1. Introduction
Graphs are a common method to visually illustrate relationships in data. The purpose of a graph is to present data that are too numerous or complicated to be described adequately in the text and in less space. The fuzzy graph (FG) theory is an important area of research that is the backbone of representations of any network with ambiguity. Crisp graphs are not sufficient to capture the uncertainty of parameters in networks, for example, strong relationships and effective, influential or popular persons. Zadeh [
1] introduced the subject of a fuzzy set (FS) in 1995. Rosenfeld [
2] proposed the subject of FGs. The definitions of FGs from the Zadeh fuzzy relations in 1973 were presented by Kaufmann [
3]. Bhutani and Rosenfeld [
4] explained the concept of strong edge (SE) in FGs. FGs and their generalizations have played an essential role in dealing with real-life problems involving uncertainties. Gau and Buehrer [
5] proposed the concept of a vague set (VS) by replacing the value of an element in a set with a sub interval of [0, 1]. Moreover, a VG can concentrate on determining the uncertainties coupled with the inconsistent and indeterminate information of any real-world problems where FGs may not lead to adequate results. Ramakrishna in [
6] proposed a new concept of VGs, belonging to the FGs family, which had good capabilities when faced with problems that could not be expressed by FGs. The notion of a VG is a new mathematical attitude to model the ambiguity and uncertainty in decision-making issues. Study on VG and results from these graphs were introduced by Kosari et al. [
7,
8,
9,
10]. Furthermore, a review was carried out on different types of FGs, and the new results were studied [
11,
12,
13]. In graph theory, a dominating set (DS) for a graph G is a subset
D of its vertices, such that any vertex of G is either in
D or has a neighbor in
D. The domination number
is the number of vertices in a smallest DS for G. DSs are of practical interest in several areas. In wireless networking, DSs are used to find efficient routes within ad hoc mobile networks. They have also been used in document summarization and in designing secure systems for electrical grids. The concept of DS in FGs, both theoretically and practically, is very valuable. A DS in FGs is used for solving problems of different branches in applied sciences such as location problems. In this way, the study of new concepts such as DS is essential in FG. Domination in VGs has applications in several fields. Domination emerges in the facility location problems, where the number of facilities is fixed and one endeavors to minimize the distance that a person needs to travel to get to the closest facility. Selvam et al. [
14] proposed the issue of domination in the join of FGs using SE. Domination in the join of incidence FGs using strong pairs was defined by Nazeer et al. [
15]. Notes on domination and strong domination and total domination in FGs were introduced by Manjusha and Sunitha [
16,
17,
18].
FGs are unable to give information about the impact of vertices on the edges. This shortage in FGs was the basic problem which is covered by
-FGs. It was Dinesh who introduced the extension of FGs known as
-FGs, which give information regarding the effect of vertices on the edges [
19].
VIGs can represent natural flow networks with extra illegal flow conditions. They have been used in physical problems related to networking and trafficking. Through this paper, the connectivity thoughts in VIG are extended along with the study of several fundamental properties of such graphs. Special influence vertices are studied and the relationships between several influence parameters have been found.
Mathew et al. [
20,
21] expressed the notions of fuzzy end vertices for
-FGs. Natarajan et al. [
22] studied strong (weak) domination in FGs. Certain properties of domination in VG products were explained by Shi et al. [
23]. New results on VG were reported by Akram et al. [
24,
25]. Borzooei et al. [
26] explained the new definition of domination in VGs. Double domination in VGs was developed by Banitalebi [
27]. Some properties of double domination in VGs were defined by [
28]. New results of FGs were presented by Rashmanlou et al. [
29,
30]. The concept of a strong pair domination number in intuitionistic
-FGs was introduced by Rehman et al. [
31]. Poulik et al. [
32] presented the Randic index in graphs.
1.1. Methodology and Importance of VIG
The idea of VIG is proposed for three reasons. First, FGs are not able to provide the effect of vertices on the edges, and this flaw is covered by -FGs, but they only provide the effect of a vertex on an edge and not on all the edges of the graph. The effect of vertices on any edge of the graph is given in VIGs. However, VIGs are incapable of intimating the degree of non-membership of the vertices, edges and -pairs. This is the main reason behind the idea of VIGs.
Second, it broadens the ideas of domination, minimal strong fuzzy in -pair DS and minimum strong -pair domination number in VIGs.
Third, there is a vertex m along with an edge , and they are not connected. Then, by using the influence theory, an -path can be generated between vertex m to vertices and edge . Lastly, -FG shows the effect of a vertex on which vertices are connected with it only, whereas VIGs are capable of reflecting not only the impact of a vertex on any edge of the graph but also providing the effect of a vertex of a graph on the edge of the other graph. In the FG theory, there was no such concept .
1.2. Research Gaps and Motivation of Study
The following points influenced us to write this article:
Due to the enormous applications of domination in FGs, including domination for FGs in distinct decision-making problems, it seems advantageous to expand the notion of domination in VIG.
There are numerous applications of the domination in VIG in chemistry, computer science, psychology, and others.
Moreover, some basic notions related to domination such as walk, path, strength of -pair, strong -pair, and -cut vertex have not yet been discussed and studied in the literature, and therefore, we expanded the notion of domination of -FG to the domination of VIG, and the strong pair domination number is investigated.
1.3. Contribution of This Study
VGs provide tools for modeling different types of real-world networks. However, we should consider more relations, especially the relationship between edges with their corresponding vertices, which usually refer to incidences where external factors influence the real flow in a network. Then, VIGs may sometimes model certain real-world situations better. In this regard, we introduce dominating sets in VIGs by using influence edges due to the importance of the concept of domination and its application in various issues.
