Vulnerability Assessment of Urban Rail Transit Network—A Case Study of Chongqing
Abstract
1. Introduction
2. Literature Review
3. Methodology
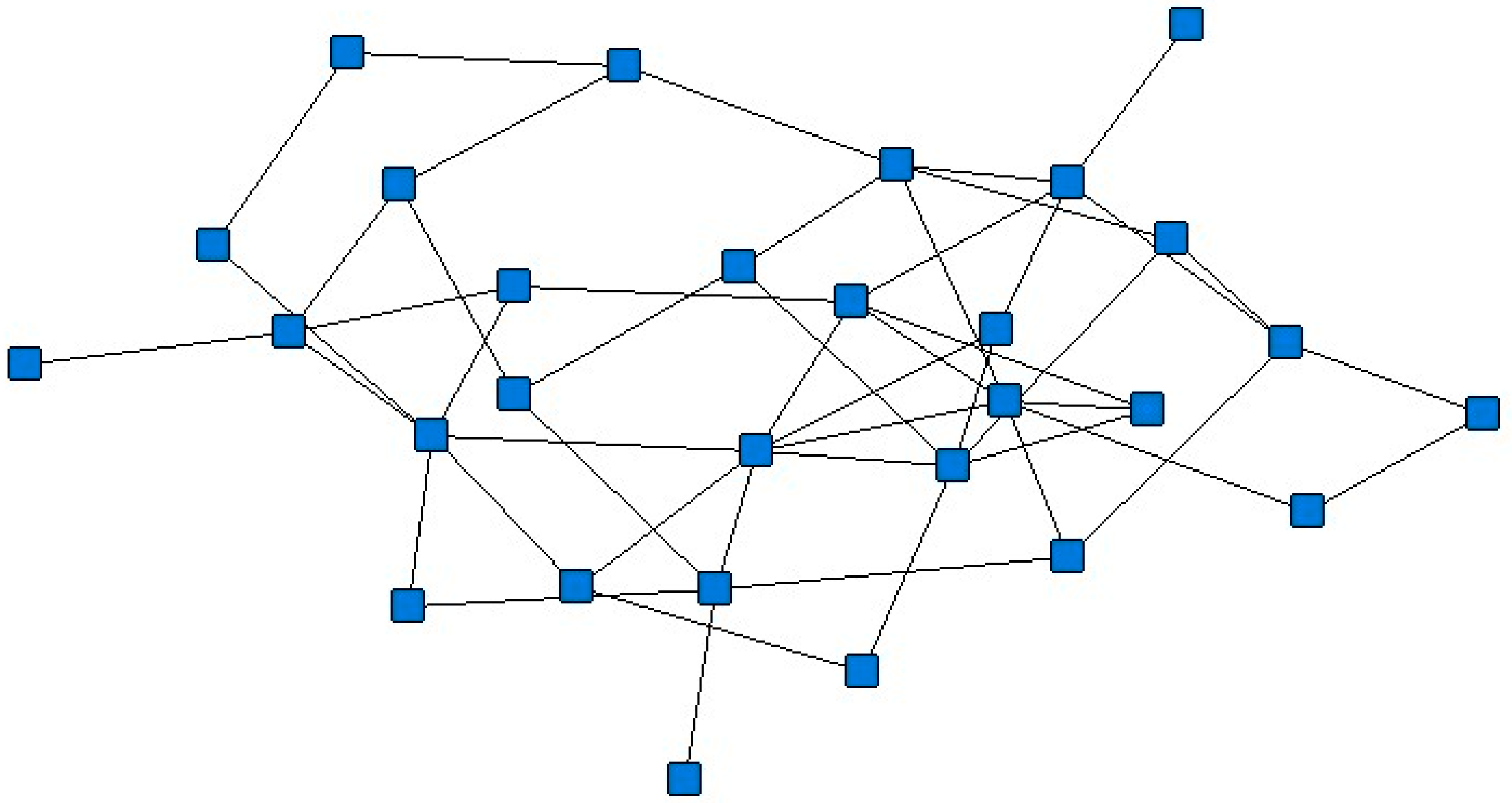
3.1. Selection of Topological Network Model Construction Method
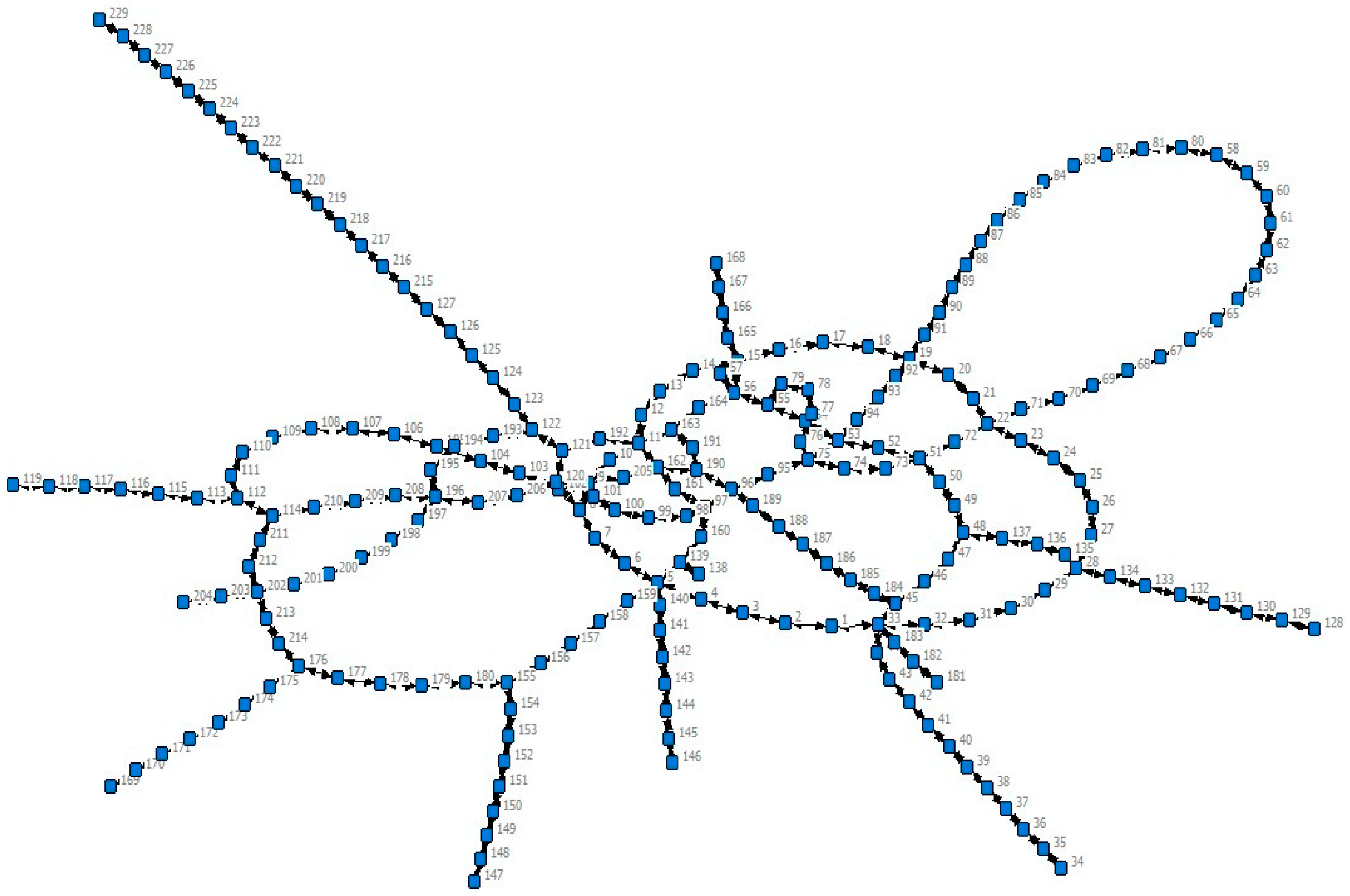
3.2. Construction of the Topological Structure Model of Rail Transit Network in Chongqing
3.2.1. Model Construction
- A.
