1. Introduction
Secure multiparty computation (MPC) is a cryptographic technique, enabling multiple mutually distrustful parties to collaboratively compute a function over their private inputs while ensuring that no party accesses the confidential data of others [
1]. Private comparison, an important branch of MPC, originated from Yao’s millionaire problem [
2], in which two millionaires meeting on the street desire to ascertain who has greater wealth without revealing their actual financial status to one another. Inspired by the millionaire problem, Boudot et al. [
3] introduced a variation called the socialist millionaire problem, where two millionaires determine whether their wealth is equal without disclosing the exact amounts. Thus, solving the millionaire problem (designing privacy comparison protocols) has become a focal point in both classical and quantum cryptography fields.
Lo [
4] pointed out that the inherent impossibility of securely evaluating a two-party function without compromising privacy in a purely bilateral framework is a critical challenge when designing privacy comparison protocols. To address this challenge, researchers have proposed incorporating a semi-honest third party (TP). Acting as a semi-trusted intermediary, the TP facilitates the secure comparison of private inputs but cannot collude with any participating parties.
The security of classical cryptographic protocols, regardless of those for privacy comparison and others, primarily rely on computationally hard mathematical problems such as integer factorization and discrete logarithms, which cannot be efficiently solved using classical computational resources under current conditions. Unfortunately, the emergence of quantum algorithms implemented on quantum computing platforms presents a substantial challenge to the security of classical cryptographic protocols. For example, Shor algorithm [
5] leverages the parallelism of quantum computing and the superposition property of quantum states to reduce the complexity of solving these hard mathematical problems from exponential scale in classical computers to polynomial time. Consequently, once quantum computing matures sufficiently, existing cryptographic systems may become vulnerable. It is imperative to develop quantum-resistance protocols that are resilient to threats posed by quantum algorithms.
In response, researchers have investigated quantum-resistance protocols that integrate classical and quantum mechanics. These include quantum secret sharing [
6,
7,
8], quantum key agreement [
9,
10,
11], quantum secure direct communication [
12,
13,
14,
15], quantum private set intersection [
16,
17] and quantum secure multiparty computation (QMPC) [
18]. The security of these quantum-resistance protocols is based on the principles of quantum mechanics, thereby resisting threats from quantum algorithms.
Quantum private comparison (QPC), a crucial branch of QMPC, enables parties to compare their confidential inputs without revealing each other’s confidential data. In 2009, Yang and Wen [
19] proposed the first QPC protocol, which utilized decoy photons and a one-way hash function to ensure security and confidentiality during the comparison process. Subsequent advancements by Tseng et al. [
20] introduced a Bell-state-based QPC protocol that achieves a qubit efficiency of 50% by utilizing the two-particle entanglement correlation of Bell states. However, this protocol is vulnerable to attacks from the TP attempting to steal participants’ private inputs by exploiting fake Bell states. To enhance its security, two feasible solutions are proposed in Ref. [
21]. Lang [
22] designed the QPC protocol that utilizes the quantum CNOT gate instead of classical exclusive-OR operations to facilitate comparison, but it cannot prevent the disturbance attack implemented by an outsider eavesdropper and the TP’s measuring attack [
23]. Huang et al. [
24] designed the protocol by utilizing the entanglement swapping among three Bell states. Although it can compare three bits in each round, it is difficult to implement with the current technologies due to the effects of decoherence and environmental noise. Lang et al. [
25] developed the protocol using a single Bell state, reducing the states generation switching costs but lowering qubit efficiency to 16.67%. Hou et al. [
26] developed a protocol that encodes private inputs into Bell states using rotation operations, achieving a qubit efficiency of 25%. Similarly, Hou and Wu [
27] employed a comparable method to encode private inputs into Bell states using unitary operations.
Additionally, various quantum states have been explored as carriers of quantum information for transmitting private data. These states include single photons [
28,
29,
30,
31,
32,
33], multi-qubit entangled states [
34,
35,
36,
37,
38,
39], cluster states [
40,
41], and d-level quantum states [
42,
43,
44,
45]. Among these, protocols that utilize simplified quantum resources (e.g., single photons and Bell states) are more feasible and practical than those relying on multi-qubit and d-level quantum states, due to the ease of operation and manipulation of single photons and Bell states. Despite the advantages of Bell states, many existing Bell-state-based QPC protocols face challenges in achieving high qubit efficiency, with many achieving less than 50%.
Inspired by the aforementioned Bell-state-based QPC protocols and with the aim of enhancing their efficiency, we propose a novel approach that utilizes Bell states and Pauli operators to design a QPC protocol. The primary contributions of this work are as follows.
- (1)
By transmitting private information as Pauli operators applied to Bell states, the proposed protocol is more practical and efficient than those that rely on multi-qubit and d-level quantum states.
- (2)
The protocol achieves a qubit efficiency of 50%, requiring one Bell state and a bit of pre-shared key for each bit compared. This efficiency surpasses that of many existing Bell-state-based QPC protocols.
- (3)
By simulating a concrete example using IBM Quantum Qiskit simulator with a designed quantum circuit, the feasibility of the protocol has been validated.
- (4)
Security analyses confirm the protocol’s resilience against both external attacks and insider threats.
The remainder of this paper is organized as follows:
Section 2 introduces the Pauli operators and Bell states used in the protocol.
Section 3 and
Section 4 detail the implementation steps of the proposed protocol and the simulations conducted via IBM Quantum Qiskit simulator, respectively.
Section 5 presents a security analysis of the protocol.
Section 6 discusses the findings, and
Section 7 concludes the paper by summarizing the contributions and exploring potential future directions.
2. Pauli Operators and Bell States
The Pauli-X and Pauli-Z operators [
46] are single-qubit gates that are mathematically defined as
Four Bell states are given by
When applying the operations
and
(where
) to four Bell states, the resulting states are shown in
Table 1.
According to
Table 1, we find that the Bell states remain unchanged if and only if the same operations are performed on both the first and second particles of the Bell states. This property is crucial for the design of the proposed protocol that follows.
3. The Implementation Steps of the Proposed Protocol
The primary objective of the quantum private comparison (QPC) protocol is to determine whether the confidential inputs X and Y, held by Alice and Bob respectively, are equivalent. This comparison is facilitated by a semi-honest third party (TP), which complies with the protocol but is restricted from colluding with either participant. Crucially, the protocol ensures that neither Alice nor Bob leaks any information about their private inputs to each other or external adversaries.
The protocol assumes a noiseless and lossless quantum channel to guarantee the integrity of quantum state transmissions. Prior to execution, Alice and Bob convert their secrets into
n-bit binary strings, denoted as
and
, where
for
. If the length of
X or
Y is shorter than
n, zeros are appended to the higher-order bits. The parameter
n, determined by security requirements, is publicly disclosed to the TP. Subsequently, Alice and Bob employ a quantum key distribution (QKD) protocol (e.g., BB84 [
47]) to establish a shared secret key
, restructured as
, where
for
Protocol Execution:
Step 1. Alice and Bob partition X and Y into groups, where ⌈·⌉ is the ceiling function. If n is odd, a padding bit (0) is added to the final group to ensure uniform group sizes of two bits.
Step 2. The TP prepares Bell states, randomly selected from the set defined in Equations (2)–(5). These states are divided into two sequences: (first particles) and (second particles). For security validation, the TP generates decoy-photon sequences and , composed of randomly chosen states from . All decoy photons in and are inserted into and , forming modified sequences and , which are transmitted to Alice and Bob, respectively.
