A Study on the Concept of Using Efficient Lightweight Hash Chain to Improve Authentication in VMF Military Standard
Abstract
1. Introduction
1.1. Limitations of the Authentication Process within the Existing VMF Military Standard and Importance
1.2. Security Requirements for Enhancing VMF Authentication and Research Contribution
- The feasibility of implementing a lightweight authentication and integration scheme to improve the existing VMF terminal authentication, such as a hash chain, must be analyzed. The network configuration in CNRs with hash chain-based authentication schemes must be similar to that of the dynamic military ad hoc network-based mobile ad hoc network (MANET) and vehicle ad hoc network (VANET) in the cell planning area.
- Cryptographic hash chain-based authentication and transmission integrity approaches must be considered. Interoperability within the next-generation NCW system, and technical adaptability and continuity in CNR networks with TDL, should also be ensured, and there should not be any deviations from the specifications of the existing VMF military standard.
- Rather than simply assembling the conceptual technology suggested by previous hash chain-based studies, a comparative analysis based on the pros and cons, differences, and limitations of each study should be considered to suit VMF-based CNR networks.
- Active security requirements that consider various military network scenarios must be established. Examples include a hash chain-based authentication, including a time-based one-time password (T-OTP) keyless point, low latency and transaction, robustness to external and internal auth attacks, a specialization of various FBCB2-based All-IP CNR network types, the introduction of re-authentication and revocation steps in the authentication scheme, and deep interoperability. Functional support and availability for rapidly changing battlefield environments and secure lightweight communication for covert activities are also required.
1.3. Paper Organization
2. Background and Related Studies
2.1. VMF Authentication Improvements Based on MIL-STD-2045-47001
- Variability—Variability minimizes message transmission and processing time by dynamically selecting only required real-time tactical messages and information when performing various operations in a limited resources-based network;
- Bit-coded transmission—Bit-coded transmission subdivides the transmission unit of a tactical message containing military operation information into bit and octet. It can maximize the transmission efficiency of the operational information and tactical data and ensure integrity;
- Applicability of multiple layers—The VMF standard is independent of arbitrary network structures applied in various types of military tactical networks. The MIL-STD-188-220 standard was applied for the physical and link layers, and the MIL-STD-6017 and MIL-STD-2045-47001 standards were applied in the application layer based on CNR networks. Therefore, the multi-layer applicability enables a configuration for the independence of the form of military tactical network and the handling of each squad’s platooning behavior and related networks;
- Integration and interoperability—The integration of VMF is an essential feature in the design, development, testing, certification, and continuous operation of the automated tactical data system (that is, it satisfies the necessary requirements for promptly transmitting command and control information through joint boundaries). In addition, an integration is required to exchange tactical data and situation awareness information between heterogeneous weapon systems, and to exchange the command system within the allied operation in real-time through an interlocking of the joint tactical data link system (JTDLS). Currently, this is being applied, with a focus on FBCB2-based platooning networks in cell planning areas and mosaic warfare.
- Weak authentication process by SHA-1 cryptographic hash function: In the existing VMF military standard, the SHA-1-based DSA authentication and modification detection process is performed according to the SPI setting in a dynamic limited CNR network without additional encryption. However, SHA-1 currently has theoretical collision vulnerability and exploits a practical proof of concept (PoC). Thus, to protect confidential military information from leakage and theft in a tactical CNR network under the VMF standard, cryptographic hash-based authentication algorithms (e.g., SHA-2, SHA-3, and LSH of Korean cryptographic hash standard) that are more robust than SHA-1 are urgently required. In addition, although the SPI setting is immediately applied, it is only assumed that authentication in the current VMF-based CNR networks is safe from the perspective of the closed military network. Therefore, it is difficult to protect consistent security in CNR networks from parameter tampering because no separate encryption process in the modification detection and authentication scheme is applied (RSA public encryption may be applied in a separate protocol header area for tactical message encryption, but this may cause additional overhead on network performance and calculation).
- Lack of factor robustness: The existing VMF standard includes variables from a rapidly changing battlefield environment (e.g., information loss from environmental changes, latency, jitter, and authentication delay), enemy types (e.g., active and passive internal and external attackers and masqueraders), and operational environments (e.g., bandwidth, energy, frequency, squad, and resources by limited CNRs) that are not well defined. Therefore, it is necessary to introduce additional requirements and establish parameter-based measures.
- Undefined re-authentication and revocation scheme: The existing VMF standard does not suggest a continuous authentication scheme when it is necessary to re-establish the reliability of the participating nodes because it takes a certain amount of time after the initial authentication for the operation of the squad to be completed. In addition, processes related to authentication rejection and exclusion as well as the elimination of hostilities are not considered. Therefore, to support a consistent authentication system in a rapidly changing VMF-based CNR network, definitions of re-authentication and revocation schemes for all nodes are urgently required.
- Non-existent exception process: The existing VMF standard does not provide any method for the detection, tolerance, and attenuation of node malfunctioning caused by dynamic changes in the network or enemy nodes corrupting operational data and stealing confidential information. Therefore, it is necessary to establish a variety of exception handling methods to satisfy the unique information exchange demand in the battlefield, and support both functional and structural stability. This can also be related to the following challenges: low speed and low bandwidth in real-time VMF-based CNR, the deployment of military base stations for constructing the cell planning area, guaranteeing the availability of authentication for low-spec networks, and the network delay and tolerance related to the establishment of the initial FBCB2-based CNR in mosaic warfare networks, which requires rapidity.
2.2. Related Research and Improvements for Introduction of Hash Chain-Based Authentication in VMF
3. Comparative Analysis of the Existing Hash Chain-Based Authentication Approaches
3.1. Definitions of Additional Tactical Security Requirements in VMF
- Configuration of keyless point (CKP) (①)—Because the hash chain-based authentication with a T-OTP value is used in a rapidly changing battlefield environment, authentication in a VMF-based CNR must be able to verify friendly tactical ad hoc networks in reliable cell planning areas and warfare networks, thereby necessitating robustness against authentication data loss. In addition, to reduce the regular authentication flow, related network overhead and the security cost of server storage after adjusting the initial tactical network, the system is configured to exclude the key ownership stage in one of the two terminals using the authentication algorithm and scheme side. Interference from a variety of environmental variables and wireless jitter must also be considered [31,32];
- Low latency (LL) (②)—To rapidly conduct tactical operations and insert this scheme in wireless static terminals, the entire initial authentication process of VMF must be quickly completed. Moreover, to secure the robustness of military-based adaptive strategies [33] in line with developing network technology trends, components of latency-related requirements, such as time-to-transmit, time-to-preprocessing, time-to-retransmission, and bias or noise in battlefield [34,35], based on general parameters in VMF, are reflected and must be defined [36,37,38,39];
- Robustness to authentication attack (RA) (③)—Security against active and passive internal and external authentication attacks on random nodes in VMF-based CNRs is necessary, which can be achieved using various defensive mechanisms, such as preventing the reuse of keys in hash chain- and state-based exception handling. In particular, the hash chain-based authentication system including a T-OTP value must be configured to minimize the impact of various ad hoc network-based wireless authentication attacks, such as rushing attacks [40] wormhole, blackhole and sinkhole attacks, jellyfish, flooding and fragmentation attacks, man-in-the-middle (MITM), eavesdropping and sniffing [41,42,43,44,45]. Specifically, considering the military security requirements, the resistance capabilities should focus on replay, MITM, and Byzantine authentication attacks.
- Low authentication overhead in limited networks (LAO) (④)—To secure interoperability across hierarchical limited-resource CNRs and connected tactical terminals with low specifications, it is necessary to minimize the authentication overhead of the computation and network transactions based on the purpose of VMF standards. In addition, unnecessary transmission and energy consumption must be reduced through exception handling, punishment, and the monitoring of participating nodes in VMF-based closed CNRs, thereby achieving higher efficiency in limited battlefields. Furthermore, it is necessary to enable rapid decision-making and provide high-quality real-time combat environment features [46];
- Re-authentication and revocation for operations (RR) (⑤)—Re-authentication and topology updation processes must be provided to ensure that new nodes continue to participate as legitimate nodes even after the initial authentication is completed, re-establish the reliability of internally authenticated nodes, and prevent authentication attacks in an environment where intrusions from enemy forces can lead to theft and damage. It is also necessary to develop immediate authentication rejection and routing-based removal processes for the detected hostile nodes in hash chain-based authentication, including a T-OTP value, and identify internal malfunctioning nodes through an online-based culprit recognition and detection mechanism. Furthermore, more realistic military scenarios related to authentication in VMF must be established to ensure consistent authentication capabilities in actual CNRs. These scenarios must be standardized based on previously proposed military features, such as heterogeneous velocity, tactical areas, optimal paths, obstacles, and unit join and leave scenarios [47,48];
- Deep interoperability in authentication scheme (DI) (⑥)—The US Army plans to employ the VMF standard for data exchange in most of its TDL- and CNR-based systems, and the US Navy uses VMF-based TDL to satisfy the tactical requirements of information exchange between ground and maritime operations. According to the unit-specific operability described in US military materials [49] published in 2008, in an actual combat environment in which 64 vehicles and one unmanned aerial vehicle are active, it is possible to observe the movement of nodes constituting squads without disconnections. When one squad moves safely through a specific operational area, other squads often follow, confirming the presence of mobility through group units. On this basis, if multiple nodes forming a squad receive similar command data while moving as a squad, platooning at the same speed and in the same direction, it is necessary to maintain the authentication robustness of the squad CNRs at a high level to ensure the security of not only a given CNR, but also of the overall tactical environment. In addition to forming a smooth C4I between squads within the same country, it is necessary to establish combined operations with the militaries of other nations. As such, any hash chain-based authentication applied in CNRs must adhere to the interoperability demands based on the purpose of VMF standards.