- Since the distance between the track sites is relatively close, the site spacing is assumed to be equal. Moreover, the paper only studies the topological structure of the orbit network to find the stations with strong vulnerability, instead of considering the passenger flow intensity on each line. Therefore, the network is reduced to the unauthorized network;
- B.
- Since the urban rail transit can operate in both directions between any two stations, the urban rail transit network can be considered as an undirected network;
- C.
- Some of the same stations contained in the different lines are not in the same location due to unreasonable planning or excessive terrain height difference. The paper does not consider the hierarchical structure of the urban rail transit transfer station, and regards it as the same node;
- D.
- All stations and lines in the initial network of urban rail transit are not disturbed and can operate normally;
- E.
- Once a site or line is attacked, it is considered that the site is unable to play its original function.
3.2.2. Model Building
3.3. Analysis of Topological Structure Parameters of Rail Transit Network in Chongqing
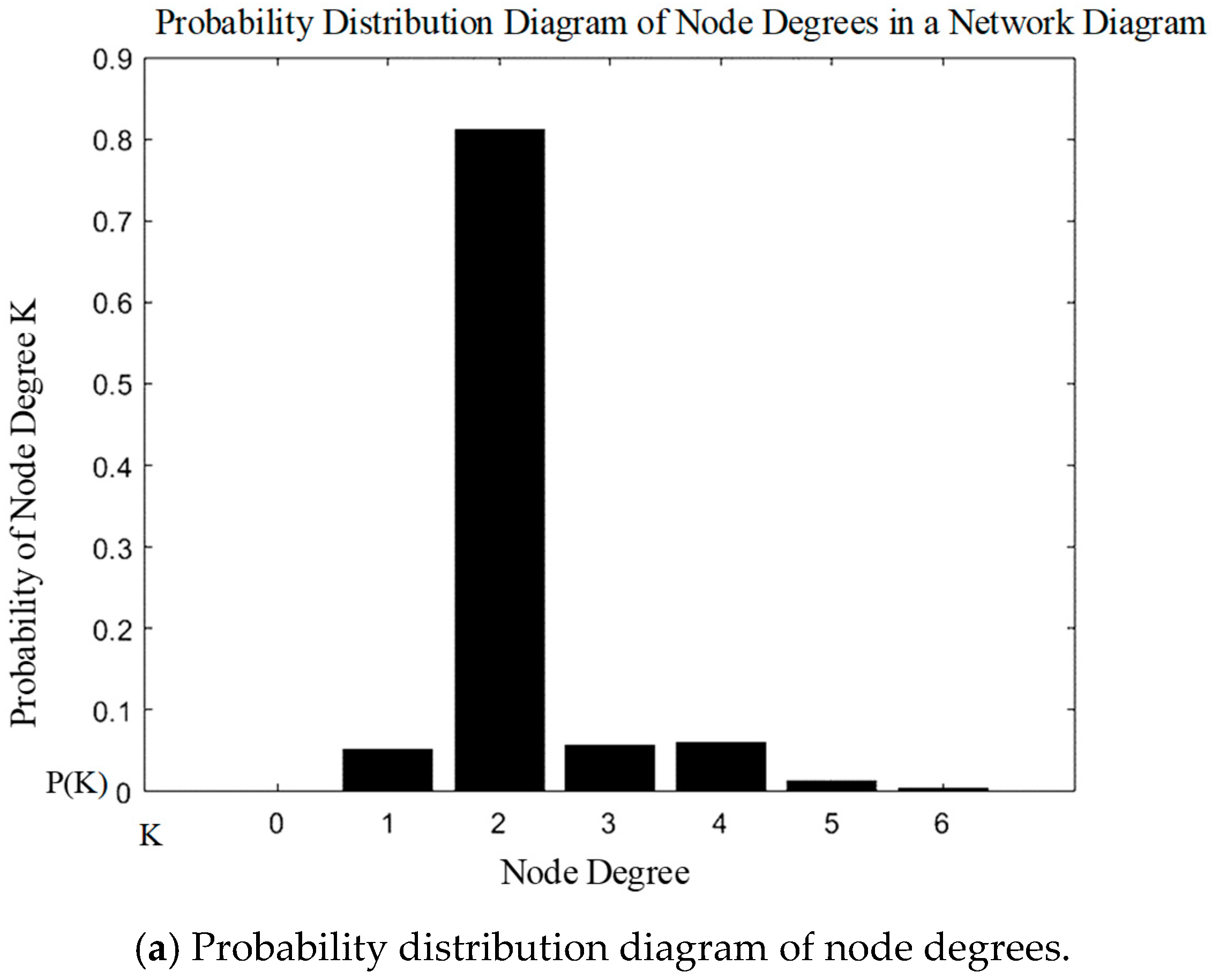
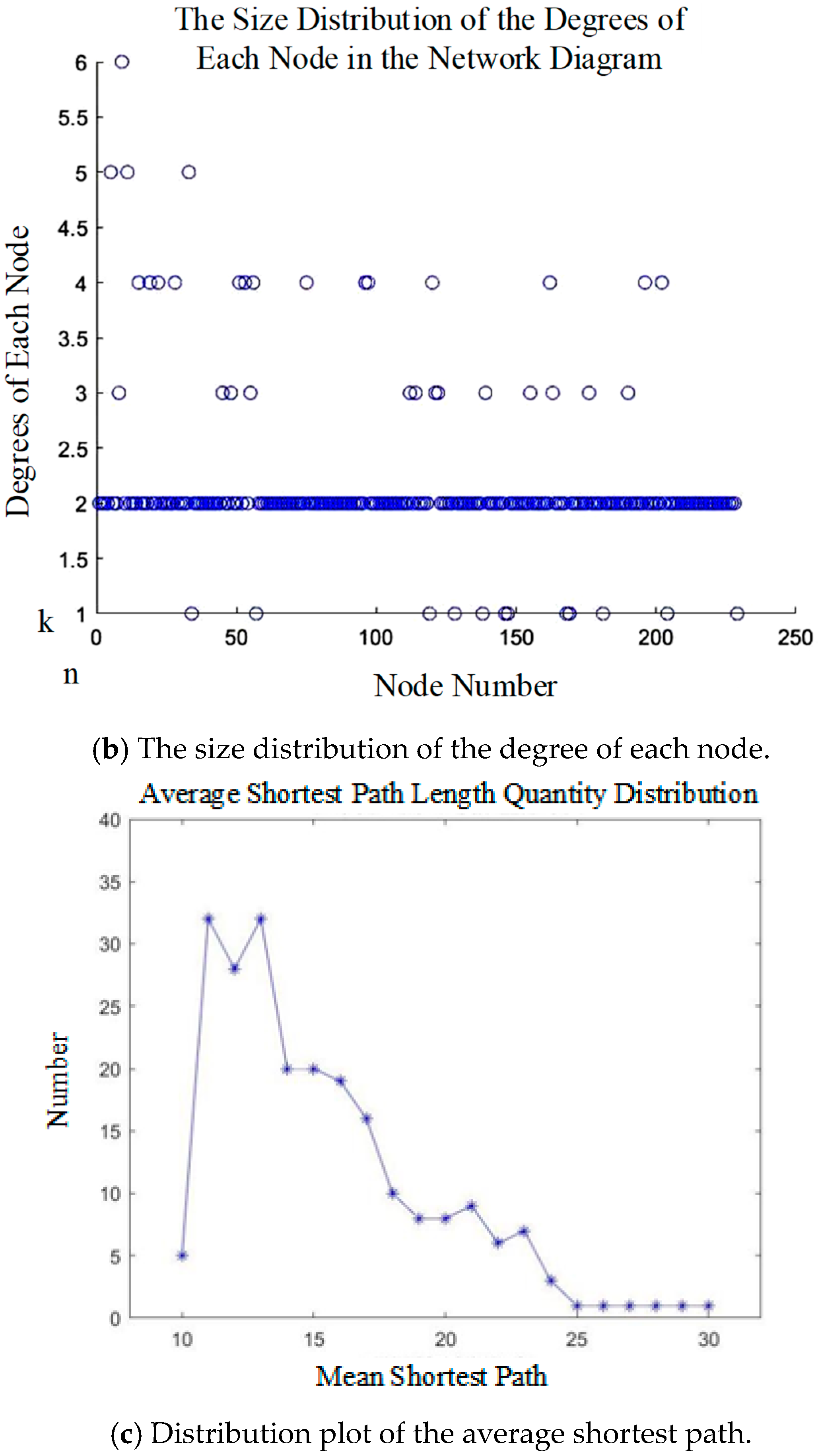
3.3.1. Node Degree
3.3.2. Aggregation Coefficient
3.3.3. Average Shortest Path Length
3.4. Rail Transit Network Vulnerability Assessment in Chongqing
3.4.1. Frailty Evaluation Index Selection and Model Construction
3.4.2. Attack Strategy
| Algorithm 1. Deliberate attack code. |
| f = find(A > 0); L = length(f); %The query vector length; [m, m] = size(A); % Get the number of rows and columns of the matrix; sum(sum(A))~ = 0 % For summing over the elements of each column of the matrix; [n, n] = size(A); k = sum(A); % Each column degree value; j = 1:n; C = [j, k]; % Matrix table of the degree values of each node; [order, lo] = sort(C(:,2),’descend’); % An ascending sort of the array returns the sorted array; p = lo(1); % Obtain the serial number corresponding to the node with the highest degree value; A(p,:) = []; % The node with the highest median value in the original matrix is all in the column of 0; A(:,p) = []; % The node with the highest median value in the original matrix has all rows of 0; L = length(A); % Returns the length of the largest array dimension in A; E = Network_efficiency(A); % Calculate the network efficiency after a deliberate attack. |
4. Results and Discussions
4.1. Changes in the Ratio of the Network Efficiency
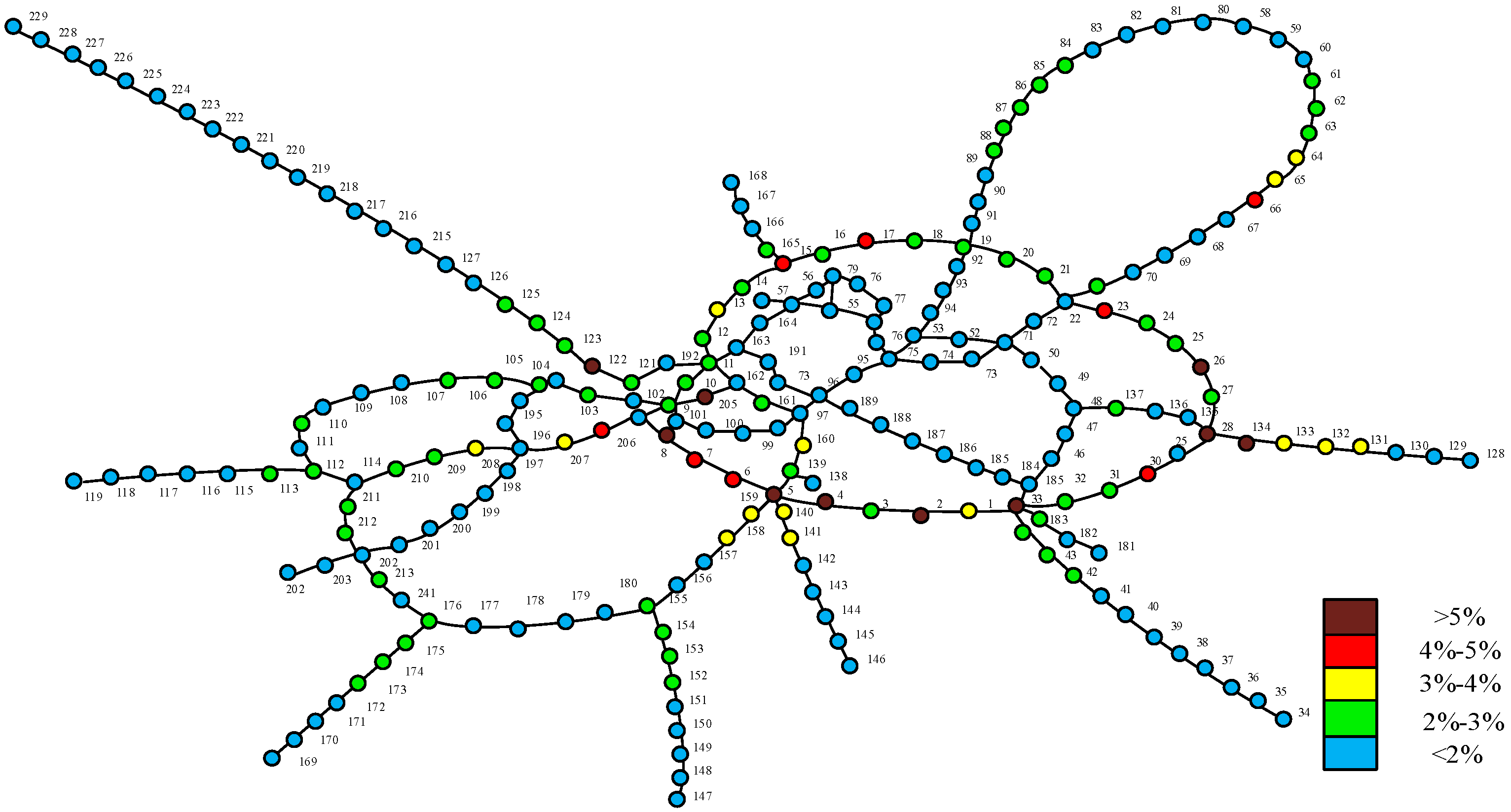
4.2. Site Vulnerability
4.3. Improvement Strategy
4.3.1. Planning Principles
4.3.2. Network Optimization
5. Conclusions
5.1. Theoretical Implications
5.2. Practical Implications
5.3. Limitations and Future Research
5.3.1. Limitations
5.3.2. Future Research
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Num. | Site | Num. | Site | Num. | Site | Num. | Site | Num. | Site |
|---|---|---|---|---|---|---|---|---|---|
| 1 | Chongqing University | 47 | Gaomiaocun | 93 | Gongmao | 139 | Dalongshan | 185 | Hongyancun |
| 2 | Yudaishan | 48 | Shiqiaopu | 94 | Tongyuanju | 140 | Xingfu Square | 186 | Fuhualu |
| 3 | Nanqiaosi | 49 | Xietaizi | 95 | Huaxinjie | 141 | Renhe | 187 | Hualongqiao |
| 4 | Sports Park | 50 | Shiyoulu | 96 | Guanyinqiao | 142 | Hemulu | 188 | Lijiaping |
| 5 | Ranjiaba | 51 | Daping | 97 | Hongqihegou | 143 | Chongguang | 189 | Mahuangliang |
| 6 | Dongbu Park | 52 | Eling | 98 | Jiazhoulu | 144 | Huxiajie | 190 | Liyuchi |
| 7 | Honghu East Road | 53 | Lianglukou | 99 | Zhengjiayuanzi | 145 | Danhe | 191 | Liujiatai |
| 8 | Min’an Ave. | 54 | Qixinggang | 100 | Tangjiayuanzi | 146 | The EXPO Garden Center | 192 | Gailanxi |
| 9 | Chongqing North Station South Square | 55 | Jiaochangkou | 101 | Shiziping | 147 | Beibei | 193 | Cruise Home Port |
| 10 | Yulu | 56 | Xiaoshizi | 102 | Longtousi | 148 | Southwest University | 194 | Hejialiang |
| 11 | Wulidian | 57 | Chaotianmen | 103 | Tongjiayuanzi | 149 | Zhuangyuanbei | 195 | Shipanhe |
| 12 | Danzishi | 58 | Yudong | 104 | Jinyu | 150 | Longfengxi | 196 | Shangwanlu |
| 13 | Tushan | 59 | Dajiang | 105 | Jintonglu | 151 | Xiangjiagang | 197 | Qinggangping |
| 14 | Renji | 60 | Baijusi | 106 | Yuanyang | 152 | Caijia | 198 | Baoshenghu |
| 15 | Shangxinjie | 61 | Liujiaba | 107 | The EXPO Garden | 153 | Caojiawan | 199 | Xingke Ave. |