Step 3. Upon receiving
), Alice (Bob) acknowledges receipt. The TP then discloses the positions and measurement bases (
Z-basis for
;
X-basis for
) of the decoy photons. Alice (Bob) measures the decoy photons in
, obtaining results
, which are returned to the TP for error rate calculation. If the error rate exceeds a predefined threshold
depending on the channel situation (e.g., the distance, etc.) [
48,
49], the protocol is terminated and restarted; otherwise, it proceeds to the next step.
Step 4. After removing decoy photons ( from ), Alice (Bob) applies operations () to ), where and (similar for ). The resulting sequences ) are embedded with new decoy-photon sequence , forming , which are sent to the TP.
Step 5. The TP verifies eavesdropping using the aforementioned decoy-photon method in Step 2. If secure, the TP removes from and performs Bell-state measurements on and . A match between the measurement results and the initially prepared Bell states confirms ; otherwise, .
4. Simulations for Two Concrete Examples
Example 1. Comparison of the equality of the secret integers and .
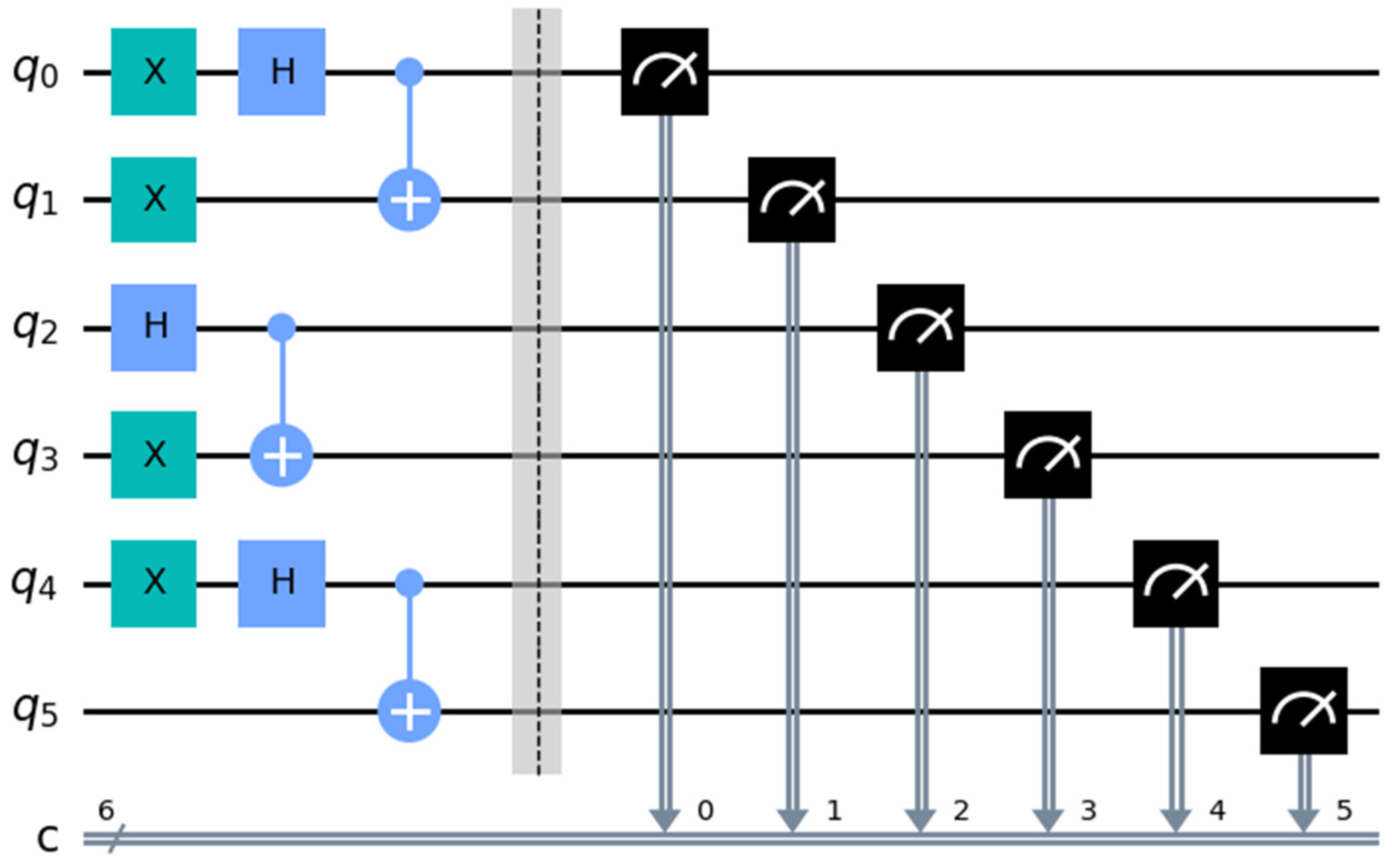
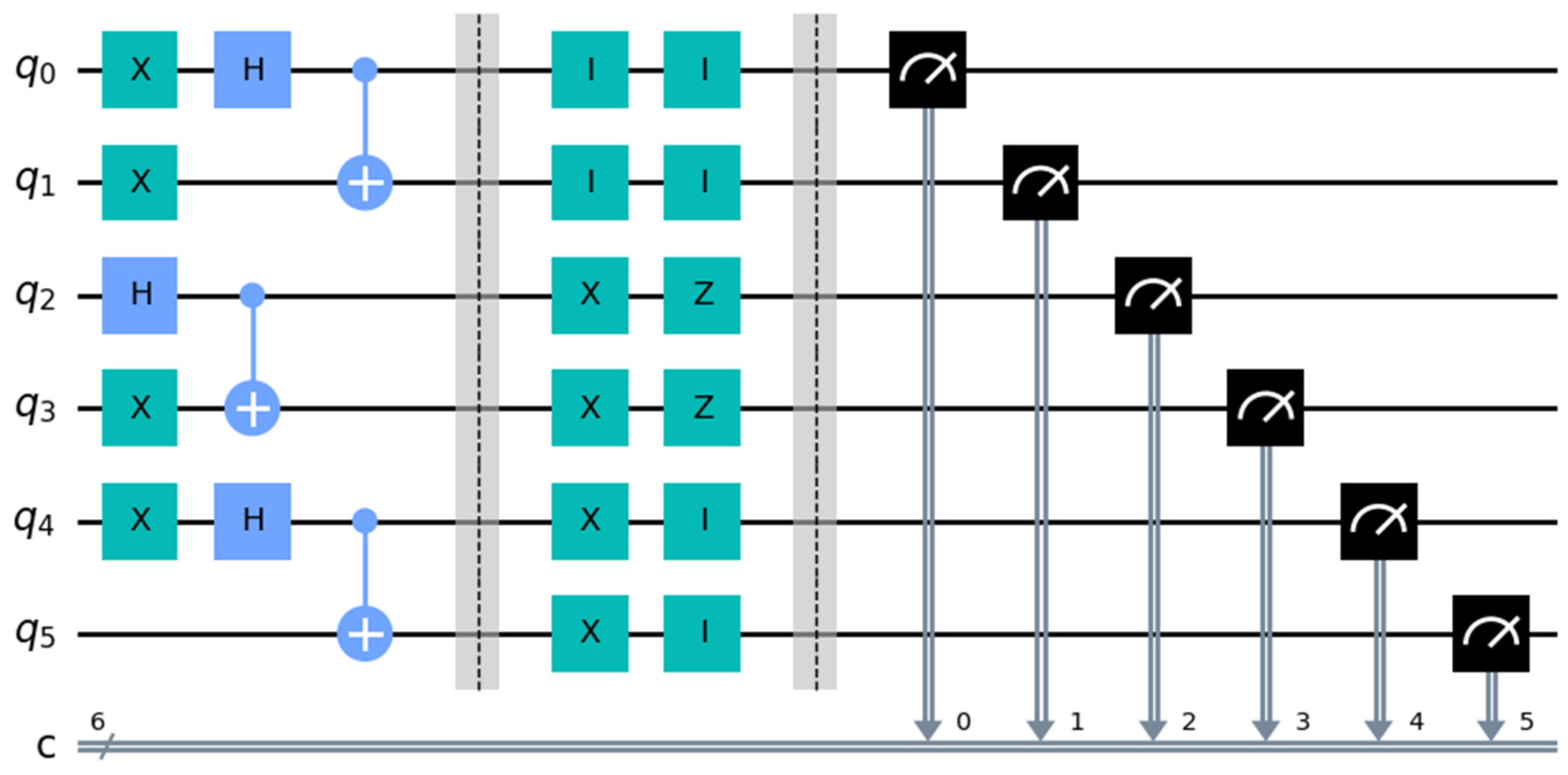
The binary representations of and are and , respectively. The length of the strings is set to 6. Since the length of is shorter than 6, zeros are appended to the higher-order bits, resulting in the restructured binary representation of as . Alice and Bob partition them into three 2-bit groups: and . Let the shared secret key . The initial preparation includes three Bell states: .