Domination in VG theory is one of the most widely used topics in other sciences, including psychology, computer science, nervous systems, artificial intelligence, decision-making theory, and combinations of them. VIGs are highly practical tools for the study of different computational intelligence and computer science domains. Dominations in VIGs have many applications, such as, in wireless networking, dominations are used to find efficient routes within networks. They have also been used in document summarization and in designing secure systems for electrical grids, ect.
Hence, in this study, we extended the -FG notion to the VIG and discussed the well-known problems of domination, walk, path, -pair, strong -pair and -cut vertex on VIG. Likewise, we introduced the new concepts of the strong pair domination number in VIGs. Finally, an application of domination in illegal drug trade was introduced.
2. Preliminaries
In this part, we study some essential definitions and notions of graphs. Such as, FGs, VGs and domination sets. Before stating the definitions, we fix some notations for graphs and sets.
Definition 1 ([
33])
. A graph is a pair , where X is called the vertex set and is called the edge set. Definition 2. Given a crisp graph , a subset of vertices is called a DS, if for every vertex , there is a vertex such that .
Definition 3 ([
34])
. In graph theory, a path in a graph is a finite or infinite sequence of edges which joins a sequence of vertices which, by most definitions, are all distinct (and since the vertices are distinct, so are the edges). Paths are fundamental concepts of graph theory, described in the introductory sections of most graph theory texts. Definition 4 ([
33])
. An FG is a pair of function and such that, for all , Definition 5. A path of length l in an FG is a sequence of distinct vertices such that . The degree of membership value (MV) of a weakest edge is defined as its strength. The strength of connectedness between two vertices m and n is defined as the maximum (MA) of the strength of all paths between m and n and is denoted by or .
An edge is called an SE if . If for each , then n is named an isolated vertex. If is an SE, then its weight is at least as great as the strength of the connectedness of its end vertices when it is deleted. Note that, is the strength of the connectedness between m and n in an FG obtained from by deleting the edge
Definition 6. Let be an FG. Any edge is called effective edge if .
Definition 7 ([
5])
