Abstract
This study defines the intrinsic and extrinsic motivational factors that influence the prevention of industrial technology leakage by high-tech company employees. It also investigates how these factors affect the employees’ intention to prevent leakage. Based on the TPB (theory of planned behavior), this study analyzes the relationship between “attitude toward behavior”, “subjective norm”, and “perceived behavioral control”, which in turn influences the behavioral intention to prevent such leakage. Specifically, an online survey was conducted among office workers in South Korea’s high-tech industry. A total of 200 questionnaires were collected and analyzed. As the analysis results show, intrinsic motivation has a positive effect on attitude toward behavior, subjective norms, and perceived behavioral control. Extrinsic motivation has a positive effect on subjective norms and perceived behavioral control but a negative effect on attitudes toward behavior. This study also proved, based on the TPB, that the three variables impact the behavioral intention to prevent technology leakage. These results confirm that, in the high-tech sector, where employees are highly specialized and autonomous, technical security behaviors are primarily influenced by individual professional ethics and judgment rather than by organizational regulation or extrinsic motivation.
1. Introduction
Technology leakage is one of the major problems that severely hamper a company’s competitiveness in high-technology industries. A technology leak can result in a company losing its competitive advantage by exposing its core technology and confidential information to the outside world, which can lead to losses for the national economy. The recent surge in cross-border data and information flows has introduced new economic value and heightened the risk of technology breaches. Consequently, industrial technology outflow crimes are on the rise. Technology leaks also occur in various ways, including industrial espionage and cyberattacks (Kim 2021; McKinsey Global Institute 2016).
The Security Magazine (2024) report estimated the national loss from trade secret theft of industrial technology and other trade secrets to be 1–3% of gross domestic product. Other industrialized nations are also losing technology each year. The United States is estimated to lose approximately USD 250 billion annually due to technology leaks. Furthermore, Germany is estimated to experience 50,000 annual instances of unemployment resulting from industrial espionage. A total of 99 cases of industrial technology leakage were identified in South Korea between 2017 and February 2022. The estimated damage amount is approximately KRW 22 trillion. For instance, a total of 139 instances of industrial technology leaks were recorded in 2023. The breakdown of these leaks by technology was as follows: 15.1% in the machinery sector, 10% in semiconductors, and 7.9% in display technology (National Police Agency 2023).
In the case of industrial technology outflows, the majority of these technologies are not only high-tech in nature and currently occupying a leading position in the global market, they are also the core technologies of new industries that will determine future growth, such as bio-health and artificial intelligence. Consequently, leakage has a profound impact on the national economy. In response, countries are mobilizing their national capabilities to address this issue, ultimately supplementing related systems and strengthening punishment provisions (Kim and Shin 2010; Baele et al. 2018).
Industrial technology leaks from these high-tech companies often occur through insiders, particularly those occupying key technical roles who are directly engaged in research and development (Jung 2024). Given the high percentage of such leaks despite various efforts to protect industrial technology, management measures are of particular importance. Ultimately, strengthening industrial security awareness and systematic leakage prevention efforts among the organization’s employees is imperative to prevent technology leakage.
In light of the existing research on this subject, Ahmad et al. (2014) argued that regularly publicizing a company’s security policy to all employees and establishing an effective training system are necessary. Additionally, Yılmaz and Gönen (2018) observed that even the most minor security measures undertaken by individuals can assist in the prevention of direct industrial technology leaks. Consequently, cultivating a culture of security awareness throughout the organization is important. Ha and Lee (2024) emphasized the necessity of reforming the legal system for industrial protection, identified significant issues in industrial technology law and policy, and suggested potential measures for improvement. Chun and Lee (2014) analyzed cases of industrial technology leaks to identify common patterns and leak pathways and to provide policy implications. Adler and Kahan (2013) and Jung (2024) emphasized the necessity of establishing a consistent response system to protect industrial technology and the urgency of establishing a legal framework. Carrière et al. (1998) and Lee (2020) analyzed the impact of industrial security management activities on companies’ security performance, and Zhu et al. (2016) proposed the introduction of a technology value evaluation system.
As such, most existing research mainly comprises theoretical or legal studies on the importance of technology leakage prevention and management studies on employee compliance with security policies and corporate security performance. Clearly, macro-level policy and legislative considerations are crucial in effectively responding to serious criminal behavior such as intentionally leaking industrial technology (Hwang and Lee 2016; Hwang and Hu 2018; Sung 2024). Nevertheless, these studies are constrained in their capacity to develop practical technology leak prevention strategies and identify root causes. Practical measures must be developed based on in-depth research and empirical validation of the factors influencing industrial technology leaks. This should include a thorough examination of the security awareness, self-control, and organizational attachment of individual members of the organization who are subject to such leaks (Hoecht and Trott 2006; Lee 2020).
Therefore, this study aims to define the intrinsic and extrinsic motivational factors that influence the prevention of leakage by high-tech company employees. This study also investigates how these factors affect the employees’ intention to prevent leakage. Moreover, based on the theory of planned behavior (TPB), this study analyzes the relationship between “attitude toward behavior”, “subjective norm”, and “perceived behavioral control”, which in turn influences the behavioral intention to prevent leakage. Ultimately, this study elucidates the factors that influence the prevention behavior of organizational employees and suggests specific implications for how companies should manage their employees to prevent such leakage.
2. Literature Review and Hypothesis Development
2.1. Motivation and Theory of Planned Behavior
Motivation is the most powerful psychological factor influencing all aspects of human life and behavior (Conner and Armitage 1998). Motivation is the driving force behind behavior, influencing its direction and persistence (Atkinson 1964). In other words, motivation has the ability to provide the energy and direction for behavior. Consequently, motivation is goal-directed behavior, which encompasses not only behavioral aspects but also emotional states (Youn 1999; Hagger and Chatzisarantis 2009a). Motivation is the process of directing and sustaining an organization’s members to voluntarily engage in goal-directed behavior (Landy and Becker 1987; Manning 2011). In other words, it can be understood as the process of guiding members in a certain direction to achieve organizational goals (Robbins and Judge 2011). These motivation theories include intrinsic and extrinsic motivation and the theories of attribution, expected value, self-determination, self-efficacy, achievement goals, and future time perspective, as shown in Table 1.

Table 1.
Motivation theories.
