Abstract
A novel method of bionic Morse coding mimicking humpback whale vocal is presented for covert underwater acoustic communication. The complex humpback whale song is translated as bionic Morse codes based on information entropy. The communication signal is made akin to the natural singing of male humpback whales. The intruder can detect the signal but will not be able to recognize the communication signal due to unified resemblance with the natural sound. This novel technique gives an excellent low probability of recognition characteristics. A flawless stealthy underwater acoustic communication has been established which has negligible chances of deciphered with high imperceptibility. Standard mimicry Morse codes have been developed for the characters of the English language and compared with Morse coding. Covert information of one character per second can be watermarked with perfect stealth and clandestine communication. This novel concept has been verified at transmission distance of five km and less than 10−3 Bit Error Rate (BER) is achieved at Signal to Noise Ratio (SNR) down to negative seven dB. Zero BER is attained by estimating the channel by a matching pursuit algorithm and equalizing the errors by virtual time reversal mirror technique.
1. Introduction
The security and privacy of information is one of the most critical issue of today’s fast moving world. Innovative and novel techniques are being explored to keep information safe from intruders [1]. The demand of secretly transmitting data in underwater acoustic channels is rapidly increasing in oceanography, military and naval operations [2,3]. Mariners desire to transmit their information clandestinely to secure it from data theft and malicious attacks [4]. Military and naval personnel need to hide their communication to prevent the leakage of such information to the enemy [5].
Covert Underwater Acoustic Communication (CUAC) is the key research area where information is transmitted furtively in an open underwater acoustic environment [6]. It is the concept of communicating secretively in an underwater acoustic channel. An underwater channel is considered as the preeminent medium for acoustic communication as sound transmitsfardistances [7,8]. The key challenge is to keep acoustic information safein the far flung sea. Variety of ways have been explored by scientists which will be discussed in detail. CUAC is classified into two major constraints as Low Probability of Detection (LPD) and Low Probability of Interception (LPI). LPD means that communication signals have a less chance ofdetection by eavesdroppers however LPI defines that communication signals can be detected by the intruder but that the enemy has a lesser chance ofextracting such information [9].
History of covert communication goes back a long way with the invention of communication; as a user needs to hide sensitive information from the enemy [10]. During World War I and II, Morse codes were extensively used for transmitting secret messages [11]. It consists of two elements termed as a dot and dash. The American Standard Code for Information Interchange (ASCII) characters are represented by a combination of these elements. Covert communication is attained by the coded combinations of Morse elements. The enemy can detect the communication signal but has less of a chance to decode the information. Perfect LPI constraint communication is achieved in underwater telephone and telegraph systems using Morse coding. The drawback of this technology is that the enemy can detect the existence of the communication and could try to decode the coded format.
In an underwater acoustic channel, earliest LPD constraint covert communication with best of our knowledge was conducted back in 1986 by J.H. Park by spreading the waveform [12]. Until the last decade, CUAC was established by reducing the SNR and spreading the waveform through Direct Sequence Spread Spectrum (DSSS) [13], Orthogonal Frequency Division Multiplexing (OFDM) [14] and other modulation techniques. It was realized however that as the enemy approaches towards the transmitter the LPD constraint communication signal is perceived by the eavesdropper as the SNR is increased by limiting the distance [15]. It is similar to the situation of two people having a secret talk and when a third person approaches them, their communication doesnot remain covert. Scientists have given a lot of contributions to increase the covert distance but it cannot be true for all regions [15,16,17]. This technique gives perfect CUAC for a bounded region but it doesnot remain covert for all communication ranges.
To trounce back above limitation, biological inspired mimicry CUAC was introduced. It is an entirely different approach where the communication signal is made akin to the natural sounds of the sea [18]. A large variety of natural noises are present in the ocean such as shipping noises, cetacean vocals, shrimp noises, wind noises, sea piling noises, etc. The natural ocean noise is mimicked by modulating or watermarking the covert information in it. The mimicked communication signal is detected by the enemy but it is excluded from the process of recognition due to its identicalness with the natural sound. The intruder assumes it as the sea natural noise due to its characteristics. It gives excellent Low Probability of Recognition (LPR) characteristics and covert communication is possible in all ranges at high SNR. First covert experiment mimicking cetacean vocals to our best knowledge was conducted by H.S. Dol et al. by dolphin clicks and whistles [19]. Liu et al. used high frequency dolphin clicks as an information carrier for covert communication [20]. Initially they attained a 37 bps data rate, which later increased to 69 bps [21]. Dolphin whistles are mimicked using differential pattern time delay shift coding for clandestine communication [22]. Duman et al. conducted successful tests for covert communication by using white sided dolphin and long fined pilot whale whistles [23]. A sea lion vocal was analyzed by Y. Jia et al. for mimicry communication and data was encapsulated. Simulation results showed a BER of almost zero [24]. Another novel method of covert mimicry communication was presented and tested using sea piling sounds using pulse position modulation [25]. A portable modemhas also been developed and tested which is suitable for transmitting mimicked covert signals [26].
Our research focuses on the development of standard mimicry codes similar to Morse code [27] based on sea natural noise. Conventional Morse codes are detected by the enemy and may be decoded. Our innovative coding technique is based on a carrier of humpback whale songs. Male humpback whales are famous for producing loud and long duration songs. They emit a vocal termed as a song in the frequency range of 8 Hz–8 kHz lasting from several minutes to hours. It is composed of several segments which are frequency and amplitude modulated. The whale song segments are mimicked into bionic Morse codes using information entropy for the characters of the English language. It gives perfect LPR constraint covert communication as the imitated communication signals have no chance of being recognized as a communication signal as it is composed of a natural humpback whale song. Our novel concept has been compared with Morse codes and better performance is achieved with a perfect covert prospective. A covert data rate of one character per second is achieved with negligible chances of detection. The novel concept has been verified at distances of five km and less than 10−3 BER is achieved. This proves that the proposed method is feasible for LPR constraint covert underwater acoustic communication for long distances.
This paper is organized as follows: Section 2 describes the technical characteristics of humpback whale songs. Section 3 highlights the contribution for the development of bionic Morse codes and comparison with Morse codes. The process of bionic Morse coding is briefly demonstrated in Section 4. Section 5 proves the novel concept feasible through the simulation experiment. Finally Section 6 concludes the paper and highlights the future research direction.