. A vague set (VS) is a pair on a set X, where and are real- valued functions which can be defined from X to , so that Definition 8 ([
6])
. A pair is called a VG on graph , where is a VS on X and is a VS on E such thatfor all . Note that is called a vague relation on . A VG is named strong iffor all Definition 9. Suppose is a VG. Then,
- (i)
A path in is a sequence of distinct vertices where , , . The length of is q.
- (ii)
If is a path between m and n of length q, then and .
is named the strength of connectedness between any two vertices m and n in where and .
Definition 10. Let be a crisp graph. Then, the triad in which is called -graph. An element of K is called an -pair.
Definition 11. Let be an -graph. A triad , where and λ are fuzzy subsets of and K, respectively, is called an -FG of , if . A vertex m and an edge are connected if there exists a path between them. The vertices are connected if there exists a path between them.
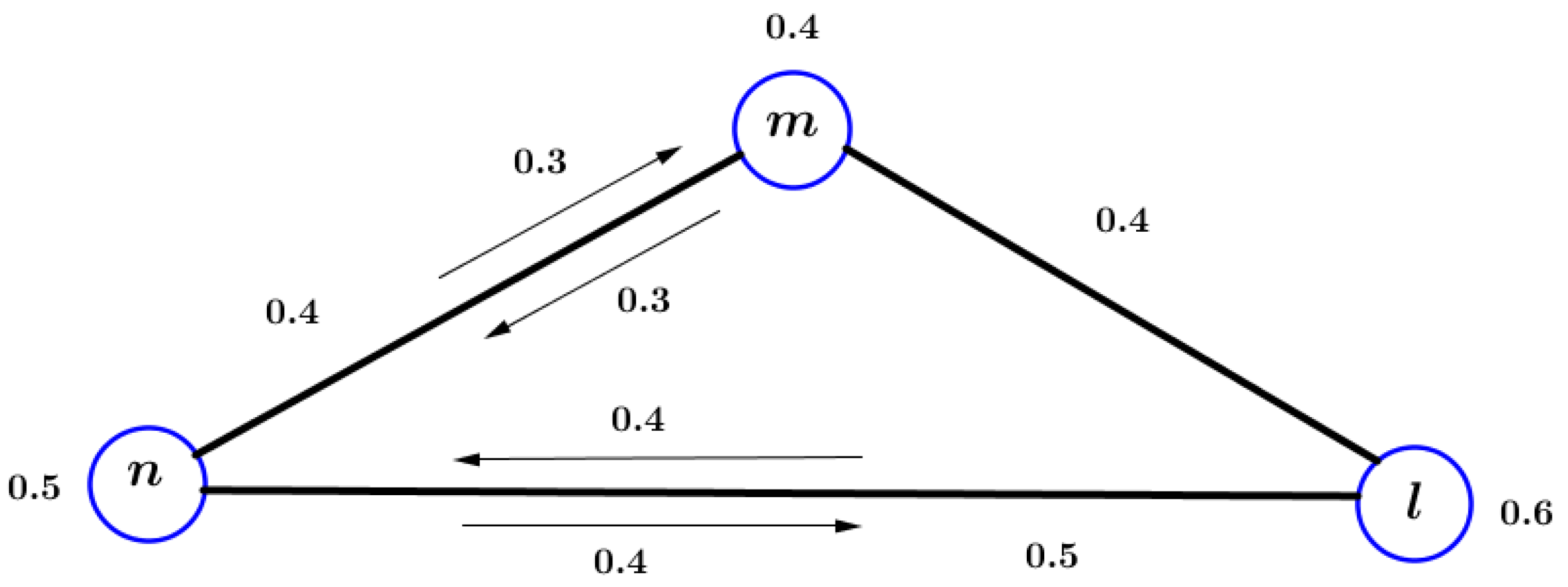
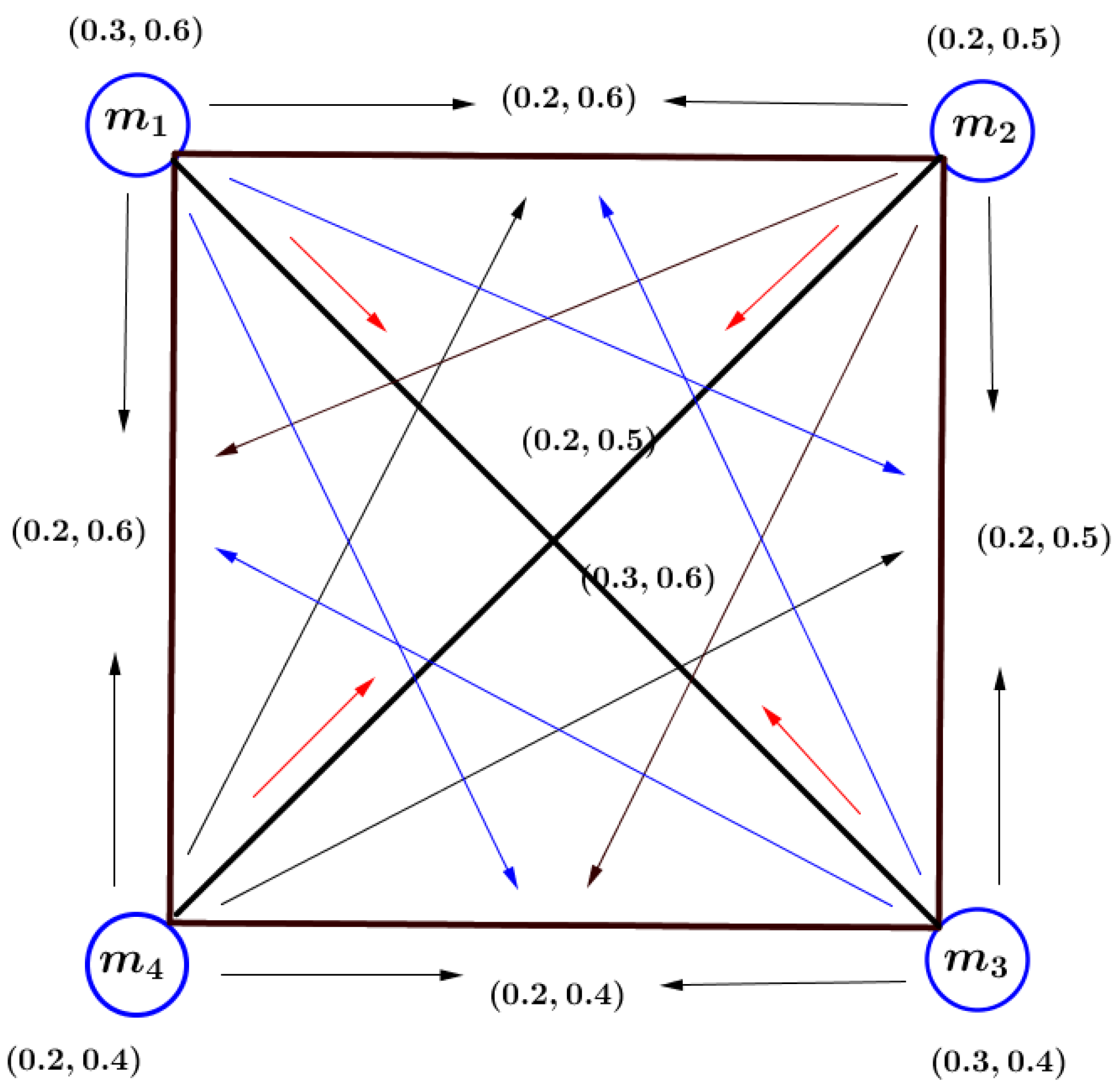
Example 1. Consider the -FG presented in Figure 1. In this -FG, we have and and . In this -FG, the vertices are connected vertices because there exist a path between them. Definition 12. An -FG of an -graph is complete -FG, if .
Definition 13. Let be an FG with any two vertices m and n. A vertex m dominates the vertex n if . A subset of the set X is called an SE DS if for every such that m dominates n. A DS is called MIL DS if there is no proper subset of that is DS. The effective edge domination number is the MIL fuzzy cardinality created from all MIL DS and is shown by , and the related set is known as MIL effective edge DS.
List of abbreviations used throughout this paper.
stands for “Fuzzy Set”;
stands for “Fuzzy Graph”;
stands for “Vague Set”;
stands for “Vague Graph”;
stands for “Vague influence Graph”;
stands for “Influence”;
stands for “Domination Set”;
stands for “Strong Edge”;
stands for “Cut Pair”;
stands for “Membership Value”;
stands for “Maximum”;
stands for “Minimum”;
stands for “Minimal”.
3. Vague Influence Graphs
In this section, we study a new notion of the influence graph and influence pair domination set on VGs. Namely, we obtain the domination set on VIGs. Furthermore, some properties of VIGs are established.
Definition 14. A triad is called a VIG on graph , where is a VS on X, and is a VS on E, and is a VS on K, such thatfor all . Definition 15. Consider that is a VIG. The vertex m and an edge are shown as connected if there exists a path of between them.
