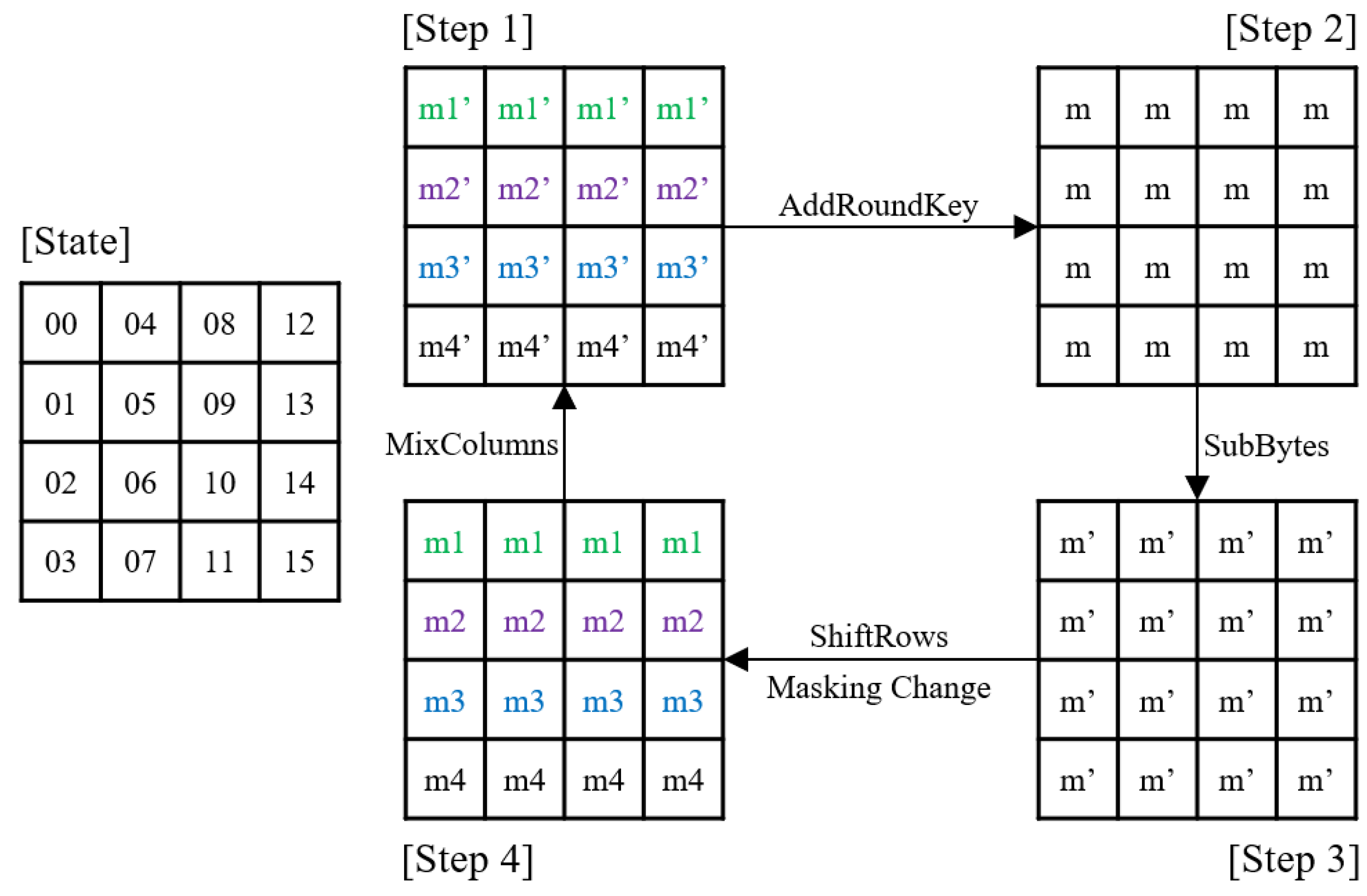
1. Introduction
Cryptanalysis is the study of the analysis of the cryptographic algorithm’s vulnerabilities to construct a secure system. Mathematical analysis, conventional cryptanalysis, reveals secret information based on the fact that an analyst knows plaintext or ciphertext. Meanwhile, Paul Kocher discovered that physical information of a cryptographic device is associated with the secret information [
1]. Although a cryptographic algorithm could be secure against mathematical analysis, it is subjected to vulnerability using physical information. Consequently, cryptanalysis research is required under the assumption that an analyst is aware of physical information in addition to plaintext/ciphertext. Side-channel analysis discloses a secret key by using physical information such as power consumption, electromagnetic, acoustic, and photon [
2,
3,
4,
5].
