Abstract
Since the research of -synchronization helps to explore how complex networks (CNs) work together to produce complex behaviors, the -synchronization task for uncertain time-delayed CNs is studied in our work. Especially, bounded external perturbations and variable delays of unknown bounds containing coupling delays, internal delays, and pulse delays are all taken into consideration, making the model more general. Through the -stable theory together with the hybrid impulsive control technique, the problems caused by uncertain inner couplings, time-varying delays, and perturbations can be solved, and novel synchronization criteria are gained for the -synchronization of the considered CNs. Different from traditional models, it is not necessary for the coupling matrices to meet the zero-row-sum condition, and the control protocol relaxes the constraint of time delays on impulse intervals. Moreover, numerical experiments and image encryption algorithms are carried out to verify our theoretical results’ effectiveness.
Keywords:
complex systems; μ-synchronization; uncertain inner couplings; hybrid impulsive control; external perturbations MSC:
05C82
1. Introduction
Complex networks (CNs) are very common in daily life [1,2], such as social networks, retrieval systems of the scientific literature, power networks, commercial networks, biological neural networks (NNs), and cellular NNs. CNs, as carriers of information dissemination, exhibit diverse synchronization phenomena. In fact, the ability of the network to achieve synchronization lies on the network’s topology and the dynamic properties of the nodes, as well as the strength of the external control. By studying the phenomenon of synchronization, we can better understand the evolution process of complex networks over time and their potential in engineering applications.
1.1. The Background and Related Works
Various categories of synchronization have been presented, such as phase synchronization [3,4], complete synchronization [5], generalized synchronization [6], finite-time synchronization [7,8,9], projective synchronization [10], and -synchronization [11,12,13,14]. -Synchronization is a generalized synchronization associated with the -function that can be converted to an exponential or logarithmic synchronization and has thus received focused attention from researchers. The -synchronization of CNs is particularly valuable in scenarios that are affected by noise, uncertainties, or other disturbances. Its applications span a wide range of fields, including secure communication, distributed computing, control systems, coupled oscillators, etc. There are several control methods for the synchronization of CNs, such as pinning control [15,16], optimal control [17], adaptive control [18], decentralized control [19], event-triggered control [20,21], and impulsive control [11,12,13,14,22]. Impulsive control only applies brief control inputs at specific time instants, rather than continuous control, which can significantly reduce the overall energy consumption. For achieving the -synchronization of multi-link CNs, a distributed delayed impulsive controller is presented by establishing a Halanay-like inequality [11]. By combining the benefits of two control theories, namely, pulse control theory and event-driven control theory, Zhang et al. [12] presented an impulsive control approach aiming for the -synchronization tasks of CNs. The -synchronization task of coupled NNs was investigated via the integration method based on pulse effects [13]. By means of an impulsive delay inequality approach, Guan et al. studied the -stabilization and -synchronization tasks of CNs with variable time delays [14]. In [22], utilizing the average impulsive interval approach, a secure impulsive controller was introduced to ensure the bounded synchronization of dynamic networks.
In many actual CNs, there exist inherent time delays in the information interactions among nodes, which significantly impact their synchronization task. Based on the decomposing technique, Liu et al. [23] investigated the anti-synchronization issue for coupled complex CNs with asynchronous variable time delays. Luo et al. [24] solved the finite-time synchronization problems of the uncertain variable time-delayed CNs by a feedback controller. Tan et al. [25] dealt with the synchronization task of CNs affected by time delays with a discrete distribution. Han et al. [26] explored complex function projective synchronization issues for CNs, in which coupling delays were considered. Intermittent control strategies were applied in [27] to achieve finite-time synchronization for delayed fuzzy CNs. The preassigned-time synchronization tasks were investigated for fuzzy memristive NNs with variable delays by putting forward a general controller in [28]. Through the Lyapunov–Krasovskii theory, the synchronization of Markovian jumping chaotic NNs with distributed time-varying delays was analyzed in [29]. Xing et al. presented the double-ring NN model with multiple bounded time delays and discussed its stability using the Coates flow graph method in [30]. In the above synchronization results, the time delay is assumed to be bounded, and the change rate of the time delay is restricted to a limited range of intervals.
In addition, there exist parameter uncertainties caused by factors such as system modeling errors, time delays, and external disturbances in practical complex networks. Parameter uncertainties including inner coupling states, node dynamics, and outer coupling topologies can affect the system’s synchronization behavior. He et al. [31] investigated the n-dimensional multi-time delayed fractional order NNs with parameter uncertainty by adopting an active control strategy, in which the parameter uncertainty involved belonged to uncertain outer couplings. Gu et al. [32] considered the synchronization tasks for memristor-based dynamical CNs with parameter uncertainty through a comparison principle and the Lyapunov method, in which parameter uncertainty describes the synaptic connection weight among different nodes. Fan et al. [33] investigated synchronization in multi-weighted CNs with parameter uncertainties that were added to the weight constant matrices of the node’s state vector. Selvaraj et al. [34] investigated the synchronization of non-linear uncertainty CNs in view of a feedback control strategy. Mirshamsi et al. [35] proposed a bounded control approach for linear time-invariant systems that considered time-varying uncertainty in state and input matrices. However, the -synchronization of CNs with internal coupling parameter uncertainty has been rarely studied.
Further, unknown external disturbances [36,37,38] can generally affect the synchronization behaviors between the drive–response CNs. Through a simple error feedback control strategy, Du et al. studied the function projective synchronization (FPS) task for CNs subjected to external perturbations [39]. In [40], by introducing the stability theory, Du et al. presented a new control method for addressing the issue of modified FPS for fractional order CNs with external perturbations. With the help of the Lyapunov stability theory and comparison criteria, the mean square exponential synchronization of CNs with stochastic perturbations was explored in [41]. By introducing a disturbance observer, the asymptotical synchronization task was focused on nonidentical CNs affected by unknown external perturbations in [42]. Liang et al. explored the synchronization task of switched duplex NNs under external stochastic disturbances by introducing channel matrices [43]. Research on the fixed-time synchronization task for delayed CNs in the presence of stochastic perturbations using the impulsive pinning control was studied in [44]. Shukla et al. [45] presented the condition for the El Niño chaotic system to achieve function matrix projective synchronization under the controller, which uses the functional projective matrix information. However, to date, few works consider how to design specific controllers for the -synchronization of uncertain CNs with unknown external perturbations and unbounded time delays, especially in the case where the coupling topology is not limited by dissipative coupling. This is also the main research motivation for this article.
