A Multi-Image Encryption with Super-Lager-Capacity Based on Spherical Diffraction and Filtering Diffusion
Abstract
1. Introduction
2. Principles of the Method
2.1. Encryption in Spherical Diffraction Domain
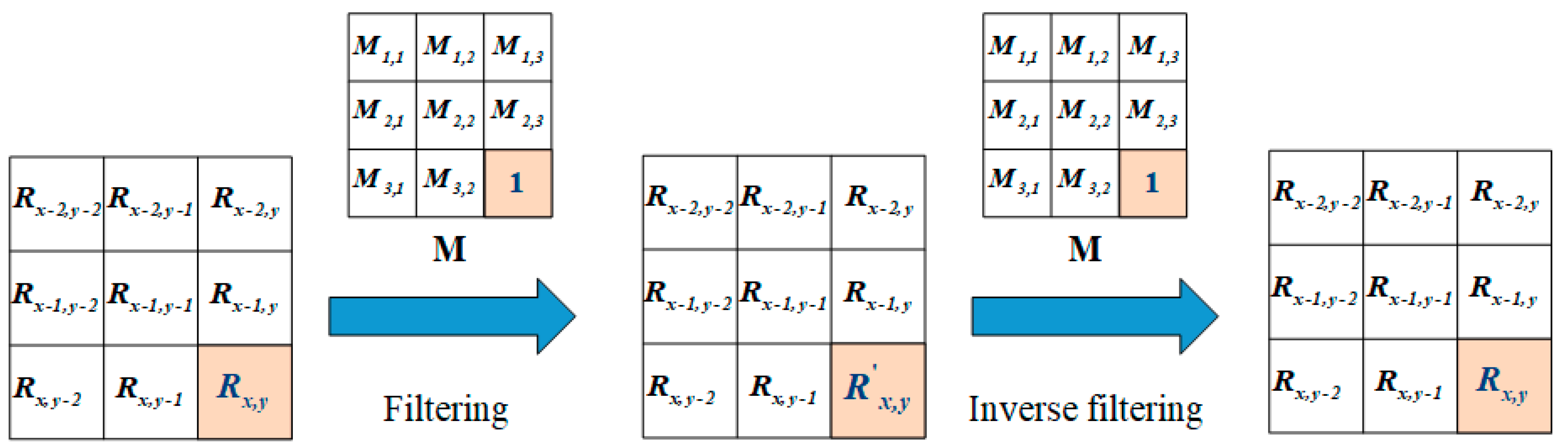
2.2. Filtering Diffusion Technology
3. Principle of Encryption and Decryption
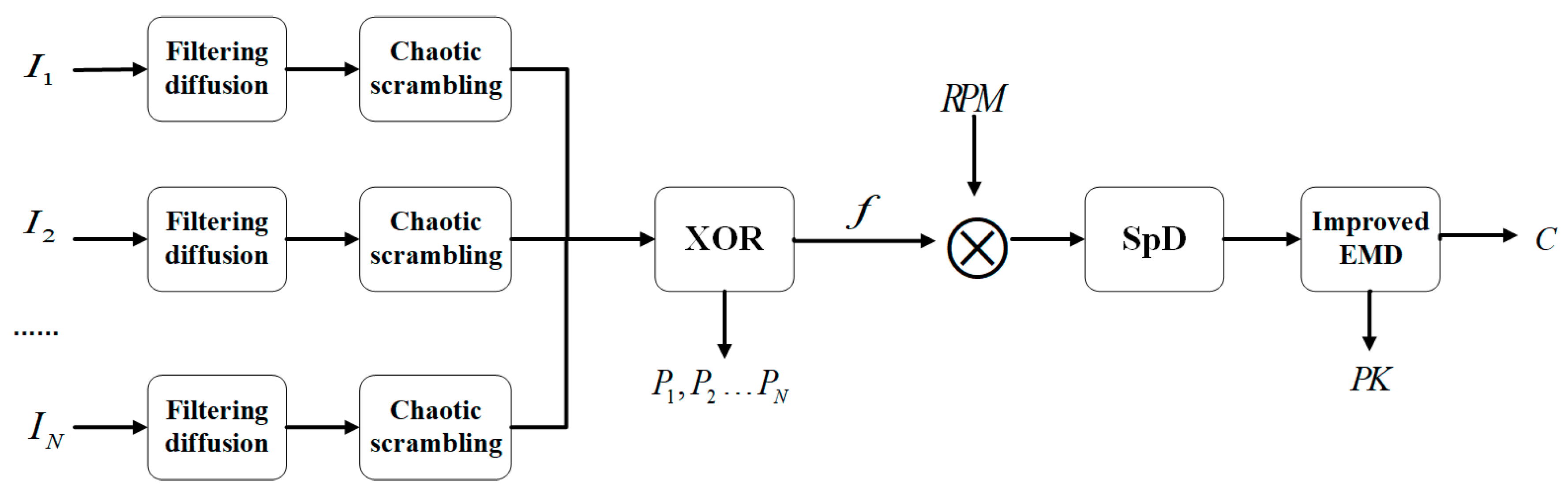
3.1. Process of Encryption
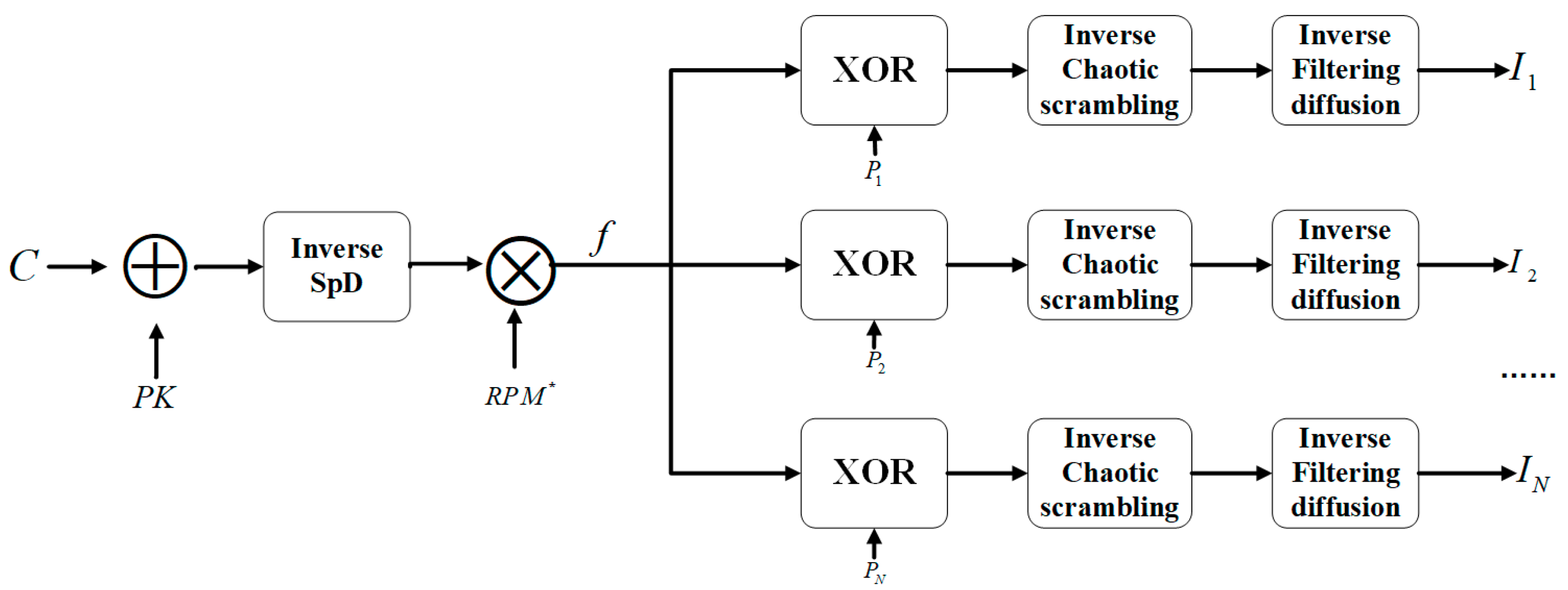
3.2. Process of Decryption
4. Simulation Results
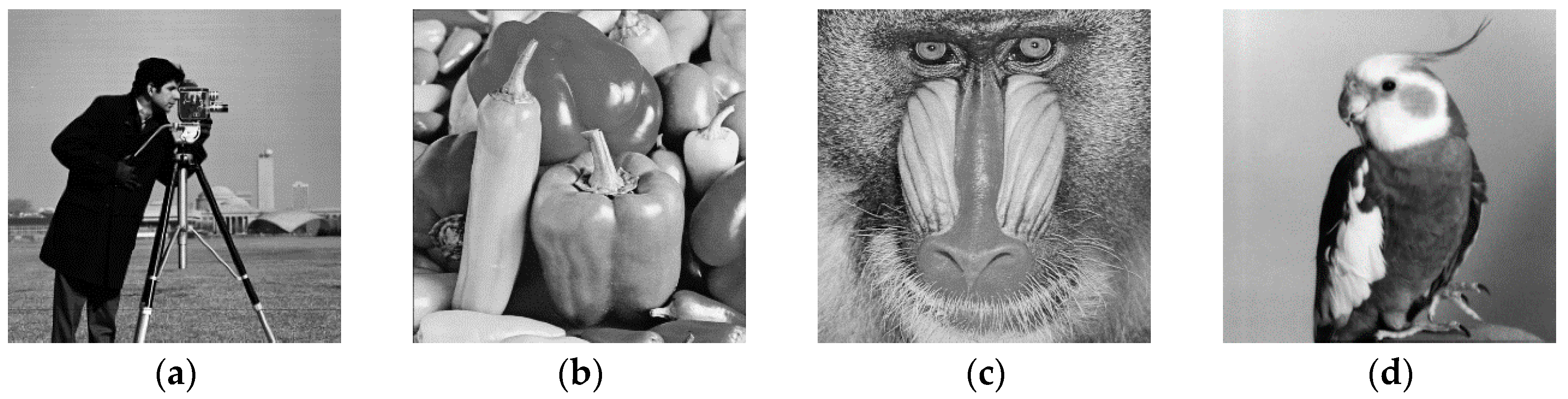
4.1. Encryption and Decryption Results
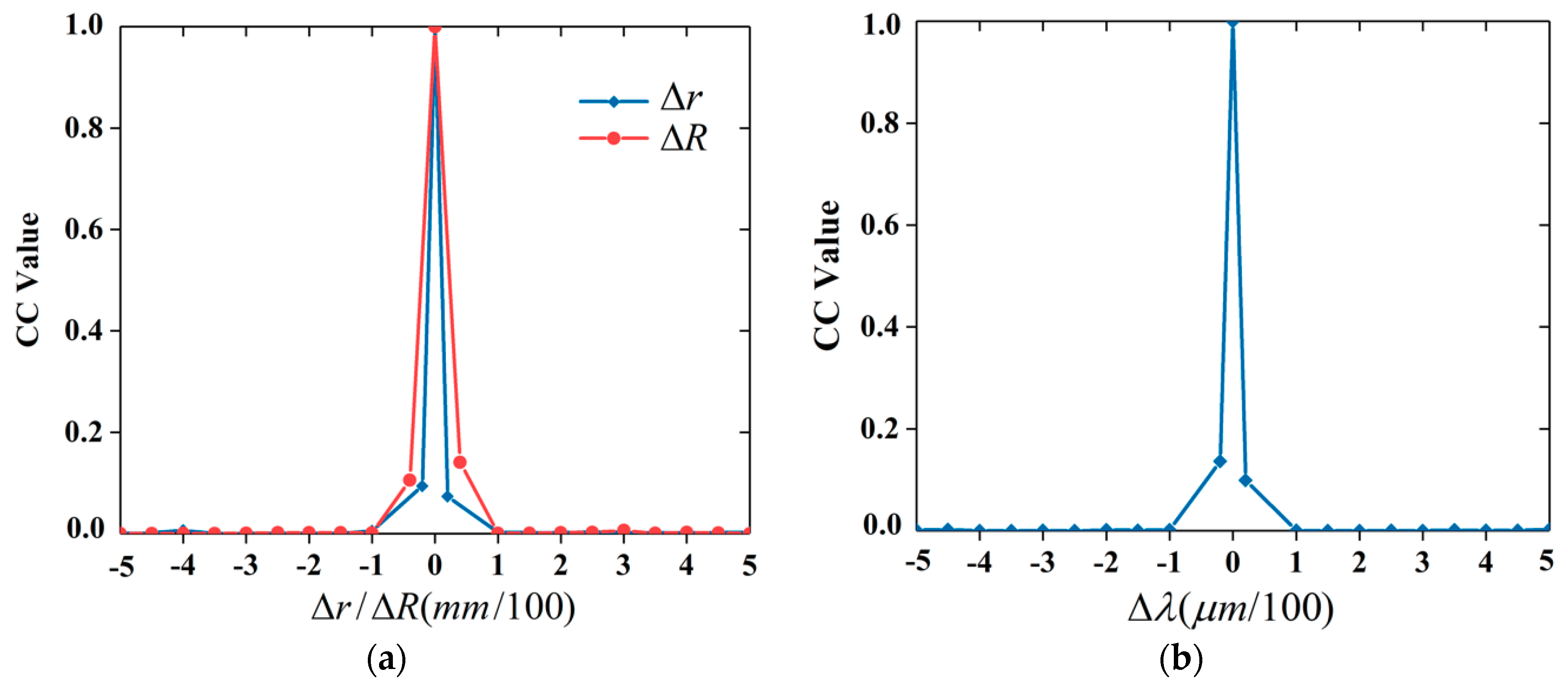
4.2. Key Sensitivity and Key Space Analysis
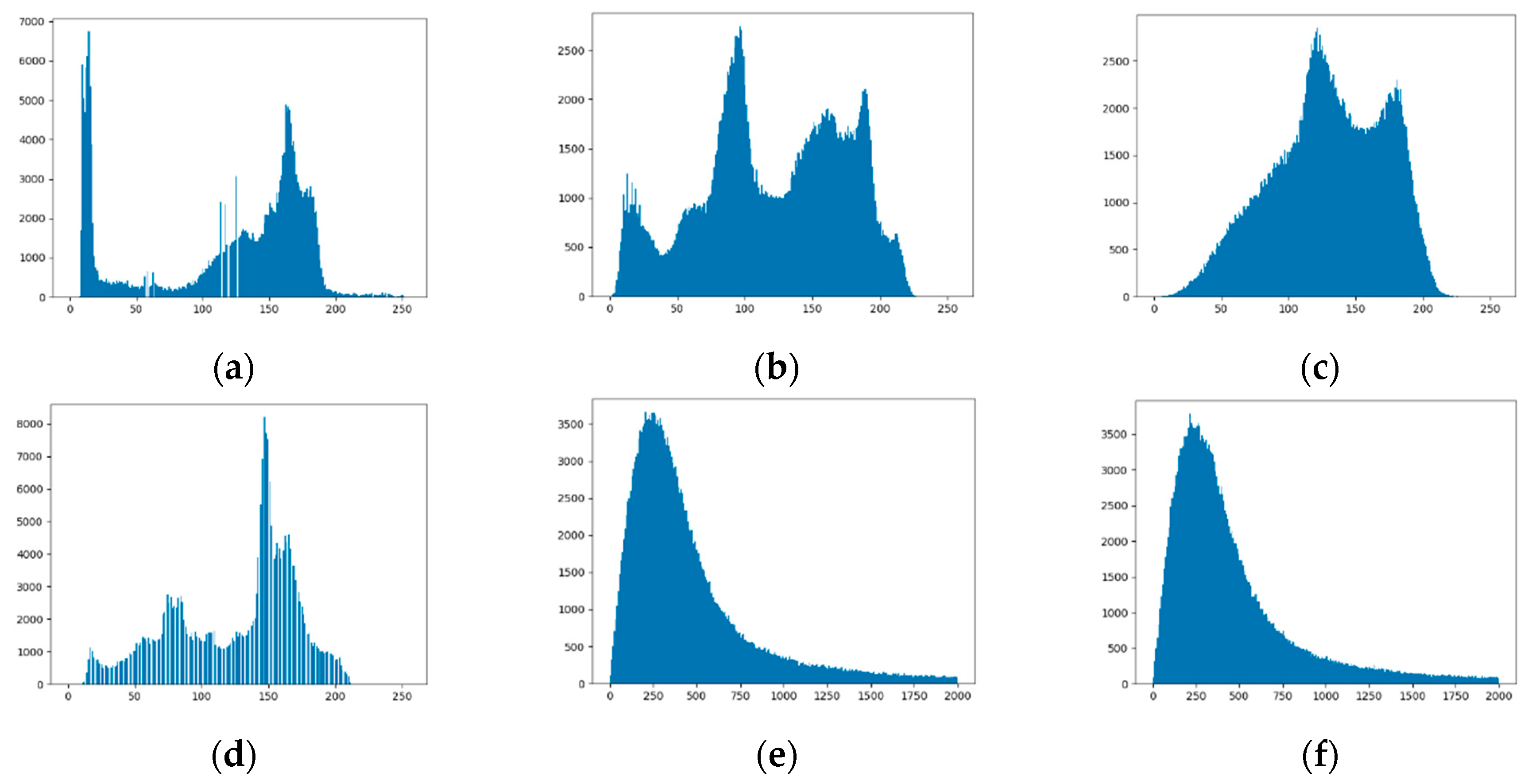
4.3. Histogram
4.4. Adjacent Pixel Correlation
4.5. Noise and Occlusion Attacks
4.6. Potential Attack Analysis
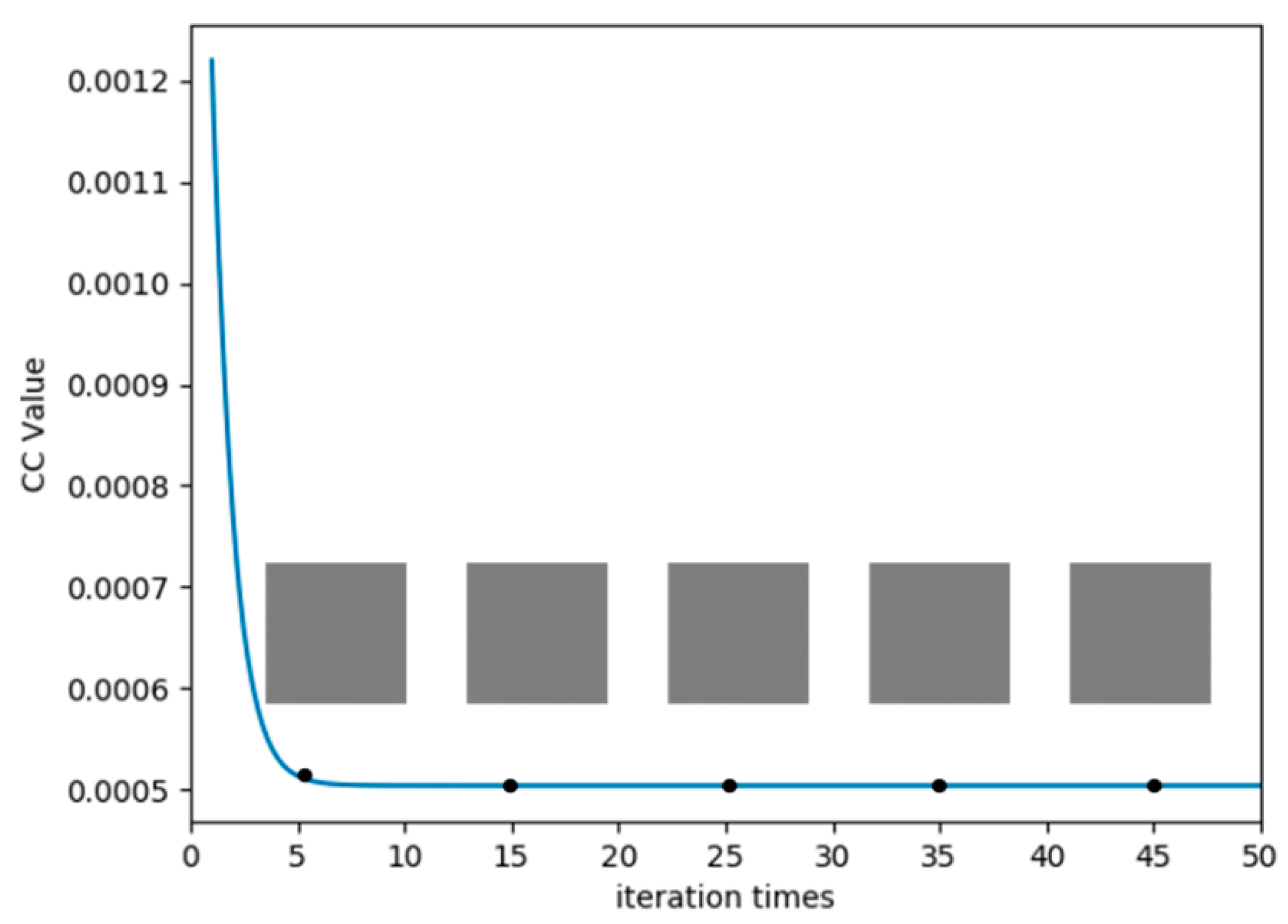
4.7. Time and Computational Complexity Analysis
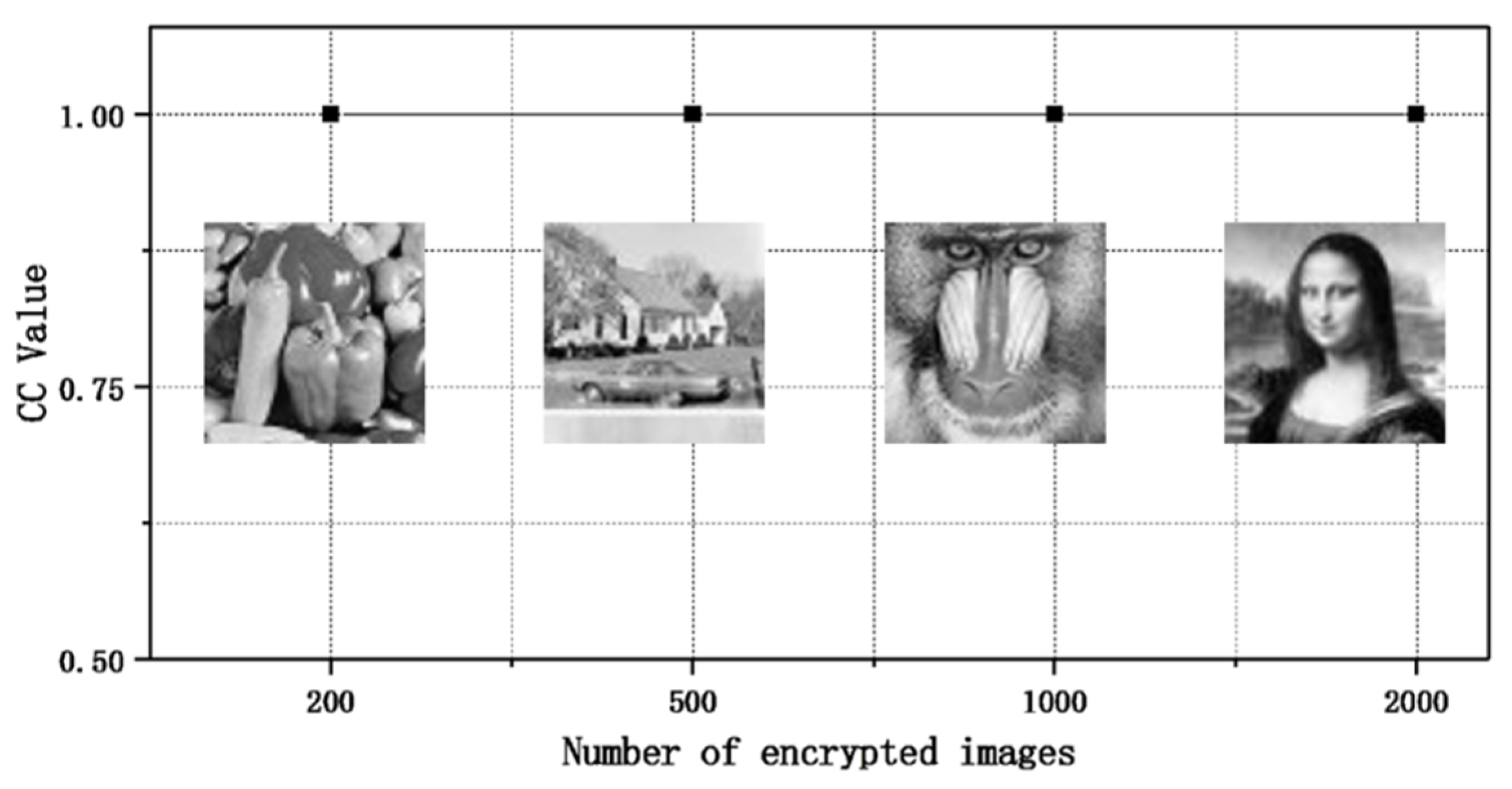
4.8. Capacity of Image Encryption
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Liu, S.T.; Mi, Q.L.; Zhu, B.H. Optical image encryption with multistage and multichannel fractional Fourier-domain filtering. Opt. Lett. 2001, 26, 1242–1244. [Google Scholar] [CrossRef] [PubMed]
- Qin, Y.; Wang, Z.P.; Wang, H.J.; Gong, Q. Binary image encryption in a joint transform correlator scheme by aid of run-length encoding and QR code. Opt. Lasers Technol. 2018, 103, 93–98. [Google Scholar] [CrossRef]
