Abstract
This paper investigates the problem of interval estimation for cyber–physical systems with unknown disturbance. In order to realize the interval estimation of cyber–physical systems, two technical methods are adopted. The first one requires the observer dynamic error system to be non-negative, and the second one relaxes this limitation by coordinate transformation. The sufficient conditions are established using both Lyapunov stability and positive system theory. Furthermore, according to the Schur complement, the linear matrix inequality is solved to determine the observer gains. Finally, the effectiveness and feasibility of the designed interval observer are verified by one numerical simulation.
MSC:
93D05; 93D09
1. Introduction
In the last two decades, there has been a great deal of research in observer design. These results lay a good foundation for the further study of the interval observer (IO), so the research of the IO has received extensive attention in recent years. Ref. [1] first introduced the concept of the IO, and the basic frame of the IO was given. Because there are always unknown but bounded perturbations and uncertainties in real systems, Refs. [2,3] studied two different classes of uncertain biological systems and designed the corresponding IO for each of them. The precondition for the IO to be effective is that the upper and lower error systems are both positive and uniformly bounded. In order to relax this condition, Ref. [4] first applied the coordinate transformation method to the interval estimation for time-varying systems and then [5] introduced this method for time-invariant systems. Under these methods, the design of the IO got more freedom. Since then, some researchers studied the IO design problem for nonlinear uncertain switched systems [6], singular systems [7] and impulse systems [8]. Ref. [9] provided an interval estimation method for discrete-time systems with uncertain inputs. Ref. [10] proposed IOs for nonlinear discrete-time systems. Ref. [11] designed a distributed interval observer for multiple Euler–Lagrange systems. In addition, there were other reports on interval observers, such as [12,13,14] and so on.
A cyber–physical system (CPS) is a typical complex system in an intelligent system. It closely integrates computing elements and physical processes to realize real-time interaction and control [15]. Among them, the main research hotspots of CPSs are state security estimation and state reconstruction under network attacks. In response to the issue of sparse sensor attacks in CPSs, Ref. [16] built a Luenberger switching observer for state estimation. Ref. [17] constructed a new observer to reduce the influence of unknown inputs by means of the gain method. Ref. [18] proposed an elastic attack detection estimator to complete security estimation and attack detection under both false data injection attacks and interference attacks. Ref. [19], based on the time differential equation and uncertainty hybrid time automaton, extended the CPS system model and established the uncertain CPS extended model. Ref. [20] provided an algorithm for building indeterminate finite-state sensors for CPSs, thus restoring the original state under attack. At present, there are few studies on the security estimation of CPSs with nonlinear term and disturbance. And the IO is an effective tool to study the state estimation method for uncertain systems with bounded disturbance. Therefore, applying the IO to such a CPS can effectively address the issue of security estimation.
Based on the above discussion, the problem of IO design for a CPS is investigated in this paper. We mainly use the monotone system method to formulate the framework of the IO; in addition, we employ the coordinate transformation method to address the situation where the error system is not cooperative. This paper is structured as follows: In Section 2, the relevant basic theory and CPS model framework are given. Section 3 gives the design method of the IO for the CPS. In Section 4, we conduct a simulation using MATLAB to illustrate the effectiveness of IO design. Section 5 is the summary of the article.
Notaion: For a matrix , means for all and . In the case of a matrix , and are defined as and . Moreover, the matrix is positive (negative) definite and can be expressed as .
2. Preliminaries
In this paper, a class of CPS models with disturbance is considered as follows:
where and are the state and output, and denotes the control input. and are the unknown process noise and measurement error, and is a nonlinear function. , , , and are given constant matrices.
Assumption 1.
The disturbance and measurement error in system (1) are bounded, i.e.,
where , , and are constant vectors.
Assumption 2.
For a function , there exists a Lipschitz constant α if for any of its domain Ω there exists α, such that the following holds:
Then, satisfies the Lipschitz continuity condition.
Lemma 1
([21]). If the Lipschitz function is globally differentiable, then it can be decomposed into the difference of two globally differentiable Lipschitz functions and , and they are two increasing functions with respect to x, such that:
Lemma 2
([21]). For any global Lipschitz function , there is a global differentiable Lipschitz function such that
From Lemmas 1 and 2, we have upper and lower bound information for the nonlinear Lipschitz function :
Lemma 3
([21]). For the global Lipschitz function and the associate function defined in Lemma 2, the variable x satisfies the bounded condition: . If is bounded, then there are matrices such that
where , , and are known matrices.