2. Characteristics of Humpback Whale Songs
The ocean is filled up of millions of sea creatures which emit sounds for detecting prey and predators, echo localizing and social interaction. Due to extremely low visibility in the sea, cetaceans rely on acoustic energy for communication [28]. The natural vocals produced by sea marine mammal ranges in the frequency band of 15 Hz to over 100 kHz [6]. They produce a variety of vocals termed as clicks, whistles, bursts and songs for different purposes [29]. They are recognized as sea noises as they are an unwanted signal for underwater communication. We take advantage of the naturally occurring sounds to embed information to realize covert mimicry communication.
Humpback whales (Megaptera novaeangliae) are one of the biggest cetacean in the ocean. They produce clicks, whistles and songs with a high source level and low frequency range. Male whales are famous in producing long and loud songs lasting from several minutes to hours. If there is a song contest between cetaceans, a humpback whale song will no doubt be victorious [30]. As well as being aesthetically attractive, humpback whale songs have been and are still being studied extensively, mostly to understand why humpback whales sing. In fact only male humpbacks are known to sing and in general only when swimming alone, and songs are primarily performed in the winter breeding season [31].
Generallyhumpback whale song lies in the frequency range of 8 Hz–8 kHz and the main energy concentrates on the bandwidth of 30 Hz–4 kHz. They emit songs at high source level around 175–188 dB re 1fPa@lm (one femto Pascal measured at one meter distance) [32]. The song of a humpback whale can be heard from far distances in the ocean due to its high source level and low frequency range. The structure of a humpback whale song is the most complex vocal emitted by cetacean [33]. One whale sings continuously for hours. The song is composed of three to nine themes and it takes ten to fifteen minutes to return backto theinitial theme. Every theme compromises of phrases that repeat several times before a new theme. One phrase is made up of a series of different sound segments and lasts about several seconds. They also learn new songs and sing with new themes and patterns [34]. The pattern of a song is not fixed as it changes in different recordings. This is similar as a human singer sings multiple songs in various patterns and also learns and sings new songs [35]. However the humpback whale sings songs with a bandwidth of 8 kHz. The songs are broadband in nature modulated with a range of frequencies within the bandwidth. A sample structure of a complex humpback whale song phrase acquired from the ocean acoustic library [36] is shown in Figure 1.
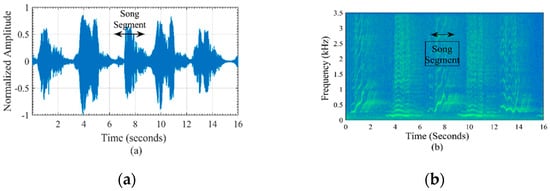
Figure 1.
Humpback whale song phrase in (a) time and (b) frequency domain.
The song phrase has five unique segments. It can be clearly see from Figure 1 that all the song segments are frequency and amplitude modulated and differ from each other. This uniqueness in different segments is used as a benefit to perform covert operations by coding song segments into unique elements of bionic Morse codes. The communication signal will be composed of humpback whale song segments where the natural song segments will represent the information at the receiver. The eavesdropper will detect the signal but exclude it in a process of recognition as it will assume it as a natural humpback whale song giving perfect LPR constraint covert communication. We opted to mimic a humpback whale song for covert communication due to its characteristics. Long range transmission of a humpback song benefits us to do covert communication for a larger distance and large duration gives us an additional advantage to perform a covert operation for an elongated period.
3. Cetacean Morse Codes
Morse codes are extremely traditional codes for encoding the characters which use combinations of dots, dashes and intervals [11,27] invented by Samuel F. B. Morse in the 18th century. They are composed of dots and dashes also termed as dit and dah which are represented as and respectively. Initially these codes were used for transmitting messages through telegraph, however later it was used to send secret messages by changing the coding algorithm [11]. It was extensively used in World War II. These codes are still being used today in military, oceanography, and amateur radio systems [37].
Theinternational Morse codes for English characters are shown in Table 1. In this paper, we will only discuss alphabets of the English language. The duration of dot is one unit and dash is thrice each dot. Each character and word are segregated by the time duration of three and seven dots respectively. The drawback of this technique is that the dot and dash can be detected by the eavesdropper since they are not a sea natural sound. The coding can be made covert by making unique combinations; however it will be intercepted by the enemy. The enemy can detect the existence of communication. The motive of our mimicry covert communication is that an eavesdropper is not able to identify the existence of communication.

Table 1.
Representation of English language characters through Morse and bionic Morse codes.
To trounce the above limitation, we have improved Morse codes by using elements of natural occurring noises in the ocean. These may include sound produced by cetacean, shrimp, tide, raindrops or shipping noises. In this paper, we have used a humpback whale song as a carrier. Additionally, our technique uses four elements instead of two elements to shorten the duration of each character. As Morse codes uses dots and dashes, they are replaced by four unique segments of the song. New bionic Morse elements are termed as club, diamond, heart and spade represented by , , and respectively.
The characters are translated by the combination of these elements with a time interval between them. The time interval between element, character and word is set as 0.1, 0.2 and 0.5 s respectively. The code length is based on the frequency of the occurrence of a particular character in the English language. The frequency of occurrence of English characters are extracted from [38] which is based on high samples of English words. The higher frequency alphabets get shorter sequences whereas code length is increased as the frequency of occurrence is decreased. Therefore
Table 1 compares the representation of characters from Morse codes and the proposed bionic Morse codes. We can clearly notice that the innovative technique of bionic coding have less elements which increases the communication speed with perfectly LPR constraint covert operation.
The novel concept of bionic Morse codes is an enhanced version of Morse codes with the possibility for having mimicry covert communication. It has the additional benefit of a smaller sequence of elements which can be evidently witnessed from Table 1. Table 2 compares the differences of Morse codes and bionic Morse codes.

Table 2.
Comparison of Morse Codes and bionic Morse Codes.
4. Bionic Morse Coding Method
The process of bionic Morse coding mimicking sea natural noise is briefly discussed in this section. It is slightly different from the process of underwater acoustic communication as it requires the communication signal to be perfectly imperceptible to sea natural noise. The structure is shown in Figure 2. We will concisely elaborate on the process step by step with the practical example of mimicking a humpback whale song.
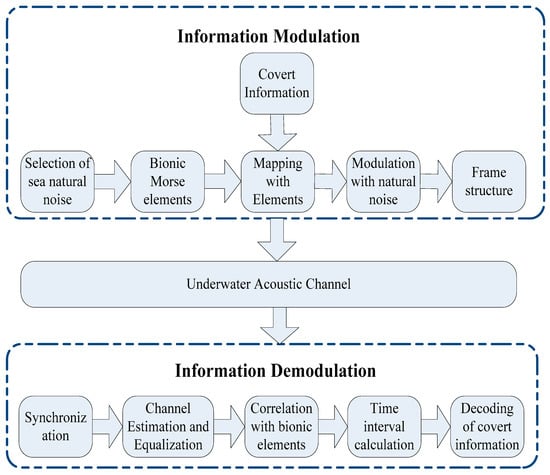
Figure 2.
