1. Introduction
Fixed point theory deals with the study of conditions that guarantee the existence and approximation of the solutions of linear and nonlinear operator equations. The development of fixed point iterative algorithms to approximate the solution of certain operator equations is another domain of fixed point theory. These iterative algorithms are classified based on their stability, data dependency, rate of convergence, time and space complexities, and well-posedness.
Banach contraction principle (BCP), a well-known result in metric fixed point theory, applies to a large range of problems dealing with the existence and approximation of the solution of nonlinear operator equations such as differential and integral equations. BCP has some limitations as well. A natural extension of Banach contraction mapping is a non-expansive mapping whose fixed points cannot be approximated through the Picard iteration algorithm employed in BCP, refer to [
1]. Indeed, it does not apply to several important classes of mappings that arise in modeling different convex optimization problems. Therefore, this principle has been generalized and extended by weakening the contraction condition. Kirk [
2], Browder [
3], and Gohde [
4] established the existence of fixed points of non-expansive mappings defined on a specific subset of a Banach space satisfying certain geometric conditions. It was proved in 1955 that Picard’s iteration for non-expansive mappings may not converge to a fixed point [
5]. For the approximation of fixed points in these mappings, numerous iterative processes have been introduced, for instance, by Mann [
6], Ishikawa [
7], Abbas and Nazir [
8], Thakur et al. [
9], and Picard–Mann [
10].
Non-expansive mappings were extended by Suzuki [
11] and Garcia-Falset et al. [
12], which gave rise to two classes of generalized non-expansive mappings: the Suzuki mapping, which is the class of mappings that satisfy property
C, and the Garcia-Falset mappings, which satisfy property
E, a property that is weaker than the property
C. The concept of Suzuki mapping is weaker than non-expansive mappings but stronger than quasi-non-expansive mappings. Similarly, the notion of Garcia-Falset mapping is weaker than Suzuki mappings [
11] but not from quasi-non-expansive mappings, as shown by Proposition 1 and Example 1 below. Several authors presented examples on
,
, and on some infinite-dimensional spaces to show the inclusivity of Suzuki mappings [
9,
11,
13]. Using three-step iterative methods, results for the existence of fixed points and convergence behavior were studied for the above-mentioned generalized non-expansive mappings [
14,
15,
16].
Over the last few years, different iterative algorithms have been presented to obtain a faster rate of convergence. Moreover, the stability results and data dependency of these algorithms have also been studied (see, for example, [
17,
18,
19,
20]). Hacıoğlu [
21] suggested a new iterative algorithm and examined the data dependency, convergence, and stability for the class of almost contraction mappings.
An iterative algorithm is preferred over another one if it converges to a fixed point with minimal iterations and computational time. To the best of our knowledge, the convergence analysis of fixed point iterative algorithms involving mapping satisfying the Garcia-Falset condition is not widely available in the literature.
In 2019, Houmani and Turcanu [
14] introduced a new class of mappings satisfying the property
E and employed Thakur’s three-step iteration algorithm to approximate the fixed point of such mappings. In this paper, we employ an iterative algorithm presented in [
21] and extend the results in [
14] to Garcia-Falset mapping. We also present existence and
-stability results. We provide examples satisfying the Garcia-Falset property and conduct numerical experiments to compare the proposed iterative algorithm with other iterative algorithms. Finally, a weak solution of a Volterra–Stieltjes-type delay functional differential equation is presented to demonstrate the significance of our results.
The hybrid-type iterative algorithm [
21] is as follows:
Let
S be a self-map on a convex, closed, and nonempty subset
A of a Banach space
B. Define the sequence
by:
Here,
is a sequence of real numbers in
.
Let us consider the following two cases in (
1).
Case 1. When
, then we have
and
Case 2. When
, then we have
Hence, we may see that (
1) does not reduce to Picard, Mann, Ishikawa, Picard–Mann, or Thakur for any
2. Preliminaries
Definition 1. Let B be a Banach space, . A mapping is called non-expansive if, for all , the following inequality holds: Definition 2. A mapping is said to be quasi-non-expansive if for all and , we havewhere, the set of all fixed points of S is denoted by Definition 3. A mapping is said to be a Suzuki mapping or Suzuki generalized non-expansive mapping if for all Definition 4. Let B be a Banach space, , and . A mapping is said to satisfy the -property or called Garcia-Falset mapping if for all , the following holds:We say condition on A is satisfied by whenever S fulfills condition for some . Definition 5. Two sequences and in A is said to be equivalent if The notion of stability or weak stability often lacks precision when the sequence
is chosen arbitrarily. To address this ambiguity, it is more natural to consider
as an approximate or equivalent sequence to
, respectively. In this context, we introduce the concept of weak
-stability, as proposed in [
22], where the approximate sequence is replaced by an equivalent one, providing a more rigorous formulation of weak
-stability.