The most important theories of personal motivation are the intrinsic and extrinsic motivation theories. This is because the primary motivating factors for human behavior derive from two distinct sources: intrinsic motivation, which values intrinsic rewards and self-purposive experiences, and extrinsic motivation, which is activated when extrinsic rewards are accessible (Deci 1971; Hagger and Chatzisarantis 2007). In intrinsic/extrinsic motivation theory, motivation is divided into intrinsic and extrinsic. Intrinsic motivation refers to those aspects of an individual that are driven from within, such as excitement, interest, engagement, seeking adventure and novelty, the pursuit of excellence, the desire for knowledge, the desire to improve, and goal orientation (Fair and Silvestri 1992; Vansteenkiste and Lens 2006). Extrinsic motivation is defined as a form of motivation that is driven by external rewards (Vansteenkiste and Lens 2006), such as external attention, praise, recognition, feedback, and grades.
These intrinsic and extrinsic motivators affect employees’ performance, organizational effectiveness, and employees’ creative behavior on the organizational side of the business. Regarding major previous studies, Pandya (2024) analyzed the impact of intrinsic and extrinsic motivation on organizational performance. A balanced integration of intrinsic and extrinsic motivational strategies has been proven to result in enhanced job satisfaction, higher productivity, and better organizational performance. Sahyunu et al. (2023) examined the impact of intrinsic and extrinsic motivation on employee performance, and their findings indicated that both have a significant impact. It was demonstrated that effectively harnessing both types of motivation can help achieve the highest levels of organizational performance. Delaney and Royal (2017) proposed a framework for enhancing strategies for motivating employees to increase engagement and optimize performance. In their employee engagement strategy, they emphasized the importance of intrinsic and extrinsic motivation in employee engagement.
These intrinsic and extrinsic motivational factors have been linked and studied as influences that explain behavioral intention in the TPB. The Theory of Reasoned Action (TRA) (Ajzen and Fishbein 1980), which explains how an individual’s attitudes and the expectations of those around them influence their behavioral intentions and actual behavior, states that humans generally behave rationally; however, this is limited by the assumption that individuals act solely of their own volition, so they may behave differently in real-world situations. To overcome these constraints, Ajzen (1991) proposed the TPB. In consideration of these human behavioral intentions, Ajzen (1991) suggested that attitudes toward behavior, subjective norms, and perceived behavioral control influence participation intentions and behavior.
First, attitudes toward participation are based on the anticipated outcomes of engaging in a specific action and the value judgments that individuals hold about those outcomes. This is the degree to which one rates the behavior positively or negatively overall. In other words, attitudes toward engagement represent a consistent set of learned and formed tendencies of response or behavior toward a particular object or situation (Fishbein and Ajzen 1975). Subjective norms are defined as an individual’s perception and acceptance of the views of others regarding one’s behavior (Fishbein 1963). Ajzen (1985) explains that subjective norms represent an individual’s perception of whether to perform a particular behavior in relation to those around them who are important to the individual and within their in-group. The concept of perceived behavioral control is an important concept in the TPB and refers to an individual’s perception of how easy or difficult it is for them to perform a particular behavior. According to Ajzen (1991), this concept refers to the extent to which individuals believe that they can control certain behaviors through their own will and ability.
2.2. Motivation and TPB in Relation to Technology Protection
In reviewing the existing literature based on motivation theory in industrial technology and information security, Deci (1971) argued that attitude toward behavior, subjective norms, and perceived behavioral control variables positively influence the intention to prevent leakage. Deci et al. (1999) found that monetary rewards are not always the most effective means of aligning human behavior and that extrinsic motivators can sometimes lead to poor task performance by lowering intrinsic motivation. Safa and Solms (2016) also emphasized the importance of internal and external motivational factors that influence information security policy compliance.
Intrinsic motivation refers to a state in which an individual is motivated by internal rewards, such as interest, pleasure, or a challenge in the behavior itself (Deci and Ryan 1985a). Individuals who are internally motivated to take action are more likely to persist and perform better than those who are externally motivated (Deci and Ryan 2000; Hagger and Chatzisarantis 2009b). These intrinsic motivations influence industrial technology leakage and security behavior.
In response, Workman and Gathegi (2007) argued that ethical factors within intrinsic motivations for security behavior have a significant effect on reinforcing security behavior. Kranz and Haeussinger (2014) demonstrated that compliance with industrial security policies is less about relying on extrinsic motivators, such as norms and sanctions, and more reliant on policies that foster intrinsic motivators, such as a sense of ethics and the communication environment. In a study on the influence of security perceptions on the relationship between intrinsic and extrinsic motivation and security behaviors in organizations, Lee (2020) found that extrinsic rewards alone are insufficient to induce sustainable security activities, and that higher intrinsic motivation increases security behaviors.
As evidenced by previous research, intrinsic motivation in the domain of industrial technology leakage also influences attitudes toward behavior, subjective norms, and perceived behavioral control. In light of these findings, this study formulated the following hypotheses:
H1.
Intrinsic motivation to protect industrial technology has a positive effect on high-tech employees’ attitudes toward their behavior.
H2.
Intrinsic motivation to protect industrial technology has a positive effect on subjective norms among high-tech employees.
H3.
Intrinsic motivation to protect industrial technology has a positive effect on perceived behavioral control among high-tech employees.
Extrinsic motivation refers to the state in which an individual is motivated to perform a particular behavior due to external factors such as rewards, recognition, or the attainment of goals (Deci and Ryan 1985a; Singh 2016). Goel and Rashmi (2023) found that extrinsic motivators such as penalty severity, security breach detection, and normative beliefs positively influence compliance with information security policies. As Fischer et al. (2019) and Padayachee (2012) posit, extrinsic motivational factors that influence security behavior will also influence the factors of planned behavior. In light of these findings, the following hypotheses were formulated:
H4.
Extrinsic motivation to protect industrial technology has a positive effect on attitudes toward the behavior among high-tech employees.
H5.
Extrinsic motivation to protect industrial technology has a positive effect on the subjective norms of high-tech employees.
H6.
Extrinsic motivation to protect industrial technology has a positive effect on perceived behavioral control among high-tech employees.
2.3. Behavioral Intention to Protect Industrial Techniques
Behavioral intention is the probability that an individual will engage in a specific behavior based on their perception of the situation. Fishbein and Ajzen (1975) argued that behavioral intention is an important variable in behavioral theory and refers to the subjective state of mind before a belief is formed, which can influence direct action and lead to the execution of a specific behavior. Ajzen (1991) explained that behavioral intention is a person’s willingness or the extent of effort that they are willing to invest in performing a specific behavior. Thus, a clear belief and commitment to a particular behavior can influence future behavioral decisions (Hungerford and Volk 1990). According to Ajzen and Fishbein (1980), behavioral intentions play an important role in predicting and understanding the emergence of various social behaviors. They suggest that the match between behavioral intent and actual behavior is not always perfect, but that intent to engage can be used as a predictor of behavior when actual behavior is not directly observable.
