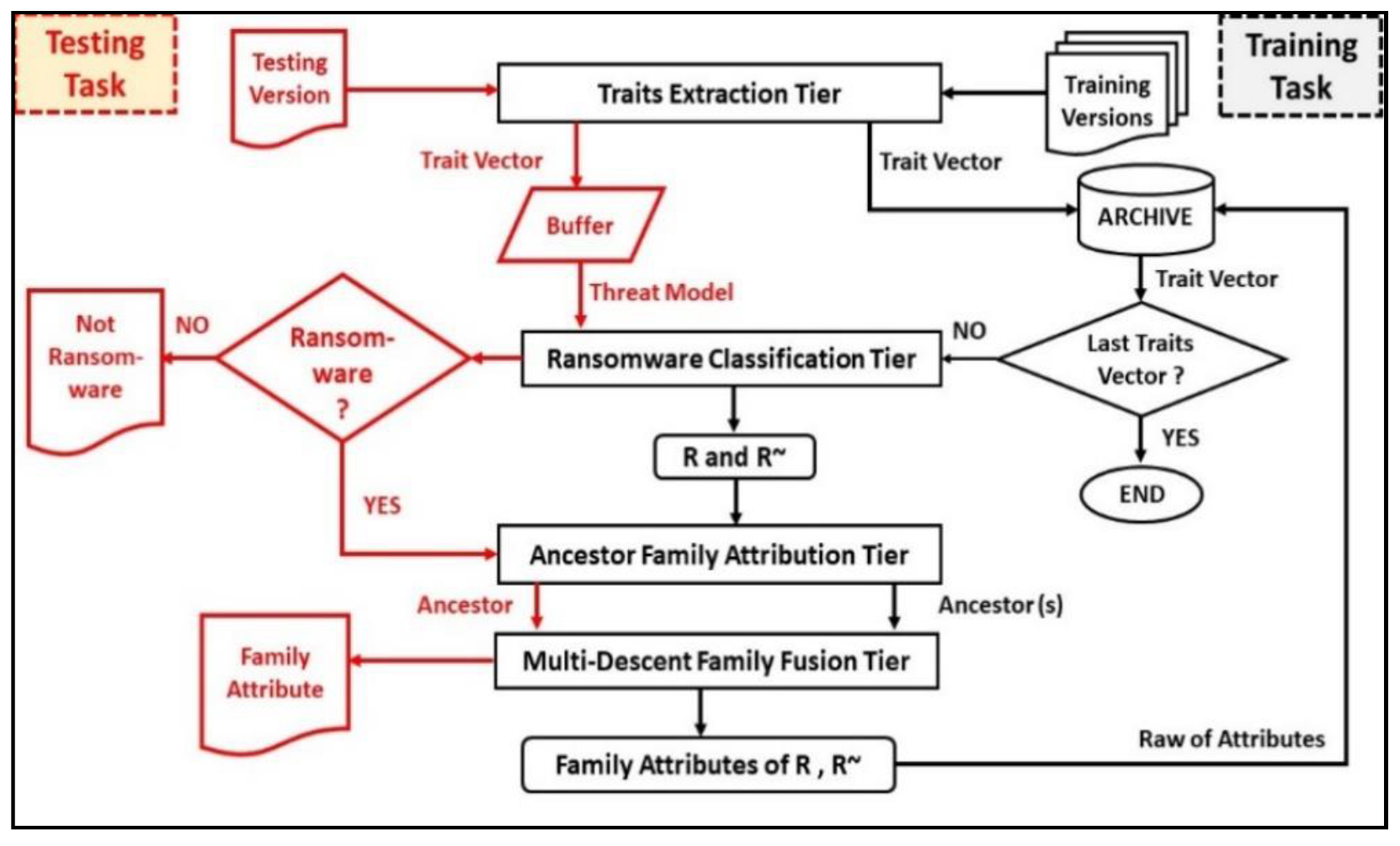
4. Materials and Methods
4.1. Ransomware Characterization
4.2. Ancestor Family Attribution and Multi-Descent Fusion
4.3. Ransomware Classification
| Algorithm 1 | |||
| Definition of Semantic Codes | |||
| Let | the stream of ransomware and non-ransomware versions such that | ||
| T the compact set of traits | |||
| Tspace the generated space of extracted traits where | |||
| Ti a trait vector included in Tspace | |||
| the decision tree of Tspace | |||
| the splitting space of Tspace such that | |||
| the class model of Ti, where , and M is the number of predictive classes | |||
| R the ransomware trait vectors (i.e., ransomware versions) | |||
| are the non-ransomware trait vectors (i.e., non-ransomware versions) | |||
| the trace file | |||
| the Attribution Rate of a trait vector | |||
| the multi-descent ratio of a trait vector | |||
| Input: | and T | ||
