Security by Design for Industrial Control Systems from a Cyber–Physical System Perspective: A Systematic Mapping Study †
Abstract
1. Introduction
- RQ1: How is the security-by-design paradigm defined?
- –
- RQ1.1 What exactly are the system development lifecycle phases concerned by security-by-design methodologies?
- –
- RQ1.2 Which security aspects (e.g., attacks, threats, vulnerabilities, and security controls) were focused on?
- –
- RQ1.3 Which security objectives (CIA, etc.) were addressed?
- –
- RQ1.4 Which other system requirements were considered while integrating security?
- RQ2: What are the characteristics of a security-by-design methodology?
- –
- RQ2.1 What are the steps that constitute each security-by-design methodology?
- –
- RQ2.2 Which security integration mechanism is used by the methodology?
- –
- RQ2.3 What element did the methodology focus on to consider security?
- –
- RQ2.4 What are the methodology models and how were they modeled?
2. Background and Related Works
2.1. Background
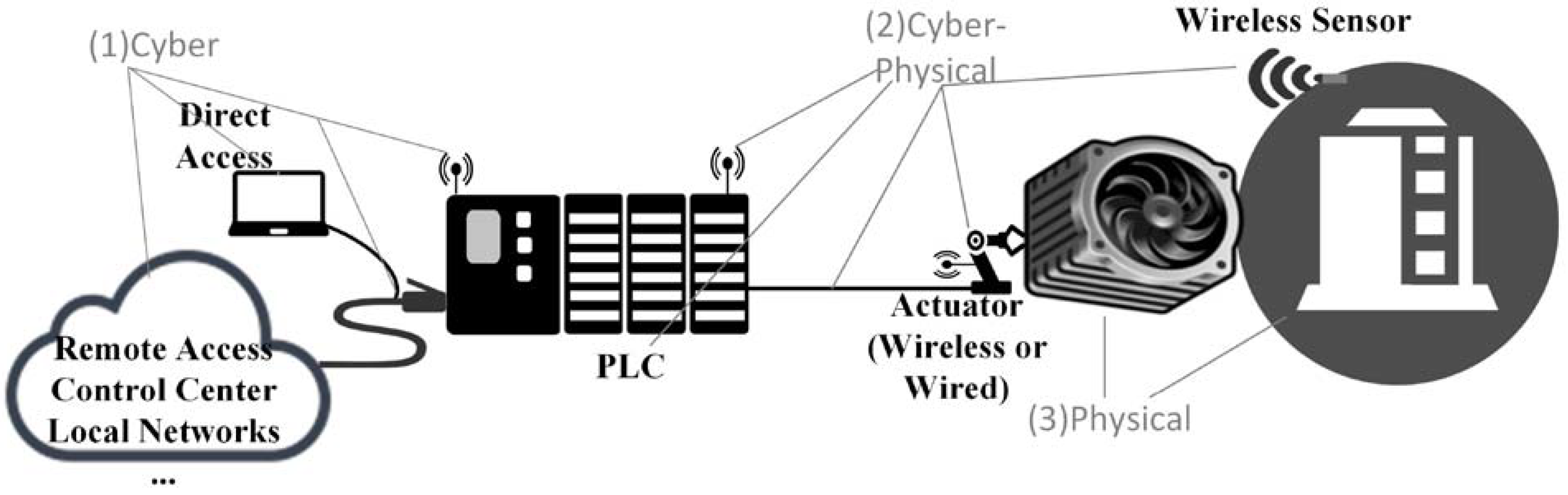
2.1.1. ICS and CPS Relationship
2.1.2. System Requirements
- Functional requirement: It encompasses the functions/components of the system and their interactions, which are necessary to provide the intended functionality [18].
- Performance requirement: It relates to performance considerations and encompasses constraints on factors such as timing, processing or reaction speed, data volume, and throughput [17].
- Specific quality requirement: It consists of specific qualities that the system or a component shall have like security, safety, and reliability [17].
- Constraint: It is a requirement that constrains the solution space beyond what is necessary for meeting the given functional, performance, and specific quality requirements [17].
2.1.3. Terminology
- Attack: “An attempt to gain unauthorized access to system services, resources, or information, or an attempt to compromise system integrity, availability, or confidentiality” [2].
- Threat: “Any circumstance or event with the potential to adversely impact agency operations (including mission, functions, image, or reputation), agency assets, or individuals through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service” [2].
- Mitigation: “A decision, action, or practice intended to reduce the level of risk associated with one or more threat events, threat scenarios, or vulnerabilities” [19].
- Weakness: “Defect or characteristic that may lead to undesirable behavior” [20].
- Vulnerability: “Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source” [2].
- Security objectives: These mainly consists of confidentiality, integrity, and availability (CIA) [21]. Other cybersecurity concepts are considered as security objectives such as authentication and non-repudiation. They are mentioned in this systematic mapping as “other security objectives”.
- Security aspects: “security threats, vulnerabilities, attacks, and security solutions as different aspects to be considered while engineering security” [7].
- Model: “a physical, mathematical, or otherwise logical representation of a system, entity, phenomenon, or process” [22].
- Modeling language: “A language in which a model is expressed. It includes syntax, rules, and its semantics” [23].
- Security by design is a security approach defined in reference [3] as the sufficiently early integration of security decisions into an established engineering workflow (or base workflow) which ensures that crucial design decisions remain open to influences.
2.2. Related Works
3. Research Method
- Planning: During this phase, our main objective is to define the protocol to follow. Firstly, the research questions were identified (Section 3.1) after analyzing the needs for this systematic mapping and extracting other systematic studies’ limitations according to our objectives. Secondly, a protocol describing in detail the steps we must follow while conducting the study is defined. After, a data extraction scheme is created. This defines the various data we should extract in order to answer our research questions. Finally, the protocol and the data extraction scheme are reviewed several times until they are approved by all the participants before moving to the second phase.
- Conducting: During this phase, we put into practice the defined protocol. First, we began by searching for a set of candidate papers on security by design. During this step, we used an automatic search in three databases (IEEE explore, ACM Digital Library, and ScienceDirect). Another technique used for searching for candidate papers is snowballing. It is used after the selection of the first set of primary studies. Second, the candidate papers are then filtered to obtain the final list of primary studies that correspond to and answer our research questions. Third, we extract data according to the extraction scheme defined in the first phase. Finally, we synthesize the data collected and analyze them using different types of graphics. This activity elaborates on the information extracted in order to answer the research questions one by one.
- Reporting: The final phase corresponds to writing up the results and disseminating the study to potentially interested parties. This report elaborates on the main findings but also discusses the threats to validity. In the end, this report is written and reviewed for publication.
3.1. Research Questions
3.2. Exclusion Criteria
- (EC1): Unrelated domain studies are excluded. (They must concern the CPS domain and its sub-domains.)
- (EC2): Studies not focusing on a “security-by-design” methodology are excluded. This means only studies that integrate security in the system development lifecycle are considered.
- (EC3): Studies not focusing on the design or implementation phases are excluded. This means that papers not considering at least one of these phases are not included.
- (EC4): The old versions of studies are excluded. For instance, we excluded certain workshop and conference papers when their extended versions were published in academic journals.
- (EC5): Studies before 2012 or after 2024 are excluded.
- (EC6): Papers less than 4 pages long are excluded.
- (EC7): Secondary and tertiary studies are excluded.
- (EC8): Non-peer-viewed papers are excluded.
- (EC9): Non-English papers are excluded.
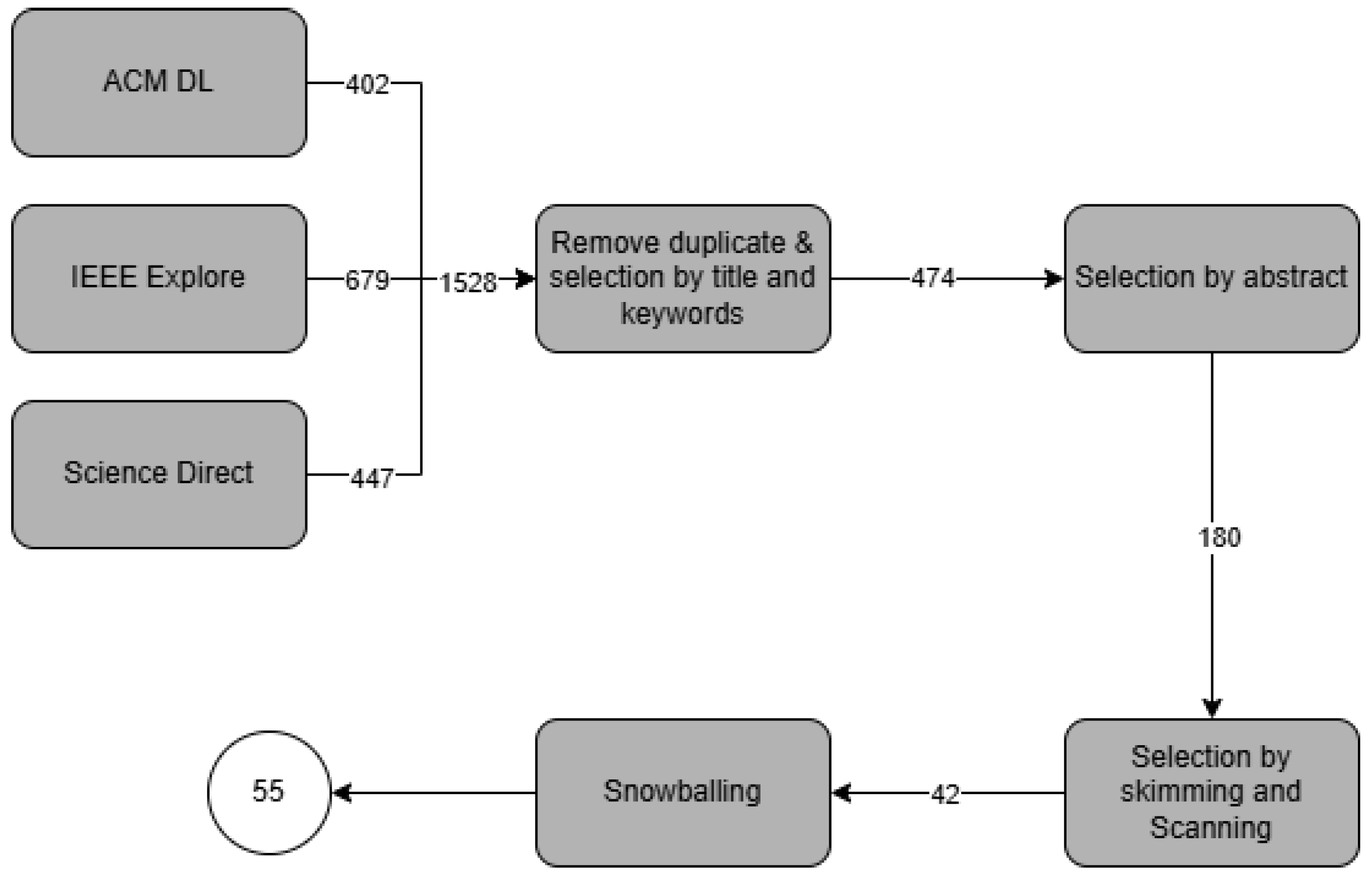
3.3. Search Strategy
3.3.1. Step 1: Automatic Search
- The population in which the evidence is collected i.e., which groups of system types are of interest for the review. Our review concentrates on CPSs. We derived other sub-types of systems from CPSs such as the Internet of Things and ICSs.