The quantum circuit implementation of these three Bell states
is composed of Hadamard and CNOT gates, as shown in
Figure 1. The left half of
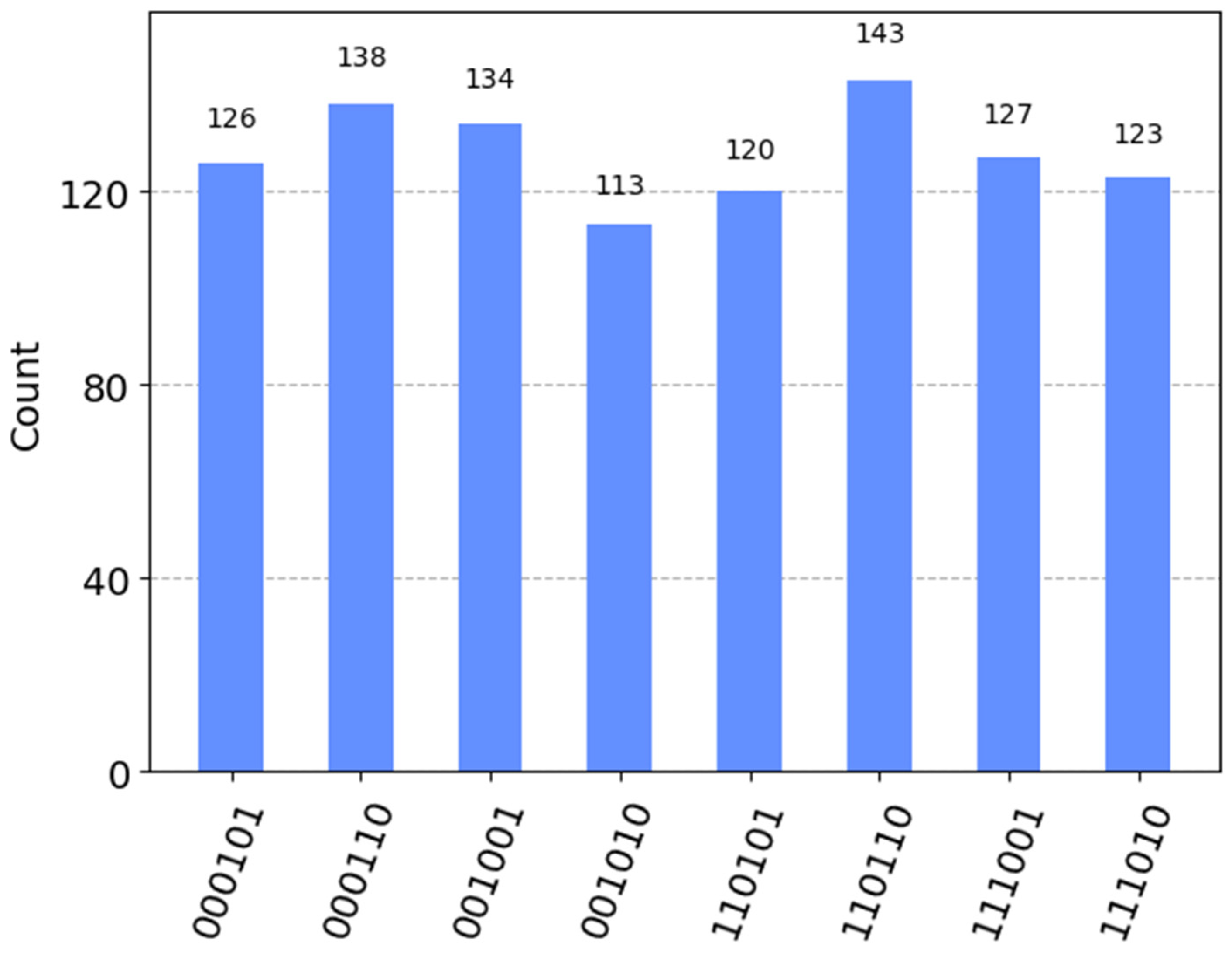
Figure 1 separated by barrier lines is for preparing Bell states, while the right half is for measuring Bell states using Z basis. The measurement results of the three Bell states, obtained using the IBM Quantum Qiskit simulator (Qiskit: 0.44.1; Python: 3.11.4; OS: Windows) with 1024 shots, are displayed in
Figure 2.