| 16 | Shanghao | 62 | Jinjiawan | 108 | Cuiyun | 154 | Jinshansi | 200 | Chunhua Ave. |
| 17 | Haitangxi | 63 | Jianqiao | 109 | Changfulu | 155 | Lijia | 201 | Langui Ave. |
| 18 | Luojiaba | 64 | Tiantangbao | 110 | Huixing | 156 | Jiuquhe | 202 | Center Park East |
| 19 | Sigongli | 65 | Xinshancun | 111 | Shuanglong | 157 | Kangzhuang | 203 | Congyansi |
| 20 | Nanhu | 66 | Dadukou | 112 | Bijin | 158 | Dazhulin | 204 | Huashigou |
| 21 | Haixialu | 67 | Ping’an | 113 | Shuangfengqiao | 159 | Guangdianyuan | 205 | Longtousi Park |
| 22 | Xiejiawan | 68 | Mawangchang | 114 | Jiangbei Airport Terminal 2 | 160 | Huahuiyuan | 206 | Minxinjiayuan |
| 23 | Olympic Sports Center Station | 69 | Dayancun | 115 | Konggang Square | 161 | Huangnibang | 207 | Sanyawan |
| 24 | Chenjiaping | 70 | Zoo | 116 | Gaohubao | 162 | Hongtudi | 208 | Huanshan Park |
| 25 | Caiyunhu | 71 | Yangjiaping | 117 | Guanyuelu | 163 | Jiangbecheng | 209 | Changhe |
| 26 | Erlang | 72 | Yuanjiagang | 118 | Lianhua | 164 | Grand Theater | 210 | Jiangbei Airport Terminal 3 |
| 27 | Hualong | 73 | Fotuguan | 119 | Jurenba | 165 | Liujiaping | 211 | Yubei Square |
| 28 | Chongqing West Station | 74 | Liziba | 120 | Chongqing North Station North Square | 166 | Changshengqiao | 212 | Lushan |
| 29 | Shangqiao | 75 | Niujiaotuo | 121 | Toutang | 167 | Qiujiawan | 213 | Central Park |
| 30 | Fengmingshan | 76 | Zengjiayan | 122 | Baoshuigang | 168 | Chayuan | 214 | Central Park west |
| 31 | Chongqing Library | 77 | Daxigou | 123 | Cuntan | 169 | Shaheba | 215 | Tieshanping |
| 32 | Tianxingqiao | 78 | Huanghuayuan | 124 | Heizi | 170 | Hongyanping | 216 | Luqi |
| 33 | Shapingba | 79 | Linjiangmen | 125 | Gangcheng | 171 | Fuxing | 217 | Guoyuan Logistics Hub |
| 34 | Bishan | 80 | Jinzhu | 126 | Taipingchong | 172 | Siyuan | 218 | Yuzui |
| 35 | Jiandingpo | 81 | Yuhulu | 127 | Tangjiatuo | 173 | Liujiayuanzi | 219 | Yanping |
| 36 | Daxuecheng | 82 | Xuetangwan | 128 | Tiaodeng | 174 | Qingxihe | 220 | Shiheqing |
| 37 | Chenjiaqiao | 83 | Dashancun | 129 | Huayan Center | 175 | Wangjiazhuang | 221 | Fusheng |
| 38 | Weidianyuan | 84 | Huaxi | 130 | Jinjianlu | 176 | Yuelai | 222 | Sanbanxi |
| 39 | Laijiaqiao | 85 | Chalukou | 131 | Zhongliangshan | 177 | International Expo Center | 223 | Longyi Ave. |
| 40 | Shuangbei | 86 | Jiugongli | 132 | Banshan | 178 | Gaoyikou | 224 | Longxing |
| 41 | Shijingpo | 87 | Linlong | 133 | Huachenglu | 179 | Huangmaoping | 225 | Gaoshita |
| 42 | Ciqikou | 88 | Bagongli | 134 | Huayansi | 180 | Huanlegu | 226 | Pufu |
| 43 | Lieshimu | 89 | Chongqing jiaotong University | 135 | Fengxilu | 181 | Xinqiao | 227 | Tongzilin |
| 44 | Yanggongqiao | 90 | Liugongli | 136 | Bashan | 182 | Gaotanyan | 228 | Shichuan |
| 45 | Xiaolongkan | 91 | Chongqing Technology and Business University | 137 | Shixinlu | 183 | Tianlilu | 229 | Huangling |
| 46 | Majiayan | 92 | Nanping | 138 | Dashiba | 184 | Tuwan |
Appendix B
| Num. | Adjacency | Num. | Adjacency | Num. | Adjacency | Num. | Adjacency | Num. | Adjacency |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 1–2 | 51 | 31–32 | 101 | 74–75 | 151 | 121–122 | 201 | 173–174 |
| 2 | 1–33 | 52 | 32–33 | 102 | 75–76 | 152 | 121–192 | 202 | 174–175 |
| 3 | 2–3 | 53 | 33–44 | 103 | 75–95 | 153 | 122–123 | 203 | 175–176 |
| 4 | 3–4 | 54 | 33–45 | 104 | 76–77 | 154 | 122–193 | 204 | 176–177 |
| 5 | 4–5 | 55 | 33–183 | 105 | 77–78 | 155 | 123–124 | 205 | 176–214 |
| 6 | 5–6 | 56 | 34–35 | 106 | 78–79 | 156 | 124–125 | 206 | 177–178 |
| 7 | 5–139 | 57 | 35–36 | 107 | 80–81 | 157 | 125–126 | 207 | 178–179 |
| 8 | 5–140 | 58 | 36–37 | 108 | 81–82 | 158 | 126–127 | 208 | 179–180 |
| 9 | 5–159 | 59 | 37–38 | 109 | 82–83 | 159 | 127–215 | 209 | 181–182 |
| 10 | 6–7 | 60 | 38–39 | 110 | 83–84 | 160 | 128–129 | 210 | 182–183 |
| 11 | 7–8 | 61 | 39–40 | 111 | 84–85 | 161 | 129–130 | 211 | 184–185 |
| 12 | 8–9 | 62 | 40–41 | 112 | 85–86 | 162 | 130–131 | 212 | 185–186 |
| 13 | 8–120 | 63 | 41–42 | 113 | 86–87 | 163 | 131–132 | 213 | 186–187 |
| 14 | 9–10 | 64 | 42–43 | 114 | 87–88 | 164 | 132–133 | 214 | 187–188 |
| 15 | 9–101 | 65 | 43–44 | 115 | 88–89 | 165 | 133–134 | 215 | 188–189 |
| 16 | 9–102 | 66 | 45–46 | 116 | 89–90 | 166 | 135–136 | 216 | 190–191 |
| 17 | 9–120 | 67 | 45–184 | 117 | 90–91 | 167 | 136–137 | 217 | 193–194 |