| Output: | R and R’ | ||
| Begin | |||
| 1. | Generate Tspace from with headers | ||
| 2. | Repeat (3) to (c) | ||
| 3. | a. Create | ||
| b. IF (all in Tspace have similar class ) THEN | |||
| c. Until THEN attach to the majority class model | |||
| 4. | For each Ti in Tspace | ||
| a. | find prior probability over Tspace by Equation (4) | ||
| b. | Find the conditional probability of about over by Equation (5) | ||
| c. | Update Ti in with the maximal | ||
| d. | Partition into and | ||
| 5. | Repeat (6) Until () AND () | ||
| 6. | Keep all computed probabilities in R and for classification decision | ||
| 7. | For each Ti in R and | ||
| a. | find | ||
| b. | find | ||
| c. | keep and in the trace file | ||
| End | |||
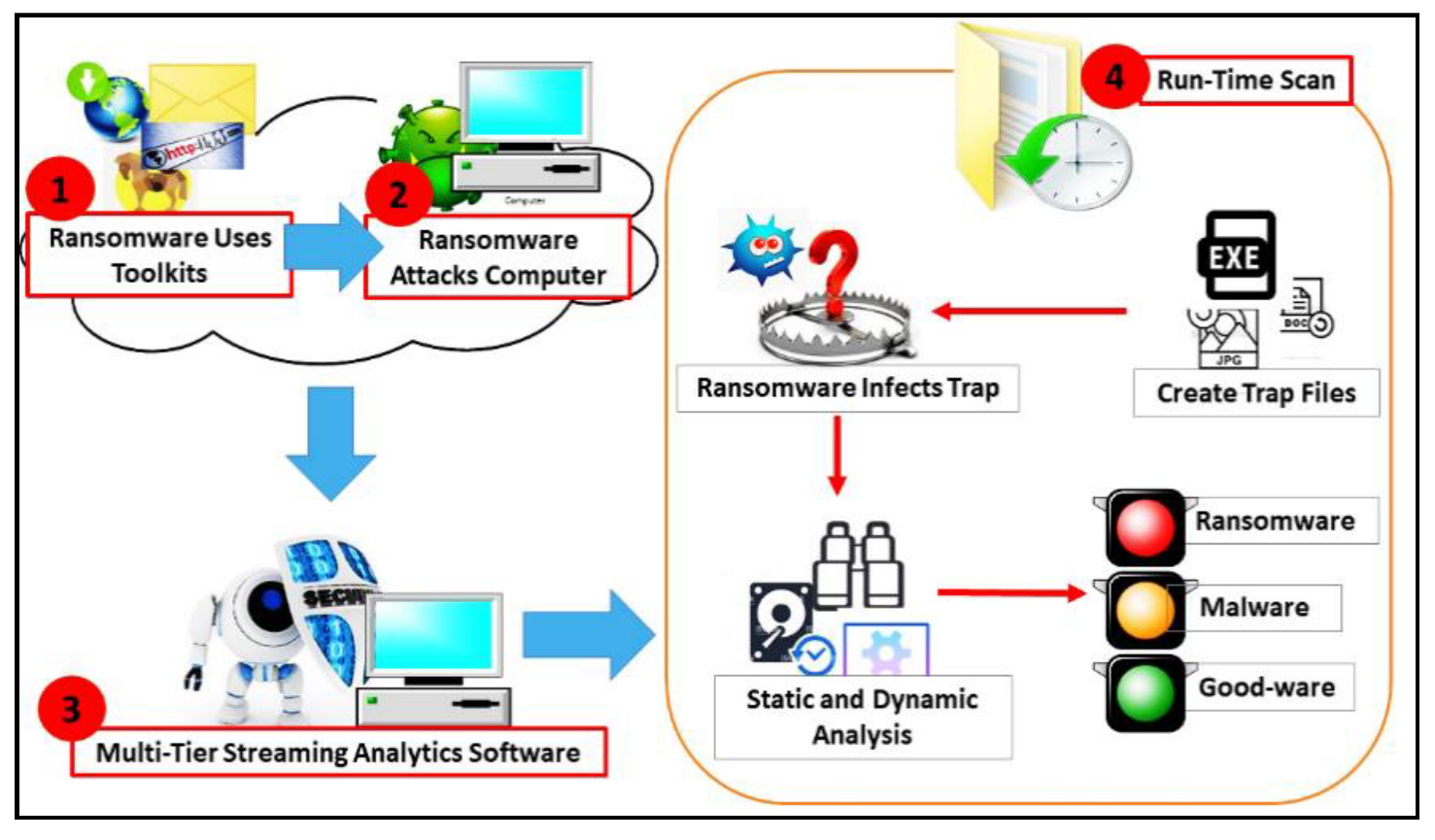
4.4. Structure of the Ransomware Multi-Tier Streaming Analytics Model
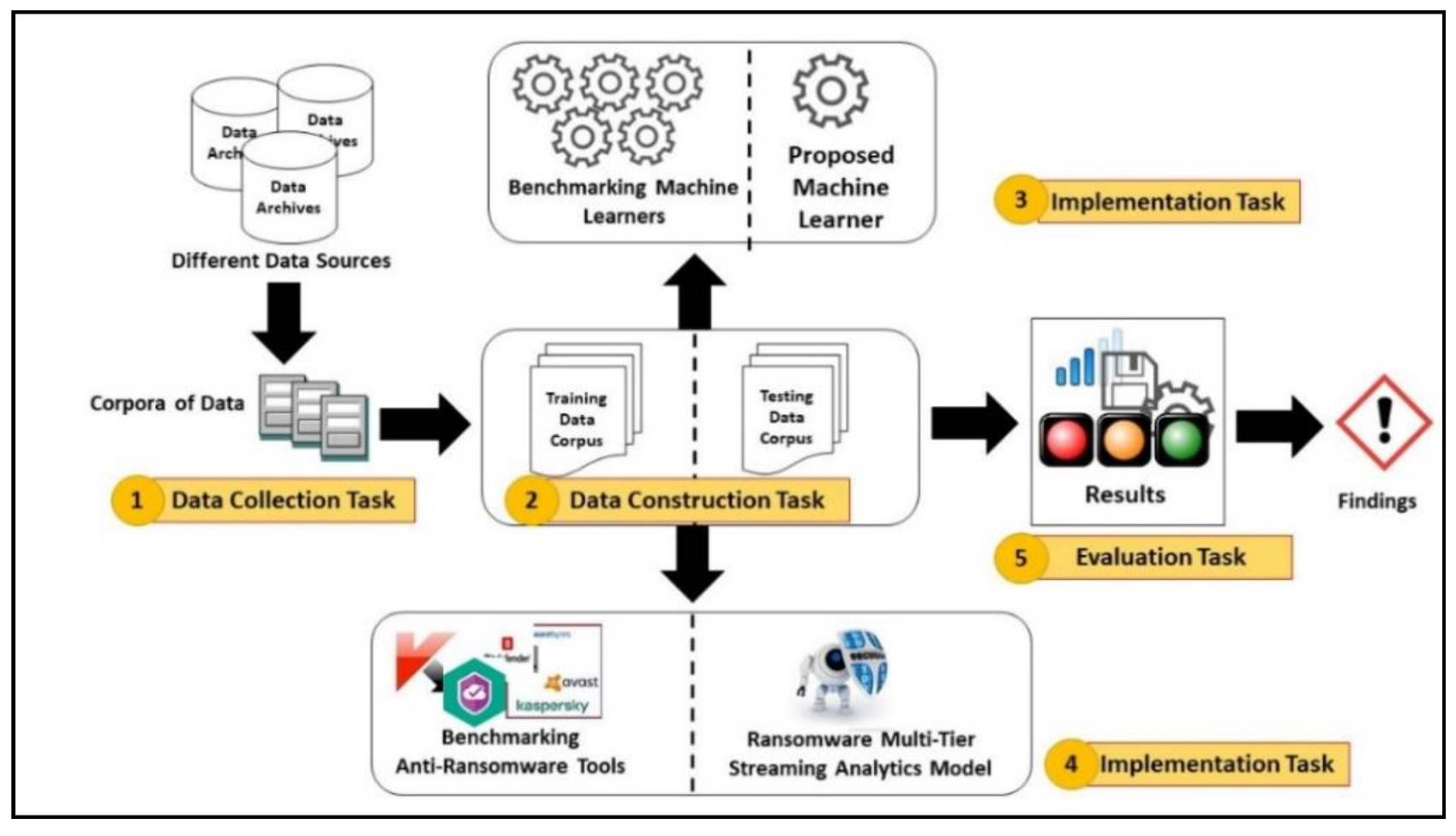
5. Experiments and Results