1.2. The Research Aim and Highlights
Since studying -synchronization helps to shed light on how CNs work together to produce complex behaviors and cognitive functions, our goal is to achieve -synchronization for the considered CNs. The research question is how to design a controller to achieve -synchronization for the uncertain time-delayed CNs. Given by the aforementioned discussions, to achieve -synchronization for a type of unbounded time-delayed CNs with external disturbances and uncertainties of inner couplings, new synchronization criteria are derived. The highlights of this article contain the following aspects: (1) The time-delayed CNs that include uncertain couplings and external perturbations are modeled. In particular, all time delays, namely, coupling delays, internal delays, and pulse sampling delays, have non-metrizable bounds. (2) Unlike the pulse control protocols in [46,47,48], the hybrid pulse controllers in this paper allow the sampling delay to be unbounded, and new synchronization conditions are obtained for the uncertain time-delayed networks studied. (3) There is no need for the model’s external coupling matrices to meet the condition of dissipative coupling, and the control protocol relaxes the constraint of time delays on pulse intervals.
Notations: I denotes the unit matrix with a certain dimension. denotes a positive definite matrix. ∀, , , : , in which o is continuously differentiable. : stands for the space of all piecewise continuous functions from to , with the segmentation points satisfying , and exists. Let , , with the norm . and are the maximum and minimum eigenvalues of the matrix individually. denotes the family of all non-decreasing functions on , which satisfies as .
2. Model and Background Description
In view of the delay and uncertainty phenomena in neural networks, the CNs considered in this article are formulated as
where , refers to the node’s state values, , N. , , and are known weight matrices, and is the function that stands for the coupling behavior among nodes. , are the functions that describe the nodes’ nonlinear behavior. and denote the coupling strengths, in which , . , denote the outer coupling matrices between different coupled nodes. It is mentioned that and if there is a coupling between nodes i and j; otherwise, . , are the matrices reflecting the inner-coupling situations, where and denote certainty coupling matrices, and and denote the uncertainty parts. and are the unbounded delays with , and is the original condition of node i.
We treat the CNs (1) as the drive system, and then take the response system with external disturbances and controllers as the following form:
where , is the node’s response state values, , N. is the original condition of node i in response networks. is the bounded external disturbance vector in the response system, which satisfies . Here, stands for the modulus of vector .
To accomplish the synchronization task, the controller in this paper contains information feedback techniques and impulse sampling schemes. denotes the system synchronization error, and the controller employing the feedback information is further designed as below:
in which refers to the sign vector function, and is the control gains. The delayed impulsive controller of the response CNs is designed as
in which with size denotes the gain matrix of the controller, and denotes the impulsive delay satisfying . Let be the set consisting of pulse instants, namely, , in which as .
Remark 1.
The uncertain time-delayed CNs studied in this article take into account multiple factors, such as the uncertain inner couplings, the nonlinear external couplings, the unbounded internal delays, the unbounded coupling delays, and the unbounded impulsive delays, which are more general in the real world. Moreover, the bounded external disturbance vector and the hybrid controller of the error signal are considered in the response system, further enhancing the practicality and generality of the model.
Note , and , , N. Then, the synchronization task of the drive–response CNs can be regarded as the -stable objective for the error network.
Assumption 1.
For the functions , and , the three conditions
hold, ∀ϱ, , , , and .
Assumption 2.
For the matrices and , which describe the network’s topological structure, the two conditions
hold, in which , .
Assumption 3.
and denote the uncertainty parts of internal coupling, which are norm-bounded and could be described as
in which are constant matrices, and the uncertainty matrix is bounded by .
Assumption 4.
The inequality conditions with regard to
can be satisfied if , , , and
3. Synchronization Analysis Results
Then, according to the assumptions in Section 2 and the Lemmas in Appendix A, the -synchronization for uncertain time-delayed CNs with external disturbances is explored. Sufficient conditions are calculated to reach the -synchronization for CNs (1) and (2). By Definition A1 in Appendix A, the error dynamical system (5) reaching -stable is equivalent to our ultimate synchronization task.
Theorem 1.
The μ-synchronization of CNs (1) and (2) under Assumptions 1–4 and the hybrid impulsive controller can be reached if
- (i)
- (ii)
- (iii)
- (iv)
- (v)
- (vi)
in which , matrix Q is with size , , and , , , , , , , a, , . Moreover, the control gain matrix is set as .
Proof.
We establish a proper form of Lyapunov function as
When , calculating the derivative of along the solution of error system (5), it can be obtained that
According to the operation rule of matrix quadratic form, one has
By Lemma A1 and Assumption 1, it can be obtained that
Similarly, by Lemma A1 and Assumption 1, it is easy to obtain that
By Lemma A1 and Assumptions 1–3, one can obtain that
Similarly, by Lemma A1 and Assumptions 1–3, one can obtain
By Lemma A1, it is calculated that
Let , ; when , we have
In the light of Lemma A2, it can be concluded that
Thus, the following inequality holds:
Remark 2.
The network model in [11] has uncertainty in system dynamics, while the parameter uncertainty of the network model in this paper is reflected in the inner coupling matrix. For these two different types of parameter uncertainty, different inequality analysis methods, assumptions, and lemmas are used in the proof process of the Theorem. Additionally, the controllers used in the two articles are different. In [11], it only adopts a distributed pulse controller, while this paper designs a hybrid controller that includes a feedback controller and a time-delay pulse controller.
Remark 3.