| 18 | 9–205 | 68 | 46–47 | 118 | 92–93 | 168 | 138–139 | 218 | 194–195 |
| 19 | 10–11 | 69 | 47–48 | 119 | 93–94 | 169 | 139–160 | 219 | 195–196 |
| 20 | 11–12 | 70 | 48–49 | 120 | 95–96 | 170 | 140–141 | 220 | 196–197 |
| 21 | 11–162 | 71 | 48–137 | 121 | 96–97 | 171 | 141–142 | 221 | 196–207 |
| 22 | 11–163 | 72 | 49–50 | 122 | 96–189 | 172 | 142–143 | 222 | 196–208 |
| 23 | 11–192 | 73 | 50–51 | 123 | 96–190 | 173 | 143–144 | 223 | 197–198 |
| 24 | 12–13 | 74 | 51–52 | 124 | 97–98 | 174 | 144–145 | 224 | 198–199 |
| 25 | 13–14 | 75 | 51–72 | 125 | 97–160 | 175 | 145–146 | 225 | 199–200 |
| 26 | 14–15 | 76 | 51–73 | 126 | 97–161 | 176 | 147–148 | 226 | 200–201 |
| 27 | 15–16 | 77 | 52–53 | 127 | 98–99 | 177 | 148–149 | 227 | 201–202 |
| 28 | 15–56 | 78 | 53–54 | 128 | 99–100 | 178 | 149–150 | 228 | 202–203 |
| 29 | 15–165 | 79 | 53–75 | 129 | 100–101 | 179 | 150–151 | 229 | 202–212 |
| 30 | 16–17 | 80 | 53–94 | 130 | 102–103 | 180 | 151–152 | 230 | 202–213 |
| 31 | 17–18 | 81 | 54–55 | 131 | 103–104 | 181 | 152–153 | 231 | 203–204 |
| 32 | 18–19 | 82 | 55–56 | 132 | 104–105 | 182 | 153–154 | 232 | 206–207 |
| 33 | 19–20 | 83 | 55–79 | 133 | 105–106 | 183 | 154–155 | 233 | 208–209 |
| 34 | 19–91 | 84 | 56–57 | 134 | 106–107 | 184 | 155–156 | 234 | 209–210 |
| 35 | 19–92 | 85 | 56–164 | 135 | 107–108 | 185 | 155–180 | 235 | 211–212 |
| 36 | 20–21 | 86 | 58–59 | 136 | 108–109 | 186 | 156–157 | 236 | 213–214 |
| 37 | 21–22 | 87 | 58–80 | 137 | 109–110 | 187 | 157–158 | 237 | 215–216 |
| 38 | 22–23 | 88 | 59–60 | 138 | 110–111 | 188 | 158–159 | 238 | 216–217 |
| 39 | 22–71 | 89 | 60–61 | 139 | 111–112 | 189 | 161–162 | 239 | 217–218 |
| 40 | 22–72 | 90 | 61–62 | 140 | 112–113 | 190 | 162–190 | 240 | 218–219 |
| 41 | 23–24 | 91 | 62–63 | 141 | 112–114 | 191 | 162–205 | 241 | 219–220 |
| 42 | 24–25 | 92 | 63–64 | 142 | 113–115 | 192 | 163–164 | 242 | 220–221 |
| 43 | 25–26 | 93 | 64–65 | 143 | 114–210 | 193 | 163–191 | 243 | 221–222 |
| 44 | 26–27 | 94 | 65–66 | 144 | 114–211 | 194 | 165–166 | 244 | 222–223 |
| 45 | 27–28 | 95 | 66–67 | 145 | 115–116 | 195 | 166–167 | 245 | 223–224 |
| 46 | 28–29 | 96 | 67–68 | 146 | 116–117 | 196 | 167–168 | 246 | 224–225 |
| 47 | 28–134 | 97 | 68–69 | 147 | 117–118 | 197 | 169–170 | 247 | 225–226 |
| 48 | 28–135 | 98 | 69–70 | 148 | 118–119 | 198 | 170–171 | 248 | 226–227 |
| 49 | 29–30 | 99 | 70–71 | 149 | 120–121 | 199 | 171–172 | 249 | 227–228 |
| 50 | 30–31 | 100 | 73–74 | 150 | 120–206 | 200 | 172–173 | 250 | 228–229 |
Appendix C
| Ranking | Num. | Network Efficiency | Vulnerability | Decline Ratio | Ranking | Num. | Network Efficiency | Vulnerability | Decline Ratio |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 0.0894 | 0.0107 | 10.69% | 116 | 83 | 0.0992 | 0.0009 | 0.90% |
| 2 | 4 | 0.0902 | 0.0099 | 9.89% | 117 | 130 | 0.0992 | 0.0009 | 0.90% |
| 3 | 26 | 0.0909 | 0.0092 | 9.19% | 118 | 29 | 0.0992 | 0.0009 | 0.90% |
| 4 | 33 | 0.092 | 0.0081 | 8.09% | 119 | 199 | 0.0993 | 0.0008 | 0.80% |
| 5 | 205 | 0.0928 | 0.0073 | 7.29% | 120 | 188 | 0.0993 | 0.0008 | 0.80% |
| 6 | 8 | 0.0934 | 0.0067 | 6.69% | 121 | 184 | 0.0993 | 0.0008 | 0.80% |
| 7 | 5 | 0.094 | 0.0061 | 6.09% | 122 | 109 | 0.0993 | 0.0008 | 0.80% |
| 8 | 134 | 0.0945 | 0.0056 | 5.59% | 123 | 69 | 0.0993 | 0.0008 | 0.80% |
| 9 | 28 | 0.0945 | 0.0056 | 5.59% | 124 | 68 | 0.0993 | 0.0008 | 0.80% |
| 10 | 67 | 0.0948 | 0.0053 | 5.29% | 125 | 56 | 0.0993 | 0.0008 | 0.80% |
| 11 | 122 | 0.095 | 0.0051 | 5.09% | 126 | 49 | 0.0993 | 0.0008 | 0.80% |
| 12 | 17 | 0.0955 | 0.0046 | 4.60% | 127 | 181 | 0.0994 | 0.0007 | 0.70% |
| 13 | 66 | 0.0956 | 0.0045 | 4.50% | 128 | 151 | 0.0994 | 0.0007 | 0.70% |
| 14 | 23 | 0.0957 | 0.0044 | 4.40% | 129 | 136 | 0.0994 | 0.0007 | 0.70% |
| 15 | 6 | 0.0959 | 0.0042 | 4.20% | 130 | 128 | 0.0994 | 0.0007 | 0.70% |
| 16 | 30 | 0.0959 | 0.0042 | 4.20% | 131 | 118 | 0.0994 | 0.0007 | 0.70% |
| 17 | 7 | 0.0959 | 0.0042 | 4.20% | 132 | 82 | 0.0994 | 0.0007 | 0.70% |
| 18 | 206 | 0.096 | 0.0041 | 4.10% | 133 | 73 | 0.0994 | 0.0007 | 0.70% |
| 19 | 15 | 0.0961 | 0.0040 | 4.00% | 134 | 48 | 0.0994 | 0.0007 | 0.70% |
| 20 | 160 | 0.0963 | 0.0038 | 3.80% | 135 | 47 | 0.0994 | 0.0007 | 0.70% |
| 21 | 65 | 0.0963 | 0.0038 | 3.80% | 136 | 39 | 0.0994 | 0.0007 | 0.70% |
| 22 | 1 | 0.0963 | 0.0038 | 3.80% | 137 | 215 | 0.0995 | 0.0006 | 0.60% |