3.2. Applicability Analysis of VMF-Based CNRs in Previous Studies on Hash Chain-Based Authentication
- The basic verification and re-authentication processes can be standardized using only one S/Key structure-based hash chain without needing multiple independent keys to periodically identify normal nodes in a resource-limited tactical network;
- S/Key has an extensible structure that is easiest to employ in multi-factor authentication without duplication for a randomly exposed key or hash value;
- To transit to a joint operation front with other squads during a combined operation, interoperability is achieved by applying the S/Key-based one-way chain structure used in the previous squad unit to the new squad unit, and based on the sequential hashing process, a rapidly lightweight tactical message transmission and authentication scheme can be secured according to the VMF-based information control. Thus, the existing authentication schemes and related parameters presented in VMF standards can be satisfied and further strengthened based on S/Key as an initial interface for the construction of a lightweight authentication scheme.
- TESLA is an authentication method for adding the calculated message authentication code (MAC), including a secret key generated through a hash function, to a packet based on a one-way chain. Therefore, based on the act of revealing the hash value owing to the loose time synchronization between the sender and the receiver, it is possible to minimize the exposure of information to the attacker and block false packet attacks. In addition, when there are multiple recipients in a multicast environment, quick and accurate individual authentication for each recipient can also be performed;
- The TESLA standard that was first proposed did not support non-repudiation, but TESLA++, an improved version, can secure a higher non-repudiation function than the elliptic curve digital signature algorithm (ECDSA). Through the TESLA-based VAST combined with the existing ECDSA, it is possible to derive specialization for authentication in military ad hoc networks such as VMF-based CNRs, including MANET and VANET [50];
- In addition to protection from valid authentication values that have not been used for long periods of time in VMF-based CNRs, a system can be established to monitor and identify spoofed nodes using such valid authentication keys. Moreover, hash chain-based authentication schemes can be constructed for an update and expansion of the squad member authorization list for long-term operations.
- LHAP was proposed to overcome the vulnerability of basic TESLA standards applied to multi-hop ad hoc networks such as MANET. Therefore, the network and computational overhead can be reduced by reducing the number and capacity of requests for nonce and hash values for initial authentication and re-initialization, and removing authentication information based on each node participating in or leaving the VMF-based ad hoc network.
- The concept of hop-by-hop access control can be realized for the behavior of malicious nodes and collaborative hostile nodes that have personal channels. In addition, the issues of exception processing for authentication delay and disconnection according to changes in the ad hoc network can be alleviated by generating a separate control packet. Furthermore, an additional lightweight authentication for distributed VMF-based WSNs can be calculated.
- Beyond filtering invalid authentication keys and packets at the authentication algorithm level, by establishing a system to authenticate and identify legitimate squad nodes and punish enemy nodes, a small-scale VMF-based CNR network specialized for more realistic battlefield environments can be constructed. Establishing trust relationships through specific keys will mitigate issues with authentication delays and network disconnections that arise in limited tactical networks and low-spec military wireless terminals.
- The central system will automatically mitigate the problem of separate re-initialization owing to the exhaustion of the root keys used for node confirmation, identification, and updation in VMF-based closed CNRs when conducting independent operations for long periods of time [51];
- When applying this hash chain-based authentication in CNR networks, issues such as the potentially limited operational time and resources, unnecessary network transactions associated with checking the remaining hash values, and securing independence owing to specificity in the military environment can be overcome.
- The re-initialization problem occurring from the exhaustion of keys used for authentication and updation when performing independent operations over a long period of time will be simply resolved. The performance cost owing to the participation of multiple new squad and member nodes and the establishment of a joint operation with other squads will also be minimized.
- The security of the authentication in each closed CNR network will be further strengthened, and the scheme will be more robust than those in other methods against the issues of limited key maintenance, authentication delays from duplicate hashing, wormhole attacks, and MITM;
- Application of this approach also enables the conversion of the authentication scheme into one that is specialized for changing battlefields in which enemy forces employ active confusion tactics based on the network.
- Limiting the lifetime of valid authentication keys that have not been used for long periods based on a predefined time span will enable the preparation of functional countermeasures to prevent, identify, and attenuate the continuous collection of information by specialized enemy nodes and conspirator nodes;
- Laying the foundation for military cyber agility [52,53] in a limited-resource CNR, based on independent cryptographic hash functions that can be deployed at any given time for each node in a tactical network, will facilitate the development of an authentication scheme that proactively prevents intrusions from specialized hostile nodes in a battlefield environment;
- Establishing a multi-factor hash chain-based authentication process including T-OTP will secure high levels of robustness and responsiveness against any initial reconnaissance attempts by enemy nodes, maintain tactical covert activities, and maximize the covert activities of friendly forces based on a scheme specialized for low-spec and low-speed closed squad networks;
- Furthermore, the ability to easily establish joint operation systems with other squad members and foreign militaries by synchronizing the hash functions will help satisfy various interoperability-related scenarios.
4. Proposed Lightweight Authentication Based on Multi-Factor Hash Chain with T-OTP in VMF
4.1. Design Principle
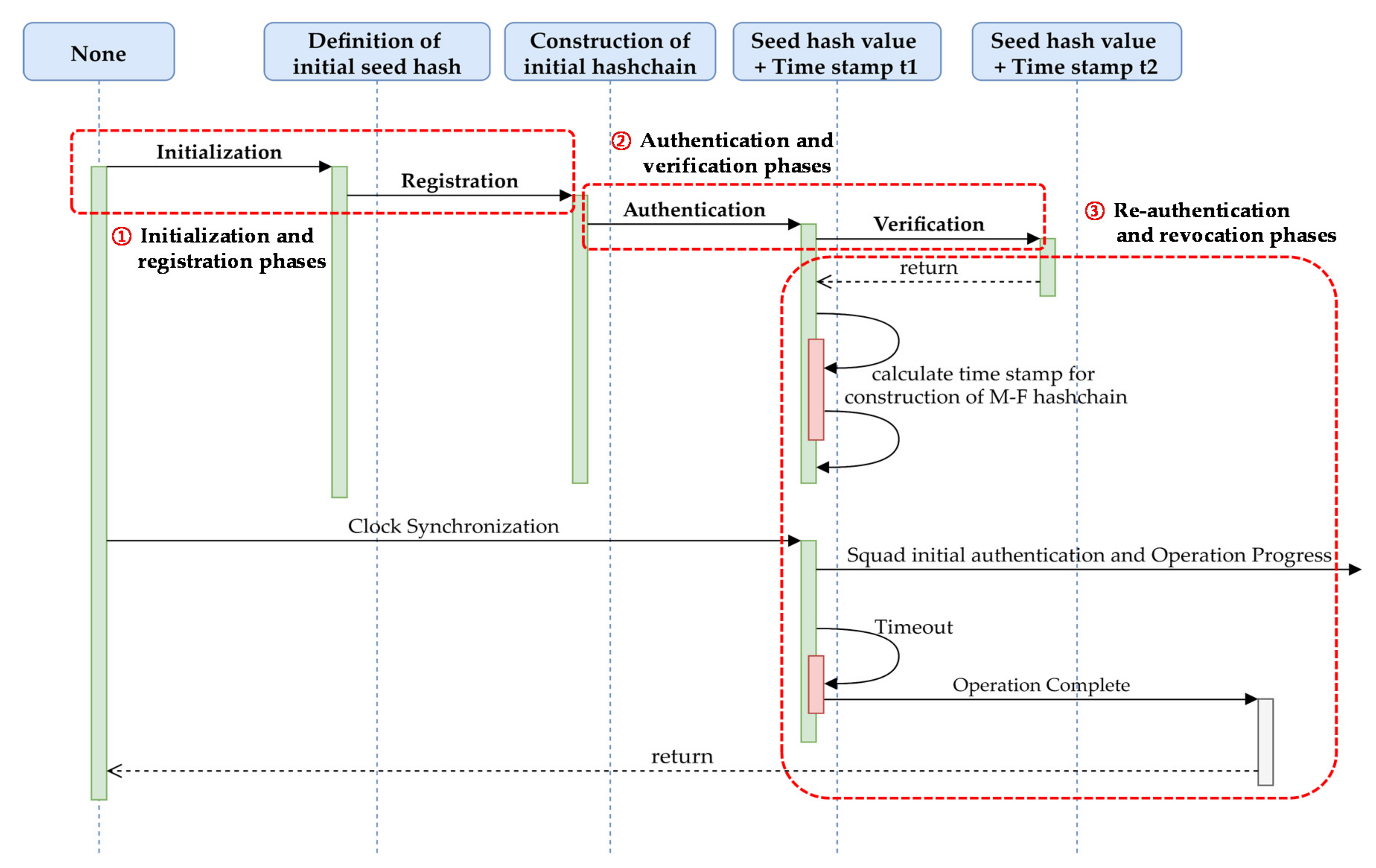
- ①
- Initialization and registration phases: The OTP seed hash generation in an LSH-based multi-factor hash chain between the administrator (the military authority or the commander of squad) and the user (the connected wireless device or squad member) in CNRs.