Power analysis, which analyzes power consumption patterns of a cryptographic device, includes the simple power analysis (SPA) [
1], differential power analysis (DPA) [
2], and correlation power analysis (CPA) [
6]. The DPA/CPA is based on the fact that power consumption when storing data in a register is related to the data. The important factor, which determines the DPA/CPA performance, is the accuracy of the power model that describes the relationship. To raise the model’s accuracy, the analyst considers every single bit of the register: i.e., the length of intermediate value should be as long as the length of the register.
The first-order correlation power analysis (FOCPA) is a statistical method that utilizes the correlation between a single point of power consumption and the sensitive intermediate value. Thus, the countermeasure such as masking is generally used [
7]. To counter the FOCPA, the first-order masking, which splits an intermediate value into two random variables, is utilized. That is, it spreads the power consumption related to the intermediate value into two points. The first-order masked implementation is vulnerable to the second-order correlation power analysis (SOCPA) that utilizes the correlation between guessable intermediate value and two split points of power consumption. Two points of power consumption are preprocessed to related to the guessable intermediate value, and the preprocessing function determines the SOCPA performance.
For the SOCPA, the longer bit length of the intermediate value reduces the correlation between the hypothetical intermediate value and preprocessed power consumption. That is, 1-bit intermediate value has the highest correlation with the preprocessed power consumption when performing the SOCPA. However, 1-bit intermediate is generally not used because shorter bit length reduces the accuracy of the power model. In this tradeoff relation, analysts commonly use an 8-bit intermediate value to improve the performance of the SOCPA.
SOCPA requires more power traces than the FOCPA to determining whether the guessed key is the right key because the correlation of the SOCPA is much lower than the FOCPA. Accordingly, several preprocessing functions had been suggested to raise the correlation of the SOCPA. The first function is the product of two points [
8]. If the power model is the Hamming weight model and the length of the intermediate value is 8, the absolute correlation coefficient is only about 0.09. In this case, theoretically, the general SOCPA requires at least
times more traces than the FOCPA because the correlation is only 0.09 [
9]. Thus, the first function is generally not used. In 2000, the absolute-difference (AD) function was proposed by Messerges [
10]. However, the correlation was still only 0.24, much lower than 1.00. To raise the correlation, Prouff suggested the product-combining (PC) function in 2009, and the correlation was enhanced to 0.35 [
11]. Existing researches are focused on the preprocessing function to enhance SOCPA performance, and the correlation has not raised significantly.
As discussed above, a 1-bit intermediate value is typically not used because it decreases the accuracy of the power model. However, the correlation between the hypothetical intermediate value and preprocessed power consumption is 1.00, if the preprocessing function is AD or PC. Thus, if there exists the 8-bit intermediate value that has the same characteristic as 1-bit, it allows significantly raising the correlation. We focus on the characteristic that the number of cases is 2, for 1-bit intermediate value. Therefore, unlike existing researches, we aim to find the intermediate values that have a smaller cardinality, such as a 1-bit intermediate value. In this paper, we propose the special intermediate value, named sparse intermediate value (SIV), based on the operational characteristics of the cryptographic algorithm, and remarkably raise the correlation from 0.35 to 1.00. That is, we reduce the the minimum trace to disclose the secret key to the same as the FOCPA.
The rest of this paper is organized as follows.
Section 2 briefly describes the overview of the CPA and MixColumns of the advanced encryption algorithm (AES). We analyze the operational characteristics to find the SIV and demonstrate the existence of the power consumption related to SIV in
Section 3.
Section 4 analyzes OpenSSL AES and compares the general SOCPA using 8-bit SubBytes output to SIV-based SOCPA.
Section 5 recommends two countermeasures against the proposed method.
Section 6 summarizes results obtained and the contribution of this paper. Finally,
Section 7 concludes the paper.
3. Sparse Intermediate Value in AES
In this section, we find the SIV based on the operational characteristic of the cryptographic algorithm. If there exists some intermediate value that behaves like a shorter length of the intermediate value, it can enhance the SOCPA performance because it raises the correlation between hypothetical intermediate value and preprocessed power consumption, as shown in
Table 2 while accurately model power consumption. Typically, the number of all possible outcomes
of an
bit intermediate value
S is
.
However, a special intermediate value SIV may exist such that
is much lower than
because of operational characteristics.
Definition 1. An intermediate value S is SIV if .