The process of bionic Morse coding mimicking sea natural noise.
4.1. Information Modulation
4.1.1. Step 1: Selection of Carrier
The most important process of bionic Morse coding is the selection of sea natural sound as carrier. As it has been discussed before there are various noises present in the ocean. Cetacean emits a variety of sounds to detect prey, predators, echo localize and for social interaction. The selection of a carrier is based on the characteristics of the sea natural noise suitable for the practical scenario. The natural noise should be researched deeply into its characteristics and purposes for emitting a particular vocal, the amplitude, frequency, duration and modulation of a particular sound including its geographical location. Through this information, the noises are classified with respect to their sound features. For long range communication, a low frequency and high source level sound should be selected as it will transmit for a large transmission distance. For bionic Morse coding proposed in this research, the carrier signal must have at least five unique sounds with respect to frequency and amplitude. One acts as a synchronization of communication signals and four unique signals as bionic Morse codes which are elaborated in detail in the Section 4.1.2. Geographical location also plays a vital role as bionic covert communication should be done in the same location where the actual noise is present. Otherwise an enemy would guess that the particular noise is not available in that region.
In this research we opted to mimic a humpback whale song due to its natural characteristics. The song is composed at a low frequency range and high source level which benefits covert operations in a large region of ocean. The singing of a song for hours gives us an additional advantage to perform a covert operation for an elongated period.
4.1.2. Step 2: Synchronization and Bionic Morse Elements Waveforms
Identification of bionic Morse elements in a sea natural carrier is a crucial procedure in this proposed technique. These elements are used to encode and extract the covert information. All four elements and the synchronization signal should be different from each other with respect to time and frequency but lie within a same sound source. If an enemy detects the signal, it should assume it as a sea natural carrier due to its signal characteristics and imperceptibility with the real ocean noise. A whole communication signal including a synchronization header should be analogous with the noise present in the ocean.
In this research we used a humpback whale song as a bionic carrier. The song phrase of whale has unique segments with respect to amplitude and frequency. Figure 3 shows the time frequency graph of all segments distinctly. It is visibly observed that each waveform is distinguishable and has a unique frequency that lies within the bandwidth of 4 kHz. One segment is used for synchronization and other segments represents bionic Morse elements termed as club, diamond, heart and spade.
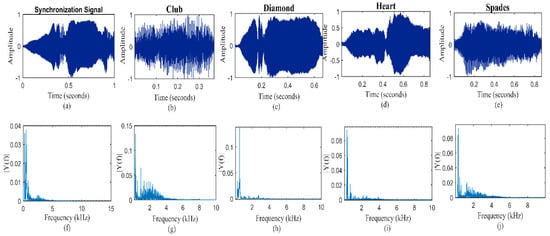
Figure 3.
(a) Synchronization signal, (b–e) bionic Morse elements as club, diamond, heart and spades in time domain, and (f) shows single sided Fourier transform of synchronization signal and (g–j) bionic Morse elements respectively.
All the bionic Morse elements and synchronization signals should be non-identical to each other in this proposed mimicry communication technique. They should be dissimilar because they are used to represent covert information. Figure 4 shows the cross and auto correlation between synchronization signal and bionic Morse elements which proves that these waveforms are non-analogous to each other. In figure we represent C and S with correlation and synchronization signal and numbered 1,2,3,4 to club, diamond, hearts and spades respectively. In Figure 4 CSS means that it is an auto correlation of synchronization signal and C21 represents the cross correlation between diamond and club bionic Morse elements.
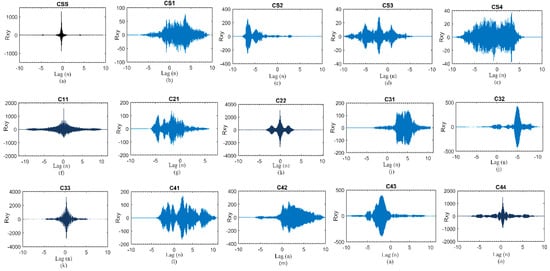
Figure 4.
Correlation between synchronization signal and bionic Morse elements.
Figure 4a–e shows the auto and cross correlation of a synchronization signal with bionic Morse elements. It can clearly witness the high correlation peak only in (a) which dictates that the synchronization signal is only identical to its signal and different from other bionic Morse elements. Similarly Figure 4f–o shows the auto and cross correlation between bionic Morse elements. We can notice that C11, C22, C33, and C44 have high correlation peaks which are not uniform in other correlation outputs. This proves that the waveforms of bionic Morse elements and synchronization signal are dis similar and they could be easily distinguishable at the receiver. The waveform can be decoded at the receiver through correlation technique. The demodulation process is briefly elaborated in Section 4.2.
4.1.3. Step 3: Mapping of Covert Information to Bionic Morse Elements
In this section, the covert information is mapped with the bionic Morse elements. In Section 3 we defined bionic Morse codes. These codes will be used in this process. Each character of the English language is equivalent to one to three bionic Morse elements as shown in Table 2. The translation of covert information to a mimicked message is done through the procedure describe in Section 3. Let us translate two words “COVERT” and “COMMUNICATION” in mimicked message using elements of a humpback whale song.
where, , , and represents club, diamond, heart and spade respectively and is equal to s. In this paper we have kept time delay to be 100 micro s. It can be increased which will result in decreasing the covert data rate.
4.1.4. Step 4: Modulation of Covert Information to Mimicked Message
In this step we modulate our covert information of bionic codes in to the sea natural noise carrier. Using the defined bionic element in step 2, the information can be translated in a humpback mimicked message. Figure 5 shows the mimicked humpback whale song representing the word “COVERT” and “COMMUNICATION”.
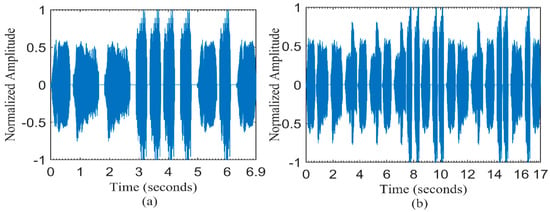
Figure 5.
A mimicked signal through a humpback whale song using bionic codes representing (a) COVERT (b) COMMUNICATION.
Covert communication speed can be defined as the mean time duration of characters watermarked in the mimicked signal. It will be equal to the total number of characters embedded in the total time of frame excluding the synchronization time. Therefore, we can write as
where is the average speed of character, is the total time of signal, is the time of the synchronization frame and represents the total number of characters in the communication signal. By using this humpback whale song segments, we found that we can watermark one character/s with a perfectly covert perspective using the proposed technique.