According to the TPB, individuals with strong intentions are more likely to make an effort to achieve their goals that is aligned with their behaviors (Norman et al. 2005). Consequently, the stronger an individual’s intention to carry out a behavioral goal or plan, the more accurately their behavior can be predicted (Ajzen and Driver 1992). The TPB presents behavioral intentions as a direct determinant of behavior. This is based on the premise that intentions are shaped by an individual’s attitudes toward the behavior in question, subjective norms, and perceived behavioral control (Ajzen 1988, 1991). Ajzen (1988) referred to perceived behavioral control as being similar to self-efficacy. Individuals who hold positive attitudes and subjective norms regarding the performance of a behavior perceive that they are in control of the behavior when they have the opportunity and resources to perform it. This perception is self-efficacy, which pursues the same line of thought as behavioral intention in that it influences positive behavior.
In the literature on organizational behavior, studies related to behavioral intention and the TPB include those conducted by Huang (2023), in which the effects of career stagnation on organizational commitment and turnover intention were examined through attitudes, subjective norms, and perceived behavioral control. Kim and Mou (2020) analyzed the factors affecting information security policy compliance behavior based on the TPB. Based on the TPB model, Otchengco and Akiate (2021) found that attitude, subjective norms, and perceived behavioral control positively influence innovation behavior intention in a manufacturing company.
A review of the existing literature on technology leakage and the information security behavior of organizational members by Sommestad and Hallberg (2013) suggests that the TPB is a valid framework for predicting and explaining information security policy compliance and violation behavior. They found that the key components of attitude, subjective norms, and perceived behavioral control have a significant impact on intentions to comply with information security policies. Ifinedo (2012) suggested that subjective norms, perceived behavioral control, and attitudes in the TPB influence intention in information security behavior. In light of these findings, this study formulated the following hypotheses:
H7.
High-tech firm employees’ attitudes toward acting to protect industrial technology have a positive effect on their behavioral intentions.
H8.
The subjective norms of high-tech employees regarding the protection of industrial technology have a positive effect on their behavioral intentions.
H9.
The perceived behavioral control over industrial technology protection has a positive effect on high-tech employees’ behavioral intentions.
3. Research Methods
3.1. Research Model
This study empirically analyzes the influence of employees’ motivation on industrial technology protection behavior in high-tech companies. The independent variables are intrinsic and extrinsic motivation, and the dependent variable is behavioral intention to prevent industrial technology leakage. The mediating variables are attitudes toward the behavior, subjective norms, and perceived behavioral control. Considering the path analysis based on the structural equation model, the research model was designed as illustrated in Figure 1.
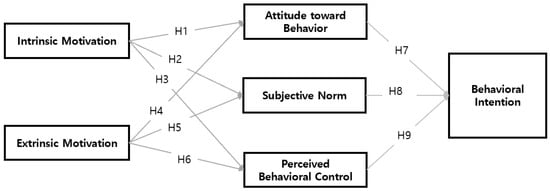
Figure 1.
Research model.
3.2. Measurement Variable and Data Collection
A survey was conducted to collect data for the models. The survey was developed by adapting questions from previous studies (see Table 2). Subsequently, the manipulated variables of the survey components that would comprise the survey were defined. The term “motivational influencing factors on industrial technology protection behavior” refers to the factors that affect the motivation of employees in high-tech enterprises, which are expressed by the intention and effectiveness of such behavior. This refers to the factors that individuals should consider in order to enhance their industrial technology protection.

Table 2.
Variable definitions and measurement items.
This study examined the impact of employee motivation on industrial technology protection behavior in high-tech companies based on the TPB, a model that extends the TRA, a psychological theory used to understand and predict human behavioral intentions and actual behavior developed by Ajzen (1991), and categorized them into attitude toward behavior, subjective norms, and perceived behavioral control.
“The attitude toward behavior” refers to the positive judgment an individual makes regarding the implementation of industrial technology protection measures. It refers to an individual’s positive or negative judgment about performing a particular behavior. Accordingly, attitudes toward behavior were defined as an influencing factor for effective industrial technology protection behavior. “Subjective norms” refers to the degree to which an individual’s expectation or recognition is influenced by a governing group to protect or not protect an industrial technology. This study identifies subjective norms as a significant influencing factor for effective industrial technology protection behavior.
“Perceived behavioral control” refers to the degree of difficulty or ease an individual perceives in protecting industrial technology and performing a particular behavior. Accordingly, the variable of perceived behavioral control was defined as a key factor influencing the effectiveness of industrial technology protection behavior. A closer examination of the relationship between behavioral intention and the three factors reveals that the more favorable attitudes there are toward the behavior, the more subjective norms that respect the behavior, and the easier performing the behavior is perceived to be, the stronger the individual’s intention to perform the behavior. In other words, the above three factors influence behavioral intention, which in turn leads to actual behavior.
Self-determination theory (motivation theory) divides behavior into intrinsic and extrinsic motivations. Intrinsic motivation is motivation that stems from personal satisfaction, such as personal pleasure, interest, and joy. Extrinsic motivation, on the other hand, is motivated by outcomes or rewards, such as monetary rewards, social approval, increased self-esteem, or the avoidance of penalties.
“Intrinsic motivation” refers to motivation that is perceived to be rewarding in and of itself, without reference to external rewards. In light of these considerations, the variable of intrinsic motivation was identified as a key influencing factor in shaping attitudes toward behavior, subjective norms, and perceived behavioral control with regard to effective industrial technology protection behavior. This was in alignment with the TPB within the context of a high-tech, industry-based environment.
“Extrinsic motivation” refers to the motivation to obtain a reward for industrial technology protection behavior, such as money, incentives, and prestige. In light of the aforementioned considerations, the variables of extrinsic motivation were defined as factors that influence effective industrial technology protection behavior. This was based on the TPB, which posits that an individual’s attitude toward a behavior, subjective norms, and perceived behavioral control are key determinants of that behavior. The theory was applied in a high-tech, industry-based environment. The dependent variable, “behavioral intention to protect industrial technology leakage”, refers to a person’s intention to voluntarily protect industrial technology or how much effort they are willing to put into it.