Based on
,
and
, the corresponding operations on the three Bell states
are {
X
,
Z
Z, XZ
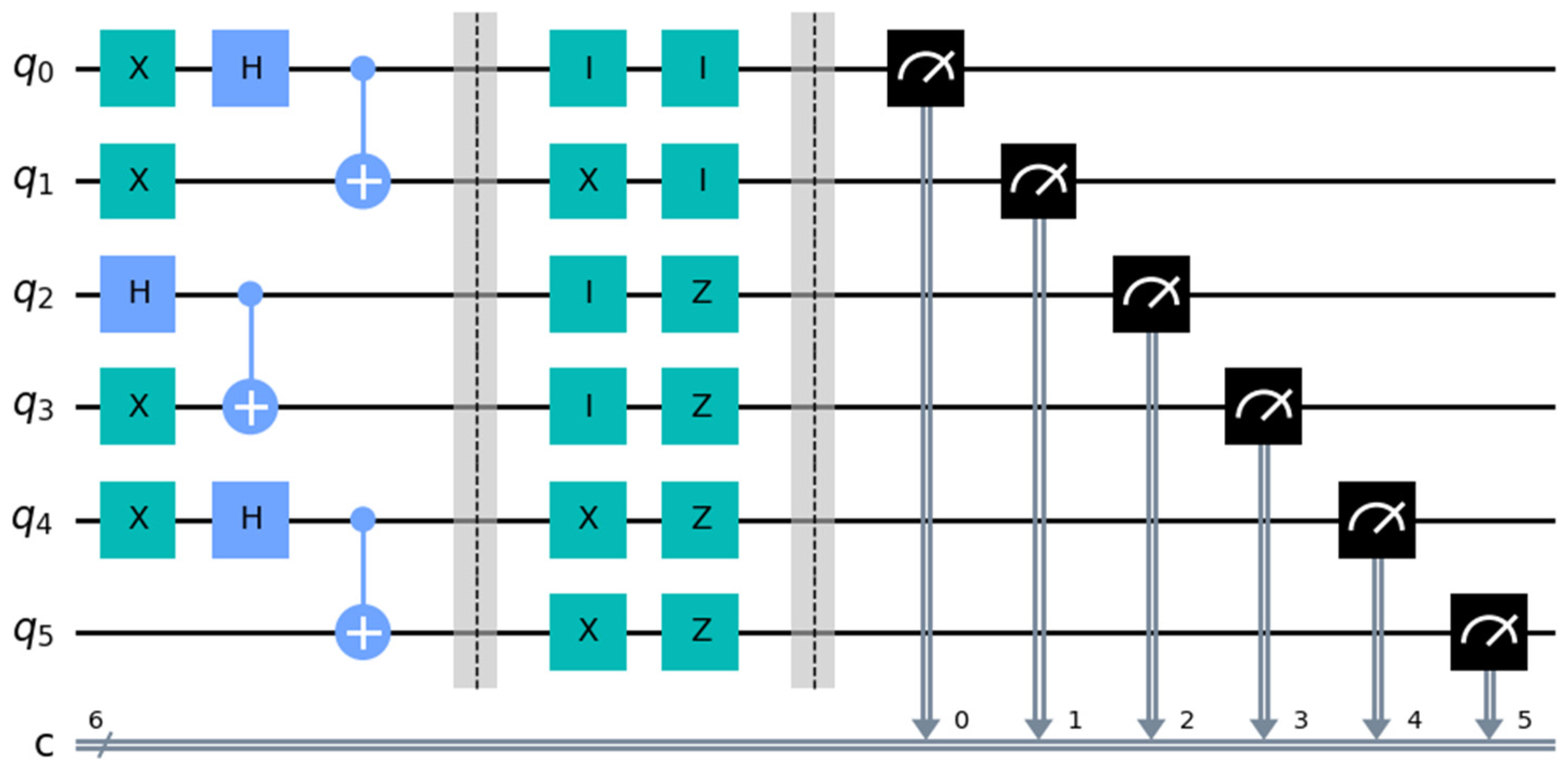
XZ}. The quantum circuit implementation for comparing the equality of the secret integers
and
is shown in
Figure 3, and the results of its probability measurements are presented in
Figure 4.
According to the bar chart in
Figure 4, the measurement results of the computational basis states do not match those in
Figure 2. This indicates that the measurement outcomes do not align with the initially prepared Bell states. Consequently, we can conclude that
.
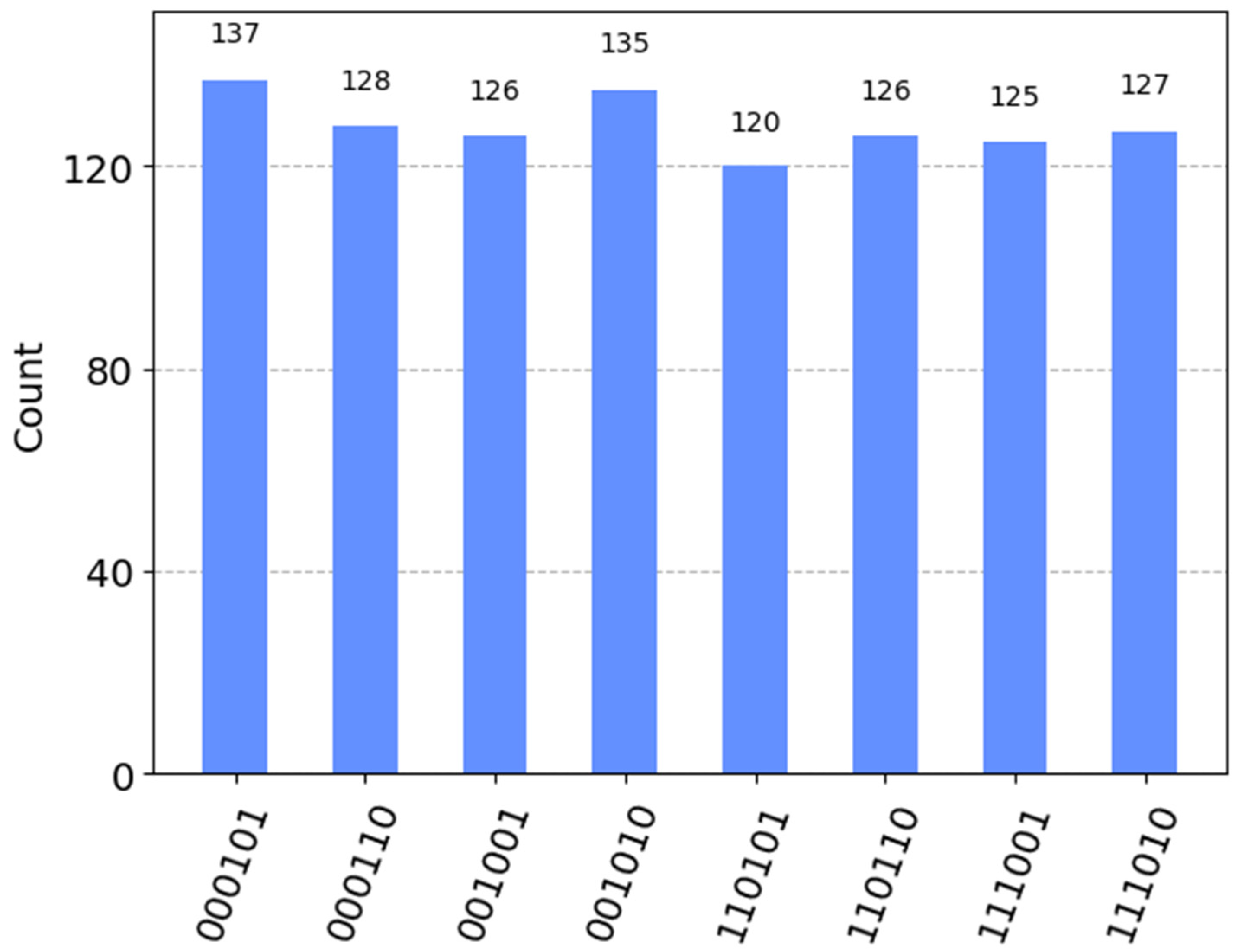
Example 2. Comparison of the equality of the secret integers and .
The binary representations of and are and , respectively. Alice and Bob partition them into three 2-bit groups: and . Let the shared secret key The initial preparation includes three Bell states: .