The global μ-synchronization task for nonlinear CNs was studied in [49] by adopting a delayed impulsive control approach. In our article, to achieve the synchronization of the drive–response CNs, a hybrid impulsive controller containing both information feedback of error signals and impulse sampling factors is proposed. In contrast, the control scheme in this paper makes the results more applicable under external disturbances.
Remark 4.
In [50,51], the impulsive interval T was set considering the factor of the bound of time delays. From condition (i) of Theorem 1, it can be seen that the pulse interval T is not affected by the values of time delays in this article. Therefore, the constraint on the impulsive interval T is relaxed in the proposed model. Moreover, in [52], the synchronization for semi-Markov impulsive coupled NNs was reached under the state feedback controller, yet the time-varying delays were bounded parameters. In [53], the synchronization algorithm for nonlinear NNs with variable topology was proposed, yet the change rate of the time delay was within a bounded interval. In this article, CNs (1) and (2) can reach synchronization even if the proposed model has unbounded time delays.
Remark 5.
The synchronization task of CNs with parameter uncertainty was investigated in [31,33,34,54]. The parameter uncertainty involved belonged to the outer coupling matrices [31,54], the connection weight matrices [33], and the nonlinear dynamics state of nodes [34]. In our article, the model considers the uncertainty of inner-coupling matrices, and novel μ-synchronization criteria of complex systems are derived. In addition, in [55], the impulsive synchronization of randomly coupled CNs was explored, in which the outer coupling matrices should satisfy the zero-row-sum condition. However, there is no need for the external coupling matrices in the proposed model to satisfy the dissipative coupling condition.
Based on Theorem 1, three specific cases are shown below, which indicates that the synchronization under the sense of power, log, and exponential can be achieved by our impulsive control scheme.
Corollary 1.
Proof.
Comparing the conditions of Theorem 1 and Corollary 1, if Assumption 4 holds, the conclusion of Corollary 1 is correct. Clearly, when , it is calculated that
Corollary 2.
Proof.
When , one can obtain that
Corollary 3.
4. Numerical Simulations
The experiments in this section are conducted to verify the correctness of the theoretical results in Section 3. The correctness of the conditions in Theorem 1 is verified through two numerical experiments.
Example 1.
First, the drive NNs containing 6 nodes with unbounded changeable delays and inner couplings of uncertainty are considered as
in which , , , , . The nonlinear functions are set as . It can be obtained that through a simple calculation, such that Assumption 1 holds. The response system is depicted as
The constant matrices , , are set, respectively, as
The certainty inner coupling matrices are set, respectively, as
The parametric uncertainties of internal coupling are selected, respectively, as
The topological matrices and are selected, respectively, as
Assumption 2 is satisfied with . Due to , Assumption 3 holds. The function and the delay parameter in Assumption 4 are set, respectively, as Let , , , , , , , , , , , and . Then, it can be obtained that , , , by calculation. According to the proof process of Corollary 1, Assumption 4 holds.
To satisfy the remaining conditions in Corollary 1, the following feasible solutions are obtained by using the Matlab LMI toolbox:
Hence, the control matrix Θ is set as
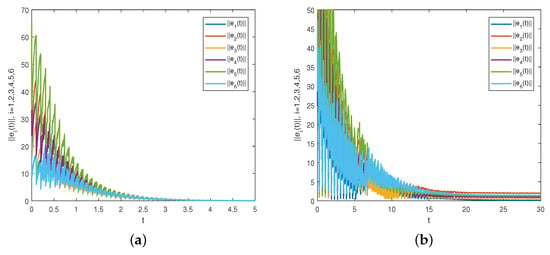
We randomly choose the initial values for six nodes from . The state trajectories of converging to 0 with respect to a proper value of Θ are presented in Figure 1a, which implies that CNs (20) and (21) have achieved synchronization. Figure 1b is a description of the non-synchronization result under an improper value of due to the state trajectories of not converging to 0. That is, CNs (20) and (21) cannot reach synchronization with respect to the changed value of matrix since the inequality condition in Corollary 1 no longer holds.

Remark 6.
By selecting a series of parameters whose values conform to the conditions in Theorem 1 through calculation, for example, the values of the parameters , a, γ, , , , , and T in the experiment conform to condition (i); the values of the parameters , , , , , , , , , , , , , , , , , , , , , , a, and N in the experiment conform to condition (ii); the values of the parameters , , , and in the experiment conform to condition (iii); and the values of the parameters γ, , Q, and in the experiment conform to condition (vi). Additionally, the correctness of the conditions in Theorem 1 is verified from the experimental results in Figure 1. Theoretical results and numerical experiments jointly demonstrate that uncertain time-delayed CNs can achieve μ-synchronization under the designed hybrid controller.
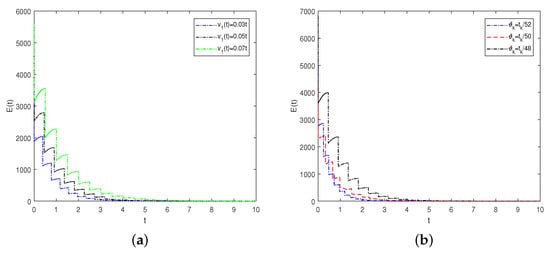
The changes in system parameters will significantly affect the synchronization stability of CNs. Our focus is on discussing two different types of time delays, namely, internal delays and impulsive delays. The total synchronization error of CNs (20) and (21) is defined as . First, we study the effect of fine-tuning the internal delay while keeping other network parameters unchanged. The internal delay gradually changes with as the initial value and as the step size, and the variation of the synchronization speeds can be seen in Figure 2a. Second, the impulsive delays are set to , , and , while the remaining parameters are kept unchanged. As can be seen in Figure 2b, the black, red, and blue curves denote the time evolution of the total synchronization error under the influence of different impulsive delays. Overall, the total synchronization error curves indicate that the efficiency of network synchronization slows down as the internal or impulsive delay increases.

Figure 2.
(a) Time evolution of under different internal delays . (b) Time evolution of under different impulsive delays .
Example 2.
