1. Introduction
Internet of Things (IoT) technology is evolving and starting to make a huge impact in a widespread range of applications, including industrial environments and smart cities. Such real world IoT applications combine communication, sensing, computation and actuation to remotely control and monitor the environment. Gartner states that the number of IoT devices will reach 20.4 billion by 2020 [
1]. Even human beings will connect to devices and each other through IoT in the near future. There is a great market opportunity offered by the IoT for Internet service providers, manufacturers, and application developers.
Figure 1 shows the wide range of IoT applications. There is a critical need for a flexible, layered architecture for the IoT because that can connect the trillions of heterogeneous devices through the Internet. Realizing the IoT vision using a host-to-host (H2H) communication standard Internet protocol (IP) is challenging in the context of constrained sensing and smart devices that connect densely with one or more networks, are highly heterogeneous, and frequently use several interfaces [
2]. There is a need to correspond with numerous security administrations and have both global and local communication ability. It is challenging for the IP to deal with this increase in devices while still integrating the minimum resource usage [
3].
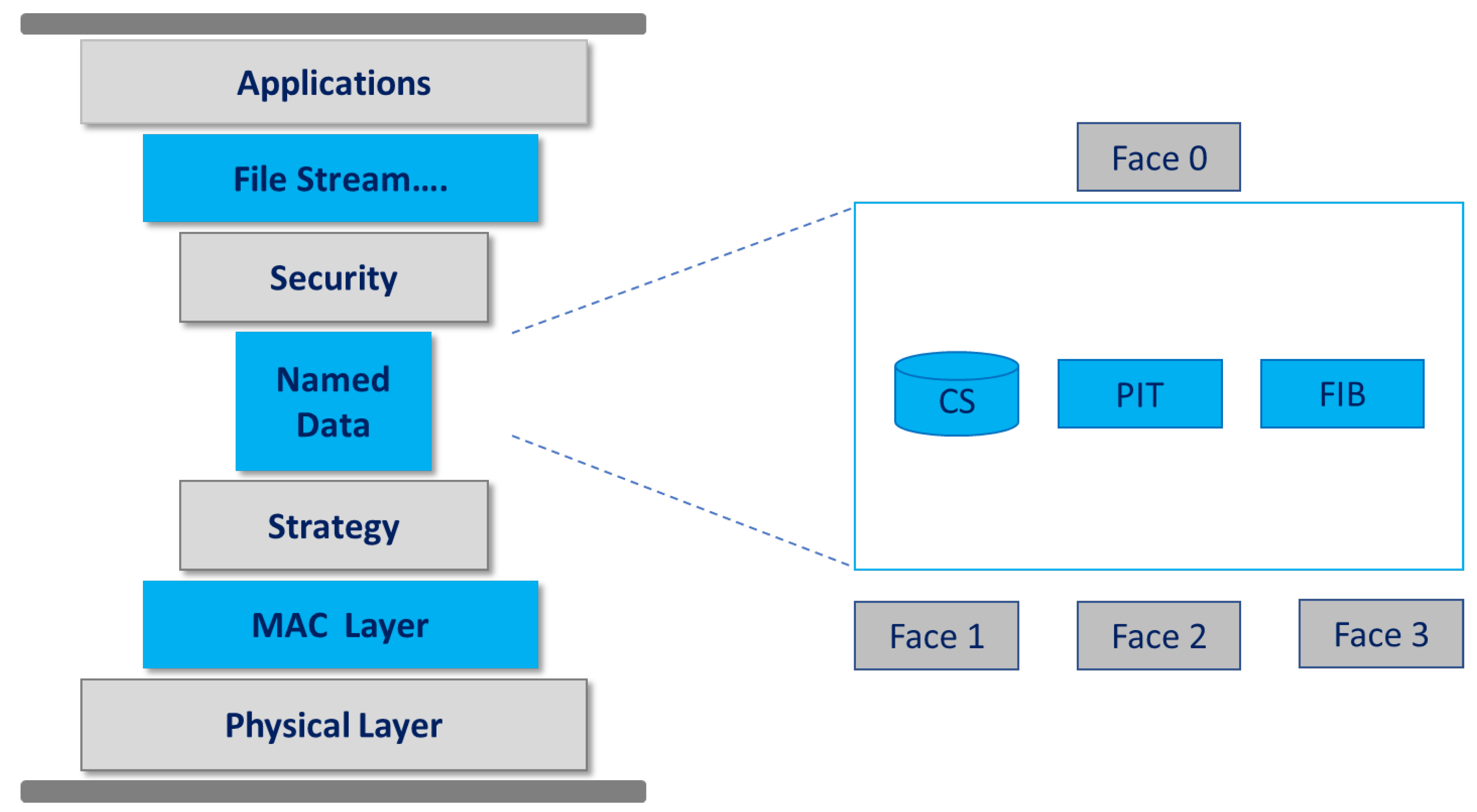
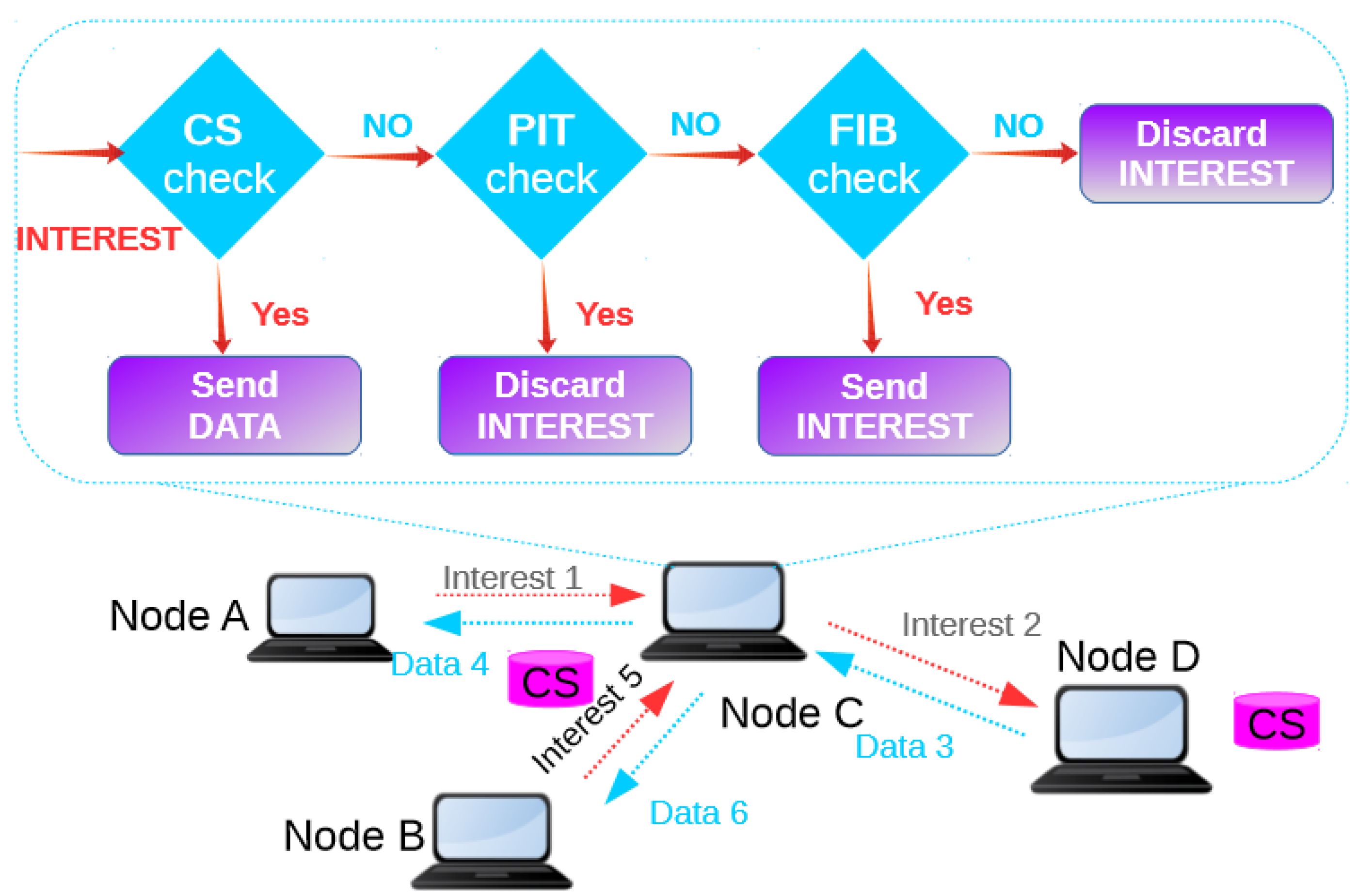
Named Data Networking (NDN) is a new and prominent communication paradigm. IoT based data communication efficiency can be improved using advantages of NDN. Communication in NDN is content centric. The main motivation behind the vision of NDN is the limitations of current internet architecture [
4]. Both NDN and IP use the same hourglass architecture, end-to-end principle, their own namespace and send datagram for the delivery of data [
5]. Named Data layer in NDN hourglass model consist of Content store (CS), Pending Interest Table (PIT) and Forwarding Information Base (FIB). The NDN hourglass architecture is presented in
Figure 2.
Named data networking as an emerging paradigm on the Internet fulfills most of the expectations of the IoT. There are always points to address among the many open aspects of research. Dense and different traffic patterns of the IoT system compared to current Internet applications, such as video streaming and web browsing, need a proper procedure to identify the devices, services, and management [
6]. IoT devices are resource constrained ones that use little power and energy, but they do not provide reliable communication in the wireless environment, so the optimization techniques for reliable data delivery must be there in NDN.