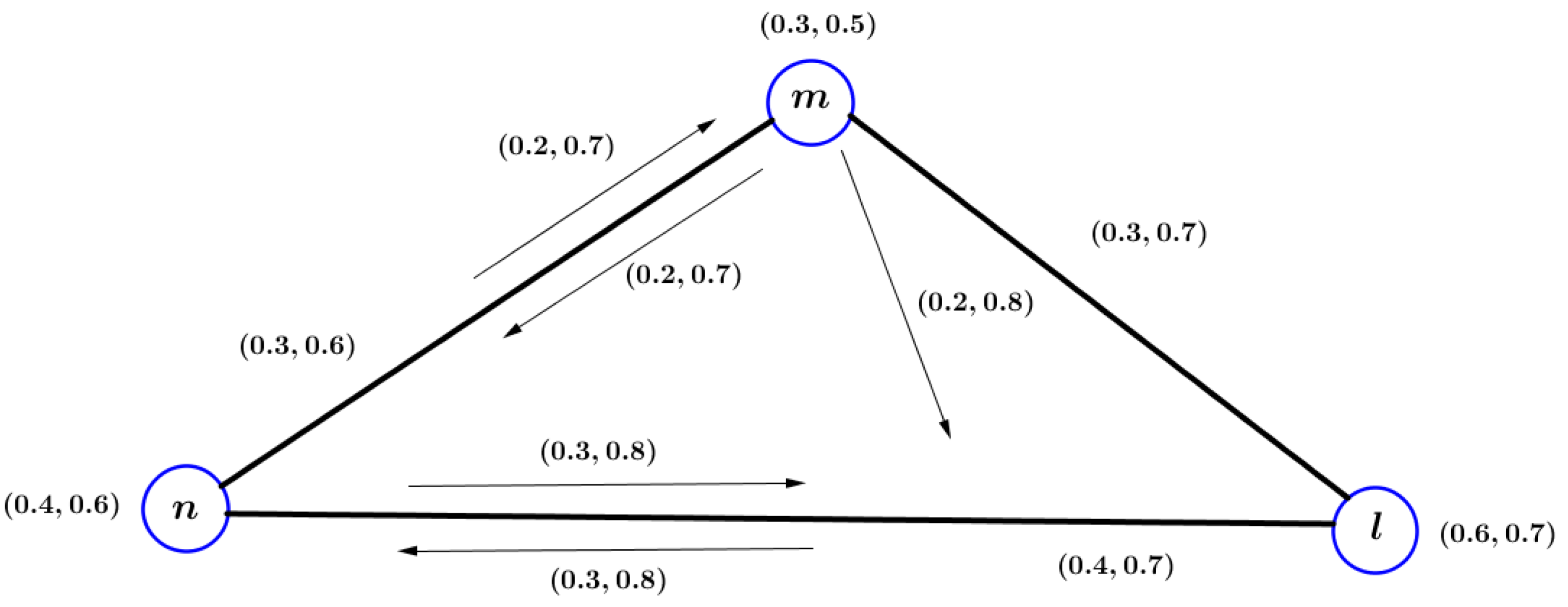
Example 2. Consider a VIG presented in Figure 2. In this VIG, we have and and . In this VIG, vertex m and an edge are shown as connected because there exists a path of between them. Definition 16. Let be a VIG. If it involves an -pair then is VIG. A sequence is a walk in , and it is an () path, whereas is also an () path. Every two vertices in VIG are known to be connected if there exists any -pair between them. Here, is an -pair as and l are distinct. This -pair shows the influence of vertex m on the edge .
Definition 17. Suppose is a VIG. An -pair in is named effective if Definition 18. Let be a VIG. Then, the influence of path indicated by and is described as, , , where and show the MV and the non-MVs of -pair lies in the path exists between m to .
Definition 19. Let be a VIG. An -pair is known as strong if . An -pair is known as the strongest In-pair if . An -pair is known as weak if .
Definition 20. Let be a VIG. The greatest -strength between m and is the highest MV with lowest non-MV from all the -paths between m to which is represented by and is defined and .
Theorem 1. Let be a VIG. If is a strong -pair, then involves a strong -path .
Proof. Suppose is a VIG. Then, a pair is an effective -pair if and . Now, consider that is an -path . Any -pair incident from m to can not have -MV more than . Similarly, any -pair which is influenced at can not have -MV more than . It means that the -path has -strength from MVs as and -strength from non-MVs as . Therefore, becomes the strong -path with the effective -pair. □
Theorem 2. Let be a VIG. If the -path involves the alone -pair, then the -pair should be strong.
Proof. Suppose is a VIG with an -pair and . Suppose the -pair is not a strong -pair, then , which is just possible if there exist any other -path that is a contradiction. Thus, if the -path contains the alone -pair, then the -pair should be strong. □
Theorem 3. Let be a VIG. If , then is known as strong -pair.
Proof. Suppose is a VIG. Let the -pair be not a strong -pair. Then, there is any -path so that the highest -strength of . Clearly, there is for every . This shows that there is any -pair that is a strong -pair, which is a contradiction. Therefore, if , then is known as a strong -pair. □
Theorem 4. Suppose is a VIG having a strong -pair, then it must be a strong -pair.
Proof. Suppose is a VIG having a strong -pair . Then, by using the definition of a strong -pair in , we have and . Suppose , then . So, for any -path , the influence of . By using Theorem 1, the -path involves the alone -pair, then the should be strong, and according to Theorem 2, the -pair having MA degree of MV should be a strong -pair. As the -pair is alone and has MA degree of MV, we have . Now, suppose , then . So, for any -path , the influence of . Again by using Theorems 1 and 2, we have . For non-MVs, consider , then . So, for any -path , the influence of . By using Theorems 1 and 2, we have . Now, suppose , then . So, for any -path , the influence of . Again, by using Theorems 1 and 2, we have . Therefore, is a strong -pair. □
Theorem 5. Let be a VIG. Then, a vertex is called an -cut vertex of if for some .