Consider a complex nonlinear network composed of six neuron nodes, where each decoupled node satisfies the following chaotic system:
where is the state vector of the i-th node, and the bounded delay is set as .
The weight matrices are set as , , .
The nonlinear activation functions are set as
When the initial value of each node in this system is , the behavior of the system exhibits chaos [13]. For neural networks (22) that include both external and internal couplings, the external coupling function is set as
It can be obtained that using the inequality scaling principle, such that Assumption 1 holds.
Let the certainty inner coupling matrices be
The uncertainties of internal coupling are set, respectively, as
The values for the outer topological matrices and are set, respectively, as
Let ; then Assumption 2 is satisfied. Similarly as before, ; then Assumption 3 is satisfied. The function and the delay parameter in Assumption 4 are set, respectively, as Let , , , , , , , , , , , , , and . Then, we can obtain , , , and . Through the proof process of Corollary 3, Assumption 4 is satisfied.
To make the remaining conditions in Corollary 3 hold true, the following feasible solutions are obtained by using the Matlab LMI toolbox:
Then, the control gain matrix Θ is set as
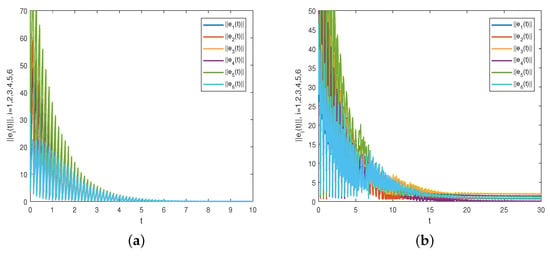
First, the conditions of Corollary 3 are satisfied by validation. Then, in Figure 3a, it can be observed that the state trajectories of under the useful matrix Θ converge to 0, which means that CNs (20) and (21) have achieved synchronization. On the other hand, Figure 3b is a display of the non-synchronization situation between CNs (20) and (21) through plotting the state trajectories of . The reason is that the value of the control matrix is changed to so that the conditions of Corollary 3 are no longer met. Furthermore, synchronization is not achieved with the time evolution of not converged to 0.

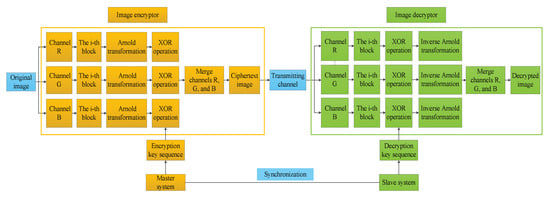
Next, network synchronization will be used for image encryption and decryption. A flowchart of the image encryption and decryption algorithm is shown in Figure 4. This scheme divides digital color images into three two-dimensional matrices by image channel. Divide each two-dimensional matrix into several sub-blocks and perform the Arnold transformation on pixel positions within each sub-block. Then, create a key using the sequence generated by the chaotic system, and encrypt each sub-block by the key. Finally, merge each of the three channels to obtain a color encrypted image.

Figure 4.
Flowchart of image encryption and decryption.
Let the colored digital image with size be the image to be encrypted. The encryption steps are as follows:
Step 1: Divide into three two-dimensional matrices, , , and , corresponding to channels R, G, and B, respectively.
Step 2: To enhance the universality of the algorithm, pad the three matrices , , and with values 0 so that their dimensions meet Equation (23).
Here, is the block size. The dimensions of the zero-padded image are and . According to Equation (23), the matrices , , and can be evenly divided into blocks of size . Therefore, each two-dimensional matrix can be divided into blocks after padding.
Step 3: The spatial position of image pixels can be changed by the discrete Arnold transformation, which is a two-dimensional reversible mapping and is often used as a permutation method in the image encryption field. Taking as an example, perform the discrete Arnold transformation on the position coordinates of the pixels in the image, that is,
where is the transformation matrix, and , represents the number of iterations. is the pixel coordinate in the i-th block of . Let be the image after the Arnold transformation, and is the coordinate of the corresponding pixel in the i-th block of . Similarly, by performing the Arnold transformation on the pixel coordinates in and , the images and can be obtained with changed pixel coordinates, respectively.
Step 4: Assume that two chaotic sequences generated by the chaotic system in the encryptor are as follows:
where , and the encrypted key sequence is calculated as
where is an adjustable integer, and , .
Step 5: After Arnold transformation, each of the pixel values in , , and ranges from 0 to 255, which can be represented by an 8-bit binary number. By performing a bitwise XOR operation between the pixel values of each sub-block of , and with , we can obtain the encrypted image in channels R, G, and B, respectively, as follows:
where ⊕ denotes the XOR operation, and , , and denote the i-th block of images , , and , respectively.
Step 6: The encrypted images from the three channels are merged to obtain the final encrypted image called .
The decryption process involves performing the reverse operation on the encrypted image, which is completely opposite to the encryption process. The image decryption process is as follows:
Step 1: Divide into three two-dimensional matrices, referred to as , , and , which correspond to channels R, G, and B, respectively.
Step 2: The decrypted chaotic sequence generated by the chaotic system in the decryptor is as follows:
Additionally, the decrypted key sequence is calculated as
where is an adjustable integer, and , .
Step 3: Decrypt the encrypted images of three channels using the key sequence as follows:
where , , and are the i-th block of images , , and , respectively. , , and denote the decrypted images of the channels R, G, and B in the first stage, respectively. , , and are the i-th block of images , , and , respectively.
Step 4: The position coordinates of the pixels in the images , , and are carried out by the inverse Arnold transformation as follows:
where denotes the inverse transformation matrix, , represents the number of iterations, and denotes the pixel’s position coordinate of the i-th block in the images , , and . Let , , and be the decrypted images after the inverse Arnold transformation in channels R, G, and B, respectively. denotes the position coordinate of the pixel in the i-th block of the images , , and .
Step 5: Remove the zero pixels of the images , , and padded during the encryption process; then the results are referred to as , , and , respectively.
Step 6: By merging three channels of the decrypted images , , and , we obtain the final decrypted image called .
Remark 7.
