Biometrics Verification Modality Using Multi-Channel sEMG Wearable Bracelet
Abstract
1. Introduction
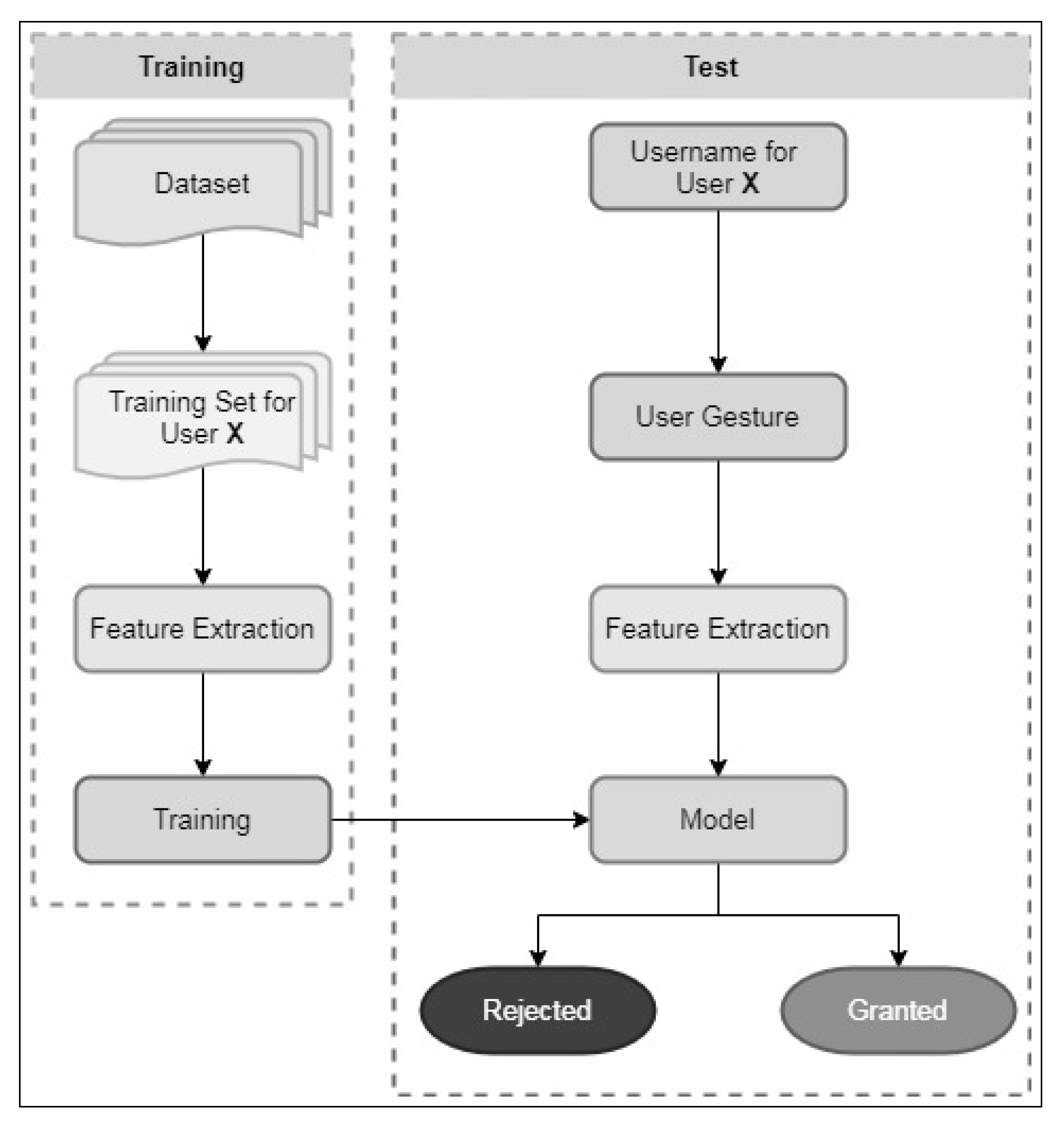
2. Methodology
3. Multi-Channel Wearable Armband
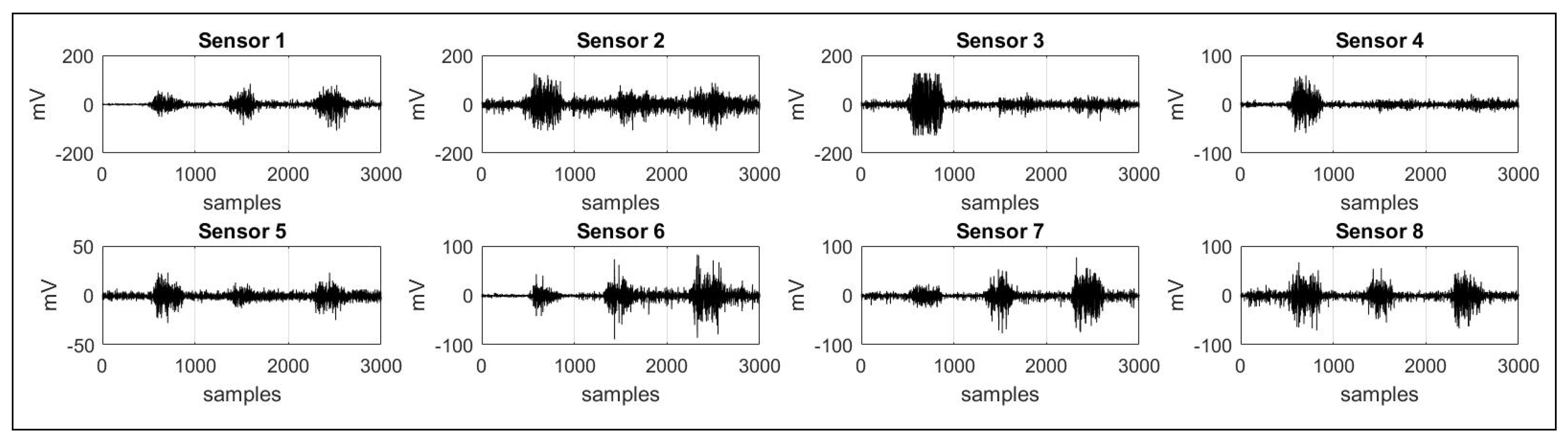
4. EMG Signal
5. Database
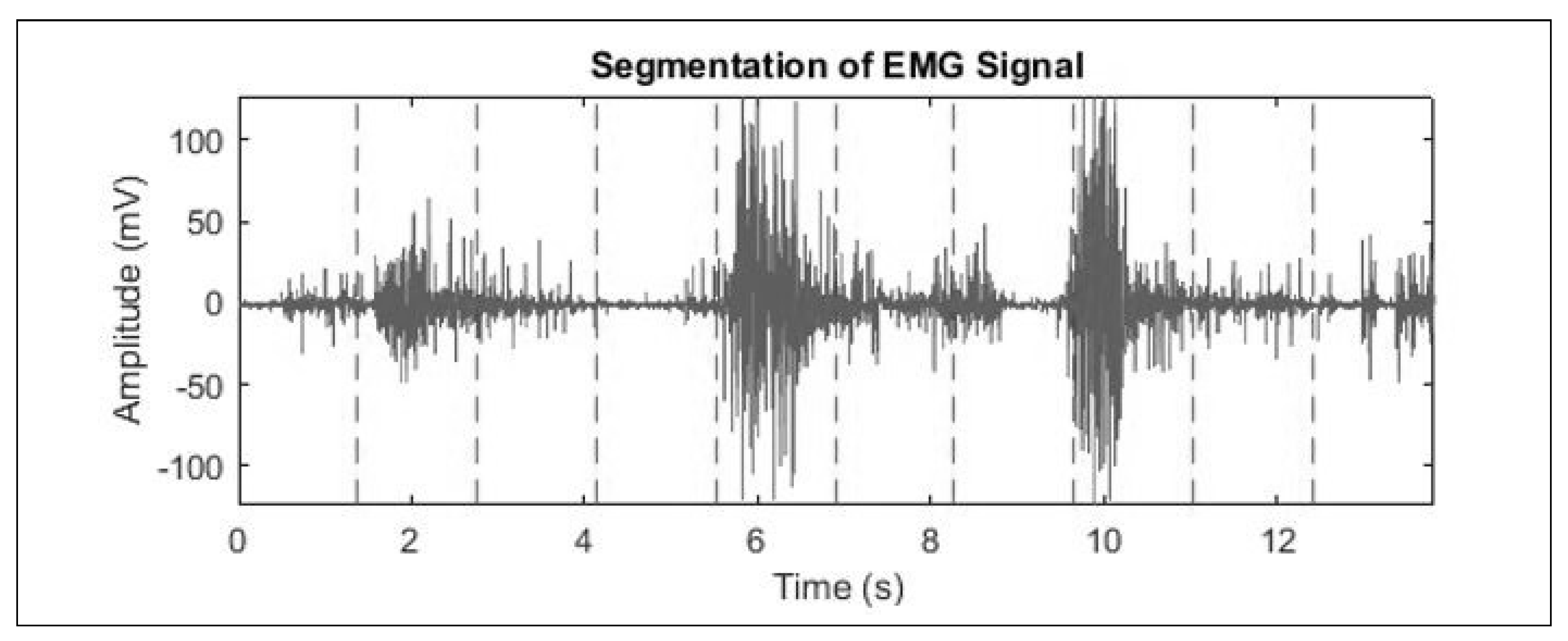
6. Features Extraction
7. Machine Learning Models
7.1. k-Nearest Neighbors
7.2. Linear Discriminant Analysis (LDA)
7.3. Ensemble Classifier (Gentle AdaBoost Algorithm)
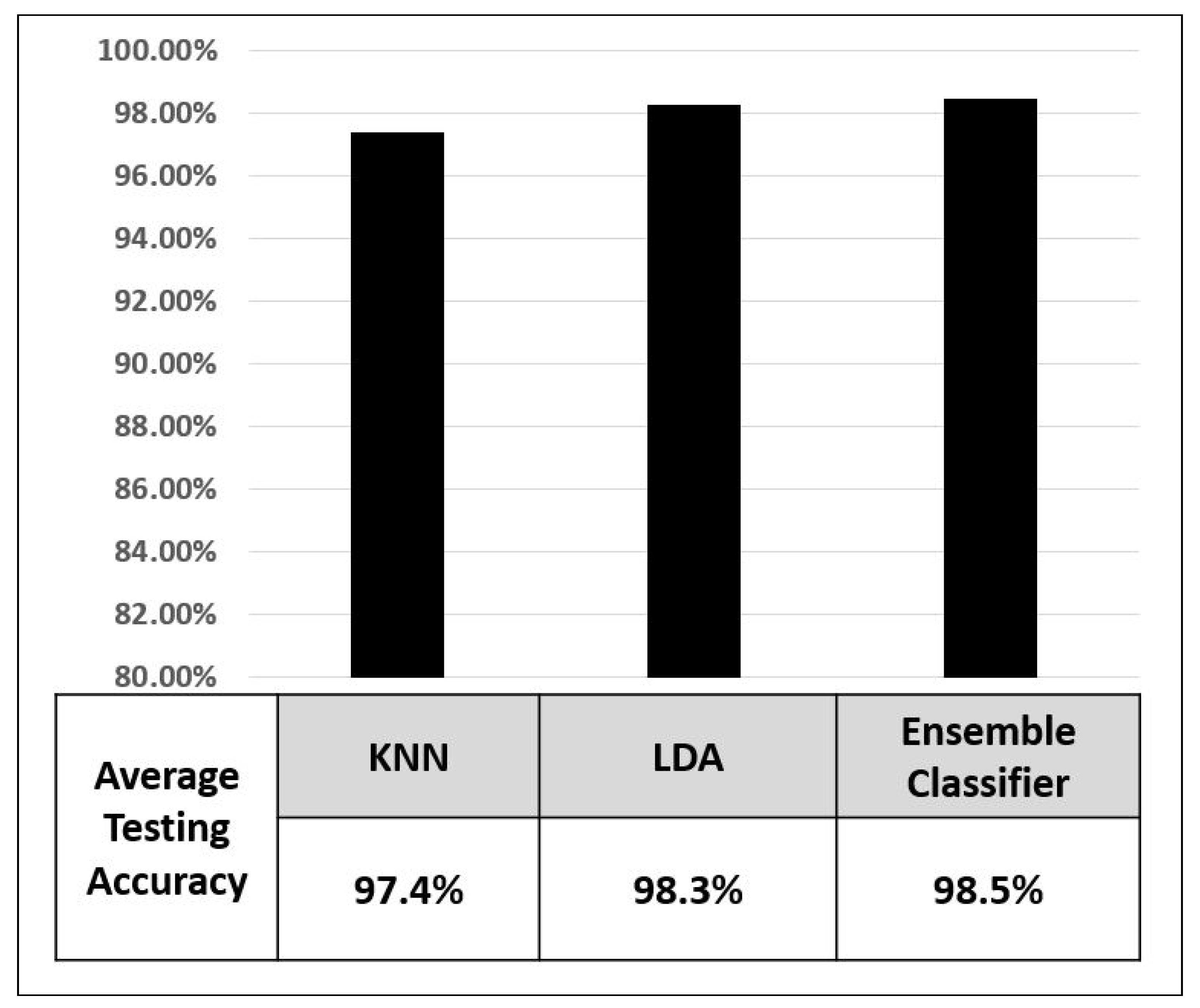
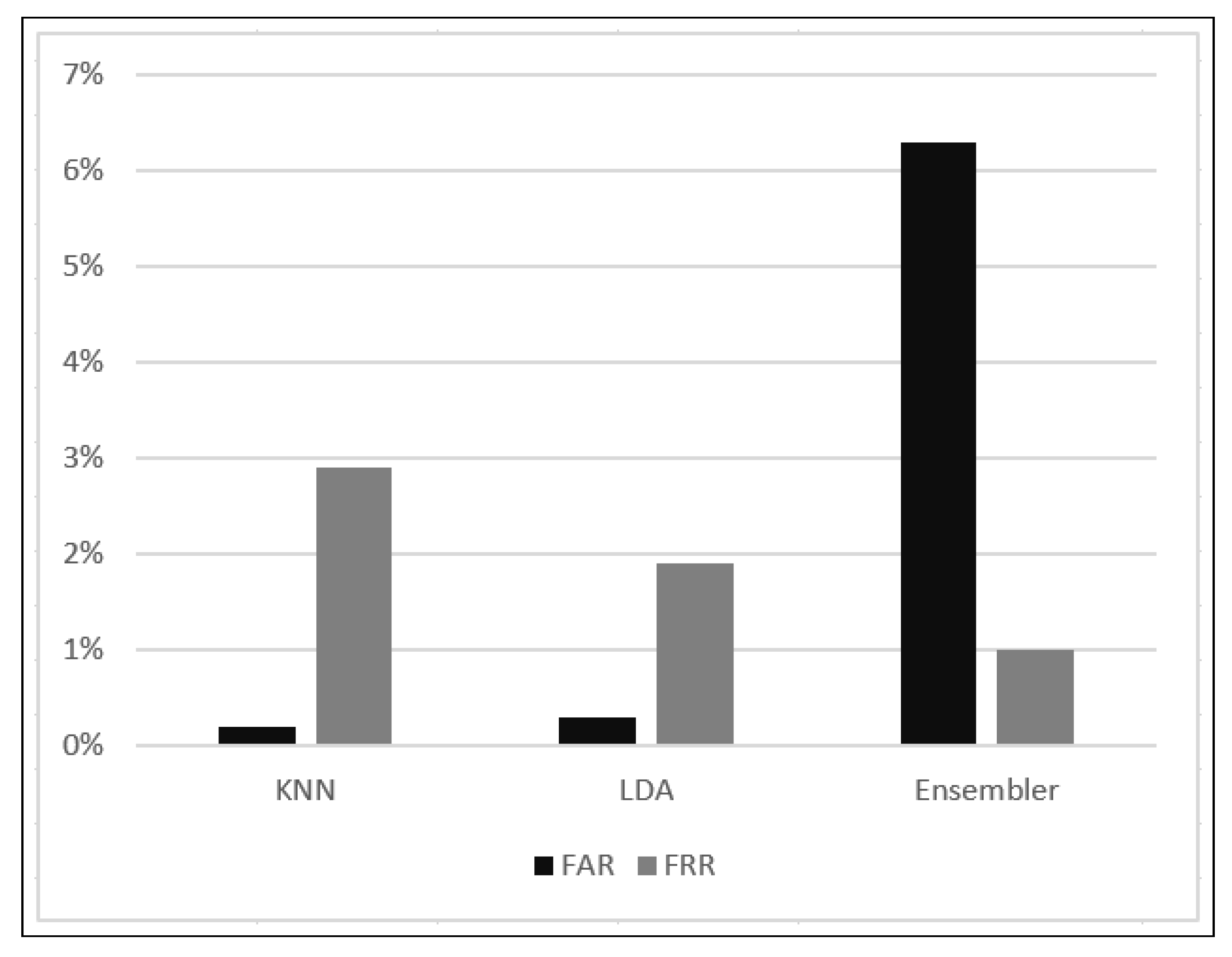
8. Results
9. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Enzo, V.; Scilingo, P. Recent Advances on Wearable Electronics and embedded computing systems for biomedical applications. Electronics 2017, 6, 12. [Google Scholar]
- Blasco, J.; Chen, T.; Tapiador, M.; Peris-Lopez, P. A survey of wearable biometric recognition systems. ACM Comput. Surv. 2016, 49, 1–35. [Google Scholar] [CrossRef]
- Said, S.; Al Kork, S.; Nait-Ali, A. Wearable Technologies in Biomedical and Biometric Applications. In Biometrics under Biomedical Considerations; Springer: Singapore, 2019; pp. 211–227. [Google Scholar]
- Kim, J.; Pan, S. A Study on EMG-based Biometrics. J. Internet Serv. Inf. Secur. (JISIS) 2017, 7, 19–31. [Google Scholar]
- Zhang, R.; Zhang, N.; Du, C.; Lou, W.; Hou, Y.; Kawamoto, T. Shoulder-surfing resistant authentication for augmented reality. In Proceedings of the International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Moon, K. Biometrics technology status and prospects. Internet Serv. Inf. Secur. 2005, 98, 38–47. [Google Scholar]