5.1. Runtime Test Routine
5.2. Data Collection and Evaluation Metrics
5.3. Comparative Experiment
5.4. Realistic Experiment
6. Discussion
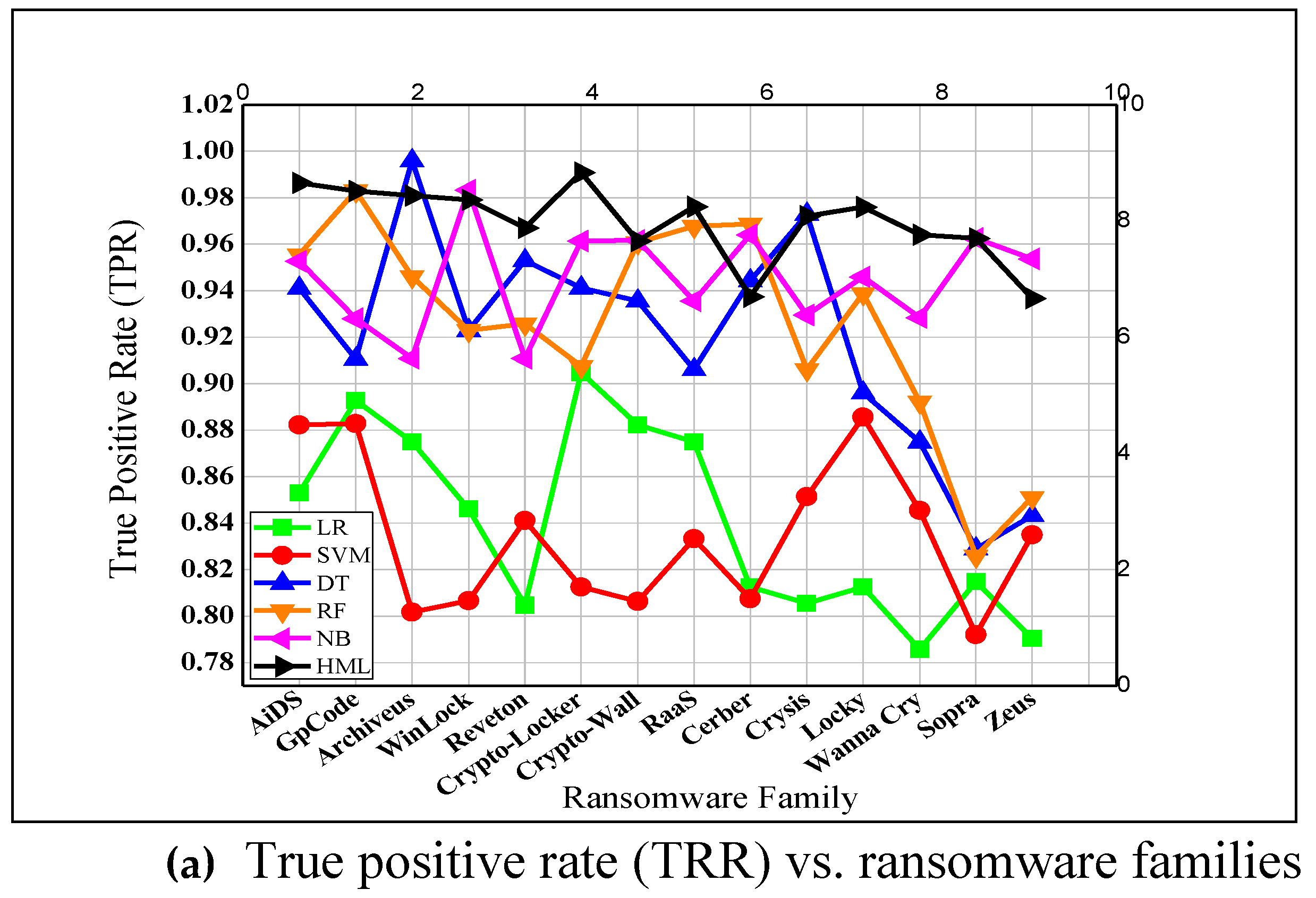
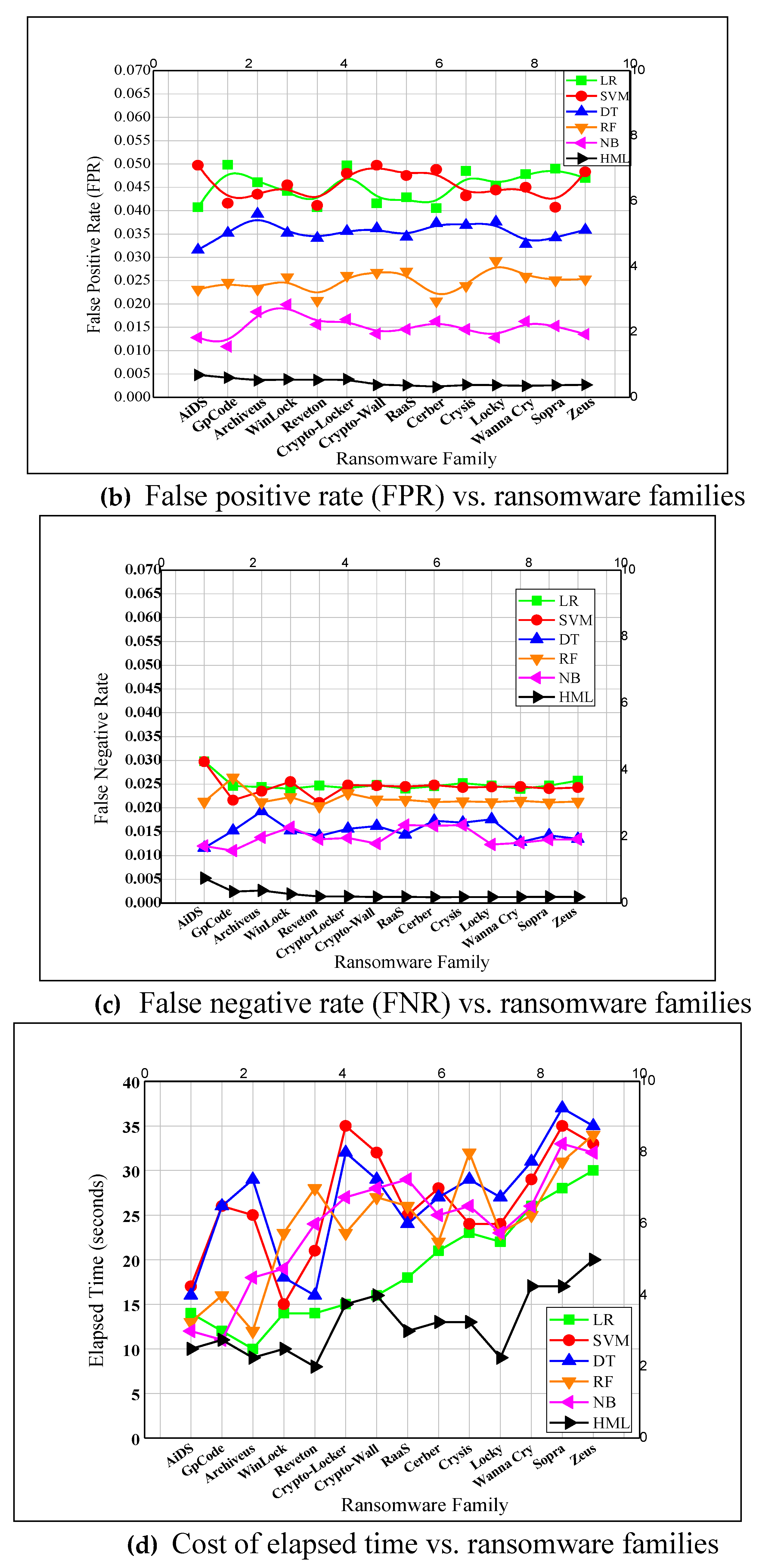
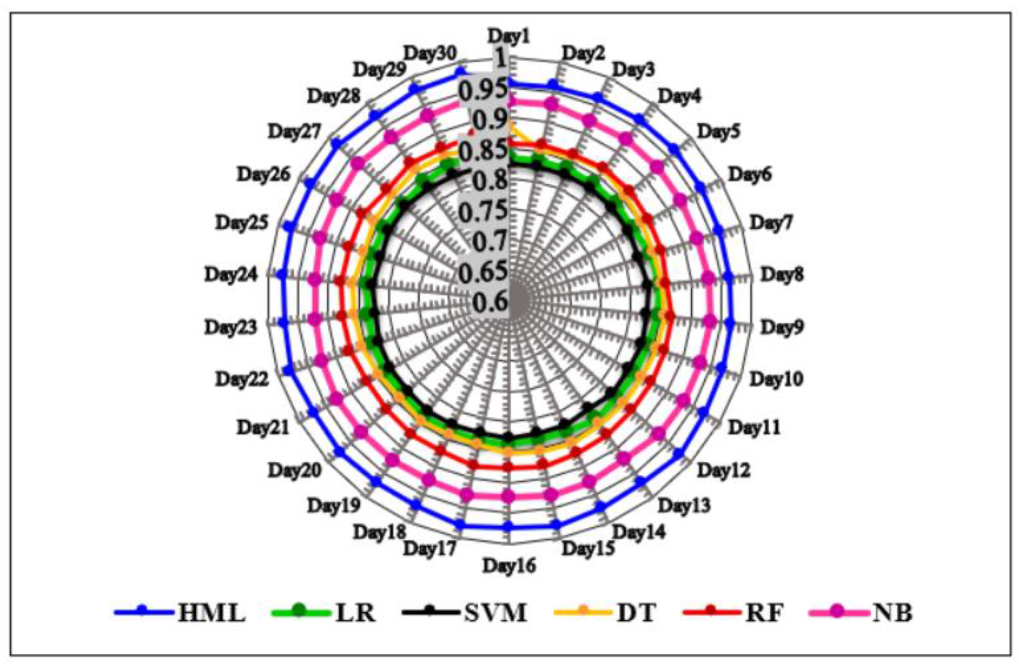
- Shortage in static analysis. Not all the state-of-the-art machine learners leverage static traits to characterize versions of all-inclusive ransomware families. Indeed, many ransomware families might exploit more adversarial scripts to intrude on their target operating systems [6,24]. Thus, the examined machine learners showed their defeatism against static exploits of ransomware, and they achieved low to sensible TPRs along with nontrivial FPRs and FNRs, as shown in Figure 6 and Figure 8. In addition, some of the examined anti-ransomware tools revealed partial characterization of such static exploits on data corpora, as shown in Figure 7.