3.1. Finding the SIV Based on Operational Characteristics
The
xtime performs different operations depending on the input’s MSB, as shown in Equation (
5). To determine the instruction to be executed in software implementation, the MSB must be extracted and stored in a register. When storing the MSB in an 8-bit register, only 1-bit changes depending on the MSB and the remaining 7 bits are always zero. Let the binary representation of the input
d be
. Then the intermediate value
, which is stored in the register when extracting MSB, is
. The
is only 2, which is much smaller than
. Therefore,
can be utilized as the SIV. Thus, we define the Property 1 as follows.
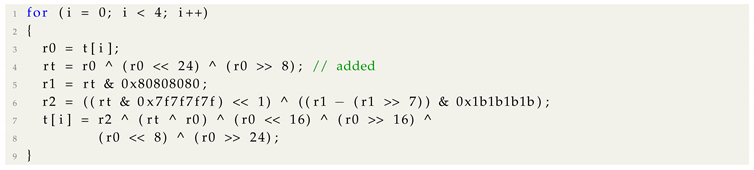
Property 1. MSB extraction is essential to implementxtime. Therefore, the SIV exists as , such that is only 2. Listing 1 is one of the xtime implementations in C language. It can be divided into two parts. One part is multiplication by x as the left-side of the XOR operator , and the other part is reduction by the irreducible polynomial as the right-side .
| Listing 1: 8-bit implementation of xtime using C language. |
![Applsci 10 03394 i001 Applsci 10 03394 i001]() |
In the reduction part, the MSB is not only extracted at but also multiplied by 0x1b to decide whether to reduce the left-side result. The intermediate value , which is stored when the MSB is multiplied by 0x1b, is . As the is only 2, can be utilized as the SIV.
Note that the difference between the Hamming weights of elements in
is 4, whereas the difference of
is only 1. The effect of
on power consumption is relatively greater compared to
.
Therefore, can relatively reduce the effect of noise. Thus, we define the Property 2 as follows.
Property 2. If SIV is computed using a certain constant, the computation result is not only utilized as the SIV, it may also significantly affect power consumption. Thus, the computation result can relatively reduce the effect of noise . In the case of Listing 1, the multiplication result can reduce the effect. The power consumption of and the collection of all possible outcomes of are expressed as follows: We demonstrate the existence of SIV via CPA and t-value. In this paper, we compare the two versions of the CPA, as follows.
Demonstration of Existence of SIV
Our experiments demonstrated that the SIV-related power consumption occurs. We analyzed 100,000 power consumption traces at a 29.538 MS/s sampling rate when AES ran on a ChipWhisperer-Lite ATXMEGA128D4 (8-bit processor) [
14]. We utilized
as the SIV.
For the FOCPA of the MixColumns, the peak correlation coefficient of the
General FOCPA is approximately 0.87, and the peak correlation of the
SIV-based FOCPA is around 0.94, as shown in
Figure 2. The peak correlation of the two versions of FOCPA is similar, demonstrating the existence of the SIV-related power consumption when performing
xtime, as shown in Property 1.
The power consumption of MixColumns is linearly related to the Hamming weight of SubBytes output because the SubBytes output is identical to the MixColumns input. In addition, the correlation of SubBytes is not zero because the Hamming weight of the SIV is linearly related to the MSB of the SubBytes output, as shown in Equation (
6).
To demonstrate Property 2, we compared each power consumption of
and
. The power consumption is divided into two groups based on the SIV, and we verified the distributions of each group. Based on Equation (
6), the effect of
on the power consumption
is four times greater than that on