- The intervention applied in the empirical study, i.e., which technology, tool, or procedure is under study. In our case, it corresponds to security by design.
- The comparison to which the intervention is compared to. Due to the exploratory study, the comparison is not relevant, so it was excluded.
- The outcomes represent the goal of the paper. In our case, we search for methodologies. This is not considered in the search string but rather in the exclusion criteria.
3.3.2. Step 2: Removing Duplicate Papers and Selection by Title and Keyword
3.3.3. Step 3: Selection by Abstract
3.3.4. Step 4: Selection by Skimming and Scanning
3.3.5. Step 5: Snowballing
3.4. Data Extraction
4. Results
4.1. Documentation
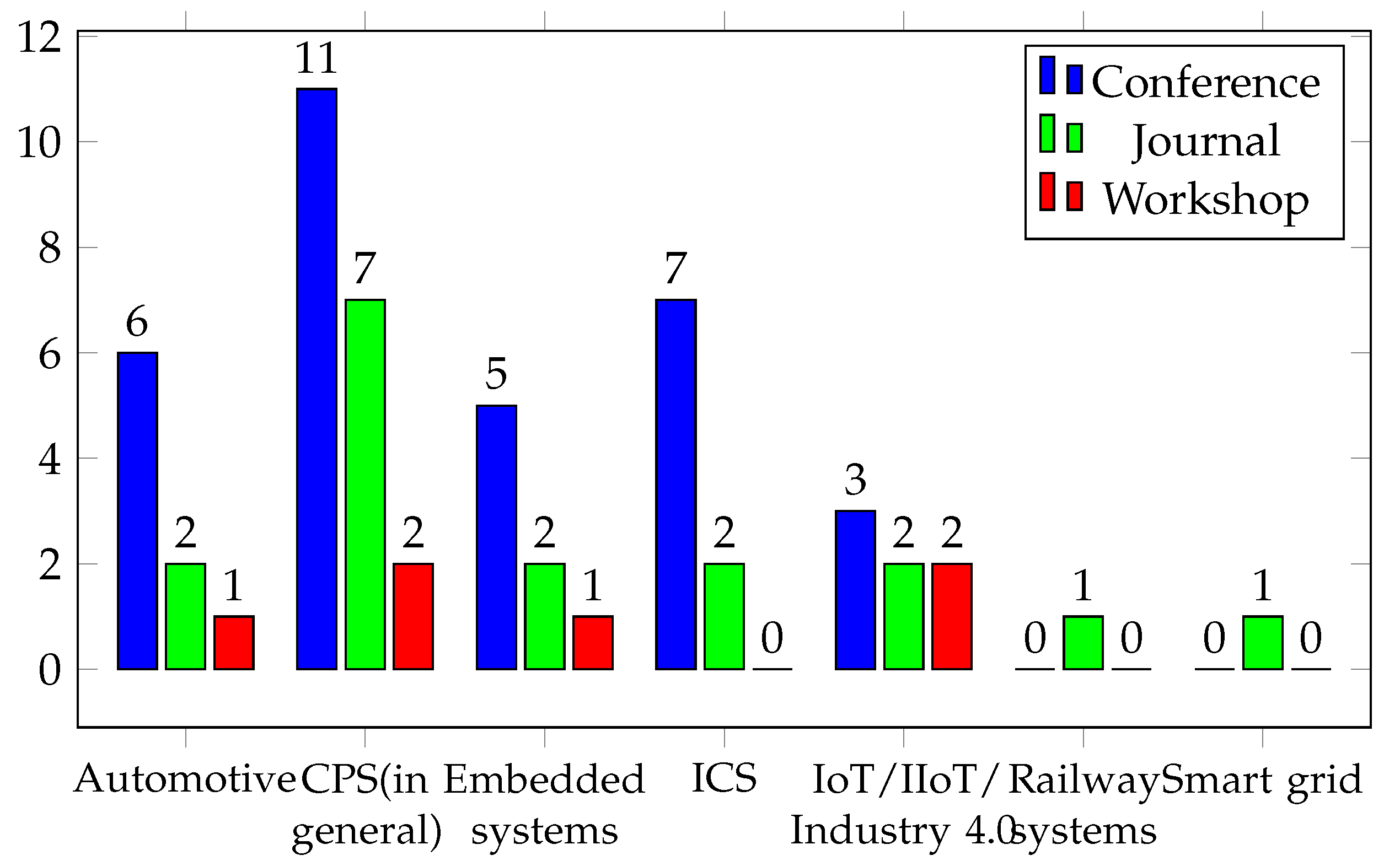
4.1.1. Domain
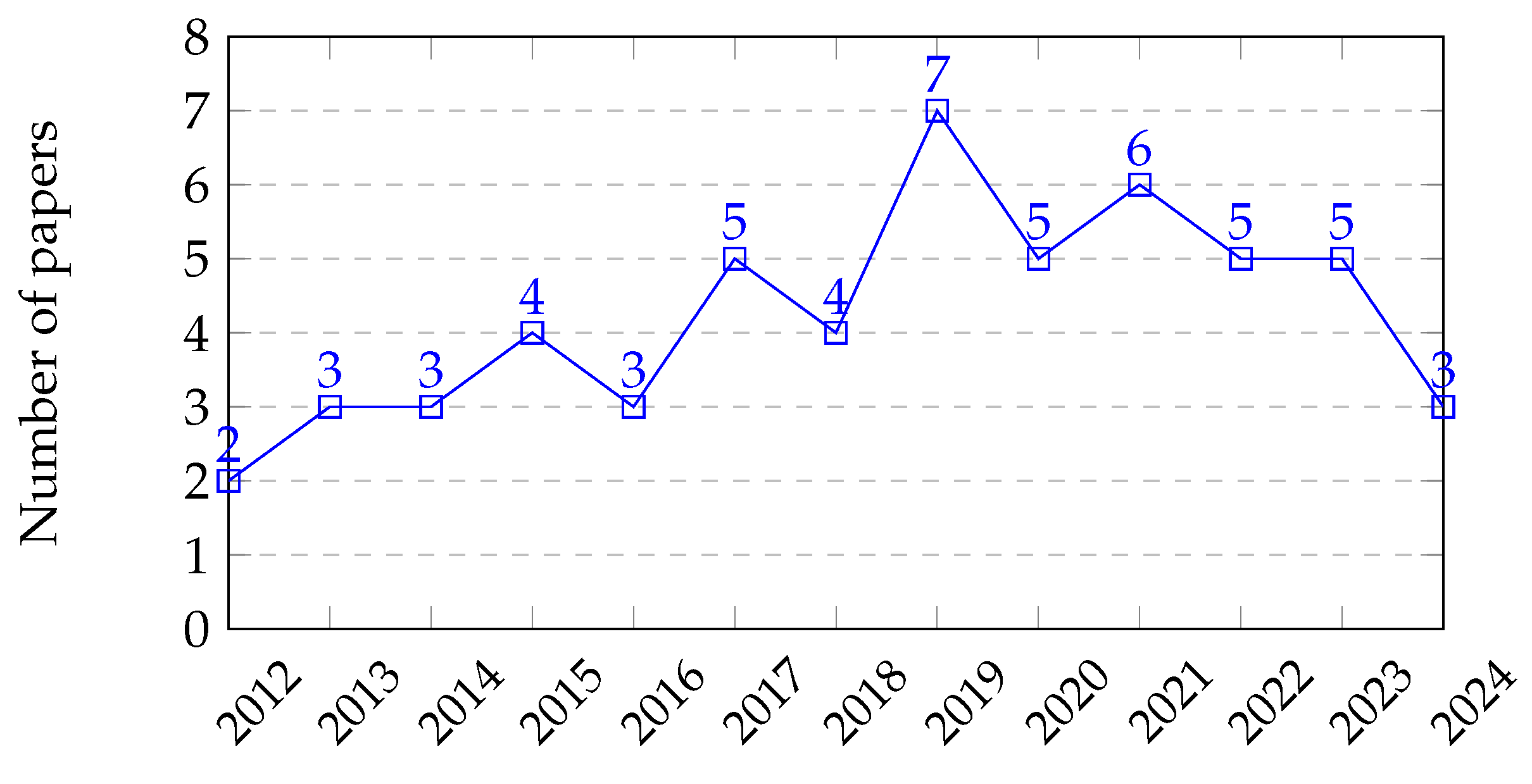
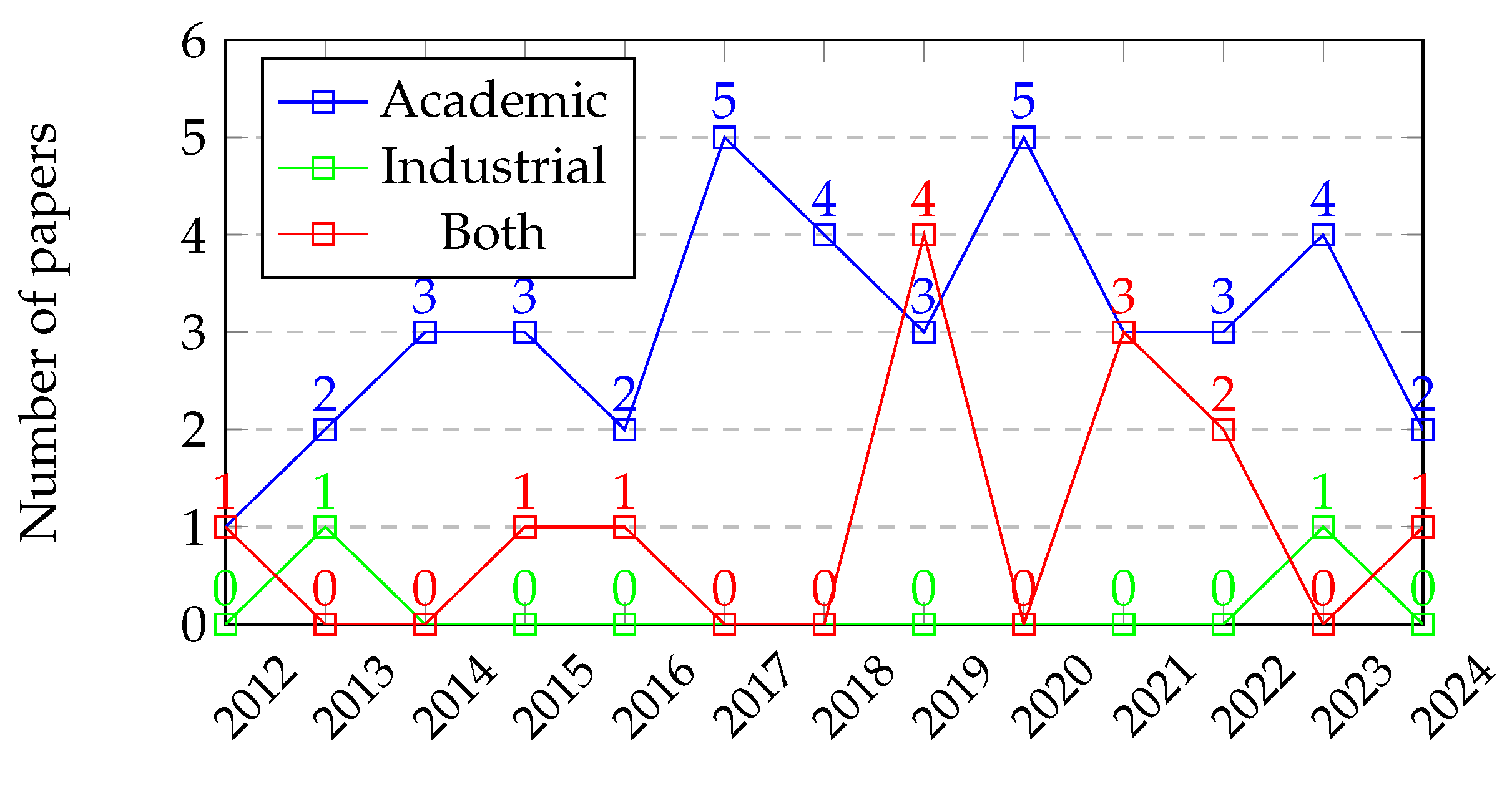
4.1.2. Publication Year
4.1.3. Venue and Type
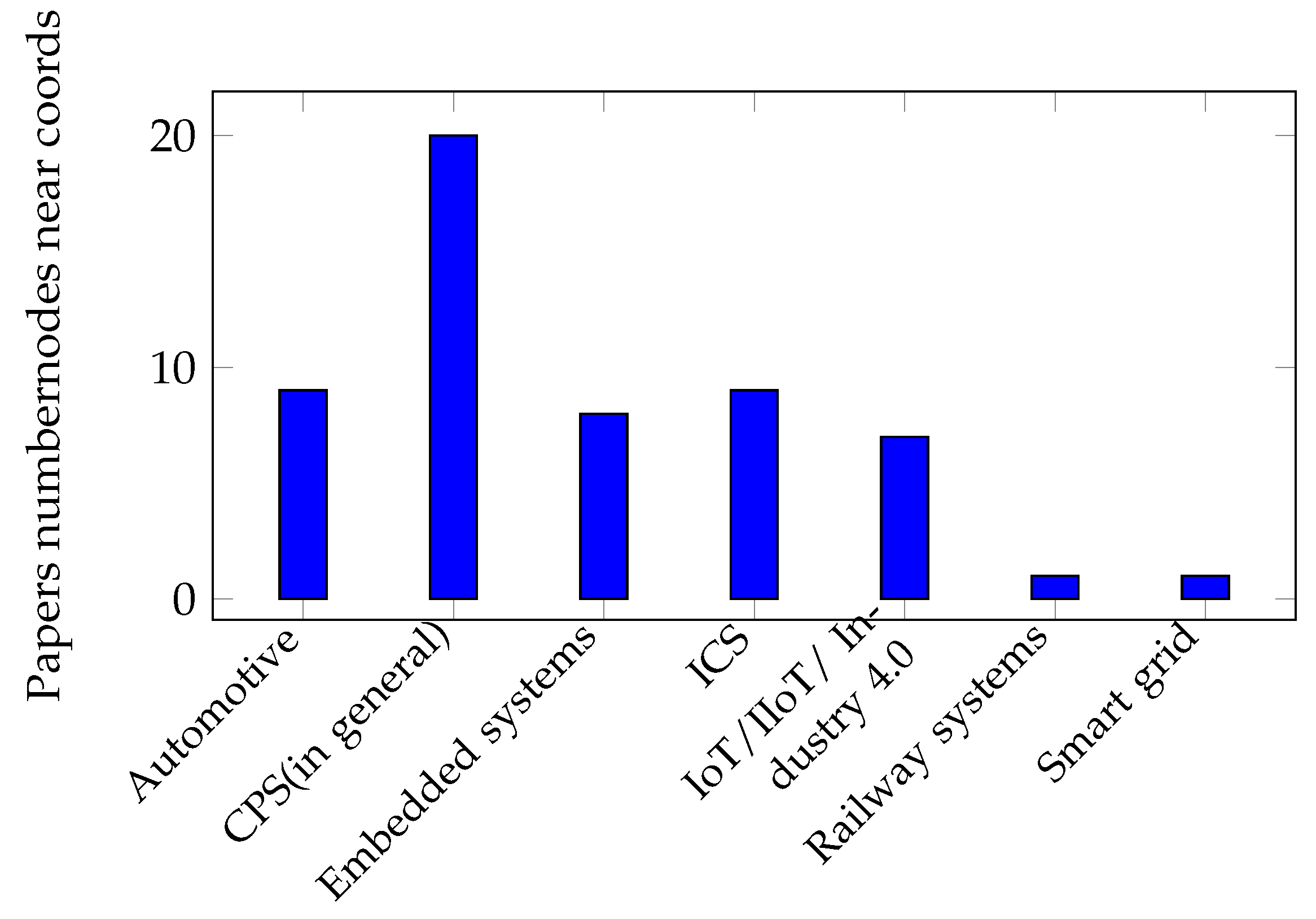
4.1.4. Context
4.2. RQ1: Towards a Security-by-Design Definition
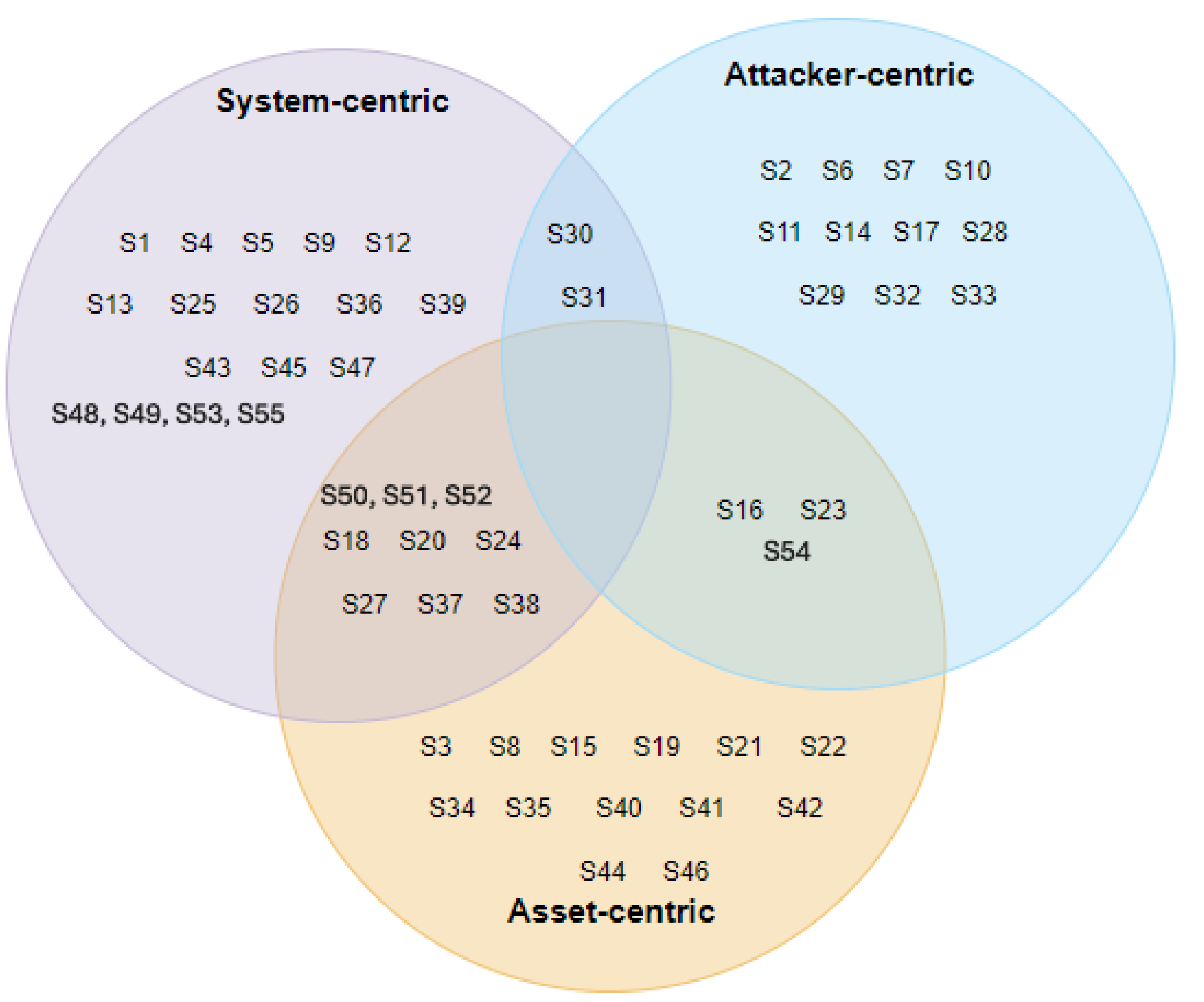
4.2.1. RQ1.1—What Exactly Are the System Development Lifecycle Phases Concerned by Security-by-Design Methodologies?
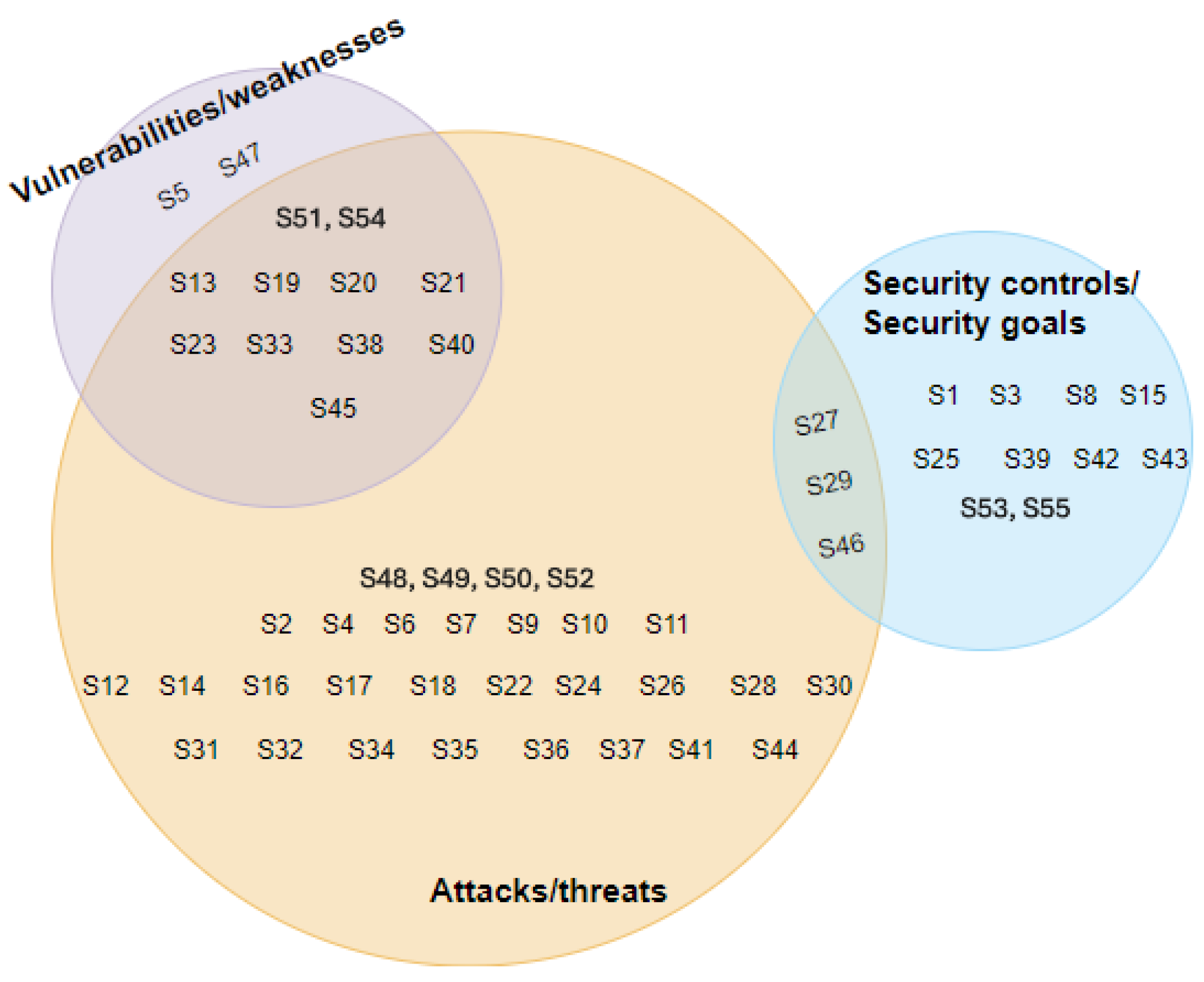
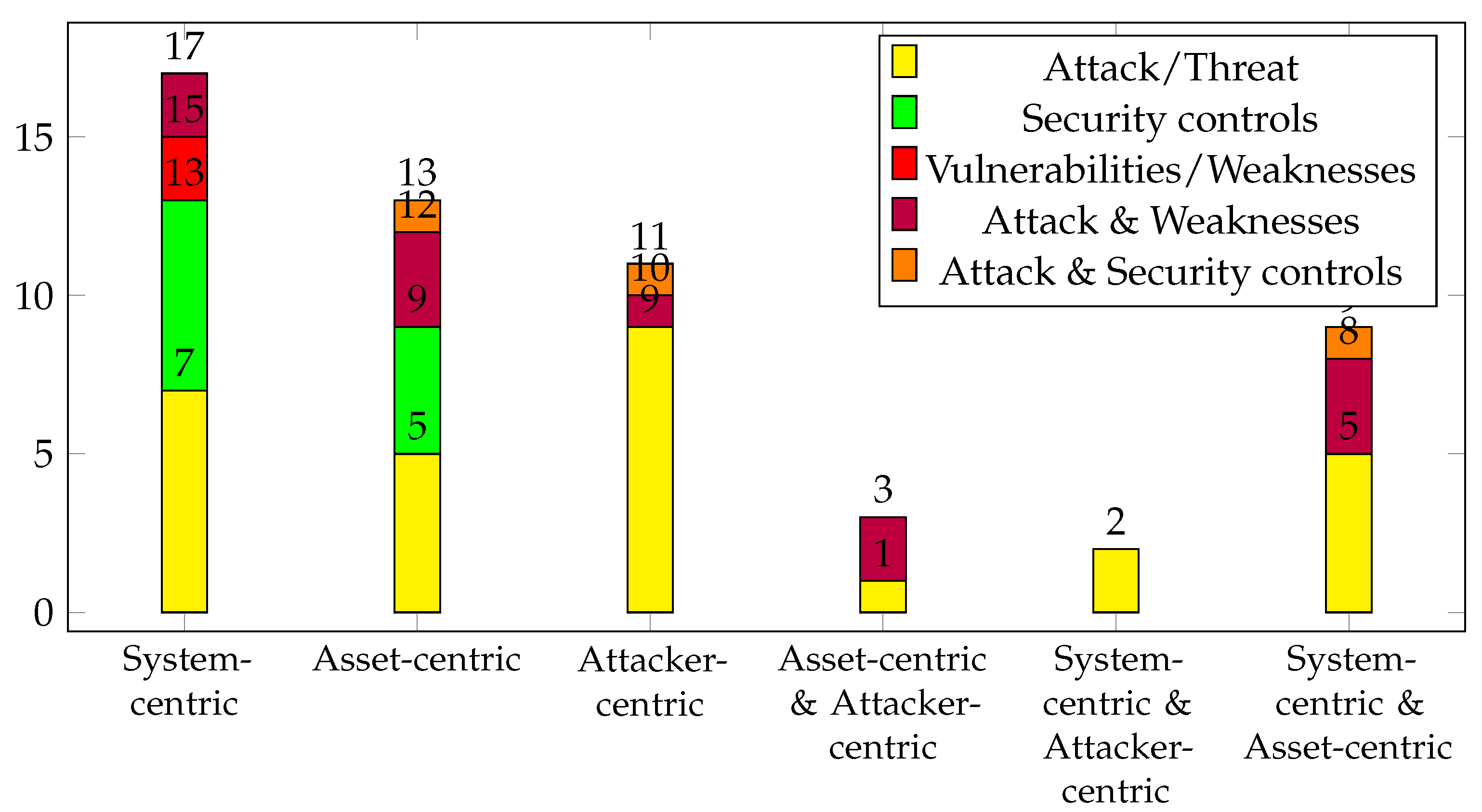