- ②
- Authentication and verification phases: Rapid authentication and verification with time-stamp-based clock synchronization values for T-OTP, and the limitation of the lifetime of arbitrary hash values in a hash chain that have not been used for a long time.
- ③
- Re-authentication and revocation phases: Tactical scenario-based network regularization of authentication status and exception handling for CNRs, including wireless terminals.
4.2. Lightweight Authentication Processes Based on Hash Chain
4.2.1. Initialization and Registration Phases
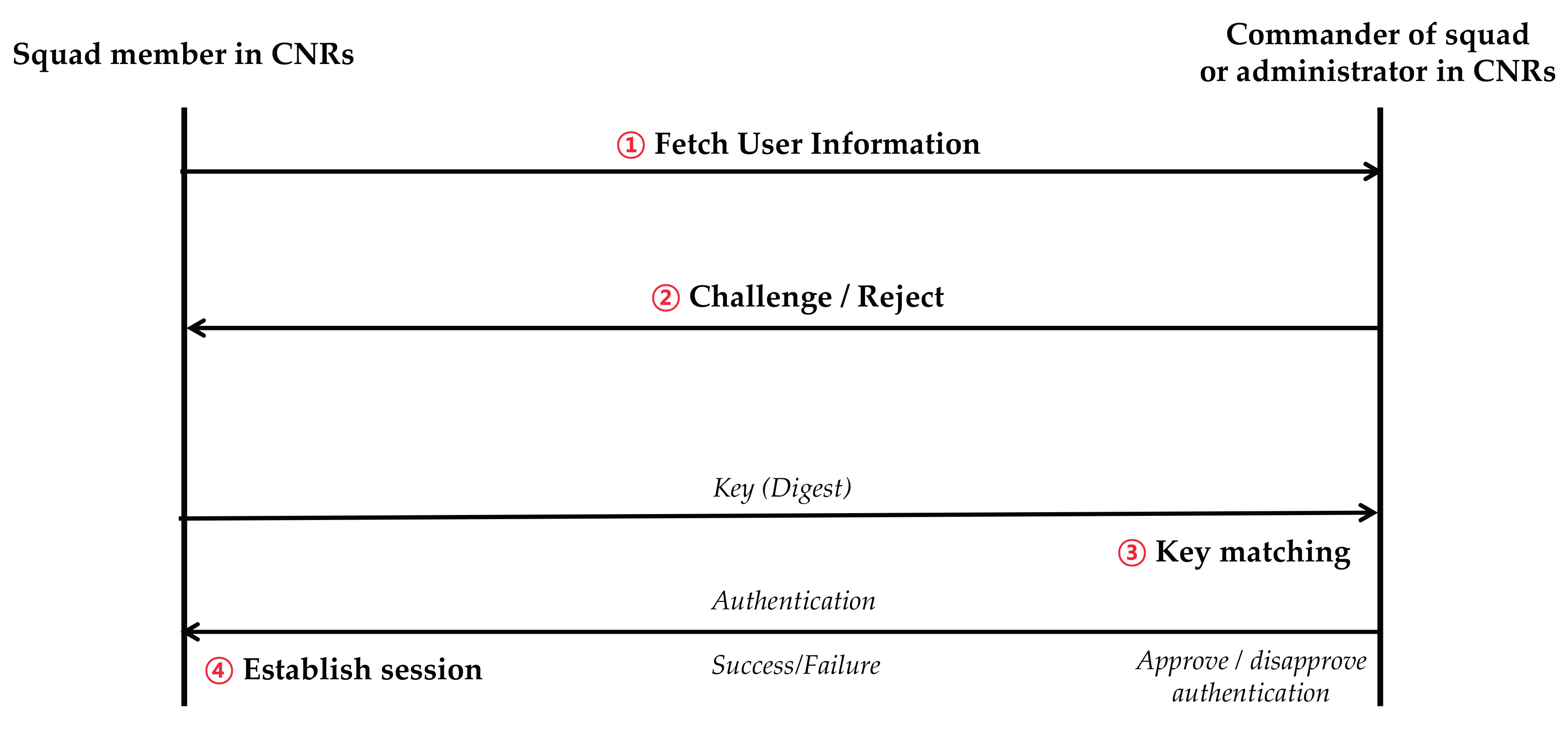
- ①
- Fetch user information: Execution of the initialization and registration phases.
- ②
- Challenge/Reject: Initial settings of the range of the time slot length for the configuration of T-OTP values in the multi-factor hash chain structure by the administrator.
- ③
- Key matching: Clock synchronization (periodic linkage of time between the user and administrator in CNR networks within a predetermined time-error range).
- ④
- Establish session: Delivery of the seed hash value on T-OTP by the administrator to the user.
4.2.2. Authentication and Verification Phases
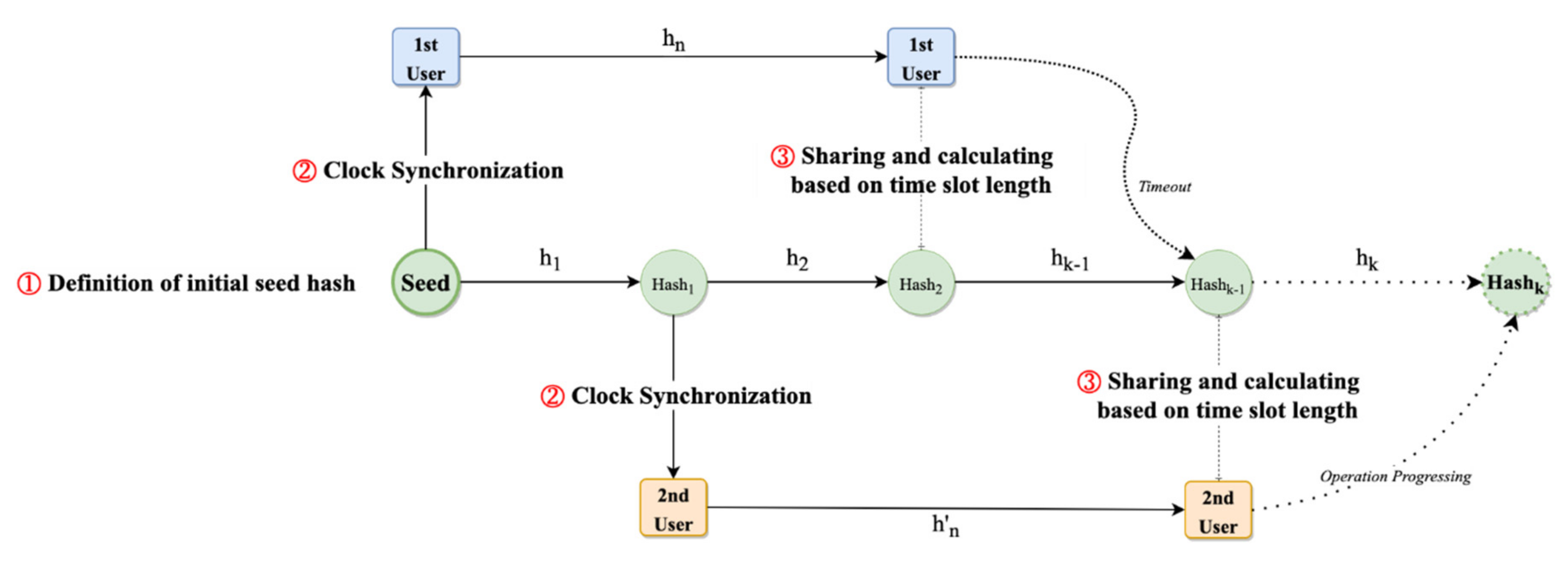
- ①
- Definition of initial seed hash: The initial seed hash of T-OTP, in which clock synchronization is executed and defined based on static transmission rules in military corps scenarios.
- ②
- Clock synchronization: The real-time authentication-based squad interoperability between the user and administrator within a predetermined time-error range is confirmed from the perspective of the operation start time in CNRs in cell-planning areas.
- ③
- Sharing and calculating based on time slot length: The calculated hash values between the administrator and user within the range of the dynamic time slot length is verified. Next, authentication is performed based on T-OTP in the LSH-based hash chain structure.