. Therefore, theoretically, the difference between the mean of the two distributions of
is four times larger than that of
. We utilized the t-value of Welch’s
t-test [
15] to measure the difference between the two distributions as follows:
where
and
denote the standard deviation of
X and
Y, respectively
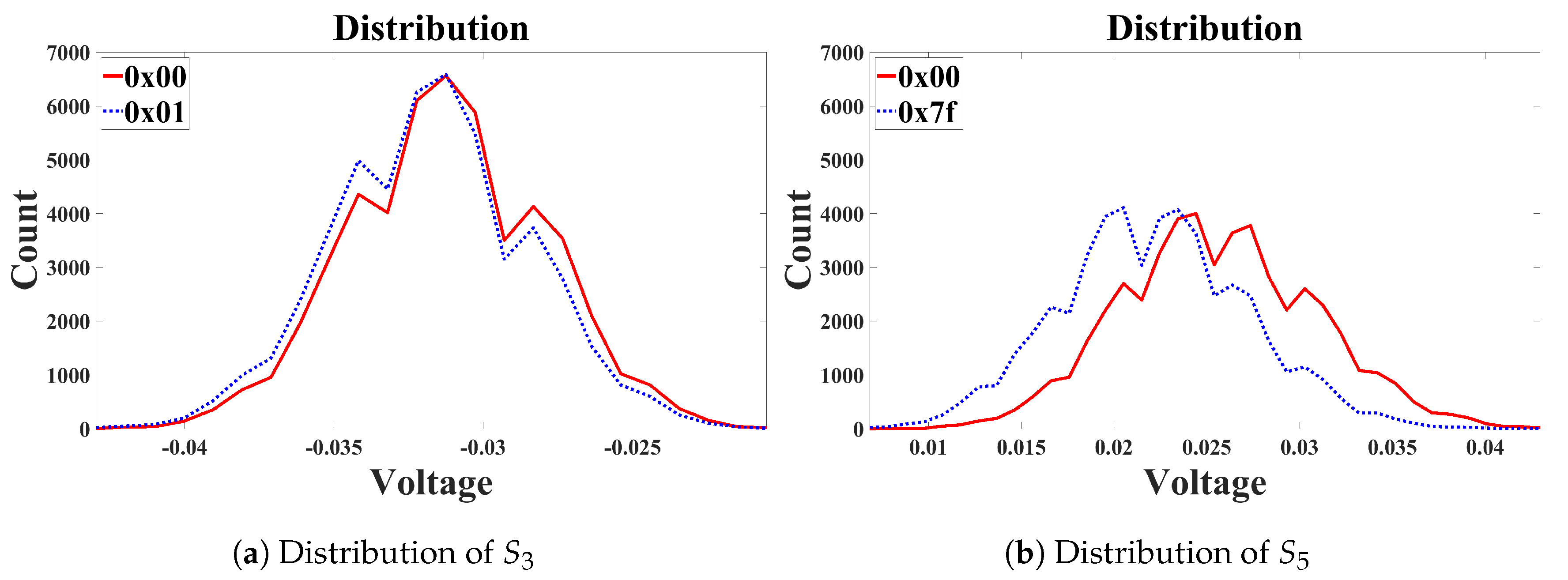
Figure 3 shows the experimental proof of Property 2. The difference between the mean of the two distributions of
is around 0.02084, which is approximately 3.5 times larger than that of
(0.005981). This is very close to the theoretical ratio of 4. The t-value of
is approximately 876.22 and that of
is 198.84. Owing to the substantial difference in the means of the two distributions of
, the two distributions are completely separated despite the noise, as shown in
Figure 3b, i.e., the effect of noise can be relatively moderated, as demonstrated in Property 2.
3.2. The Performance Improvement of SOCPA Using SIV
In
Section 3.1, we demonstrated the existence of SIV using the operational characteristic. In the case of AES, the cardinality of all possible outcomes of SIV is only 2. Moreover, the Hamming weights of outcomes are different. Note that constant multiplication with random variables only affects the sign of the correlation coefficient:
where
a and
b are the arbitrary constants, and
is the sign function. Thus, the theoretical correlation coefficient of Equation (
1) is the same as the 1-bit correlation presented in
Table 2, although the length of the SIV is 8. For example, let
be the
intermediate value, then the theoretical correlation of the SIV is the same as that of some 1-bit intermediate value.
Therefore, when the preprocessing functions are AD and PC, the SIV can increase the correlation coefficient of SOCPA from 0.24 to 1.00 and from 0.35 to 1.00, respectively. That is, the SIV theoretically allows to reduce the minimum trace to disclose the secret key,
times and
times, respectively [
9].
5. Countermeasures
We recommend two countermeasures against the SIV-based SOCPA. The first countermeasure changes the sequence of computations to increase the time complexity in calculating the SIV. The second countermeasure is to implement the SIV generating operation using a precomputed table to eliminate power consumption related to the SIV. Typically, Listing 3 is an implementation of the MixColumns to reduce the time complexity in the 8-bit device.
5.1. Increasing the Time Complexity of the SIV-Based SOCPA
The first countermeasure is to modify the MixColumns implementation, as shown in Listing 3. This listing utilizes the associative property to change the sequence of computations to complicate the calculation of the SIV.
| Listing 3: Countermeasures to increase the time complexity of the intermediate value [17]. |
![Applsci 10 03394 i003 Applsci 10 03394 i003]() |
The existing MixColumns implementation in Listing 2 performs
xtime for each term and then adds two terms, as shown on the left-hand side of Equation (
7). Contrarily, the proposed implementation adds two terms and then performs
xtime, as shown on the right-hand side of Equation (
7). To calculate the input of
xtime, the analyst must guess two keys XORed with
and
.
Although the SIV occurs in this implementation, the size of keyspace to perform the SIV-based SOCPA increases from to . Therefore, performing the SIV-based SOCPA is impractical because the complexity of calculating the MSB of the xtime input increases to 65,536 times. As this countermeasure only changes the sequence of computations, there is no overhead for countermeasure.