- Bailey, K.; Okolica, J.; Peterson, G. User identification and authentication using multi-modal behavioral biometrics. Comput. Secur. 2014, 43, 77–89. [Google Scholar] [CrossRef]
- Hadid, A.; Evans, N.; Marcel, S.; Fierrez, J. Biometrics Systems Under Spoofing Attack. IEEE Signal Process. Mag. 2015, 32, 20–30. [Google Scholar] [CrossRef]
- Evans, N. Handbook of Biometric Anti-Spoofing: Presentation Attack Detection; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Saponas, T.; Tan, S.; Morris, D.; Balakrishnan, R. Demonstrating the feasibility of using forearm electromyography for muscle–computer interfaces. In Proceedings of the 26th SIGCHI Conference on Human Factors in Computing Systems, Florence, Italy, 5–10 April 2008. [Google Scholar]
- Faragó, P.; Groza, R.; Ivanciu, L.; Hintea, S. A Correlation-based Biometric Identification Technique for ECG, PPG and EMG. In Proceedings of the 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 3–5 July 2019. [Google Scholar]
- Belgacem, N.; Fournier, R.; Nait-Ali, A.; Bereksi-Reguig, F. A novel biometric authentication approach using ECG and EMG signals. J. Med. Eng. Technol. 2015, 39, 226–238. [Google Scholar] [CrossRef]
- Shin, S.; Jung, J.; Kim, Y. A study of an EMG-based authentication algorithm using an artificial neural network. In Proceedings of the IEEE SENSORS, Glasgow, UK, 29 October–1 November 2017. [Google Scholar]
