1. Introduction
Information protection is an important element of human life, from both a private and a professional standpoint. To protect information that is electronically stored or processed, various methods are used, based on solutions that are not always accepted by all users. Those processes can be a source of electromagnetic emissions correlated with the processed information, which become fully useful in the electromagnetic infiltration process.
In the TEMPEST evaluation process, all digital signals transferred from the communication ports of the tested equipment are considered to be compromising signals, such as PS/2 port connector [
1], USB (Universal Serial Bus ports or peripherals) [
2,
3], RJ45 modular connector [
4], video signals from VGA (Video Graphics Array), DVI (Digital Visual Interface), HDMI (High-Definition Multimedia Interface) and other display ports [
5,
6,
7] or RS232 serial port [
8]. Output devices such as printers [
9,
10,
11,
12] and video projectors [
13] are also being investigated. The video display signal is considered to be the most unsafe in terms of vulnerability to electromagnetic intrusion attacks from all compromising signals that can be emitted by a personal computer. This is also recognized by the TEMPEST procedures [
14], which assign to this type of signal the most restrictive corresponding category as a compromising signal. The successive video frames are similar to each other and, for this reason, the video signal has the attributes of a repetitive signal, which means that it is almost periodic [
15]. This feature can allow a potential attacker to apply the mediation processes that highlight the video signal, reducing the effect of ambient noise in this way.
The effectiveness of the electromagnetic infiltration can be limited in several ways: limiting levels of electromagnetic emissions correlated (having distinctive features) with processed information [
14,
15,
16,
17], a disturbance of existing revealing emissions [
18,
19] or appropriate shaping of the emission source to eliminate features that enable identification e.g., of text data characters [
20,
21,
22].
TEMPEST protection countermeasures now involve hardware modification of Information Technology and Communications (IT&C) equipment by applying shielding measures (shielded housings and shielding window), power and signal filtering, or modifying printed circuit boards in order to minimize the total amount of the equipment electromagnetic radiation and not only those containing information (compromising emanation). This is reflected in the cost of the shielded equipment, which is often 5–8 times higher than the modified commercial equipment. It is true that the security of sensitive information is related to national security issues and must be applied regardless of the costs involved, but maintaining the level of security of this information with reducing costs is the target of the TEMPEST protection measures, which is specified by official documents as the “protection zone model”.
The disturbance of existing revealing emissions does not lower the levels of these emissions. It introduces additional sources of electromagnetic disturbances, some of which can reach significant levels. This solution is not recommended, due to the deliberate introduction of additional sources of electromagnetic emissions into the environment.
Shaping the sources of such emissions is another method that limits the effectiveness of electromagnetic infiltration. This is achieved by changing the colors of the text and the background. An appropriate selection of color pairs may reduce the effectiveness of the source of unwanted emissions [
15,
16]. However, this method is not universal from the point of view of application in video standards. A certain properly selected text and background color pairs can be effective for the analogue VGA standard, but, in the case of the digital DVI (HDMI) standard, the efficiency of a color pair may not be so obvious [
16].
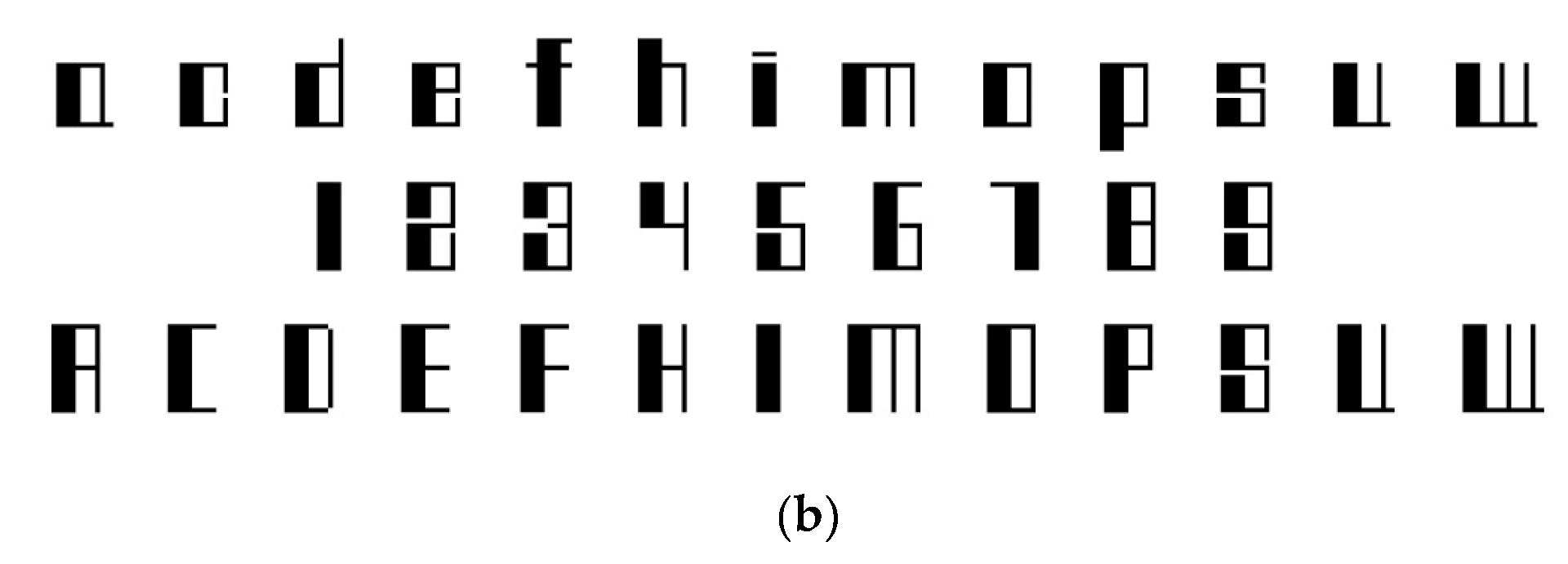
There is a new proposed method based on computer fonts with specially designed shapes (
Figure 1). Font characters shape the electrical signal of each video standard, which is a potential source of emission.
Fonts do not reduce electromagnetic emissions. However, font character shapes without characteristic elements create a high level of similarity of the revealing emissions in the time domain. By using these special fonts, a potential attacker will manage to restore the image by receiving the compromised emanation (CE) generated by the IT&C equipment, but will not be able to extract information from the restored image which represents the target of the TEMPEST domain.
Another important issue is the practical advantages of the method. This assessment is carried out using a special receiver dedicated to the measurement of electromagnetic revealing emissions. The level of these electromagnetic emissions is very low, and the bandwidth of the signals, especially digital ones, is very wide. Therefore, the sensitivity of the measuring receiver must be very high, and the available measurement bands very wide, up to 500 MHz [
23,
24,
25]. The second method of verifying the graphic sources of revealing emissions is visual analysis. This analysis is based on graphic images that are obtained as a result of the rasterization process of recorded revealing emissions.
The authors are analysing the possibility of data recovery processed by electronic devices by a possible intruder that does not have access to the location in which the equipment is placed, just from spurious electromagnetic emissions. Usually such locations are secured ones, placed under guard, and, if such an intruder appears, they cannot have bulky equipment and suspicious behaviour. They cannot carry a computer or laptop and wait there while it still performs numerical algorithms to identify the data from electromagnetic emissions. That is why the visual method is used, and, as with any method based on human perception, quantitative numerical indicators do not apply. However, many test subjects have been used, and the conclusions regarding the degree of similarity between different letters and numbers written with the secure symmetrical and secure asymmetrical fonts are presented in section 4 [
20]. It has been proven that the results obtained based on visual method correspond to the ones that used numerical algorithms for similarity assessment and character recognition algorithms. Moreover, the visual method is widely used in such applications and also imposed by military standards, being the first step of the TEMPEST measurement procedures for the video display signal.
The practical advantages of the new computer fonts in terms of electromagnetic protection of processed text data were carried out by two independent institutions—Military Communication Institute (MCI) and Special Telecommunications Services (STS)—with extensive experience in the study and classification of electromagnetic emissions. This allowed for a reliable evaluation of the fonts and independent method verification.
2. Methods
The verification of the new set of fonts based on visual analysis was carried out in two measurement environments: an anechoic chamber of the laboratory of the MCI and an anechoic chamber of STS. Each laboratory uses a different measuring receiver, which was the purpose of the evaluation of new fonts in the secure processing of text information.