5.2. Removing Bit Extraction Operation
The second countermeasure is to implement xtime, which is the SIV generating operation, by precomputation table. This implementation does not extract the input’s MSB or generate the SIV; it only refers to the table. Thus, the power consumption related to the SIV does not occur. However, to implement this countermeasure, additional memory is required. Therefore, if the AES is implemented using a precomputed table of SubBytes and MixColumns known as T-table, it requires 4KB memory. Additionally, if a precomputation table achieves the only xtime, 256 bytes of memory are required. As these implementations substitute several operations to memory reference operations, the time complexity is generally lower than Listing 2.
6. Discussion
Herein, the special intermediate value, named SIV, was proposed based on the operational characteristics of the cryptographic algorithm. The SIV of the AES is determined by analyzing the reduction operation of the MixColumns. It remarkably raises the correlation of SOCPA to 1.00 compared to existing studies that have only increase the correlation to 0.35 [
8,
10,
11]. That is, SIV theoretically allows reducing the MTD approximately 8.1633 times than
General SOCPA [
9].
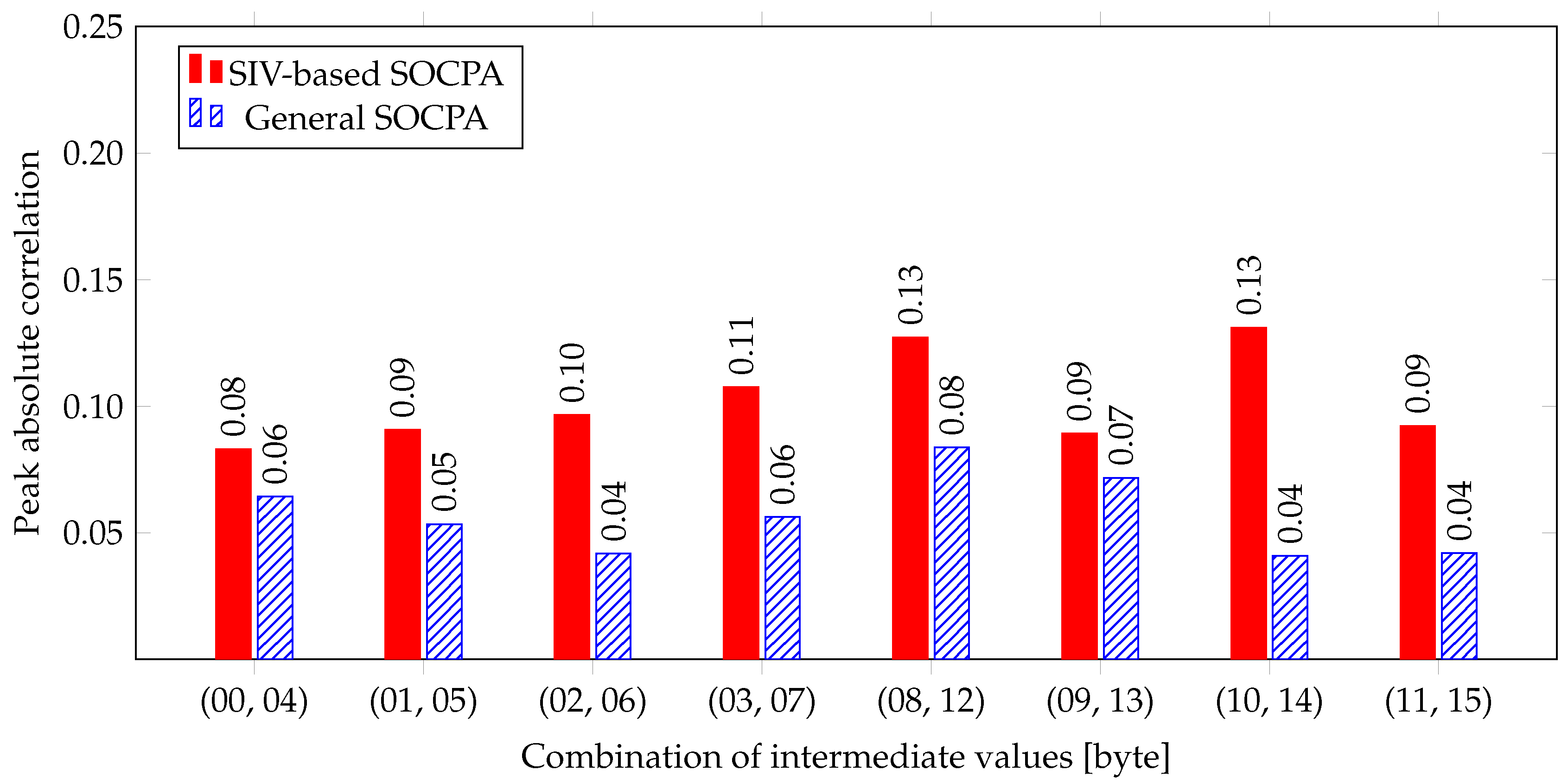
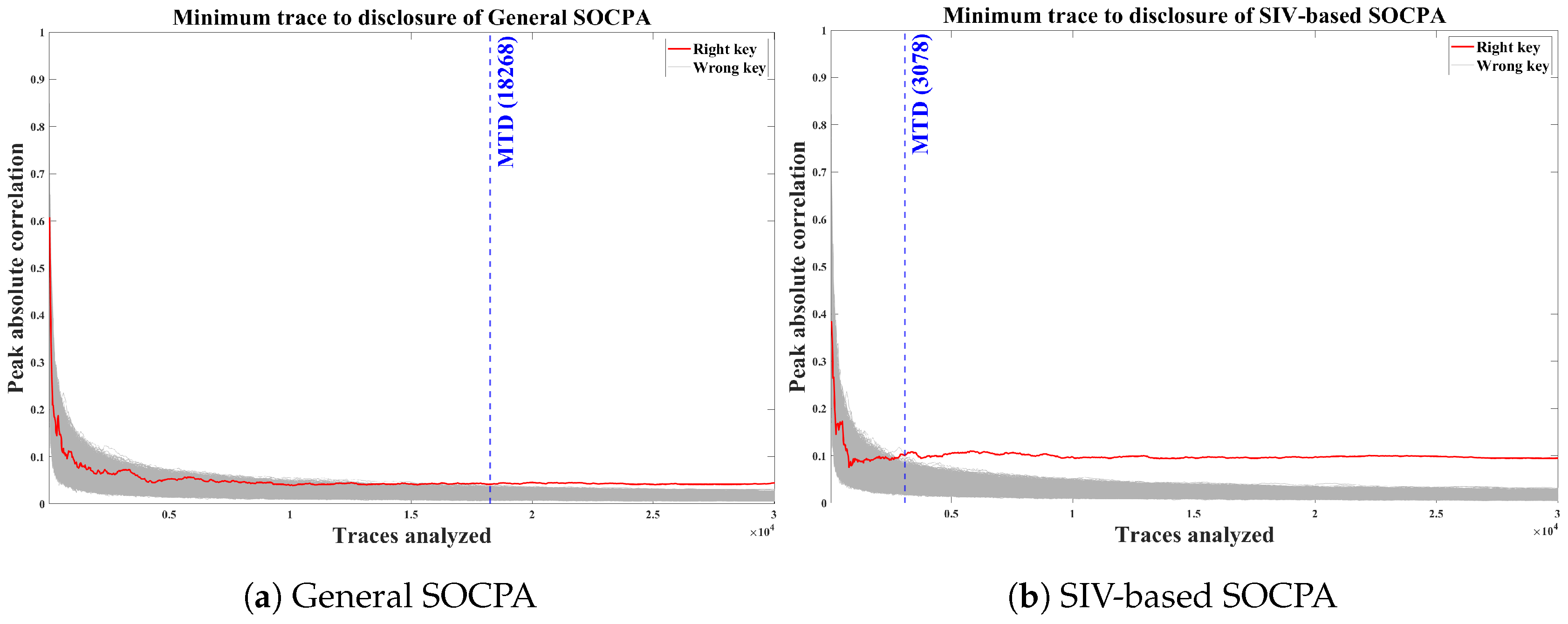
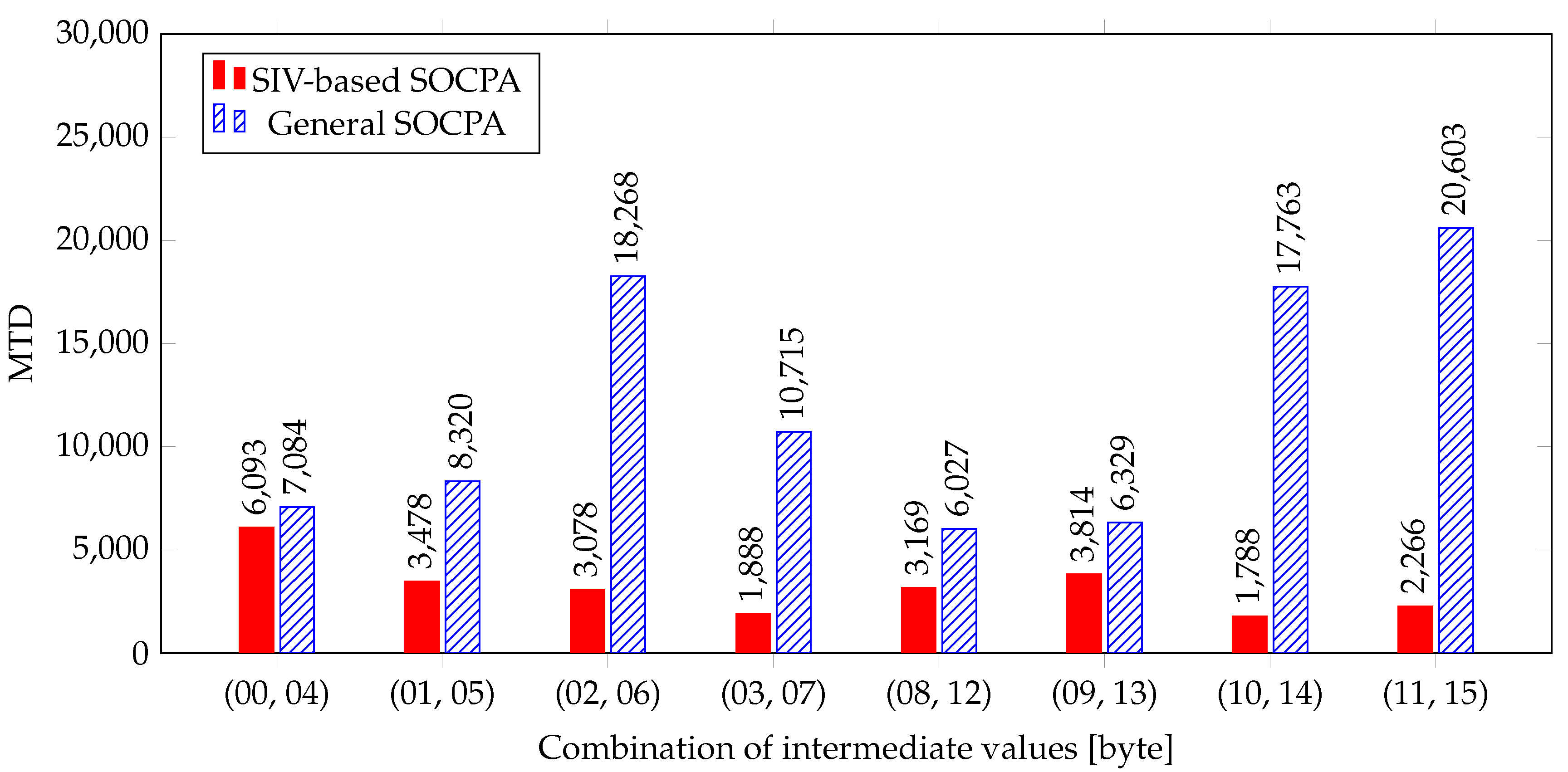
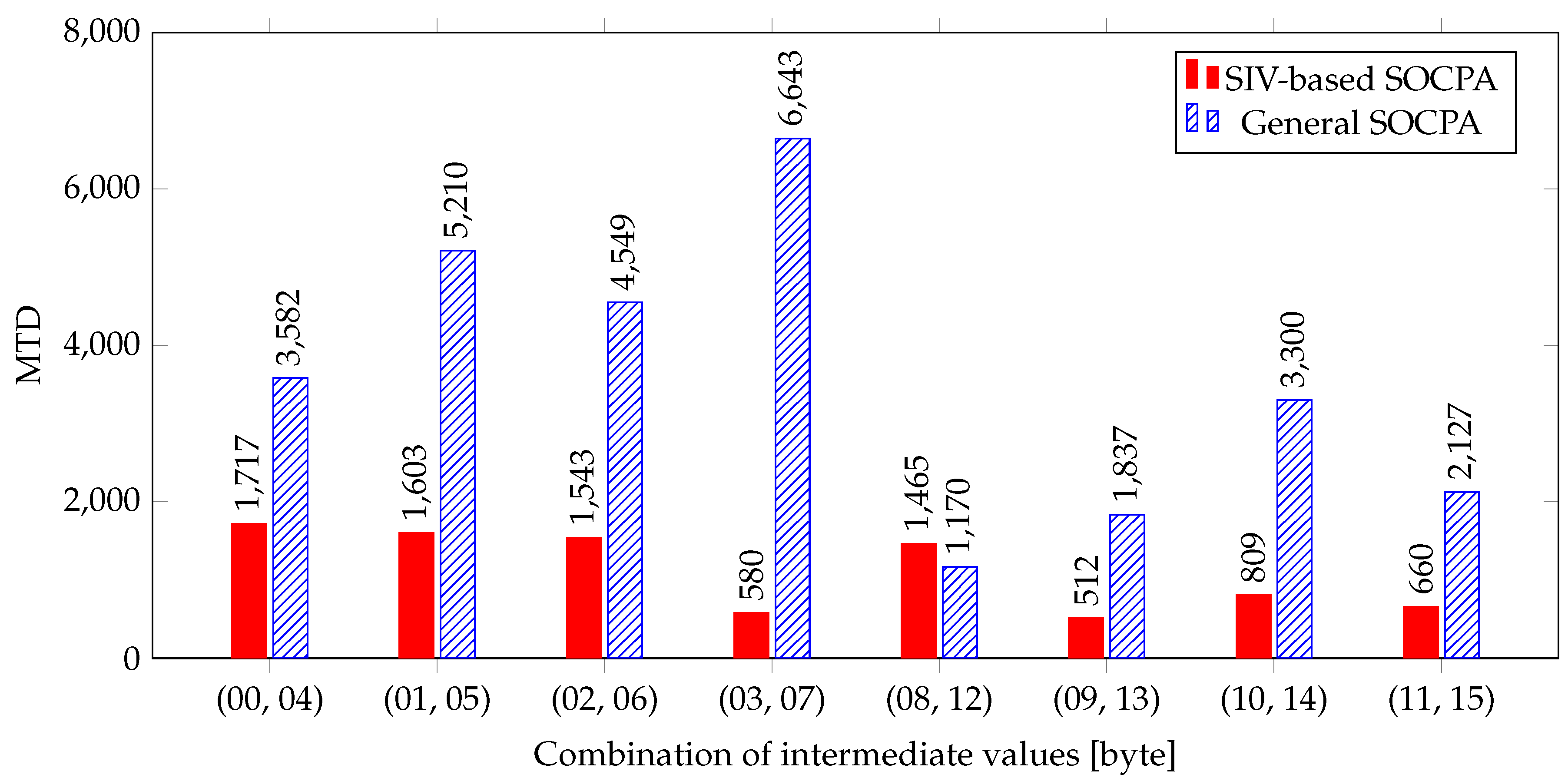
We analyzed the AES of OpenSSL, which is one of the most commonly used secure socket layer toolkit. As shown in
Table 5, correlation is increased from 0.0910 to 0.1722, and the
SIV-based SOCPA can disclose the entire secret key with only about quarter trace required for the
General SOCPA. The correlation is lower than the theoretical value 1.00 and MTD is not reduced as much as the theory, because the remaining 24 bits behave similarly to noise. However, we showed that the SIV-based SOCPA could improve the analysis performance by more than four times.