4.1.5. Step 5: Frame Structure
The entire communication frame of bionic mimicry communication should be composed of sea natural sound including the synchronization header. It should give perfect imperceptibility with sea natural sounds. If the synchronization header is different from the sea natural noise, the enemy will detect it making the covert communication false.
The synchronization header plays an important role in bionic mimicry covert communication. We know that this type of communication needs to be done where the actual sea natural sound is present. The synchronization header acts as a differentiator between the real sea natural sound and the mimicked signal at the receiver. This is done through adding a checksum of bits in the unique sea natural noise assigned as synchronization.
The frame structure of the proposed novel method is shown in Figure 6. For mimicking through a humpback whale song, the first segment of the song phrase is used as synchronization. This song phrase is defined at an intended receiver. The receiver accepts it as a communication frame in two steps. First it recognizes the song phrase. Secondly it verifies it by the checksum of bits. The communication frame contains covert information modulated as bionic Morse elements using a humpback song.

Figure 6.
Frame structure of bionic mimicry communication.
The complete communication frame is composed of a humpback whale song. The communication frame is perfectly imperceptible of a humpback whale song as all its ingredients are made up of natural sounds present in ocean. If the enemy detects this mimicked signal, it will exclude it from the process of recognition assuming it has a humpback whale song. This frame structure is transmitted to an underwater channel giving perfect LPR constraint covert communication.
4.2. Information Modulation
The information demodulation at a receiver after passing through an underwater channel is composed of following major steps.
4.2.1. Step 1: Synchronization
The first step at the receiver is to identify the mimicked signal. A variety of similar noises are present is the sea. The synchronization header plays an important role in the identification of the mimicked waveform and differentiating it with real sea noise. This is done through correlation with the synchronization vocal and verifying it by the checksum of bits in the synchronization header. If the numbers of bits are not same as defined in the synchronization header, it could be the ocean noise. The synchronization waveform with the checksum of bits should be known to the receiver.
In this research we have used a humpback whale song for bionic communication. The synchronization signal is also composed of one segment of a humpback whale song. The time and transform characteristics of the synchronization waveform are shown in Figure 3a,f respectively. It is the broadband signal modulated with a wide range of frequencies from 0.1 to 3.5 kHz. The first segment of Figure 1b is used as a synchronization signal in this research. We can clearly notice from Figure 1 that all the segments are broadband in nature modulated with multiple frequencies. Figure 7 shows that the characteristics of humpback whale song with respect to the Doppler factor and auto correlation. The Doppler factor is calculated by change in frequency with respect to carrier frequency. Therefore it can be equated as
where is the Doppler factor and and represents the change in frequency and carrier frequency respectively.
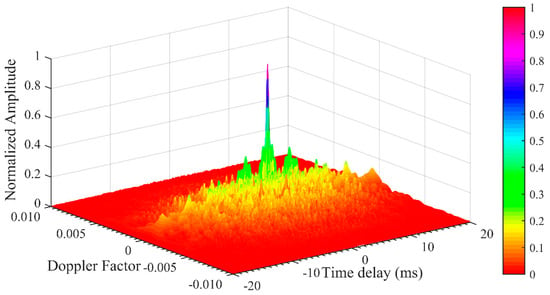
Figure 7.
Ambiguity function of a humpback whale song.
The received signal from the channel is composed of the synchronization signal and the message signal. First the synchronization signal is identified using a correlation method. Figure 8 demonstrates the detection process of the synchronization signal from the received waveform. The high peak of correlation illustrates that the correct mimicked signal is received at the receiver. Since there are plenty of similar vocals present in the ocean, the synchronization signal is verified by checking the checksum of bits.
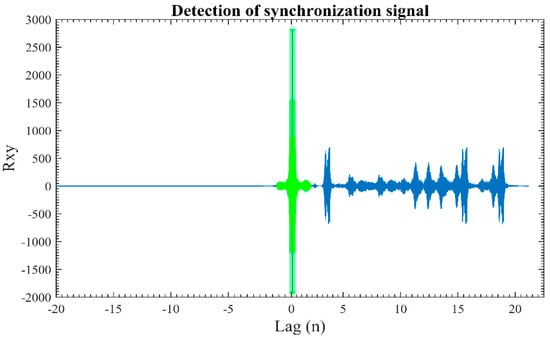
Figure 8.
Detection of the synchronization waveform at the receiver.
After the verification of the correct synchronization received, it is removed from the received signal. Now the received signal consists of a message frame modulated with bionic Morse elements which holds covert information. Detection of bionic Morse elements and mapping it to covert information is briefly elaborated in Section 4.2.3 and Section 4.2.5 respectively.
4.2.2. Step 2: Channel Estimation and Equalization
The acoustic channel in the underwater sea environment degrades the communication signal poorly due to multipath arrivals, frequency and time variance [39]. These variations are adjusted by estimating the channel and equalizing the errors through the estimated channel impulse response. The goal of channel estimation and equalization is to enhance the performance of system. In this research, the matching pursuit (MP) estimation technique is opted for due to its robustness in changing the SNR and higher computational efficiency [40]. It sequentially identifies and estimates channel tap coefficients. Let us consider that the multipath channel has Additive White Gaussian Noise (AWGN) with variance σ2. The received signal can be written as
where = 0, 1, 2 …, , is the transmitted symbol, is the th channel tap and is the AWGN. The equation can be expanded as
It can be seen from Equation (4) that the majority of the components of channel tap are extremely small or zero. Therefore, the columns of are added to get the received data. The residual is acquired by the difference of and for − 1 iterations, considering . At th iteration, the column of onto which the residual has the maximal rank-one projection denoted as is equated as
where, represents the column of and superscript is defined for Hermitian Transpose. is the index set of all previously selected columns. The component of termed as associated by is estimated as
Hence, the residual vector is calculated as
The objective of the channel estimation and equalization is to enhance the performance of the system. It reduces the bit error rate by evaluating the effect of multipath, time and frequency variance in an underwater acoustic channel. The channel equalization adds the distributed energy of multipath arrivals projected by the channel estimation technique which reduce errors. We equalize the errors using a virtual time reversal method (VTRM). The framework of the VTRM is shown in Figure 9. The estimated channel is inverted in time domain and convolved with . The final virtual signal received is acquired by convolving the received signal by the inverted estimated channel. Therefore:
where is the equalized signal and represents the convolution operator. The VTRM equalized channel is equated as . When the estimated channel approaches to the real channel , the multipath signals are overlapped with each other making the communication signal energy strong and efficient. It also restrains inter symbol interference caused by multi path arrivals.