- Zhou, N.R.; Pan, S.M.; Cheng, S.; Zhou, Z.H. Image compression-encryption scheme based on hyper-chaotic system and 2D compressive sensing. Opt. Lasers Technol. 2016, 82, 121–133. [Google Scholar] [CrossRef]
- Chang, K.-M.; Chen, C.; Wang, J.; Wang, Q.-H. Improved single-random-phase holographic encryption using double-phase method. Opt. Commun. 2019, 443, 19–25. [Google Scholar] [CrossRef]
- Dou, Y.Q.; Li, M. Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map. Appl. Sci. 2020, 10, 2187. [Google Scholar] [CrossRef]
- Zhu, Z.; Chen, X.D.; Wu, C.; Wang, J.; Wang, W.X. An asymmetric color-image cryptosystem based on spiral phase transformation and equal modulus decomposition. Opt. Lasers Technol. 2020, 126, 106106. [Google Scholar] [CrossRef]
- Catak, F.O.; Aydin, I.; Elezaj, O.; Yildirim-Yayilgan, S. Practical Implementation of Privacy Preserving Clustering Methods Using a Partially Homomorphic Encryption Algorithm. Electronics 2020, 9, 229. [Google Scholar] [CrossRef]
- Refregier, P.; Javidi, B. Optical-Image Encryption Based on Input Plane and Fourier Plane Random Encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef]
- Frauel, Y.; Castro, A.; Naughton, T.J.; Javidi, B. Resistance of the double random phase encryption against various attacks. Opt. Express 2007, 15, 10253–10265. [Google Scholar] [CrossRef]
- Peng, X.; Zhang, P.; Wei, H.Z.; Yu, B. Known-plaintext attack on optical encryption based on double random phase keys. Opt. Lett. 2006, 31, 1044–1046. [Google Scholar] [CrossRef]