Based on
,
and
, the corresponding operations on three Bell states
are {
I, XZ
XZ, X
X
}. The quantum circuit implementation for comparing the equality of the secret integers
and
is shown in
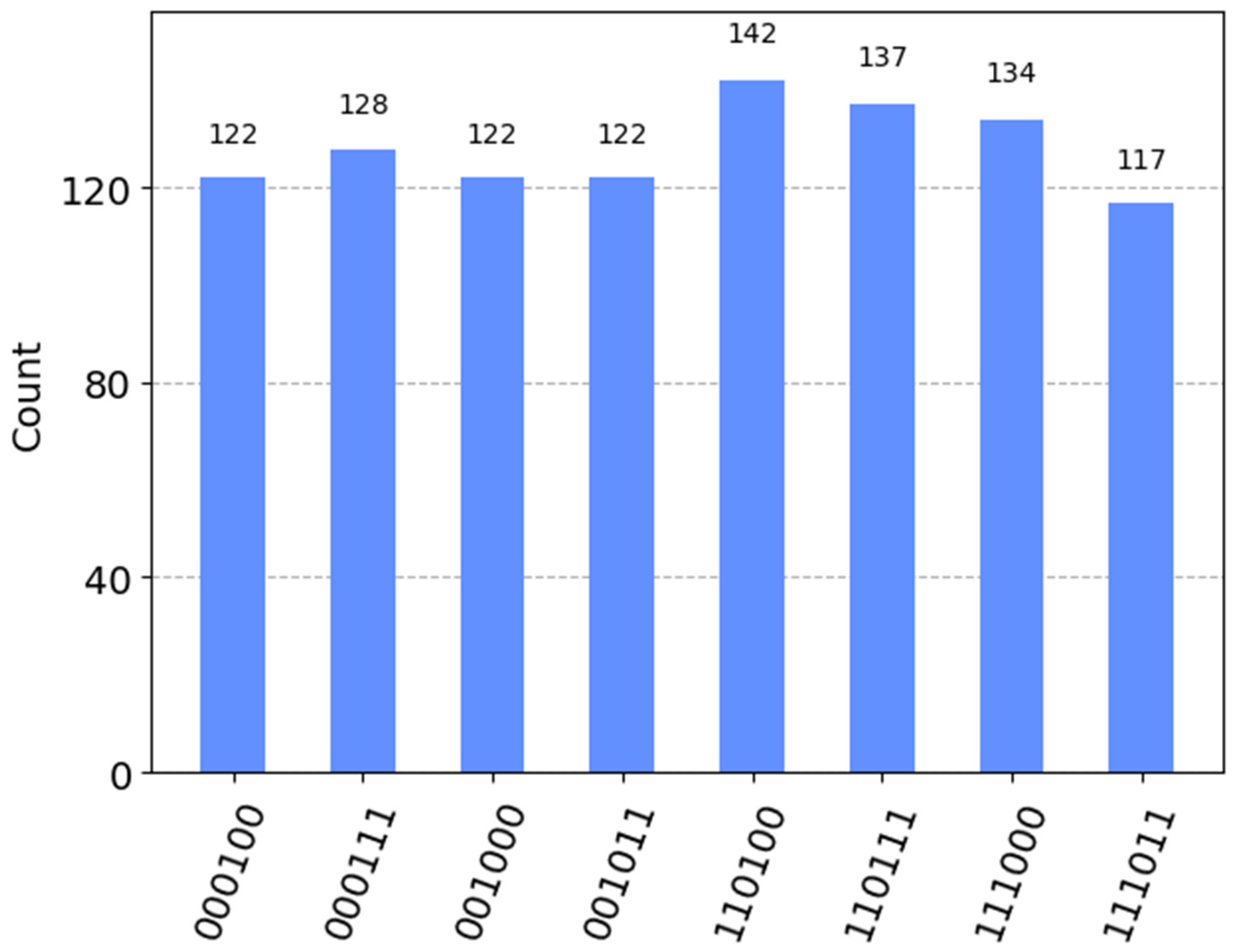
Figure 5, and the results of its probability measurements are presented in
Figure 6.
According to the bar chart in
Figure 6, the measurement results of the computational basis states are identical to those in
Figure 2, although the counts of each computational basis state may differ due to the influence of noise and decoherence. This result indicates that the measurement results align with the initially prepared Bell states. Consequently, we can conclude that
.
Although we utilize two example simulation experiments to demonstrate the feasibility of the proposed protocol, its scalability when comparing multiple bits remains unaffected. It has been reported that Zuchongzhi 3.0 [
50], a superconducting quantum computer prototype comprising 105 qubits and achieving high operational fidelities, was constructed in 2025. As the number of available qubits increases, our protocol can further demonstrate its scalability on actual quantum hardware.
5. Security Analysis
In the execution of the protocol, the entanglement correlation between particles in Bell states is utilized to ensure the security of the particle distribution phase. The insertion of decoy photons into the particles, along with the implementation of quantum key distribution for sharing a pre-shared key, enhances security during the information transfer phase. In this section, we demonstrate that the proposed protocol is resilient against both external and participant attacks.
5.1. External Attacks
When quantum sequences are transmitted through a quantum channel, an external eavesdropper, often referred to as Eve, may employ quantum-attack strategies to compromise the private inputs. The primary quantum attack strategies include intercept-measure-resend [
51], entangle-measure [
52], man-in-the-middle [
53], and quantum Trojan-Horse attacks [
54]. We will analyze whether the proposed protocol is secure against these quantum attack strategies as follows.
5.1.1. Intercept-Measure-Resend Attack
In the proposed QPC protocol, the intercept-measure-resend attack refers to Eve intercepting the quantum sequences and , measuring them with Z-basis or X-basis, and resending the modified sequences to the TP. Unfortunately, this attack faces significant challenges due to the lack of information regarding the inserted positions and measurement bases of the decoy photons. These specific details will be disclosed when the TP receives the sequences.
As an example, consider a decoy photon prepared in the state
. When Eve measures this decoy photon using the Z basis (
), she successfully passes the eavesdropping detection. Conversely, when she measures the decoy photon using the X basis (
), she passes the eavesdropping detection with a probability of 50%, since
and
are equal superpositions of
and
. The choice between the Z basis and the X basis occurs with equal probability, each having a 50% chance. Thus, the probability of choosing the X basis and passing the eavesdropping detection is
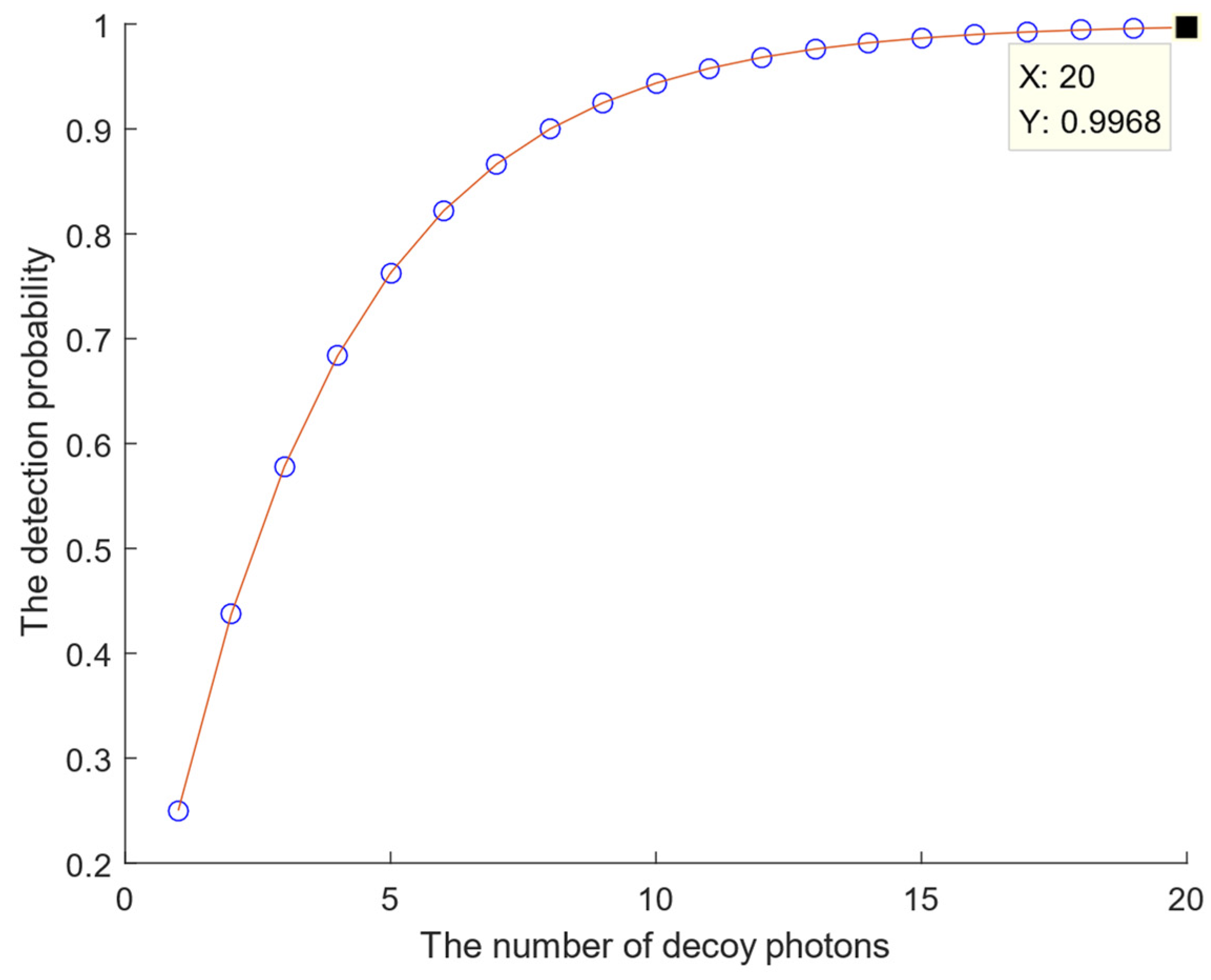
. Consequently, for each decoy photon, Eve has a 3/4 probability of successfully performing the intercept-measure-resend attack. However, for
d decoy photons, the detection probability becomes
. The relationship between the number of decoy photons and the detection probability is illustrated in
Figure 7.