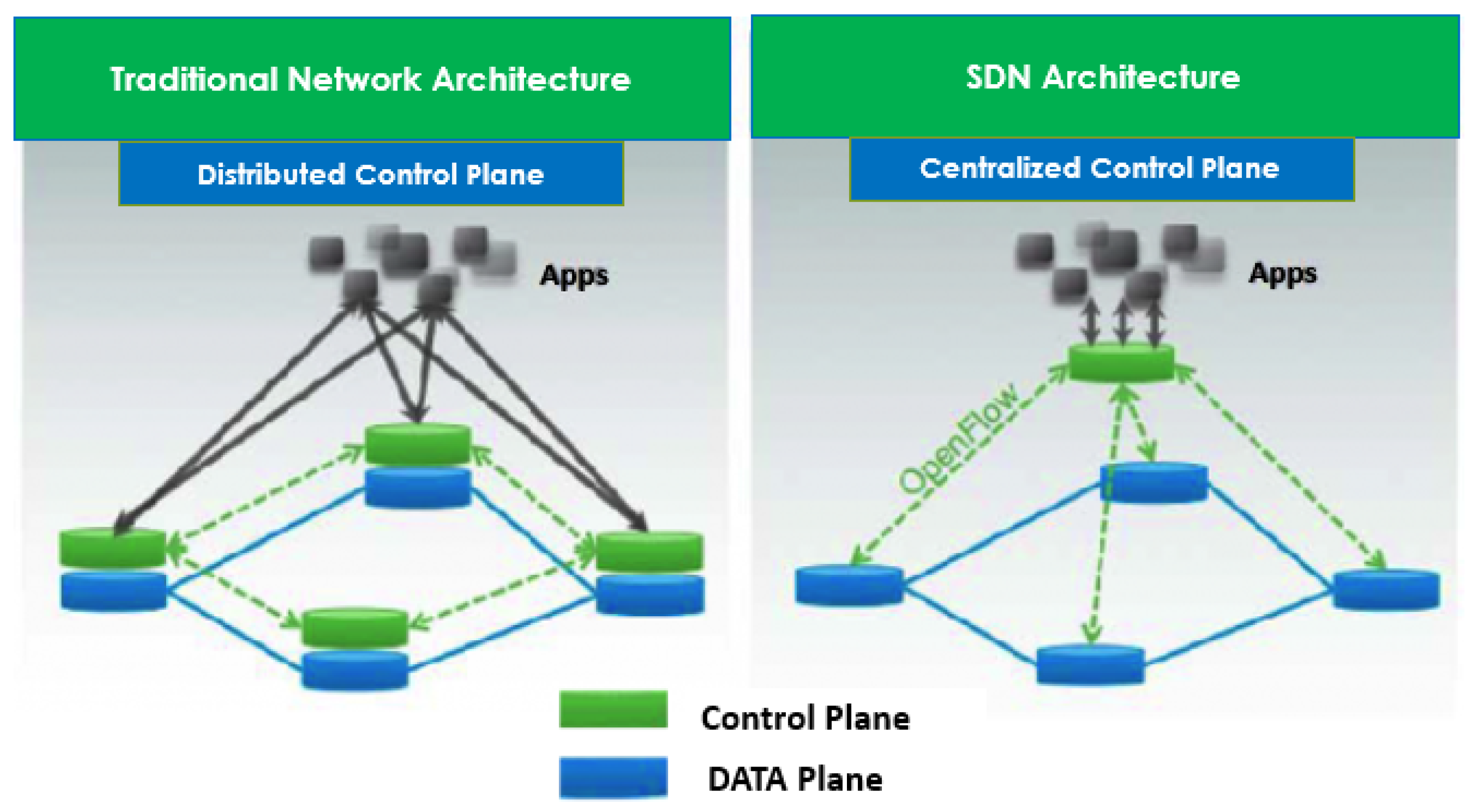
Software Defined Networking (SDN) is an emerging technology that makes computer networks more programmable. SDN is offering new ways to interact within networking devices by adding flexibility to existing networking operations and designs. SDN provides an innovative approach towards the design, implantation and management of networks that separates the control plane and data plane. SDN provides a centralized control plane for the control and management applications, and removes the decision-making part from the router that makes it different from traditional networking [
7]. Two primary components of SDN are the controller and switches. Management of the entire network is the responsibility of the SDN controller while, on the other hand, instruction-based operation is done by the switches. Software defined networking is a good solution for emerging technologies and efficient resource utilization and communication [
8].
There are open problems and challenges, like scalability, integration, management of flow table, and real-time SDN updates. In urban scenario, hundreds of IoT devices, actuators and sensors are sensing and transmitting the data for processing in an heterogenous environment. In IoT environment drastically increase in population and IoT devices makes communication and data management more challenging [
9]. Real-time efficient management and retrieval of data in the IoT environment is a challenge that can be solved using SDN [
10]. Software defined networking can benefit the IoT system because the control intelligence moves to the centralized controller and is removed from the data plane devices. The controller itself interacts with the devices of the data plane. The SD-IoT architecture consists of three layers: the physical infrastructure layer, the application layer and the control layer [
11]. The SDN architecture is presented in
Figure 3. There are benefits for environment communication and performance when these three paradigms—NDN, SDN, and IoT—are connected to develop a new joinable SD-NDN–IoT architecture.
Forwarding strategies in References [
12,
13,
14] used SDN controller to forward the packets. Some forwarding strategies used native flooding mechanism aided with controller to forward the packet that brings high overhead and broadcast storm issues on network. There is no strategy to prevent the energy consumption with the use of controller in related work. They did not handle the priority and emergency packets efficiently in WSNs and IoTs. In References [
15,
16,
17], proposed forwarding mechanisms to mitigate the broadcast storm issue but lack of work to find efficient forwarding path and more overhead on the controller. In References [
18,
19,
20], authors proposed energy efficient forwarding schemes in IoT. Proposed energy efficient mechanism in this paper results in improved average energy consumption and network life time. In this paper an efficient forwarding mechanism in NDN based IoTs is proposed using the centralized controller of SDN. The main purpose of our proposed scheme is to ensure the in-time and fast packet transmission of high priority packets in dense IoT environment with maximum satisfaction rate. The focus is on the energy efficiency of the whole network to guarantee the maximum output. This paper is organized as follows:
Section 1 introduces the three paradigms—IoT, NDN, and SDN.
Section 2 provides a brief explanation of NDN, and its architecture with IoT is presented.
Section 3 consists of the motivation behind integration of SDN and ICN along with the advantages of SDN-NDN-IOT combination.
Section 4 consists of related work. Problem scenarios are presented in
Section 5.
Section 6 proposes a scheme and discusses it in detail. Finally,
Section 7 and
Section 8 depict the simulation graphs and conclusion, respectively.
3. Motivations of Integrating SDN and Inofrmation Centric Networking
Although excellent research work has already been presented in SDN and ICN separately, these two promising futuristic paradigms are complementary, benefiting each other by tackling different kinds of networking problems. The research community has started investing their efforts in SDN and ICN. Benefits of SDN over current Internet, including centralized control, powerful data management, and monitoring tool and global views of the whole network, also apply to ICN [
24]. ICN can handle distribution of data in upgraded networks, smooth the transition phase, and simplify the deployment with the help of SDN. A lot of surveys and research ideas have been proposed in SDN and ICN on issues of energy efficiency [
25], security, mobility, caching, and forwarding [
26]. The centralized SDN controller has powerful control of data transfer as well as a global view of the status of network. SDN is a promising way to manage networks simply. The combined SDN-ICN can benefit the network by opening new opportunities after shifting the question from “where” to “what.” SDN can take full advantage of the main feature of ICN—that is, in-network caching. SDN is able to exploit the multipath routing and in network caches. Routing of content can be optimized because SDN can monitor in network caches efficiently. New data centric services can be enabled using SDN over ICN. ICN can remove the security threats over northbound and southbound communication in SDN due to its nature of protecting content as opposed to communicating between channels. SDN can provide powerful control over distributed elements of ICN. Centralized management, revocation of keys, and distribution of SDN can strengthen the security of ICN. SDN can benefit ICN with its agility and programmability in named based forwarding.
Software Defined Networking Enabled Named Data IoTs (SDN-NDN-IoT)
SDN enabled NDN–IoT architecture is an emerging research combination that uses the benefits of NDN with IoT systems to improve efficiency using the SDN model. High-priority messages can support NDN–IoT in case of any alarming situation by notifying governments, emergency departments, hospitals, or law enforcement authorities using push-based forwarding in NDN. Support of periodic and event triggered data and content pushing must be overhauled in NDN–IoT architecture. Device configuration procedures and device discovery is an important requirement in the IoT system. In NDN–IoT architecture, service publish and discovery protocols (SPDPs) [
27] and neighbor discovery protocols (NDPs) [
22] can be use to discover and configure the device in the IoT system. In the global IoT environment, named-based routing of NDNappears to be extremely useful. Packets can communicate in the network without resolving any network addresses because of the uniqueness of the content name. Specific application-based naming can clearly benefit the NDN solution for the IoT. The current IoT system needs IoT names to be able to identify the services, tasks, and applications ensured by the device. For example, sensor type, sensor position, type of the data, and time when data is needed. User readability and user-friendly NDN names can cause serious security-related issues in IoT applications such as spoofing. NDN offers an amazing solution for the secure content dissemination in the IoT environment by putting publisher signatures in the data packet. In NDN–IoT, there is a need to develop efficient authorization mechanisms, trust models, and access control policies to support security and minimize risks. In-network caching in NDN can be crucial to provide the scalability, readability, and robustness to the IoT environment [
28]. The NDN strategy layer allows the named data network to interact with the IoT. The IoT data passes through heterogeneous devices during communication within the network, so NDN–IoT architecture must develop a mechanism to support the heterogeneous environment of the IoT system. A combination of NDN and IoT is a good solution that benefits the communication of smart devices and enhances the overall performance of the IoT system. Named data networking takes care of the security of data packets by securing them on the network layer. A producer signature, binding data payloads and data names in a cryptographic way, authentication and reconstruction chains for the verification of the data and recorded information, and signing key certificates in key information locators are methods used to secure the data.