- Peng, X.; Wei, H.Z.; Zhang, P. Chosen-plaintext attack on lensless double-random phase encoding in the Fresnel domain. Opt. Lett. 2006, 31, 3261–3263. [Google Scholar] [CrossRef] [PubMed]
- Chen, W.; Chen, X.D. Optical color image encryption based on an asymmetric cryptosystem in the Fresnel domain. Opt. Commun. 2011, 284, 3913–3917. [Google Scholar] [CrossRef]
- Wang, J.; Wang, Q.H.; Hu, Y.H. Image Encryption Using Compressive Sensing and Detour Cylindrical Diffraction. IEEE Photonics J. 2018, 10, 1–4. [Google Scholar] [CrossRef]
- Ding, X.L.; Huang, Y.M.; Zhang, D.Y.; Song, Y. Nonlinear Double-Image Encryption in Cylindrical Diffraction-Based Scheme by Aid of Position Multiplexing. IEEE Access 2020, 8, 205–214. [Google Scholar] [CrossRef]
- Wang, J.; Li, X.; Hu, Y.; Wang, Q.-H. Phase-retrieval attack free cryptosystem based on cylindrical asymmetric diffraction and double-random phase encoding. Opt. Commun. 2018, 410, 468–474. [Google Scholar] [CrossRef]
- Singh, H.; Yadav, A.K.; Vashisth, S.; Singh, K. Double phase-image encryption using gyrator transforms, and structured phase mask in the frequency plane. Opt. Lasers Eng. 2015, 67, 145–156. [Google Scholar] [CrossRef]
- Zhou, N.R.; Li, H.L.; Wang, D.; Pan, S.M.; Zhou, Z.H. Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt. Commun. 2015, 343, 10–21. [Google Scholar] [CrossRef]
- Hwang, H.-E.; Chang, H.T.; Lie, W.-N. Multiple-image encryption and multiplexing using a modified Gerchberg-Saxton algorithm and phase modulation in Fresnel-transform domain. Opt. Lett. 2009, 34, 3917–3919. [Google Scholar] [CrossRef]