4.2.2. RQ1.2—Which Security Aspects (e.g., Attacks, Threats, Vulnerabilities, and Security Controls) Were Focused on?
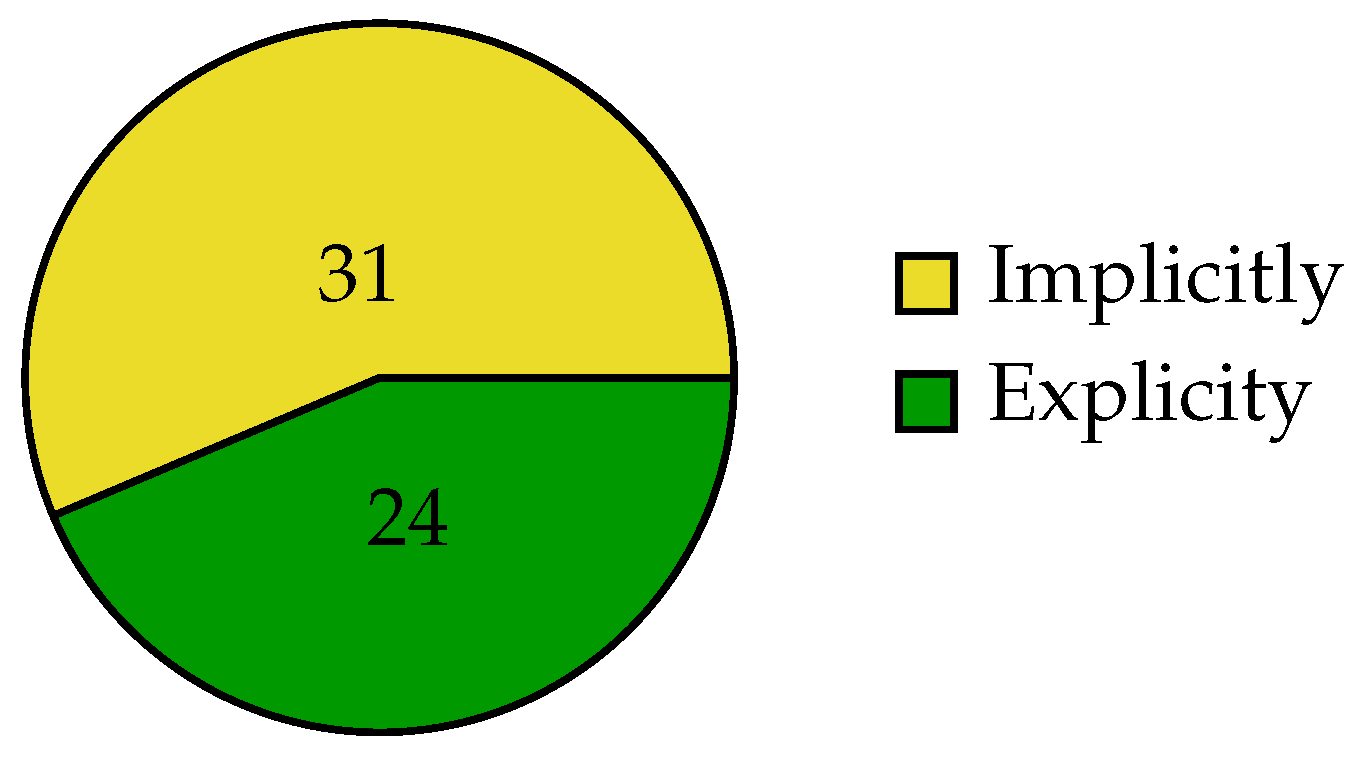
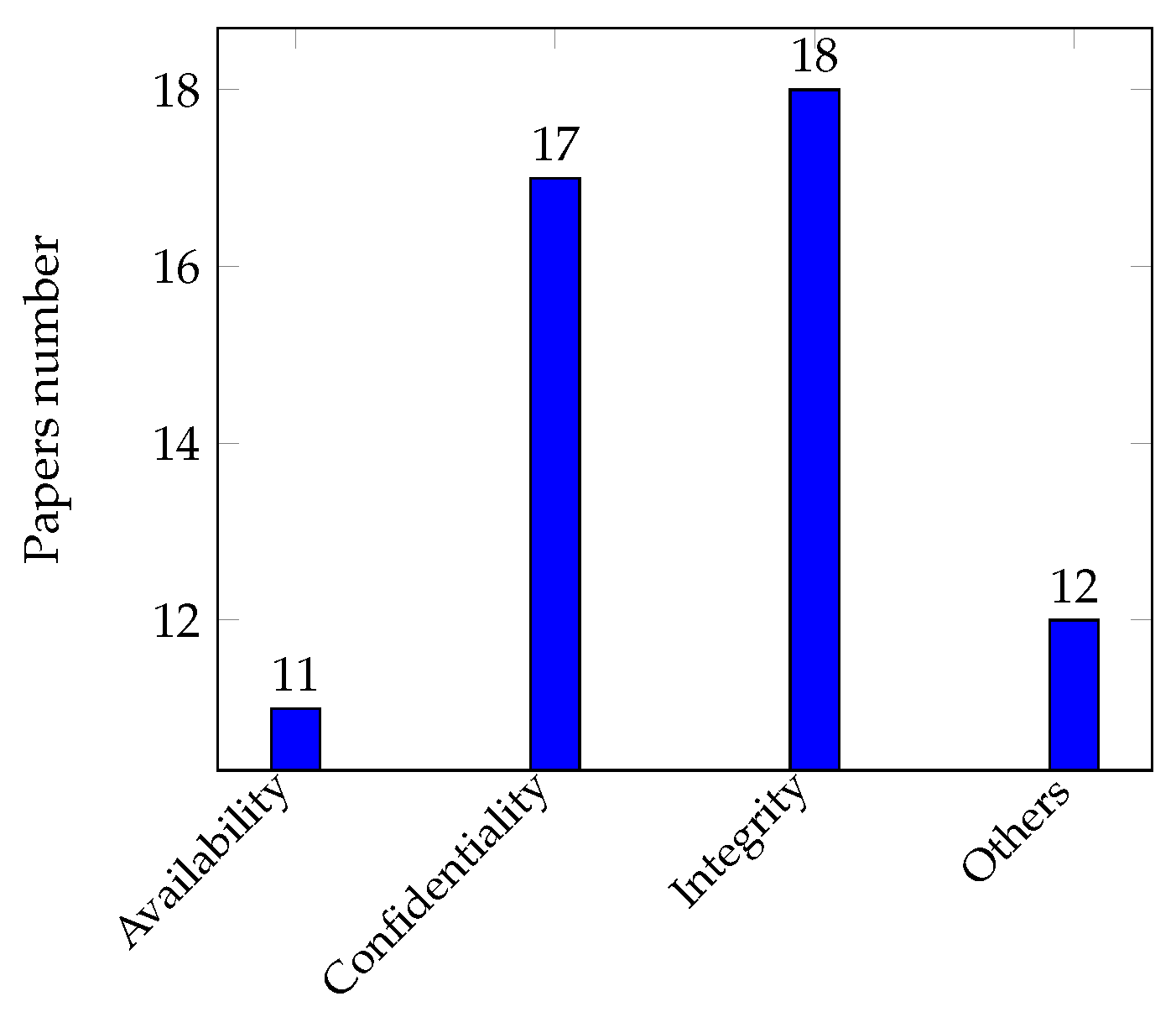
4.2.3. RQ1.3—Which Security Objectives (CIA, etc.) Were Addressed?
4.2.4. RQ1.4—Which Other System Requirements Were Considered While Integrating Security?
4.3. RQ2: Security-by-Design Methodology Characteristics
4.3.1. RQ2.1—What Are the Steps That Constitute Each Security-by-Design Methodology?
4.3.2. RQ2.2—Which Security Integration Mechanism Is Used by the Methodology?
- Merging: The base workflow is modified to incorporate (merge) a set of security steps from the security workflow.
- Coupling: The security and base workflows are independent but interconnected through connection points, with each utilizing and feeding back into the other.
- Triggering: In this mechanism, a single connection point to the base workflow triggers the security workflow. After completion, the results can, but do not have to, be returned to the base workflow.
- Harmonization: In this mechanism, the security workflow is adapted to be as similar as possible to the base workflow; i.e., the two workflows are harmonized.