- Shortage in dynamic analysis. Tracking the behavioral traits, executed server controls, I/O resources, buffers, system activity, file events, CPU processes, and memory usage; all together, these are more distinctive to classify ransomware versions than the static exploitations [13,15,21]. However, their analysis and extraction require a virtual testbed which must be designed under realistic conditions to trigger ransomware payloads, linking libraries, and access permissions. As shown in Figure 6, the state-of-the-art machine learners fall short in tracing a ransomware’s infection chain, and they produced trivial FPRs because they are mostly devoted to semi-realistic environments and lack the necessary triggers. Then, they are rendered vulnerable against any 0-Day ransomware versions during the second comparative experiment in realistic practice (see Figure 7).
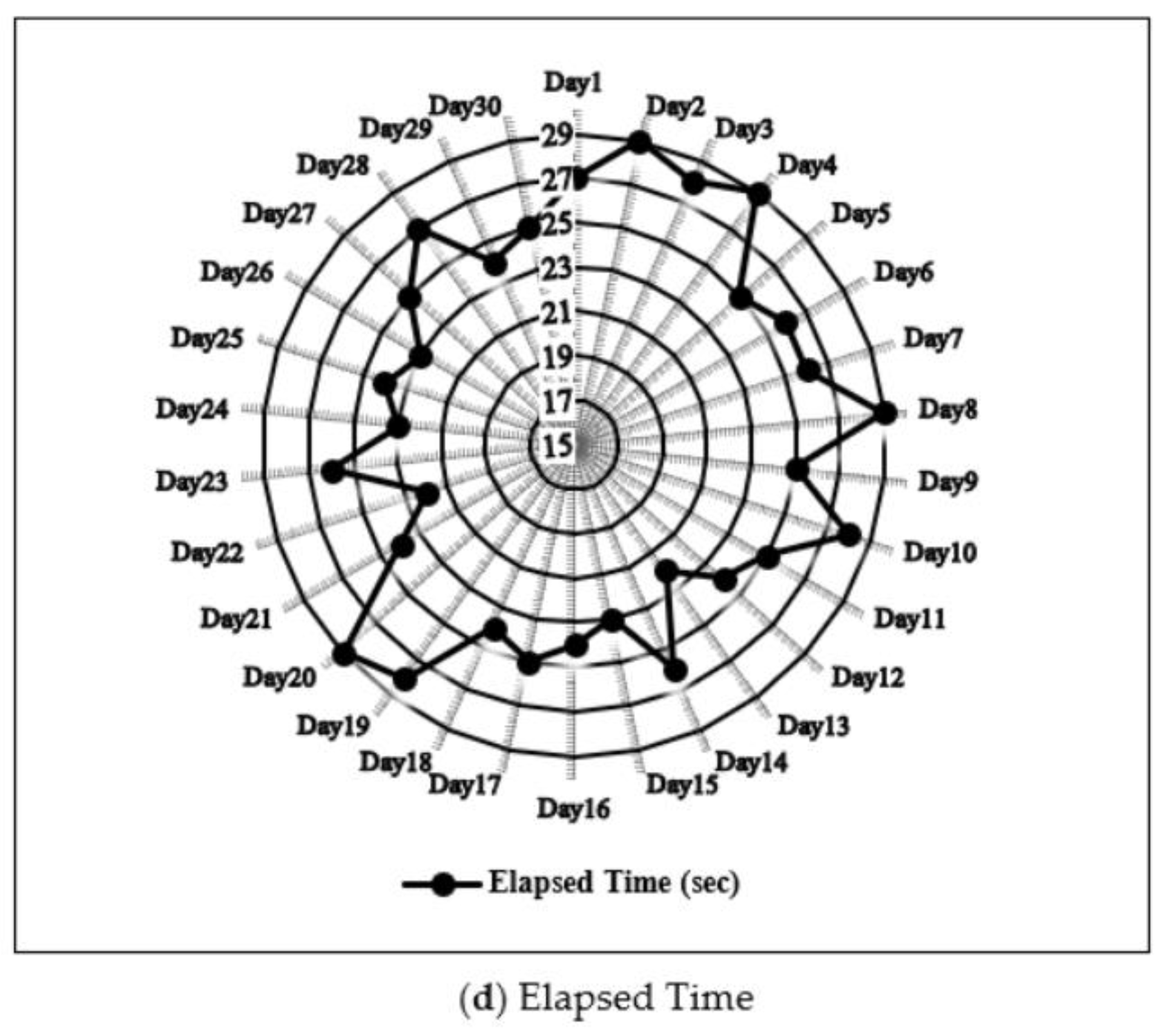
- Elapsed time-accuracy trade-off. The trade-off between elapsed time and classification accuracy is a double-edges sword in machine learning [37]. Almost all, the examined machine learners and anti-ransomware tools achieved acceptable accuracy rates but at unacceptable elapsed time for detecting an incremental stream of training and testing corpora (see Figure 6 and Figure 7). Elapsed time is a crucial factor to consider in ransomware detection since its computation depends on the traits’ relevance and redundancy to the data corpus, the number of traits to be extracted from data corpus, the dimensionality of data corpus to learn, the extensive utilization of device’s resources like CPU and memory and the computation complexity of the machine learning algorithm during both learning and testing tasks. Thus, some machine learners showcase high accuracy rates, but they spend a long elapsed time to obtain the detection results.