Definition 6 ([
22])
. Let be a metric space and and . Consider an iterative sequence defined bywhere is any function. Suppose thatand for any equivalent sequence of ifthen we say that is weak -stable in S. Definition 7 ([
1])
. For two sequences and with and , ifthen, we say that converges faster than Definition 8. Suppose that two iterative sequences and are converging to and we have the following error estimates,If the sequence of positive real numbers converges to 0 faster than the sequence of positive real numbers does, then we say that faster than Definition 9. If, for every sequence, converges weakly to , and for each with , we haveThen the Banach space B is said to satisfy Opial’s condition. Sentor and Dotson [
23] introduced Condition
on given self-mappings as follows:
Definition 10. A mapping is said to satisfy the Condition if there is a non-decreasing function such thatholds for all a in where - i.
- ii.
for all
- iii.
Let us recall the definitions given in [
24].
Definition 11. Suppose that is a bounded sequence in Define the by:A positive real number is known as an asymptotic radius of the sequence at If then asymptotic radius of relative to A is defined byThe set is defined as:is called asymptotic center of relative to The asymptotic center is a singleton whenever
B is a uniformly convex Banach space space [
25].
Definition 12. Let A be a nonempty subset of a Banach space B. A mapping is said to be demiclosed at if, for every sequence in A converging weakly to a in A and converging strongly to d gives that
It is known that if A is a nonempty closed, bounded, and convex subset of a uniformly convex Banach space B and is non-expansive, then is demiclosed.
Proposition 1 ([
12])
. Suppose a mapping satisfies Garcia-Falset property on then S is quasi-non-expansive provided that is nonempty. Proof. Suppose
, i.e.,
, and
be arbitrarily chosen. Using the Garcia-Falset condition with
, we have:
Since
, it follows that
. Hence,
which shows that
S is quasi-non-expansive. □
However, the converse does not hold. This is illustrated by the following example.
Example 1. Define as All fixed points are clearly in and S is clearly quasi-non-expansive mapping.
Now, take , .
But, ; hence, S is a quasi-non-expansive mapping, but does not satisfy .
Lemma 1 ([
26])
. Suppose B is a uniformly convex Banach space and for all Let and be two sequences satisfying , and for any then Lemma 2 ([
11])
. Suppose that A is a weakly compact subset of a uniformly convex Banach space. If S satisfies the Condition C, then S has a fixed point. 3. Convergence Theorems
We now present the convergence of an iterative algorithm of the mapping satisfying the Garcia-Falset property. Throughout the section, B is a uniformly convex Banach space and is a closed and convex subset of
Lemma 3. Suppose that satisfies the Garcia-Falset property and Let be an arbitrary fixed element in A. For an iterative algorithm given in (1). Then, exists, where Proof. As
S satisfies Garcia-Falset property, and
from Proposition 1,
S is quasi-non-expansive. Note that,
Thus, we have
Also,
It follows from (
6) that
By (
8),
is decreasing and bounded below, for all
. Hence,
exists. □
Lemma 4. Suppose that satisfies the Garcia-Falset property. Let be an arbitrary fixed element in A. For an iterative algorithm given in (1). Then, if and only if is bounded and Proof. Suppose that
is bounded,
and
As
S is Garcia-Falset mapping, we obtain that
which implies that
.
Since
B is a uniformly convex Banach space, by the uniqueness of asymptotic center,
is a singleton. Thus,
Conversely, suppose that
From Lemma 3,
exists and
is bounded. Suppose that
From (
7), we have
Since
S is a quasi-non-expansive mapping, we have
Now,
From (
9) and (
10), we obtain that
Thus,
We can rewrite that
From (
10), (
11), (13) and Lemma 1, we have
□
Theorem 1. Suppose satisfies the Garcia-Falset property and Let be an arbitrary fixed element in A. For an iterative algorithm , given in (1), converges weakly to when B fulfills the Opial’s condition. Proof. From the Lemma 3,
exists. Let
and
be two subsequences of
with weak limits
and
, respectively. By Lemma 4, we have
Using demiclosedness of
at zero, we have
that is,
Similarly,
. We now show that
. If not, then by using Opial’s condition, we have
which is a contradiction. Hence,
converges weakly to
□
Theorem 2. Suppose that satisfies the Garcia-Falset property, where A is nonempty closed and convex subset of B. Let be an arbitrary fixed element in A. For an iterative algorithm given in (1), then converges to p if, and only if, or . Proof. Let where we have or .