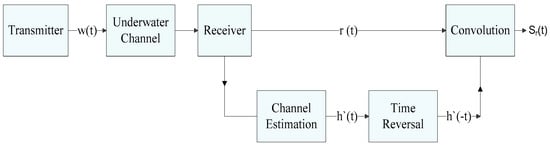
Figure 9.
Frame work of Virtual Time Reversal Mirror method.
4.2.3. Step 3: Detection of Bionic Morse Elements
The next step is to demodulate the covert information. The covert information is extracted by the detection of bionic Morse elements present in the communication message signal. The receiver is aware of bionic Morse elements in this novel technique. The covert information is extracted by matching the received signal with bionic Morse elements using correlation. It gives a high peak value if the communication signal matches the specific interval of time. Mathematically correlation can be written as
where is the correlation for all values of . and are the transmitted and received signal respectively. For this method the value of is one to four since we have four elements. Figure 10 demonstrates the detection process of bionic Morse elements club, diamond, heart and spade from the mimicked waveform holding covert information “COMMUNICATION”. We can clearly notice that the correlation gives the high peak showing the existence of the element. These positions are stored which will be further used to map the covert information.
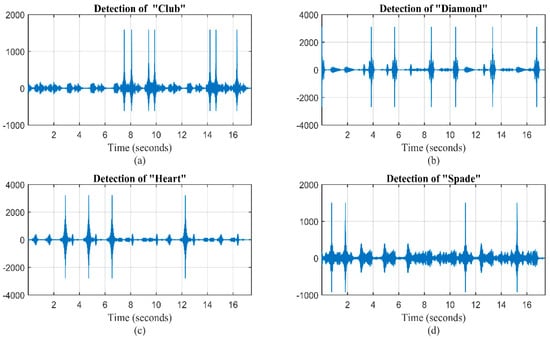
Figure 10.
Detection of bionic Morse elements (a) club, (b) diamond, (c) heart and (d) spade from a mimicked message “COMMUNICATION”.
4.2.4. Step 4: Time Interval
This step calculates the time gap between the correlation peaks obtained in the last process. The time interval is used to map the covert information. In this method, letters of the English language are defined through one to three bionic Morse elements as listed in Table 1. One letter may consist the element of other letter. To differentiate this lack, a time delay is inserted between the elements and characters. Let the time delay and the time duration of bionic Morse element be denoted as and respectively. In the modulation process, the time interval between the elements and characters are set as 0.1 and 0.2 s respectively. We took the mean value in the detection.
Let be the threshold time termed as . If 0.15 s, it means that the next element is part of the same character. If this condition is false, it represents that other characters have startedand the element is part of other characters. Let us understand with the help of an example. Figure 11 shows the detection of “club” in the mimicked message “COVERT”. The of element club is 0.37 s. The first correlation peak is detected at 2.9 s. The subsequent correlation peak at 3.37 s. Time delay is calculated as 0.47 s. Therefore = 0.1 s which means that the subsequent element is part of the same character. The green embossed correlation peak lies in the same character representing the English letter “V”. The fourth correlation peak dictates that the new character has started as of fourth and third peak is calculated as 0.2 s.
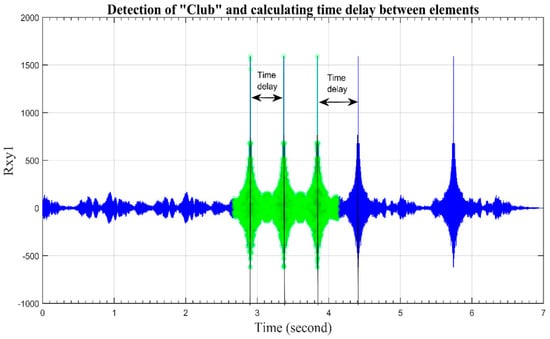
Figure 11.
Detection of “club” and calculation of time delay between elements.
4.2.5. Step 5: Mapping of Covert Information
The last step of information demodulation is mapping. This step is the inverse of step 3 in the information modulation procedure. In last two steps we obtained the location of the bionic Morse elements and determined the time delay between them. This data is used to map the covert information. The location and delay are mapped into English language characters according to Table 1. Combing the results of step 4 and step 5, we get the output as shown in Figure 12.

Figure 12.
Extraction of mimicked information “COMMUNICATION” from the received signal.
The above frame describes the covert information. S and N represent the same letter and next letter respectively based on the value of time threshold as calculated in the previous Section 4.2.4. Finally, mapping of this information with the Table 1 gives us the word “COMMUNICATION” which is our covert information transmitted in a mimicked humpback whale song.
5. Imperceptibility
Imperceptibility is tool to measure the similarity or resemblance between signals. This is the most vital parameter in mimicry covert underwater acoustic communication. The main key of biologically inspired covert communication is the likeness of a man-made signal with real sea ocean noise [4]. The mimicked signal containing a watermark should be akin to the original ocean noise. When the eavesdropper detects the mimicked signal it should be identified as a cetacean vocal due to its resemblance in structure, time duration, intensity, frequency and modulation. The geographical location of a particular vocal should also be considered and covert experiments should be performed in the same particular region where the specific cetacean exists. The mimicked signal should be highly imperceptible with the real ocean noise waveform.
There are a variety of methods to measure imperceptibility ofaudio vocals. Usually imperceptibility is measured through a human auditory system (HAS), time correlation and comparing the frequency spectrum [41,42]. Correlation methods are usually used if any information is embedded in the audio signal. It checks the similarity between two signals by a cross correlation of waveforms. The higher the value of correlation equates to higher imperceptibility. HAS is used to check imperceptibility by the response of users listening to the voice. It is done by making a mean score through a pool of people listening the voice. If the mean score is higher, then it is assumed that the voices are similar. Another method to check imperceptibility is by comparing the frequency spectrum of the original and mimicked signal. This is done by mapping the spectrum characteristics of the real and mimicked voice. If the sound holds the characteristics of a particular vocal, it is identified as the particular vocal. In this article, we opted to estimate imperceptibility by comparing the frequency spectrum.
In this research, the covert information is watermarked by shuffling the humpback whale song segments. None of the ingredients other than the humpback whale song is added in the communication waveform, however the pattern of the humpback whale is altered. The humpback whale produces long duration songs with a variety of themes and patterns. Each theme is composed of phrases that repeat several times before a new theme. The exact pattern of the humpback whale song or repetition of phrases is unknown [43]. There is no evidence that humpback songs are hierarchically structured [35]. However they sing the song in the bandwidth of 8 kHz. New humpback whale songs are being discovered with new phrases and patterns [34]. This is similar to an English speaking singer singing the songs. He will sing a variety of songs but a listener will identify it all as English songs. Thus we can conclude that a humpback whale sings a variety of songs with diverse patterns within its bandwidth range and spectrum characteristics.