The name-based forwarding in NDN enables the IoT and named data networks to communicate directly with the packets, unlike the IP network. Name-based stateful forwarding can benefit other features of the IoT system, like fast local recovery, congestion control (hop by hop), and delay tolerant communication style. The in-network storage ability of NDN is a big advantage to IoT devices: in case of sensors deployment with limited storage capacity in an agriculture field, sensors can quickly transfer the data they monitor to the nearby repository. A controller can retrieve the desired data from the repository as well. The in-network storage can reduce overhead from the network because the nodes can cache the data packets they forward and can efficiently cache the popular data and fast local recovery.
By Default, SDN does not support Sensor and IoT networks. With the decoupling of control plane from data plane, SDN benefits the IoT with intelligent management. One or multiple SDN controllers can be there in IoT environment, in which devices can be manage in the range of specific SDN controller. To attain the resource management and flexibility benefits, many authors proposed the concepts of root controller and hierarchical controller. Energy consumption is a huge problem for companies around the world because of the need for continuous availability and the enormous architecture of IoT devices. Companies spend a huge amount of revenue to solve this problem of energy consumption. One solution is SDN, which can reduce the consumption of overall energy. The programmability, openness, and feasibility of SDN reduces the implementation complexity for software and hardware. It is a candidate by which we can limit our resources, and reduction in resource usage in turn reduces overall energy consumption.
Energy-saving techniques and power-saving schemes can be applied to reduce energy consumption. Energy consumption is not consistent at all times. For example, during the day, Internet traffic is high while at night, traffic is significantly reduced. In scenarios with low Internet traffic, most of the nodes are unutilized. Flexible programming in SDN can solve this problem and can make intelligent decisions according to the situation of the traffic. Unutilized nodes can be sent to sleep mode while the activation period in network for the nodes can be defined through SDN. A content-based method can also be a solution for SDN resource management. This method ensures reduced power consumption with proper resource utilization because content length can be known to the forwarder in NDN and ICN, so the required resources can be delivered to the most fitted nodes. Named data networking can also be beneficial to the SDN–IoT combination. Load balancing and flow management techniques in the SDN can reduce overall energy consumption. Traffic management based on information from the nodes and switches can reduce collisions of interest and data packets. Constant and timely updates to the SDN controller about energy consumption and resource allocation can enhance network performance against energy consumption, interest satisfaction rate and network life time. Finally, the combination of SDN and IoT with NDN can be a great addition to research advancements and the development of science because of their fruitful results.
4. Related Work
Current NDN architecture updates its FIB using flooding mechanism. Software defined networking based NDN architecture reduces the effect of such problem on consumption of network resource. An SDN-based routing scheme (SRSC) in Reference [
12], also proposes a NDN-based forwarding scheme over SDN. Then a control process controls and manages the FIB with the help of an SDN controller at the node level. Controller announcement and neighbor discovery are the two phases at the controller level. In this routing protocol, flooding is used to forward packets. This scheme has no efficient forwarding mechanism but has a controller attachment only.
A controller-based routing strategy for NDN (CRos-NDN) in Reference [
13] is another SDN controller–enabled scheme. The aim of CRos-NDN is to define specific procedures and names for efficient forwarding. It consista of two processes, bootraping and named data routing. During the bootstrapping process, a hello packet is transmitted across the whole network. Nodes connect with the controller after recognizing it. Neighboring routers acquire information by sending an interest packet. The routing step gives permission to fill the FIB nodes, which then send the packet as relay nodes. CRos-NDN improves the mobility efficacy.
In Reference [
14], NDN improved the forwarding process with topology discovery and the management of tables. It used all three tables: CS, PIT, and FIB. It is a waste of time if there is no name prefix in the CS when dealing with huge tables. Named data networks improve the forwarding mechanism by adding the FlowFIB table, which minimizes the access number for prefixes and tables. There are two types of action, local and external, after redirecting the interest toward FlowFIB. Local action is all about the existence of a prefix in the CS. External action refers to the port that follows the forwarding process after prefix matching. Named data networks resolve problems like consumption of bandwidth, scalability, and delay. IT outperforms SRSC and CRoS-NDN. The above discussed forwarding strategies do not handle the priority packets, communication, or energy consumption of sensor nodes. There is no efficient forwarding model in the above discussed strategies.
Adaptive forwarding based link recovery for mobility support (AFIRM) in Reference [
23] is an efficient novel solution for mobility issues among producers and makes the data availability more effective. The focus of AFIRM is on data availability requirements.
Markov Decision Process Based Interest Scheduling (MDP-IOT) in Reference [
29] is an efficient technique to satisfy IoT applications that are delay intolerant. In this scheme, the interest schedule moves towards the right interface with low latencies after prioritizing the IoT traffic that results in less RTT.
Controller based Selective forwarding (CSF) in Reference [
15] is an efficient scheme to mitigate the broadcast storm problem using forwarding flows calculated in SDN controller. Consumer nodes can request these forwarding flows whenever needed, and only selective nodes perform forwarding instead of the native flooding mechanism. Broadcast Storm Avoidance Mechanism (BSAM) in Reference [
16] is a distance based forwarding mechanism that controls the packets propagation using controller. Each node calculates a counter value by calculating its distance from a sender node. The farthest node will then forward the packet. SDN controlled VNDN in Reference [
17] is an efficient forwarding mechanism that uses SDN controller for greater view of network for user. Packet classification triggers the Emergency packet dissemination. Road side unit has been equipped with Policy based bifold classifier for packet classification. Hybrid swarm optimization and cuckoo search algorithms are used for the best path selection. In Reference [
30] an SDN aided forwarding strategy in ICN is presented that copes with the mobility issues and dynamically updates the controller whenever a consumer or a producer detaches from the network.
SD-EAR in Reference [
18] is an energy efficient software defined forwarding mechanism. In the mechanism, network is divided in multiple clusters, controlled by SDN controller. Each controller already knows the topology inside the cluster zone. Outside the cluster, SDN is in the charge of controlling nodes to send their packets. SDN controller discovers the optimum energy efficient path after checking the residual energy of the nodes and flow tables. In this paper, a sleeping mechanism has been used for the exhausted nodes.
GIF in Reference [
19] proposes an energy efficient forwarding strategy. Sink nodes are used to keep record of neighbor ID, position and remaining energy of all the nodes in cluster. In this scheme, the sink node having more resources than the sensor nodes, but, the high loads in the sink node results in the more energy consumption and eventually in the death. Such sink nodes’ death causes to path loss and packet drops. There is no such criteria to prevent the energy of sink nodes, having most of the information of the cluster that will cause serious management problem.
The DMIF in Reference [
20] comprises of two collective forwarding modes, in which several energy efficient mechanisms including flooding scope control, flexible mode shift, packet suppression, broadcast storm avoidance and energy weight factors are designed to balance and save the energy consumption.
5. Problem Statements
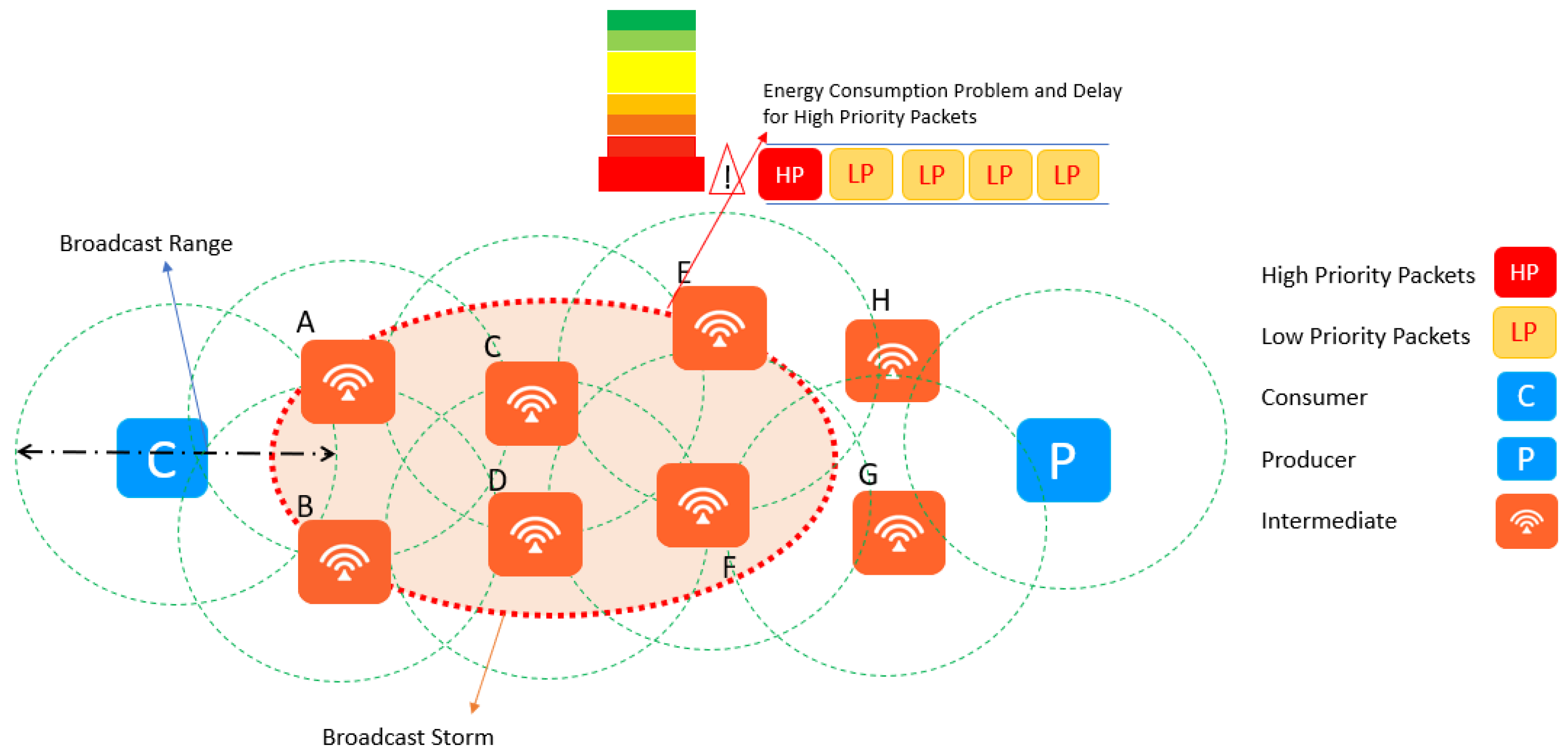
In this section, problems in wireless networks, IoT, and NDN are discussed. These problems include broadcast storms because of the flooding nature of wireless channels and NDN. Energy problems, which cause a decrease in network performance, cost and delay important packets, are discussed as well. Some NDN-based IoTs can take befit from the broadcasting nature of NDN and the wireless medium to propagate interest packets. More than one neighboring node can listen to the packet transmission of an interest. These neighbors are the possible relay nodes and intermediate forwarders. These multiple forwarders increase the probability of packets being forwarded to the producer. The way content is requested, and the broadcast nature of the wireless medium, imposes challenges to the deployment of NDN-IoTs, particularly the “broadcast storm problem.” For NDN, after an interest is transmitted and received by neighbor nodes, the nodes will repeat the same process. Nodes are equipped with one wireless interface. In this scenario, the same interface is used to forward the packet, and all the nodes that are in the transmission range will receive the packet, even the nodes that have already received it. This leads to the broadcast storm problem. In this case, the consequences increase collisions and medium access time. Nodes using the same path can collide. The broadcast nature of NDN makes it even harder for the development of NDN based IoTs.