- Gao, Y.; Jiao, S.M.; Fang, J.C.; Lei, T.; Xie, Z.W.; Yuan, X.C. Multiple-image encryption and hiding with an optical diffractive neural network. Opt. Commun. 2020, 463, 125476. [Google Scholar] [CrossRef]
- Sui, L.S.; Zhang, L.W.; Wang, Q.; Tian, A.L.; Anand, A. Multiple-image authentication based on the single-pixel correlated imaging and multiple-level wavelet transform. Opt. Lasers Eng. 2020, 130, 106102. [Google Scholar]
- Xi, S.X.; Yu, N.N.; Wang, X.L.; Wang, X.G.; Lang, L.Y.; Wang, H.Y.; Liu, W.W.; Zhai, H.C. Optical encryption scheme for multiple-image based on spatially angular multiplexing and computer generated hologram. Opt. Lasers Eng. 2020, 127, 105953. [Google Scholar] [CrossRef]
- Sui, L.; Zhang, X.; Tian, A. Multiple-Image Hiding Based on Cascaded Free-Space Wave Propagation Using the Structured Phase Mask for Lensless Optical Security System. IEEE Photonics J. 2017, 9, 1–14. [Google Scholar] [CrossRef]
- Zhang, L.; Yuan, X.; Wang, K.; Zhang, D. Multiple-Image Encryption Mechanism Based on Ghost Imaging and Public Key Cryptography. IEEE Photonics J. 2019, 11, 1–14. [Google Scholar] [CrossRef]
- Wu, C.; Wang, Y.; Chen, Y.; Wang, J.; Wang, Q.-H. Asymmetric encryption of multiple-image based on compressed sensing and phase-truncation in cylindrical diffraction domain. Opt. Commun. 2019, 431, 203–209. [Google Scholar] [CrossRef]
- Kong, D.Z.; Shen, X.J.; Xu, Q.Z.; Xin, W.; Guo, H.Q. Multiple-image encryption scheme based on cascaded fractional Fourier transform. Appl. Opt. 2013, 52, 2619–2625. [Google Scholar] [CrossRef]