The TEMPEST measurement procedures involve two successive steps: the first proves the existence of the CE on a certain frequency (the image recovery when considering the video signal as CE) and the second is the evaluation of the CE level. The level of the emanation is compared with the limits stipulated by the TEMPEST procedures for the classification of the equipment in a certain risk category for information security. Therefore, the possibility of image recovery does not automatically mean that equipment under test (EUT) fails the test.
2.1. Military Communication Institute
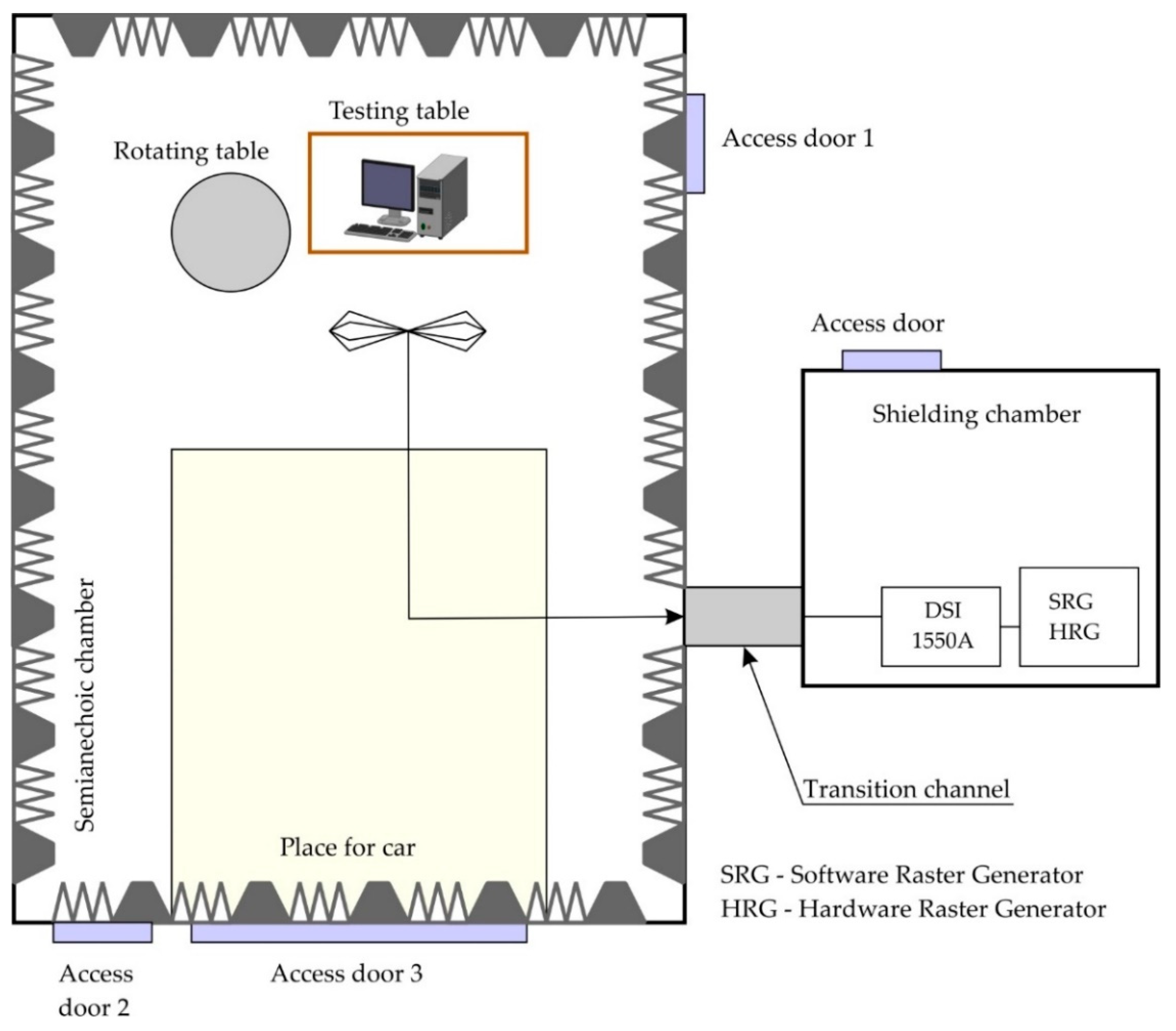
The tests were carried out inside an anechoic chamber of electromagnetic compatibility laboratory of MCI (
Figure 2). A Tempest Test System DSI 1550A receiver and a special set of antennas were used for these tests. The secure fonts were installed on a typical desktop computer with a 24” monitor (1024 × 768, 60 Hz). The monitor was connected to the main unit of the computer by DVI and VGA standard interfaces. The sizes of fonts were equal to 36 points and 24 points. The distance between the antenna and the monitor was equal to 1 m (the distance according to the MIL-STD-461E (F and G)). An electromagnetic emission was measured on a frequency of 860 MHz (
BW = 50 MHz) [
26].
2.2. Special Telecommunications Services
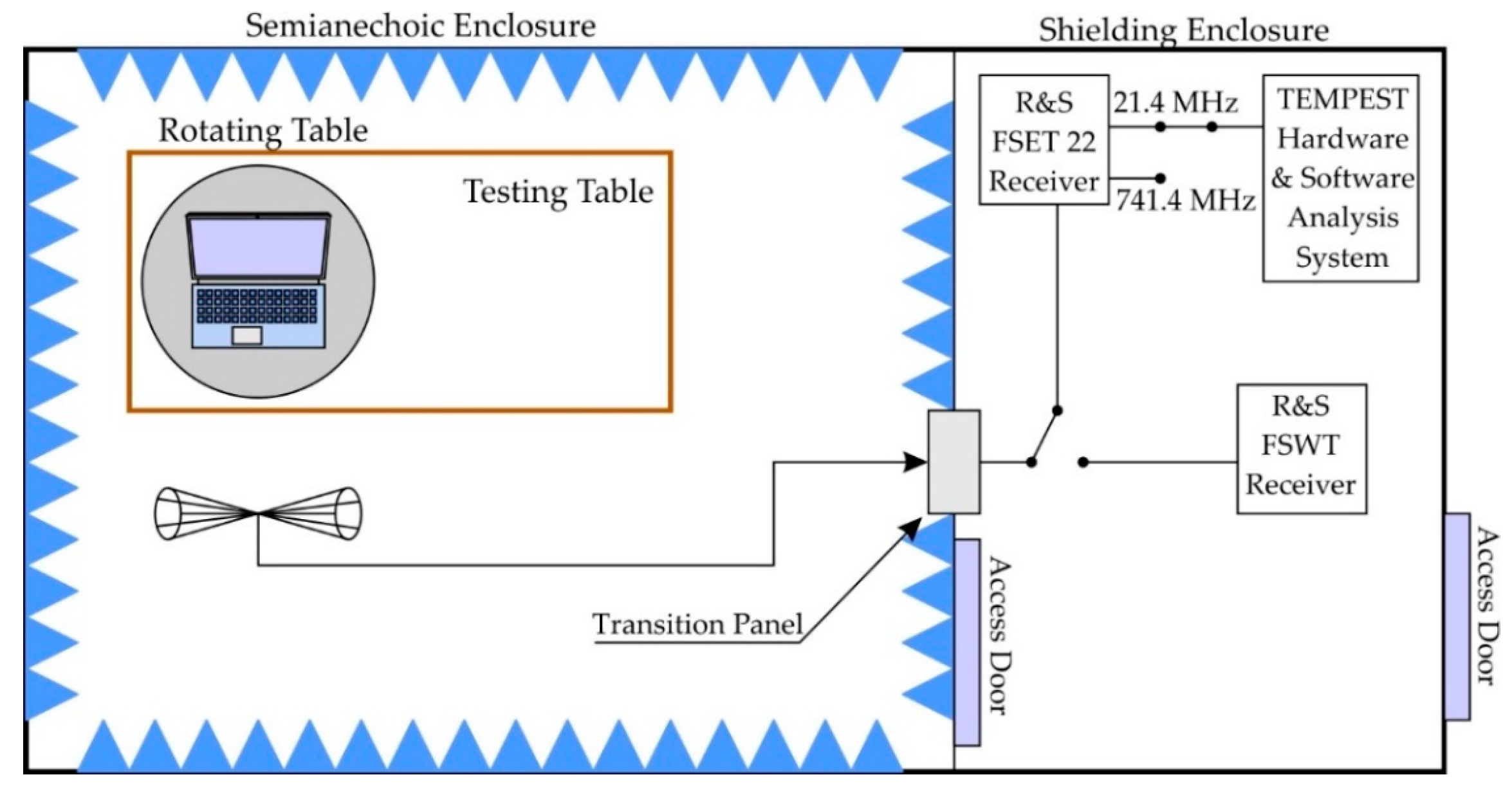
The measurements were performed in a TEMPEST laboratory consisting of two shielded enclosures that have a common wall, as illustrated in
Figure 3. One of the enclosures is a semi-anechoic chamber (there is no radio absorbent material on the floor) and is actually the testing room. The equipment is positioned in accordance to the American EMC standard, MIL-STD-461E. This standard has many similarities, but also some differences with the test configuration specified by the TEMPEST procedures, but in the end it has the closest configuration of all EMC standards. As TEMPEST procedures are classified, information cannot be disclosed, so we will consider the configuration of this EMC standard as a reference.