Conversely, suppose that
From Lemma 3,
exists for all
We now show that
is a Cauchy sequence. As
for
there exists
, such that
Particularly,
This implies that there is
, such that
For
we have
Thus,
is Cauchy. As
A is closed, there exists
, such that
Now,
implies that
□
Theorem 3. Suppose that satisfies the Garcia-Falset property, where A is a nonempty compact and convex subset of B. Let be an arbitrary fixed element in A. For the iterative algorithm given in (1), if , then converges strongly to Proof. Suppose
then from Lemma 4, we get
By compactness of
there exists a subsequence
of
, such that
By Garcia-Falset property, we have
On taking limit as
we have
Hence,
i.e.,
By Lemma 3, exists, and hence □
The following result establishes strong convergence using Condition (I).
Theorem 4. Suppose that satisfies the Garcia-Falset property and the Condition (I), where A is a nonempty closed and convex subset of B. Let be an arbitrary fixed element in A for an iterative algorithm given in (1). Then, converges strongly to . Proof. From Lemma 4, we have
Using the Condition
we have
which implies that
Hence, we get
Finally, all conditions of the Theorem 2 are satisfied, so
converges strongly to a fixed point of
□
We will demonstrate the strong convergence and
-stability of the iterative algorithm (
1) under the following contractive condition: there is a constant
and a continuous, monotonic increasing function
with
, such that for any
, the following inequality holds:
Theorem 5. Suppose that satisfies the contractive condition (14). Let be an arbitrary fixed element in A. Then, an iterative algorithm given in (1) converges strongly to with the following estimate: Proof. Using Equation (
14) and algorithm (
1), we have
Since
this implies
Inductively, we have
On taking the limit as
, we have
that is,
converges strongly to
□
5. Numerical Experiments and Graphical Analysis
This section is dedicated to numerical and graphical convergence analysis of the iterative algorithm (
1). In the Examples 2–4, we compare some famous iterative algorithms with the algorithms (
1) and (