- Krishnamohan, P.; Holi, M. GMM modeling of person information from EMG signals. In Proceedings of the IEEE Recent Advances in Intelligent Computational Systems, Gerona, Spain, 11–15 July 2017. [Google Scholar]
- Al-Mulla, M.; Sepulveda, F. Novel Pseudo-Wavelet function for MMG signal extraction during dynamic fatiguing contractions. Sensors 2014, 14, 9489–9504. [Google Scholar] [CrossRef]
- Yamaba, H.; Kurogi, A.; Kubota, S.; Katayama, T.; Park, M.; Okazaki, N. Evaluation of feature values of surface electromyograms for user authentication on mobile devices. Artif. Life Robot. 2017, 22, 108–112. [Google Scholar] [CrossRef]
- Cannan, J.; Hu, H. Automatic user identification by using forearm biometrics. In Proceedings of the IEEE/ASME International Conference on Advanced Intelligent Mechatronics, Wollongong, Australia, 9–12 July 2013. [Google Scholar]
- Shioji, R.; Ito, S.; Ito, M.; Fukumi, M. Personal authentication based on wrist EMG analysis by a convolutional neural network. In Proceedings of the 5th IIAE International Conference on Intelligent Systems and Image Processing, Waikiki, HI, USA, 7–12 September 2017. [Google Scholar]
- Benatti, S.; Milosevic, B.; Farella, E.; Gruppioni, E.; Benini, L. A prosthetic hand body area controller based on efficient pattern recognition control strategies. Sensors 2017, 17, 869. [Google Scholar] [CrossRef]
- Englehart, K.; Hudgins, B. A robust, real-time control scheme for multifunction myoelectric control. IEEE Trans. Biomed. Eng. 2003, 50, 848–854. [Google Scholar] [CrossRef] [PubMed]