The tests were performed with a Fujitsu Siemens laptop, Lifebook C110. The chosen equipment is an older generation laptop and was used with the 220V mains power supply unit. The laptop’s electric charger is usually an electromagnetic noise generator that makes the process of video image recovery more difficult to fulfill. Very often, the emissions of these electric chargers are in the frequency range of up to about 500 MHz. For this reason we selected a much higher recovery frequency, respectively 910 MHz.
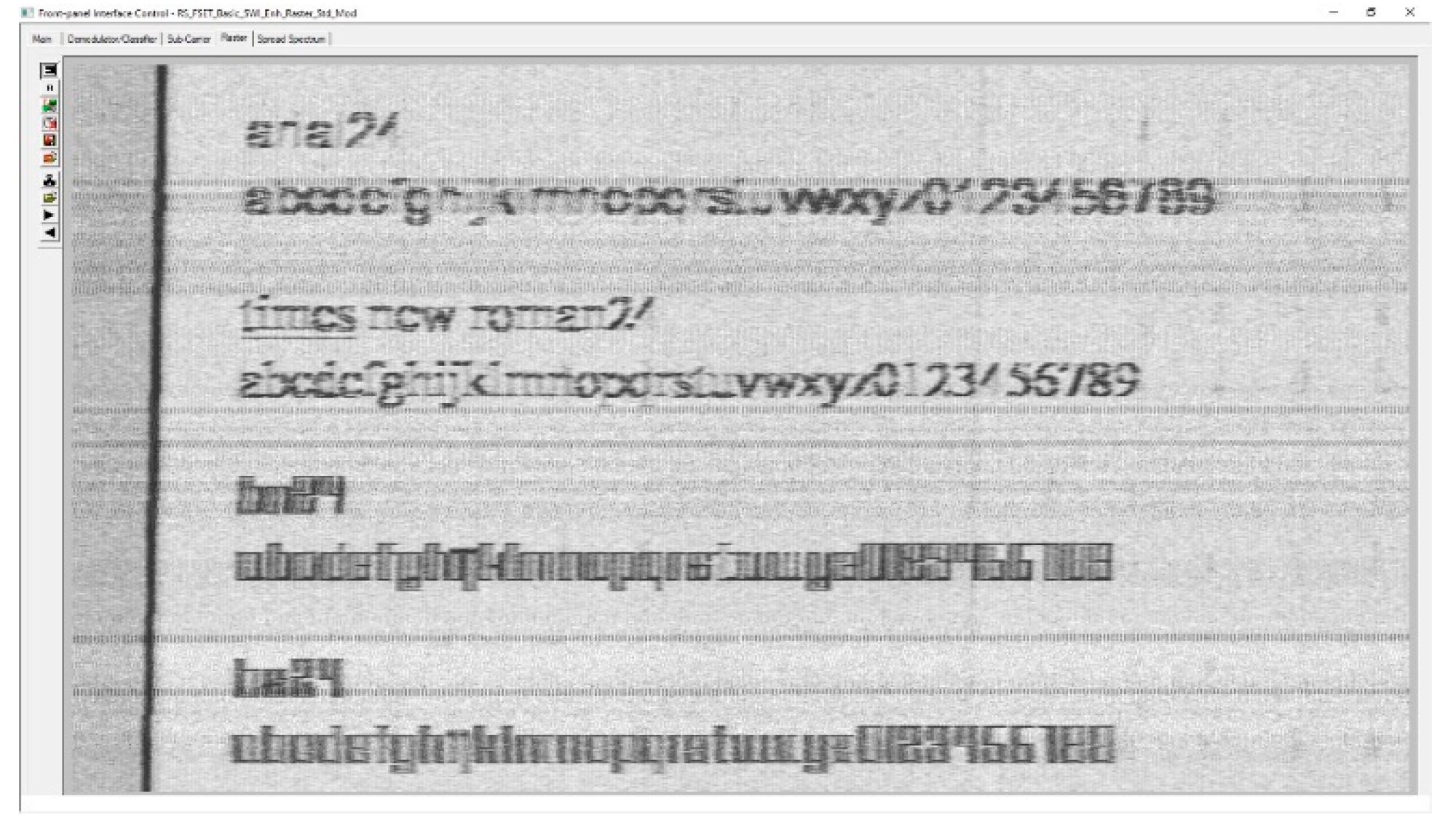
It does not matter which EUT is chosen for testing, but to do comparative tests, we also used, besides the analyzed fonts, 2 other common fonts, namely Times New Roman and Arial.
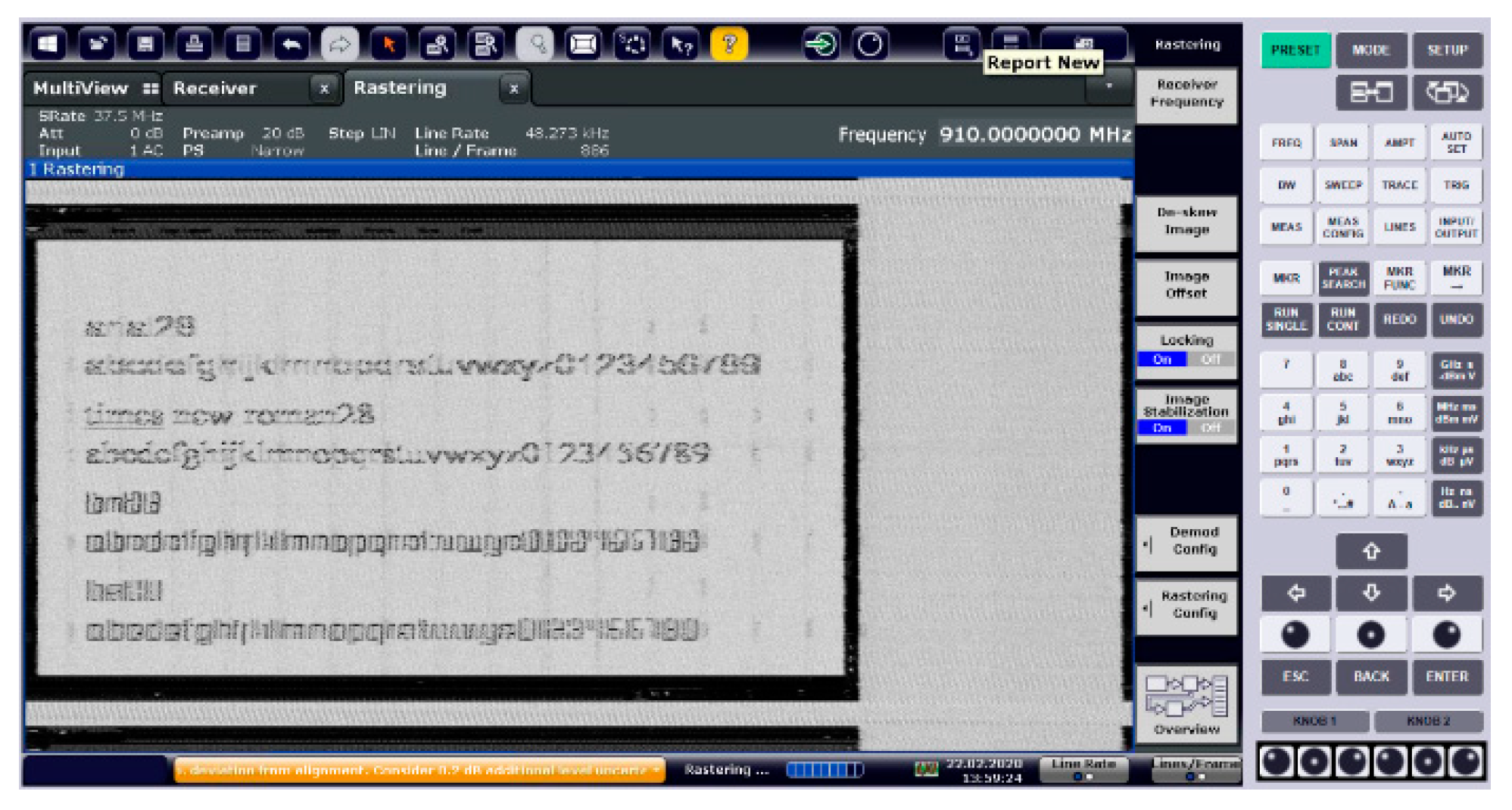
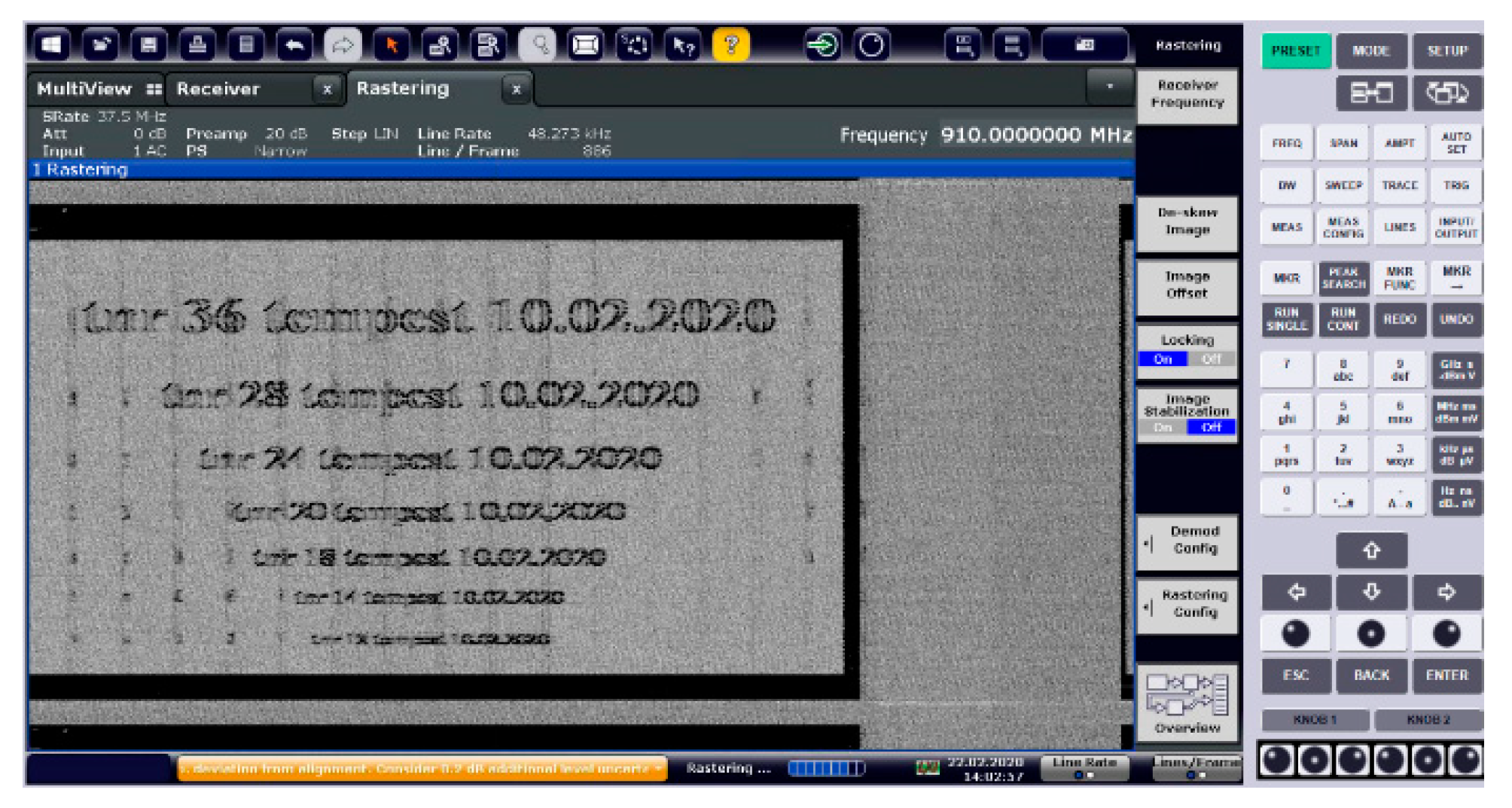
It should be mentioned that, after establishing the reception and the video recovery parameters, only the images displayed by the EUT have been modified, while all the reception parameters and the analysis of the compromising signal remained unchanged until the end of the tests performed. We used a Rohde & Schwarz (R&S) FSET 22 test receiver and specialized TEMPEST analysis software. Unfortunately, we had to crop from the analyzed images the information that includes the video recovery parameters, because it represents sensitive information that we are not allowed to publish. The test receiver parameters are: 10 MHz Resolution Bandwidth (RBW), 50 ms sweep time, SPAN 0 working mode, and narrow filter pre-selector, and internal preamp amplification was 10 dB. The display resolution of the EUT is 1024 × 768 with the refresh rate of 60 Hz. Thus, all the time parameters of the displayed video signal can be found in the VESA Coordinated Video Timings (CVT) Standard, version 1.2 (February 2013): vertical refresh of approximately 48.363 kHz (most important), pixel frequency of 65.0 MHz, front and back porches (horizontally and vertically), the whole line and whole frame duration.