To verify the variable patterns of a humpback whale song, several samples of humpback whale songs are compared. Figure 13 shows the spectrum characteristics of some phrases of different humpback whale songs depicted from the ocean acoustic library [36]. It is evident form the figure that humpback whale songs have diverse characteristics with various patterns but the bandwidth of the waveform lies within 8 kHz. The main energy in concentrated within 4 kHz. Thus we can conclude there is no fix pattern of humpback whale songs.
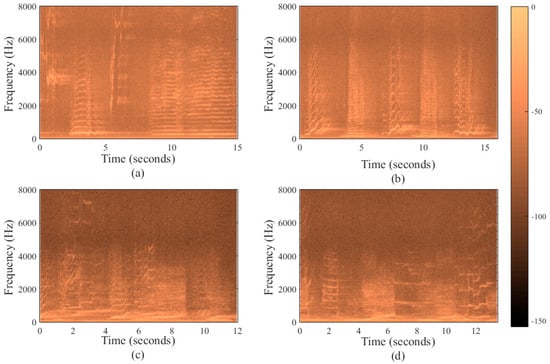
Figure 13.
Spectrum of multiple humpback whale songs’ segments. (a–d) shows the spectrum of four different Humpback whale songs. We can clearly notice that the frequency spectrum of all humpback whale songs are different and not identical which shows that they don’t have any regular pattern.
For mimicry covert underwater acoustic communication, if the enemy detects the mimicked signal it will exclude it from the process of recognition assuming it as a humpback whale song due to its characteristics. The pattern will not be analyzed as a humpback whale sings song with unique patterns. Therefore, we can say that the proposed mimicry covert underwater acoustic communication gives perfect imperceptibility with natural humpback whale songs. It can give perfect LPR constraint covert communication in an underwater acoustic channel.
6. Simulation Experiment
To verify the feasibility of the proposed novel method, simulation experiments were conducted in Additive White Gaussian Noise AWGN and multipath channels of a sea medium. The performance of a covert information word “COVERTCOMMUNICATION” is analyzed in this experiment. Information is modulated mimicking humpback whale song using bionic Morse code.
The performance of the multipath channel is verified by the simulation experiment using a Bellhop ray tracing algorithm in MATLAB. Real data of a sound speed profile is extracted from the World Ocean Atlas [44] which is shown in Figure 14a. The channel impulse response based on the sound velocities is graphed in Figure 14b. The ideal surface and bottom are selected in this simulation which has a total reflection. Long distance covert communication has been performed at a five km distance. The transmitter and receiver depth are selected at 20 m and 25 m respectively. The depth of the sea is 60 m. The beam angle is acoustic rays is 30 degrees.
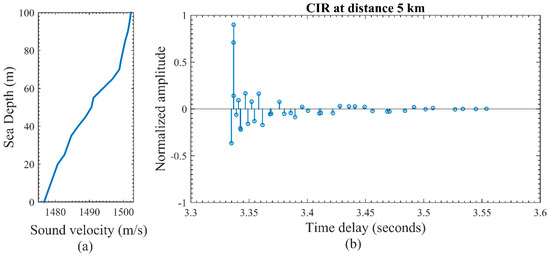
Figure 14.
(a) Sound velocity profile of the channel. (b) Channel impulse response based on sound speed profile.
To overcome the effects of multipath arrivals and reduce BER, the MP estimation algorithm and VTRM technique are used for channel estimation and equalization, respectively. The estimated channel is shown in Figure 15. From the figure, it can be seen that there is one direct path with a high energy coefficient and others are indirect paths with a lower amplitude and a small time delay. These are multipath arrivals which have been created due to the echoes from the surface and bottom of the sea. The high energy components were accumulated, while the low energy delayed arrivals were ignored for the sake of simplicity. The errors were equalized using the VTRM equalization technique discussed in Section 4.2.
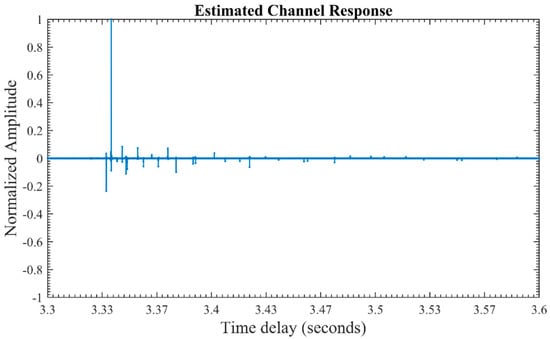
Figure 15.
MP Estimated Channel Impulse Response.
Figure 16 illustrates the BER curve of the proposed bionic method for covert information. First the performance of the AWGN channel is observed. The red dotted line BER curve in Figure 16 depicts the performance of the proposed method in the AWGN channel. It can be evidently seen that it is not much affected by AWGN and gives zero BER with SNR greater than 15 dB. The blue line is the BER with simulated channel whose channel impulse response is shown in Figure 14b. It clearly depicts that 10−3 BER is achieved at SNR −7 dB. The green curve shows the BER achieved after estimating the channel by MP algorithm. It further decrease the errors drastically from −14 dB. Zero BER is achieved at SNR greater than −11 dB. The resultsprovesthat the proposed method is perfect for underwater commination due to extremely low BER. Further it gives perfect covert LPR constraint covert communication. The proposed method is feasible for perfect covert operation at extremely low BER.
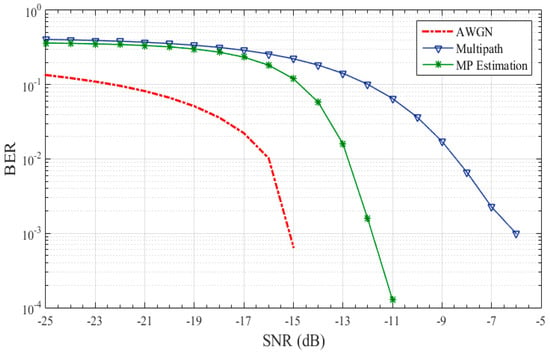
Figure 16.
BER curve of mimicked signals at a five km distance.