- Englehart, K.; Hudgins, B.; Parker, P.; Stevenson, M. Classification of the myoelectric signal using time-frequency based representations. Med Eng. Phys. 1999, 21, 431–438. [Google Scholar] [CrossRef]
- Zecca, M.; Micera, S.; Carrozza, M.; Dario, P. Control of multifunctional prosthetic hands by processing the electromyographic signal. Crit. Rev. Biomed. Eng. 2002, 30, 4–6. [Google Scholar] [CrossRef] [PubMed]
- Sharma, S.; Farooq, H.; Chahal, N. Feature extraction and classification of surface EMG signals for robotic hand simulation. Commun. Appl. Electron. (CAE) 2016, 4, 27–31. [Google Scholar] [CrossRef]
- Arief, Z.; Sulistijono, I.; Ardiansyah, R. Comparison of five time series EMG features extractions using Myo Armband. In Proceedings of the International Electronics Symposium (IES), Surabaya, Indonesia, 29–30 September 2015; pp. 11–14. [Google Scholar]
- Chantaf, S.; Naït-Ali, A.; Karasinski, P.; Khalil, M. ECG modelling using wavelet networks: Application to biometrics. Int. J. Biom. 2010, 2, 236–249. [Google Scholar] [CrossRef]
- Yamaba, H.; Kurogi, T.; Aburada, K.; Kubota, S.; Katayama, T.; Park, M.; Okazaki, N. On applying support vector machines to a user authentication method using surface electromyogram signals. Artif. Life Robot. 2018, 23, 87–93. [Google Scholar] [CrossRef]
- Dantcheva, A.; Velardo, C.; D’angelo, A.; Dugelay, J. Bag of soft biometrics for person identification. Multimed. Tools Appl. 2011, 51, 739–777. [Google Scholar] [CrossRef]