These variables were defined as the questions in the questionnaire, which consisted of 21 questions in total. However, the factor analysis resulted in the rejection of one intrinsic motivation factor, one extrinsic motivation factor, and one perceived behavioral control factor. For data analysis, SPSS 26.0 was employed to analyze the demographic characteristics and descriptive statistics, and to conduct exploratory factor analysis. For the path analysis of our hypotheses, AMOS 24.0 was used for confirmatory factor analysis (CFA) based on the structural equation model, model validation, and path analysis. A final CFA was also performed using AMOS.
3.3. Demographic Information from the Data
This study used an online survey and the random sample method of office workers in high-tech industries. The data for this survey were collected between 29 April and 6 May 2024. The survey subjects were members of high-tech companies in South Korea, and companies composed of large companies and SMEs (small and medium-sized companies). Dang et al. (2018) argued that the size of a company can be classified based on its total assets, total sales, and market capitalization, and as per the National Statistical Office in South Korea (2024), large companies mean total assets of 10 trillion or more based on corporate total assets. Accordingly, this study conducted a random survey of a total of 48 companies with total assets of KRW 10 trillion or more and other SMEs. A total of 220 surveys were collected and analyzed, with 8 being excluded on the grounds of dishonesty. This resulted in 200 valid samples (see Table 3).

Table 3.
Demographic information of survey participants.
4. Results
4.1. Reliability and Validity Results
A descriptive statistical analysis was conducted to determine the descriptive statistics of the variables (see Table 4). First, the mean of intrinsic motivation is 3.90, with a standard deviation of 0.575. The mean value for extrinsic motivation is 3.06, with a standard deviation of 0.793. For attitudes, the mean is 4.22, with a standard deviation of 0.596. The mean value for norms is 3.82, with a standard deviation of 0.710. Awareness has a mean of 3.52 and a standard deviation of 0.788. For behavioral intentions, the mean is 3.87, with a standard deviation of 0.645. A normality test was conducted on both the univariate and multivariate forms. Skewness and kurtosis were employed to ascertain the normality of the data. The skewness statistic indicates the degree of asymmetry in a data set. In contrast to a normal distribution, which is symmetrical around the mean, a positive skewness indicates that the data are clustered to the left of the mean, while a negative skewness indicates that the data are clustered to the right, thus resulting in an asymmetrical distribution. A variable is considered to be normally distributed if the skewness does not exceed an absolute value of 3 and the kurtosis does not exceed that of 8 (Kline 2005). A normality check of the responses indicated that the assumption of univariate normality was not invalidated by skewness and kurtosis.

Table 4.
Descriptive statistical analysis results.
As illustrated in Table 5, factor rotation—Varimax rotation—was conducted using the orthogonal rotation method for exploratory factor analysis, and the Kaiser–Meyer–Olkin (KMO) test and Bartlett’s Test of Sphericity were performed in unison. The KMO Measure of Sampling Adequacy demonstrated an adequate level of suitability at 0.735, and Bartlett’s Test of Sphericity exhibited a value below 0.05, thereby confirming the appropriateness of employing factor analysis. The factor loadings were good, ranging from 0.624 to 0.923, and all above 0.6, and the construct validity (CV) was significant, ranging from 0.700 to 0.949. The average variance extracted (AVE) values ranged from 0.534 to 0.767, and Cronbach’s α values ranged from 0.650 to 0.896. These results indicate that the convergent validity of the instrument is satisfactory.

Table 5.
Results of reliability and convergent validity test.
The goodness-of-fit analysis of the structural equation model of measurement revealed a χ2 (df) of 234.019. The Comparative Fit Index (CFI) value was 0.928, and the Tucker–Lewis Index (TLI) value was 0.906, both of which were significant at levels above 0.9. The Root Mean Squared Error of Approximation (RMSEA) value of 0.079 and the Standardized Root Mean Square Residual (SRMR) value of 0.047, both of which are significant below 0.1, indicate that the measurement model fit the constructs statistically significantly (see Table 6).

Table 6.
Goodness-of-fit of confirmatory factor analysis.
Pearson correlation analysis was employed to ascertain the degree of correlation between the variables. The statistical analysis indicates that all factors are significantly correlated, as demonstrated in Table 7. To evaluate discriminant validity, the correlation coefficient squared was also calculated for each variable. The analysis indicates that the value does not exceed the AVE.

Table 7.
Correlation matrix and discriminant validity.
4.2. Analysis Results of Structural Model
The goodness-of-fit of the structural model was analyzed (see Table 8, Figure 2), and the resulting χ2 (df) value was 149.764, with a corresponding χ2/degrees of freedom value of 1.498. The model demonstrates satisfactory performance, with a Goodness-of-Fit Index (GFI) of 0.923 and a Normal Fit Index (NFI) of 0.923. The Root Mean Square Residual (RMR) is 0.027, the Adjusted Goodness-of-Fit Index (AGFI) is 0.882, and the RMSEA is 0.050, indicating that the model’s goodness-of-fit is significant. The CFI, which indicates the explanatory power of the model without being affected by the sample, is 0.972, and the TLI, which determines the explanatory power of the structural model, is 0.962. These values indicate that the basic model is a good fit.

Table 8.
The analysis results for the hypotheses.
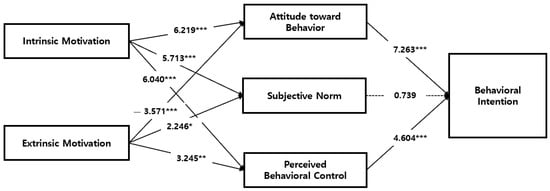
Figure 2.
Research result model (Note: * p < 0.05, ** p < 0.01, *** p < 0.001).
Hypothesis testing was conducted through path analysis of the structural equation model, which resulted in the rejection of one of the nine hypotheses. Among the behavioral planning theories, subjective norms (0.739) had no effect on behavioral intention; thus, the hypothesis was rejected. On the other hand, intrinsic motivation had a positive effect on attitude toward the behavior (6.219, p < 0.001), subjective norms (5.713, p < 0.001), and perceived behavioral control (6.040, p < 0.001). Extrinsic motivation had a negative effect on attitude toward the behavior (−3.571), a positive effect on the subjective norms (2.246, p < 0.05), and a positive effect on perceived behavioral control (3.245, p < 0.01). Attitude toward the behavior (7.263, p < 0.001) and perceived behavioral control (4.604, p < 0.001) had a positive effect on behavioral intention.