7. Conclusions
An innovative bionic Morse coding technique mimicking a humpback whale song is presented in this research. The mimicked communication signal can be detected by the eavesdropper but is excluded from the process of recognition as the communication signal characteristics are akin to a humpback whale song. The eavesdropper will assume it as a natural sound due to its signature. The humpback whale song segments are translated to standardized bionic Morse codes. Characters of the English language are compared with traditional Morse coding and found better speed with lower complexity. Less than 10−3 BER is achieved at a five km transmission at SNR down to −7 dB. The errors were diminished to zero BER by MP estimation and equalizing errors by VTRM technology. Proposed novel bionic Morse coding technique is feasible for LPR constraint covert communication which can be applied in military and oceanography for perfectly secure and stealthy communications. Future works include to verify the novel concept with the Doppler spread and experiments in lake and sea trails.
Author Contributions
All authors contributed significantly to the work presented in this manuscript. The detail of contribution is: conceptualization, S.L. and M.B.; methodology, M.B.; software, M.B.; validation, S.L., L.W. and G.Q.; formal analysis, S.L., M.B. and Y.T.; investigation, M.B. and L.W.; resources, G.Q.; data curation, S.L. and Y.T.; writing—original draft preparation, M.B.; writing—review and editing, S.L.; visualization, S.L. and M.B.; supervision, G.Q. All authors have read and agreed to the published version of the manuscript.
Funding
This work was funded by the National Natural Science Foundation of China [Grant Nos. 61771152, 61431004, 61601136 and 61601137], National Key R&D Program of China [Grant Nos. 2018YFC0308500 and 2017YFC0305702] and the Natural Science Foundation of Heilongjiang Province of China (Grant No. YQ2019F002).
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zuber, K.W.; Opieliński, K.J. Animal Mimicry in Covert Underwater Communication: Application of Syntax Generation and Simulated Genome Method. In Proceedings of the 2018 Joint Conference—Acoustics, Ustka, Poland, 11–14 September 2018; pp. 1–5. [Google Scholar]
- Diamant, R.; Lampe, L. Low Probability of Detection for Underwater Acoustic Communication: A Review. IEEE Access 2018, 6, 19099–19112. [Google Scholar] [CrossRef]
- Baek, C.-U.; Jung, J.-W.; Do, D.-W. Study on the Structure of an Efficient Receiver for Covert Underwater Communication Using Direct Sequence Spread Spectrum. Appl. Sci. 2018, 8, 58. [Google Scholar] [CrossRef]
- Qiao, G.; Bilal, M.; Liu, S.; Ma, T.; Zhao, Y.; Kong, B. Symmetry Oriented Covert Acoustic Communication by Mimicking Humpback Whale Song. Symmetry 2019, 11, 752. [Google Scholar] [CrossRef]
- Jans, W.; Nissen, I.; Gerdes, F.; Sangfelt, E.; Solberg, C.-E.; van Walree, P. UUV—Covert acoustic communication—Preminilary results of first sea experiment. In Proceedings of the Undersea Defence Technology Conference and Exhibition, Hamburg, Germany, 27–29 June 2006. [Google Scholar]
- Qiao, G.; Bilal, M.; Liu, S.; Babar, Z.; Ma, T. Biologically inspired covert underwater acoustic communication—A review. Phys. Commun. 2018, 30, 107–114. [Google Scholar] [CrossRef]
- Stojanovic, M.; Freitag, L. Recent Trends in Underwater Acoustic Communications. Mar. Technol. Soc. J. 2013, 47, 45–50. [Google Scholar] [CrossRef]
- Liu, L.; Zhao, H.; Li, M.; Zhou, L.; Jin, J.; Zhang, J.; Lv, Z.; Ren, H.; Mao, J. Modelling and Simulation of Pseudo-Noise Sequence-Based Underwater Acoustic OSDM Communication System. Appl. Sci. 2019, 9, 2063. [Google Scholar] [CrossRef]
- Liu, S.; Qiao, G.; Ismail, A.; Liu, B.; Zhang, L. Covert underwater acoustic communication using whale noise masking on DSSS signal. In Proceedings of the OCEANS 2013 MTS/IEEE Bergen: The Challenges of the Northern Dimension, Bergen, Norway, 10–13 June 2013; IEEE Oceanic Engineering Society (IEEE/OES); Marine Technology Society (MTS): Washington, DC, USA, 2013. [Google Scholar]
- Chitre, M.; Shahabudeen, S.; Freitag, L.; Stojanovic, M. Recent advances in underwater acoustic communications & networking. In Proceedings of the Oceans 2008, Quebec City, QC, Canada, 15–18 September 2008; pp. 1–10. [Google Scholar]
- Wyler, A.R.; Ray, M.W. Aphasia for Morse code. Brain Lang. 1986, 27, 195–198. [Google Scholar] [CrossRef]
- Park, J.H. LPI Techniques in the Underwater Acoustic Channel. In Proceedings of the IEEE Military Communications Conference—Communications-Computers: Teamed for the 90’s, MILCOM 1986, Monterey, CA, USA, 5–9 October 1986; pp. 10.15.11–10.15.15. [Google Scholar]
- Yang, T.C.; Yang, W.-B. Performance analysis of direct-sequence spread-spectrum underwater acoustic communications with low signal-to-noise-ratio input signals. J. Acoust. Soc. Am. 2007, 123, 842–855. [Google Scholar] [CrossRef]
- Leus, G.; van Walree, P.A.; Boschma, J.; Fanciullacci, C.; Gerritsen, H.; Tusoni, P. Covert Underwater Communications with Multiband OFDM. In Proceedings of the Oceans 2008, Quebec City, QC, Canada, 15–18 September 2008; pp. 391–398. [Google Scholar]
- Diamant, R.; Lampe, L.; Gamroth, E. Bounds for Low Probability of Detection for Underwater Acoustic Communication. IEEE J. Ocean. Eng. 2017, 42, 143–155. [Google Scholar] [CrossRef]
- Yang, T.C.; Yang, W.-B. Low probability of detection underwater acoustic communication for mobile platforms. In Proceedings of the Oceans 2008 MTS/IEEE Conference, Quebec City, QC, Canada, 15–18 September 2008. [Google Scholar]