- Soutar, C.; Roberge, D.; Stoianov, A.; Gilroy, R.; Kumar, B. Biometric Encryption: Enrollment and verification procedures. Int. Soc. Opt. Photonics 1998, 3386, 24–35. [Google Scholar]
- Yamaba, H.; Nagatomo, S.; Aburada, K.; Kubota, S.; Katayama, T.; Park, M.; Okazaki, N. An Authentication Method Independent of Tap Operation on the Touchscreen of a Mobile Device. J. Robot. Netw. Artif. Life 2015, 2, 60–63. [Google Scholar] [CrossRef][Green Version]
- Said, S.; Alkork, S.; Beyrouthy, T.; Fayek, M. Wearable Bio-Sensors Bracelet for Driver’s Health Emergency. In Proceedings of the 2nd International conference on Bio-engineering for Smart Technlogied (Biosmart), Paris, France, 30 August–1 September 2017. [Google Scholar]
- Rawat, S.; Vats, S. Evaluating and exploring the MYO ARMBAND. In Proceedings of the International Conference System Modeling & Advancement in Research Trends (SMART), Moradabad, India, 25–27 November 2016. [Google Scholar]
- Qingqing, L.; Penghui, D.; Zheng, J. Enhancing the Security of Pattern Unlock with Surface EMG-Based Biometrics. Appl. Sci. 2020, 10, 541. [Google Scholar]
- Robertson, D.; Caldwell, G.; Hamill, J.; Kamen, G. Whittlesey, S. Research Methods in Biomechanics; Human Kinetics: Champaign, IL, USA, 2014. [Google Scholar]
- Said, S.; Boulkaibet, I.; Sheikh, M.; Karar, A.S.; Alkork, S.; Nait-ali, A. Machine-Learning-Based Muscle Control of a 3D-Printed Bionic Arm. Sensors 2020, 20, 3144. [Google Scholar] [CrossRef] [PubMed]