Lemma 4
([22]). There exists a vector g such that , for any matrix , and then:
Lemma 5
([23]). The following systems
where is a non-negative matrix, and the nonlinear function . Then, for all , we have .
Lemma 6
([24]). Given a positive constant α and two arbitrary matrices , the matrix and the following inequality holds:
Definition 1.
If there exist positive constants r and b, for the following error system
with initial conditions , and for all , we have , and then the error system is called uniformly ultimately bounded (UUB).
3. Main Results
3.1. Design of the IO
Based on Section 2, we design the following IO for system (1):
where and are the estimated upper and lower bounds of the state . , , and . The specific calculation steps of gain L will be given in the sequel.
Theorem 1.
Suppose that is non-negative, and the initial condition of satisfies , then it holds that
Proof.
Denote that and , and then one obtains the error system:
where , , and . In view of Lemma 4, then , , and . Also, according to Lemma 5, we can conclude that
□
Continuing Theorem 1, it is assumed that is non-negative. Denote , and according to (11), the error system has the following form:
where
Theorem 2.
Given a set of constants and λ satisfy . Suppose that both Assumptions 1 and 2 hold. If there exists such that
where
and
Then, system (9) is UUB, i.e., the error system is eventually bounded upper and lower.
Proof.
Choosing the Lyapunov function , then we derive from that
Define that
It is derived from Lemma 6 that
Thus,
From Lemma 3, we can deduce that
Substituting (18) into (17), then
Define that
Therefore, we can obtain
then
According to Assumption 1, letting , by iteration, one can obtain
where satisfies , and according to Definition 1, then system (9) is UUB, and system (9) is the interval observer of system (1). □
3.2. IO Design by Coordinates Transformation Method
Under the condition that is not non-negative, to facilitate the design of the IO, we can adopt the method of coordinate transformation. Let , where is invertible, and system (1) can be equivalent to:
where , , , and , and the transformation M is chosen such that satisfies the non-negative.
Remark 1.
The transformation matrix M can be constructed according to the Sylvester equation, and based on the transformation of the Schur form, so as to obtain T through the inverse substitution. The specific selection process can be referred to in [5].
To facilitate the estimation of the bounds for by denoting that
where and are defined as the upper and lower bound estimates of the designed IO for , and .
According to Lemma 4, the nonlinear function can satisfy the following inequality
and define that
Remark 2.
Because the transformation matrix T is invertible and is known to satisfy the initial condition (30), and satisfies , we have
where
Remark 3.
The observed values of the system after coordinate transformation meet the requirements of the original system:
The specific proof process can be referred to in [4].
Theorem 3.
If is not non-negative, we can find a matrix M such that in error system (33) is non-negative, and the initial condition of satisfies , and then it holds that
Define that and . Therefore, the error system can be derived as:
where , , and .
In view of Lemma 4, then , , and . The initial condition of satisfies , and according to Remark 2, we can obtain that the initial condition of satisfies . Finally, according to Lemma 5, we can conclude that
The proof of Theorem 3 has finished.
Theorem 3 only provides the IO frame for system (1). In order to make the error system UUB, i.e., system (26) becomes an IO of system (24), the sufficient conditions and specific proof are given below.
Theorem 4.
Given a set of constants and λ satisfy . Suppose that both Assumptions 1 and 2 hold. If there exists such that
where
and
Then, system (26) is UUB, i.e., the error system is eventually upper and lower bounded.
Proof.
Choosing the Lyapunov function , then we derive from that
Define that
It is derived from Lemma 6 that
Thus,
From Lemma 3, we can deduce that
Substituting (40) into (39), then
Define that
Therefore, we can obtain
Letting the eigenvalues of P be . , then
where
according to Assumption 1. We know that and are bounded; then, let and plug it into inequality (44).
If here satisfies , then
then
so
□
According to Definition 1, then system (26) is UUB. Moreover, both the upper and lower errors eventually obtained by the error system are bounded, which completes the proof of Theorem 4.