- Unaware of multi-descent versions of ransomware. The training and testing corpora of versions might involve versions of other malware and scareware families that probably share similar and mutually inter-related static exploits and dynamic behaviors and functionalities [6,24]. This may confuse machine learners, which leverage binary-class inductive function rather than a multi-class inductive function [36,37]. As a result, almost examined machine learners achieved high to moderate false classifications versus valid ransomware versions; those are descents of multiple ransomware and/or malware families, as shown in Figure 6, Figure 7 and Figure 8. Hence a manifold induction could be attained by hybridizing multiple machine learners and/or statistic pruning formularization as it is adopted in HML
- Imbalanced corpora of data. Experimentally, the state-of-the-art machine learners produced their own predictions by learning the employed set of traits on the corpus of training data that was (i) various in the versions of other cyber-attacks like scareware and malware, etc. (ii) sub-optimally representative of ransomware detection, (iii) imbalanced in ransomware family population and ransomware-type distribution (i.e., crypto and locker), and (iv) varied in aggregation time. Altogether, it caused substantial FPRs, FNRs, and insignificant AUCs, as shown in Figure 6 and Figure 7, respectively. Similarly, the examined anti-ransomware tools achieved incompetent outcomes versus the aforesaid corpus of data, as shown in Figure 8.
- Unreliable source of data. Most of the popular archives of ransomware fall short in providing reliable and unique ransomware datasets that is a complementary factor of boosting the implicit ransomware classification against 0-Day ransomware versions and imperviously detected ransomware families [4,6,7,12]. It is observed in Figure 6 and Figure 7 that predicting valid ransomware versions across unreliable training corpus of data could be crucial to adjust the decision margins of the examined machine learners. Hence, resembling a reliable training corpus by re-learning the default predictions would solve the problem of substantial FPRs [37,38].
- Unaware of family attribution. Escalated ransomware streams from 2005 to 2019 yield more than 30 different ransomware families of both locker and crypto types [21,24,34,35]. This is attributed to the availability of e-services, social engineering, and primitive ciphering technologies that enable cyber-criminals to advance their ransomware without sophisticated knowledge [21,24]. However, the big stream of ransomware versions might share mutually inter-related traits that cause overfitting to decisive margins of machine learners and then limited detection against some ransomware families with high rates of FNR, as shown in Figure 6.
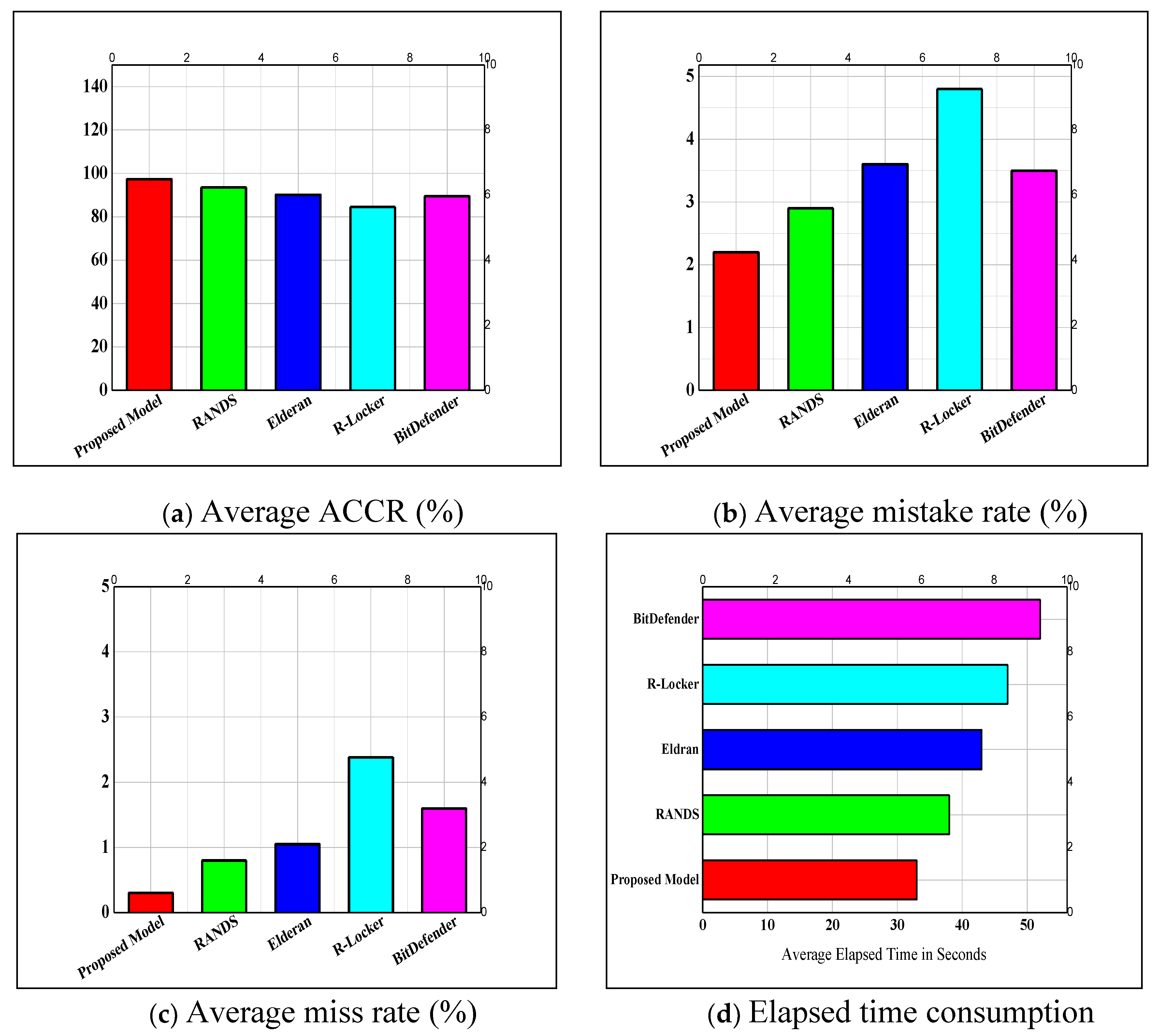
- Realistic and semi-realistic environment. The comparable machine learners, except HMLC that is devoted by [34,35], are still inactive to learn the misclassified versions of ransomware, and they achieve sub-optimal AUCs (see Figure 9). This is attributed to their decisive default settings, which fall short in minimizing the future cases of their predictions, which rely on their high rates of falsely detected versions versus their low rates of the truly detected versions. By product, the examined machine learners are still unaware of imperviously classified ransomware families on chronologically increasing ransomware stream.