- Barioul, R.; Ghribi, S.F.; Kanoun, O. A low cost signal acquisition board design for myopathy’s EMG database construction. In Proceedings of the 13th International Multi-Conference on Systems, Signals & Devices (SSD), Leipzig, Germany, 21–24 March 2016; pp. 274–279. [Google Scholar]
- Akhmadeev, K.; Houssein, A.; Moussaoui, S.; Høgestøl, E.A.; Tutturen, I.; Harbo, D.; Laplaud, H.F.; Gourraud, P.A. SVM-based tool to detect patients with multiple sclerosis using a commercial EMG sensor. In Proceedings of the 2018 IEEE 10th Sensor Array and Multichannel Signal Processing Workshop (SAM), Sheffield, UK, 8–11 July 2018. [Google Scholar]
- Chantaf, S.; Makni, L.; Nait-ali, A. Single Channel Surface EMG Based Biometrics. In Hidden Biometrics; Springer: Singapore, 2020; pp. 71–90. [Google Scholar]
- Kay, S. Modern Spectral Estimation: Theory and Application; Pearson Education India: Delhi, India, 1998. [Google Scholar]
- Proakis, J. Digital Signal Processing: Principles Algorithms and Applications; Pearson Education India: Delhi, India, 2001. [Google Scholar]
- Barbé, K.; Pintelon, R.; Schoukens, J. Welch method revisited: Nonparametric power spectrum estimation via circular overlap. IEEE Trans. Signal Process. 2009, 58, 553–555. [Google Scholar] [CrossRef]
- Paul, Y.; Goyal, V.; Jaswal, R. Comparative analysis between SVM & KNN classifier for EMG signal classification on elementary time domain features. In Proceedings of the 4th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 21–23 September 2017. [Google Scholar]