Another interesting discussion would be the size of the font that would be most suitable for use in our tests. Usually documents are edited with size 12, while PowerPoint presentations use size 28 or even larger to be visible to all participants. So, we used the following dimensions: 36, 28, 24, 20, 18, 14 and 12.
4. Discussion
In the equipment TEMPEST evaluation, mainly upper case letters are used, because it facilitates the video recovery process, which represents the “worst case scenario” mentioned repeatedly in the TEMPEST procedures. Thus, the video recovery process for the font Arial was repeated, but this time with the use of the upper case letters and numbers, as illustrated in
Figure 12. We performed the tests for secure asymmetrical font again and the results are shown in
Figure 13.
Color coding in RGB format (red, green and blue) is done by combining in some proportions these 3 primary colors, with values between 0 and 255. Thus, the blue color is coded for example [0,0,255] or “0000FF” in hexadecimal format (HEX) while black is represented by [0,0,0] or "000000" (HEX) and the white color of [255,255,255] or "FFFFFF" (HEX). The inverted video option practically means the reversal of the white color with the black, meaning the consideration of the values [255,255,255] for black and [0,0,0], for white respectively. So it does not represent an additional processing of the video CE signal, but it is only the option for a TEMPEST engineer regarding the visualization of the restored image. In the opinion of our specialists, the images restored with the "reverse video" option enabled are more intelligible and less tiring for the eyes. Due to the fact that the TEMPEST specialist spends several hours each working day with such images displayed, this technical aspect related to the working mode is very important to them. The restored images illustrated in
Figure 6,
Figure 7,
Figure 8,
Figure 9,
Figure 10,
Figure 11,
Figure 12 and
Figure 13 were performed with the “reverse video” option enabled. Without activating this setting, the image shown in
Figure 14 is obtained.