Figure 6 shows the scenario of broadcast storm problem. In our scenario case, C (consumer node) broadcasts an interest packet to P (Producer node). Node A and B receive the interest and broadcast it further. Then all the other nodes, C, D, E, F, G, and H receive the interest and broadcast the same request in the network in same manner that causes a broadcast storm issue.
Energy is one of the most critical aspects in real deployments of sensor networks and IoTs. A sensor node participates in sensing, processing, and communication subsystems. Optimization of energy consumption in sensor networks is generally a hard task, since it effects on maximizing the network life time along with reduction in energy consumption. The minimizing of sensor networks’ power consumption is becoming increasingly significant, especially in situations where many countries are independently developing programs to improve the efficiency of power networks and power supplies. The energy efficiency and power consumption of various devices are defined in several different conditions of work. In the case of load applications, it would imply efficiency at different levels relative to the rated power of the device. The energy consumption of the sensor nodes largely depend on protocols the sensors use for communication.
In an IoT system, the access communication of the regular and periodic interest and data packets sensed and sent by the sensor nodes can consume most of the energy and resources of the sensor nodes and network [
31]. In fact, in IoT scenarios, the less important regular sensing data flow regularly in access in the network and probability of emergency data with high priority is very low. This scenario can be a problem for the high-priority and reactive interest packets and data packets. So efficient routing and forwarding mechanisms are needed to preserve the energy and power of sensor nodes, enhance the network’s lifetime, minimize the overall energy consumption, and improve overall network performance.
Figure 6 shows the sensor node’s energy problem. In our scenario case, consumer node C broadcasts a less important interest packet to producer node P. Nodes A and B receive the interest and broadcast again. Then nodes C, D, E, F, and G receive the interest and broadcast the same request in the network. The communication of the less important packet consumes the energy of the sensor node. When a high-priority packet arrives, the node energy of E goes down very critically because the regular flow of low priority packet consumes most of the energy of the node. Hence, the packet faces a path loss or packet drop issue. Large data packets create an unacceptable delay for important packets because of the head-of-line (HOL) problem. The broadcast storm problem caused by the broadcast nature of wireless networks as well as the NDN forwarding model and the energy problem caused by the access in periodic movement of unimportant sensed data can be harmful to the in-time, efficient, and fast forwarding of the important, high priority, and emergency interest and data [
22].
Figure 6 show the delay problem in which low priority packets create the delay problem for high priority packets on node E. The emergency and critical messages have higher priority than a chat between friends or the regular patterns of the traffic.
6. Energy-Efficient, Priority-Based Forwarding (EPF)
To cope with the broadcast storms and communication delays in the network, and to improve overall energy consumption, an Energy efficient Priority based Forwarding strategy has been proposed in this paper. Two main architectures are presented in our system model: 1. Node side architecture and 2. Controller side architecture.
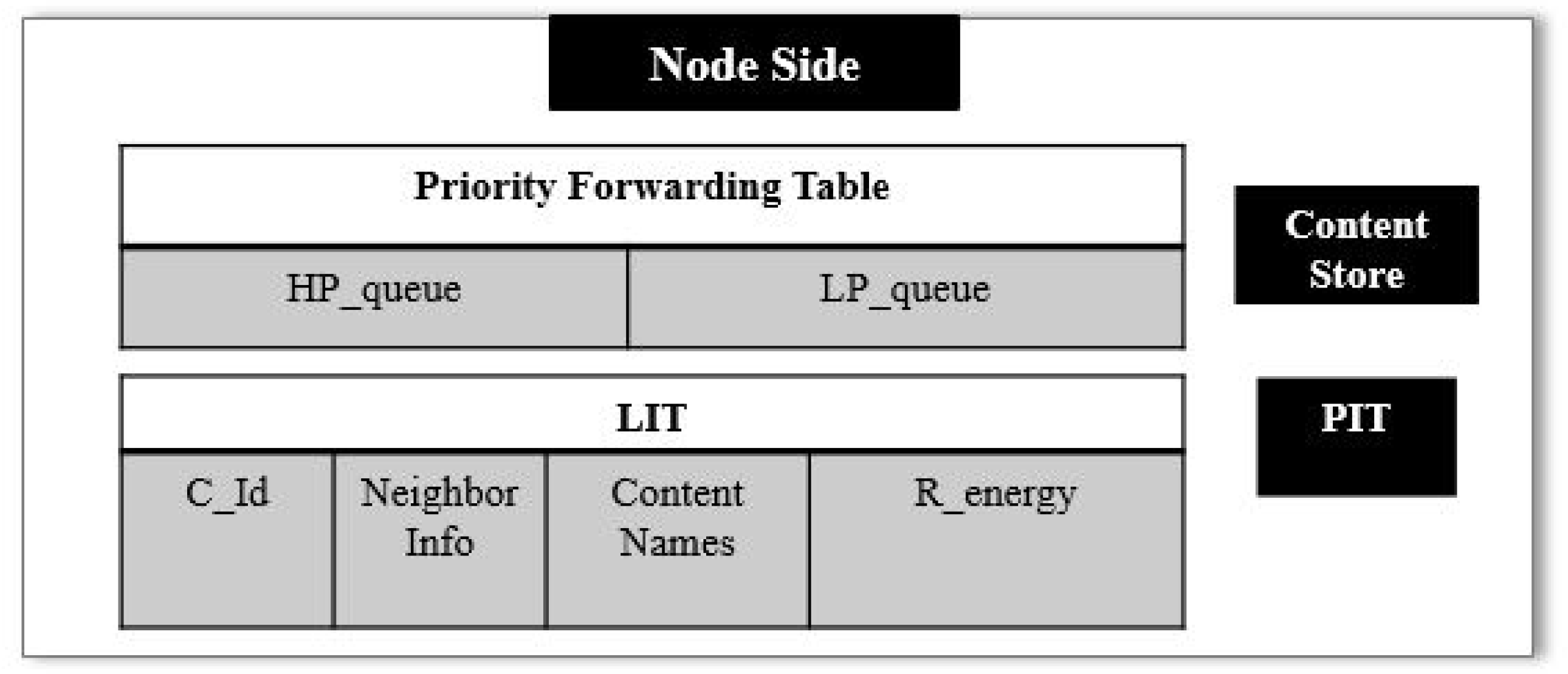
6.1. Node Side Architecture
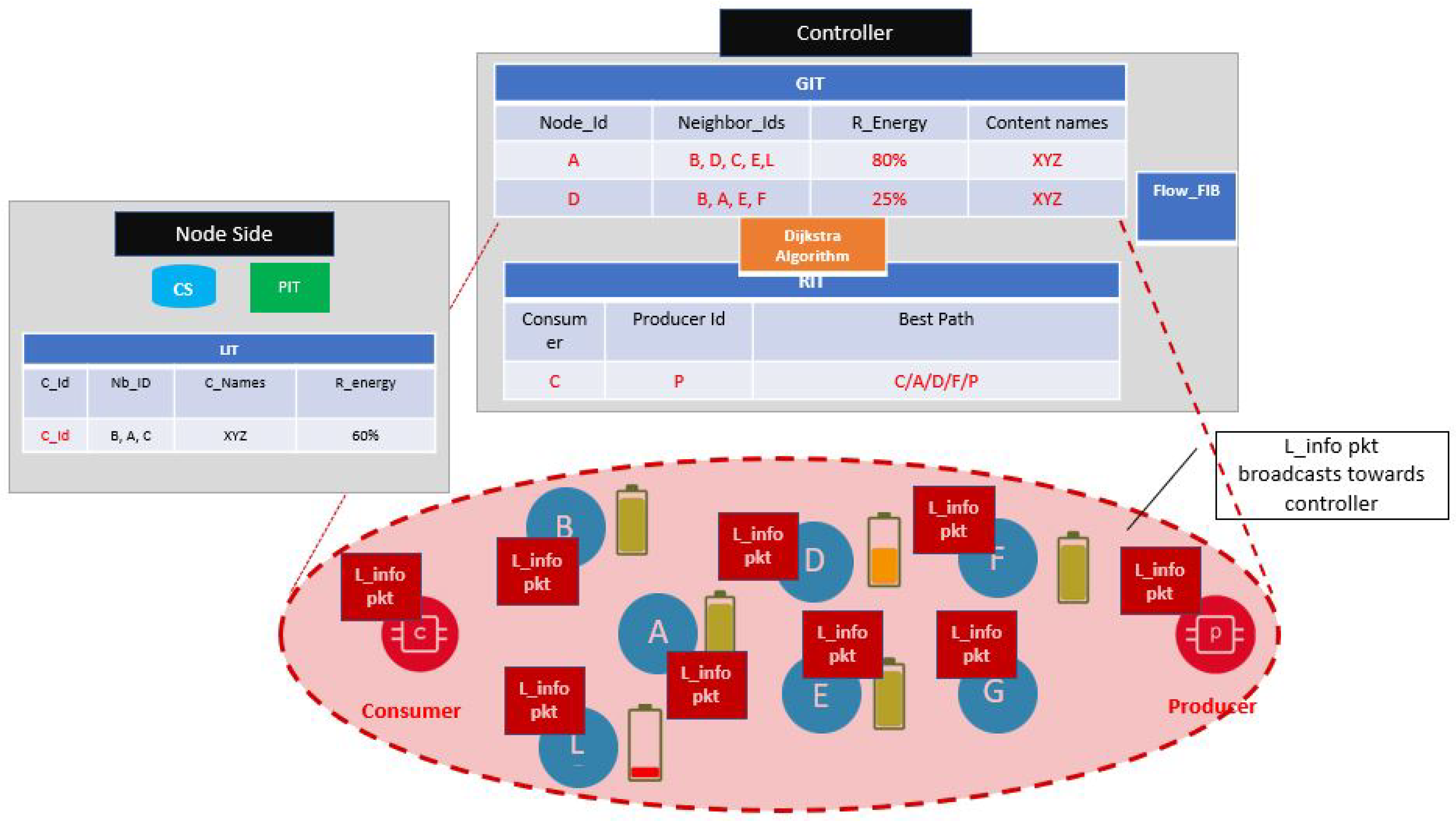
Like the traditional NDN architecture, Node side architecture contains CS that keeps the record of the content. The PIT keeps the information of unsatisfied packets. The additional part of EPF is its Local Information Table (LIT) and priority forwarding table. The LIT stores information of controller, neighbor IDs, residual energy and content names.