4.3.3. RQ2.3—What Element Did the Methodology Focus on to Consider Security?
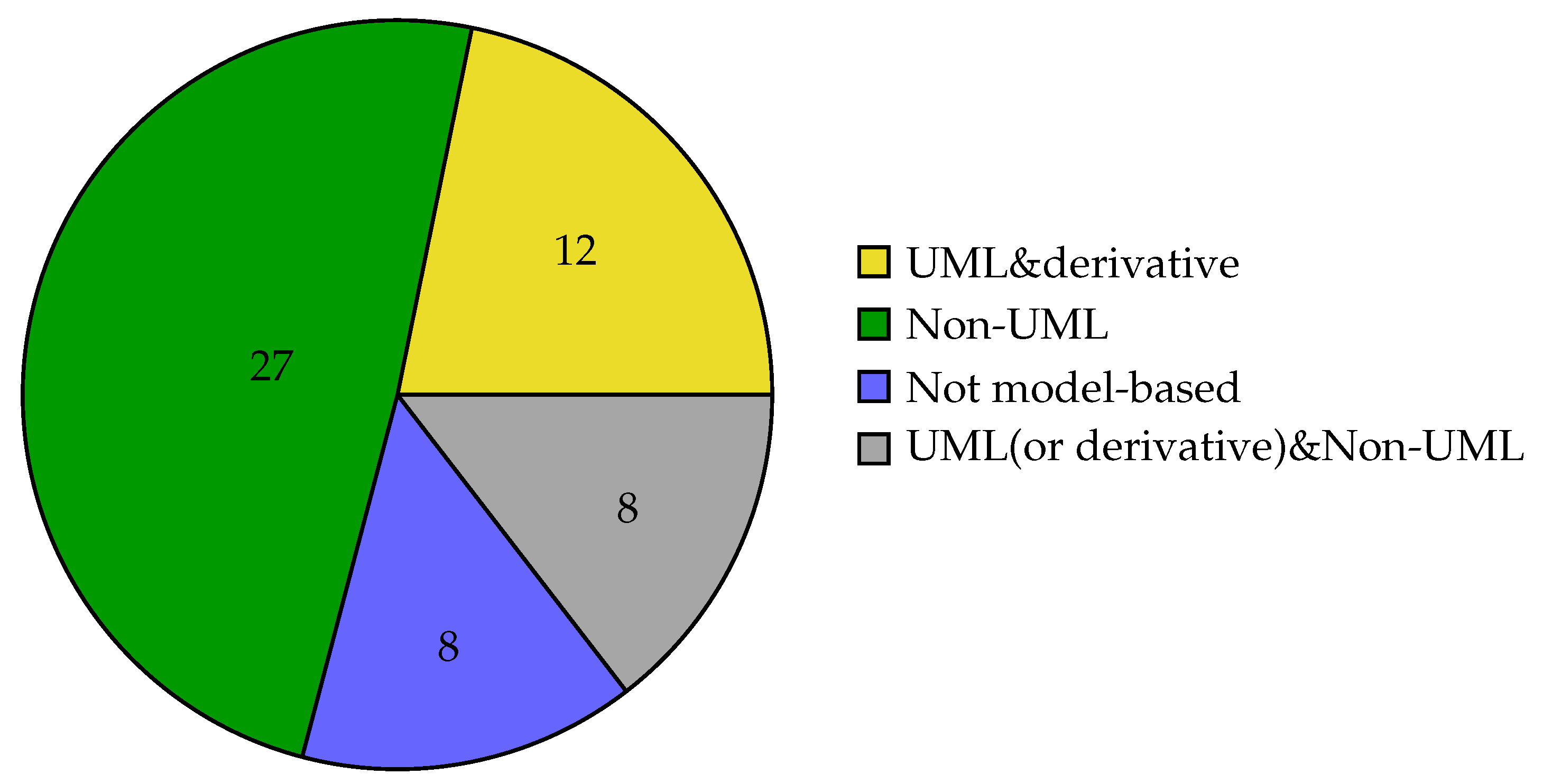
4.3.4. RQ2.4—What Are the Methodology Models and How Were They Modeled?
5. Open Issues and Research Directions
5.1. Development Lifecycle Phases Beyond the Design Phase Are Not Sufficiently Considered
5.2. Vulnerabilities/Flaws Are Not Sufficiently Considered in Security Analysis
5.3. Security Properties/Objectives Are Not Often Very Explicit
5.4. Conflicts Related to Security and Other System Requirements Are Not Well Addressed
5.5. Challenges in Security-by-Design Methodologies: Incomplete Standard Integration, Insufficient Technical Detail, Limited Formal Verification, Low Automation, and Neglect of Security Engineering Principles
5.6. Lack of Independent and Influential Security-by-Design Methodologies
5.7. Lack of Joint Consideration of Different Perspectives
6. Threats to Validity
6.1. Construct Validity
6.2. Internal Validity
6.3. Conclusion Validity
6.4. External Validity
7. Conclusions and Future Work
- RQ1: How is the security-by-design paradigm defined? The “security-by-design” paradigm, in its most effective form, advocates for the integration of security measures from the very inception of the development lifecycle. However, the common focus is too often placed exclusively on the design phase, a practice that, while crucial, is insufficient on its own. New and significant vulnerabilities can, and often do, emerge during the subsequent implementation and deployment phases. Therefore, a truly robust security-by-design methodology must extend its reach beyond mere architectural planning to permeate every stage of development. It also tends to focus more on addressing potential attacks and threats rather than underlying system vulnerabilities, which can lead to gaps in system resilience and disruption prevention from both known and unknown threats. Security objectives are frequently considered implicitly, with a greater emphasis on integrity and confidentiality over availability, despite the latter being critical in many systems. Additionally, while some studies recognize the need to balance security with other system requirements such as safety and performance, these conflicts are not adequately resolved. To improve the security-by-design approach, it should encompass the entire development lifecycle, prioritize addressing vulnerabilities, clearly define security objectives, and effectively manage conflicts that may arise with other system requirements.