4.3. Mediated Effect
As presented in Table 9, to assess the significance of the indirect effect, a bootstrapping method was employed to derive the direct, indirect, and total effects. Our path analysis revealed that neither intrinsic nor extrinsic motivational factors served as mediators of subjective norms on behavioral intention. Ultimately, the findings indicate that intrinsic and extrinsic motivation in industrial security are more effective when they mediate attitudes toward behavior and perceived behavioral control for behavioral intentions to emerge. Furthermore, for extrinsic motivation, attitudes toward behavior have a negative effect, which influences the behavioral intention. Consequently, attitudes toward behavior based on extrinsic motivators do not necessarily have a positive effect on behavioral intention, in contrast to intrinsic motivators.

Table 9.
Results of mediated effects.
5. Discussions
This study employs the intrinsic and extrinsic motivation theories and the TPB with the aim of determining the intrinsic and extrinsic motivation factors for individual employees preventing industrial technology leakage in high-tech companies. It presents empirical results on the impact of motivational factors on technology leakage prevention behavioral intentions, which are mediated by attitudes toward the behavior, subjective norms, and perceived behavioral control factors. This analysis has led to the following key findings:
First, subjective norms do not influence the behavioral intention of high-tech employees to prevent industrial technology leakage. In this regard, Armitage and Conner (2001) have already highlighted that subjective norms exert a relatively weak influence compared to other factors in the TPB. In the TPB, the subjective norms are the concept of perceived social pressure from others to perform a behavior (Ajzen 1991; Rivis and Sheeran 2003). Consequently, behavioral intentions exhibit differences that are contingent upon the strength of the pressure, as it is not the individual’s subjective norms that influence behavior but rather the pressure of social norms perceived by others. This is because employees in high-tech companies have a high degree of professionalism and autonomy. Consequently, their behavior is driven by their own professional ethics and professional judgment rather than social pressure. A high level of awareness regarding information protection is an intrinsic motivator for individuals engaged in the process of advanced technological development. Furthermore, strong security policies and training programs also have a direct influence on individual behavior. Consequently, the analysis indicates that the behavioral intentions to prevent industrial technology leakage among advanced firms are more likely to be influenced by intrinsic than extrinsic motivational factors.
Second, the findings indicated that extrinsic motivation has a negative impact on attitudes toward behavior. As Deci and Ryan (2000) argued, when humans receive external rewards for an activity that they find enjoyable or satisfying, their interest and willingness to engage in the activity can diminish and even shift to a negative attitude. Moreover, Deci et al. (1999) posited that individuals tend to adopt a negative attitude when they perceive extrinsically motivated rewards as an externally controlling factor. Ultimately, the findings indicate that in terms of industrial technology leak protection behavior, employees in high-tech companies may perceive extrinsic motivators as a form of pressure or stress rather than as positive feedback or rewards. The working environment in high-tech companies is such that a high work intensity and competition create constant performance pressure, which in turn makes extrinsic motivation an additional burden. Furthermore, strict security protocols can create a heightened psychological burden and a fear of noncompliance. This study found that even when extrinsic motivation is stimulated for positive purposes, employees are more likely to perceive it as a source of stress rather than a positive influence. This supports the idea that an emphasis on extrinsic motivators may have a negative effect on fostering behavior to protect companies from industrial technology leaks.
Hence, these results reveal that intrinsic motivation has a stronger influence on employees’ behavioral intentions to prevent industrial technology leakage in high-tech companies than extrinsic motivation. Hagger and Chatzisarantis (2009a) and Kor and Mullan (2011) have argued that the TPB is strongly linked to self-determination, one of individuals’ most intrinsic motivators. The current study established that intrinsic motivational factors exert a stronger influence on attitudes toward behavior, subjective norms, and perceived behavioral control in preventing leaks among high-tech company employees.
6. Conclusions
6.1. Research Implications
The findings indicate three specific implications for high-tech companies with regard to the prevention of future high-tech security leaks. First, enhancing intrinsic motivation may have a positive impact on behavioral intentions to prevent technology leaks. Research on motivation theory suggests that proactive security behaviors can be pursued over the long term by improving an individual’s intrinsic motivation rather than their extrinsic motivation. Intrinsic motivation enhances an individual’s autonomy and self-determination to engage in activities that they naturally find enjoyable and satisfying. To achieve this, companies need to grant their employees autonomy and provide them with the opportunity to participate in decisions related to their work. This is a crucial factor in strengthening employees’ intrinsic motivation.
Furthermore, companies need to facilitate an understanding among their employees regarding the manner in which their work contributes to the company’s goals and vision. Such an approach fosters a sense of importance and value among employees, which in turn contributes to increased intrinsic motivation. Furthermore, providing employees with avenues for personal understanding, growth, and development through ongoing technical security education and training programs is crucial. This can make employees feel more positive about their jobs, which can ultimately have a positive impact on their intentions to engage in technology leak prevention behaviors.
Second, to achieve this, organizations should continue to emphasize the importance of security policies and technology leak prevention through strong internal communications. Furthermore, it is important to raise security awareness among employees through regular meetings, newsletters, training sessions, etc. Additionally, executives and team leaders need to demonstrate exemplary conduct and unwavering compliance with security policies. This creates a positive social pressure on employees, thereby facilitating the influence of subjective norms on behavioral intentions to prevent technical leaks.
Leaders’ demonstration of a willingness to assume responsibility for security compliance conveys a significant message to employees. This can contribute to strengthening security awareness throughout the organization. Moreover, cultivating an atmosphere where employees can influence each other through constructive feedback and recognition regarding security compliance is crucial. For instance, positive social norms can be reinforced by offering incentives to employees who comply well with security policies or by hosting sessions to share best practices.
Third, extrinsic motivation can negatively impact attitudes. Therefore, it is important to minimize it and direct it in a positive direction. Extrinsic motivation can evidently have a detrimental impact on individual autonomy, thereby leading to increased stress and performance pressure. Consequently, it is imperative for companies to enhance their extrinsic reward systems. Rather than merely offering financial incentives, implementing a reward system that fosters a sense of empowerment among employees would be more beneficial. The negative impact of extrinsic motivation can be mitigated by providing non-financial rewards for project completion, such as team-building activities, additional learning opportunities, or time off.