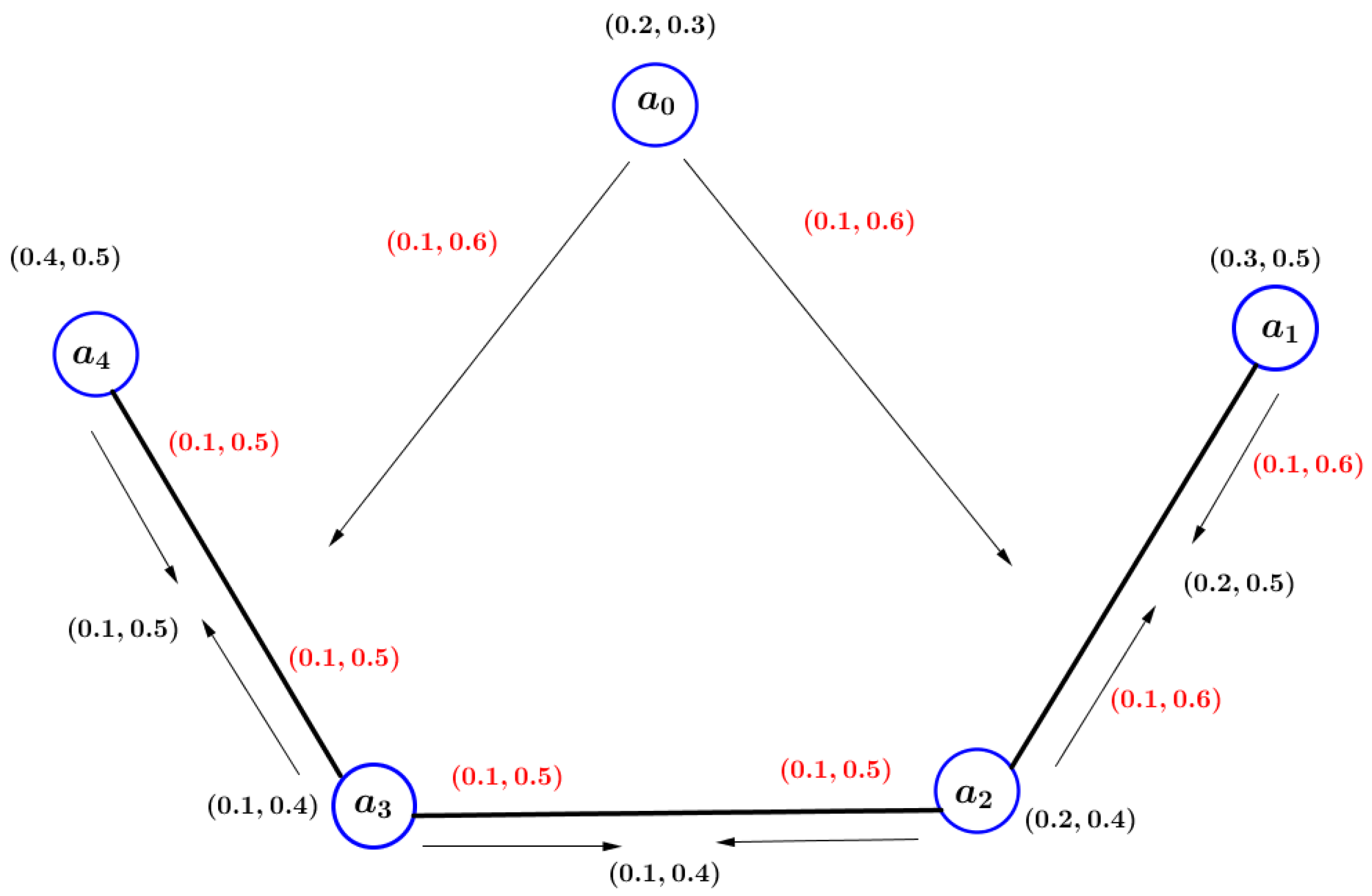
Example 3. Consider that is a VIG as shown in Figure 3. In this VIG, there are two -paths from to namely: and . For , , and for , Definition 21. Let be a VIG. Then, is described as VIG block if does not involve any cut vertex.
Theorem 6. Suppose is a VIG with an -pair . Then, the vertex deleted from the -pair is a cut vertex of .
Proof. Suppose is a VIG with an -pair . There is only one -path from m to namely having . Therefore, m is a -cut vertex. □
Definition 22. Let be a VIG. Then, an edge for each is called a bridge of if for some .
Definition 23. Let be a VIG. Then, is bridgeless if it involves no bridge.
Definition 24. Let be a VIG. Then, an -pair is defined to be an -CP of if for some .