The decryption process must use exactly the same key as the encryption process to obtain the correct decrypted image. In other words, the response system and the driving system must be synchronized so that the chaotic sequences generated by the encryption and decryption ends are the same. Since the encryption key and the decryption key are identical, the decrypted image is indistinguishable from the original image.
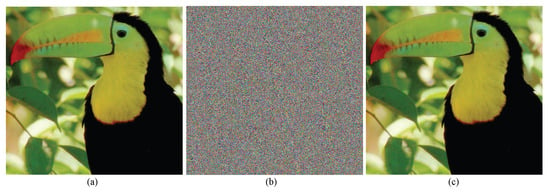
Use a color digital image “Parrot” as the image to be encrypted, as shown in Figure 5a. The encryption and decryption algorithm is simulated and verified on the Matlab R2024a platform in the Windows 10 operating system environment. Figure 5a–c show the original image, ciphertext image, and correctly decrypted image, respectively. From a visual perspective, the ciphertext image does not have a correlation with the original image.

Figure 5.
The results of encrypting and decrypting for the color digital image “Parrot”. (a) The original image; (b) the ciphertext image; (c) the decrypted image.
- (1)
- Histogram analysis.
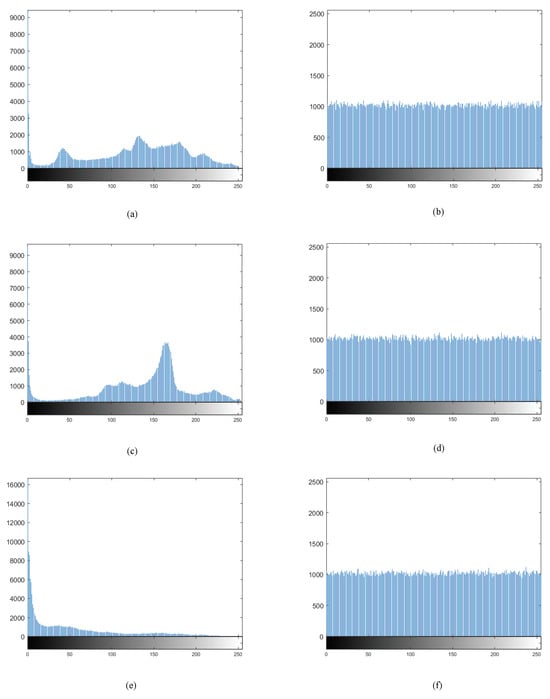
In the image histogram, the horizontal axis ranges from 0 to 255, and the vertical axis represents the frequency of the value of each pixel appearing in the entire image. Therefore, the distribution of pixel values in the image can be reflected through the histogram. Figure 6a–f show the histograms of the R, G, and B channels of the image before and after encryption, respectively. From Figure 6, it can be seen that the histograms of channels R, G, and B in the original image fluctuate, while the histograms of the three channels in the ciphertext image are evenly distributed and have pseudo-random properties, which can hide the statistical characteristics of the original image and effectively resist histogram-based statistical attacks on images.

Figure 6.
Histogram of image “Parrot” in three channels before and after encryption. (a) Histogram of R component before encryption; (b) histogram of encrypted R component; (c) histogram of G component before encryption; (d) histogram of encrypted G component; (e) histogram of B component before encryption; (f) histogram of encrypted B component.
- (2)
- Correlation of pixel values between adjacent positions.
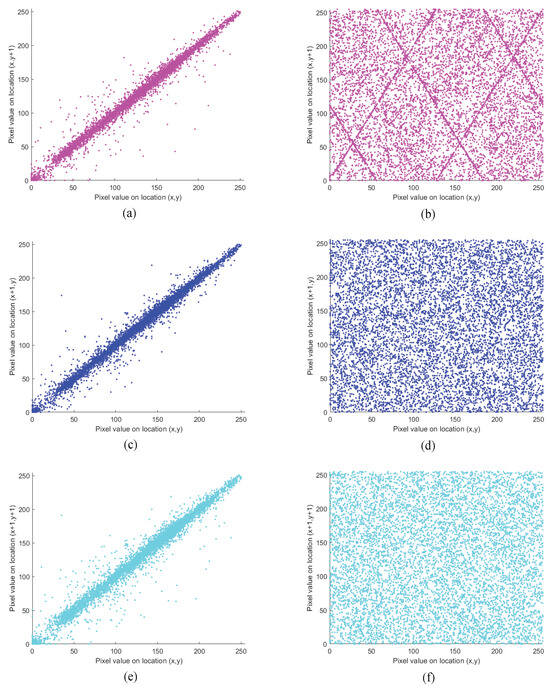
The ability of an image to resist attacks is inversely proportional to the correlation between its adjacent pixel values. To test the resistance of the image to attacks, 5000 pairs of adjacent pixels are randomly selected in the horizontal, vertical, and diagonal directions for correlation analysis. To compare the correlation of pixel values between adjacent positions of images before and after encryption more intuitively, a point graph is drawn in Figure 7, with the horizontal axis representing the pixel values of random point positions and the vertical axis representing the pixel values of adjacent positions.

Figure 7.
Correlation between adjacent pixel values of images before and after encryption. (a) Correlation between horizontally adjacent pixels in the original image; (b) correlation between horizontally adjacent pixels in the ciphertext image; (c) correlation between vertically adjacent pixels in the original image; (d) correlation between vertically adjacent pixels in the ciphertext image; (e) correlation between adjacent pixels in the diagonal direction of the original image; (f) correlation between adjacent pixels in the diagonal direction of the ciphertext image.
Figure 7a–b show the correlation coefficient plots of pixel values between adjacent positions of images before and after encryption in the horizontal direction, respectively. Figure 7c–d show the correlation coefficient plots of pixel values between adjacent positions of images before and after encryption in the vertical direction, respectively. Figure 7e–f show the correlation coefficient plots of pixel values between adjacent positions of images before and after encryption in the diagonal direction, respectively. It can be seen that the pixel values of adjacent positions in all three directions of the original image have strong correlation, and the distribution of pixel points shows a linear relationship. The correlation between adjacent pixel values in all three directions in the ciphertext image is almost zero, and the distribution of pixel points is completely random. Therefore, there is no correlation between the distribution of adjacent pixel values in the ciphertext image, whether in horizontal, vertical, or diagonal directions. This encryption algorithm completely changes the pixel values and shuffles pixel positions of the original image, and thus has strong resistance to attacks.