| 23 | 207 | 0.0964 | 0.0037 | 3.70% | 138 | 201 | 0.0995 | 0.0006 | 0.60% |
| 24 | 13 | 0.0964 | 0.0037 | 3.70% | 139 | 200 | 0.0995 | 0.0006 | 0.60% |
| 25 | 156 | 0.0965 | 0.0036 | 3.60% | 140 | 194 | 0.0995 | 0.0006 | 0.60% |
| 26 | 132 | 0.0965 | 0.0036 | 3.60% | 141 | 169 | 0.0995 | 0.0006 | 0.60% |
| 27 | 144 | 0.0966 | 0.0035 | 3.50% | 142 | 168 | 0.0995 | 0.0006 | 0.60% |
| 28 | 208 | 0.0968 | 0.0033 | 3.30% | 143 | 163 | 0.0995 | 0.0006 | 0.60% |
| 29 | 159 | 0.0968 | 0.0033 | 3.30% | 144 | 101 | 0.0995 | 0.0006 | 0.60% |
| 30 | 145 | 0.0968 | 0.0033 | 3.30% | 145 | 72 | 0.0995 | 0.0006 | 0.60% |
| 31 | 64 | 0.0969 | 0.0032 | 3.20% | 146 | 59 | 0.0995 | 0.0006 | 0.60% |
| 32 | 140 | 0.097 | 0.0031 | 3.10% | 147 | 55 | 0.0995 | 0.0006 | 0.60% |
| 33 | 131 | 0.097 | 0.0031 | 3.10% | 148 | 54 | 0.0995 | 0.0006 | 0.60% |
| 34 | 158 | 0.0971 | 0.0030 | 3.00% | 149 | 46 | 0.0995 | 0.0006 | 0.60% |
| 35 | 209 | 0.0972 | 0.0029 | 2.90% | 150 | 45 | 0.0995 | 0.0006 | 0.60% |
| 36 | 155 | 0.0972 | 0.0029 | 2.90% | 151 | 193 | 0.0996 | 0.0005 | 0.50% |
| 37 | 133 | 0.0972 | 0.0029 | 2.90% | 152 | 189 | 0.0996 | 0.0005 | 0.50% |
| 38 | 174 | 0.0973 | 0.0028 | 2.80% | 153 | 180 | 0.0996 | 0.0005 | 0.50% |
| 39 | 157 | 0.0974 | 0.0027 | 2.70% | 154 | 177 | 0.0996 | 0.0005 | 0.50% |
| 40 | 25 | 0.0974 | 0.0027 | 2.70% | 155 | 166 | 0.0996 | 0.0005 | 0.50% |
| 41 | 63 | 0.0975 | 0.0026 | 2.60% | 156 | 114 | 0.0996 | 0.0005 | 0.50% |
| 42 | 42 | 0.0975 | 0.0026 | 2.60% | 157 | 108 | 0.0996 | 0.0005 | 0.50% |
| 43 | 12 | 0.0975 | 0.0026 | 2.60% | 158 | 107 | 0.0996 | 0.0005 | 0.50% |
| 44 | 9 | 0.0975 | 0.0026 | 2.60% | 159 | 81 | 0.0996 | 0.0005 | 0.50% |
| 45 | 210 | 0.0976 | 0.0025 | 2.50% | 160 | 50 | 0.0996 | 0.0005 | 0.50% |
| 46 | 146 | 0.0976 | 0.0025 | 2.50% | 161 | 36 | 0.0996 | 0.0005 | 0.50% |
| 47 | 123 | 0.0976 | 0.0025 | 2.50% | 162 | 40 | 0.0996 | 0.0005 | 0.50% |
| 48 | 87 | 0.0976 | 0.0025 | 2.50% | 163 | 185 | 0.0997 | 0.0004 | 0.40% |
| 49 | 18 | 0.0976 | 0.0025 | 2.50% | 164 | 179 | 0.0997 | 0.0004 | 0.40% |
| 50 | 139 | 0.0977 | 0.0024 | 2.40% | 165 | 178 | 0.0997 | 0.0004 | 0.40% |
| 51 | 106 | 0.0977 | 0.0024 | 2.40% | 166 | 162 | 0.0997 | 0.0004 | 0.40% |
| 52 | 27 | 0.0977 | 0.0024 | 2.40% | 167 | 149 | 0.0997 | 0.0004 | 0.40% |
| 53 | 3 | 0.0977 | 0.0024 | 2.40% | 168 | 119 | 0.0997 | 0.0004 | 0.40% |
| 54 | 154 | 0.0978 | 0.0023 | 2.30% | 169 | 111 | 0.0997 | 0.0004 | 0.40% |
| 55 | 41 | 0.0978 | 0.0023 | 2.30% | 170 | 100 | 0.0997 | 0.0004 | 0.40% |
| 56 | 173 | 0.0979 | 0.0022 | 2.20% | 171 | 53 | 0.0997 | 0.0004 | 0.40% |
| 57 | 175 | 0.0979 | 0.0022 | 2.20% | 172 | 52 | 0.0997 | 0.0004 | 0.40% |
| 58 | 110 | 0.0979 | 0.0022 | 2.20% | 173 | 51 | 0.0997 | 0.0004 | 0.40% |
| 59 | 121 | 0.0979 | 0.0022 | 2.20% | 174 | 216 | 0.0998 | 0.0003 | 0.30% |
| 60 | 34 | 0.0979 | 0.0022 | 2.20% | 175 | 192 | 0.0998 | 0.0003 | 0.30% |
| 61 | 14 | 0.0979 | 0.0022 | 2.20% | 176 | 191 | 0.0998 | 0.0003 | 0.30% |
| 62 | 211 | 0.098 | 0.0021 | 2.10% | 177 | 190 | 0.0998 | 0.0003 | 0.30% |
| 63 | 164 | 0.098 | 0.0021 | 2.10% | 178 | 187 | 0.0998 | 0.0003 | 0.30% |
| 64 | 62 | 0.098 | 0.0021 | 2.10% | 179 | 182 | 0.0998 | 0.0003 | 0.30% |
| 65 | 115 | 0.0981 | 0.0020 | 2.00% | 180 | 143 | 0.0998 | 0.0003 | 0.30% |
| 66 | 86 | 0.0981 | 0.0020 | 2.00% | 181 | 126 | 0.0998 | 0.0003 | 0.30% |
| 67 | 19 | 0.0981 | 0.0020 | 2.00% | 182 | 120 | 0.0998 | 0.0003 | 0.30% |
| 68 | 11 | 0.0981 | 0.0020 | 2.00% | 183 | 99 | 0.0998 | 0.0003 | 0.30% |
| 69 | 124 | 0.0982 | 0.0019 | 1.90% | 184 | 91 | 0.0998 | 0.0003 | 0.30% |
| 70 | 105 | 0.0982 | 0.0019 | 1.90% | 185 | 90 | 0.0998 | 0.0003 | 0.30% |
| 71 | 10 | 0.0982 | 0.0019 | 1.90% | 186 | 80 | 0.0998 | 0.0003 | 0.30% |
| 72 | 138 | 0.0983 | 0.0018 | 1.80% | 187 | 38 | 0.0998 | 0.0003 | 0.30% |
| 73 | 44 | 0.0983 | 0.0018 | 1.80% | 188 | 37 | 0.0998 | 0.0003 | 0.30% |
| 74 | 43 | 0.0983 | 0.0018 | 1.80% | 189 | 186 | 0.0999 | 0.0002 | 0.20% |
| 75 | 212 | 0.0984 | 0.0017 | 1.70% | 190 | 142 | 0.0999 | 0.0002 | 0.20% |
| 76 | 170 | 0.0984 | 0.0017 | 1.70% | 191 | 141 | 0.0999 | 0.0002 | 0.20% |
| 77 | 153 | 0.0984 | 0.0017 | 1.70% | 192 | 135 | 0.0999 | 0.0002 | 0.20% |
| 78 | 147 | 0.0984 | 0.0017 | 1.70% | 193 | 129 | 0.0999 | 0.0002 | 0.20% |
| 79 | 161 | 0.0985 | 0.0016 | 1.60% | 194 | 125 | 0.0999 | 0.0002 | 0.20% |