Two countermeasures against the SIV-based SOCPA were recommended. The first is the ability to double the keyspace that must be guessed to calculate SIV, which increases the time complexity by 65,536 times. The countermeasure does not require any computation and memory overhead. Next is the implementation of the lookup table, which performs transformation without the subroutine that causes the SIV. This countermeasure has a 4 KB memory overhead. Typically, these two countermeasures provide guidelines for implementation that are resistant to the SIV-based SOCPA.
Our limitation is that, unlike improvements the preprocessing function is applicable to every cryptography, SIV-based SOCPA has to analyze the operational characteristic to determine the SIV for each cryptography, and we only discovered the SIV of the AES. And we applied only to the AES
7. Conclusions
In this paper, we proposed a special intermediate value, SIV, that has a unique characteristic.
The SIV improves the SOCPA performance significantly because it can accurately model power consumption and retain the theoretical correlation of 1-bit intermediate value. When the length of the intermediate value is 8, existing researches have only improved the correlation to 0.35, but the SIV has remarkably raised the correlation to 1.00. That is, the MTD for the General SOCPA requires at least 8.1633 times more traces than the FOCPA, whereas the SIV-based SOCPA is theoretically the same as the FOCPA.
We analyzed the OpenSSL, which is the most commonly used open-source secure socket layer, and confirmed that there exists the SIV. Consequently, the proposed SIV-based SOCPA can disclose the whole secret key using only a quarter of the trace required by the General SOCPA. Further, we recommended two countermeasures as a guideline for implementing a cryptographic algorithm that is resistant to the proposed method.
The limitation of the proposed method is that it has to discover the SIV for each cryptographic algorithms or implementation. In this paper, only the AES was analyzed. Finding the SIV from other cryptographic algorithms is an interesting further work. Thus in the future, we are going to apply to the proposed method for other cryptographic algorithms.