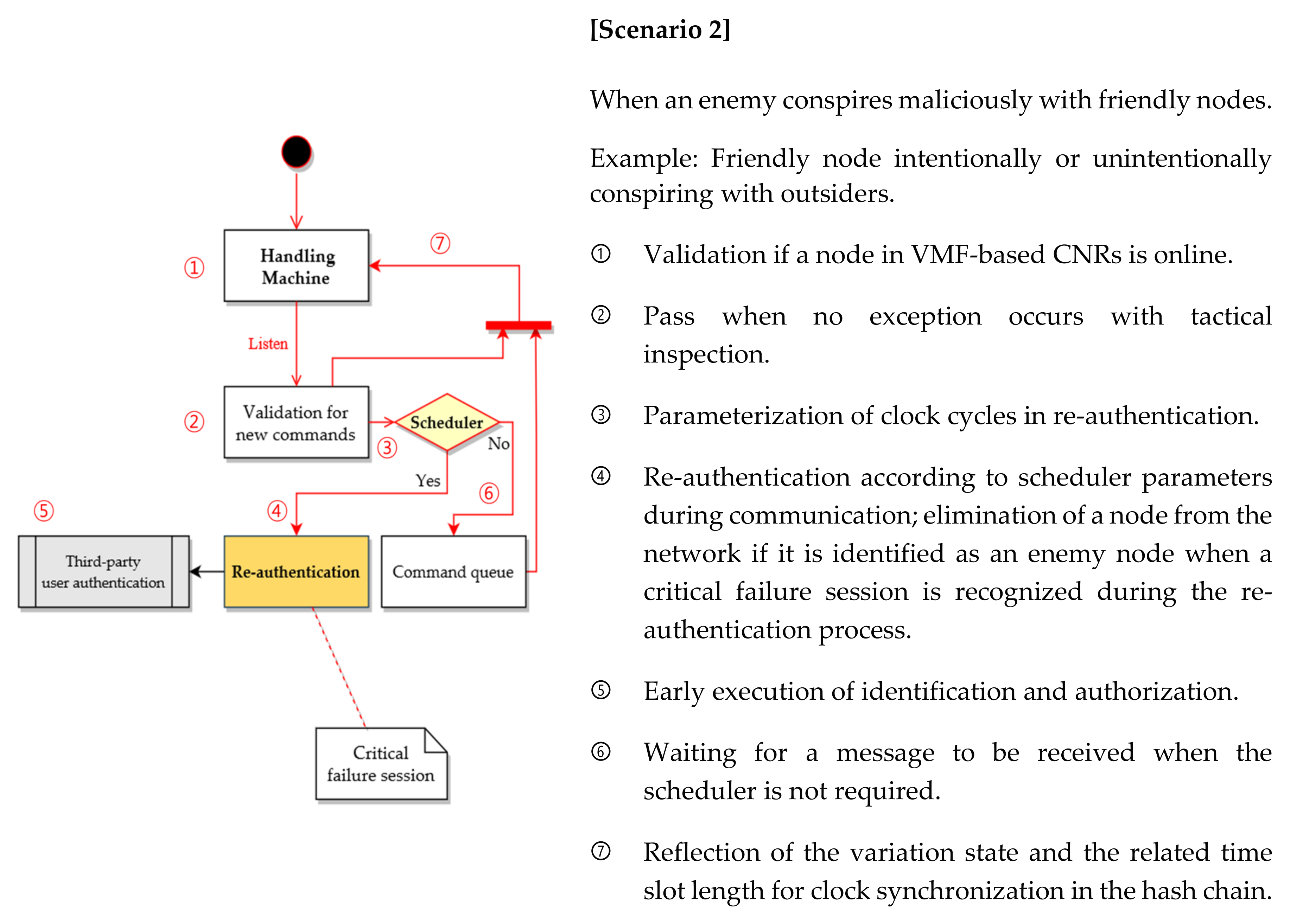
4.2.3. Re-authentication and Revocation Phases
- ①
- Identify the state: The current authentication state of each squad member node in VMF-based CNR networks and a tactical system is identified.
- ②
- Check if a failure session occurs within this arbitrary time: The re-authentication variable-based military scenario in dynamic battlefields is recognized.
- ③
- Whether a user has already achieved authentication within this arbitrary time is checked: The squad node authentication and re-authentication are executed in CNR networks for refreshing.
- ④
- Setting of a time scheduler for clock synchronization: The re-authentication time scheduler for a configuration of the dynamic time stamp is set.
- ⑤
- Re-configuration of time slot length: The slot length for clock synchronization is configured.
- ⑥
- Phase execution: The re-authentication and execution of this overall phase is awaited.
- ⑦
- Phase repetition: The authentication and verification phases with the re-authentication scheduler (if necessary) are repeated.
4.2.4. Testing of Exception Handling Flows in Specialized Military Scenarios in VMF-Based CNRs
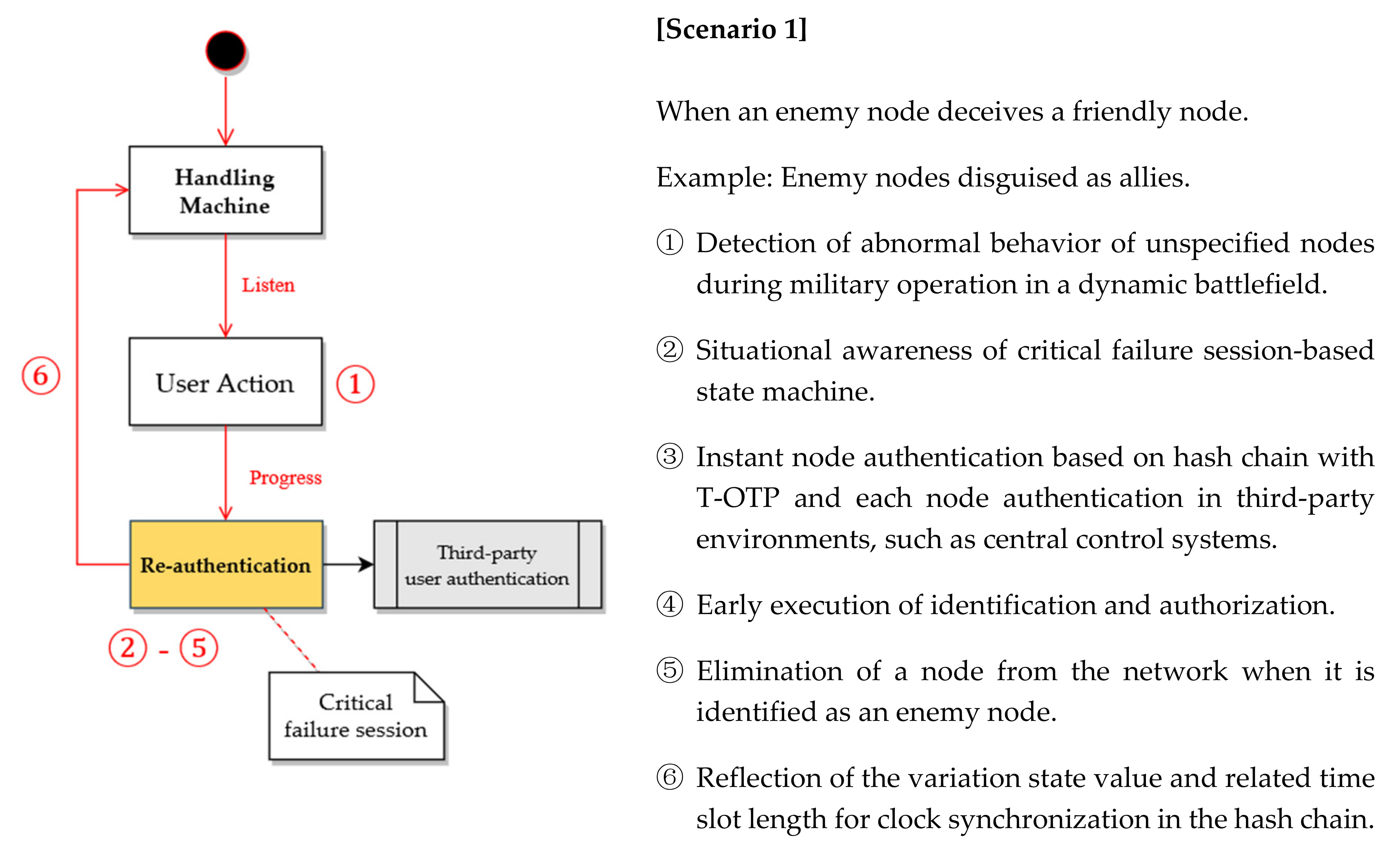
- Scenario 1: Masquerading hostile nodes for exfiltration of tactical information (Figure 5).
- Scenario 2: Internal friendly nodes deliberately or accidentally conspiring with malicious outsiders based on deceptive collusion attacks (Figure 6).