| 80 | 85 | 0.0985 | 0.0016 | 1.60% | 195 | 204 | 0.0999 | 0.0002 | 0.20% |
| 81 | 61 | 0.0985 | 0.0016 | 1.60% | 196 | 35 | 0.0999 | 0.0002 | 0.20% |
| 82 | 32 | 0.0985 | 0.0016 | 1.60% | 197 | 117 | 0.0999 | 0.0002 | 0.20% |
| 83 | 24 | 0.0985 | 0.0016 | 1.60% | 198 | 116 | 0.0999 | 0.0002 | 0.20% |
| 84 | 20 | 0.0985 | 0.0016 | 1.60% | 199 | 94 | 0.0999 | 0.0002 | 0.20% |
| 85 | 176 | 0.0986 | 0.0015 | 1.50% | 200 | 89 | 0.0999 | 0.0002 | 0.20% |
| 86 | 104 | 0.0986 | 0.0015 | 1.50% | 201 | 79 | 0.0999 | 0.0002 | 0.20% |
| 87 | 213 | 0.0987 | 0.0014 | 1.40% | 202 | 222 | 0.1 | 0.0001 | 0.10% |
| 88 | 195 | 0.0987 | 0.0014 | 1.40% | 203 | 219 | 0.1 | 0.0001 | 0.10% |
| 89 | 112 | 0.0987 | 0.0014 | 1.40% | 204 | 167 | 0.1 | 0.0001 | 0.10% |
| 90 | 165 | 0.0988 | 0.0013 | 1.30% | 205 | 150 | 0.1 | 0.0001 | 0.10% |
| 91 | 137 | 0.0988 | 0.0013 | 1.30% | 206 | 98 | 0.1 | 0.0001 | 0.10% |
| 92 | 127 | 0.0988 | 0.0013 | 1.30% | 207 | 93 | 0.1 | 0.0001 | 0.10% |
| 93 | 88 | 0.0988 | 0.0013 | 1.30% | 208 | 92 | 0.1 | 0.0001 | 0.10% |
| 94 | 31 | 0.0988 | 0.0013 | 1.30% | 209 | 58 | 0.1 | 0.0001 | 0.10% |
| 95 | 21 | 0.0988 | 0.0013 | 1.30% | 210 | 97 | 0.1001 | 0.0000 | 0.00% |
| 96 | 16 | 0.0988 | 0.0013 | 1.30% | 211 | 96 | 0.1001 | 0.0000 | 0.00% |
| 97 | 196 | 0.0989 | 0.0012 | 1.20% | 212 | 95 | 0.1001 | 0.0000 | 0.00% |
| 98 | 183 | 0.0989 | 0.0012 | 1.20% | 213 | 78 | 0.1001 | 0.0000 | 0.00% |
| 99 | 171 | 0.0989 | 0.0012 | 1.20% | 214 | 77 | 0.1001 | 0.0000 | 0.00% |
| 100 | 152 | 0.0989 | 0.0012 | 1.20% | 215 | 76 | 0.1001 | 0.0000 | 0.00% |
| 101 | 103 | 0.0989 | 0.0012 | 1.20% | 216 | 75 | 0.1001 | 0.0000 | 0.00% |
| 102 | 84 | 0.0989 | 0.0012 | 1.20% | 217 | 74 | 0.1001 | 0.0000 | 0.00% |
| 103 | 71 | 0.0989 | 0.0012 | 1.20% | 218 | 217 | 0.1001 | 0.0000 | 0.00% |
| 104 | 203 | 0.099 | 0.0011 | 1.10% | 219 | 172 | 0.1001 | 0.0000 | 0.00% |
| 105 | 202 | 0.099 | 0.0011 | 1.10% | 220 | 228 | 0.1001 | 0.0000 | 0.00% |
| 106 | 197 | 0.099 | 0.0011 | 1.10% | 221 | 227 | 0.1001 | 0.0000 | 0.00% |
| 107 | 60 | 0.099 | 0.0011 | 1.10% | 222 | 225 | 0.1001 | 0.0000 | 0.00% |
| 108 | 214 | 0.0991 | 0.0010 | 1.00% | 223 | 223 | 0.1001 | 0.0000 | 0.00% |
| 109 | 148 | 0.0991 | 0.0010 | 1.00% | 224 | 226 | 0.1001 | 0.0000 | 0.00% |
| 110 | 113 | 0.0991 | 0.0010 | 1.00% | 225 | 224 | 0.1001 | 0.0000 | 0.00% |
| 111 | 70 | 0.0991 | 0.0010 | 1.00% | 226 | 221 | 0.1001 | 0.0000 | 0.00% |
| 112 | 57 | 0.0991 | 0.0010 | 1.00% | 227 | 220 | 0.1001 | 0.0000 | 0.00% |
| 113 | 22 | 0.0991 | 0.0010 | 1.00% | 228 | 218 | 0.1001 | 0.0000 | 0.00% |
| 114 | 198 | 0.0992 | 0.0009 | 0.90% | 229 | 229 | 0.1001 | 0.0000 | 0.00% |
| 115 | 102 | 0.0992 | 0.0009 | 0.90% |
References
- Yi, P.; Huang, F.; Wang, J.; Peng, J. Topology augmented dynamic spatial-temporal network for passenger flow forecasting in urban rail transit. Appl. Intell. 2023, 53, 24655–24670. [Google Scholar] [CrossRef]
- Hu, H.; Li, J.; Wu, S. Simulation Evaluation of a Current Limiting Scheme in an Urban Rail Transit Network. Sustainability 2023, 15, 375. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, Y.; Zhang, J. Large-Scale Origin–Destination Prediction for Urban Rail Transit Network Based on Graph Convolutional Neural Network. Sustainability 2024, 16, 10190. [Google Scholar] [CrossRef]
- Arabiun, A.; Dehkordi, A.M.; Hosseini, E.; Brahmi, M. A Framework for Strategic Analysis in Dynamic and Complex Environments. In Exploring Business Ecosystems and Innovation Capacity Building in Global Economics; Joshi, M., Brahmi, M., Aldieri, L., Vinci, C., Eds.; IGI Global Scientific Publishing: Hershey, PA, USA, 2023; pp. 26–47. [Google Scholar]
- Wei, W.; Yang, X.; Xiao, X.; Ma, Z.; Zhu, T.; Dou, F.; Wu, J.; Chen, A.; Gao, Z. Understanding the Resilience of Urban Rail Transit: Concepts, Reviews, and Trends. Engineering 2024, 41, 7–18. [Google Scholar] [CrossRef]
- Chen, Z.P.; Xie, N.; Wang, C.M.; Qian, Z. Vulnerability Evaluation and Robustness Improvement Strategy of Complex Power Network Based on Fractal Mechanism. Power Syst. Technol. 2021, 45, 657–665. [Google Scholar]
- Wei, J.L.; Zhao, L.Y. Urban Road Network Vulnerability Assessment and Mitigation Strategies: A Case Study in Wuhan Main City. Mod. Urban Res. 2020, 35, 6. [Google Scholar]
- Yang, L.P.; Qian, D.L. Vulnerability Analysis of Road Networks. J. Transp. Syst. Eng. Inf. Technol. 2012, 12, 105–110. [Google Scholar] [CrossRef]