- Wang, X.G.; Zhao, D.M. Multiple-image encryption based on nonlinear amplitude-truncation and phase-truncation in Fourier domain. Opt. Commun. 2011, 284, 148–152. [Google Scholar] [CrossRef]
- Liansheng, S.; Xiao, Z.; Chongtian, H.; Ailing, T.; Krishna Asundi, A. Silhouette-free interference-based multiple-image encryption using cascaded fractional Fourier transforms. Opt. Lasers Eng. 2019, 113, 29–37. [Google Scholar] [CrossRef]
- Li, Y.B.; Zhang, F.; Li, Y.C.; Tao, R. Asymmetric multiple-image encryption based on the cascaded fractional Fourier transform. Opt. Lasers Eng. 2015, 72, 18–25. [Google Scholar] [CrossRef]
- Gong, Q.; Liu, X.Y.; Li, G.Q.; Qin, Y. Multiple-image encryption and authentication with sparse representation by space multiplexing. Appl. Opt. 2013, 52, 7486–7493. [Google Scholar] [CrossRef]
- Shi, Y.; Zhang, J. Research on the phase retrieval algorithm used for multiple-image encryption with region multiplexing. Guangxue Xuebao Acta Opt. Sin. 2009, 29, 2705–2708. [Google Scholar] [CrossRef]
- Situ, G.H.; Zhang, J.J. Multiple-image encryption by wavelength multiplexing. Opt. Lett. 2005, 30, 1306–1308. [Google Scholar] [CrossRef] [PubMed]
- He, X.L.; Tao, H.; Jiang, Z.L.; Kong, Y.; Wang, S.Y.; Liu, C. Single-shot optical multiple-image encryption by jointly using wavelength multiplexing and position multiplexing. Appl. Opt. 2020, 59, 9–15. [Google Scholar] [CrossRef] [PubMed]