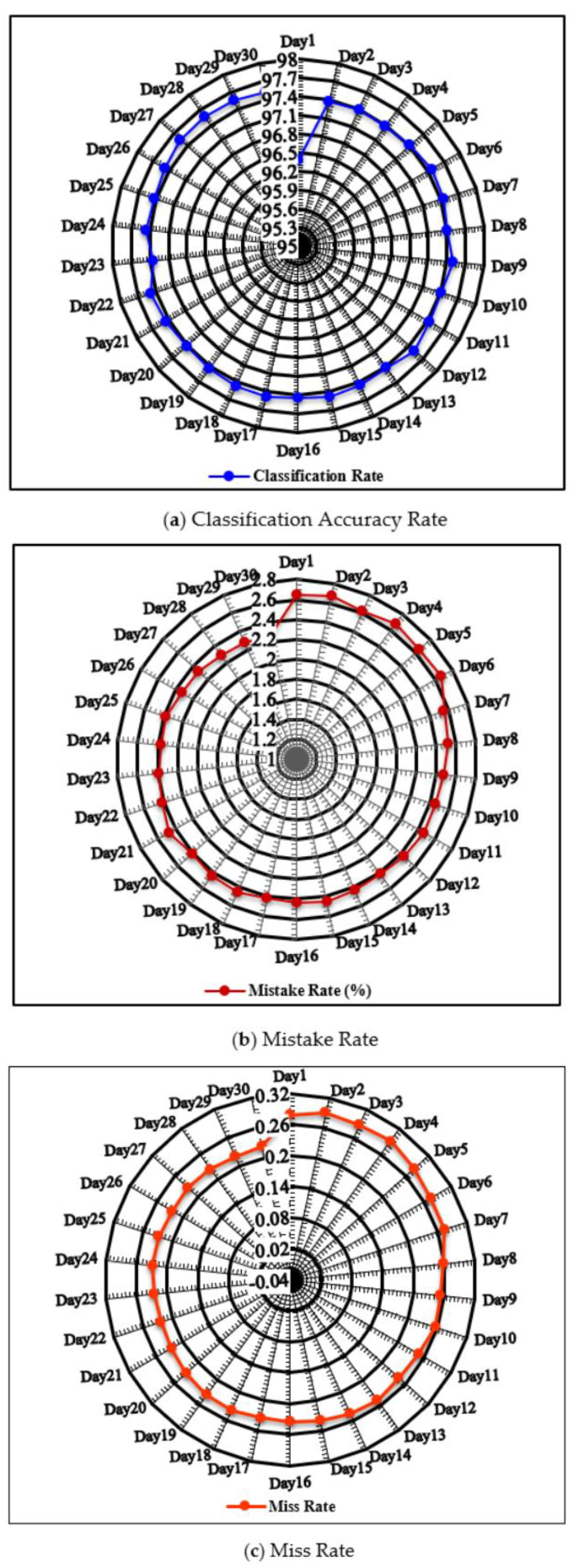
- Set of traits. Great care was put on exploring and utilizing the most generic and evolutionary traits of ransomware families. Twenty-four different traits of both static-type and dynamic-type are used to provide a holistic characterization of ransomware versions among the versions of other cyber-attacks. Thus, our proposed work was privileged at classifying ransomware in the semi-realistic and realistic modes as it is observed from the experimental outcomes in Figure 6, Figure 7, Figure 8 and Figure 9.
- Hybrid machine learner. The evaluation outcomes in Figure 6, Figure 7, Figure 8 and Figure 9 restated that the proposed HML was more competent among its competitors. This was attributed to (i) its dual inductive function that is a hybrid of NB and DT functions, and (ii) its adjustable decisive boundary that is complementary of numeral and statistic metrics, AR and MDR. Accordingly, it achieved higher detection rates than others against the versions of ever-seen and/or never-seen ransomware families on big and different corpora of data.
- Training and testing corpora of data. The corpora of data were collected during a one-year period of time at different runtimes ₮. Due to this periodic aggregation of data corpora every ₮, the training, and testing tasks would be less biased versus the implicit and explicit class distribution problem in the examined data stream. Moreover, the data corpora were privileged in terms of quantity and variety of versions 45 K of ransomware, malware, and good-ware versions), quantity and variety of families (14 ransomware families), the difference of aggregation time, the difference of data archives, and imbalance of versions belong to common ancestors as well as the multi-descent versions (see Figure 6, Figure 7, Figure 8 and Figure 9).
- Realistic conditions. To customize the overall performance, the proposed ransomware streaming analytics model with the presence of the proposed HML was run with the assumption of learning a corpus of data at its actual runtime ₮. Hence, a suspicious version R that was inspected at time ₮ could be classified as a ransomware version in the future runtime iteration of (₮ + Δ). That, in turn, would control the trade-off between the elapsed time, which relied on both CPU and memory consumption of the hosted system and the rate of detection accuracy in the realistic environment (see Figure 8 and Figure 9).
7. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Bhardwaj, A.; Avasthi, V.; Sastry, H.; Subrahmanyam, G.V.B. Ransomware digital extortion: A rising new age threat. Indian J. Sci. Technol. 2016, 9, 1–5. [Google Scholar] [CrossRef]
- Richardson, R.; North, M. Ransomware: Evolution, mitigation and prevention. Int. Manag. Rev. 2017, 13, 10–21. [Google Scholar]
- Azmoodeh, A.; Dehghantanha, A.; Conti, M.; Choo, K.K.R. Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J. Ambient Intell. Humaniz. Comput. 2018, 9, 1141–1152. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- Tailor, J.P.; Patel, A.D. A comprehensive survey: Ransomware attacks prevention, monitoring and damage control. Int. J. Res. Sci. Innov. 2017, 4, 2321–2705. [Google Scholar]
- Kok, S.; Abdullah, A.; Jhanjhi, N.; Supramaniam, M. Ransomware, threat and detection techniques: A review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 136. [Google Scholar]
- Yaqoob, I.; Ahmed, E.; Rehman, M.H.; Ahmed, A.I.A.; Al-Garadi, M.A.; Imran, M.; Guizani, M. The rise of ransomware and emerging security challenges in the Internet of Things. Comput. Netw. 2017, 129, 444–458. [Google Scholar] [CrossRef]
- Pathak, P.B.; Nanded, Y.M. A dangerous trend of cybercrime: Ransomware growing challenge. Int. J. Adv. Res. Comput. Eng. Technol. 2016, 5, 371–373. [Google Scholar]
- Herrera Silva, J.A.; Barona López, L.I.; Valdivieso Caraguay, Á.L.; Hernández-Álvarez, M. A survey on situational awareness of ransomware attacks—detection and prevention parameters. Remote Sens. 2019, 11, 1168. [Google Scholar] [CrossRef]
- Zavarsky, P.; Lindskog, D. Experimental analysis of ransomware on windows and android platforms: Evolution and characterization. Proced. Comput. Sci. 2016, 94, 465–472. [Google Scholar]
- Sgandurra, D.; Muñoz-González, L.; Mohsen, R.; Lupu, E.C. Automated dynamic analysis of ransomware: Benefits, limitations and use for detection. arXiv 2016, arXiv:1609.03020. [Google Scholar]
- Kok, S.H.; Abdullah, A.; Jhanjhi, N.Z.; Supramaniam, M. Prevention of crypto-ransomware using a pre-encryption detection algorithm. Computers 2019, 8, 79. [Google Scholar] [CrossRef]
- Morato, D.; Berrueta, E.; Magaña, E.; Izal, M. Ransomware early detection by the analysis of file-sharing traffic. J. Netw. Comput. Appl. 2018, 124, 14–32. [Google Scholar] [CrossRef]
- Sihwail, R.; Omar, K.; Ariffin, K.A.Z. A survey on malware analysis techniques: Static, dynamic, hybrid and memory analysis. Int. J. Adv. Sci. Eng. Inf. Technol. 2018, 8, 1662. [Google Scholar] [CrossRef]
- Stiborek, J.; Pevný, T.; Rehák, M. Probabilistic analysis of dynamic malware traces. Comput. Secur. 2018, 74, 221–239. [Google Scholar] [CrossRef]
- Cybersecurity, K.E. The Protection Technologies of Kaspersky Endpoint Security. Available online: https://mediacircle.de/pdf/Protection_Technologies_Whitepaper.pdf (accessed on 3 March 2020).