- Huang, Z.; Loo Becky, P.Y. Vulnerability assessment of urban rail transit in face of disruptions: A framework and some lessons from Hong Kong. Sustain. Cities Soc. 2023, 98, 104858. [Google Scholar] [CrossRef]
- Deng, Y.; Li, Q.; Lu, Y.; Yuan, J. Topology Vulnerability Analysis and Measure of Urban Metro Network: The ease of Nanjing. J. Netw. 2013, 8, 1350. [Google Scholar] [CrossRef]
- Latora, V.; Marchiori, M. Is the Boston subway a small-world network? Phys. A Stat. Mech. Its Appl. 2002, 314, 109–113. [Google Scholar] [CrossRef]
- Zhang, J.H. The Research on Connectivity Vulnerability of Metro Complex Networks. Ph.D. Thesis, Huazhong University of Science and Technology, Wuhan, China, 2012. [Google Scholar]
- Yalçınkaya, Ö.; Bayhan, G.M. Modelling and optimization of average travel time for a metro line by simulation and response surface methodology. Eur. J. Oper. Res. 2008, 196, 225–233. [Google Scholar] [CrossRef]
- Raveau, S.; Muñoz, J.C.; Grange, L.D. A topological route choice model for metro. Transp. Res. Part A 2010, 45, 138–147. [Google Scholar] [CrossRef]
- Cheng, Y.-Y.; Lee, R.K.-W.; Lim, E.-P.; Zhu, F. DelayFlow centrality for identifying critical nodes in transportation networks. Adv. Soc. Netw. Anal. Min. 2013, 1462–1463. [Google Scholar]
- Cai, H.; Zhu, J.; Yang, C.; Fan, W.; Xu, T. Vulnerability Analysis of Metro Network Incorporating Flow Impact and Capacity Constraint after a Disaster. J. Urban Plan. Dev. 2016, 143, 04016031. [Google Scholar] [CrossRef]
- Sun, D.; Zhao, Y.; Lu, Q.-C. Vulnerability Analysis of Urban Rail Transit Networks: A Case Study of Shanghai, China. Sustainability 2015, 7, 6919–6936. [Google Scholar] [CrossRef]
- Sun, D.; Guan, S. Measuring vulnerability of urban metro network from line operation perspective. Transp. Res. Part A Policy Pract. 2016, 94, 348–359. [Google Scholar] [CrossRef]
- Xu, X.; Song, S.X.; Yuan, P.W. Evaluation of network vulnerability of subway stations based on ANP. China Saf. Sci. J. 2015, 25, 129–134. [Google Scholar]
- Cheng, F.F.; Chang, M.; Chen, Q. A methodology to assess vulnerability of environmental incidents in cities and towns. China Popul. Resour. Environ. 2016, 26, 48–52. [Google Scholar]
- Albert, R.; Jeong, H.; Barabasi, A.L. Error and attack tolerance of complex networks. Nature 2000, 406, 378–382. [Google Scholar] [CrossRef]
- Yang, J.F.; Zhu, D.P.; Zhao, R.L. Analysis on Characteristics of Urban Rail Transit Network and Robustness of Cascading Failure. Comput. Eng. Appl. 2022, 58, 250–258. [Google Scholar]
- Lv, J.; Chen, G.; Ogorzalek, M.J.; Trajković, L. Theory and applications of complex networks: Advances and challenges. In Proceedings of the IEEE International Symposium on Circuits & Systems, Beijing, China, 19–23 May 2013; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar]
- Thai, M.T.; Pardalos, P.M. (Eds.) Handbook of Optimization in Complex Networks. Theory and Applications; Springer Optimization & Its Applications; Springer: Berlin/Heidelberg, Germany, 2011; Volume 58, pp. 0111222–0112001. [Google Scholar]
- Albert, R.; Albert, I.; Nakarado, G.L. Structural vulnerability of the North American power grid. Phys. Rev. E Stat. Phys. Plasmas Fluids Relat. Interdiscip. Top. 2004, 69, 025103(R). [Google Scholar] [CrossRef] [PubMed]
- Wang, J.W.; Rong, L.L. Cascade-based attack vulnerability on the US power grid. Saf. Sci. 2009, 47, 1332–1336. [Google Scholar] [CrossRef]
- Winkler, J.; Duenas-Osorio, L.; Stein, R.; Subramanian, D. Performance assessment of topologically diverse power systems subjected to hurricane events. Reliab. Eng. Syst. Saf. 2010, 95, 323–336. [Google Scholar] [CrossRef]
- Ezzeldin, M.; El-Dakhakhni, W.E. Robustness of Ontario power network under systemic risks. Sustain. Resilient Infrastruct. 2021, 6, 252–271. [Google Scholar] [CrossRef]
- Ouyang, M.; Yu, M.H.; Huang, X.Z.; Luan, E.J. Emergency response to disaster-struck scale-free network with redundant systems. Phys. A Stat. Mech. Its Appl. 2008, 387, 4683–4691. [Google Scholar] [CrossRef]
- Simone, A.; Ridolfi, L.; Berardi, L.; Laucelli, D.; Giustolisi, O. Complex Network Theory for Water Distribution Networks analysis. In Proceedings of the 13th International Conference on Hydroinformatics, HIC 2018, Palermo, Italy, 1–5 July 2018. [Google Scholar]