- (3)
- Information entropy analysis.
Information entropy represents the degree of confusion of information in a system; therefore, in an image, information entropy represents the confusion degree of the pixel values in the image. It is defined as follows:
where represents the proportion of pixel value in the image. According to Equation (32), the maximum theoretical information entropy of an image is 8. After calculation, the information entropy of the original image is , and the information entropy of the ciphertext image is . It can be seen that the information entropy of the ciphertext image is very close to the maximum theoretical information entropy value, indicating that the degree of chaos in the ciphertext image is approaching the theoretical limit. Therefore, this encryption algorithm can effectively resist attacks based on image information entropy.
- (4)
- Analysis of key capacity.
A good encryption algorithm requires a sufficiently large key space, generally not less than . In this scheme, the size of the key space is simply estimated as
where denotes the number of nodes in the network and in the experiment. is a positive integer related to the precision of computer floating-point numbers, with a value of 14. It can be obtained that the key space of the proposed scheme is much larger than , which can effectively resist brute-force attacks.
5. Conclusions
With the purpose of achieving -synchronization for the proposed CNs, our work studies the -synchronization task for CNs subjected to uncertain inner couplings, unbounded time delays, and external disturbances. For the CNs studied, there is no need for the coupling topology to satisfy the zero-row-sum condition, allowing for the application of the network more widespread. The three types of time delays are unbounded, which makes the model and results better applied to real engineering scenarios, such as image encryption. Several milder sufficient conditions are gained utilizing the new hybrid pulse control technique, under which the considered CNs can reach -synchronization. To sum up, we adopt the hybrid pulse controller containing both the error feedback information and the pulse control factor to make the proposed CNs achieve -synchronization by the Lyapunov method. In the future, one field of focus will be the finite-time synchronization of fuzzy CNs with high-order topologies via adaptive event-triggering impulsive control.
Author Contributions
Conceptualization, A.Z., C.Y. (Chengbo Yi) and H.F.; methodology, A.Z., C.Y. (Chongming Yang) and C.Y. (Chengbo Yi); software, A.Z. and H.F.; writing—original draft, A.Z. and H.F.; writing—review and editing, A.Z., C.Y. (Chongming Yang), C.Y. (Chengbo Yi) and H.F.; Funding acquisition, C.Y. (Chongming Yang). All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Guangdong Provincial Key Laboratory (Grant 2023B1212060076), the High-Level Talent Initiation Project of Shenzhen Polytechnic University (Grant 6024330003K), the R&D Center for CNOOC Equipment (Shenzhen) Offshore Engineering Technology, Shenzhen Polytechnic University (Grant 602331006PQ), and the Research Projects of Department of Education of Guangdong Province (Grant 2024KQNC034).
Data Availability Statement
The data that support the findings of this study are available within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
Definition A1
Remark A1.
acts as a bridge to obtain different types of synchronization. By selecting different , the synchronization can be converted to other synchronizations. Considering setting different functions, for example, if is set to , and , respectively, then the μ-synchronizations are correspondingly turned into power synchronization, exponential synchronization, and logarithmic synchronization, in which , , , .
Lemma A1
([11]). There exist real matrix and such that
Lemma A2
([13]). The matrix inequality below
holds, if the matrices , , and satisfy one of the following conditions,
where and .
Lemma A3
([49]). The two inequality conditions with regard to
are assumed to be satisfied under Assumption 4, in which , , , , , , n, . If there are constants , satisfying
and
then the following relationship with respect to can be gained
in which is the supremum of in the interval .
References
- Zhu, S.; Zhou, J.; Chen, G.; Lu, J.A. A new method for topology identification of complex dynamical networks. IEEE Trans. Cybern. 2021, 51, 2224–2231. [Google Scholar] [CrossRef] [PubMed]
- Wang, S.; Shi, K.; Wang, J.; Yu, Y.; Wen, S.; Yang, J.; Han, S. Synchronization sampled-data control of uncertain neural networks under an asymmetric Lyapunov-Krasovskii functional method. Expert Syst. Appl. 2024, 239, 122475. [Google Scholar] [CrossRef]
- Dorfler, F.; Bullo, F. Synchronization in complex networks of phase oscillators: A survey. Automatica 2014, 50, 1539–1564. [Google Scholar] [CrossRef]
- Sultornsanee, S.; Radhakrishnan, S.; Falco, D.; Zeid, A.; Kamarthi, S. Phase synchronization approach to construction and analysis of stock correlation network. Procedia Comput. Sci. 2011, 6, 52–56. [Google Scholar] [CrossRef]
- Chen, W.W.; Li, H.L. Complete synchronization of delayed discrete-time fractional-order competitive neural networks. Appl. Math. Comput. 2024, 479, 128872. [Google Scholar] [CrossRef]
- Shen, Y.; Liu, X.Z. Generalized synchronization of delayed complex-valued dynamical networks via hybrid control. Commun. Nonlinear Sci. Numer. Simul. 2023, 118, 107057. [Google Scholar] [CrossRef]