2) (Case 1). The criterion of comparison chosen here is the error
, where
is an iterative sequence and
p is a fixed point. Different initial points are selected from the domain to compare the computational efficiency of the iterative processes.
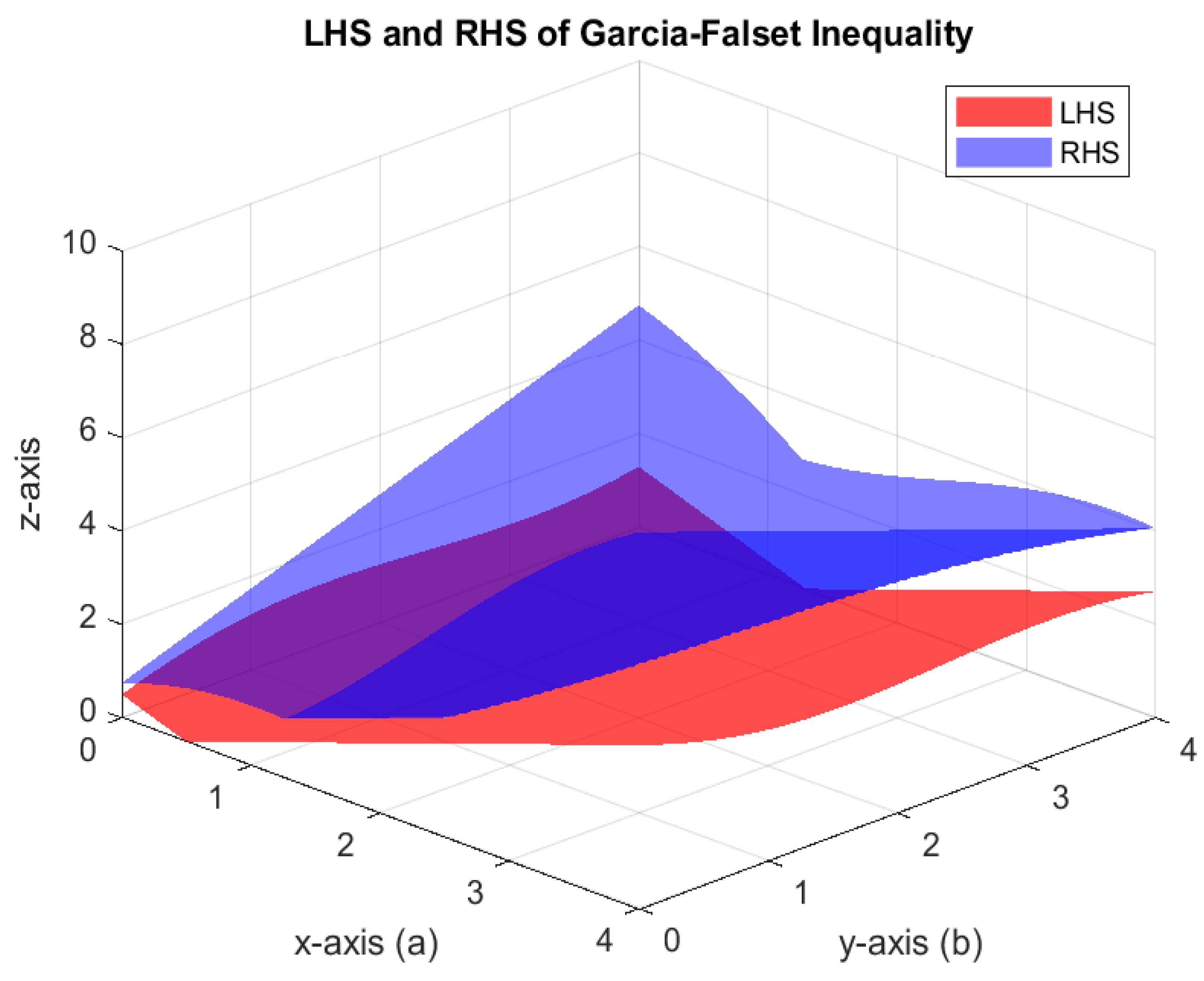
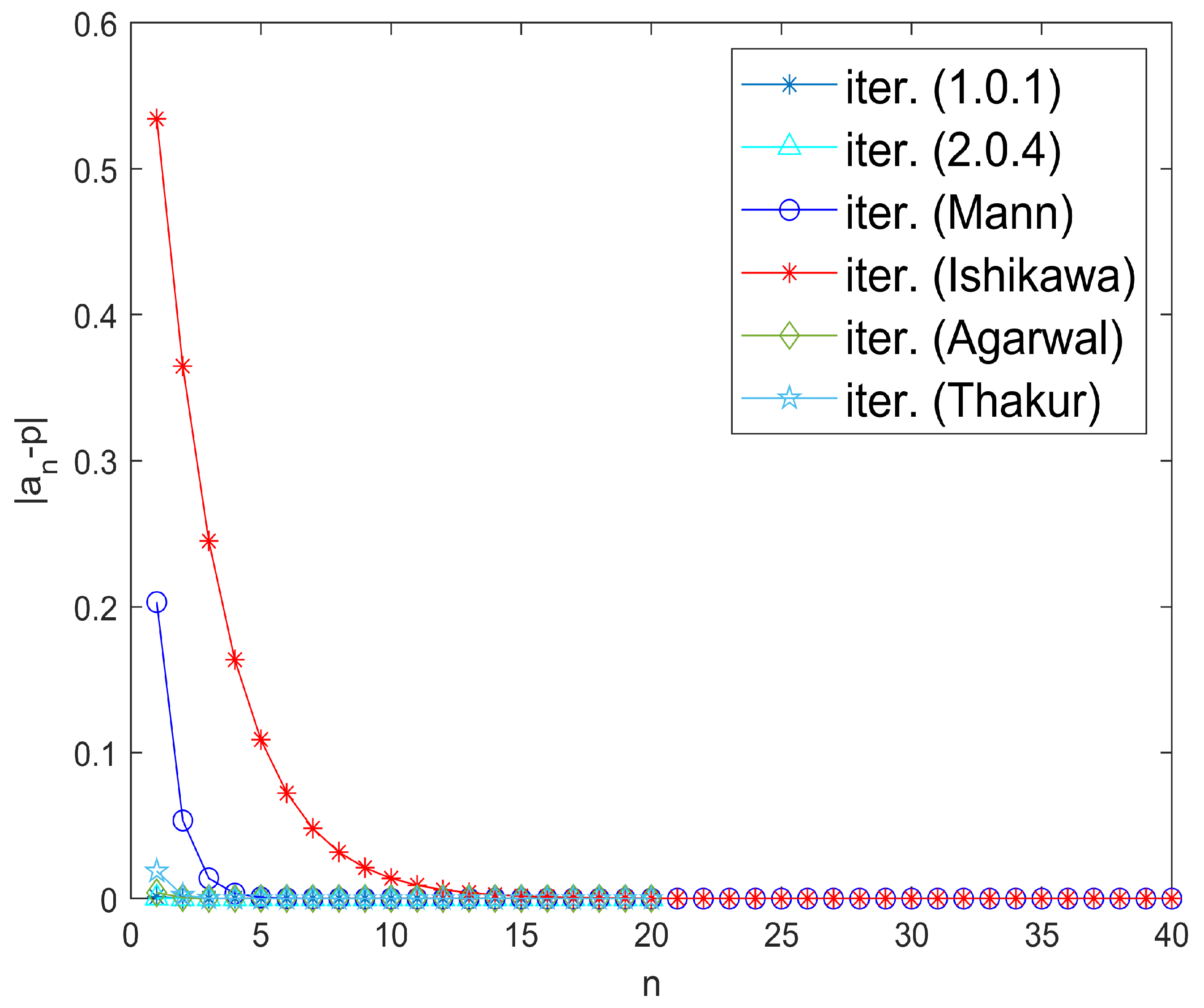
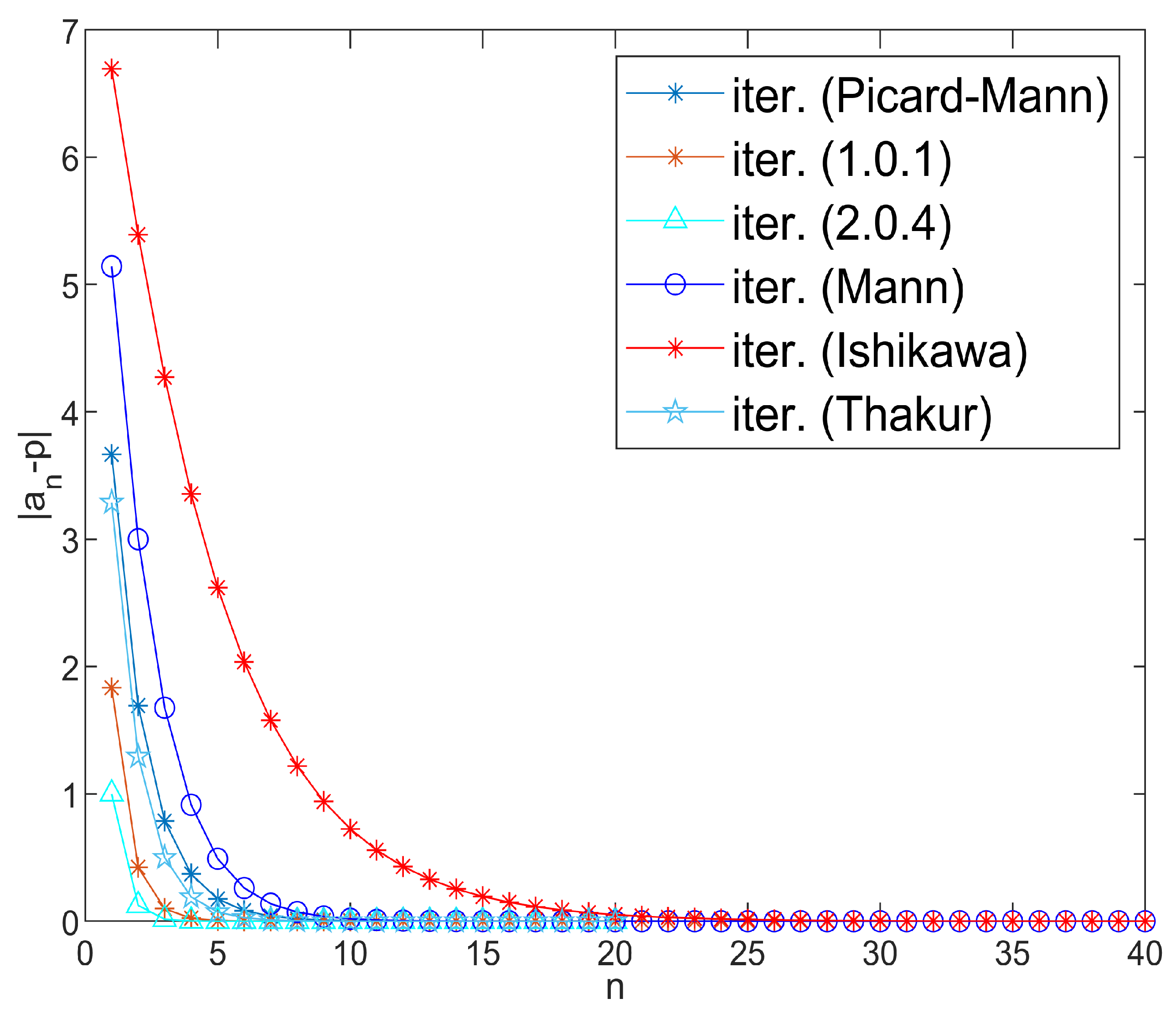
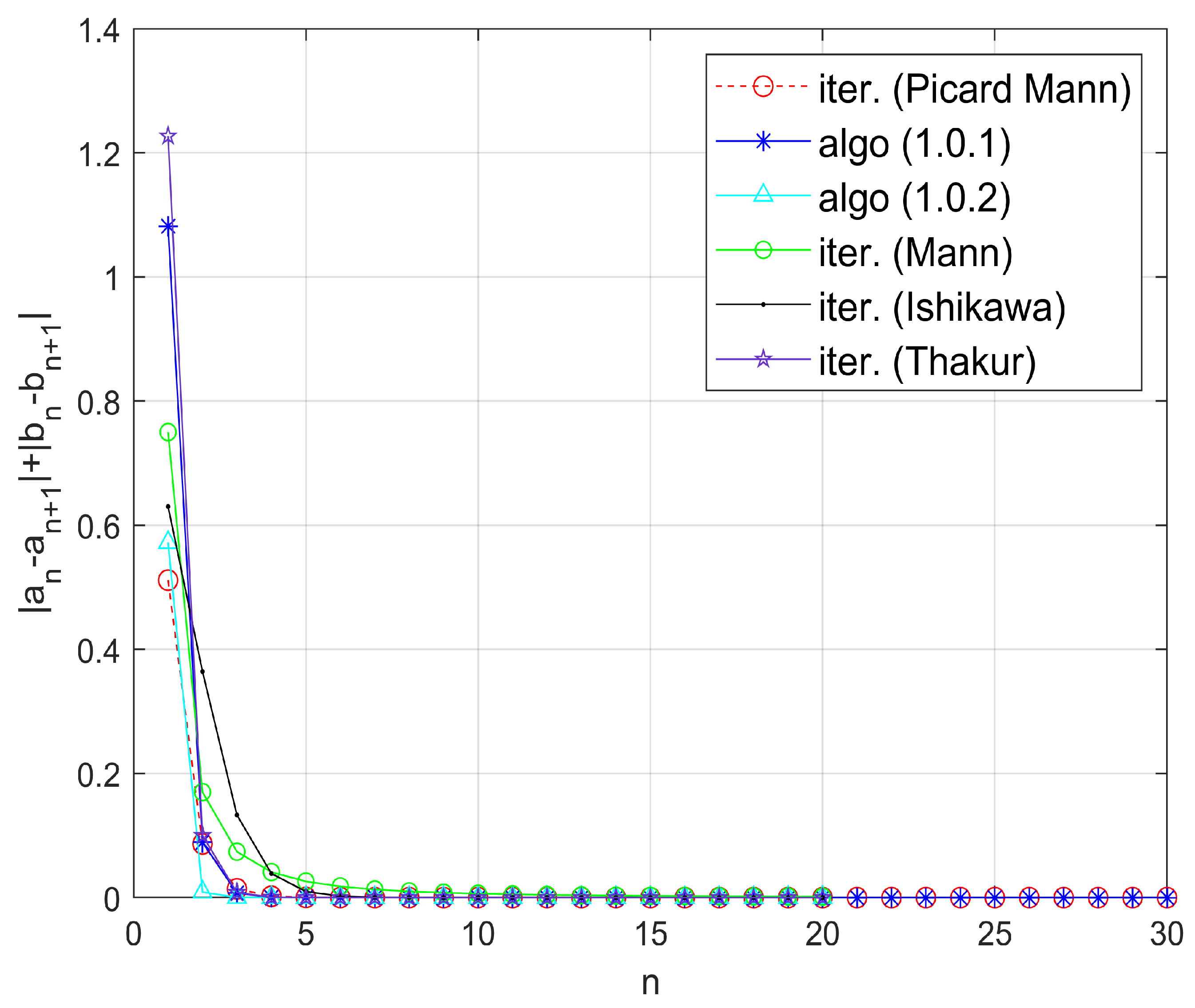
Example 2. Let be endowed with the usual norm. Define the mapping byTake for all and initial guess . Numerical computations with MATLAB version 9.10.0.1602886 (R2021a) software suggest that is the unique fixed point of the map S, satisfying the fixed point equation approximately. Moreover, Figure 1 visually confirms that inequality (4) holds, indicating that the mapping S satisfies the -property. Since S satisfies the Garcia-Falset property and , it follows from Theorem 3 that the iterative algorithm (1) converges to the fixed point . Observe that the algorithm (1) converges faster than the iterative algorithms given by Picard–Mann, Mann, Ishikawa, and Thakur, as shown in Table 1 and Figure 2. In Table 2, we compare the convergence of various iterative algorithms for different choices of initial points. The parameter was chosen to be . Example 3. Let be endowed with the usual norm. Define a mapping by Numerical simulations show that is a unique fixed point of S. Also, S satisfies -property given by (4). Choose for all . We pick as initial guess. Now, all the conditions of Theorem 3 are fulfilled and iterative algorithm (1) converges to Clearly, it converges faster than the iterative algorithms given by Picard–Mann, Mann, Ishikawa, and Thakur, as shown in Table 3 and Figure 3. For parameter Table 4 exhibits the quicker convergence of the iterative algorithm (1) for different choices of initial points. Example 4. Suppose is equipped with the usual norm. Define the mapping by:Note that S does not satisfy the Condition . However, S is a Garcia-Falset mapping. Indeed, for and we haveAlsoHence,but . This implies that S does not satisfy the Condition . Suppose that . Consider the following cases.