- Diamant, R.; Lampe, L.; Gamroth, E. Low probability of detection for underwater acoustic communication. In Proceedings of the 2014 Oceans—St. John’s, St. John’s, NL, Canada, 14–19 September 2014; pp. 1–6. [Google Scholar]
- Liu, S.; Qiao, G.; Ismail, A. Covert underwater acoustic communication using dolphin sounds. J. Acoust. Soc. Am. 2013, 133, EL300–EL306. [Google Scholar] [CrossRef]
- Dol, H.S.; Quesson, B.A.J.; Benders, F.P.A. Covert underwater communication with marine mammal sounds. In Proceedings of the UDT Europe 2008, Glasgow, UK, 10–12 June 2008; pp. 1–7. [Google Scholar]
- Liu, S.; Qiao, G.; Yu, Y.; Zhang, L.; Chen, T. Biologically inspired covert underwater acoustic communication using high frequency dolphin clicks. In Proceedings of the 2013 OCEANS, San Diego, CA, USA, 23–27 September 2013; IEEE: New York, NY, USA, 2013. [Google Scholar]
- Liu, S.; Liu, B.; Yin, Y.; Qiao, G. M-ray covert underwater acoustic communication by mimicking dolphin sounds. J. Harbin Eng. Univ. 2014, 35, 119–125. [Google Scholar] [CrossRef]
- Han, X.; Yin, J.; Du, P.; Zhang, X. Experimental demonstration of underwater acoustic communication using bionic signals. Appl. Acoust. 2014, 78, 7–10. [Google Scholar] [CrossRef]
- ElMoslimany, A.; Zhou, M.; Duman, T.M.; Papandreou-Suppappola, A. A new signaling scheme for Underwater Acoustic communications. In Proceedings of the 2013 OCEANS, San Diego, CA, USA, 23–27 September 2013; pp. 1–5. [Google Scholar]
- Jia, Y.; Liu, G.; Zhang, L. Bionic camouflage underwater acoustic communication based on sea lion sounds. In Proceedings of the 2015 International Conference on Control, Automation and Information Sciences (ICCAIS), Changshu, China, 29–31 October 2015; pp. 332–336. [Google Scholar]
- Liu, S.; Wang, M.; Ma, T.; Qiao, G.; Bilal, M. Covert underwater communication by camouflaging sea piling sounds. Appl. Acoust. 2018, 142, 29–35. [Google Scholar] [CrossRef]
- Qiao, G.; Zhao, Y.; Liu, S.; Bilal, M. Dolphin Sounds-Inspired Covert Underwater Acoustic Communication and Micro-Modem. Sensors 2017, 17, 2447. [Google Scholar] [CrossRef] [PubMed]
- Shinagawa, Y.; Kunii, T.L.; Kergosien, Y.L. Surface coding based on Morse theory. IEEE Comput. Graph. Appl. 1991, 11, 66–78. [Google Scholar] [CrossRef]
- Bahl, R.; Ura, T.; Sugimatsu, H.; Inoue, T.; Sakamaki, T.; Kojima, J.; Akamatsu, T.; Takahashi, H.; Behera, S.K.; Pattnaik, A.K.; et al. Acoustic Survey of Irrawaddy Dolphin Populations in Chilika Lagoon: First Test of a Compact High-Resolution Device. In Proceedings of the OCEANS 2006—Asia Pacific, Singapore, 16–19 May 2007; pp. 1–6. [Google Scholar]
- Zhang, L.; Wang, D.; Bao, C.; Wang, Y.; Xu, K. Large-Scale Whale-Call Classification by Transfer Learning on Multi-Scale Waveforms and Time-Frequency Features. Appl. Sci. 2019, 9, 1020. [Google Scholar] [CrossRef]
- Zimmer, W.M.X. Passive Acoustic Monitoring of Cetaceans; Cambridge University Press: Cambridge, UK, 2011; Volume 1. [Google Scholar]
- Payne, R.S.; McVay, S. Songs of Humpback Whales. Science 1971, 173, 585–597. [Google Scholar] [CrossRef]
- Mazhar, S.; Ura, T.; Bahl, R. Effect of Temporal Evolution of Songs on Cepstrum-based Voice Signature in Humpback Whales. In Proceedings of the OCEANS 2008—MTS/IEEE Kobe Techno-Ocean, Kobe, Japan, 8–11 April 2008; pp. 1–8. [Google Scholar]
- Adam, O.; Cazau, D.; Gandilhon, N.; Fabre, B.; Laitman, J.T.; Reidenberg, J.S. New acoustic model for humpback whale sound production. Appl. Acoust. 2013, 74, 1182–1190. [Google Scholar] [CrossRef]
- Green, S.R.; Mercado, E.; Pack, A.A.; Herman, L.M. Recurring patterns in the songs of humpback whales (Megaptera novaeangliae). Behav. Process. 2011, 86, 284–294. [Google Scholar] [CrossRef]
- Mercado, E., III; Handel, S. Understanding the structure of humpback whale songs (L). J. Acoust. Soc. Am. 2012, 132, 2947–2950. [Google Scholar] [CrossRef]
- Ocean Acoustic Libary. Available online: http://oalib.hlsresearch.com/ (accessed on 15 October 2019).
- Jiang, J.; Zhou, Z.; Yin, E.; Yu, Y.; Liu, Y.; Hu, D. A novel Morse code-inspired method for multiclass motor imagery brain–computer interface (BCI) design. Comput. Biol. Med. 2015, 66, 11–19. [Google Scholar] [CrossRef] [PubMed]
- Shah, A.; Saidin, A.Z.; Taha, I.F.; Zeki, A.M.; Bhatti, Z. Similarities and Dissimilarities between Character Frequencies of Written Text of Melayu, English, and Indonesian Languages. In Proceedings of the 2013 International Conference on Advanced Computer Science Applications and Technologies, Kuching, Malaysia, 23–24 December 2013; pp. 192–194. [Google Scholar]
- Yin, J.; Yang, G.; Huang, D.; Jin, L.; Guo, Q. Blind adaptive multi-user detection for under-ice acoustic communications with mobile interfering users. J. Acoust. Soc. Am. 2017, 141, EL70–EL75. [Google Scholar] [CrossRef] [PubMed]
- Cotter, S.F.; Rao, B.D. Sparse channel estimation via matching pursuit with application to equalization. IEEE Trans. Commun. 2002, 50, 374–377. [Google Scholar] [CrossRef]
- Saadi, S.; Merrad, A.; Benziane, A. Novel secured scheme for blind audio/speech norm-space watermarking by Arnold algorithm. Signal Process. 2019, 154, 74–86. [Google Scholar] [CrossRef]
- Hua, G.; Huang, J.; Shi, Y.Q.; Goh, J.; Thing, V.L.L. Twenty years of digital audio watermarking—A comprehensive review. Signal Process. 2016, 128, 222–242. [Google Scholar] [CrossRef]
- Smith, J.N.; Goldizen, A.W.; Dunlop, R.A.; Noad, M.J. Songs of male humpback whales, Megaptera novaeangliae, are involved in intersexual interactions. Anim. Behav. 2008, 76, 467–477. [Google Scholar] [CrossRef]
- NOAA. World Ocean Atlas. Available online: http://staff.washington.edu/dushaw/WOA/ (accessed on 15 October 2019).
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).