- Kharraz, A.; Kirda, E. Redemption: Real-time protection against ransomware at end-hosts. In International Symposium on Research in Attacks, Intrusions, and Defenses; Springer: Cham, Switzerland, 2017; pp. 98–119. [Google Scholar]
- Kharaz, A.; Arshad, S.; Mulliner, C.; Roberson, W.K.; Krida, E. UNVEIL: A large scale, automated approach to detecting ransomware. In Proceedings of the 2017 IEEE 24th International Conference on Software Analysis, Evolution and Reengineering (SANER), Klagenfurt, Austria, 20–24 February 2017; pp. 757–772. [Google Scholar]
- Gómez-Hernández, J.A.; Álvarez-González, L.; García-Teodoro, P. R-Locker: Thwarting ransomware action through a honeyfile-based approach. Comput. Secur. 2018, 73, 389–398. [Google Scholar] [CrossRef]
- Cabaj, K.; Gregorczyk, M.; Mazurczyk, W. Software-defined networking-based crypto ransomware detection using HTTP traffic characteristics. Comput. Electr. Eng. 2018, 66, 353–368. [Google Scholar] [CrossRef]
- Hampton, N.; Baig, Z.; Zeadally, S. Ransomware behavioural analysis on windows platforms. J. Inf. Secur. Appl. 2018, 40, 44–51. [Google Scholar] [CrossRef]
- Feng, Y.; Liu, C.; Liu, B. Poster: A new approach to detecting ransomware with deception. In Proceedings of the 38th IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–24 May 2017. [Google Scholar]
- Cimitile, A.; Mercaldo, F.; Nardone, V.; Santone, A.; Visaggio, C.A. Talos: No more ransomware victims with formal methods. Int. J. Inf. Secur. 2018, 17, 719–738. [Google Scholar] [CrossRef]
- Zhang, H.; Xiao, X.; Mercaldo, F.; Ni, S.; Martinelli, F.; Sangaiah, A.K. Classification of ransomware families with machine learning based on N-gram of opcodes. Future Gener. Comput. Syst. 2019, 90, 211–221. [Google Scholar] [CrossRef]
- Alhawi, O.M.; Baldwin, J.; Dehghantanha, A. Leveraging machine learning techniques for windows ransomware network traffic detection. In Cyber Threat Intelligence; Advances in Information Security (ADIS, Volume 70); Springer: Cham, Switzerland, 2018; pp. 93–106. [Google Scholar]
- Bae, S.I.; Lee, G.B.; Im, E.G. Ransomware detection using machine learning algorithms. Concurr. Comput. Special Issue 2016. [Google Scholar] [CrossRef]
- Aburomman, A.A.; Reaz, M.B.I. A survey of intrusion detection systems based on ensemble and hybrid classifiers. Comput. Secur. 2017, 65, 135–152. [Google Scholar] [CrossRef]
- Tsai, C.-F.; Hsu, Y.-F.; Lin, C.-Y.; Lin, W.-Y. Intrusion detection by machine learning: A review. Expert Syst. Appl. 2009, 36, 11994–12000. [Google Scholar] [CrossRef]
- Shabtai, A.; Moskovitch, R.; Elovici, Y.; Glezer, C. Detection of malicious code by applying machine learners on static features: A state-of-the-art survey. Inf. Secur. Tech. Rep. 2009, 14, 16–29. [Google Scholar] [CrossRef]
- Continella, A.; Guagnelli, A.; Zingaro, G.; De Pasquale, G.; Barenghi, A.; Zanero, S.; Maggi, F. ShieldFS: A self-healing, ransomware-aware filesystem. In Proceedings of the 32nd Annual Conference on Computer Security Applications, ACM, New York, NY, USA, 5–8 December 2016; pp. 336–347. [Google Scholar]
- Ahmadian, M.M.; Shahriari, H.R. 2entFOX: A framework for high survivable ransomwares detection. In Proceedings of the 13th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), Tehran, Iran, 7–8 September 2016; pp. 79–84. [Google Scholar]
- Zimba, A. Malware-free Intrusion: A novel approach to Ransomware infection vectors. Int. J. Comput. Sci. Inf. Secur. 2017, 15, 317. [Google Scholar]
- Shaukat, S.K.; Ribeiro, V.J. RansomWall: A layered defense system against cryptographic ransomware attacks using machine learning. In Proceedings of the 10th International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 3–7 January 2018; pp. 356–363. [Google Scholar]
- Zuhair, H.; Selamat, A. RANDS: A machine learning-based anti-ransomware tool. In Advancing Technology Industrialization through Intelligent Software Methodologies, Tools and Techniques, In Proceedings of the 18th International Conference on New Trends in Intelligent Software Methodologies, Tools and Techniques (SoMeT2019), Kuching, Sarawak, Malaysia, 23–25 September 2019; IOS Press: Amsterdam, The Netherlands, 2019; pp. 573–587. [Google Scholar] [CrossRef]
- Zuhair, H.; Selamat, A. An Intelligent and Real-Time Ransomware Detection Tool Using Machine Learning Algorithm. J. Theor. Appl. Inf. Technol. 2019, 97, 3448–3461. [Google Scholar]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R.; Choo, K.K.R.; Newton, D.E. DRTHIS: Deep ransomware threat hunting and intelligence system at the fog layer. Future Gener. Comput. Syst. 2019, 90, 94–104. [Google Scholar] [CrossRef]
- Krawczyk, B.; Minku, L.L.; Gama, J.; Stefanowski, J.; Woźniak, M. Ensemble learning for data stream analysis: A survey. Inf. Fusion 2017, 37, 132–156. [Google Scholar] [CrossRef]
- Huang, G.; Huang, G.B.; Song, S.; You, K. Trends in extreme learning machines: A review. Neural Netw. 2015, 61, 32–48. [Google Scholar] [CrossRef]
- Kwon, O.; Sim, J.M. Effects of data set features on the performances of classification algorithms. Expert Syst. Appl. 2013, 40, 1847–1857. [Google Scholar] [CrossRef]
- Benign Software. Available online: http://software.informer.com/software/ (accessed on 4 April 2019).
- Virus Share, “Malware Repository”. Available online: https://virusshare.com (accessed on 13 January 2019).
- Virus Total-Intelligence Search Engine, “Free Online Virus, Malware URL Scanner”. Available online: https://www.virustotal.com (accessed on 21 August 2019).