- RQ2: What are the characteristics of a security-by-design methodology? A security-by-design methodology emphasizes building cybersecurity and safety into systems from the outset by following several core principles. Many approaches align with established domain standards, providing structured evaluation frameworks that integrate safety and security requirements. However, simulation and formal verification, while beneficial for understanding system behavior and ensuring rigor, are rarely implemented. Additionally, these methodologies often lack technical depth, which limits their applicability to complex CPSs with diverse needs. Manual intervention is still common, as automation tools are underutilized, suggesting an opportunity to streamline processes and lessen dependency on human expertise. Security solutions also tend to prioritize analysis over practical integration, leaving mitigation strategies underdeveloped. Lastly, many methodologies rely on “Merging” or “Triggering” mechanisms independently, though combining these could better address both system-wide and component-level security, ultimately enhancing decision-making in complex systems.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Selected Studies
| S1 | Saadatmand, Mehrdad, and Thomas Leveque. “Modeling security aspects in distributed real-time component-based embedded systems.” 2012 Ninth International Conference on Information Technology-New Generations. IEEE, 2012. |
| S2 | J. F. Ruiz, R. Harjani, A. Mana, V. Desnitsky, I. Kotenko and A. Chechulin, “A Methodology for the Analysis and Modeling of Security Threats and Attacks for Systems of Embedded Components,” 2012 20th Euromicro International Conference on Parallel, Distributed and Network-based Processing, Munich, Germany, 2012, pp. 261–268, |
| S3 | Vasilevskaya, Maria, et al. “Integrating security mechanisms into embedded systems by domain-specific modelling.” Security and Communication Networks 7.12 (2014): 2815–2832. |
| S4 | R. Oates, D. Foulkes, G. Herries and D. Banham, “Practical extensions of safety critical engineering processes for securing industrial control systems,” 8th IET International System Safety Conference incorporating the Cyber Security Conference 2013, Cardiff, 2013, pp. 1–6, |
| S5 | William Young and Nancy Leveson, “Systems thinking for safety and security”, 29th Annual Computer Security Applications Conference (ACSAC ’13). Association for Computing Machinery, New York, NY, USA, 1–8, |
| S6 | A. Wasicek, P. Derler and E. A. Lee, “Aspect-oriented modeling of attacks in automotive Cyber-Physical Systems,” 2014 51st ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 2014, pp. 1–6, |
| S7 | I. Stierand, S. Malipatlolla, S. Fröschle, A. Stühring and S. Henkler, “Integrating the Security Aspect into Design Space Exploration of Embedded Systems,” 2014 IEEE International Symposium on Software Reliability Engineering Workshops, Naples, Italy, 2014, pp. 371–376, |
| S8 | P. Mundhenk, S. Steinhorst, M. Lukasiewycz, S. A. Fahmy and S. Chakraborty, “Security analysis of automotive architectures using probabilistic model checking,” 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 2015, pp. 1–6, |
| S9 | C. Schmittner, Z. Ma and E. Schoitsch, “Combined safety and security development lifecylce,” 2015 IEEE 13th International Conference on Industrial Informatics (INDIN), Cambridge, UK, 2015, pp. 1408–1415. |
| S10 | Sabaliauskaite, Giedre and Aditya P. Mathur. “Aligning Cyber-Physical System Safety and Security.” CSDM Asia (2014), |
| S11 | S. Marrone, R. J. Rodríguez, R. Nardone, F. Flammini, V. Vittorini, “On synergies of cyber and physical security modelling in vulnerability assessment of railway systems, Computers &Electrical Engineering, Volume 47, 2015 |
| S12 | A. Motii, B. Hamid, A. Lanusse and J. -M. Bruel, ”Guiding the Selection of Security Patterns for Real-Time Systems,“ 2016 21st International Conference on Engineering of Complex Computer Systems (ICECCS), Dubai, United Arab Emirates, 2016, pp. 155–164, |
| S13 | S. Cong, M. Jianfeng and Y. Qingsong, ”On the Architecture and Development Life Cycle of Secure Cyber-Physical Systems,“ in Journal of Communications and Information Networks, vol. 1, no. 4, pp. 1–21, Dec. 2016, |
| S14 | J. -P. Nicklas, M. Mamrot, P. Winzer, D. Lichte, S. Marchlewitz and K. -D. Wolf, “Use case based approach for an integrated consideration of safety and security aspects for smart home applications,” 2016 11th System of Systems Engineering Conference (SoSE), Kongsberg, Norway, 2016, pp. 1–6, |
| S15 | C. Bernardeschi, M. Di Natale, G. Dini, D. Varano, “Modeling and generation of secure component communications in AUTOSAR”, |
| S16 | Cui, Jin, and Giedre Sabaliauskaite. “On the alignment of safety and security for autonomous vehicles.” IARIA CYBER, Barcelona, Spain (2017). |
| S17 | Tan, Benjamin, Morteza Biglari-Abhari, and Zoran Salcic. “An automated security-aware approach for design of embedded systems on MPSoC.” ACM Transactions on Embedded Computing Systems (TECS) 16.5s (2017): 1–20. |
| S18 | Gabriel, Angelito, Juan Shi, and Cagil Ozansoy. “A proposed alignment of the National Institute of Standards and Technology Framework with the funnel risk graph method.” IEEE Access 5 (2017): 12103–12113. |
| S19 | Josyula, Surya Kant, and Daya Gupta. “A new security methodology for internet of things.” 2017 international conference on computing, communication and automation (ICCCA). IEEE, 2017. |
| S20 | Neureiter, Christian, et al. “A concept for engineering smart grid security requirements based on SGAM models.” Computer Science-Research and Development 31 (2016): 65–71. |
| S21 | Bakirtzis, Georgios, et al. “A model-based approach to security analysis for cyber-physical systems.” 2018 Annual IEEE International Systems Conference (SysCon). IEEE, 2018. |
| S22 | Geismann, Johannes, Christopher Gerking, and Eric Bodden. “Towards ensuring security by design in cyber-physical systems engineering processes.” Proceedings of the 2018 international conference on software and system process. 2018. |
| S23 | Mouratidis, Haralambos, and Vasiliki Diamantopoulou. “A security analysis method for industrial Internet of Things.” IEEE Transactions on Industrial Informatics 14.9 (2018): 4093–4100. |
| S24 | Lisova, Elena, et al. “A systematic way to incorporate security in safety analysis.” 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W). IEEE, 2018. |
| S25 | Passerone, Roberto, et al. “A methodology for the design of safety-compliant and secure communication of autonomous vehicles.” IEEE Access 7 (2019): 125022–125037. |
| S26 | Tantawy, Ashraf, Sherif Abdelwahed, and Qian Chen. “Continuous stirred tank reactors: Modeling and simulation for CPS security assessment.” 2019 11th International Conference on Computational Intelligence and Communication Networks (CICN). IEEE, 2019. |
| S27 | Eckhart, Matthias, et al. “Security development lifecycle for cyber-physical production systems.” IECON 2019-45th Annual Conference of the IEEE Industrial Electronics Society. Vol. 1. IEEE, 2019. |
| S28 | Mili, Saoussen, Nga Nguyen, and Rachid Chelouah. “Transformation-based approach to security verification for cyber-physical systems.” IEEE Systems Journal 13.4 (2019): 3989–4000. |
| S29 | Gressl, Lukas, Christian Steger, and Ulrich Neffe. “Consideration of security attacks in the design space exploration of embedded systems.” 2019 22nd Euromicro Conference on Digital System Design (DSD). IEEE, 2019. |
| S30 | Apvrille, Ludovic, and Letitia W. Li. “Harmonizing safety, security and performance requirements in embedded systems.” 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE). IEEE, 2019. |
| S31 | Chattopadhyay, Anupam, Kwok-Yan Lam, and Yaswanth Tavva. “Autonomous vehicle: Security by design.” IEEE Transactions on Intelligent Transportation Systems 22.11 (2020): 7015–7029. |
| S32 | Aigner, Andreas, and Abdelmajid Khelil. “A Semantic Model-based Security Engineering Framework for Cyber-Physical Systems.” 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). IEEE, 2020. |
| S33 | Levshun, Dmitry, et al. “Design and verification of a mobile robot based on the integrated model of cyber-Physical systems.” Simulation modelling practice and theory 105 (2020): 102151. |
| S34 | Tanveer, Awais, Roopak Sinha, and Matthew MY Kuo. “Secure links: secure-by-design communications in IEC 61499 industrial control applications.” IEEE Transactions on Industrial Informatics 17.6 (2020): 3992–4002. |
| S35 | Kern, Matthias, et al. “An architecture-based modeling approach using data flows for zone concepts in industry 4.0.” 2020 IEEE International Symposium on Systems Engineering (ISSE). IEEE, 2020. |
| S36 | Moukahal, Lama J., Mohammad Zulkernine, and Martin Soukup. “Towards a secure software lifecycle for autonomous vehicles.” 2021 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW). IEEE, 2021. |
| S37 | Japs, Sergej, Harald Anacker, and Roman Dumitrescu. “SAVE: Security & safety by model-based systems engineering on the example of automotive industry.” procedia CIRP 100 (2021): 187–192. |
| S38 | Tripathi, Dipty, et al. “Model based security verification of Cyber-Physical System based on Petrinet: A case study of Nuclear power plant.” Annals of Nuclear Energy 159 (2021): 108306. |
| S39 | Suri, Kunal, Gabriel Pedroza, and Patrick Leserf. “Model-Based Approach for Co-optimization of Safety and Security Objectives in Design of Critical Architectures.” Model and Data Engineering: 10th International Conference, MEDI 2021, Tallinn, Estonia, June 21–23, 2021, Proceedings 10. Springer International Publishing, 2021. |
| S40 | Larsen, Martin H., Gerrit Muller, and Satyanarayana Kokkula. ”A Conceptual Model-Based Systems Engineering Method for Creating Secure Cyber-Physical Systems.” INCOSE International Symposium. Vol. 32. 2022. |
| S41 | Escamilla-Ambrosio, Ponciano Jorge, et al. “IoTsecM: a UML/SysML extension for internet of things security modeling.” Ieee Access 9 (2021): 154112–154135. |
| S42 | Aranha, Helder, et al. “Securing the metrological chain in IoT environments: an architectural framework.” 2021 IEEE International Workshop on Metrology for Industry 4.0 & IoT (MetroInd4.0&IoT). IEEE, 2021. |
| S43 | Quamara, Megha, Gabriel Pedroza, and Brahim Hamid. “Formal analysis approach for multi-layered system safety and security co-engineering.” European Dependable Computing Conference. Cham: Springer International Publishing, 2022. |
| S44 | Casola, Valentina, et al. “Designing Secure and Resilient Cyber-Physical Systems: A Model-based Moving Target Defense Approach.” IEEE Transactions on Emerging Topics in Computing (2022). |
| S45 | Mahmoodi, Yasamin, et al. “Security Analysis of Embedded Systems Using Virtual Prototyping.” |
| S46 | Promyslov, Vitaly G., Kirill V. Semenkov, and Georgy V. Promyslov. “Practical Method of the I&C System Security Architecture Design Using Graph Models.” IFAC-PapersOnLine 55.9 (2022): 227–232. |
| S47 | Sion, Laurens, et al. “Towards automated security design flaw detection.” 2019 34th IEEE/ACM International Conference on Automated Software Engineering Workshop (ASEW). IEEE, 2019. |
| S48 | SHAKED, Avi. A model-based methodology to support systems security design and assessment. Journal of Industrial Information Integration, 2023, vol. 33, p. 100465. |
| S49 | LISBOA MALAQUIAS, Felipe, GIANTAMIDIS, Georgios, BASAGIANNIS, Stylianos, et al. Towards a Methodology to Design Provably Secure Cyber-physical Systems. ACM SIGAda Ada Letters, 2023, vol. 43, no 1, p. 94–99. |
| S50 | KHALIL, Shaymaa Mamdouh, BAHSI, Hayretdin, OCHIENG’DOLA, Henry, et al. Threat modeling of cyber-physical systemsa case study of a microgrid system. Computers & Security, 2023, vol. 124, p. 102950. |
| S51 | GOWDANAKATTE, Shwetha, RAY, Indrakshi, et ABDELGAWAD, Mahmoud. Model based risk assessment and risk mitigation framework for cyber-physical systems. In : 2023 5th IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPSISA). IEEE, 2023. p. 203–212. |
| S52 | FÖLDVÁRI, András, BRANCATI, Francesco, et PATARICZA, András. Preliminary risk and mitigation assessment in cyber-physical systems. In : 2023 53rd Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W). IEEE, 2023. p. 267–274. |
| S53 | AMIRI, Amirali, STEINDL, Gernot, GORTON, Ian, et al. Integrated safety and security by design in the IT/OT convergence of industrial systems: A graph-based approach. In : 2024 IEEE International Conference on Software Services Engineering (SSE). IEEE, 2024. p. 123–129. |
| S54 | FISCHER, Alexander, TOLVANEN, Juha-Pekka, et KOLAGARI, Ramin Tavakoli. Automotive Cybersecurity Engineering with Modeling Support. In : 2024 19th Conference on Computer Science and Intelligence Systems (FedCSIS). IEEE, 2024. p. 319–329. |
| S55 | HOSSEINI, Ali M., SAUTER, Thilo, et KASTNER, Wolfgang. Integrating Security into Industrial Control System Architecture Based on IEC 42010. In : 2024 IEEE 29th International Conference on Emerging Technologies and Factory Automation (ETFA). IEEE, 2024. p. 1–8. |
References
- Short History of Manufacturing: From Industry 1.0 to Industry 4.0. 2021. Available online: https://kfactory.eu/the-industrial~-revolution-short-history-of-manufacturing (accessed on 16 June 2025).