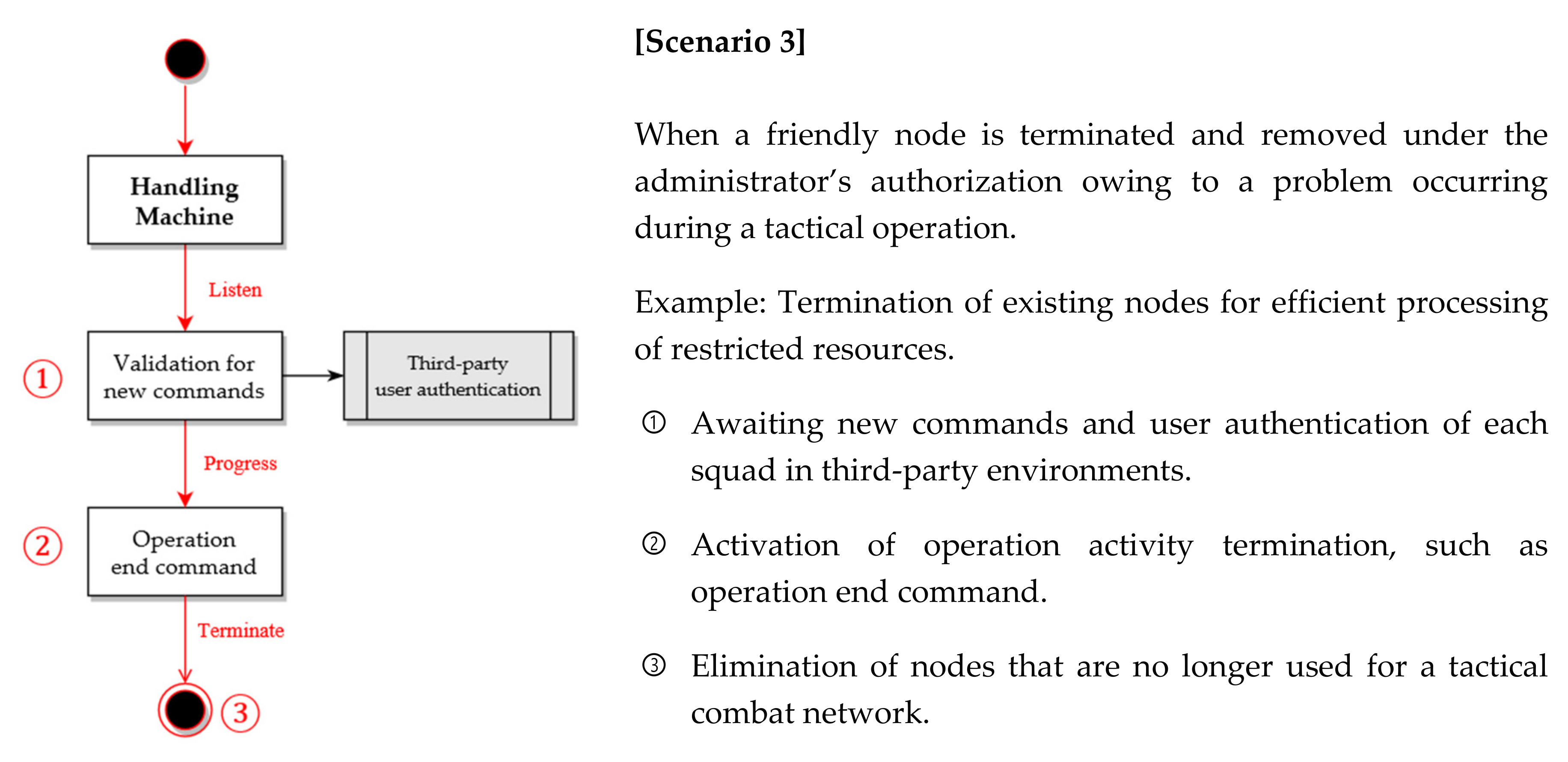
- Scenario 3: Selfish friendly nodes monopolizing limited network resources with an enemy node that has been compromised (Figure 7).
4.3. Configuration of Experimental Environments and Related Variables Based on VMF-Based CNR Networks
- ①
- Currently, the VMF-based CNR networks, to which the LSH-based multi-factor hash chain with a T-OTP authentication system is applied, are considered to support a maximum bandwidth of approximately 2 Mbps and BPSK modulation. The primary goal is to transfer messages as quickly and with as low an overhead as possible, while ensuring low-transaction-based authentication and integrity within the CNRs. Therefore, preferentially, based on the extreme configuration from a minimum of 2.4 kbps bandwidth to a maximum of 192 kbps bandwidth, additional variables such as transmission rate, transmission and reception electric power, modulation and demodulation, maximum transmit time (MTT), and jitter should be variably defined.
- ②
- There are differences in the communication power specifications of wireless devices for each squad class and military specification in the VMF-based CNRs. In addition, there is a difference in the equipment used for mixed voice and multi-media transfers. In other words, the wireless communication for infantry in a small squad network does not have an amplifier; as such, the bandwidth is low owing to small energy resources. However, the pieces of wireless communication terminal equipment mounted on tanks, corps helicopters, and corps unmanned vehicles have an amplifier, resulting in high radio energy emissions; as such, the bandwidth is higher. Therefore, all these aspects should be applied within the VMF-based military ad hoc network for each communication environment such as MANET and VANET, and the concepts of mobility variations and ground device specifications to simulate rapidly changing battlefields and limited network resources should be defined and calculated.
- ③
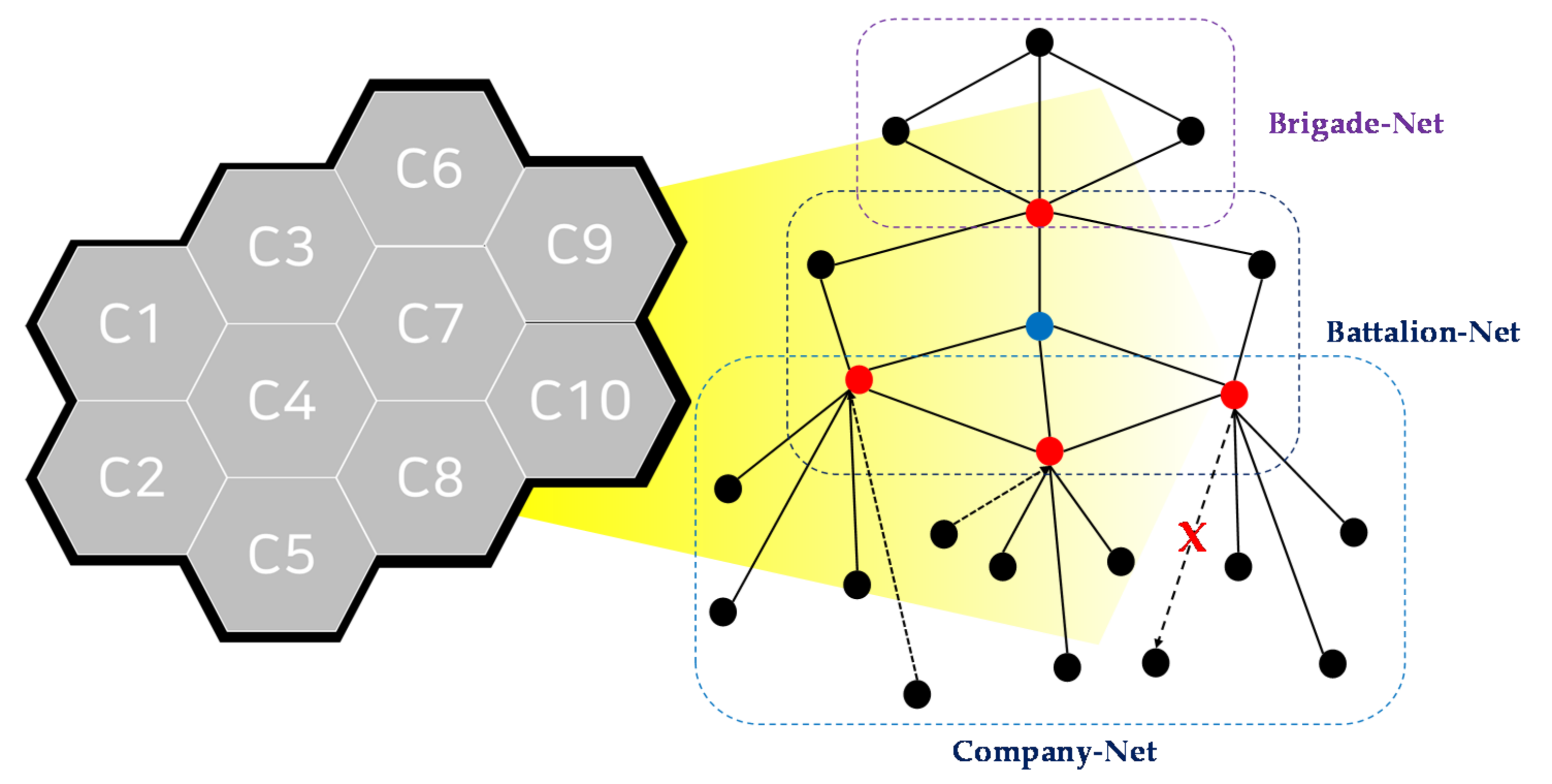
- The VMF-based CNR networks are largely classified into an FM radio-based communication type and an All-IP-oriented non-FM radio-based communication type. The FM radio environment includes a hierarchical star cluster network such as “brigade–battalion–company–platoon,” and each commander-specific communication uses different frequency bands. The All-IP-based non-FM radio environment includes a ring-type network, determines upper, lower, and unmanned swarming communication based on WAN-LAN, and uses different frequency bands for each operation or set of military occupational skills (MOS). Therefore, by applying all these aspects, isolated closed radio networks within VMF-based CNRs and related ad hoc networks should be constructed.