- Wu, J.J.; Gao, Z.Y.; Sun, H.J. Effects of the cascading failures on scale-free traffic networks. Phys. A Stat. Mech. Its Appl. 2007, 378, 505–511. [Google Scholar] [CrossRef]
- Zhang, J.; Cao, X.B.; Du, W.B.; Cai, K.Q. Evolution of Chinese airport network. Phys. A Stat. Mech. Its Appl. 2010, 389, 3922–3931. [Google Scholar] [CrossRef] [PubMed]
- Ma, Z.L.; Hu, D.W.; Chien Steven, I.; Liu, J.; Liu, Y.; Wu, K. Robustness of Urban Rail Transit Networks Considering Cascade Failure under Attacks: A Case Study of Nanjing, China. ASCE-ASME J. Risk Uncertain. Eng. Syst. Part A Civ. Eng. 2025, 11, 04024093. [Google Scholar] [CrossRef]
- Tang, M.; Guo, X.; Qiu, J.; Li, J.; An, B. Electric Vehicle Charging Load Demand Forecasting in Different Functional Areas of Cities with Weighted Measurement Fusion UKF Algorithm. Energies 2024, 17, 4505. [Google Scholar] [CrossRef]
- Lee, K.; Jung, W.-S.; Park, J.S.; Choi, M. Statistical analysis of the Metropolitan Seoul Subway System: Network structure and passenger flows. Phys. A Stat. Mech. Its Appl. 2008, 387, 6231–6234. [Google Scholar] [CrossRef]
- Lu, Q.-C.; Lin, S. Vulnerability Analysis of Urban Rail Transit Network within Multi-Modal Public Transport Networks. Sustainability 2019, 11, 2109. [Google Scholar] [CrossRef]
- Zhang, T.Y.; Song, R.; Zheng, L. Analysis of Domestic Subway Network Characteristics Based on Complex Network Theory. J. Transp. Inf. Saf. 2012, 30, 50–54. [Google Scholar]
- Gu, Y.; Cheng, L. The Robustness of Urban Rail Transit Network based on Complex Network Theory. In Proceedings of the 2016 3rd International Conference on Materials Engineering, Manufacturing Technology and Control, Taiyuan, China, 27–28 February 2016; Atlantis Press: Amsterdam, The Netherlands, 2016. [Google Scholar]
- Latora, V.; Marchiori, M. Efficient behavior of small-world networks. Phys. Rev. Lett. 2001, 87, 198701. [Google Scholar] [CrossRef] [PubMed]
- Holme, P.; Kim, B.J.; Yoon, C.N.; Han, S.K. Attack vulnerability of complex networks. Phys. Rev. E Stat. Nonlin. Soft Matter. Phys. 2002, 65, 056109. [Google Scholar] [CrossRef] [PubMed]
- Ma, M.; Hu, D.W.; Shu, L.; Ma, Z.L. Resilience assessment and recovery strategy on urban rail transit network. J. Jilin Univ. (Eng. Technol. Ed.) 2023, 53, 396–404. [Google Scholar]





| The Initial Network | After Suffering From a Node Attack | After Suffering From the Edge Attack | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| N1 | N2 | N3 | N4 | N5 | N1 | N2 | N3 | N4 | N5 | N1 | N2 | N3 | N4 | N5 | |||
| N1 | 0 | 1 | 1 | 0 | 0 | N1 | 0 | 0 | 1 | 0 | 0 | N1 | 0 | 0 | 1 | 0 | 0 |
| N2 | 1 | 0 | 1 | 0 | 0 | N2 | 0 | 0 | 0 | 0 | 0 | N2 | 0 | 0 | 1 | 0 | 0 |
| N3 | 1 | 1 | 0 | 1 | 1 | N3 | 1 | 0 | 0 | 1 | 1 | N3 | 1 | 1 | 0 | 1 | 1 |
| N4 | 0 | 0 | 1 | 0 | 1 | N4 | 0 | 0 | 1 | 0 | 1 | N4 | 0 | 0 | 1 | 0 | 1 |
| N5 | 0 | 0 | 1 | 1 | 0 | N5 | 0 | 0 | 1 | 1 | 0 | N5 | 0 | 0 | 1 | 1 | 0 |
| Number | Site | Network Efficiency | Vulnerability | Decline Ratio |
|---|---|---|---|---|
| 2 | Yudaishan | 0.0894 | 0.0107 | 10.69% |
| 4 | Sports Park | 0.0902 | 0.0099 | 9.89% |
| 26 | Erlang | 0.0909 | 0.0092 | 9.19% |
| 33 | Shapingba | 0.092 | 0.0081 | 8.09% |
| 205 | Longtousi Park | 0.0928 | 0.0073 | 7.29% |
| 8 | Min’an Ave | 0.0934 | 0.0067 | 6.69% |
| 5 | Ranjiaba | 0.094 | 0.0061 | 6.09% |
| 134 | Huayansi | 0.0945 | 0.0056 | 5.59% |
| 28 | Chonogqing West Station | 0.0945 | 0.0056 | 5.59% |
| 67 | Ping’an | 0.0948 | 0.0053 | 5.29% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, L.; Xiang, P.; Qian, Y.; Yang, S.; Zhou, T.; Wang, F. Vulnerability Assessment of Urban Rail Transit Network—A Case Study of Chongqing. Buildings 2025, 15, 170. https://doi.org/10.3390/buildings15020170
Xu L, Xiang P, Qian Y, Yang S, Zhou T, Wang F. Vulnerability Assessment of Urban Rail Transit Network—A Case Study of Chongqing. Buildings. 2025; 15(2):170. https://doi.org/10.3390/buildings15020170
Chicago/Turabian StyleXu, Lan, Pengcheng Xiang, Yan Qian, Simai Yang, Tao Zhou, and Feng Wang. 2025. "Vulnerability Assessment of Urban Rail Transit Network—A Case Study of Chongqing" Buildings 15, no. 2: 170. https://doi.org/10.3390/buildings15020170
APA StyleXu, L., Xiang, P., Qian, Y., Yang, S., Zhou, T., & Wang, F. (2025). Vulnerability Assessment of Urban Rail Transit Network—A Case Study of Chongqing. Buildings, 15(2), 170. https://doi.org/10.3390/buildings15020170