In addition, extrinsic motivation can increase stress and performance pressure, thus underscoring the importance of implementing an effective stress management program. Employers are recommended to provide employees with resources to help them manage stress effectively, such as job stress management workshops, counseling services, or flexible work hours. Additionally, by ensuring that rewards and feedback are fair and transparent, employees feel that their efforts are being properly valued, and extrinsic motivation has a smaller negative impact on their motivation. This can assist employees in maintaining a positive attitude toward their work, which in turn has a positive impact on their intentions to engage in technology breach prevention behaviors.
6.2. Limitations and Future Directions
The findings and implications of this study enhance our comprehension of the technology leakage prevention behavior of individuals in high-tech industries and identify more precise implications for the management of employees in companies to prevent industrial technology leakage. Nevertheless, this study has the following limitations:
First, the specific nature of the sample and the limitations of generalization are limitations. As this study was conducted in South Korean high-tech companies, limitations exist in terms of generalizing the results to other countries or industries. The economic, cultural, social, and legal environments of each country are different, which can result in variations in organizational culture regarding technology leaks. In addition, the perception and management of technology leaks vary depending on the size and type of organization. Research should take these differences into account. This study should be expanded to other countries and industries in the future to compare results.
Second, while this study focuses on intrinsic and extrinsic motivation as the main variables, it does not fully consider other important variables that may affect technology leakage prevention, including personal factors such as personal profit, financial incentives, and career factors such as job satisfaction, competition, and work pressure. This may be a limitation of the explanatory power of the findings. In the future, conducting qualitative research, such as interviews or case studies, would be beneficial to collect more variables to build a more in-depth research model and analyze the interaction of each variable. Further research is required.
Third, this study is constrained by its inability to provide insights into how intrinsic motivation, extrinsic motivation, behavioral attitudes, subjective norms, and perceived behavioral control vary over time. Given the potential for behavioral intentions to change over time in relation to the prevention of technology leakage, adopting a long-term perspective is crucial. Future research could analyze the long-term effects of intrinsic motivation, extrinsic motivation, behavioral attitudes, subjective norms, and perceived behavioral control by conducting a follow-up study to observe changes over time.
Author Contributions
Conceptualization, S.L.; methodology, S.L.; software, S.L.; validation, S.L. and B.K.; formal analysis, B.K.; investigation, S.L. and U.V.I.; resources, S.L. and U.V.I.; data curation, B.K.; writing—original draft preparation, S.L. and B.K.; writing—review and editing, U.V.I. and B.K.; visualization, B.K.; supervision, B.K. and U.V.I.; project administration, U.V.I. and B.K.; funding acquisition, S.L. and U.V.I. All authors have read and agreed to the published version of the manuscript.
Funding
This paper is written with support for research funding from aSSIST University.
Institutional Review Board Statement
Ethic Committee Name: The Research Ethics Committee of aSSIST University Approval Code: The Statistics Act No. 33, 34 Approval Date: 22 July 2024.
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
Data are not publicly available due to the privacy of respondents.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Adler, Barry E., and Marcel Kahan. 2013. The technology of creditor protection. University of Pennsylvania Law Review 161: 1773–814. [Google Scholar]
- Ahmad, Atif, Rachelle Bosua, and Rens Scheepers. 2014. Protecting organizational competitive advantage: A knowledge leakage perspective. Computers & Security 42: 27–39. [Google Scholar]
- Ajzen, Icek. 1985. From Intentions to Actions: A Theory of Planned Behavior. Berlin/Heidelberg: Springer. [Google Scholar]
- Ajzen, Icek. 1988. Attitudes, Personality, and Behavior. Chicago: Dorsey Press. [Google Scholar]
- Ajzen, Icek. 1991. The theory of planned behavior. Organizational Behavior and Human Decision Processes 50: 179–211. [Google Scholar] [CrossRef]
- Ajzen, Icek. 2006. Constructing a TpB Questionnaire: Conceptual and Methodological Considerations. Working Paper. Amherst: University of Massachusetts. Available online: http://www-unix.oit.umass.edu/~aizen/pdf/tpb.measurement.pdf (accessed on 15 June 2024).
- Ajzen, Icek, and Beverly Driver. 1992. Application of the theory of planned behavior to leisure choice. Journal of Leisure Research 24: 207–24. [Google Scholar] [CrossRef]
- Ajzen, Icek, and Martin Fishbein. 1980. Understanding Attitudes and Predicting Social Behavior. Englewood Cliffs: Prentice Hall. [Google Scholar]
- Armitage, Christopher, and Mark Conner. 2001. Efficacy of the theory of planned behavior: A meta-analytic review. British Journal of Social Psychology 40: 471–99. [Google Scholar] [CrossRef] [PubMed]
- Atkinson, John W. 1964. An Introduction to Motivation. Princeton: Van Nostrand. [Google Scholar]
- Baele, Stephane, David Lewis, Anke Hoeffler, Olivier Sterck, and Thibaut Slingeneyer. 2018. The ethics of security research: An ethics framework for contemporary security studies. International Studies Perspectives 19: 105–27. [Google Scholar] [CrossRef]
- Bandura, Albert. 1977. Social Learning Theory. Englewood Cliffs: Prentice-Hall. [Google Scholar]
- Carrière, Jean-Bernard, Jacqueline Dionne-Proulx, and Yves Beauchamp. 1998. Strategic management of new technologies and prevention of industrial accidents: Theoretical framework and empirical analyses. Human Factors and Ergonomics in Manufacturing & Service Industries 8: 1–22. [Google Scholar]
- Chun, Yongtae, and Julak Lee. 2014. An analysis on the industrial technology leakage cases in South Korea. British Journal of Business and Management Research 1: 103–14. [Google Scholar] [CrossRef]
- Conner, Mark, and Christopher Armitage. 1998. Extending the theory of planned behavior: A review and avenues for further research. Journal of Applied Social Psychology 28: 1429–64. [Google Scholar] [CrossRef]
- Dang, Chongyu, Zhichuan Frank Li, and Chen Yang. 2018. Measuring firm size in empirical corporate finance. Journal of Banking & Finance 86: 159–76. [Google Scholar]
- Deci, Edward L. 1971. Effects of externally mediated rewards on intrinsic motivation. Journal of Personality and Social Psychology 18: 105–11. [Google Scholar] [CrossRef]
- Deci, Edward L., and Richard M. Ryan. 1985a. Intrinsic Motivation and Self-Determination in Human Behavior. New York: Plenum. [Google Scholar]