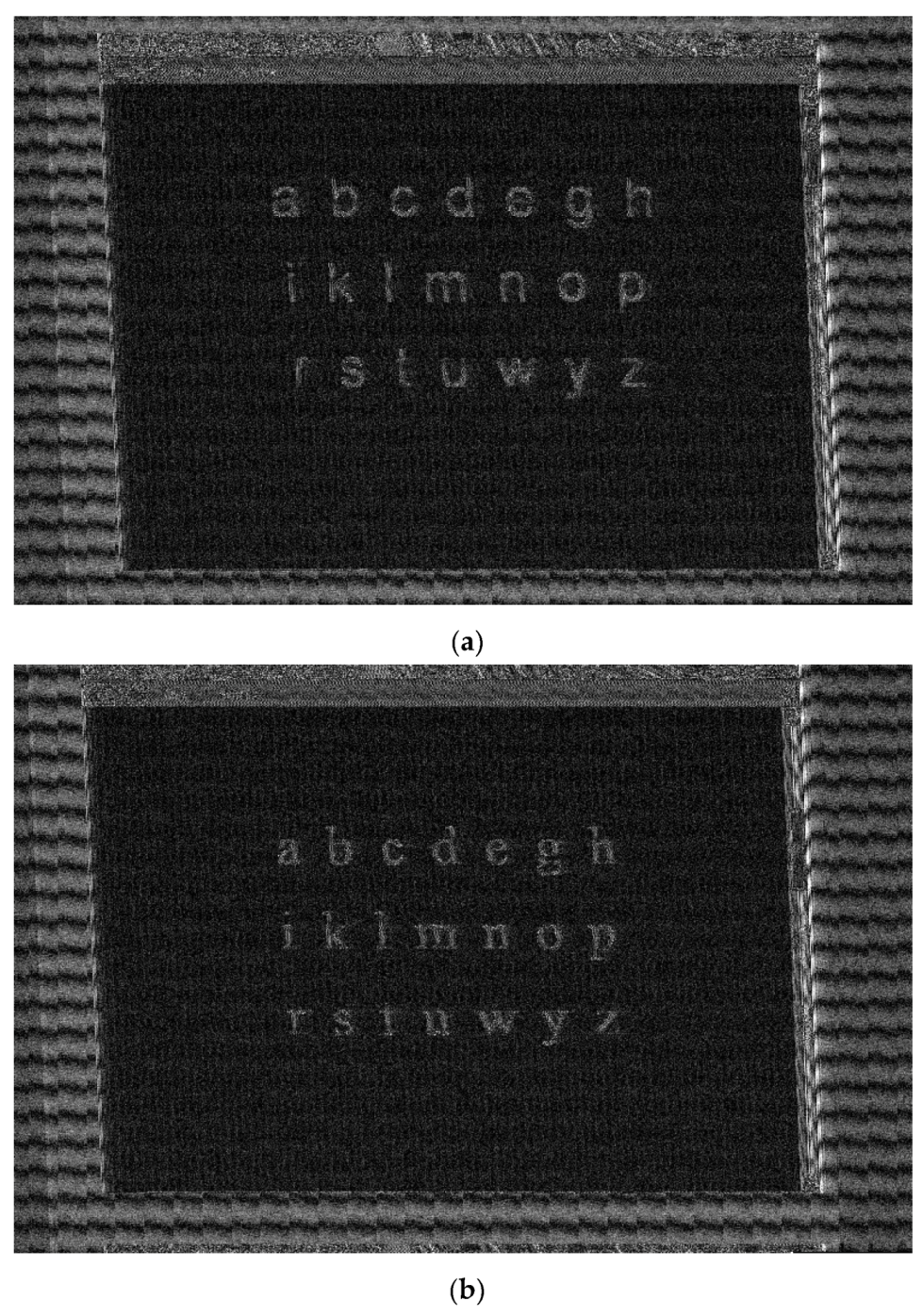
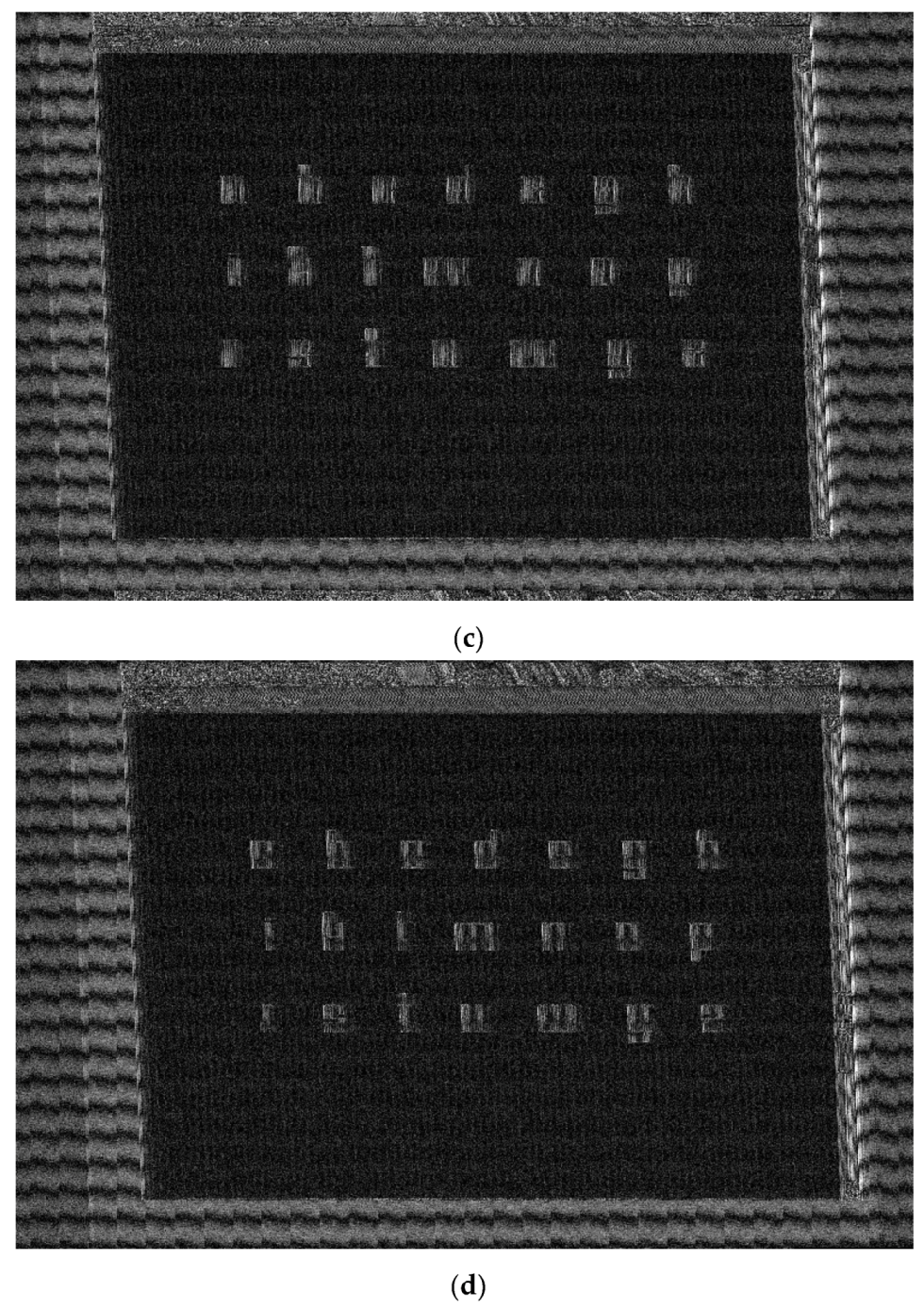
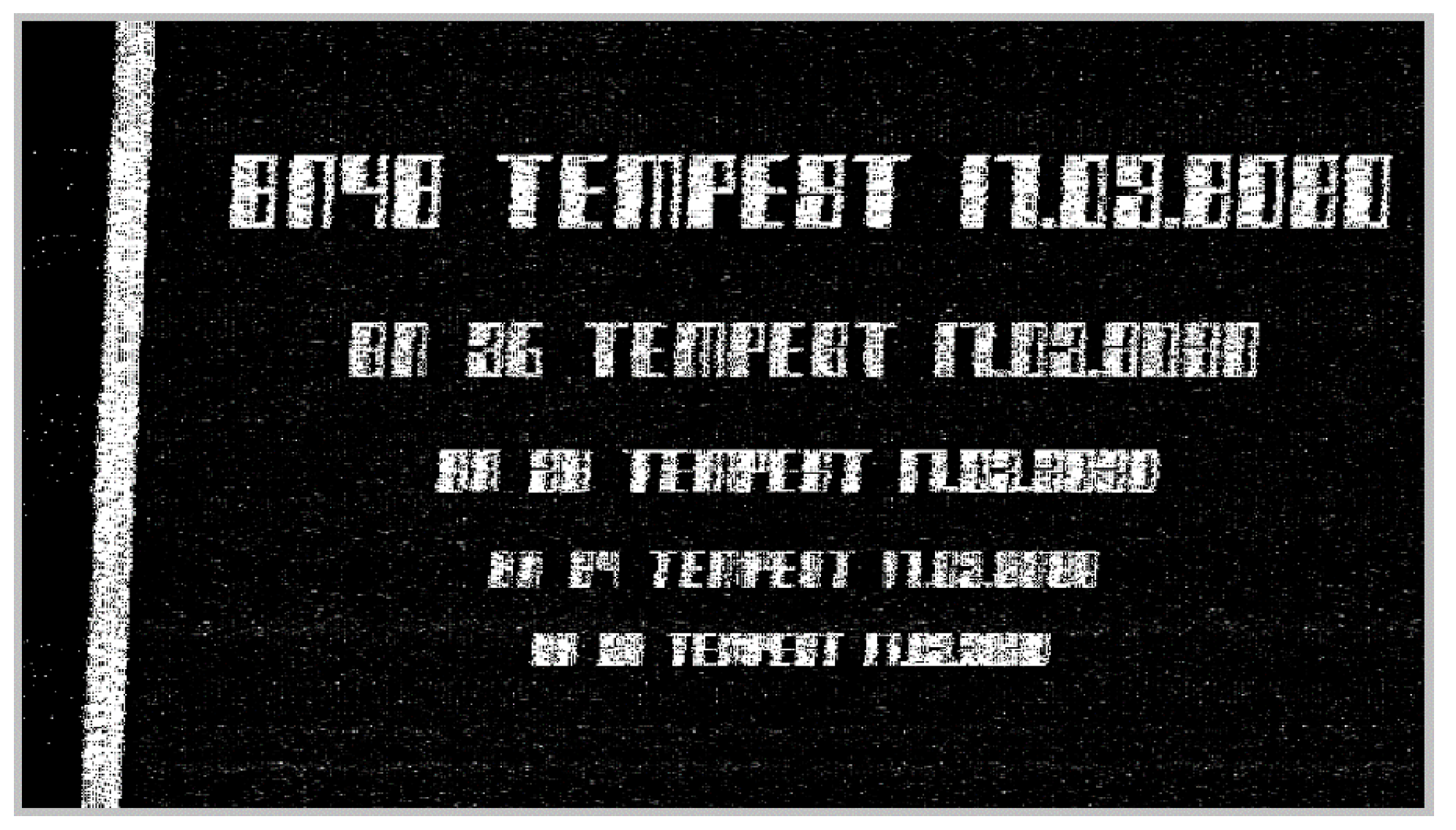
We can consider that the text is intelligible for the font size of 36, 28 and 24 and not for all the letters, this statement being valid only for size 36 in case of Arabic numerals, and even at this size, the number 2 can be easily confused with the number 8. However, it can be observed that the date of the measurements cannot be understood for the secure asymmetrical font with a size less than 28 and for the secure symmetrical font with a size less than 24. We consider that for the font size 12, no alphanumeric character is intelligible, regardless of the font considered, secure asymmetrical or secure symmetrical. It is also true that the tested fonts are difficult to track even in the Word Office editing environment and that the human operator needs an adaptation period to use these fonts.
In conclusion, we consider that the fonts are efficient in terms of resistance to the video recovery process and that the secure asymmetrical font is more efficient than the secure symmetrical one, although the characters of the secure asymmetrical font have been restored with a better contrast. The documents edited with size 12 are impossible to recover if any of these fonts would be used.