- Zhang, H.; Zhao, Y.; Yao, F.; Xu, L.; Shang, P.; Li, G. An adaptation strategy of using LDA classifier for EMG pattern recognition. In Proceedings of the 35th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Osaka, Japan, 3–7 July 2013. [Google Scholar]
- Freund, Y.; Schapire, R. A desicion-theoretic generalization of on-line learning and an application to boosting. In Proceedings of the European Conference on Computational Learning Theory, Barcelona, Spain, 13–15 March 1995. [Google Scholar]
- Freund, Y.; Schapire, R.; Abe, N. A short introduction to boosting. J. Jpn. Soc. Artif. Intell. 1999, 14, 771–780. [Google Scholar]
- Friedman, J.; Hastie, T.; Tibshirani, R. Additive logistic regression: A statistical view of boosting. Ann. Stat. 2000, 28, 337–374. [Google Scholar] [CrossRef]
- Mekhalfa, F.; Nacereddine, N. Gentle Adaboost algorithm for weld defect classification. In Proceedings of the Signal Processing: Algorithms, Architectures, Arrangements, and Applications (SPA), Poznan, Poland, 20–22 September 2017; pp. 301–306. [Google Scholar]
- He, J.; Jiang, N. Biometric From Surface Electromyogram (sEMG): Feasibility of User Verification and Identification Based on Gesture Recognition. Front. Bioeng. Biotechnol. 2020, 8, 58. [Google Scholar] [CrossRef] [PubMed]

| Frequency-Domain Features | Time-Domain Features |
|---|---|
| Kurtosis | Length of the signal |
| Signal Power | Root Mean Square of each segment of the signal |