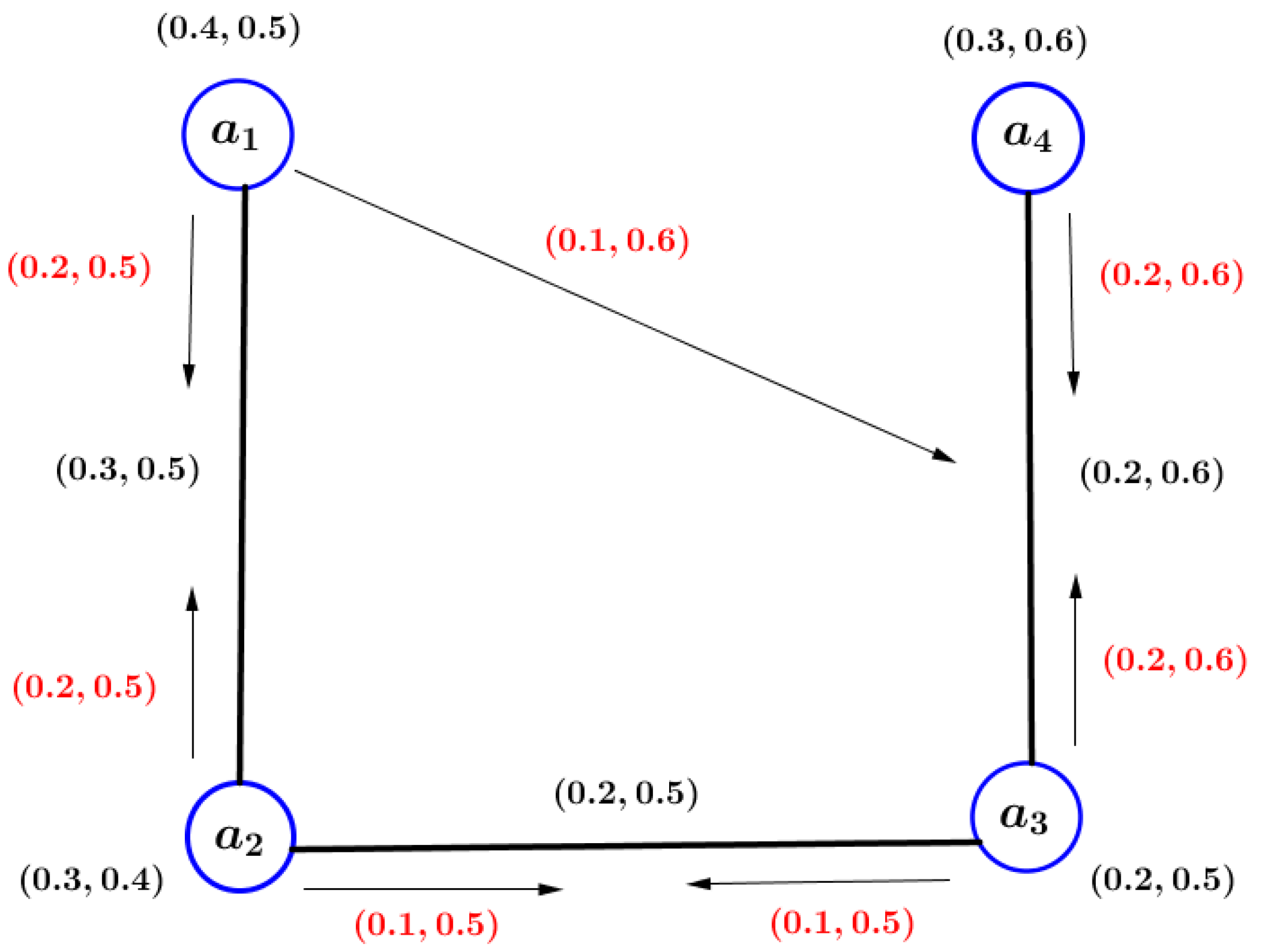
Example 4. Consider that is a VIG as shown in Figure 4. The MV and non-MV of pairs of VIG are shown in Table 1. In this VIG, there is only one -path from to , namely . If we delete the edge , we obtain . Hence, is an influence bridge. If we delete the -pair , we have . Hence, is an -CP.
Definition 25. A VIG is known as a complete VIG, if every vertex m has the influence on every edge with and .
Example 5. Consider that is a complete VIG as shown in Figure 5. The MV and non-MV of pairs of VIG are shown in Table 1. This is a complete VIG because has an influence on and . Similarly, has an influence on and . Furthermore, also, has an influence on and . Lastly, has an influence on and . This graph also has a vague fuzzy influence cycle.
Definition 26. Let be a VIG. Then, is a cycle if is a cycle, while is shown as a fuzzy cycle if is a cycle and it does not contains a unique such that . The VIG is known as a VIG cycle if it does not contains a unique -pair so that and .
Theorem 7. Let be a VIG. If is complete, then each -pair of is a CP.
Proof. Let be a complete VIG. If we remove any vertex from , then it must reduce the -connectivity between two vertices or between the vertex and edge. Assume any three vertices and l makes a complete VIG. If we remove a vertex m from , we obtain . Therefore, if is complete, then each pair of is a CP. □
Theorem 8. Let be a VIG. Then, a pair is an -pair CP if and only if the removal of the pair reduces the -connectivity between m and .
Proof. Let be a VIG. Suppose is the -CP in . Now, by using the definition, we have . From all the -paths , the path will have the MA-influenced strength, namely . So, it is clear that by removing the -pair the -connectivity between m and will be reduced.
Conversely, if we have , then by the definition, it shows that the pair is an -CP of . □
Definition 27. Let be a VIG with any three vertices and l. A vertex m dominates the vertex l if . A subset of the set X is called a strong -pair DS, if for each such that m dominates l.
Definition 28. Let be a VIG. Then, the degree of vertex m in is represented by and is described as , where and , where .
Definition 29. Let be a VIG. Then, the minimum(MI) degree of is represented by and is described as , .
Definition 30. Let be a VIG. Then, the MA degree of is represented by and is described as , .
Definition 31. Let be a VIG. Then, the order of is shown by and is described as Definition 32. Let be a VIG. Then, the size of is shown by and is defined as , where and , where .
Definition 33. Let be a VIG. A strong -pair DS is known as a MIL strong -pair DS if no proper subset of is a strong -pair DS.