- Gao, L.; Cai, Y. Finite-time stability of time-delay switched systems with delayed impulse effects. Circuits Syst. Signal Process. 2016, 35, 3135–3151. [Google Scholar] [CrossRef]
- Liu, X.; Chen, T. Finite-time and fixed-time cluster synchronization with or without pinning control. IEEE Trans. Cybern. 2018, 48, 240–252. [Google Scholar] [CrossRef] [PubMed]
- Fan, H.G.; Chen, X.J.; Shi, K.B.; Liang, Y.H.; Wang, Y.; Wen, H. Mittag-Leffler synchronization in finite time for uncertain fractional-order multi-delayed memristive neural networks with time-varying perturbations via information feedback. Fractal Fract. 2024, 8, 422. [Google Scholar] [CrossRef]
- Fan, H.G.; Rao, Y.; Shi, K.B.; Wen, H. Time-varying function matrix projection synchronization of Caputo fractional-order uncertain memristive neural networks with multiple delays via mixed open loop feedback control and impulsive control. Fractal Fract. 2024, 8, 301. [Google Scholar] [CrossRef]
- Fan, H.G.; Chen, X.J.; Shi, K.B.; Wen, H. Distributed delayed impulsive control for μ-synchronization of multi-link structure networks with bounded uncertainties and time-varying delays of unmeasured bounds: A novel Halanay impulsive inequality approach. Chaos Solitons Fractals 2024, 186, 115226. [Google Scholar] [CrossRef]
- Zhang, W.; Xiao, J.; Gong, B.Y. Global μ-synchronization for coupling delayed complex dynamical networks via event-triggered delayed impulsive control. ISA Trans. 2024, 145, 124–131. [Google Scholar] [CrossRef] [PubMed]
- Fan, H.G.; Xiao, Y.; Shi, K.B.; Wen, H.; Zhao, Y. μ-synchronization of coupled neural networks with hybrid delayed and non-delayed impulsive effects. Chaos Solitons Fractals 2023, 173, 113620. [Google Scholar] [CrossRef]
- Guan, K.Z.; Cai, Z.W. Impulsive μ-stabilization and μ-synchronization for delayed network systems with any time-varying delays. Neurocomputing 2020, 411, 498–509. [Google Scholar] [CrossRef]
- Chen, H.B.; Shi, P.; Lim, C.C. Pinning impulsive synchronization for stochastic reaction-diffusion dynamical networks with delay. Neural Netw. 2018, 106, 281–293. [Google Scholar] [CrossRef]
- Liang, J.C.; Liu, J.; Tse, C.K.; Liu, M.X. Observer-based aperiodically intermittent pinning synchronization of complex-valued dynamical networks with time-varying delay. Phys. A 2024, 635, 129516. [Google Scholar] [CrossRef]
- Fan, H.G.; Shi, K.B.; Guo, Z.Z.; Zhou, A.R. Finite-time synchronization criteria for Caputo fractional-order uncertain memristive neural networks with fuzzy operators and transmission delay under communication feedback. Fractal Fract. 2024, 8, 619. [Google Scholar] [CrossRef]
- Jiang, G.H.; Wang, L.M.; Hu, X.F.; Li, H.Y.; Zong, X.F. Semiglobal fixed/preassigned-time synchronization of stochastic neural networks with random delay via adaptive control. Neurocomputing 2024, 593, 127832. [Google Scholar] [CrossRef]
- Zhang, S.; Xu, J.J.; Zhang, H.S. Decentralized control of forward and backward stochastic difference system with nested asymmetric information. Appl. Math. Comput. 2024, 478, 128834. [Google Scholar] [CrossRef]
- Wang, S.; Shi, K.; Cao, J.; Wen, S. Fuzzy adaptive event-triggered synchronization control mechanism for T-S fuzzy RDNNs under deception attacks. Commun. Nonlinear Sci. Numer. Simul. 2024, 134, 107985. [Google Scholar] [CrossRef]
- Ruan, Z.Y.; Li, Y.Y.; Hu, J.H.; Mei, J.; Xia, D. Finite-time synchronization of the drive-response networks by event-triggered aperiodic intermittent control. Neurocomputing 2022, 485, 89–102. [Google Scholar] [CrossRef]
- Zhang, L.Z.; Lu, J.Q.; Jiang, B.X.; Zhong, J. Impulsive synchronization control for dynamic networks subject to double deception attacks. Expert Syst. Appl. 2024, 251, 124000. [Google Scholar] [CrossRef]
- Liu, X.W.; Li, Z.H. Finite time anti-synchronization of complex-valued neural networks with bounded asynchronous time-varying delays. Neurocomputing 2020, 387, 129–138. [Google Scholar] [CrossRef]
- Luo, Y.P.; Yao, Y.J. Finite-time synchronization of uncertain complex dynamic networks with time-varying delays. Adv. Differ. Equ. 2020, 32, 32. [Google Scholar] [CrossRef]
- Tan, Y.X.; Huang, Z.K. Synchronization of drive-response networks with delays on time scales. IEEE/CAA J. Autom. Sin. 2024, 11, 1063–1065. [Google Scholar] [CrossRef]
- Han, M.; Zhang, Y.M. Complex function projective synchronization in drive-response complex-variable dynamical networks with coupling time delays. J. Frankl. Inst. 2016, 353, 1742–1758. [Google Scholar] [CrossRef]
- Wang, L.M.; Hu, Y.Q.; Hu, C.; Zhou, Y.J.; Wen, S.P. Finite-time synchronization of delayed fuzzy inertial neural networks via intermittent control. Neurocomputing 2024, 574, 127288. [Google Scholar] [CrossRef]
- Wang, L.M.; Li, H.Y.; Hu, C.; Hu, J.H.; Wang, Q.Y. Synchronization and settling-time estimation of fuzzy memristive neural networks with time-varying delays: Fixed-time and preassigned-time control. Fuzzy Sets Syst. 2023, 470, 108654. [Google Scholar] [CrossRef]
- Rakkiyappan, R.; Chandrasekar, A.; Petchiammal, G. Non-fragile robust synchronization for Markovian jumping chaotic neural networks of neutral-type with randomly occurring uncertainties and mode-dependent time-varying delays. ISA Trans. 2014, 53, 1760–1770. [Google Scholar] [CrossRef] [PubMed]
- Xing, R.T.; Xiao, M.; Zhang, Y.Z.; Qiu, J.L. Stability and Hopf bifurcation analysis of an (n plus m)-neuron double-ring neural network model with multiple time delays. J. Syst. Sci. Complex. 2022, 35, 159–178. [Google Scholar] [CrossRef]