Case I.
and give thatwhich is true. Case II.
When it gives If , we obtain , which leads to , a statement that is true. On the other hand, if , we derive , which simplifies to , and this is also true.
Case III.
and give
We can easily check that it is true. Thus, S is the Garcia-Falset mapping.
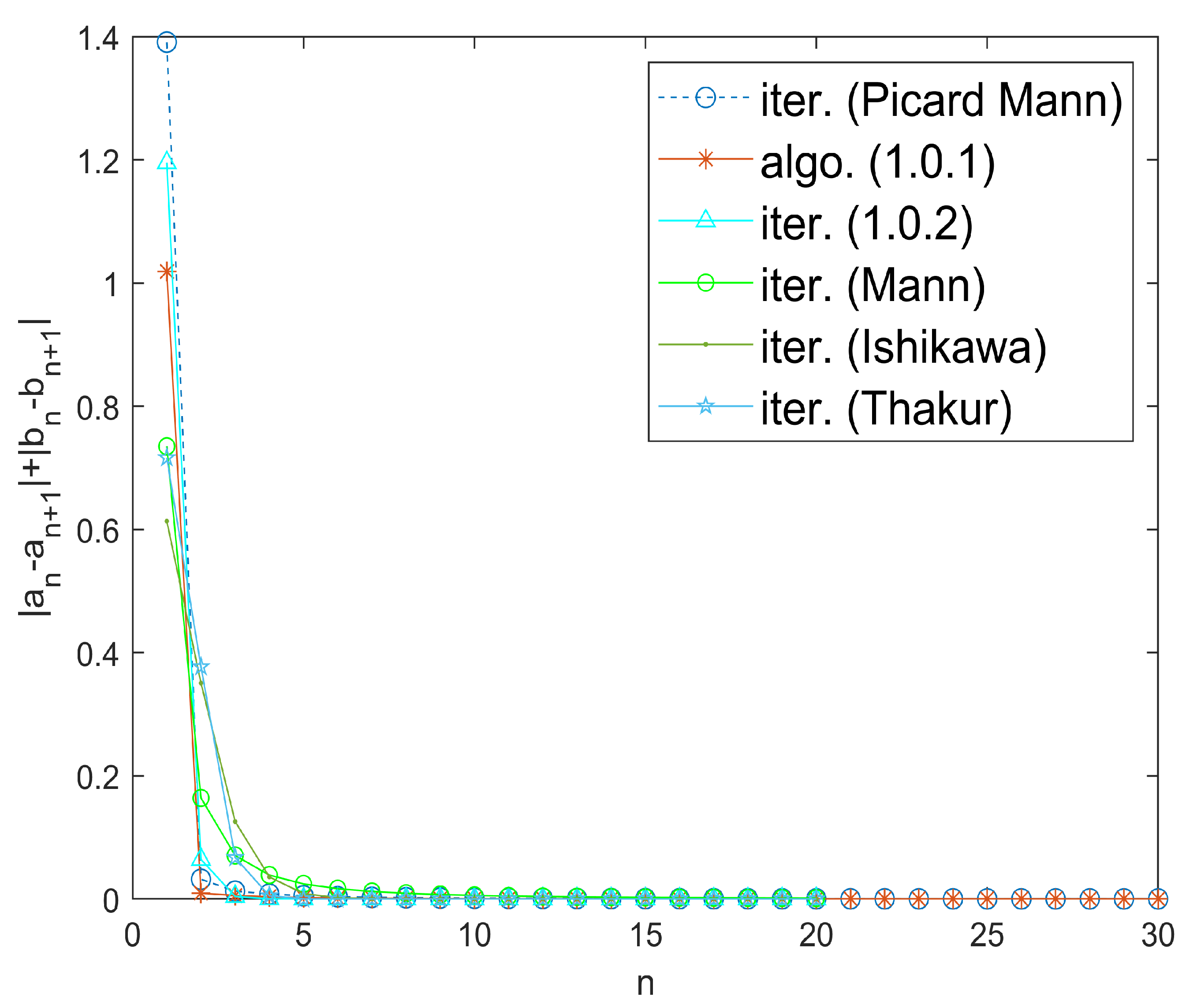
We now present a numerical experiment for the comparison of the convergence of algorithm (1). Taking an initial value and , it is noted that the iterative algorithm (1) has the quickest convergence rate, as compared to other algorithms, as shown in Table 5 and Figure 4 with fixed point 0. Now, we compare the convergence of the iterative algorithm (1) with other iterative algorithms by choosing different initial points. Take parameter . Indeed, the algorithm (1) proves to be more suitable for Garcia-Falset operators as it has a quicker rate of convergence. The numerical results are demonstrated in Table 6. In the following example, it must be noted that the mapping does not have a unique fixed point, and different iterative processes may converge to any of the fixed points for a certain initial value. Hence, to test the convergence, we employ an appropriate stopping criterion: for ,
Example 5. Define a mapping by,where . The distance between the points is defined using the Euclidean norm. First, we show that S is not non-expansive. Consider the points and . Then,We compute the Euclidean distance:andThus,which implies . Hence, S is not non-expansive. To show that S satisfies the Garcia-Falset property, we consider the following cases:
Case I.
If then for , following inequality, it must hold for S to satisfy the condition Divide the above inequality into two parts:If we consider (22), then for , we haveandIf we take (23), then for the given range of and , we haveandFrom the above inequalities, it is clear that S has the Garcia-Falset property. Case II.
Let then for , following inequality, it should hold for S to satisfy the condition
Again, divide the above inequality into two parts:For the given range of a and b, (24) becomes That is, So the inequality is satisfied. The inequality (25) is proven in Case I. Hence, S satisfies the Garcia-Falset property for Case II.