- ④
- The communication nodes are physically separated from the network, and only commander nodes, such as the brigade commander, battalion commander, company commander and platoon commander, can perform hierarchical sequential communication. In other words, in the FM radio environment, commander nodes other than the rank of platoon commander use two static radio channels instead of one, and squad members can communicate only to commanders in the same squad networks. Commander nodes in an All-IP-based non-FM radio environment have two IP classes themselves, such that they can simultaneously configure closed or open radio channels. All radio channels or IP addresses in FM and non-FM radio environments are not dynamically assigned, but are statically injected and maintained until the end of the operation. In addition, when an arbitrary commander node belonging to the lower cluster network requests communication from the upper commander, the lower node must directly join the upper network and change to the frequency of the upper cluster network. Therefore, all these aspects should be considered and applied.
- ⑤
- The authentication variable values related to the LSH-based multi-factor hash chain with the T-OTP system are obtained in a form that is injected before the start of the tactical operation. In addition, wireless communication authentication in the cell-planning areas based on corps ground and air control stations is similarly considered. Therefore, all these aspects should be considered and applied.
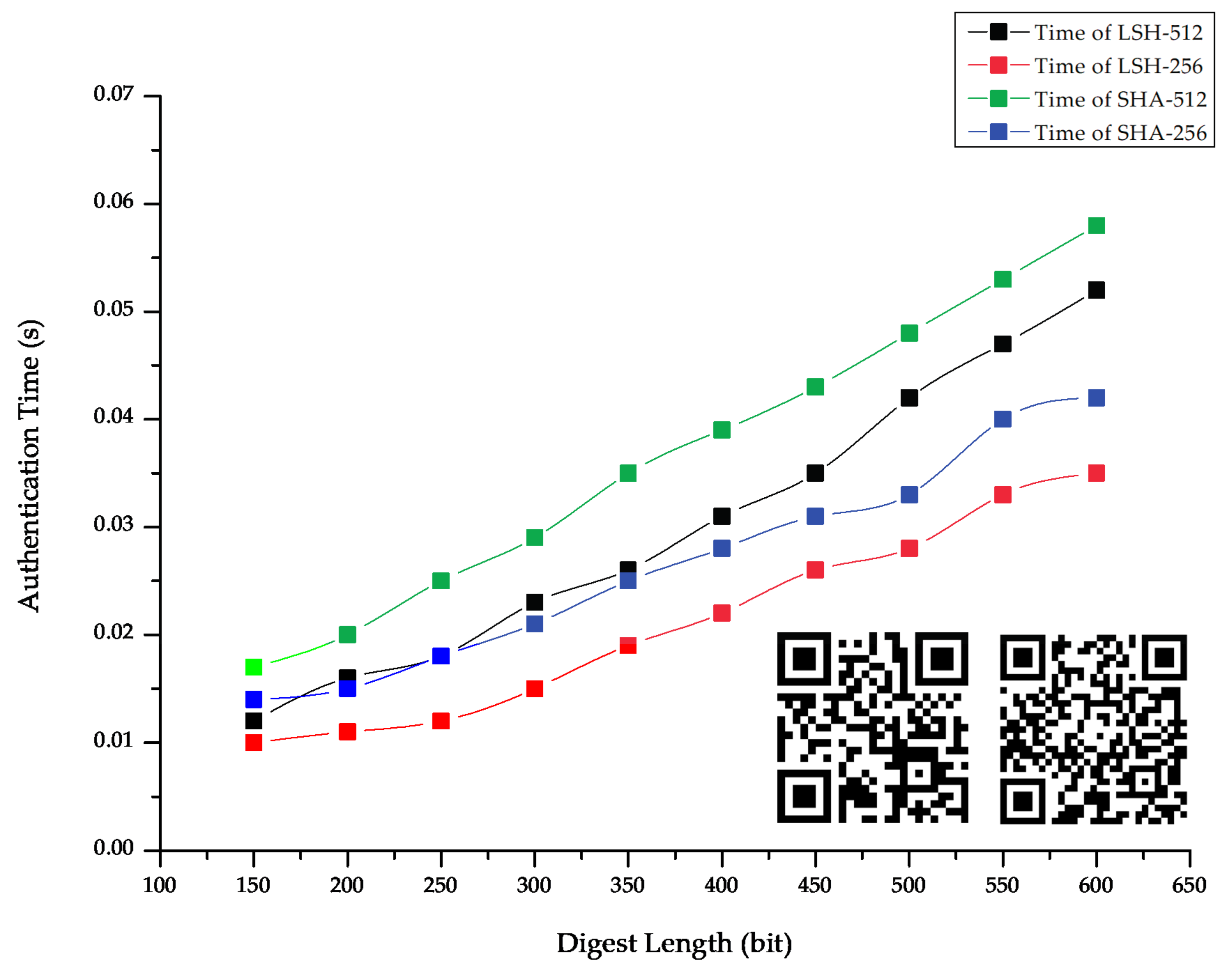
4.4. Comparison between Overall Proposed Model and Previous Studies
5. Conclusions
- Because this hash chain-based study focused on the design and analysis of a lightweight authentication for a VMF standard, future studies will assess its quantitative performance through network load tests in TDL based on the Korean Army Corps network scenarios with related equations, pseudo codes, and compound All-IP- or non-All-IP-based wireless topologies.
- During the re-authentication and re-validation phases, aiming to take advantage of the dedicated hash chain configured using the Byzantine fault tolerance property among other failure models in a distributed system, specific scenario-based schemes and attack graphs will be presented. In addition, they will be judged on their ability to be classified into specific tactical scenarios, including state machines for critical failure between actual operations.
- To obtain a dynamic adaptation of the proposed authentication process for a rapidly changing battlefield environment, the responsiveness of each squad must be considered for the rapid deployment of various nodes and the successful execution of various tactics and strategies. Therefore, by further devising a process for applying concrete state-based conditional exception handling modeling, a military communication system-based VMF message transfer standard will be produced that can also consider real-time authentication situations.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- MIL-STD-2045/47001D (w/CHANGE 1), Department of Defense Interface Standard: Connectionless Data Transfer Application Layer Standard. June 2008. Available online: http://everyspec.com/MIL-STD/MIL-STD-2000-2999/MIL-STD-2045_47001D_CHANGE-1_25098 (accessed on 1 November 2020).
- The FIPS 180-1 Secure Hash Standard. April 1995. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/FIPS/fipspub180-1.pdf (accessed on 1 November 2020).
- Wang, X.; Yin, Y.; Yu, H. Finding collisions in the full SHA-1. In Advances in Cryptology—CRYPTO 2005, Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621, pp. 17–36. [Google Scholar]
- Wang, X.; Yin, Y.L.; Yu, H. Finding Collisions in the Full SHA-1. In Advances in Cryptology–CRYPTO 2005; CRYPTO 2005; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621. [Google Scholar] [CrossRef]
- Stevens, M.; Bursztein, E.; Karpman, P.; Albertini, A.; Markov, Y. The first collision for full SHA-1. In Proceedings of the 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Berlin/Heidelberg, Germany, 2005; Volume 10401, pp. 570–596. [Google Scholar]
- Lee, J.; Kim, J. LSH: A new fast secure hash function family. In Proceedings of the 17th International Conference on Information Security and Cryptology, Seoul, Korea, 3–5 December 2014; Springer: Berlin, Germany, 2005; Volume 8949, pp. 286–313. [Google Scholar]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Eldefrawy, M.H.; Khan, M.K.; Alghathbar, K. One-time password system with infinite nested hash chains. In Security Technology, Disaster Recovery and Business Continuity; Communications in Computer and Information Science: Berlin, Germany, 2010; Volume 122, pp. 161–170. [Google Scholar]
- Hu, Y.C.; Perrig, A. A survey of secure wireless ad hoc routing. IEEE Secur. Priv. 2004, 2, 28–39. [Google Scholar]
- Hyun, S.; Ning, P.; Liu, A.; Du, W. Seluge: Secure and DoS-resistant code dissemination in wireless sensor networks. In Proceedings of the International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 445–456. [Google Scholar]
- Deng, J.; Han, R.; Mishra, S. Secure code distribution in dynamically programmable wireless sensor networks. In Proceedings of the 5th International Conference on Information Processing in Sensor Networks, Nashville, TN, USA, 19–21 April 2006; pp. 292–300. [Google Scholar]
- Haller, N.M. The S/Key™ one-time password system. In Proceedings of the Internet Society Symposium on Network and Distributed System, San Diego, CA, USA, 1 January 1994; pp. 151–157. [Google Scholar]
- Zhang, Y.; Chen, Y.; Sun, Y.; Chen, M. Training demand analysis for airlines safety manager based on improved OTP model. In Proceedings of the International Conference on Human-Computer Interaction, as Vegas, NV, USA, 15–20 July 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 334–342. [Google Scholar]
- Mitchell, C.J.; Chen, L. Comments on the S/KEY user authentication scheme. ACM SIGOPS Oper. Syst. Rev. 1996, 30, 12–16. [Google Scholar] [CrossRef]
- Perrig, A.; Canetti, R.; Tygar, J.D.; Song, D. The TESLA broadcast authentication protocol. RSA CryptoBytes Tech. Newsl. 2002, 5, 2–13. [Google Scholar]
- Perrig, A.; Song, D.; Canetti, R.; Tygar, J.; Briscoe, B. Timed Efficient Stream Loss-Tolerant Authentication (TESLA): Multicast Source Authentication Transform Introduction. Req. Comments 2005, RFC-4082. Available online: https://tools.ietf.org/html/rfc4082 (accessed on 12 December 2020).