Figure 7 shows the node side architecture.
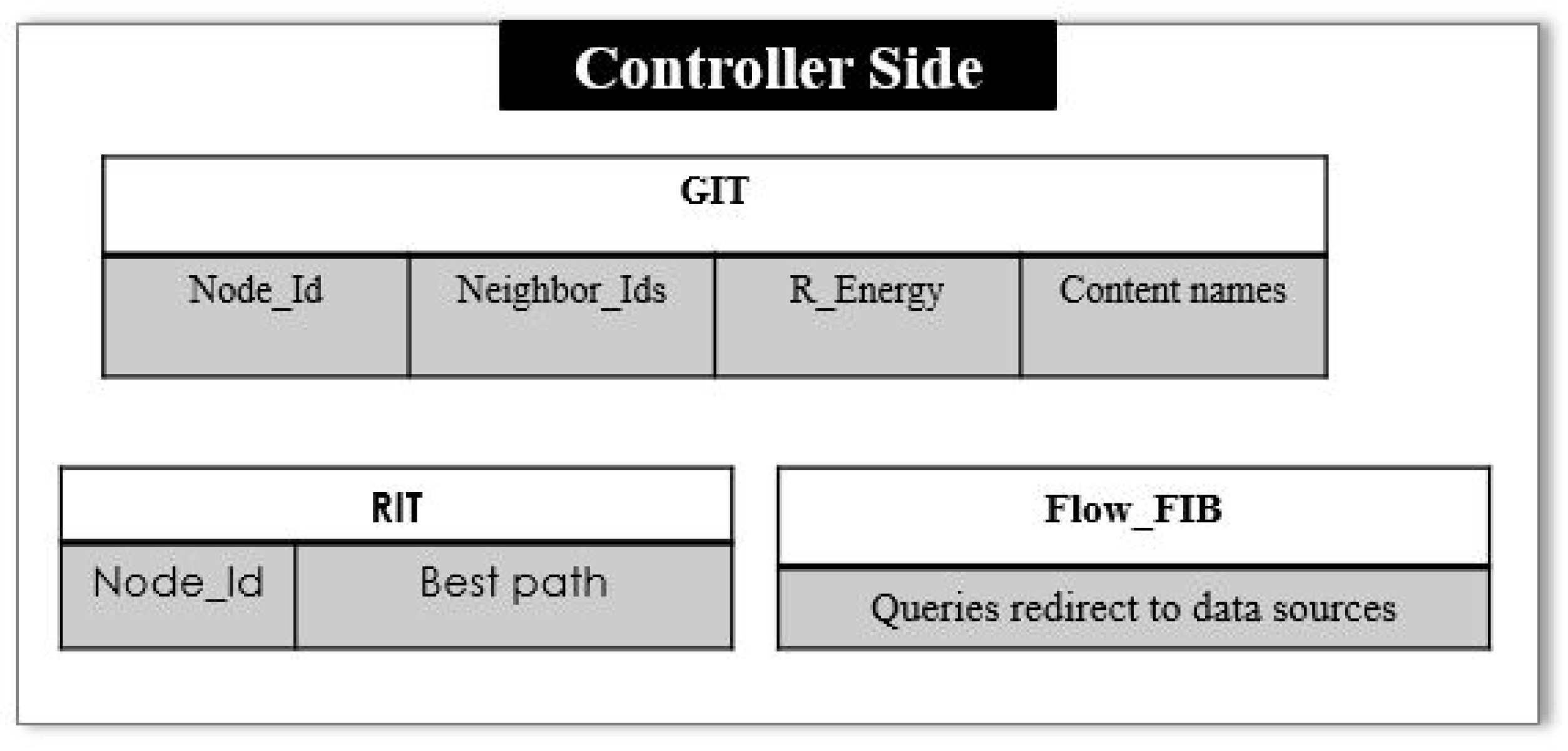
6.2. Controller Side Architecture
Controller side architecture in
Figure 8 consists of the Routing Information Table (RIT), FIB and Global Information Table (GIT). In the GIT, the entries are against each node’s ID, neighbor nodes, residual energy of the nodes, and content names presented in the CS. The RIT in the controller computes the best and the shortest possible path toward the producer node by keeping the track of the hop count to a minimum.
6.3. Packet Formats
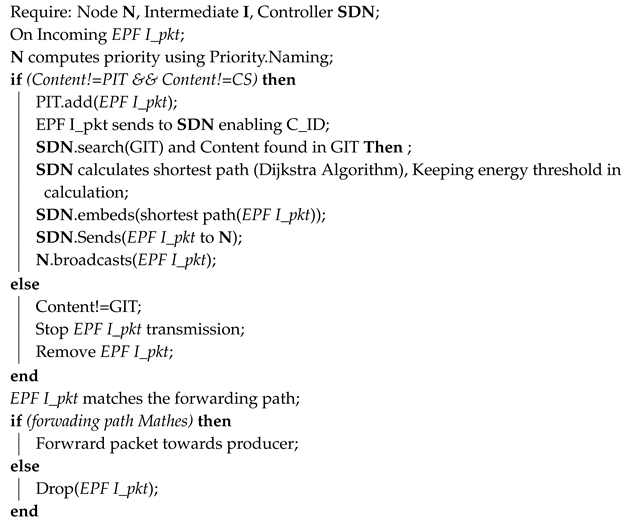
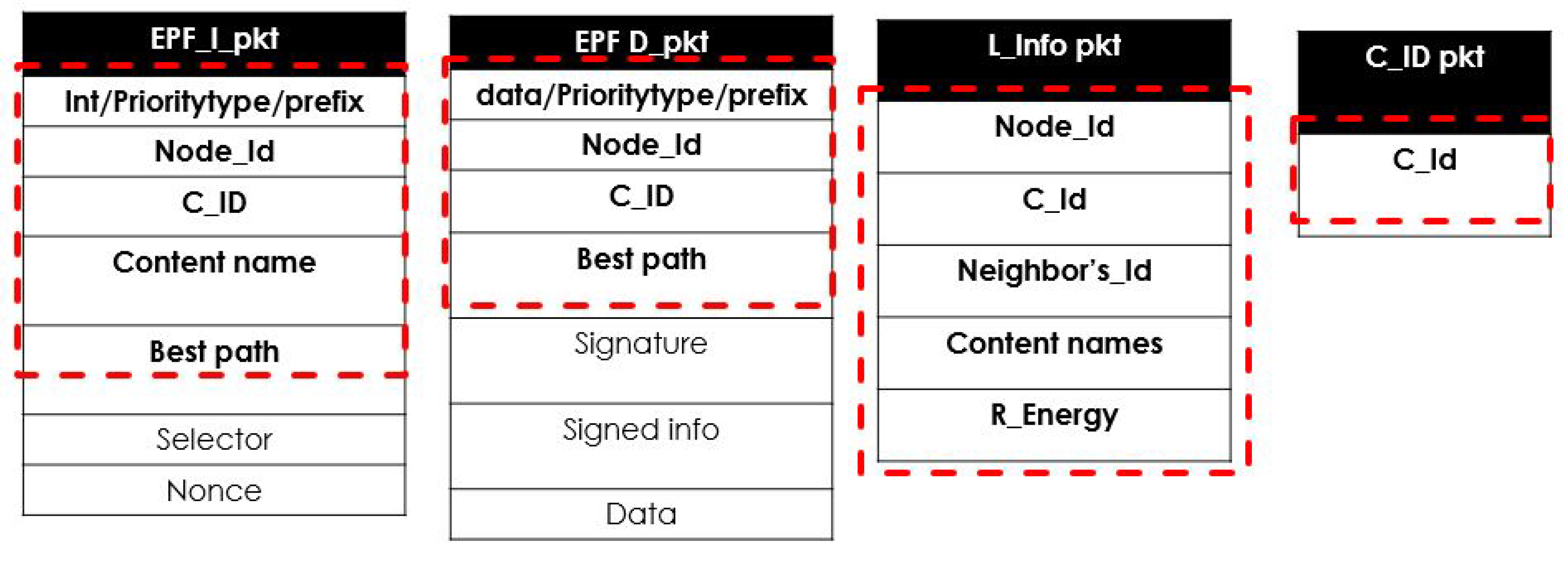
Four types of packets are used in the EPF. Controller ID packets (C_ID pkt) contain information on the controller ID. This packet is broadcasted once at the start of the topology. New nodes in the network can communicate with neighbor nodes and send their information to the controller node after syncing with it. Local information packets (L_info pkt) have information on the node’s ID, the node’s residual energy, and the content names, which are broadcasted to the controller node and neighbor nodes for the population of the GIT and LIT. Interest packets in EPF (EPF I_pkt) have a naming scheme in which some priority criteria is presented: the path information, requested content name, and the nonce for the unique identifier of the packet. Data packets in EPF (EPF D_pkt) have the same structure as EPF I_pkt with addition of Producer’s signature.