- Deci, Edward L., and Richard M. Ryan. 1985b. The general causality orientations scale: Self-determination in personality. Journal of Research in Personality 19: 109–34. [Google Scholar] [CrossRef]
- Deci, Edward L., and Richard M. Ryan. 2000. The “What” and “Why” of goal pursuits: Human needs and the self-determination of behavior. Psychological Inquiry 11: 227–68. [Google Scholar] [CrossRef]
- Deci, Edward L., Richard Koestner, and Richard Ryan. 1999. A meta-analytic review of experiments examining the effects of extrinsic rewards on intrinsic motivation. Psychological Bulletin 125: 627–68. [Google Scholar] [CrossRef] [PubMed]
- Delaney, Mark, and Michael Royal. 2017. Breaking engagement apart: The role of intrinsic and extrinsic motivation in engagement strategies. Industrial and Organizational Psychology 10: 127–40. [Google Scholar] [CrossRef]
- Dweck, Carol S. 1986. Motivational processes affecting learning. American Psychologist 41: 1040–48. [Google Scholar] [CrossRef]
- Eccles, Jacquelynne, and Allan Wigfield. 2002. Motivational beliefs, values, and goals. Annual Review of Psychology 53: 109–32. [Google Scholar] [CrossRef] [PubMed]
- Fair, Ellen, and Leonard Silvestri. 1992. Effects of rewards, competition and outcome on intrinsic motivation. Journal of Instructional Psychology 19: 3–8. [Google Scholar]
- Fischer, Carmen, Charlotte Malycha, and Ernestine Schafmann. 2019. The influence of intrinsic motivation and synergistic extrinsic motivators on creativity and innovation. Frontiers in Psychology 10: 137. [Google Scholar] [CrossRef]
- Fishbein, Martin. 1963. An investigation of the relationships between beliefs about an object and the attitude toward that object. Human Relations 16: 233–39. [Google Scholar] [CrossRef]
- Fishbein, Martin, and Icek Ajzen. 1975. Belief, Attitude, Intention, and Behavior. An Introduction to Theory and Research. Reading: Addison-Wesley. [Google Scholar]
- Goel, Nidhi, and Kumari Rashmi. 2023. Impact of motivation on employee engagement: A literature review. Journal of Statistics and Management Systems 26: 537–47. [Google Scholar] [CrossRef]
- Guay, Frédéric, Robert J. Vallerand, and Céline Blanchard. 2000. On the assessment of situational intrinsic and extrinsic motivation: The Situational Motivation Scale (SIMS). Motivation and Emotion 24: 175–213. [Google Scholar] [CrossRef]
- Ha, Reeda, and Hwansoo Lee. 2024. Legal improvements to protect and manage industrial technology. Korean Security Journal 78: 29–52. [Google Scholar] [CrossRef]
- Hagger, Martin S., and Nikos L. D. Chatzisarantis. 2007. Self-Determination Theory and the Theory of Planned Behavior: An Integrative Approach toward a More Complete Model of Motivation. In Psychology of Motivation. Edited by Lois V. Brown. Hauppauge: Nova Science Publishers, pp. 83–98. [Google Scholar]
- Hagger, Martin S., and Nikos L. D. Chatzisarantis. 2009a. Integrating the theory of planned behaviour and self-determination theory in health behaviour: A meta-analysis. British Journal of Health Psychology 14: 275–302. [Google Scholar] [CrossRef] [PubMed]
- Hagger, Martin S., and Nikos L. D. Chatzisarantis. 2009b. Intrinsic Motivation and Self-Determination in Exercise and Sport. Champaign: Human Kinetics. [Google Scholar]
- Heider, Fritz. 1958. The Psychology of Interpersonal Relations. New York: Wiley. [Google Scholar]
- Hoecht, Andreas, and Paul Trott. 2006. Innovation risks of strategic outsourcing. Technovation 26: 672–81. [Google Scholar] [CrossRef]
- Huang, Yung-Chuan. 2023. Integrated concepts of the UTAUT and TPB in virtual reality behavioral intention. Journal of Retailing and Consumer Services 70: 103127. [Google Scholar] [CrossRef]
- Hungerford, Harold, and Trudi Volk. 1990. Changing learner behavior through environmental education. Journal of Environmental Education 21: 8–21. [Google Scholar] [CrossRef]
- Husman, Jenefer, and Willy Lens. 1999. The role of the future in student motivation. Educational Psychologist 34: 113–25. [Google Scholar] [CrossRef]
- Hwang, Hyundong, and Changmoo Lee. 2016. A study on the relationship between industrial technology leakage, self-control, and organizational attachment. Journal of Korean Security Guard Association 47: 119–38. [Google Scholar]
- Hwang, Inho, and Sungho Hu. 2018. A study on the influence of information security compliance intention of employee: Theory of planned behavior, Justice Theory, and Motivation Theory Applied. Digital Convergence Research 16: 225–36. [Google Scholar]
- Ifinedo, Princely. 2012. Understanding information systems security policy compliance: An integration of the theory of planned behavior and the protection motivation theory. Computers & Security 31: 83–95. [Google Scholar]
- Jung, Jeyong. 2024. Analysis of the US industrial technology leak response system and legislation. Crime Investigation Research 19: 233–57. [Google Scholar] [CrossRef]
- Kim, Jongki, and Jian Mou. 2020. Meta-analysis of information security policy compliance based on theory of planned behavior. Journal of Digital Convergence 18: 169–76. [Google Scholar]
- Kim, Seonwook. 2021. Legislative improvement plan for the prevention of national core technology leakage by industrial spy. Wonkwang Law Review 37: 33–53. [Google Scholar] [CrossRef]
- Kim, Soonseok, and Jaechul Shin. 2010. The plan for core personnel management to prevent industrial technology leakage. Journal of Korean Security Science Association 25: 109–30. [Google Scholar] [CrossRef]
- Kline, Rex. 2005. Principles and Practice of Structural Equation Modeling, 2nd ed. New York: The Guilford Press. [Google Scholar]
- Kor, Kenny, and Barbara Mullan. 2011. Sleep hygiene behaviours: An application of the theory of planned behavior and the investigation of perceived autonomy support, past behavior and response inhibition. Psychology & Health 26: 1208–24. [Google Scholar]
- Kranz, Johann, and Felix Haeussinger. 2014. Why Deterrence Is Not Enough: The Role of Endogenous Motivations on Employees’ Information Security Behavior. Paper presented at the IS Security and Privacy, Thirty Fifth International Conference on Information Systems, Auckland, New Zealand, December 14–17. [Google Scholar]
- Landy, Frank, and William Becker. 1987. Motivation theory reconsidered. Research in Organizational Behavior 9: 1–38. [Google Scholar]
- Lee, Ganghook. 2020. Study on the risk of industrial technology infringement by insiders: Focusing on R&D workers. Security Research 63: 129–52. [Google Scholar]
- Li, Chunxiao, Yandan Wu, and YingHwa Kee. 2016. Validation of the volunteer motivation scale and its relations with work climate and intention among Chinese volunteers. Asian Journal of Social Psychology 19: 124–33. [Google Scholar] [CrossRef]
- Manning, Mark. 2011. When we do what we see: The moderating role of social motivation on the relation between subjective norms and behavior in the theory of planned behavior. Basic and Applied Social Psychology 33: 351–64. [Google Scholar] [CrossRef]
- McKinsey Global Institute. 2016. Digital Globalization: The New Era of Global Flows. Chicago: McKinsey & Company. [Google Scholar]
- National Police Agency. 2023. 2023 Year Special Crackdown on Economic Security Crimes; Seoul: National Police Agency Press Release.