| Deciles, | |
| Median frequency | |
| Frequency peak | |
| Dissymmetry coefficient | |
| Frequency Peak |
| k-Nearest Neighbors | |
| Number of neighbors | 2 |
| Distance metric | Minkowski |
| Distance Weight | Inverse |
| Exponent | 0.57 |
| Linear Discriminant Analysis | |
| Delta | 0.01 |
| Gamma | 0.7 |
| Discriminant Type | PseudoLinear |
| Ensemble Classifier | |
| Weak Learner | Decision Tree |
| Method | GentleBoost |
| Number of Learning Cycles | 11 |
| Learning Rate | 0.95 |
| Minimum Leaf Size | 22 |
| Maximum number of Split | 1 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Said, S.; Karar, A.S.; Beyrouthy, T.; Alkork, S.; Nait-ali, A. Biometrics Verification Modality Using Multi-Channel sEMG Wearable Bracelet. Appl. Sci. 2020, 10, 6960. https://doi.org/10.3390/app10196960
Said S, Karar AS, Beyrouthy T, Alkork S, Nait-ali A. Biometrics Verification Modality Using Multi-Channel sEMG Wearable Bracelet. Applied Sciences. 2020; 10(19):6960. https://doi.org/10.3390/app10196960
Chicago/Turabian StyleSaid, Sherif, Abdullah S. Karar, Taha Beyrouthy, Samer Alkork, and Amine Nait-ali. 2020. "Biometrics Verification Modality Using Multi-Channel sEMG Wearable Bracelet" Applied Sciences 10, no. 19: 6960. https://doi.org/10.3390/app10196960
APA StyleSaid, S., Karar, A. S., Beyrouthy, T., Alkork, S., & Nait-ali, A. (2020). Biometrics Verification Modality Using Multi-Channel sEMG Wearable Bracelet. Applied Sciences, 10(19), 6960. https://doi.org/10.3390/app10196960