- Liu, L.; Shan, M.; Zhong, Z.; Liu, B. Multiple-image encryption and authentication based on optical interference by sparsification and space multiplexing. Opt. Lasers Technol. 2020, 122, 105858. [Google Scholar] [CrossRef]
- Deepan, B.; Quan, C.; Wang, Y.; Tay, C.J. Multiple-image encryption by space multiplexing based on compressive sensing and the double-random phase-encoding technique. Appl. Opt. 2014, 53, 4539–4547. [Google Scholar] [CrossRef]
- Zhao, H.Z.; Liu, J.; Jia, J.; Zhu, N.; Xie, J.H.; Wang, Y.T. Multiple-image encryption based on position multiplexing of Fresnel phase. Opt. Commun. 2013, 286, 85–90. [Google Scholar] [CrossRef]
- Hu, K.-Y.; Wu, C.; Wang, Y.; Wang, J.; Wang, Q.-H. An asymmetric multi-image cryptosystem based on cylindrical diffraction and phase truncation. Opt. Commun. 2019, 449, 100–109. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, S. Double image encryption based on iterative fractional Fourier transform. Opt. Commun. 2007, 275, 324–329. [Google Scholar] [CrossRef]
- Wang, J.; Wang, Q.-H. Outside-in Propagation Model for Spherical Computer-Generated Hologram, International Workshop on Holography and Related Technologies; IWH: Beijing, China, 2014. [Google Scholar]
- Jackin, B.J.; Yatagai, T. Fast calculation of spherical computer generated hologram using spherical wave spectrum method. Opt. Express 2013, 21, 935–948. [Google Scholar] [CrossRef]