- Jakobsson, M. Fractal hash sequence representation and traversal. In Proceedings of the IEEE International Symposium on Information Theory, Lausanne, Switzerland, 30 June–5 July 2002; p. 437. [Google Scholar]
- Hu, Y.-C.; Jakobsson, M.; Perrig, A. Efficient constructions for one-way hash chains. In Proceedings of the International Conference on Applied Cryptography and Network Security, New York, NY, USA, 7–10 June 2005; pp. 423–441. [Google Scholar]
- Zhu, S.; Xu, S.; Setia, S.; Jajodia, S. LHAP: A lightweight hop-by-hop authentication protocol for ad-hoc networks. In Proceedings of the 23rd International Conference on Distributed Computing Systems Workshops, Providence, RI, USA, 19–22 May 2003; pp. 749–755. [Google Scholar]
- Lu, B.; Pooch, U.W. A lightweight authentication protocol for mobile ad hoc networks. In Proceedings of the International Conference on Information Technology: Coding and Computing (ITCC’05), Las Vegas, NV, USA, 4–6 April 2005; pp. 546–551. [Google Scholar]
- Akbani, R.; Korkmaz, T.; Raju, G.V.S. HEAP: Hop-by-hop efficient authentication protocol for mobile ad-hoc networks. In Proceedings of the 2007 Spring Simulaiton Multiconference, Norfolk, VA, USA, 25–29 March 2007; pp. 157–165. [Google Scholar]
- Goyal, V. How to re-initialize a hash chain. IACR Cryptol. ePrint Arch. 2004, 97, 1–9. [Google Scholar]
- Zhang, H.; Li, X.; Ren, R. A novel self-renewal hash chain and its implementation. In Proceedings of the IEEE/IFIP International Conference on Embedded and Ubiquitous Computing, Shanghai, China, 17–20 December 2008; pp. 144–149. [Google Scholar]
- Eldefrawy, M.H.; Alghathbar, K.; Khan, M.K. OTP-based two-factor authentication using mobile phones. In Proceedings of the Eighth International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 11–13 April 2011; pp. 327–331. [Google Scholar]
- Bittl, S. Efficient construction of infinite length hash chains with perfect forward secrecy using two independent hash functions. In Proceedings of the 11th International Conference on Security and Cryptography (SECRYPT), Vienna, Austria, 28–30 August 2014; pp. 213–220. [Google Scholar]
- Kogan, D.; Manohar, N.; Boneh, D. T/Key: Second-factor authentication from secure hash chains. In Proceedings of the ACM SIGSAC Conference on Computer and Communications, Dallas, TX, USA, 30 October–3 November 2017; pp. 983–999. [Google Scholar]
- Yin, X.; He, J.; Guo, Y.; Han, D.; Li, K.C.; Castiglione, A. An efficient two-factor authentication scheme based on the Merkle tree. Sensors 2020, 20, 5735. [Google Scholar] [CrossRef] [PubMed]
- Burbank, J.L.; Chimento, P.F.; Haberman, B.K.; Kasch, W.T. Key challenges of military tactical networking and the elusive promise of MANET technology. IEEE Commun. Mag. 2006, 44, 39–45. [Google Scholar] [CrossRef]
- Tang, H.; Salmanian, M.; Chang, C. Strong Authentication for Tactical Mobile Ad Hoc Networks; Defence R & D Canada: Ottawa, ON, Canada, 2007. [Google Scholar]
- Lee, K.; Lee, S.; Kim, Y.; Kwon, K.; Lim, W. A study for hop count on the ad-hoc of wireless communication. In Proceedings of the 14th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 19–22 February 2012; Volume 176, pp. 931–935. [Google Scholar]
- Tu, W.; Lai, L. Keyless authentication and authenticated capacity. IEEE Trans. Inf. Theory 2018, 64, 3696–3714. [Google Scholar] [CrossRef]
- Jiang, S. Keyless authentication in a noisy model. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1024–1033. [Google Scholar] [CrossRef]
- Kong, J.; Luo, H.; Xu, K.; Gu, D.L.; Gerla, M.; Lu, S. Adaptive security for multilevel ad hoc networks. Wirel. Commun. Mob. Comput. 2002, 2, 533–547. [Google Scholar] [CrossRef]
- Ji, H.; Park, S.; Yeo, J.; Kim, Y.; Lee, J.; Shim, B. Ultra-reliable and low-latency communications in 5G dwnlink: Physical layer aspects. IEEE Wirel. Commun. 2018, 25, 124–130. [Google Scholar] [CrossRef]
- Ji, H.; Park, S.; Shim, B. Sparse vector coding for ultra reliable and low latency communications. IEEE Trans. Wirel. Commun. 2018, 17, 6693–6706. [Google Scholar] [CrossRef]
- Parvez, I.; Rahmati, A.; Guvenc, I.; Sarwat, A.I.; Dai, H. A survey on low latency towards 5G: RAN, core network and caching solutions. IEEE Commun. Surv. Tutorials. 2018, 20, 3098–3130. [Google Scholar] [CrossRef]
- Gao, P.X.; Narayan, A.; Karandikar, S.; Carreira, J.; Han, S.; Agarwal, R.; Ratnasamy, S.; Osdi, I.; Gao, P.X.; Narayan, A.; et al. Network Requirements for Resource Disaggregation. In Proceedings of the 12th USENIX Symposium on Operating Systems Design and Implementation, Savannah, GA, USA, 2–4 November 2016; pp. 249–264. [Google Scholar]
- Seok, B.; Sicato, J.C.S.; Erzhena, T.; Xuan, C.; Pan, Y.; Park, J.H. Secure D2D communication for 5G IoT network based on lightweight cryptography. Appl. Sci. 2019, 10, 217. [Google Scholar] [CrossRef]
- Vladyko, A.; Khakimov, A.; Muthanna, A.; Ateya, A.A.; Koucheryavy, A. Distributed edge computing to assist ultra-low-latency VANET applications. Future Internet 2019, 11, 128. [Google Scholar] [CrossRef]
- Hu, Y.C.; Perrig, A.; Johnson, D.B. Rushing attacks and defense in wireless ad hoc network routing protocols. In Proceedings of the 2nd ACM Workshop on Wireless Security, San Diego, CA, USA, 19 September 2003; pp. 30–40. [Google Scholar]
- Wu, B.; Chen, J.; Wu, J.; Cardei, M. A survey of attacks and countermeasures in mobile ad hoc networks. In Wireless Network Security; Springer: Berlin/Heidelberg, Germany, 2007; pp. 103–135. [Google Scholar]
- Aad, I.; Hubaux, J.P.; Knightly, E.W. Impact of denial of service attacks on ad hoc networks. IEEE/ACM Trans. Netw. 2008, 16, 791–802. [Google Scholar] [CrossRef]
- Abdul-Ghani, H.A.; Konstantas, D.; Mahyoub, M. A comprehensive IoT attacks survey based on a building-blocked reference model. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 355–373. [Google Scholar]
- Ponsam, J.G.; Srinivasan, R. A survey on MANET security challenges, attacks and its countermeasures. Int. J. Emerg. Trends Technol. Comput. Sci. 2014, 3, 274–279. [Google Scholar]
- Alani, M.M. MANET security: A survey. In Proceedings of the IEEE International Conference on Control System, Computing and Engineering (ICCSCE), Batu Ferringhi, Malaysia, 28–30 November 2014; pp. 559–564. [Google Scholar]
- Bar-Noy, A.; Cirincione, G.; Govindan, R.; Krishnamurthy, S.; Laporta, T.F.; Mohapatra, P.; Neely, M.; Yener, A. Quality-of-information aware networking for tactical military networks. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Seattle, WA, USA, 21–25 March 2011; pp. 2–7. [Google Scholar]
- Aschenbruck, N.; Gerhards-Padilla, E. A survey on mobility models for performance analysis in tactical mobile networks. J. Telecommun. Inf. Technol. 2008, 2, 54–61. [Google Scholar]