Next, we considered that dimension 24 represents the intelligibility limit for the two TEMPEST fonts analyzed. Thus, we continued to use as a test video signal a page with size 24, corresponding to all four previously used fonts. The image recovery results corresponding to this video signal can be seen in
Figure 15.
Here, we can identify all the numbers for the secure symmetrical font and partially for the secure asymmetrical. The most readable characters are ‘b’, ‘g’, ‘k’, ‘p’, ‘q’, ‘s’ and ‘t’, while the numbers 2, 3 and 4 can be identified, even for the secure asymmetrical font. The characters ‘a’, ‘c’, ‘n’, ‘o’, ‘u’ and ‘v’ can be easily confused with each other (they have an almost identical shape in the restored image) and also the letters ‘g’ and ‘y’.
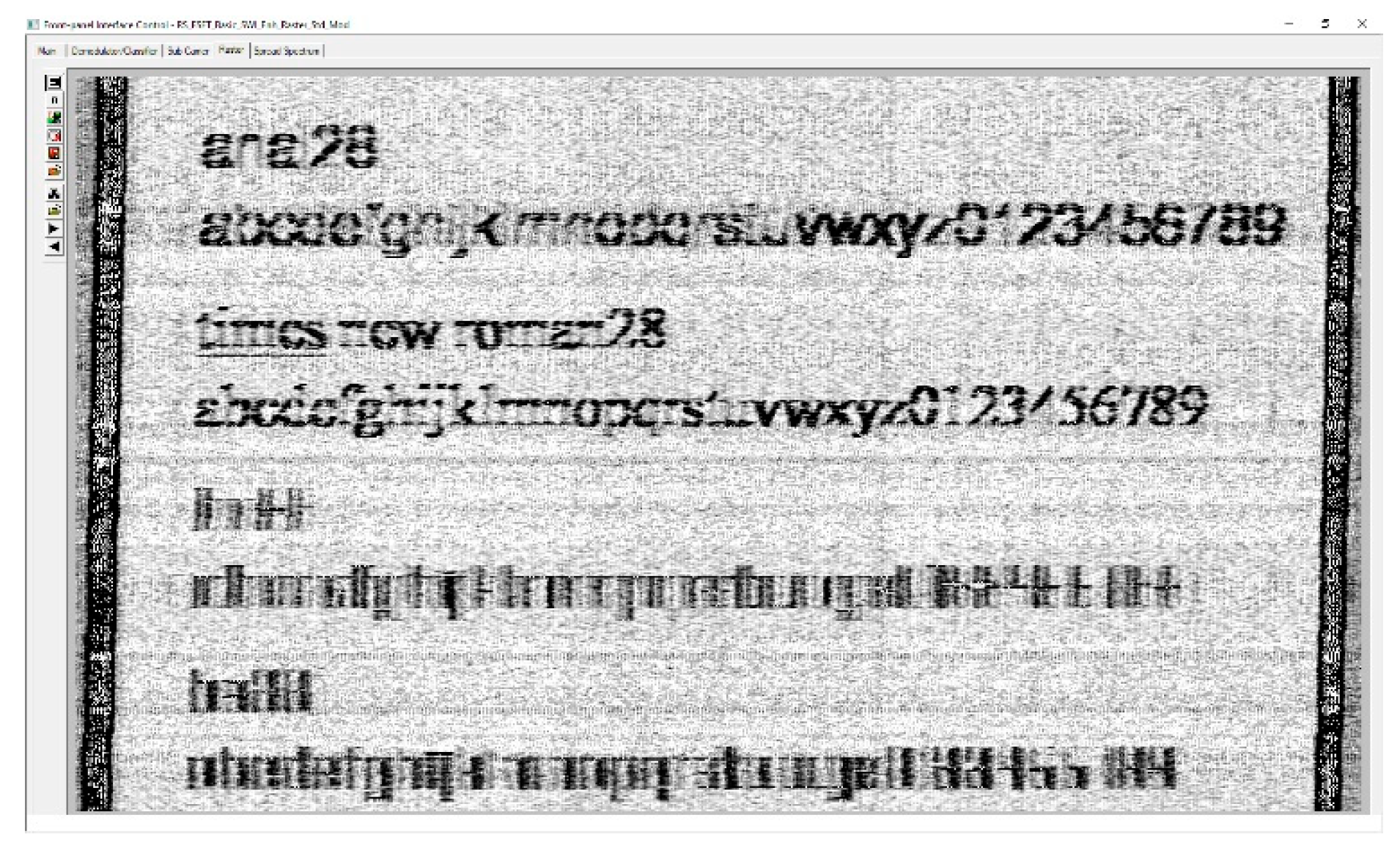
Next, we increased the font size to see if the quality of the restored image is improved and the results are not positive in this sense (the text is not intelligible), as can be seen in
Figure 16.