Definition 34. Let be a VIG. The MI strong -pair domination number obtained from all MIL strong -pair SDs and is represented by .
Definition 35. Let be a VIG. Then, the MI number of elements in the MIL strong -pair DS is shown by , where , is a MIL strong -pair DS.
Theorem 9. Suppose that is a VIG. If is complete, then .
Proof. Suppose that is a DS. Let and . As is a complete VIG, so each -pair is an effective -pair, then by using the Theorem 7, every -pair is a CP. Now, by using Theorem 8, every CP is a strong -pair as it decreases the -connectivity between and . It implies that dominates each . It shows that is a MIL strong -pair DS. Therefore, □
4. Application: Recognition of Companies Participating in Illegal Drug Trade
Graph theory has expanded greatly as a result of a wide variety of applications in optimization combinatorial issues, chemistry, physics and other fields. In this section, we describe a real-world application of VIGs.
Currently, the illegal drug trade is seen as a high-risk, high-reward dirty industry. It is estimated that arms, medicine, drugs, alcohol and tobacco are the five largest illegal businesses in the world. The drug trade is a big business that generates billions of dollars in illegal income. Criminals mostly design many creative methods of illegal drug transportation, focusing on buying and selling. It is hard to find hidden ways to enforce the law, so the police must be aware of the latest illegal trends. For the drug trading market, we can use VIG to highlight the safest path chosen by the dangerous international networks of illegal drug trade between two companies and can also announce its removal, which reduces the safety of that route.
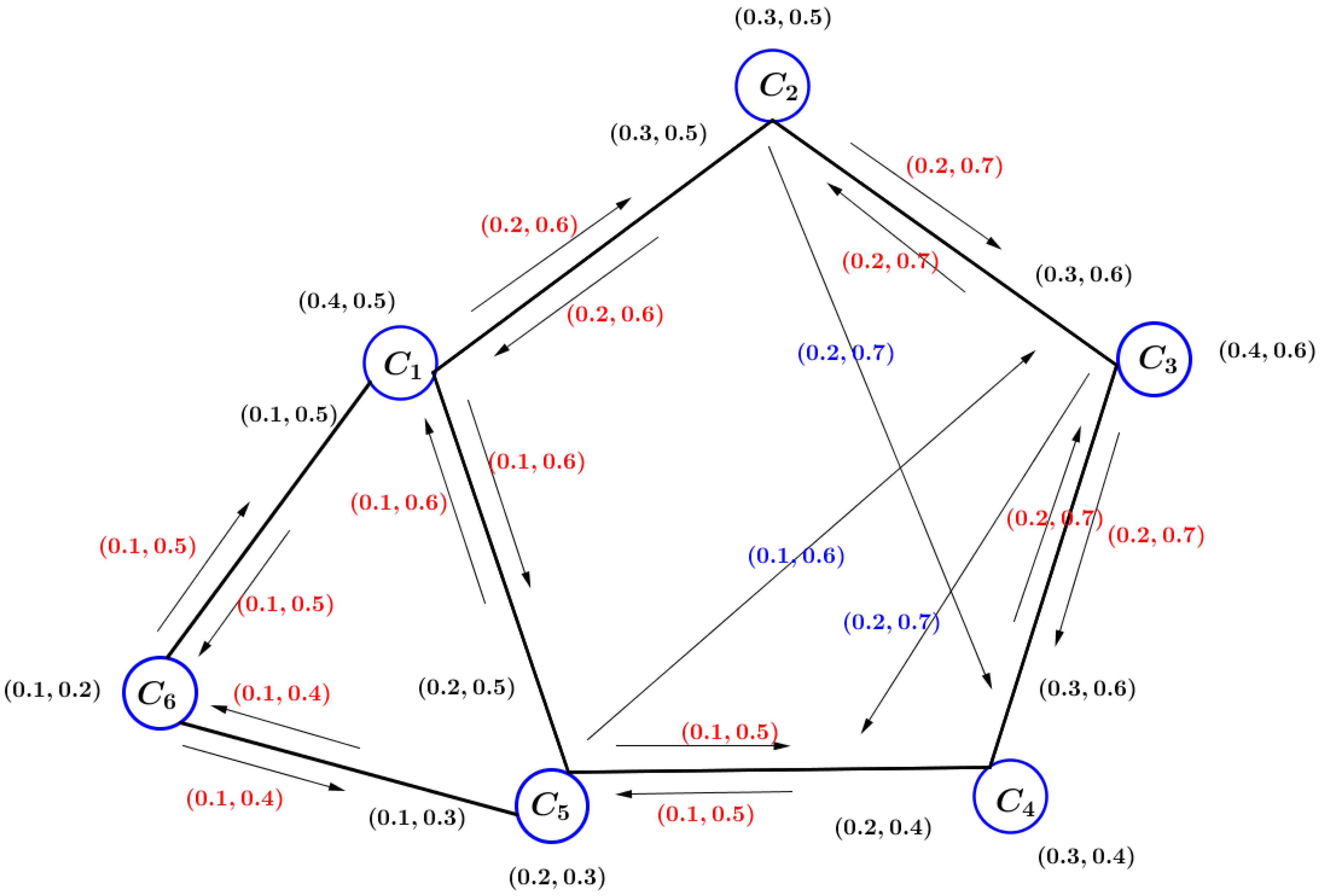
Consider how many companies in the world take part illegal drug trade, which is a major threat to humans, in the following series:
(see in
Figure 6). VIG
defined on set
X is presented in
Table 2.