According to the results presented in
Figure 7, when
d = 20, the detection probability reaches 0.9968. However, as the number of decoy photons increases, the detection probability approaches 1. Consequently, Eve will not succeed in executing the intercept-measure-resend attack.
5.1.2. Entangle-Measure Attack
This attack involves Eve intercepting the quantum sequences and , and entangling them with the prepared auxiliary state through a specific unitary operation during the first quantum sequence transmission. During the second quantum sequence transmission, Eve intercepts the quantum sequences and , and performs the specific unitary operation to entangle them with the prepared auxiliary state . Eve can then measure the prepared auxiliary states and to extract private information about the confidential inputs.
During the first quantum sequence transmission, performing
on
and states
and
proceeds as follows:
The states
are four pure states determined by unitary operation
and satisfy the following conditions.
Without loss of generality, we can set
We specify the angles between nonorthogonal vectors as
Furthermore, the probability of Eve not being detected is given as
Therefore, the average detection probability during the first quantum sequence transmission is given by
When
,
comes to the minimum.
During the second quantum sequence transmission, performing
on
and states
and
proceeds as follows:
The states
are four pure states determined by unitary operation
and satisfy the following conditions.
Without loss of generality, we can set
We specify the angles between nonorthogonal vectors as
In the same way, the average detection probability during the second quantum sequence transmission is given by
Reference [
55] pointed out that the optimal incoherent attack by Eve consists of a balanced strategy, where
. Therefore, we have
The mutual information between the participants and Eve is written as
where
h denotes the Shannon binary entropy. From Equation (30), we can infer that
is a monotonic increasing function. The more information Eve seeks to obtain, the greater the detection probability she will induce. Therefore, Eve will not succeed in executing the entangle-measure attack.
5.1.3. Man-in-the-Middle Attack
This attack involves Eve intercepting the sequences containing the encoded private inputs and preparing fake sequences in place of the intercepted sequence. We take intercepting the sequence and preparing as an example. The same method can be applied to analyze the interception of sequence . For security validation, Eve prepares guessed states as decoy photons, denoting the i-th decoy photon as , which corresponds to the j-th qubit in . The j-th qubit of is denoted as . Both and are prepared using basis and . When Alice discloses the measurement basis of , Eve measures using the basis B′ and obtains the results . The probability that is as follows.
- (1)
If and , the probability that is 1.
- (2)
If and , the probability that is 0.
- (3)
If and , the probability that is 1/2.
The detection probability for a decoy photon is
For d decoy photons, the detection probability becomes . When , the detection probability reaches 0.999. However, as the number of decoy photons increases, the detection probability approaches 1. Consequently, Eve will not succeed in executing the man-in-the-middle attack.
5.1.4. Quantum Trojan-Horse Attacks
Quantum Trojan horse attacks are broadly classified into two categories: (1) invisible photon attacks [
36], where an eavesdropper injects undetectable photons into the quantum channel to probe transmitted states, and (2) delayed photon attacks [
38], where photons are strategically delayed to intercept or alter communication. These attacks represent critical vulnerabilities in bidirectional quantum communication systems. The round-trip transmission mechanism inherent to the proposed protocol is particularly susceptible to such threats. To counter these risks, the protocol integrates wavelength filters to eliminate extraneous photon wavelengths and photon-number splitters to detect anomalous photon counts, thereby neutralizing covert eavesdropping attempts.
5.2. Participant Attacks
Participants may maliciously attempt to deduce or alter each other’s private inputs, thereby compromising data confidentiality. A detailed security analysis of insider threats is provided below.
5.2.1. Security Against Attacks from Alice or Bob
In this protocol, Alice and Bob assume symmetrical roles. For generality, we analyze the scenario where Bob acts maliciously to deduce Alice’s secret. Alice encodes her secrets through quantum operations (Pauli-X and Pauli-Z gates) on sequence SA. To reconstruct Alice’s secrets, Bob would require both SA and the transformed sequence UA. However, since no direct quantum channel exists between Alice and Bob, Bob’s only opportunity to obtain SA and UA lies in intercepting transmissions between the TP and Alice. Such interception falls under external eavesdropping, which the protocol neutralizes via the decoy-state method described in Steps 3 and 5. An analogous analysis applies if Alice attempts to compromise Bob’s secrets. Therefore, the protocol’s design inherently safeguards both parties’ secrets against collusion and insider attacks.
5.2.2. Security Against Attacks from TP
While the semi-honest TP might attempt to extract additional information by analyzing intermediate results or deviating from the protocol, its capabilities are limited by the protocol’s architectural constraints. The TP is solely responsible for the initial preparation and distribution of Bell states and subsequent Bell-basis measurements. Although the TP possesses knowledge of the initially prepared and post-transformation Bell states, it cannot reverse-engineer the participants’ secrets (X or Y) from these correlations. Even if the TP hypothetically substitutes Bell states with single photons and measures the returned particles, it lacks knowledge of the shared secret key KAB, which is exclusively held by Alice and Bob. Without KAB, the TP cannot resolve the encoded values X and Y. As a result, the protocol ensures that the TP gains no information about the participants’ secrets beyond the final comparison outcome.
6. Discussion
Qubit efficiency [
29], a critical metric for evaluating quantum resource utilization, quantifies the ratio of classical bits securely compared to the total quantum resources consumed excluding those used for eavesdropping detection. Given that
denotes the number of classical bits compared,
denotes the qubits used for encoding private inputs, and
denotes the bits allocated for pre-shared key, the qubit efficiency is defined as:
In our protocol, ⌈
n/2⌉ Bell states (two-qubit systems) and an
n-bit pre-shared key enable the comparison of
n classical bits, yielding
,
, and
. This results in a qubit efficiency of 50%. A comparative analysis with existing protocols is detailed in
Table 2.