- Stouffer, K.; Pease, M.; Tang, C.; Zimmerman, T.; Pillitteri, V.; Lightman, S.; Hahn, A.; Saravia, S.; Sherule, A.; Thompson, M. Guide to Operational Technology (OT) Security: Technical Report NIST Special Publication (SP) 800-82 Rev. 3; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023. [Google Scholar] [CrossRef]
- Fluchs, S.; Tasten, E.; Mertens, M.; Horch, A.; Drath, R.; Fay, A. Security by Design Integration Mechanisms for Industrial Control Systems. In Proceedings of the IECON 2022—48th Annual Conference of the IEEE Industrial Electronics Society, Brussels, Belgium, 17–20 October 2022; pp. 1–6, ISSN 2577-1647. [Google Scholar] [CrossRef]
- Ani, U.P.D.; He, H.M.; Tiwari, A. Review of cybersecurity issues in industrial critical infrastructure: Manufacturing in perspective. J. Cyber Secur. Technol. 2017, 1, 32–74. [Google Scholar] [CrossRef]
- Cheminod, M.; Durante, L.; Valenzano, A. Review of Security Issues in Industrial Networks. IEEE Trans. Ind. Inform. 2013, 9, 277–293. [Google Scholar] [CrossRef]
- European Commission. Cyber Resilience Act|Shaping Europe’s Digital Future. 2024. Available online: https://digital-strategy.ec.europa.eu/en/policies/cyber-resilience-act (accessed on 16 June 2025).
- Nguyen, P.H.; Ali, S.; Yue, T. Model-based security engineering for cyber-physical systems: A systematic mapping study. Inf. Softw. Technol. 2017, 83, 116–135. [Google Scholar] [CrossRef]
- Geismann, J.; Bodden, E. A systematic literature review of model-driven security engineering for cyber–physical systems. J. Syst. Softw. 2020, 169, 110697. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Technical Report EBSE 2007-01; Keele University: Newcastle, UK; Durham University: Durham, UK, 2007. [Google Scholar]
- Petersen, K.; Vakkalanka, S.; Kuzniarz, L. Guidelines for conducting systematic mapping studies in software engineering: An update. Inf. Softw. Technol. 2015, 64, 1–18. [Google Scholar] [CrossRef]
- Elmarkez, A.; Kesraoui-Mesli, S.; Oquendo, F.; Berruet, P. Insights on Security-by-Design of Cyber-Physical Production Systems: A Systematic Mapping. In Proceedings of the CIGI QUALITA MOSIM 2025—Conference on Modeling, Optimisation and Simulation, Troyes, France, 8–10 July 2025. [Google Scholar]
- Lee, E.A. Computing needs time. Commun. ACM 2009, 52, 70–79. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security—A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Kumar, C. Cyber-physical Systems (CPS) Security: State of the Art and Research Opportunities for Information Systems Academics. Commun. Assoc. Inf. Syst. 2020, 47. [Google Scholar] [CrossRef]
- Kayan, H.; Nunes, M.; Rana, O.; Burnap, P.; Perera, C. Cybersecurity of Industrial Cyber-Physical Systems: A Review. ACM Comput. Surv. 2022, 54, 1–35. [Google Scholar] [CrossRef]
- Bouskela, D.; Falcone, A.; Garro, A.; Jardin, A.; Otter, M.; Thuy, N.; Tundis, A. Formal requirements modeling for cyber-physical systems engineering: An integrated solution based on FORM-L and Modelica. Requir. Eng. 2022, 27, 1–30. [Google Scholar] [CrossRef]
- Glinz, M. On Non-Functional Requirements. In Proceedings of the 15th IEEE International Requirements Engineering Conference (RE 2007), Delhi, India, 15–19 October 2007; pp. 21–26, ISSN 2332-6441. [Google Scholar] [CrossRef]
- Tripathi, D.; Singh, L.K.; Tripathi, A.K.; Chaturvedi, A. Model based security verification of Cyber-Physical System based on Petrinet: A case study of Nuclear power plant. Ann. Nucl. Energy 2021, 159, 108306. [Google Scholar] [CrossRef]
- Ross, R.; Pillitteri, V.; Graubart, R.; Bodeau, D.; McQuaid, R. Developing Cyber-Resilient Systems: A Systems Security Engineering Approach; Technical Report NIST Special Publication (SP) 800-160 Vol. 2 Rev. 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021. [Google Scholar] [CrossRef]
- Ross, R.; Winstead, M.; McEvilley, M. Engineering Trustworthy Secure Systems; Technical Report NIST Special Publication (SP) 800-160 Vol. 1 Rev. 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2022. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. Standards for Security Categorization of Federal Information and Information Systems; Technical Report Federal Information Processing Standard (FIPS) 199; U.S. Department of Commerce: Gaithersburg, MD, USA, 2004. [CrossRef]
- DoD Modeling and Simulation (M&S) Glossary. Available online: https://apps.dtic.mil/sti/citations/ADA349800 (accessed on 16 June 2025).
- Modeling Language (Glossary)—SEBoK. Available online: https://sebokwiki.org/wiki/Modeling_Language_(glossary) (accessed on 16 June 2025).
- Nguyen, P.H.; Kramer, M.; Klein, J.; Traon, Y.L. An extensive systematic review on the Model-Driven Development of secure systems. Inf. Softw. Technol. 2015, 68, 62–81. [Google Scholar] [CrossRef]
- Lun, Y.Z.; D’Innocenzo, A.; Malavolta, I.; Benedetto, M.D.D. Cyber-Physical Systems Security: A Systematic Mapping Study. arXiv 2016, arXiv:1605.09641. [Google Scholar]
- Uzunov, A.V.; Fernandez, E.B.; Falkner, K. Engineering Security into Distributed Systems: A Survey of Methodologies; Verlag der Technischen Universität Graz: Graz, Austria, 2012. [Google Scholar] [CrossRef]
- Kriaa, S.; Pietre-Cambacedes, L.; Bouissou, M.; Halgand, Y. A survey of approaches combining safety and security for industrial control systems. Reliab. Eng. Syst. Saf. 2015, 139, 156–178. [Google Scholar] [CrossRef]
- Huang, S.; Poskitt, C.M.; Shar, L.K. Security Modelling for Cyber-Physical Systems: A Systematic Literature Review. arXiv 2024, arXiv:2404.07527. [Google Scholar] [CrossRef]
- Mashkoor, A.; Egyed, A.; Wille, R.; Stock, S. Model-driven engineering of safety and security software systems: A systematic mapping study and future research directions. J. Softw. Evol. Process. 2023, 35, e2457. [Google Scholar] [CrossRef]
- Harkat, H.; Camarinha-Matos, L.M.; Goes, J.; Ahmed, H.F.T. Cyber-physical systems security: A systematic review. Comput. Ind. Eng. 2024, 188, 109891. [Google Scholar] [CrossRef]
- Del-Real, C.; De Busser, E.; van den Berg, B. Shielding software systems: A comparison of security by design and privacy by design based on a systematic literature review. Comput. Law Secur. Rev. 2024, 52, 105933. [Google Scholar] [CrossRef]
- Wohlin, C. Guidelines for snowballing in systematic literature studies and a replication in software engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering, London, UK, 13–14 May 2014; pp. 1–10. [Google Scholar] [CrossRef]
- Extracted Data Repository. Available online: https://shorturl.at/Lp0wi (accessed on 16 June 2025).
- Advisory: COVID-19 Exploited by Malicious Cyber Actors. Available online: https://www.ncsc.gov.uk/news/covid-19-exploited-by-cyber-actors-advisory (accessed on 16 June 2025).
- On the Architecture and Development Life Cycle of Secure Cyber-Physical Systems. J. Commun. Inf. Netw. 2016, 1, 1–21. [CrossRef]
- Apvrille, L.; Li, L.W. Harmonizing Safety, Security and Performance Requirements in Embedded Systems. In Proceedings of the 2019 Design, Automation & Test in Europe Conference & Exhibition, Florence, Italy, 25–29 March 2019; pp. 1631–1636, ISSN 1558-1101. [Google Scholar] [CrossRef]
- Mosterman, P.; Zander, J. Cyber-physical systems challenges: A needs analysis for collaborating embedded software systems. Softw. Syst. Model. 2015, 15, 5–16. [Google Scholar] [CrossRef]
- A04 Insecure Design OWASP Top 10:2021. Available online: https://owasp.org/Top10/A04_2021-Insecure_Design/ (accessed on 16 June 2025).