| Family | Year | Type | Exploits and Actions | Damage (s) |
|---|---|---|---|---|
| AiDS [10] | 1989 | Crypto | It was delivered to computer-based information systems via floppy disks |
|
| GpCode [10,11] | 2005 | Crypto | It was developed with an asymmetric encryption algorithm to encrypt users’ data files |
|
| Archiveus [10,11] | 2006 | Crypto | It was applied with the RSA algorithm to encrypt system files |
|
| WinLock [10,11] | 2010 | Locker | It locked the computer system and demanded ransom via sending SMS to the victim’s phone number |
|
| Reveton [4,10,11] | 2012 | Locker | It impersonated the law enforcement agencies to deceive users with rumor claims |
|
| Crypto-Locker [4,10,11] | 2013 | Crypto | It encrypted the file’s contents by RSA algorithm with private and public keys |
|
| Crypto-Wall [4,10,11] | 2014 | Crypto | It encrypted the system files and injected malicious codes which freezes the system’s firewalls |
|
| Ransom as Service (RaaS) [6,10] | 2015 | Locker | It used the social engineering techniques to impersonate a good-ware website as a malicious website in the dark web |
|
| Cerber [10,11] | 2016 | Crypto | It injected the malicious instructions to overwrite an encrypted content onto the original system |
|
| Crysis [10] | 2016 | Crypto | It encrypted the system files, rewrote their contents, and renamed them |
|
| Locky [4,10,11] | 2016 | Locker | It used the social engineering techniques to intrude the system through vulnerabilities of system settings, deactivated the registry actions, and removed the backup data |
|
| WannaCry [4,10] | 2017 | Crypto | It encrypted the contents of the system files and removed the original system files |
|
| Sopra [12,13] | 2017 | Crypto | It encrypted the contents of the system files and removed the original system files |
|
| Zeus [12,13] | 2018 | Crypto | It encrypted the contents of systems files and created new files with extensions belonging to different ransomware versions |
|
| Table | Description | Demerits | Examples |
|---|---|---|---|
| Misuse-Based Technology [6,14,15,16] | They analyze ransomware versions to extract cryptographic primitives, suspicious scripts, built-in functions, infected files’ paths, and extensions. They achieved moderate accuracy in lightweight performance | -User’s data can be lost -They can be obfuscated -They can be defeated against 0-Day ransomware versions -A lot of false alarms -The database must be updated frequently | Bitdefender |
| Kaspersky | |||
| McAfee | |||
| Avast | |||
| Anomaly-Based Technology [17,18,19,20,21,22,23] | They trace ransomware runtime activities, computer processes, CU and memory footprints, server actions and control to detect ransomware versions effectively and efficiently | -The infirm vs. scalable network traffic -They can be defeated vs. 0-Day ransomware versions -Fragile analysis vs. big and imbalanced dataset | R-Locker |
| RansomFlare | |||
| Poster | |||
| UNIVEIL | |||
| Talos | |||
| Machine Learning-Based Technology [11,24,25,26,27,28,29,30,31,32] | They apply machine learning algorithms to classify training and testing sets of ransomware and good-ware instances with a hybrid set of static and dynamic traits. Then, generated class models characterize generic and/or unseen ransomware versions with high detection accuracy, low false alarms, and misclassifications | -They can be evaded by adversarial ransomware traits and newly emerged ransomware families -Simi-real testbed and real-mode conditions are needed -Obsolescent detection vs. various ransomware families | EldeRan |
| ShieldFS | |||
| 2entFOX | |||
| GAN | |||
| NetConverse | |||
| RansomWall | |||
| RANDS | |||
| DRTHIS |
| Existing Tools | Method | Machine Learning Algorithm | Lacks |
|---|---|---|---|
| EldeRan [11] | It detected the updates of API calls, registry key and file system operations via a sandbox versus locker-ransomware families | DT |
|
| ShieldFS [30] | It detected some crypto-ransomware families that exploit generic ransomware traits like I/O and low-level file system infections, encrypting file contents, and overwriting the original contents by monitoring file system activity and then updating the threat profile overtime on a realistic environment. | DT |
|
| Net-Converse [26] | It used dynamic traits and six machine learning algorithms to detect 0-Day versions of locker-ransomware versions | LR, DT, BN |
|
| 2entFOX [31] | It detected static and dynamic traits of crypto-ransomware by using graph traversal network | BN |
|
| GAN [32] | It develops a generative adversarial network for detecting versions of locker-ransomware families with a generic set of dynamic traits | NN, NB, RF, SVM |
|
| Ransom-Wall [33] | A multi-layered tool detects 0-Day versions of crypto-ransomware families by developing a generalized model comprised of static and dynamic traits | LR, SVM, NN, RF |
|
| RANDS [34,35] | A hybrid machine learning-based anti-ransomware tool that detects 0-Day versions of both crypto and locker ransomware families by using dynamic traits on Windows platform | HMLC |
|
| DRTHIS [36] | A three-fold machine learner that identifies crypto and locker ransomware versions among malware and good-ware versions using dynamic traits. | NN |
|
| Traits | Type | Ransomware Families | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Crypto-Wall | Win-Lock | Reventon | Crypto-Locker | Archiveus | GpCode | AiDS | RaaS | Cerber | Locky | Crysis | Wanna-Cry | Sopra | Zeus | ||
| Windows API calls | Dynamic | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✖ |
| Windows Cryptographic APIs | Dynamic | ✔ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ | ✖ |
| Registry Key | Dynamic | ✔ | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✖ |
| System File Process | Dynamic | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✖ |
| Directory Actions | Dynamic | ✔ | ✔ | ✖ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ | ✖ | ✔ | ✔ | ✔ | ✔ |
| Application Folders | Dynamic | ✔ | ✔ | ✖ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Control Panel Settings | Dynamic | ✔ | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ |
| System File Locations | Dynamic | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✖ |
| Pay-loaders/Downloaders | Dynamic | ✔ | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ |
| Command and Control Server | Dynamic | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ |
| Windows Volume Shadow (vssadmin.exe and WMIC.exe) | Dynamic | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ |
| File Fingerprint | Dynamic | ✔ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✖ | ✖ |
| Directory Listing Queries | Dynamic | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✖ |
| Windows Safe Mode Booting (bcdedit.exe) | Dynamic | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ |
| File Extensions | Static | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ | ✔ |
| Files Names | Static | ✖ | ✖ | ✖ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ | ✔ |
| Portable Executable Header | Static | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ |
| Embedded Resources | Static | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ |
| Packers | Static | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ |
| Shannon’s Entropy | Static | ✔ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ |
| Cryptors | Static | ✔ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ | ✖ | ✖ | ✖ |
| Portable Executable Signature | Static | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ |
| Embedded Scripts | Static | ✖ | ✔ | ✔ | ✖ | ✖ | ✖ | ✔ | ✔ | ✖ | ✔ | ✖ | ✔ | ✔ | ✔ |
| Fuzzy Hashing | Static | ✔ | ✖ | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ | ✔ | ✖ | ✖ |
| Description | Corpus | |
|---|---|---|
| Number of Valid Ransomware Versions | 35,000 | |
| Number of Malware Versions | 500 | |
| Number of Good-ware Versions | 500 | |
| Data Archives | [40,41,42] | |
| Aggregation Time | 1/1/2019–1/9/2019 | |
| Training Data Corpus | 17,332 | |
| Testing Data Corpus | 17,666 | |
| Ransomware Families | AiDS | 4000 |
| GpCode | 8000 | |
| Archiveus | 1500 | |
| WinLock | 3620 | |
| Reveton | 2400 | |
| CryptoLocker | 1720 | |
| CryptoWall | 3250 | |
| RaaS | 1300 | |
| Cerber | 1535 | |
| Locky | 2000 | |
| Crysis | 1320 | |
| WannaCry | 1300 | |
| Sopra | 1570 | |
| Zeus | 1500 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zuhair, H.; Selamat, A.; Krejcar, O. A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning. Appl. Sci. 2020, 10, 3210. https://doi.org/10.3390/app10093210
Zuhair H, Selamat A, Krejcar O. A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning. Applied Sciences. 2020; 10(9):3210. https://doi.org/10.3390/app10093210
Chicago/Turabian StyleZuhair, Hiba, Ali Selamat, and Ondrej Krejcar. 2020. "A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning" Applied Sciences 10, no. 9: 3210. https://doi.org/10.3390/app10093210
APA StyleZuhair, H., Selamat, A., & Krejcar, O. (2020). A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning. Applied Sciences, 10(9), 3210. https://doi.org/10.3390/app10093210