Figure 9 shows the packet formats for EPF.
6.4. System Model
6.4.1. Controller Announcement
When the network starts, the controller announces its presence in the network by broadcasting the C_ID pkt. All the nodes update their LITs after receiving the packet, as shown in
Figure 10.
6.4.2. Topology Discovery and Content Placement
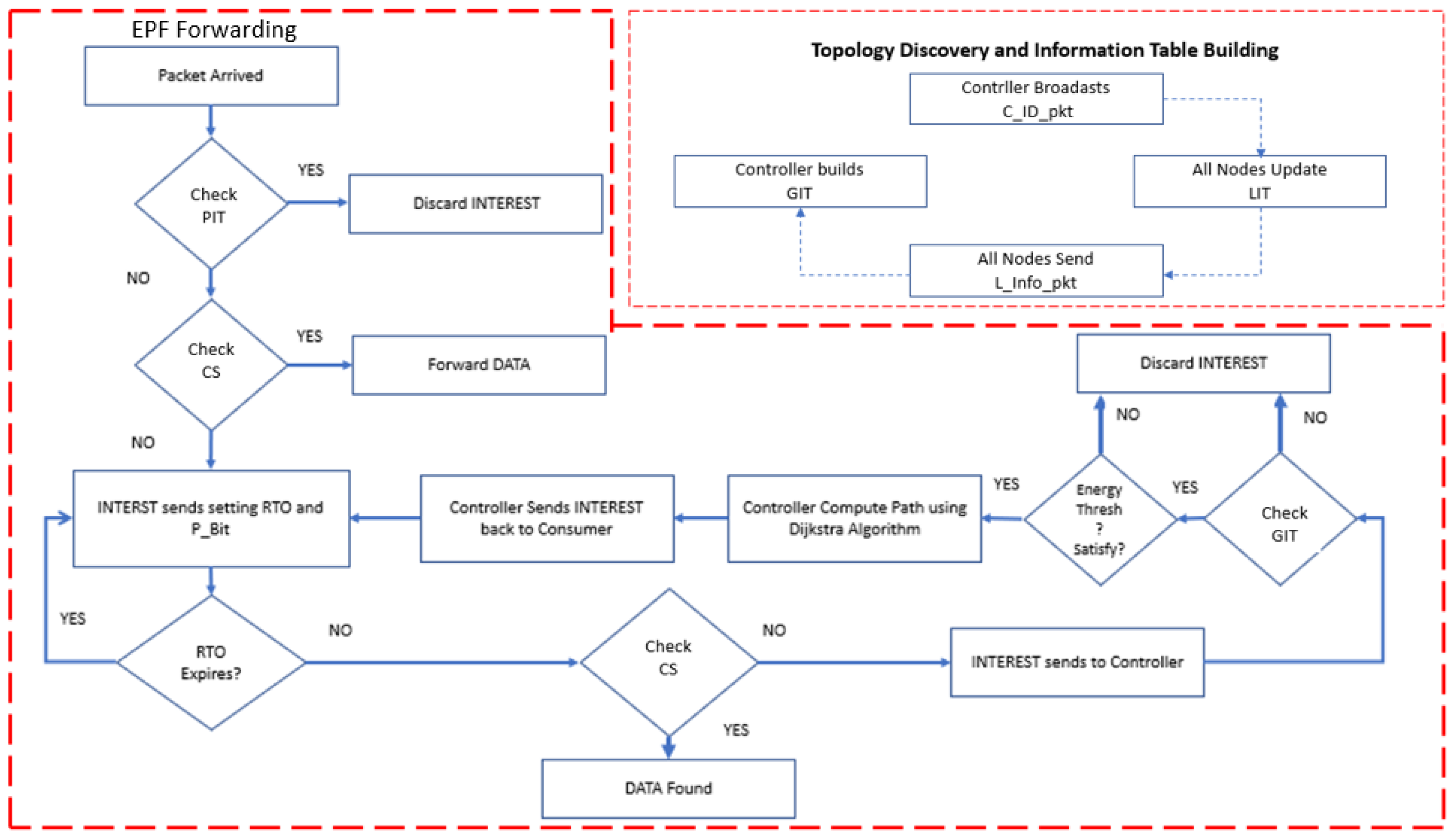
At first, All the nodes broadcast L_info pkt to their neighbor nodes (in one-hop network range) after controllers’ announcement with its ID. After updating LITs, all the nodes then send L_info pkt to controller having information of their content names, ID, neighbor ID and the remaining energy of the nodes by enabling controller ID. Controller then updates the table entries of its GIT using the information sent by each node in L_info pkt. After GIT setup, the actual forwarding mechanism starts. This whole process of topology discovery is presented in
Figure 11 and Algorithm 1.
| Algorithm 1: Topology Discovery and Controller Table Building |
![Applsci 10 07675 i001 Applsci 10 07675 i001]() |
6.5. EPF Forwarding Model
There are two communication modes in the IoT system discussed in earlier sections: a pull-based communication model that needs an interest request to respond with a data packet and a push-based communication model in which sensing nodes in the IoT system itself sense, collect, process and send data to the consumer without any prior request for that data.
When the consumer node sends an interest packet for content, the interest is sent to a neighbor node for content discovery and retrieval. The node matches its CS against the requested content. If data is found, the producer node sends data back to the consumer node. If there is no entry in the PIT or the CS, then the consumer node itself retransmits the packet to the controller to discover a producer in an efficient way. After receiving the interest packet, the controller checks its GIT for the matching content name and the producer of that content. After matching the content in the GIT, the controller computes the best possible and shortest path between the consumer and producer using the Dijkstra algorithm. In this computation, the controller verifies the residual energy of the potential forwarder with the content type and the active network status. The Dijkstra algorithm is the classical single-source algorithm that is always optimized in computation [
32]. After the computation and path establishment, the controller sends the packet back to the consumer node after embedding the path information in the packet. The consumer sends the interest packet to the producer, and every potential forwarder responds to the request after matching the path-naming scheme. All the nodes that do not match the path naming will drop the packet, while other nodes will send data back toward the consumer or forward the packet toward the next hop.
As discussed in detail, the regular and unimportant sensing data is much more present in the IoT environment than high priority and important data. Important information is rarely generated after time in the network, while the regular flow of the traffic in the IoT system can cause problems for the sensor node’s energy. Therefore, the arrival of high-priority information can be met with problems in in-time and efficient delivery. Government-related information, law enforcement agency-related information, high red-alert alarms, emergency situations, road accidents, and theft are scenarios of high priority; chatting, traffic patterns, and temperature are low-priority information. We categorized the five different types of data according to priority type in
Table 1.
Potential forwarders check the name embedded in an interest and data packet to differentiate the high and low priority packets. Naming schemes match the name in packet headers to the priority level, as defined in
Table 1. An energy threshold is set to achieve reliable transmission of high priority interest and data packets. We set the energy threshold value as 16%. Only high priority packets can forward through nodes beyond defined energy thresholds. GIT will update residual energy when the node’s residual energy reaches the threshold after getting information from L_info_pkt.
In our scheme, the priority mechanism is performed by using the timer-based rebroadcast mechanism for both interest and data packets. A defer timer value is set locally by each forwarder after evaluating the priority level that is embedded in packet header. The value of the timer is computed in a fully distributed way by each processing node without incurring any signaling overhead. Interest and data packet communication are described in Algorithm 2 and discussed above in EPF forwarding model.
| Algorithm 2: Received Interest/Data Packet |
![Applsci 10 07675 i002 Applsci 10 07675 i002]() |
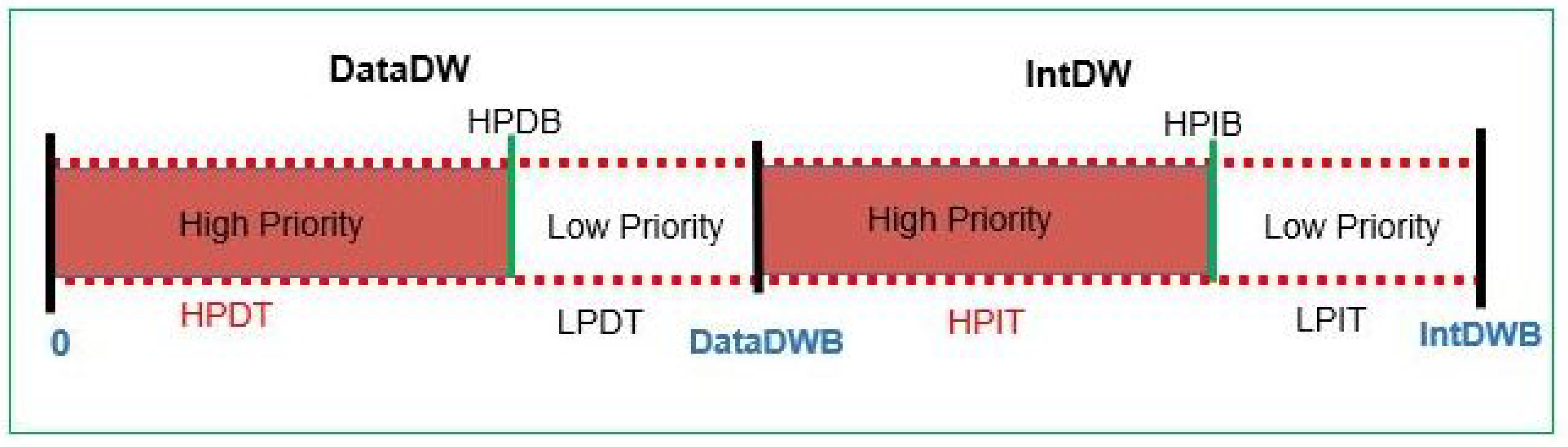
In order to assign priority to Data packets over Interest packets, two adjacent and distinct time windows are used to initialize the defer timers for Interest and Data forwarding. The above said time windows are Interest Defer Window (IntDW) and Data Defer Window(DataDW). The range of DataDW is [0, DataDWB] and range of IntDW is [DataDWB, IntDWB]. DataDWB and IntDWB are window bounds for DataDW and IntDW respectively. The sizes of DataDW and IntDW are set according to the the short inter-frame spacing (SIFS) and 802.11 slot time to adapt MAC dynamics quickly.