To analyze the rate of convergence of different iterative algorithms and iterative algorithm (1), we have chosen the sequence with initial guess as . Finally, through numerical approximation using MATLAB version 9.10.0.1602886 (R2021a) software, it is determined that the iterative algorithm (1) converges to the fixed point faster than Picard–Mann, Mann, Ishikawa, and Thakur’s iterative algorithms, as shown in Figure 5. Again, for a different initial guess we conclude that the iterative algorithm (1) converges to fixed point faster than Picard–Mann, Mann, Ishikawa, and Thakur iterative algorithms, as shown in Figure 6. Now, we compare the iterative algorithms using different initial points. It can be observed from Table 7 that algorithm (1) and its Case (2) converges in a lesser number of iterations. 6. Application to Volterra–Stieltjes-Type Delay Functional
Differential Equation
Recently, many authors have studied the existence and uniqueness of the solution of Volterra–Stieltjes-type delay functional differential equations, see [
27,
28] and references therein. As an application of our results, we propose the approximation of the weak solution of Volterra–Stieltjes-type delay functional differential equation utilizing the iterative method (
1). Suppose
B is a reflexive Banach space equipped with the norm
, the dual space of
B is denoted as
, and the class of continuous functions is denoted as
with the norm as follows:
Let us consider a non-linear second-order Volterra–Stieltjes-type initial value delay functional differential problem as follows:
with the initial condition
Let us consider the following assumptions:
- i.
is continuously non-decreasing and
- ii.
For
, each
weakly fulfills the Lipschitz condition and is weakly continuous, such that
where
are Lipschitz constants.
- iii
is continuous function with
- iv.
Lemma 5 ([
27])
. A solution of the non-linear second-order Volterra–Stieltjes-type initial value delay functional differential problem (26) and (27) exists whenever it is expressed as an integral equation as follows: We derive the following theorem for the existence of the solution of (
26) and (
27) by using an iterative algorithm (
1).
Theorem 7. Suppose that the assumptions (i)–(iv) hold and is a sequence approximated by (1). Then, initial value problem (26) and (27) has a unique solution and converges to Proof. Let
be sequence approximated by (
1). Let
S be an operator on
by
We have
Consider
Using assumption (ii), we have
and
Moreover,
yields
Also,
Further, from assumption (ii), we get
and
Since
,
Using (
29) we obtain
We have
Thus,
By setting
we obtain
which implies
So,
□