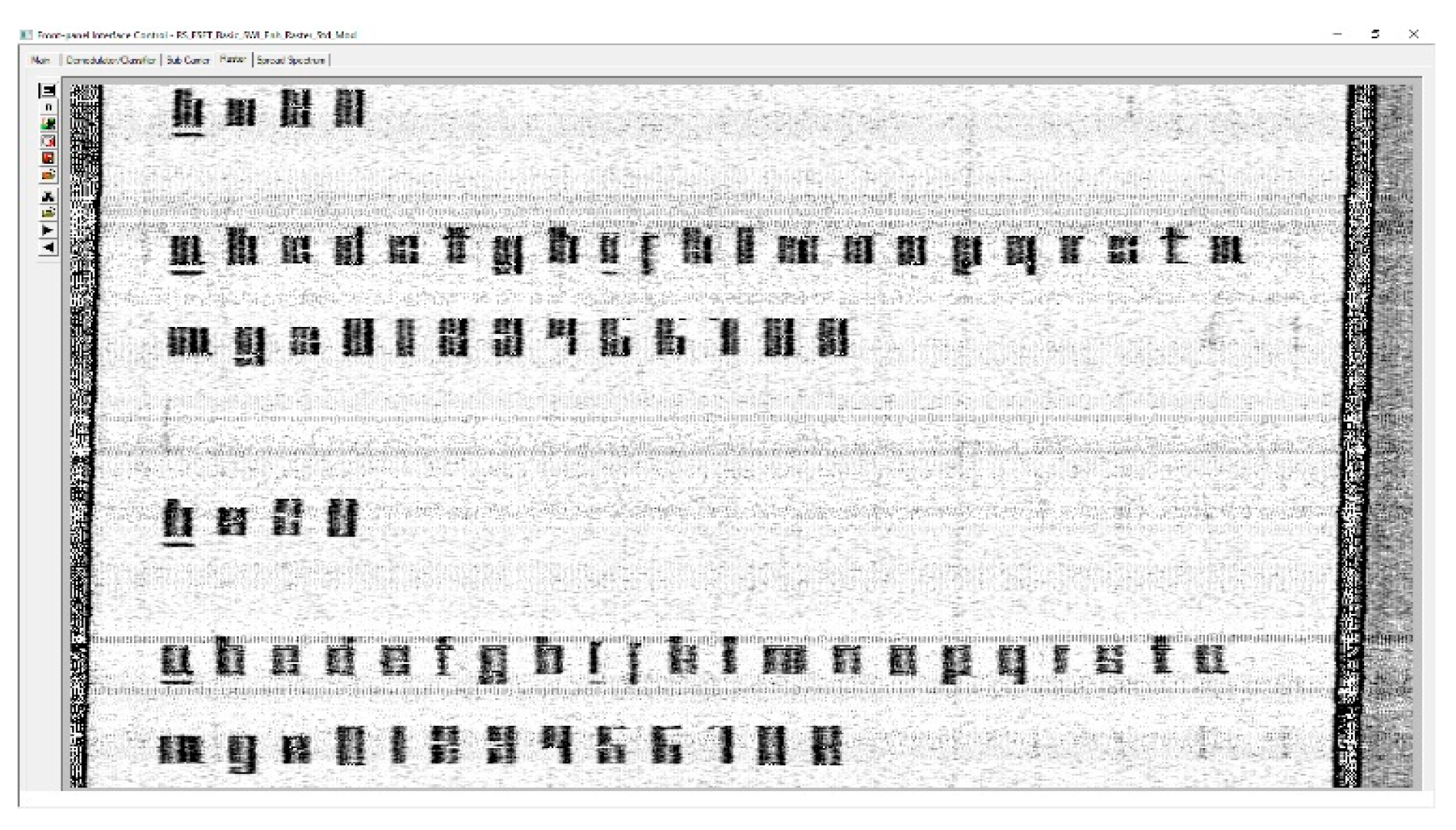
For intelligibility reasons, we have introduced blank spaces between alphanumeric characters written with secure asymmetrical and secure symmetrical fonts. The result can be seen in
Figure 17. In this case, we consider that the letters ‘b’, ‘c’, ‘d’, ‘f’, ‘p’, ‘q’, ‘r’, ‘s’ and ‘t’ can be identified for the secure asymmetrical font and the letters ‘b’, ‘f’, ‘m’, ‘p’, ‘q’, ‘r’, ‘s’ and ‘t’ for the secure symmetrical font.
The numbers from 1 to 7 can be identified for the secure symmetrical font, while the secure asymmetrical font makes it impossible to identify the numbers 5 and 6.
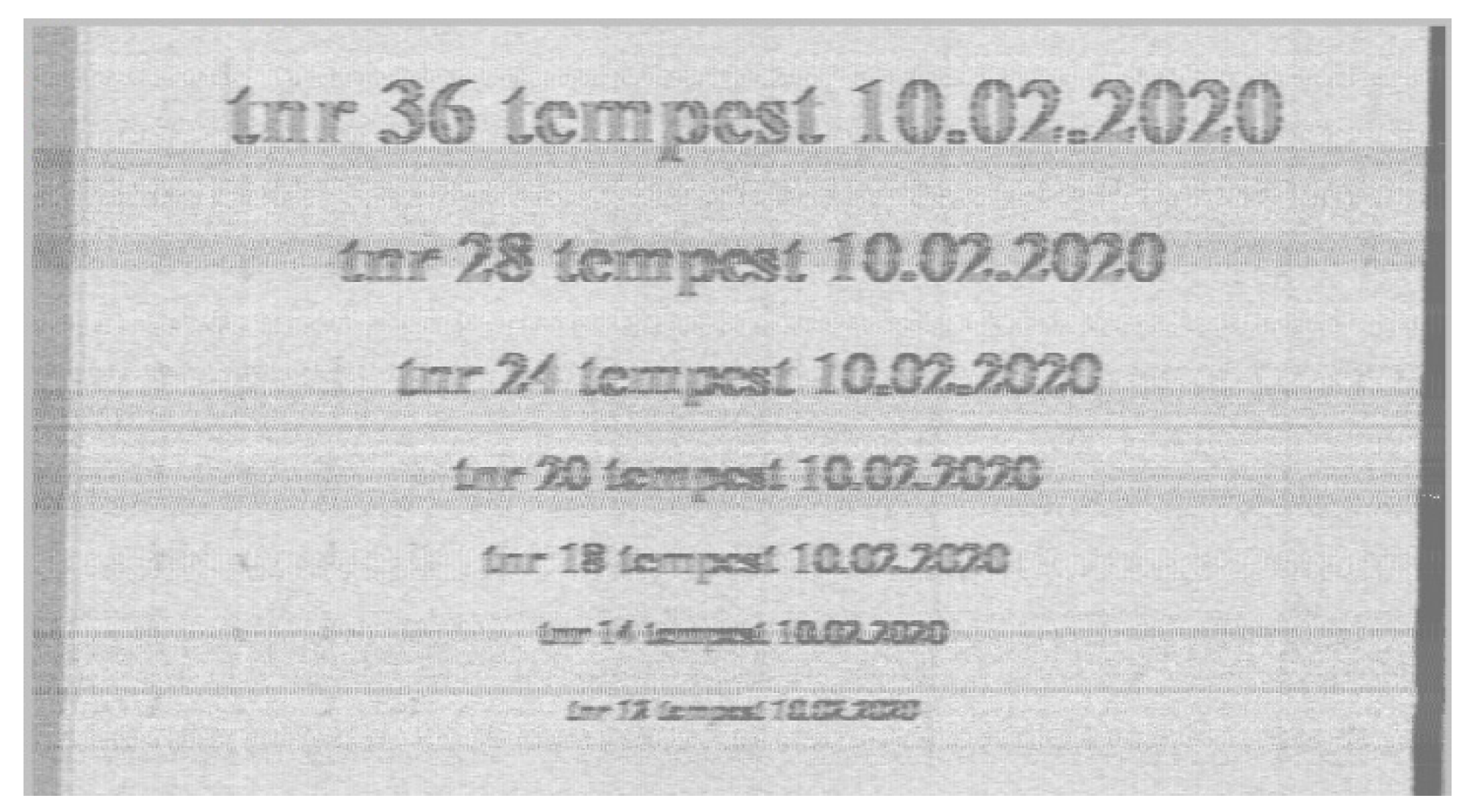
As we mentioned before, we can conclude that secure asymmetrical font is safer than secure symmetrical and for this reason we repeated the test in which all the alphanumeric characters were displayed with the fonts Arial, Times New Roman (TNR) and secure asymmetrical with dimension 28 (we skipped over dimension 24), as illustrated in
Figure 18.
We can observe in
Figure 18 that the fonts Arial and Times New Roman are 100% intelligible, while the secure asymmetrical font is not intelligible at all. We have further introduced blank spaces between alphanumeric characters to increase the degree of intelligibility, as illustrated in
Figure 19.