- Li, G.; Phan, A.H.; Kim, N.; Park, J.H. Synthesis of computer-generated spherical hologram of real object with 360 degrees field of view using a depth camera. Appl. Opt. 2013, 52, 3567–3575. [Google Scholar] [CrossRef]
- Tachiki, M.L.; Sando, Y.; Itoh, M.; Yatagai, T. Fast calculation method for spherical computer-generated holograms. Appl. Opt. 2006, 45, 3527–3533. [Google Scholar] [CrossRef]
- Li, G.; Hong, K.; Yeom, J.; Chen, N.; Park, J.H.; Kim, N.; Lee, B. Acceleration method for computer generated spherical hologram calculation of real objects using graphics processing unit. Chin. Opt. Lett. 2014, 12, 060016. [Google Scholar]
- Hua, Z.; Zhou, Y. Design of image cipher using block-based scrambling and image filtering. Inf. Sci. 2017, 396, 97–113. [Google Scholar] [CrossRef]
- Hua, Z.; Xu, B.; Jin, F.; Huang, H. Image Encryption Using Josephus Problem and Filtering Diffusion. IEEE Access 2019, 7, 8660–8674. [Google Scholar] [CrossRef]
- Wang, J.; Chen, X.; Zeng, J.; Wang, Q.-H.; Hu, Y. Asymmetric Cryptosystem Using Improved Equal Modulus Decomposition in Cylindrical Diffraction Domain. IEEE Access 2019, 7, 66234–66241. [Google Scholar] [CrossRef]





| R | r | λ | xn | μ |
|---|---|---|---|---|
| 500 × 10−3 m | 50 × 10−3 m | 250 × 10−6 m | 0.50 | 3.70 |
| Correlation Coefficient | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| cameraman | 0.966649 | 0.978250 | 0.978232 |
| peppers | 0.973320 | 0.976367 | 0.980875 |
| baboon | 0.879297 | 0.799324 | 0.799965 |
| coco | 0.989351 | 0.990687 | 0.990696 |
| ciphertext | 0.000046 | 0.000203 | 0.002142 |