In
Table 2,
shows law enforcement efforts of the company for illegal drug trade,
indicates the involvement of the company in organized illegal drug trade, and the neutral approach of the company to illegal drug trade can be considered as a degree of indeterminacy. We define VIG
in
Table 3. An element of VIG
represents illegal drug trade between those two companies.
In
Table 3,
shows the rate of illegal drug trade between companies, and
shows the rate of the world’s negative effect for that illegal drug trade.
Consider that
and
represent the degree of safety and degree of risk for illegal drug trade, respectively, to use
as a source company, relationship on
and arrive at destination company
. Similarly, the MV and non-MV of the other pairs of VIG are shown in
Table 4.
The interesting thing is that there are multiple -paths between every two vertices. Consider, we are finding the -paths from to , thus all possible are as follows:
The strengths of these -pairs are given by
, , ,
, , .
The t- strength and f- strength of connectedness are given by
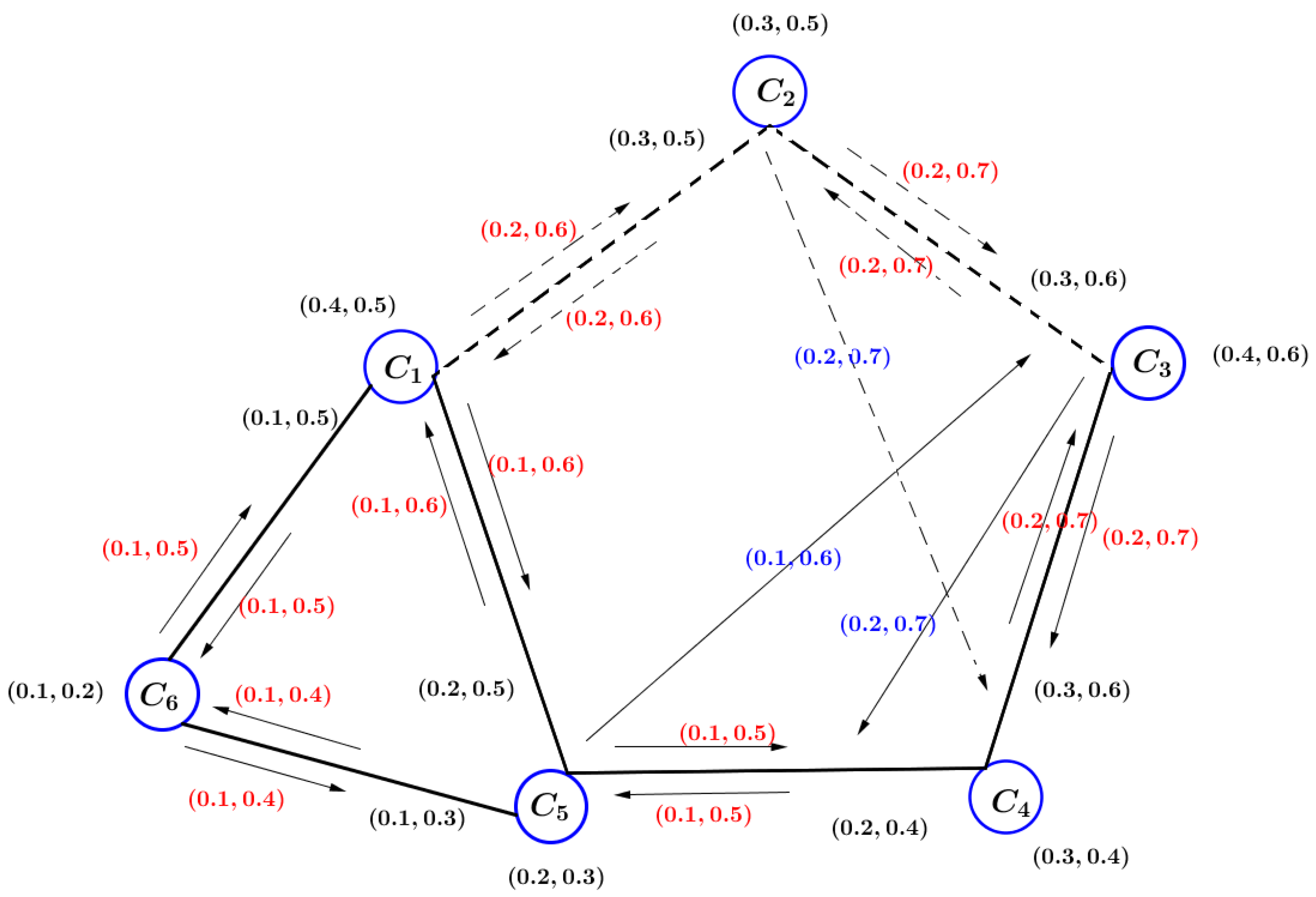
Here, we consider that if the connection between companies is reduced, the amount of illegal drug trade will decrease. Let us remove
and
of VIG
, as shown in
Figure 7. Then,
Therefore, the removal of
and
decreases the safety of the path.
Comparative Analysis
We want to eliminate the safest route through which the dangerous international drug trade networks between two companies conduct their interactions. Therefore, we need to check this application with the VIG graph. In this section, we considered six companies that have the most illegal interactions with each other and that these companies have caused an increase in illegal drug trade due to their interactions with each other. Each of the paths shows the rate of illegal drug trade between companies and rate of the world’s negative effect for that illegal drug trade. Here, we consider that if the connection between companies is reduced, the amount of illegal drug trade will be reduced. First, we chose two companies and . There are several routes between these two companies that we are finding in the -paths from to . Then, we obtained the strength and strength of connectedness. By removing the route that had the most power of penetration and connection between the two companies, the safety of the route decreased, so by reducing the interactions between the companies, the amount of illegal drug trade can be prevented.