Our attempt was partially successful, meaning that the letters ‘C’, ‘E’, ‘F’, ‘G’, ‘L’, ‘P’ and ‘T’ are 30% intelligible, as well as the numbers ‘5’, ‘6’ and ‘7’. Next, we wrote the alphanumeric characters with bold and the result can be seen in
Figure 20. As we can see, the level of intelligibility for the secure asymmetrical font does not increase compared to
Figure 19.
Since we were not successful in understanding the information written with secure asymmetrical font contained in the video restorations illustrated above, we increased the font to the maximum possible size from our point of view, respectively size 72. We have also left the font size 36 and 28 for comparison reasons and the result is shown in
Figure 21.
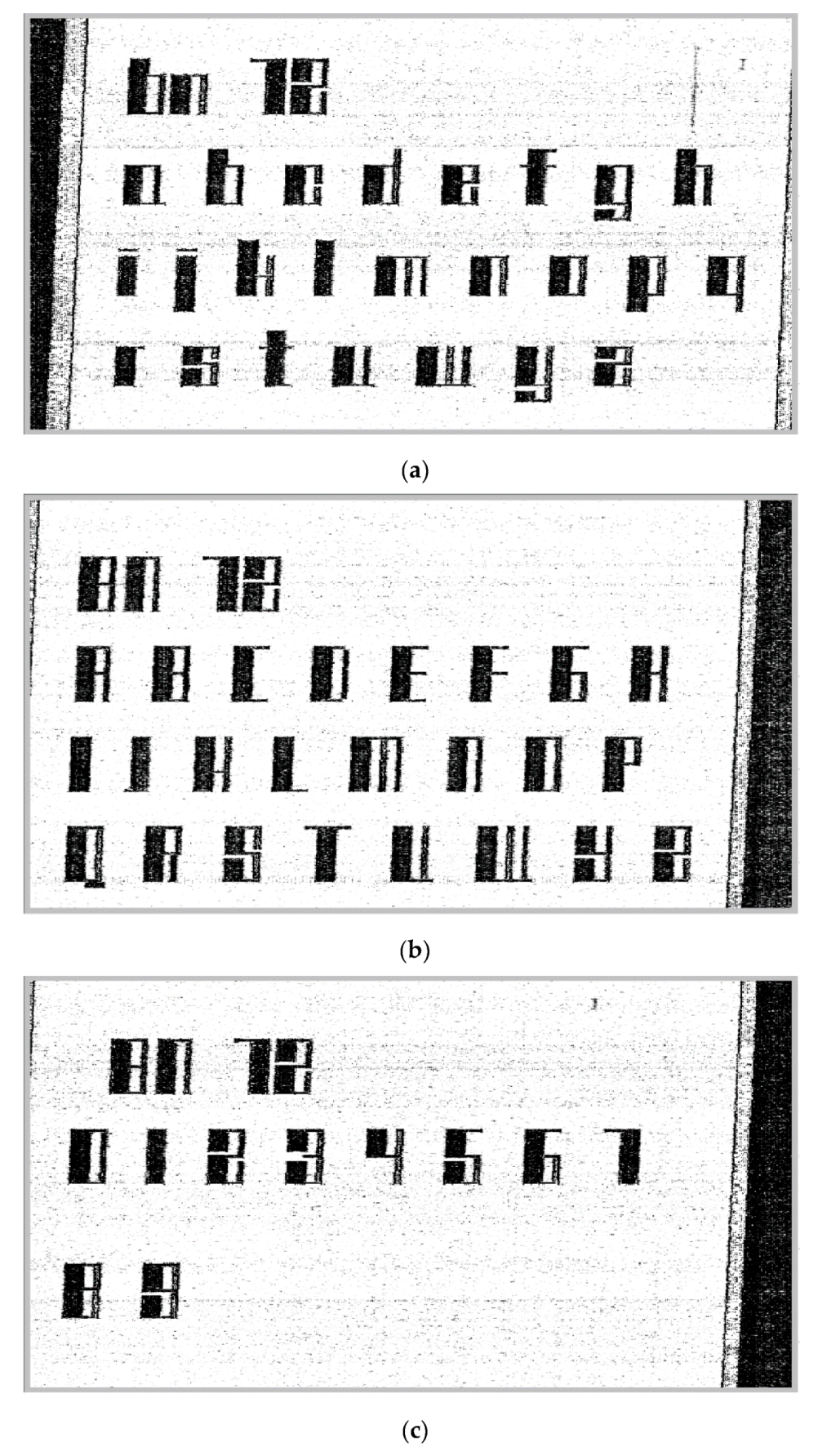
In order to analyze the characteristics of each alphanumeric character of the secure asymmetrical font, we continued the tests only with the display of the size 72 characters and numbers, both for upper and lower case letters, as can be seen in
Figure 22a–c.
From
Figure 22, we can observe that certain alphanumeric characters have similar shape characteristics and can be very easily confused between each other if they are not even identical:
lower case letters that have similar shape (
Figure 22a)
the letters ‘a’, ‘c’ and ‘o’;
the letters ‘I’, ‘j’ and ‘r’;
the letters ‘l’ and ‘t’;
the letters ‘g’ and ‘y’.
upper case letters that have similar shape (
Figure 22b)
the numerical characters can be differentiated between each other, as we can see in
Figure 22c.
Additionally, some numbers can be easily confused with the capital letters as follows: ‘2’ with ‘Z’, ‘1’ with ‘I’ and ‘8’ with ‘B’.
Appropriate tests were carried out for VGA standard. The standard is still very popular in classified systems, because it has a higher resistance to electromagnetic infiltration than the DVI standard. Analyzing
Figure 23 and the previous Figures, it can be observed that the new solution in form of secure fonts is a universal one. The new approach could be effective for both the analogue and the digital video standards.
5. Conclusions
This article presents the results of research and analysis of the possibilities of using secure fonts (secure symmetrical and secure asymmetrical) in the protection of processed text data against electromagnetic infiltration. The analyses were based on the visual method as the main method in the classification process of revealing emissions.
The presented secure fonts are a new and evolving method that can support the protection of text data against electromagnetic eavesdropping. Any new solution that can decide on information security must be subject to verification. The best approach in this case is to assess the effectiveness of the method by independent institutions, which also have various measuring devices. Thus, it is possible to carry out independent analyses, and their results can fully confirm or contradict the suitability of the methods in the area of application under consideration.
The fonts presented in this paper can be applied as a security measure against electromagnetic compromising emissions, by applying the security policies that have to be applied to the computer and communication systems.
The tests of secure fonts were carried out at two independent institutions: Military Communications Institute (Poland) and Special Telecommunications Services (Romania). These institutions used various receiving systems (Military Communications Institute: Tempest Test System DSI 1550A; Special Telecommunications Services: Rohde&Schwarz FSET22 and Rohde&Schwarz FSWT), which additionally confirmed the effectiveness of the new proposed method. The tests were carried out in anechoic chambers. The source of unwanted emissions was a typical stationary computer set (in case of MCI) and a portable computer (in case of STS). In each case, revealing emissions were detected, which were registered and rasterized. The images obtained in this way showed the superiority of the secure fonts over traditional ones in the field of protection of text information against electromagnetic penetration. This applies to cases when the font character size was not larger than 24 points. Character recognition is possible for larger sizes. For traditional fonts, the text was readable for virtually any size of characters.
The conclusions are also true for analogue graphic standard. In
Figure 23, each considered font is presented. The size of characters was equal to 14 points and the text written by using secure fonts is very difficult to read.
The presented method of using secure fonts in the protection of text data against electromagnetic infiltration will still be developed in the future. The fonts must be fully usable, i.e., contain the required characters for the full editing of text documents.
The main originality of the paper stands in the use of the secure symmetrical and secure asymmetrical sets of characters and numbers that were patented by the Polish Office Pattern in the form of the Industrial Design (No. 24487) and Patent (No. 231691). We propose the use of these fonts to be introduced as one of the official TEMPEST countermeasures in the classified NATO documents, that impose the regulations of the activities involved in this technical field and which represent national security measures for the IT equipment of each Member State (NATO and EU).Their security have been tested by the MCI, Poland, in their laboratory, but here it is the first time when they are also checked in STS, Romania, in an independent laboratory with a different setup and test equipment. Since in the two testing environments there have been obtained similar results, that asses the fact that the secure symmetrical and secure asymmetrical sets of characters and numbers are less vulnerable to interception through revealing electromagnetic emissions. We consider this to be the beginning of a long process of EU and/or NATO endorsement of this TEMPEST protection countermeasure.