The aim of proposed forwarding scheme is to give High Priority (HP) Interest and Data packets, priority over Low Priority (LP) Interest and Data packets. For this purpose, we further split DataDW and IntDW into two separate sub-windows. In first sub-window of DataDW, only HP data packets can communicate using high priority timer (HPDT) in range of [0, HPDB]. The transmission of LP data packets will take place in second sub-window by selecting low priority timer (LPDT) in the range of [HPDB, DataDWB]. In IntDW, we used same mechanism in which only HP Interest packets can transmit using high priority timer (HPIT) in range of [DataDWB, HPIB] and LP Interst packet transmission will take place in second sub-window by selecting low priority timer (LPIT) in the range of [HPIB, IntDWB]. HPDB and HPIB are the bounds for high priority data and interest packets respectively. The complete defer window mechanism described in
Figure 12.
This is the responsibility of each node to compute HPDB and HPIB dynamically according to the overheard traffic load for each priority level. To compute HPDB and HPIB, each node used to keep the track of total received data bytes of HP and LP. RHP and RLP are the total number of high priority and low priority bytes received. Any node can easily infer the RHP and RLP from packet-size field in NDN packet’s header. The bound between high priority and low priority (data packets and Interest packets respectively) in DataDW is dynamically computed as:
Higher number of HP results in higher HPDB and HPIB. We can compute the LPDB and LPIB analogously. After computation of defer window bounds each node needs to calculate (HPDT, HPIT, LPDT and LPIT for high priority and low priority Data and Interest packets respectively), whenever a node wants to forward the packet. If we use the aforementioned defer timer scheme then we can forward the high priority data and Interest packets earlier than the low priority ones. This mechanism reduces the unnecessary delay in forwarding of high priority packets.
Figure 13 shows the Complete Forwarding flow of EPF.
7. Simulations and Results
In this section, we presented a brief discussion about comparative schemes and simulation results. We evaluated the simulation under different performance metrics and simulation parameters. We compare our work in EPF with GIF and traditional flooding in NDN and evaluate the performance of our scheme. Selection of the best suitable threshold value for energy efficient strategy has also been presented in this section. We compared our scheme with an efficient forwarding scheme named Geographic Interest Forwarding (GIF) [
19]. In GIF, the support for Push based traffic is provided for NDN-IoT environment. Forwarding strategy in GIF is designed to enhance the network performance in term of energy consumption and scalability of sensor devices in IoT environment. In this scheme, the sink node having more resources than the sensor nodes, but the maximum load on the sink node results in the resource consumption. Whenever a node sensed some data, after Producer table entry in sink node, the push based forwarding consume a lot of energy. Sensor nodes can die very early in GIF because of the regular passing of the interest and data packet. Path loss issue can be there because of the dead sensor nodes. If the sink node will die and consume its energy then there is no criteria to preserve recent entries in the sink node and define another sink node. This paper is the most relevant to our proposed EPF. There are papers that discuss controller-based forwarding, but there is a lack of papers in the IoT domain that handle SDN controller-based communication with NDN-enabled communication. Some papers present the architecture of SDN-enabled communication, but still do not describe a forwarding mechanism. Others provide forwarding schemes related to SDN–IoT but in VANETs related IoT, not for WSNs and IoT. For the comparative study and analysis, we selected the GIF scheme because it was the most relevant to our simulation parameters and provided us with a broader and clearer view of the results of our scheme.
7.1. Simulation Model
The aim of the simulation is to evaluate whether the EPF based on the SDN–NDN–IoT system can provide us with better results in terms of network efficiency, efficient forwarding, and energy consumption of sensor nodes. To that end, the implementation of our code is in ndnSim and evaluation of EPF is with the GIF and native-flooding mechanism of NDN. In our simulation environment, IEEE 802.15.4 MAC protocol used. We deployed sensor nodes in a lattice and grid topology. The grid size is 10 × 10 nodes. The transmission range of each node was 100 m. The transmission network range was 1000 m × 1000 m. We evaluated our simulation results over an average of 20 independent runs and computed the results after that. For energy related computations, energy model of NDN is used in the simulation scenario. The initial energy of the nodes was 50 joules. Implemented simulation parameters are shown in
Table 2.
7.2. Performance Metrics
To evaluate the simulation, six different performance metrics were used in our results:
Total number of interests (NI): The total NI packets transmitted in the network from the consumer side.
Number of high-priority interests (HPI): The total number of high-priority interests successfully communicated in the network.
Total number of Retransmissions (RTx): RTx shows the total number of retransmitted interest packets.
Average energy consumption (AEC): The average power consumption of all the sensor nodes in the network.
Content retrieval time (CRT): The time it takes for the consumer to send an interest and receive data.
Network lifetime (NLT): The time when the first node dies in the network.
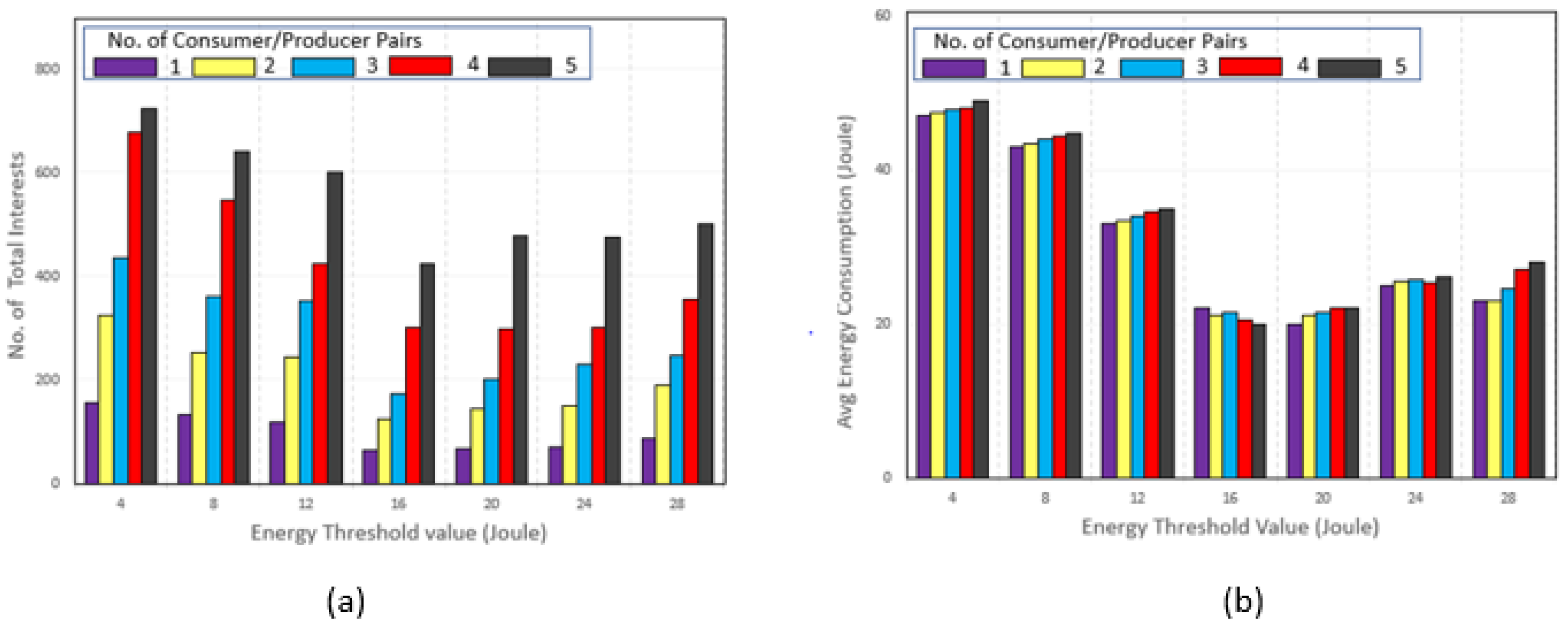
7.3. Threshold Selection
In our scheme for energy efficiency, an energy threshold value that is, 16% has been set to limit access transmission of the unimportant and periodic network packets. In this section, we analyze different threshold values for the sake of selecting a threshold value with the improved results in NI, retransmissions, dead nodes, overall AEC, interest satisfaction ratio. and priority interests. We selected the values 4, 8, 12, 16, 20, 24, and 28 as threshold values to identify the best threshold value. The gap between the values is four so that we can analyze the results better. A smaller gap between threshold values would not permit significant analysis. We analyzed the threshold value with different threshold and a different number of consumer–producer pairs. The main idea to increase the number of consumer–producer pairs was to increase the traffic rate in the network and the flow of different types of traffic so that we could analyze the threshold results better.
Figure 14a shows an analysis of the total NI in the network. As the threshold value increases, the value of the total NI decreases gradually. Due to the threshold value, we limit the interests with low priorities. So, the low-priority packets less than the threshold value could not pass through the network. The interest rate increased with the increase in consumer–producer pairs. The lowest value of the threshold value was 16%, but as the threshold value increased from 20 due to an increase in retransmission interest, the total NI also increased.
Figure 14b shows an analysis of the AEC in the network. The average consumption of the nodes’ energy was high with a low threshold because of the excessive transmission of low-priority packets. With a threshold value of 16%–20%, AEC was lowest. With increase in threshold value, an increase in AEC occurred because of packet retransmission. The NI packet was smaller, with a threshold value of 16%, which resulted in fewer retransmissions of the packet. These two factors resulted in fewer dead nodes, and the energy consumption was also limited to the threshold selection. After evaluating and analyzing different threshold values with different evaluation parameters, threshold value of 16% gives us better results in almost all the evaluation comparisons. Therefore, we selected the threshold value of 16 for our energy efficiency scheme.