- Suri, N.; Benincasa, G.; Lenzi, R.; Tortonesi, M.; Stefanelli, C.; Sadler, L. Exploring value-of-information-based approaches to support effective communications in tactical networks. IEEE Commun. Mag. 2015, 53, 39–45. [Google Scholar] [CrossRef]
- Lu, X.; Chen, Y.-C.; Leung, I.; Xiong, Z.; Liò, P. A novel mobility model from a heterogeneous military MANET trace. In Proceedings of the International Conference on Ad-Hoc Networks and Wireless, Sophia-Antipolis, France, 10–12 September 2008; Volume 5198, pp. 463–474. [Google Scholar]
- Studer, A.; Bai, F.; Bellur, B.; Perrig, A. Flexible, extensible, and efficient VANET authentication. J. Commun. Netw. 2009, 11, 574–588. [Google Scholar] [CrossRef]
- Chefranov, A.G. One-time password authentication with infinite hash chains. In Novel Algorithms and Techniques in Telecommunications, Automation and Industrial Electronics; Springer: Berlin/Heidelberg, Germany, 2008; pp. 283–286. [Google Scholar]
- Mitchell, W. Three C2 Models for Military Agility in the 21st Century; Royal Danish Defence College Press: Copenhagen, Denmark, 2012. [Google Scholar]
- Alexeev, A.; Henshel, D.S.; Levitt, K.; McDaniel, P.; Rivera, B.; Templeton, S.; Weisman, M. Constructing a science of cyber-resilience for military systems. In Proceedings of the NATO IST-153 Workshop on Cyber Resilience, Munich, Germany, 23–25 October 2017; pp. 23–25. [Google Scholar]



| Code | Reference |
|---|---|
| 0000 (0) | Authentication (using SHA-1 and DSA)/No Encryption |
| 0001–1111 (1–15) | Undefined |
| Field Name | Size (Bits) |
|---|---|
| Keying Material ID | 0–64 |
| Cryptographic Initialization | 0–128 |
| Key Token | 0–512 |
| Authentication Data (A) | 320–1024 |
| Authentication Data (B) | 320–1024 |
| Message Security Padding | 0–128 |
| Octet | Field Identification | Value |
|---|---|---|
| 1 | Block Number: Identifies specific data block. | 15 |
| 2 | Length: Indicates the length of the Address Designation Parameters block in octets. | Variable length: 13 + size of Digital Signature |
| 3 | Hash Algorithm: Used to produce the hash. | 0 = MD5 1 = SHA-1 |
| 4 | Crypto Algorithm: Identification of the crypto algorithm used to encrypt the hash to produce the digital signature. | 0 = Not encrypted 1 = RSA 2–255 User defined |
| 5–13 | Key ID: signer’s public key. | 8 octet binary field |
| 14-Length field | Digital Signature: Authentication of the sender of the message. |
| CKP (①) | LL (②) | RA (③) | LAO (④) | RR (⑤) | DI (⑥) | |
|---|---|---|---|---|---|---|
| Haller et al. [12] | X | X | △ | △ | △ | △ |
| Perrig et al. [15] | X | △ | ▲ | ▲ | ▲ | △ |
| Zhu et al. [19] | X | △ | ▲ | ▲ | ▲ | ▲ |
| Zhang et al. [23] | X | △ | △ | △ | ▲ | △ |
| Hamdy et al. [24] | X | △ | X | ▲ | ▲ | △ |
| Bittl et al. [25] | X | △ | O | X | △ | △ |
| Kogan et al. [26] | O | △ | O | △ | ▲ | O |
| Yin et al. [27] | O | ▲ | O | ▲ | ▲ | ▲ |
| Message | Generation Cycle (s) | Generation Length (Bit) | Importance | Allocation |
|---|---|---|---|---|
| Location reporting | 10 | 200, 400, 600 | Routine | Broadcast |
| Reconnaissance reporting | 1000–2000 | 2000, 4000, 12,000 | Priority | Multicast |
| Volley ordering | 1000–2000 | 150 | Urgent | Unicast |
| Parameter | Value | Description |
|---|---|---|
| Number of static cells | 1–7 | Number of cell clusters with center |
| Number of nodes | 8–1200 | Number of participating nodes in CNRs |
| Execution time (s) | 120–259,200 (3 days) | Operation time in VMF-based CNRs |
| Join nodes | 0–200 | Number of join nodes in ad hoc |
| Withdrawal nodes | 0–30 | Number of withdrawal nodes in ad hoc |
| Bandwidth (kbps) | 2.4–192 | Frequency band size |
| Frequency | Declared according to bandwidth | Frequency band |
| Power (w) | 0.01–0.2 | Transmit and receiver power |
| Coverage | Declared according to power | Device communication coverage |
| Distance (m) | 1–3000 | Distance of transmission |
| Number of channels | 1–3 | Number of sessions for communication |
| Modulation | BPSK, QPSK | Modulation method |
| Data rate (bps) | 2400–7200 | Data transfer rate |
| MTT | 0.0–0.02 | Maximum transmit time |
| PER | 0.0–0.1 | Packet error rate |
| BER | 0.0–0.1 | Bit error rate |
| Parameter | Value |
|---|---|
| Hash algorithm | LSH-256, LSH-512 |
| Size of nonce (bit) | 224, 256, 384, 512 |
| Minimum security length (bit) | 112 (NIST), 224 (BSA), 256 (NSA) |
| Execution time based on hash chain (s) | 128–1024 |
| Time slot length for T-OTP (s) | 5, 10, 30, 60, 300, 600 |
| Message digest (bit) | 150, 200, 400, 600, 2000, 4000, 12,000 |
| Crypto period (year) | 1, 2, 3 |
| Element | Value |
|---|---|
| Processor 1 for central administration | Intel Xeon E series, Intel i7-10700 |
| Processor 2 for commander | Intel i7-10875H, Samsung Exynos 8890 (virtual) |
| Processor 3 for member | Qualcomm Snapdragon 805 (virtual) |
| Type of communication nodes | Producer, Interpreter, Forwarder, Consumer, and Noise node (Declared according to number of nodes) |
| Enabling jitter nodes for causing overhead such as PDV, PER, and BER | True (0–20) |
| Type of communication packets | Voice, Data, Image, and Video |
| Type of ACK | TWOACK and S-ACK |
| Re-transmission of max count-based ACK | 0–3 |
| Type of wireless radio-based SDR | HF (AM), VHF (AM), and UHF (AM/FM) |
| Enabling cell-planning node | True (0–10)/False |
| Enabling terrain information | False |
| CKP (①) | LL (②) | RA (③) | LAO (④) | RR (⑤) | DI (⑥) | |
|---|---|---|---|---|---|---|
| VMF [1] | O | O | O | O | X | X |
| Haller et al. [12] | X | X | △ | △ | △ | △ |
| Perrig et al. [15] | X | △ | ▲ | ▲ | ▲ | △ |
| Zhu et al. [19] | X | △ | ▲ | ▲ | ▲ | ▲ |
| Zhang et al. [23] | X | △ | △ | △ | ▲ | △ |
| Hamdy et al. [24] | X | △ | X | ▲ | ▲ | △ |
| Bittl et al. [25] | X | △ | O | X | △ | △ |
| Kogan et al. [26] | O | △ | O | △ | ▲ | ▲ |
| Yin et al. [27] | O | ▲ | O | ▲ | ▲ | ▲ |
| Our proposed authentication model | O | ▲ | O | ▲ | O | O |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, D.; Seo, S.; Kim, H.; Lim, W.G.; Lee, Y.K. A Study on the Concept of Using Efficient Lightweight Hash Chain to Improve Authentication in VMF Military Standard. Appl. Sci. 2020, 10, 8999. https://doi.org/10.3390/app10248999
Kim D, Seo S, Kim H, Lim WG, Lee YK. A Study on the Concept of Using Efficient Lightweight Hash Chain to Improve Authentication in VMF Military Standard. Applied Sciences. 2020; 10(24):8999. https://doi.org/10.3390/app10248999
Chicago/Turabian StyleKim, Dohoon, Sang Seo, Heesang Kim, Won Gi Lim, and Youn Kyu Lee. 2020. "A Study on the Concept of Using Efficient Lightweight Hash Chain to Improve Authentication in VMF Military Standard" Applied Sciences 10, no. 24: 8999. https://doi.org/10.3390/app10248999
APA StyleKim, D., Seo, S., Kim, H., Lim, W. G., & Lee, Y. K. (2020). A Study on the Concept of Using Efficient Lightweight Hash Chain to Improve Authentication in VMF Military Standard. Applied Sciences, 10(24), 8999. https://doi.org/10.3390/app10248999