- Konsta, A.M.; Lluch Lafuente, A.; Spiga, B.; Dragoni, N. Survey: Automatic generation of attack trees and attack graphs. Comput. Secur. 2024, 137, 103602. [Google Scholar] [CrossRef]
- Young, W.; Leveson, N. Systems thinking for safety and security. In Proceedings of the 29th Annual Computer Security Applications Conference, New Orleans, LA, USA, 9–13 December 2013; pp. 1–8. [Google Scholar] [CrossRef]
- Ruiz, J.F.; Harjani, R.; Mana, A.; Desnitsky, V.; Kotenko, I.; Chechulin, A. A Methodology for the Analysis and Modeling of Security Threats and Attacks for Systems of Embedded Components. In Proceedings of the 2012 20th Euromicro International Conference on Parallel, Distributed and Network-Based Processing, Munich, Germany, 15–17 February 2012; pp. 261–268, ISSN 2377-5750. [Google Scholar] [CrossRef]








| Related Work | Focus on Security by Design | Consideration of Other Requirements | Focus on CPS |
|---|---|---|---|
| [3] | ✓ | ||
| [24] | ✓ | ||
| [8] | ✓ | ✓ | |
| [7] | ✓ | ✓ | |
| [25] | ✓ | ✓ | |
| [13] | ✓ | ||
| [26] | ✓ | ||
| [27] | ✓ | ||
| [28] | ✓ | ✓ | |
| [29] | ✓ | ✓ | |
| [30] | ✓ | ||
| [31] | ✓ | ||
| This work | ✓ | ✓ | ✓ |
| PICO | Keywords |
|---|---|
| Population | “Abstract”:cps OR “Abstract”:“cyber-physical system” OR “Abstract”: ”CPS” OR “Abstract”: ics OR “Abstract”: “industrial control systems” OR “Abstract”: “industrial control system” OR “Abstract”: IoT OR “Abstract”: “internet of things” OR “Abstract”: “digital twin” OR “Abstract”:“device shadow” OR “Abstract”:“autonomous vehicle” OR “Abstract”: “smart grid” OR “Abstract”: scada OR “Abstract”: “embedded systems” OR “Abstract”: “power grid” OR “Abstract”: “smart car” OR “Abstract”:“aircraft system” OR “Abstract”: “healthcare system” OR “Abstract”:“embedded system” OR “Abstract”:“industry 4.0” |
| Intervention | “Abstract”:“security by design” OR “Abstract”: “secure by design” OR “Abstract”: “secure by construction” OR “Abstract”:“security by construction” OR “Abstract”:“security engineering” OR “Abstract”: “secure engineering” OR “Abstract”: “secure development life-cycle” OR “Abstract”:“security development lifecycle” OR “Abstract”: “engineering security” OR “Abstract”:“secure design” OR “Abstract”:“security-aware” OR (((“Abstract”:“model-based”) OR (“Abstract”:“model-driven”)) AND “Abstract”:security) |
| Venue | Number of Studies | Type |
|---|---|---|
| IEEE Access | 3 | Journal |
| ACM/EDAC/IEEE Design Automation Conference (DAC) | 2 | Conference |
| IEEE International Symposium on Software Reliability Engineering Workshops | 2 | Workshop |
| IEEE Transactions on Industrial Informatics | 2 | Journal |
| International Conference on Cyber-Technologies and Cyber-Systems | 2 | Conference |
| Security Objective | Study ID |
|---|---|
| Availability | S3, S4, S6, S8, S11, S26, S36, S38, S42, S43, and S45 |
| Confidentiality | S1, S3, S7, S8, S11, S15, S19, S26, S29, S30, S31, S34, S36, S41, S42, S44, and S45 |
| Integrity | S3, S6, S7, S8, S15, S17, S19, S26, S29, S30, S31, S34, S36, S38, S41, S42, S43, and S45 |
| Other | S1, S3, S4, S11, S17, S19, S25, S29, S30, S31, S42, and S43 |
| System Requirement | Study ID |
|---|---|
| Functional requirements | S5, S13, S23, S33, S36, S38, and S43 |
| Performance requirements | S1, S7, S12, S17, S25, S29, S30, and S33 |
| Specific quality requirements | S4, S5, S9, S10, S14, S16, S18, S24, S25, S26, S30, S31, S36, S37, S39, S43, S52, and S53 |
| Constraints | S7, S13, S17, S29, S39, S42, and S44 |
| Development Phases | Methodology Steps | Sub-Steps | Frequency | Article IDs |
|---|---|---|---|---|
| Requirements | System requirement establishment | Formalization of the uses needed | 1 | S33 |
| System domain analysis | 1 | S2 | ||
| Specific quality requirement establishment | Risk assessment | 5 | S9, S10, S19, S22, and S30 | |
| Security requirement establishment/ modeling | 14 | S2, S9, S10, S13, S16, S19, S25, S27, S31, S34, S36, S38, S39, S40, and S45 | ||
| Security requirement prioritization | 2 | S19 and S36 | ||
| Anti-requirements/misuse case definition/ modeling | 1 | S22 | ||
| Hazard identification | 3 | S9, S10, and S30 | ||
| Definition of safety requirements | 3 | S10, S16, and S39 | ||
| Design | System modeling | Function modeling | 5 | S3, S12, S30, S35, and S38 |
| Data/control flow | 4 | S5, S46, S47, and S50 | ||
| System components | 21 | S6, S8, S11, S21, S23, S25,S26, S28, S34, S35, S39, S41, S43, S45, S48, S49, S51, S52, S52, S54, and S55 | ||
| Use cases | 1 | S14 | ||
| Task/Resource matrix | 1 | S17 | ||
| System state | 1 | S27 | ||
| System of system | 2 | S1 and S32 | ||
| Building blocks | 1 | S33 | ||
| Black box | 1 | S37 | ||
| Missions | 1 | S43 | ||
| Task | 2 | S7 and S29 | ||
| Design security Analysis | System model annotation (with missing security properties/requirements) | 4 | S1, S3, S15, and S47 | |
| Attack/threat analysis | 19 | S2, S7, S10, S12, S13, S14, S16, S17, S23, S29, S32, S38, S41, S44, S48, S49, S50, S52, and S54 | ||
| Security property/goal/objective analysis | 12 | S2, S3, S6, S7, S8, S19, S23, S25, S42, S43, S53, and S55 | ||
| Security flaw/weakness/vulnerability analysis | 5 | S8, S21, S38, S47, and S51 | ||
| Zone and conduit analysis | 3 | S10, S27, and S35 | ||
| Relevant system task/asset analysis | 10 | S3, S18, S20, S23, S24, S29, S40, S41, S42, and S44 | ||
| Security concept modeling | 11 | S2, S6, S11, S13, S22, S23, S26, S28, S33, S40, and S41 | ||
| Risk estimation | 2 | S20 and S31 | ||
| Attack path/threat prioritization | 1 | S23 | ||
| Security requirement identification/ analysis | 6 | S5, S7, S12, S17, S20, and S53 | ||
| Attack impact analysis | 1 | S17 | ||
| Specific quality requirements concept analysis | System hazard analysis | 3 | S5, S26, and S37 | |
| Identification of security risks/threats causing system hazards | 3 | S4, S24, and S26 | ||
| Safety property modeling | 1 | S14 | ||
| Safety mitigation definition/integration | 2 | S10 and S30 | ||
| Harmonization/consolidation/alignment of safety and security and/or performance | 5 | S4, S9, S10, S14, and S30 | ||
| Constraint analysis | 3 | S13, S19, S42, and S52 | ||
| Performance analysis | Design space exploration according to performance and security | 4 | S7, S12, S29, and S30 | |
| Secure system synthesis | Security mitigation selection and/or integration | 27 | S1, S3, S6, S10, S13, S16, S17, S18, S22, S23, S25, S26, S27, S30, S31, S32, S34, S36, S38, S40, S41, S42, S44, S45, S46, S53, and S55 | |
| Constraint satisfaction problem | 1 | S39 | ||
| Security policy definition | 2 | S22 and S31 | ||
| Security mitigation selection and its impact analysis | 1 | S19 | ||
| Design verification | Model checking | 1 | S28 | |
| Virtual prototyping | 1 | S45 | ||
| Verification of security policies | 1 | S22 | ||
| Verification that the system is protected against a type and level of attack | 1 | S33 | ||
| Analysis of security and safety properties using theorem proving | 1 | S43 | ||
| Qualitavive analysis | 1 | S38 | ||
| Quantitative analysis | 2 | S11 and S38 | ||
| Planning for implementation and deployment | Planning of operation and maintenance | 1 | S36 | |
| Planning of safety and security validation | 1 | S36 | ||
| Planning of installation and commissioning | 1 | S36 | ||
| Cybersecurity assurance planning | 1 | S36 | ||
| Implementation | Secure development | Security mechanisms implementation | 3 | S19, S22, and S34 |
| Secure/safe hardware/software development | 5 | S9, S16, S27, S36, and S45 | ||
| Security testing | Unit/static/dynamic testing | 4 | S2, S13, S27, and S36 | |
| Verification of security requirements | 1 | S19 | ||
| Simulation/ prototyping | 2 | S23 and S25 | ||
| Vulnerability scanning/fuzzing/penetration testing | 1 | S36 | ||
| Code generation | Security algorithms/components | 2 | S13 and S15 | |
| Secure code automatic generation | 2 | S15 and S30 | ||
| Hardware/platform implementation | Hardware threat specification | 1 | S24 | |
| Security artifact generation | 1 | S24 | ||
| Platform artifact specification | 1 | S24 | ||
| Deployment | Safety and security monitoring and periodic assessment | 4 | S9, S10, S13, and S18 | |
| Incident response | 3 | S18, S27, and S36 | ||
| Security management | 1 | S27 |
| Security Integration Mechanisms | Study ID | Number of Studies |
|---|---|---|
| Merging | S2, S6, S7, S10, S12, S16, S17, S18, S22, S24, S25, S27, S29, S33, S35, S38, S40, S42, S43, S45, S46, S49, S52, S53, and S55 | 25 |
| Triggering | S3, S4, S5, S8, S11, S15, S28, S20, S21, S23, S26, S37, S47, S31, S32, S34, S41, S44, S48, S50, S51, and S54 | 22 |
| Harmonization | S1, S9, S14, S30, and S39 | 5 |
| Coupling | S13, S19, and S36 | 3 |
| Type of Element Being Modeled | The Element Being Modeled | Model Languages Used |
|---|---|---|
| System | System Components | Secure Tropos, continuous-time Markov chain, P&ID, IEC 61499, DSL, Procom, SysML/UML, Ptolemy II, AADL, TOGAF Archimate, and EAST-ADL |
| Function/task | DSL, stochastic Petri net, UML, and task/resource graph | |
| System behavior | State machine diagram | |
| Data | DSL and text | |
| Information flow | Data flow diagram, SysML/UML, and graph | |
| Operation/mission | UML | |
| Security aspects | Threat/attack | Attack tree, Bayesian network-based attack graph (BNAG), text, Ptolemy 2, stochastic petri net, and UML |
| Security mechanisms/ patterns | UML and tree | |
| Safety aspects Requirements | Hazards/failures | Fault tree |
| Safety use cases | SysML (sequence diagram) | |
| Requirements | First-order logic, SysML/UML, and BCI |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Elmarkez, A.; Mesli-Kesraoui, S.; Berruet, P.; Oquendo, F. Security by Design for Industrial Control Systems from a Cyber–Physical System Perspective: A Systematic Mapping Study. Machines 2025, 13, 538. https://doi.org/10.3390/machines13070538
Elmarkez A, Mesli-Kesraoui S, Berruet P, Oquendo F. Security by Design for Industrial Control Systems from a Cyber–Physical System Perspective: A Systematic Mapping Study. Machines. 2025; 13(7):538. https://doi.org/10.3390/machines13070538
Chicago/Turabian StyleElmarkez, Ahmed, Soraya Mesli-Kesraoui, Pascal Berruet, and Flavio Oquendo. 2025. "Security by Design for Industrial Control Systems from a Cyber–Physical System Perspective: A Systematic Mapping Study" Machines 13, no. 7: 538. https://doi.org/10.3390/machines13070538
APA StyleElmarkez, A., Mesli-Kesraoui, S., Berruet, P., & Oquendo, F. (2025). Security by Design for Industrial Control Systems from a Cyber–Physical System Perspective: A Systematic Mapping Study. Machines, 13(7), 538. https://doi.org/10.3390/machines13070538