7.4. Simulation Results
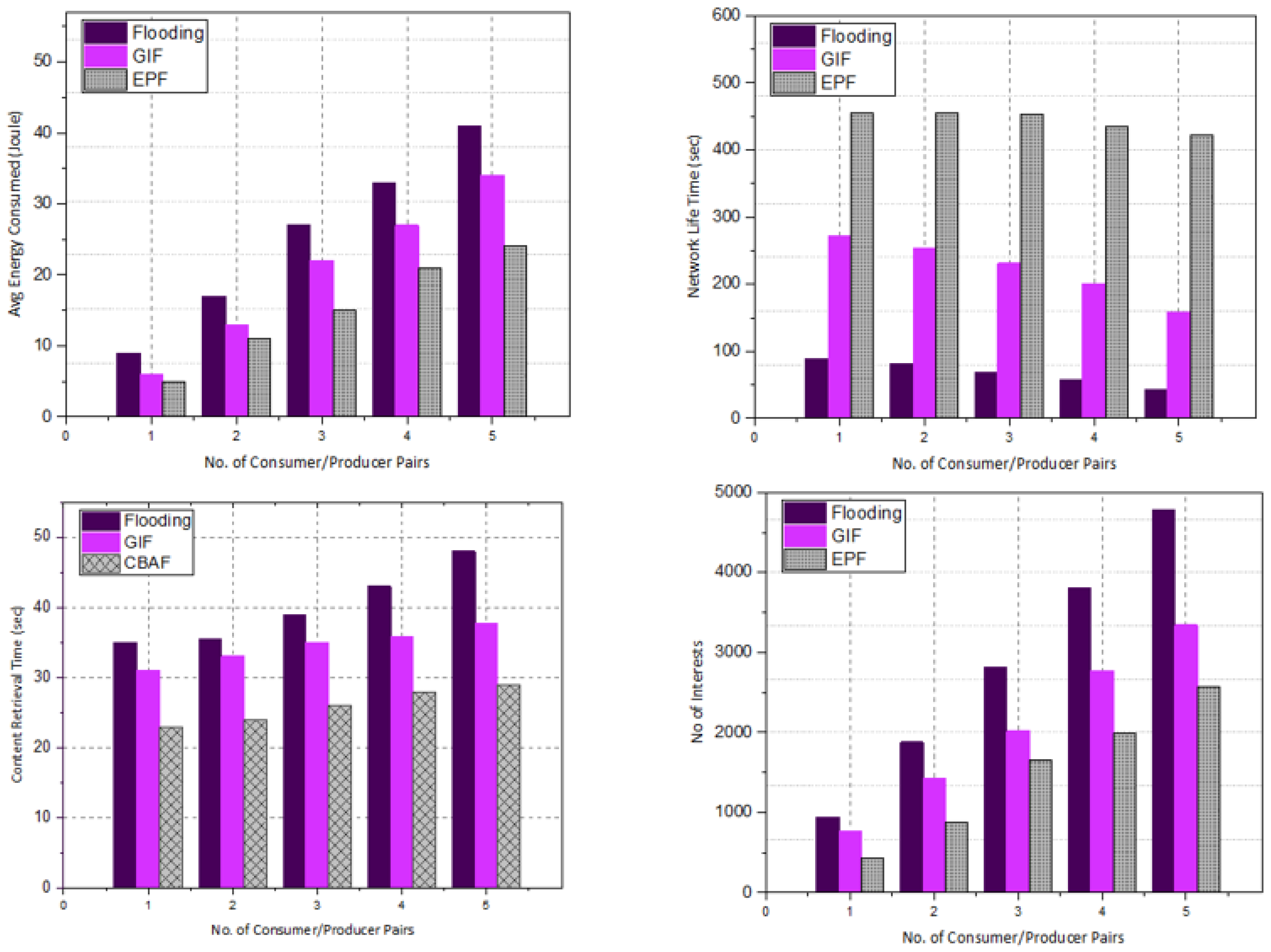
Figure 15 shows the performance analysis of CRT, NI, AEC, and NLT against one to five consumer–producer pairs. The value of the x-axis is consumer–producer pairs; y-axis values are CRT, NI, AEC, and NLT. This performance graph illustrates that the performance of EPF was better than the performance of GIF and flooding. The value of CRT also increased with more consumer–producer pairs because of the access in traffic load and network congestion. The CRT of EPF was lower than GIF. The NI and AEC in EPF were less than both comparative schemes because of efficient use of the SDN controller and energy-efficient forwarding. Low energy consumption led to lower NLT in EPF against GIF and flooding. The energy efficient mechanism based on threshold that prevents the node energy for high priority packets results in better performance as compare to flooding and GIF. Increased Consumer/Producer pairs results in more traffic in the network. Any potential forwarder with energy below the threshold value will drop the LP packets. Efficient energy consumption will lead to the better NLT. As, only HP packets can travel through the nodes with energy less than threshold value, so so the NLT will also increase. The proposed forwarding mechanism uses controller and energy efficient mechanism, that results in better CRT as compared to other schemes. Controller involvement makes sure the fast and in-time packet delivery. While the limitation on low priority packets also results in better CRT and NI.
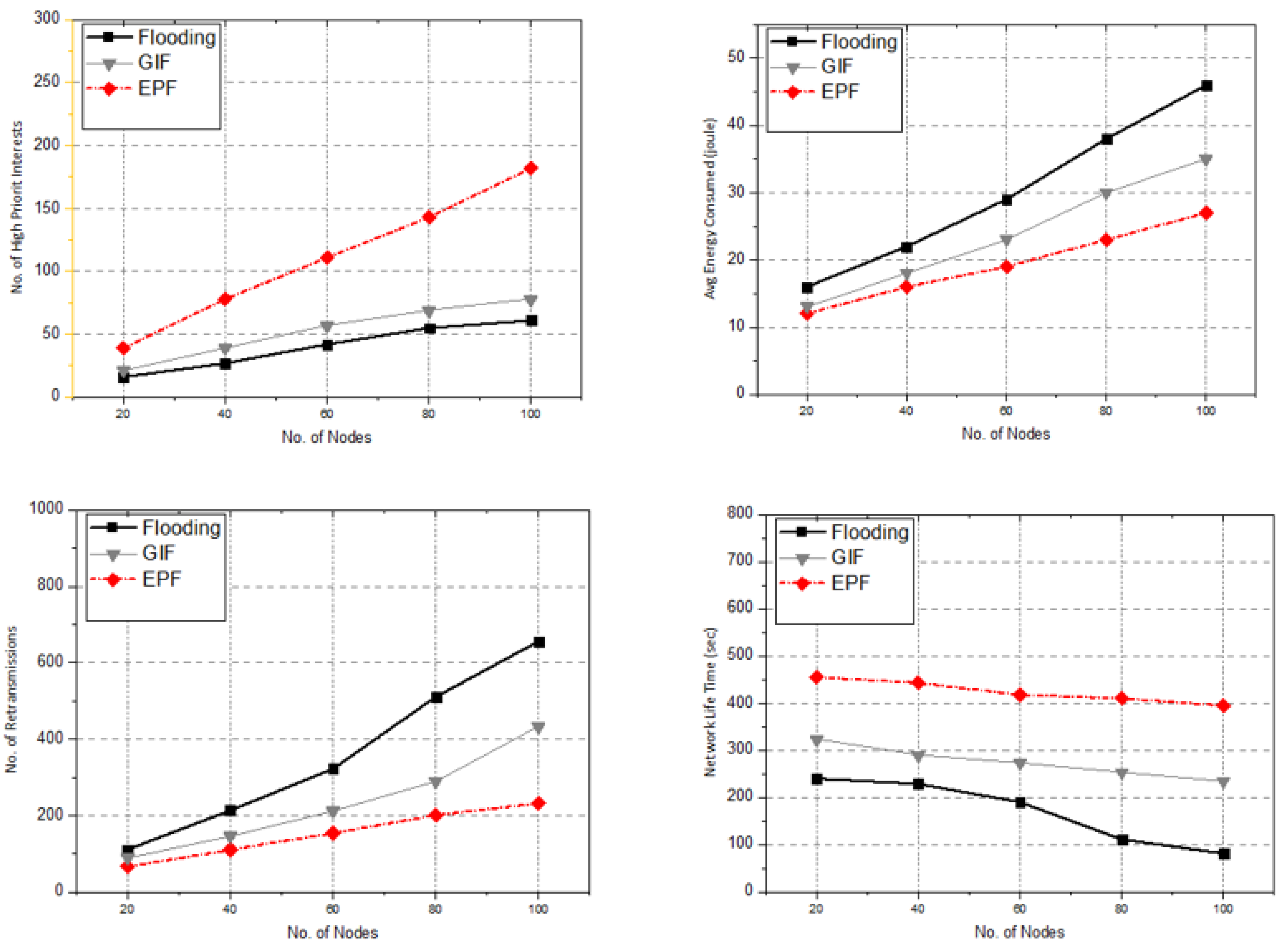
Figure 16 shows the evaluation of the performance according to the number of high-priority interests (HPI), number of retransmissions (RTx), AEC, and NLT against the number of nodes. The value of the x-axis is the number of nodes; y-axis values are HPI, RTx, AEC, and NLT. This performance graph illustrates that the performance of the EPF is far better than the performance of GIF and flooding. When the number of nodes increased, the value of the HPI increased in EPF because of the efficient priority forwarding mechanism. The priority interest satisfaction rate in EPF is far better than others, because of energy aware priority forwarding mechanism. Network availability is more reliable in EPF. In our proposed scheme, decreased NI and increased satisfaction ratio results in lower RTx in EPF than GIF because of the limitation on low priority packets and exact location mapping of the content through controller. The AEC in EPF is lower than both comparative schemes because of the efficient use of the SDN controller and energy-efficient forwarding. Low energy consumption led to lower NLT in EPF against GIF and flooding.