- He, J.M.; Pei, L.J. Function matrix projection synchronization for the multi-time delayed fractional order memristor-based neural networks with parameter uncertainty. Appl. Math. Comput. 2023, 454, 128110. [Google Scholar] [CrossRef]
- Gu, Y.J.; Yu, Y.G.; Wang, H. Synchronization for fractional-order time-delayed memristor-based neural networks with parameter uncertainty. J. Frankl. Inst. 2016, 353, 3657–3684. [Google Scholar] [CrossRef]
- Fan, H.G.; Shi, K.B.; Wen, H.; Zhao, Y. Synchronization of multi-weighted complex networks with mixed variable delays and uncertainties via impulsive pinning control. Phys. D 2023, 456, 133935. [Google Scholar] [CrossRef]
- Selvaraj, P.; Kwon, O.M.; Sakthivel, R. Disturbance and uncertainty rejection performance for fractional-order complex dynamical networks. Neural Netw. 2019, 112, 73–84. [Google Scholar] [CrossRef] [PubMed]
- Mirshamsi, A.; Nobakhti, A. Uncertainty disturbance estimator control for delayed linear systems with input constraint. Automatica 2024, 167, 111763. [Google Scholar] [CrossRef]
- Wen, G.; Yu, X.; Yu, W.; Lu, J. Coordination and control of complex network systems with switching topologies: A survey. IEEE Trans. Syst. Man Cybern. Syst. 2020, 51, 6342–6357. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, Y.; Gunasekaran, N.; Vadivel, R. Almost sure consensus of multi-agent systems: An intermittent noise. IEEE Trans. Circuits Syst. II 2022, 69, 2897–2901. [Google Scholar] [CrossRef]
- Tirandaz, H. Adaptive modified projective synchronization of gyroscopes with unknown parameters and external disturbances. ICIC Express Lett. 2018, 12, 287–294. [Google Scholar]
- Du, H.Y. Function projective synchronization in complex dynamical networks with or without external disturbances via error feedback control. Neurocomputing 2016, 173, 1443–1449. [Google Scholar] [CrossRef]
- Du, H.Y. Modified function projective synchronization between two fractional-order complex dynamical networks with unknown parameters and unknown bounded external disturbances. Phys. A 2019, 526, 120997. [Google Scholar] [CrossRef]
- Ze, T.; Park, J.H.; Lee, T.H.; Feng, J.W. Mean square exponential synchronization for impulsive coupled neural networks with time-varying delays and stochastic disturbances. Complexity 2016, 21, 190–202. [Google Scholar]
- Zhao, Y.S.; Li, X.D.; Rao, R.F. Synchronization of nonidentical complex dynamical networks with unknown disturbances via observer-based sliding mode control. Neurocomputing 2021, 454, 441–447. [Google Scholar] [CrossRef]
- Liang, T.; Zhang, W.L.; Yang, D.G. Fixed-time synchronization of switched duplex networks with stochastic disturbances and limited communication. Commun. Nonlinear Sci. Numer. Simul. 2023, 121, 107227. [Google Scholar] [CrossRef]
- Ren, H.W.; Shi, P.; Deng, F.Q.; Peng, Y.J. Fixed-time synchronization of delayed complex dynamical systems with stochastic perturbation via impulsive pinning control. J. Frankl. Inst. 2020, 357, 12308–12325. [Google Scholar] [CrossRef]
- Shukla, V.K.; Joshi, M.C.; Mishra, P.K.; Xu, C.J. Mechanical analysis and function matrix projective synchronization of El-Nino chaotic system. Phys. Scr. 2025, 100, 015255. [Google Scholar] [CrossRef]
- Liu, X.Z.; Zhang, K.X. Synchronization of linear dynamical networks on time scales: Pinning control via delayed impulses. Automatica 2016, 72, 147–152. [Google Scholar] [CrossRef]
- Li, X.D.; Song, S.J.; Wu, J.H. Exponential stability of nonlinear systems with delayed impulses and applications. IEEE Trans. Autom. Control 2019, 64, 4024–4034. [Google Scholar] [CrossRef]
- Zhang, L.; Yang, X.S.; Xu, C.; Feng, J.W. Exponential synchronization of complex-valued complex networks with time-varying delays and stochastic perturbations via time-delayed impulsive control. Appl. Math. Comput. 2017, 306, 22–30. [Google Scholar] [CrossRef]
- Fan, H.G.; Shi, K.B.; Zhao, Y. Global μ-synchronization for nonlinear complex networks with unbounded multiple time delays and uncertainties via impulsive control. Phys. A 2022, 599, 127484. [Google Scholar] [CrossRef]
- Liu, L.F.; Liu, K.; Xiang, H.Y.; Liu, Q. Pinning impulsive cluster synchronization of complex dynamical networks. Phys. A 2020, 545, 123580. [Google Scholar] [CrossRef]
- Peng, D.X.; Li, X.D. Leader-following synchronization of complex dynamic networks via event-triggered impulsive control. Neurocomputing 2020, 412, 1–10. [Google Scholar] [CrossRef]
- Karthick, S.A.; Sakthivel, R.; Alzahrani, F.; Leelamani, A. Synchronization of semi-Markov coupled neural networks with impulse effects and leakage delay. Neurocomputing 2020, 386, 221–231. [Google Scholar] [CrossRef]
- Furtat, I.B. Robust synchronization of the structural uncertainty nonlinear network with delay and disturbances. IFAC Proc. Vol. 2013, 46, 227–232. [Google Scholar] [CrossRef]
- Jia, T.Y.; Chen, X.Y.; He, L.P.; Zhao, F.; Qiu, J.L. Finite-time synchronization of uncertain fractional-order delayed memristive neural networks via adaptive sliding mode control and its application. Fractal Fract. 2022, 6, 502. [Google Scholar] [CrossRef]
- Chandrasekar, A.; Rakkiyappan, R.; Cao, J.D. Impulsive synchronization of Markovian jumping randomly coupled neural networks with partly unknown transition probabilities via multiple integral approach. Neural Netw. 2015, 70, 27–38. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).