- National Statistical Office in South Korea. 2024. Company Size Classification. Available online: https://kostat.go.kr/board.es?mid=a10502010000&bid=12282&tag=&act=view&list_no=414440&ref_bid= (accessed on 8 August 2024).
- Nicholls, John. 1984. Achievement motivation: Conceptions of ability, subjective experience, task choice, and performance. Psychological Review 91: 328–46. [Google Scholar] [CrossRef]
- Norman, Paul, Tim Clark, and Glen Walker. 2005. The Theory of Planned Behavior, Descriptive Norms, and the Mediation Role of Group Identification. Journal of Applied Social Psychology 35: 1008–29. [Google Scholar] [CrossRef]
- Otchengco, Alberto Magtoto, Jr., and Yuri Walter Dulay Akiate. 2021. Entrepreneurial intentions on perceived behavioral control and personal attitude: Moderated by structural support. Asia Pacific Journal of Innovation and Entrepreneurship 15: 14–25. [Google Scholar] [CrossRef]
- Padayachee, Keshnee. 2012. Taxonomy of compliant information security behavior. Computers & Security 31: 673–80. [Google Scholar]
- Pandya, Jainisha. D. 2024. Intrinsic & extrinsic motivation & its impact on organizational performance at Rajkot city: A review. Journal of Management Research and Analysis 11: 46–53. [Google Scholar]
- Quintal, Vanessa, Julie Lee, and Geoffrey Soutar. 2010. Risk, uncertainty and the theory of planned behavior: A tourism example. Tourism Management 31: 797–805. [Google Scholar] [CrossRef]
- Rivis, Amanda, and Paschal Sheeran. 2003. Social influence and the theory of planned behaviour: Evidence for a direct relationship between prototypes and young people exercise behaviour. Psychology and Health 18: 567–83. [Google Scholar] [CrossRef]
- Robbins, Stephen, and Timothy Judge. 2011. Organizational Behavior. Boston: Prentice Hall. [Google Scholar]
- Ryan, Richard, and Edward L. Deci. 2000a. Intrinsic and extrinsic motivations: Classic definitions and new directions. Contemporary Educational Psychology 25: 54–67. [Google Scholar] [CrossRef] [PubMed]
- Ryan, Richard, and Edward L. Deci. 2000b. Self-determination theory and the facilitation of intrinsic motivation, social development, and well-being. American Psychologist 55: 68–78. [Google Scholar] [CrossRef]
- Safa, Nader Sohrabi, and Rossouw Von Solms. 2016. An information security knowledge sharing model in organizations. Computers in Human Behavior 57: 442–51. [Google Scholar] [CrossRef]
- Sahyunu, La Ode Abdul Manan, Ghalib Suprianto, Sri Wiyati Mahrani, and Wa Ode Safariati. 2023. The effect of intrinsic and extrinsic motivation on employee performance at digital engineering consultant. IOSR Journal of Business and Management 25: 50–55. [Google Scholar]
- Security Magazine. 2024. Insider-Driven Data Loss Incidents Cost an Average of $15 Million. Available online: https://www.securitymagazine.com/articles/100483-insider-driven-data-loss-incidents-cost-an-average-of-15-million (accessed on 15 June 2024).
- Singh, Rajesh. 2016. The impact of intrinsic and extrinsic motivators on employee engagement in information organizations. Journal of Education for Library and Information Science 57: 197–206. [Google Scholar]
- Sommestad, Teodor, and Johan Hallberg. 2013. A Review of the Theory of Planned Behaviour in the Context of Information Security Policy Compliance. In Security and Privacy Protection in Information Processing Systems. Edited by Lech J. Janczewski, Henry B. Wolfe and Sujeet Shenoi. IFIP Advances in Information and Communication Technology. Berlin: Springer, vol. 405, pp. 243–57. [Google Scholar] [CrossRef]
- Sung, Jinki. 2024. A study on the introduction of the technology valuation system to investigation on industrial technology leaks. Crime Investigation Research 19: 213–32. [Google Scholar] [CrossRef]
- Vansteenkiste, Maarten, and Willy Lens. 2006. Intrinsic versus extrinsic goal contents in self-determination theory: Another look at the quality of academic motivation. Educational Psychologist 41: 19–31. [Google Scholar] [CrossRef]
- Weiner, Bernard. 1985. An attributional theory of achievement motivation and emotion. Psychological Review 92: 548–73. [Google Scholar] [CrossRef] [PubMed]
- Workman, Michael, and John Gathegi. 2007. Punishment and ethics deterrents: A study of insider security contravention. Journal of the American Society for Information Science and Technology 58: 212–22. [Google Scholar] [CrossRef]
- Yılmaz, Ercan Nurcan, and Serkan Gönen. 2018. Attack detection/prevention system against cyber attack in industrial control systems. Computers & Security 77: 94–105. [Google Scholar]
- Youn, Yunsung. 1999. Teaching-learning theories and effective motivational strategies. Journal of Social Science 2: 209–35. [Google Scholar]
- Zhu, Sherry, Eric Guo, Max Lu, and Anna Yue. 2016. An Efficient Data Leakage Prevention Framework for Semiconductor Industry. Paper presented at the 2016 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Bali, Indonesia, December 4–7. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).