Ref. [
20] utilizes Bell states and XOR operations with single-particle measurements, achieving 50% efficiency. However, it is vulnerable to semi-honest TP attacks via fake Bell states. Ref. [
22] employs Bell states and CNOT gates with Z-basis measurements, attaining 50% efficiency but is susceptible to outsider disturbance attacks and TP measuring attacks. Ref. [
24] relies on entanglement swapping and GHZ-basis measurements, requiring three Bell states and nine pre-shared key bits to compare three classical bits, yielding 20% efficiency. Ref. [
25] uses single Bell states
and XOR operations, achieving only 16.67% efficiency (three Bell states per compared bit). Refs. [
26,
27] incorporate rotation/unitary operations and Bell measurements, achieving 25% efficiency (one Bell state and one pre-shared key bit per compared bit).
Compared with existing Bell-state-based QPC protocols, our protocol offers the following improvements.
- (1)
Our protocol employs Bell states, Pauli-X and Pauli-Z encoding, and Bell measurements without entanglement swapping [
24], further enhancing its feasible implementation.
- (2)
By leveraging a single Bell state and two pre-shared key bits to compare two classical bits, it achieves 50% qubit efficiency—double that of Refs. [
26,
27] and higher than Refs. [
24,
25].
- (3)
Although the proposed protocol has equal qubit efficiency with Refs. [
20,
22], it provides security against the TP’s attack and external eavesdropping through decoy-state validation and the QKD-secured key, while the schemes in Refs. [
20,
22] are not secure and may result in privacy disclosure.
7. Conclusions
In this study, we propose an efficient quantum private comparison (QPC) protocol that harnesses the entanglement properties of Bell states to enable secure and privacy-preserving comparisons of confidential data. Participants encode their private inputs using Pauli-X and Pauli-Z operators on quantum sequences distributed by a semi-honest third party (TP). This design achieves 50% qubit efficiency—a significant improvement over existing Bell-state-based protocols—by utilizing a single Bell state and two pre-shared key bits to compare two classical bits. The protocol’s practicality is validated through experimental simulations on the IBM Quantum Qiskit simulator, confirming its operational feasibility in real-world quantum environments. A comprehensive security analysis demonstrates the protocol’s robustness against both external attacks and insider threats. By integrating Bell-state encoding, QKD-secured keys, and decoy-state validation, our protocol addresses vulnerabilities in prior works, such as susceptibility to fake Bell states and disturbance attacks. Compared to existing QPC schemes, our protocol offers superior efficiency and experimental viability, achieved through minimal quantum resource requirements and simplified operations (no entanglement swapping or GHZ-basis measurements). Future work will extend this framework to noisy intermediate-scale quantum (NISQ) environments, incorporating error mitigation techniques for real-world deployment. Additionally, we aim to design semi-quantum private comparison protocols to reduce reliance on quantum devices, further alleviating resource constraints in practical applications.
Author Contributions
Conceptualization, M.H. and S.Z.; methodology, M.H.; software, M.H.; validation, M.H. and S.Z.; formal analysis, M.H.; investigation, M.H.; resources, M.H.; data curation, M.H.; writing—original draft preparation, M.H.; writing—review and editing, Y.W. and S.Z.; visualization, S.Z.; supervision, S.Z.; project administration, S.Z.; funding acquisition, S.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Research Project of Key R&D Programs in Tibet Autonomous Region (No. XZ202501ZY0094), the National Natural Science Foundation of China (No. 62076042), the National Key Research and Development Plan of China, Key Project of Cyberspace Security Governance (No. 2022YFB3103103), the Key Research and Development Project of Chengdu (No. 2023-XT00-00002-GX), the Key Research and Development Support Program Project of Chengdu (No. 2024-YF05-01227-SN), and the Open Fund of Network and Data Security Key Laboratory of Sichuan Province (Grant No. NDS2024-1).
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Lindell, Y. Secure multiparty computation. Commun. ACM 2020, 64, 86–96. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), Washington, DC, USA, 3–5 November 1982; p. 160. [Google Scholar]
- Boudot, F.; Schoenmakers, B.; Traore, J. A fair and efficient solution to the socialist millionaires’ problem. Discret. Appl. Math. 2001, 111, 23–36. [Google Scholar] [CrossRef]
- Lo, H.K. Insecurity of quantum secure computations. Phys. Rev. A 1997, 56, 1154–1162. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Qin, Y.; Cheng, J.; Ma, J.; Zhao, D.; Yan, Z.; Jia, X.; Xie, C.; Peng, K. Efficient and secure quantum secret sharing for eight users. Phys. Rev. Res. 2024, 6, 033036. [Google Scholar] [CrossRef]
- Shen, A.; Cao, X.Y.; Wang, Y.; Fu, Y.; Gu, J.; Liu, W.-B.; Weng, C.-X.; Yin, H.-L.; Chen, Z.-B. Experimental quantum secret sharing based on phase encoding of coherent states. Sci. China Phys. Mech. Astron. 2023, 66, 260311. [Google Scholar] [CrossRef]
- Senthoor, K.; Sarvepalli, P.K. Theory of communication efficient quantum secret sharing. IEEE Trans. Inf. Theory 2022, 68, 3164–3186. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.B.; Chang, Y.; Chi, Q.; Dong-Mei, L.; Min, H. Quantum key agreement protocol based on quantum search algorithm. Int. J. Theor. Phys. 2021, 60, 838–847. [Google Scholar] [CrossRef]
- Karim, F.; Abulkasim, H.; Alabdulkreem, E.; Ahmed, N.; Jamjoom, M.; Abbas, S. Improvements on new quantum key agreement protocol with five-qubit Brown states. Mod. Phys. Lett. A 2022, 37, 2250128. [Google Scholar] [CrossRef]
- Wang, C.; Zhang, Q.; Liang, S.; Zhu, H. Secure mutual authentication quantum key agreement scheme for two-party setting with key recycling. Quantum Inf. Process. 2024, 23, 139. [Google Scholar] [CrossRef]
- Pan, D.; Long, G.L.; Yin, L.; Sheng, Y.-B.; Ruan, D.; Ng, S.X.; Lu, J.; Hanzo, L. The evolution of quantum secure direct communication: On the road to the qinternet. IEEE Commun. Surv. Tutor. 2024, 23, 1898–1949. [Google Scholar] [CrossRef]
- Pan, D.; Song, X.T.; Long, G.L. Free-space quantum secure direct communication: Basics, progress, and outlook. Adv. Devices Instrum. 2023, 4, 0004. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.; Chang, Y.; Yang, F.; Hou, M.; Cheng, W. Quantum secure direct communication based on quantum homomorphic encryption. Mod. Phys. Lett. A 2021, 36, 2150263. [Google Scholar] [CrossRef]
- Zhang, H.; Sun, Z.; Qi, R.; Yin, L.; Long, G.-L.; Lu, J. Realization of quantum secure direct communication over 100 km fiber with time-bin and phase quantum states. Light Sci. Appl. 2022, 11, 83. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Situ, H.; Huang, Q.; Zhang, C. A novel quantum private set intersection scheme with a semi-honest third party. Quantum Inf. Process. 2023, 22, 429. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Zhang, S. Quantum multi-party private set intersection using single photons. Phys. A Stat. Mech. Its Appl. 2024, 649, 129974. [Google Scholar] [CrossRef]