| Ref. [36] | 0.002800 | 0.034100 | −0.054700 |
| Ref. [22] | −0.026800 | 0.013500 | 0.010300 |
| Ref. [23] | 0.025300 | 0.019700 | 0.026900 |
| Image | NPCR (%) | UACI (%) |
|---|---|---|
| cameraman | 99.6046 | 33.1825 |
| peppers | 99.6046 | 33.9021 |
| baboon | 99.6046 | 33.3199 |
| coco | 99.6046 | 34.1323 |
| Size | One Image | Two Images | Three Images | Four Images |
|---|---|---|---|---|
| 256 × 256 | 0.6393 s | 1.2354 s | 1.8577 s | 2.4489 s |
| 512 × 512 | 2.5149 s | 4.9587 s | 7.4733 s | 9.7806 s |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, H.; Wang, J.; Zhang, Z.; Chen, X.; Zhu, Z. A Multi-Image Encryption with Super-Lager-Capacity Based on Spherical Diffraction and Filtering Diffusion. Appl. Sci. 2020, 10, 5691. https://doi.org/10.3390/app10165691
Wu H, Wang J, Zhang Z, Chen X, Zhu Z. A Multi-Image Encryption with Super-Lager-Capacity Based on Spherical Diffraction and Filtering Diffusion. Applied Sciences. 2020; 10(16):5691. https://doi.org/10.3390/app10165691
Chicago/Turabian StyleWu, Hanmeng, Jun Wang, Ziyi Zhang, Xudong Chen, and Zheng Zhu. 2020. "A Multi-Image Encryption with Super-Lager-Capacity Based on Spherical Diffraction and Filtering Diffusion" Applied Sciences 10, no. 16: 5691. https://doi.org/10.3390/app10165691
APA StyleWu, H., Wang, J., Zhang, Z., Chen, X., & Zhu, Z. (2020). A Multi-Image Encryption with Super-Lager-Capacity Based on Spherical Diffraction and Filtering Diffusion. Applied Sciences, 10(16), 5691. https://doi.org/10.3390/app10165691