- Sutradhar, K.; Om, H. An efficient simulation for quantum secure multiparty computation. Sci. Rep. 2021, 11, 2206. [Google Scholar] [CrossRef] [PubMed]
- Yang, Y.G.; Wen, Q.Y. An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 2009, 42, 055305. [Google Scholar] [CrossRef]
- Tseng, H.Y.; Lin, J.; Hwang, T. New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 2012, 11, 373–384. [Google Scholar] [CrossRef]
- Wang, C.; Xu, G.; Yang, Y.X. Cryptanalysis and improvements for the quantum private comparison protocol using EPR pairs. Int. J. Quantum Inf. 2013, 11, 1350039. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum gate-based quantum private comparison. Int. J. Theor. Phys. 2020, 59, 833–840. [Google Scholar] [CrossRef]
- Ming-Yi, D. Cryptanalysis and improvement of quantum gate-based quantum private comparison. Int. J. Theor. Phys. 2021, 60, 195–199. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.B.; Chang, Y.; Hou, M.; Cheng, W. Efficient quantum private comparison based on entanglement swapping of bell states. Int. J. Theor. Phys. 2021, 60, 3783–3796. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum private comparison using single bell state. Int. J. Theor. Phys. 2021, 60, 4030–4036. [Google Scholar] [CrossRef]
- Hou, M.; Sun, S.Y.; Zhang, W. Quantum private comparison for the socialist millionaire problem. Front. Phys. 2024, 12, 1408446. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. New Quantum Private Comparison Using Bell States. Entropy 2024, 26, 682. [Google Scholar] [CrossRef] [PubMed]
- Huang, X.; Zhang, W.F.; Zhang, S.B. Efficient multiparty quantum private comparison protocol based on single photons and rotation encryption. Quantum Inf. Process. 2023, 22, 272. [Google Scholar] [CrossRef]
- Kou, T.Y.; Che, B.C.; Dou, Z.; Chen, X.-B.; Lai, Y.-P.; Li, J. Efficient quantum private comparison protocol utilizing single photons and rotational encryption. Chin. Phys. B 2022, 31, 060307. [Google Scholar] [CrossRef]
- Liu, B.; Xiao, D.; Huang, W.; Jia, H.-Y.; Song, T.-T. Quantum private comparison employing single-photon interference. Quantum Inf. Process. 2017, 16, 180. [Google Scholar] [CrossRef]
- Pan, H.M. Two-party quantum private comparison using single photons. Int. J. Theor. Phys. 2018, 57, 3389–3395. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Single-photon-based quantum secure protocol for the socialist millionaires’ problem. Front. Phys. 2024, 12, 1364140. [Google Scholar] [CrossRef]
- Liu, B.; Gao, F.; Jia, H.; Huang, W.; Zhang, W.-W.; Wen, Q.-Y. Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process. 2013, 12, 887–897. [Google Scholar] [CrossRef]
- Ji, Z.; Zhang, H.; Wang, H. Quantum private comparison protocols with a number of multi-particle entangled states. IEEE Access 2019, 7, 44613–44621. [Google Scholar] [CrossRef]
- Ye, T.Y.; Ji, Z.X. Two-party quantum private comparison with five-qubit entangled states. Int. J. Theor. Phys. 2017, 56, 1517–1529. [Google Scholar] [CrossRef]
- Fan, P.; Rahman, A.U.; Ji, Z.; Ji, X.; Hao, Z.; Zhang, H. Two-party quantum private comparison based on eight-qubit entangled state. Mod. Phys. Lett. A 2022, 37, 2250026. [Google Scholar] [CrossRef]
- Ji, Z.X.; Ye, T.Y. Quantum private comparison of equal information based on highly entangled six-qubit genuine state. Commun. Theor. Phys. 2016, 65, 711. [Google Scholar] [CrossRef]
- Ji, Z.X.; Zhang, H.G.; Fan, P.R. Two-party quantum private comparison protocol with maximally entangled seven-qubit state. Mod. Phys. Lett. A 2019, 34, 1950229. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. Efficient Quantum Private Comparison Based on GHZ States. Entropy 2024, 26, 413. [Google Scholar] [CrossRef] [PubMed]
- Zha, X.W.; Yu, X.Y.; Cao, Y.; Wang, S.-K. Quantum private comparison protocol with five-particle cluster states. Int. J. Theor. Phys. 2018, 57, 3874–3881. [Google Scholar] [CrossRef]
- Li, C.; Chen, X.; Li, H.; Yang, Y.; Li, J. Efficient quantum private comparison protocol based on the entanglement swapping between four-qubit cluster state and extended Bell state. Quantum Inf. Process. 2019, 18, 158. [Google Scholar] [CrossRef]
- Wang, B.; Liu, S.Q.; Gong, L.H. Semi-quantum private comparison protocol of size relation with d-dimensional GHZ states. Chin. Phys. B 2022, 31, 010302. [Google Scholar] [CrossRef]
- Zhou, N.R.; Xu, Q.D.; Du, N.S.; Gong, L.-H. Semi-quantum private comparison protocol of size relation with d-dimensional Bell states. Quantum Inf. Process. 2021, 20, 124. [Google Scholar] [CrossRef]
- Wang, B.; Gong, L.H.; Liu, S.Q. Multi-party semi-quantum private comparison protocol of size relation based on two-dimensional Bell states. Chin. Phys. B 2024, 33, 110303. [Google Scholar] [CrossRef]
- Zhou, N.R.; Chen, Z.Y.; Liu, Y.Y.; Gong, L.-H. Multi-Party Semi-Quantum Private Comparison Protocol of Size Relation with d-Level GHZ States. Adv. Quantum Technol. 2024, 8, 2400530. [Google Scholar] [CrossRef]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers Systems and Signal Processing, Bangalore, India, 12 December 1984; pp. 175–179. [Google Scholar]
- Jennewein, T.; Simon, C.; Weihs, G.; Weinfurter, H.; Zeilinger, A. Quantum cryptography with entangled photons. Phys. Rev. Lett. 2000, 84, 4729. [Google Scholar] [CrossRef] [PubMed]
- Hughes, R.J.; Nordholt, J.E.; Derkacs, D.; Peterson, C.G. Practical free-space quantum key distribution over 10 km in daylight and at night. New J. Phys. 2002, 4, 43. [Google Scholar] [CrossRef]
- Gao, D.; Fan, D.; Zha, C.; Bei, J.; Cai, G.; Cai, J.; Cao, S.; Chen, F.; Chen, J.; Chen, K.; et al. Establishing a new benchmark in quantum computational advantage with 105-qubit zuchongzhi 3.0 processor. Phys. Rev. Lett. 2025, 134, 090601. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.F.; Li, D.F.; Zheng, Y.D.; Yang, X.-L.; Zhou, J.; Tan, Y.-Q.; Liu, M.-Z. Experimental realization of quantum controlled teleportation of arbitrary two-qubit state via a five-qubit entangled state. Chin. Phys. B 2022, 31, 050301. [Google Scholar] [CrossRef]
- Ye, T.Y.; Ye, C.Q. Measure-resend semi-quantum private comparison without entanglement. Int. J. Theor. Phys. 2018, 57, 3819–3834. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Zhang, S. Practical quantum protocols for blind millionaires’ problem based on rotation encryption and swap test. Phys. A Stat. Mech. Its Appl. 2024, 637, 129614. [Google Scholar] [CrossRef]
- Jain, N.; Anisimova, E.; Khan, I.; Makarov, V.; Marquardt, C.; Leuchs, G. Trojan-horse attacks threaten the security of practical quantum cryptography. New J. Phys. 2014, 16, 123030. [Google Scholar] [CrossRef]
- Lucamarini, M.; Mancini, S. Secure deterministic communication without entanglement. Phys. Rev. Lett. 2005, 94, 140501. [Google Scholar] [CrossRef] [PubMed]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).