Remark 4.
The designed IO can be successfully applied to the CPS without attacks, and the bounds of the system states can be reconstructed. Even if there exist attacks in the CPS, the accurate bounds of the system states can still be estimated for the purpose of the security problem.
4. Simulation
In order to verify the effectiveness of the IO design method, this section gives a specific numerical simulation of the CPS. We consider the unmanned ground vehicle system [25], whose dynamic equation can be written as:
where is the state of the car, s is the position of the car and is the speed of the car. and m represent the average friction coefficient and mass of the car, respectively. In the experiment, we choose and . At the same time, we consider the existence of certain nonlinear terms in the system, as well as the process noise and measurement errors. The parametric matrix of system (49) after discretization is:
In addition, the disturbance and measurement error parameters of the system are chosen as:
Meanwhile, the nonlinear function is expressed as:
The coordinate transformation matrix M and the constants , are selected
and then P and can be obtained as:
thus, L can be obtained by Theorem 3
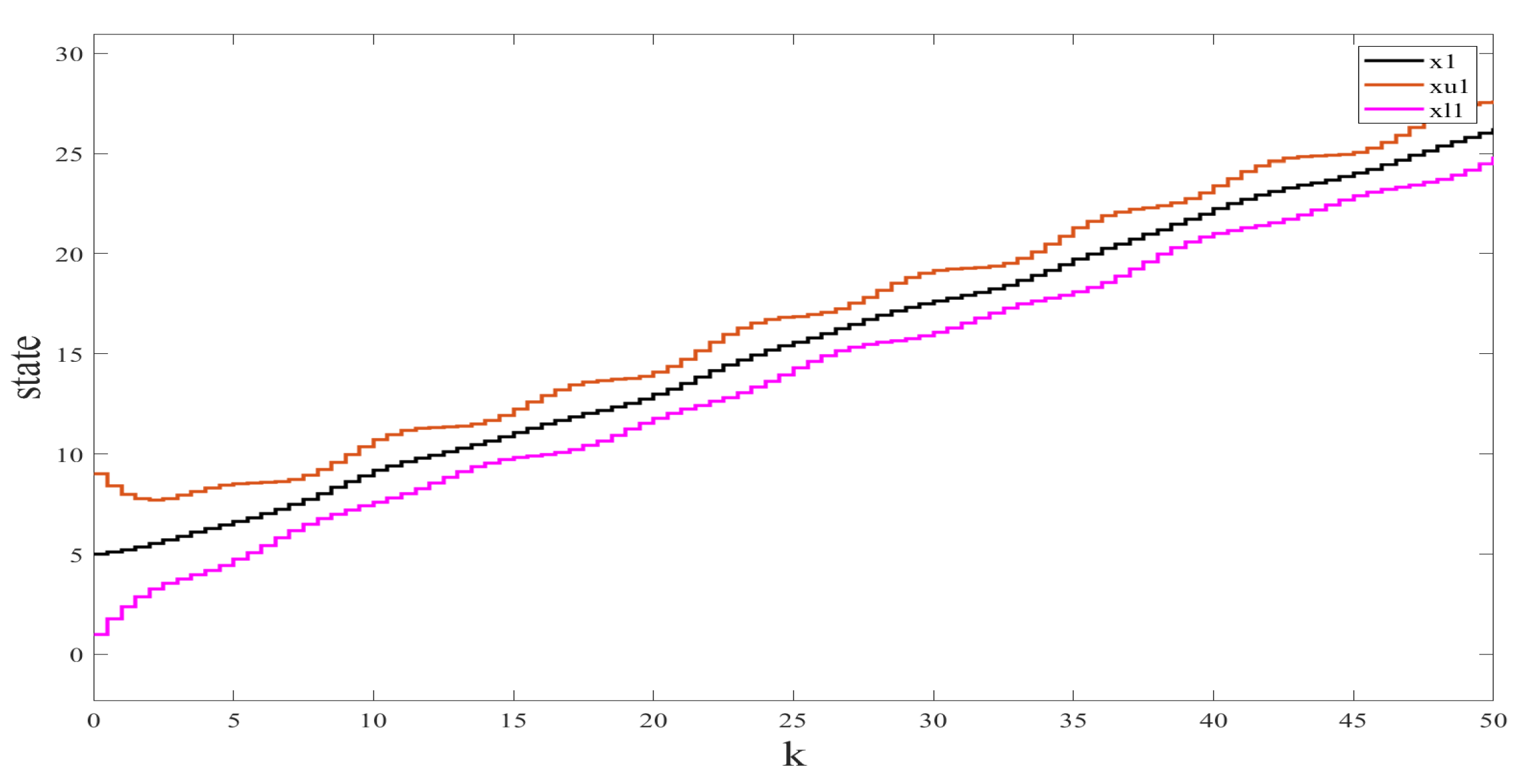
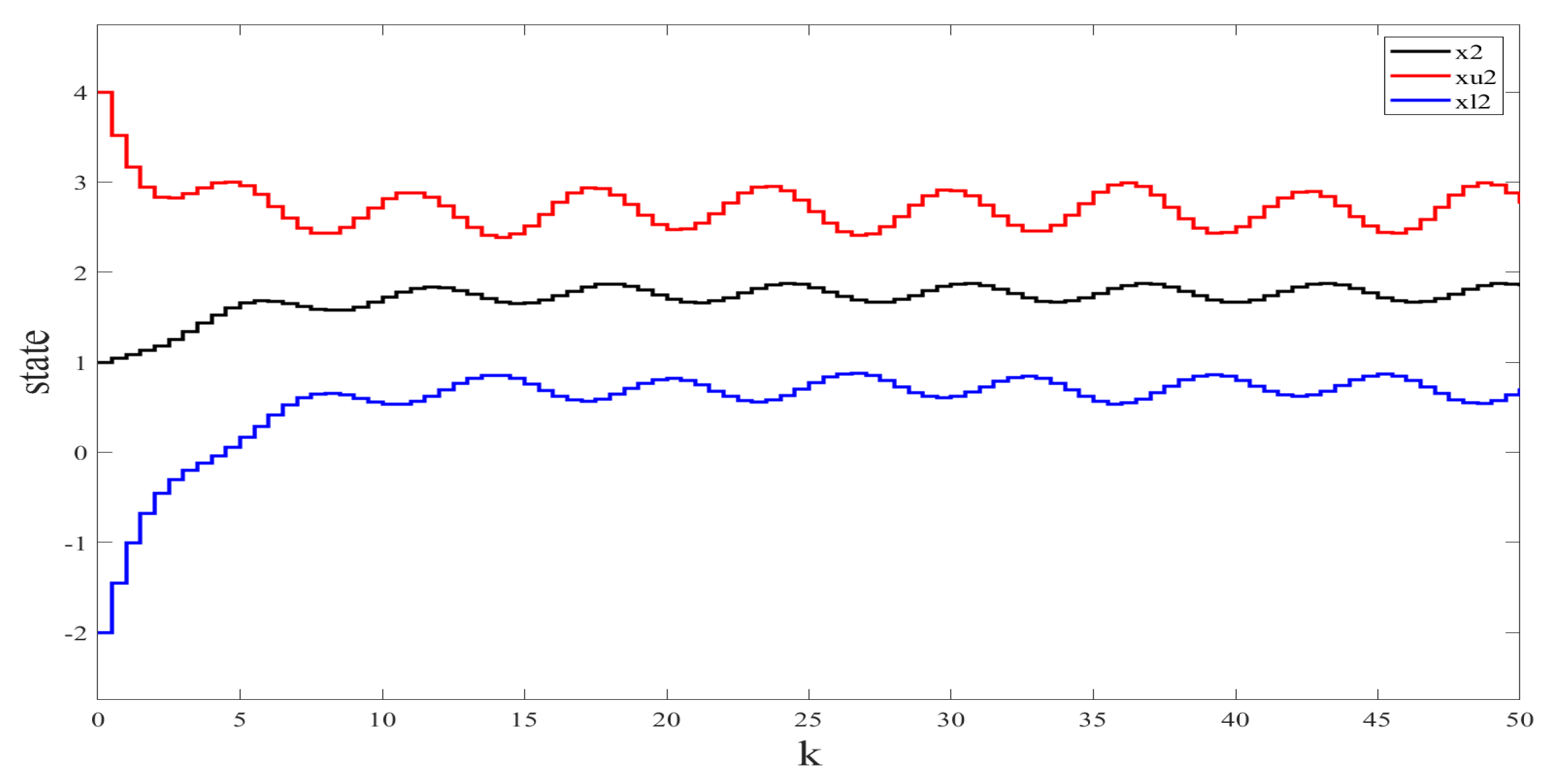
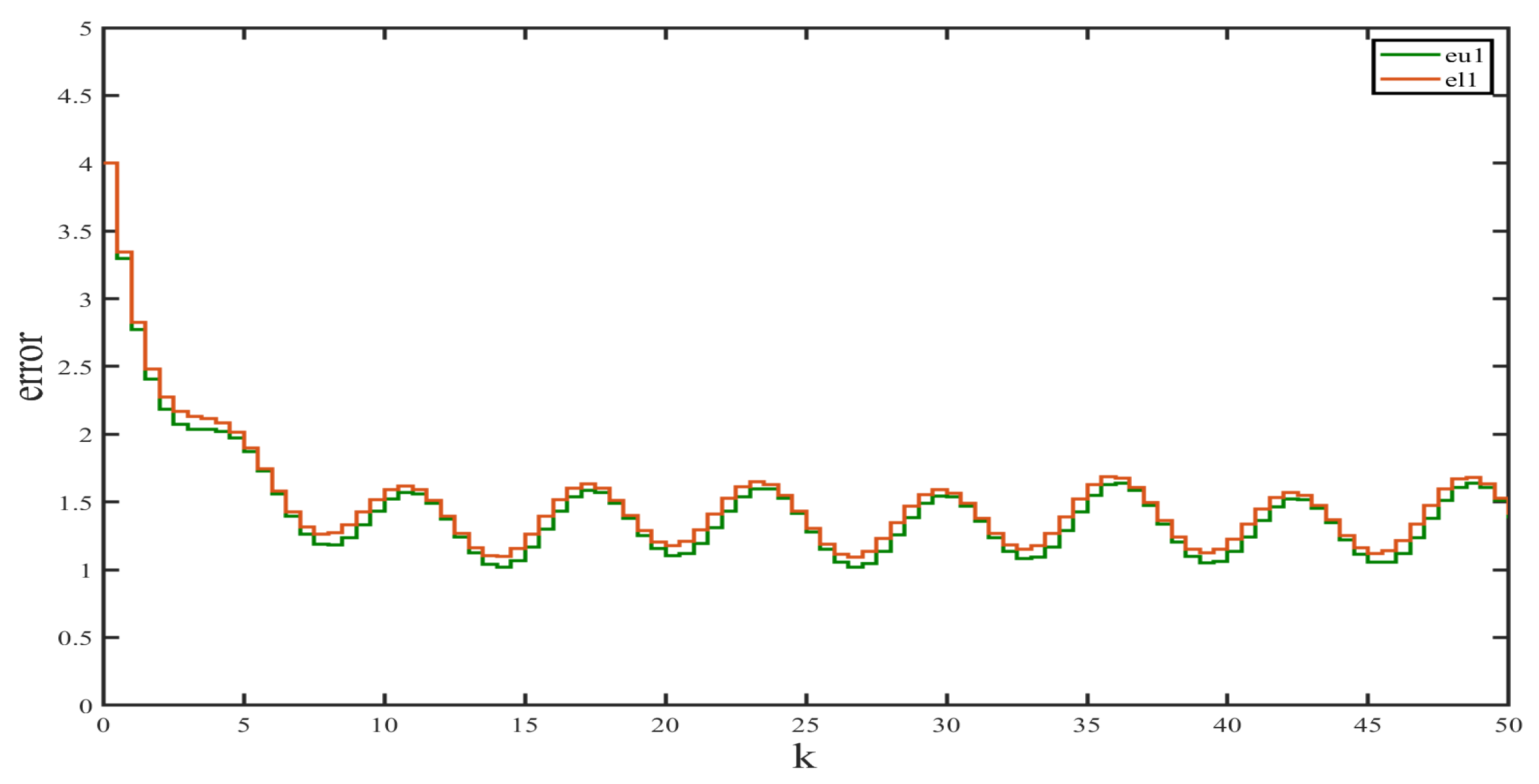
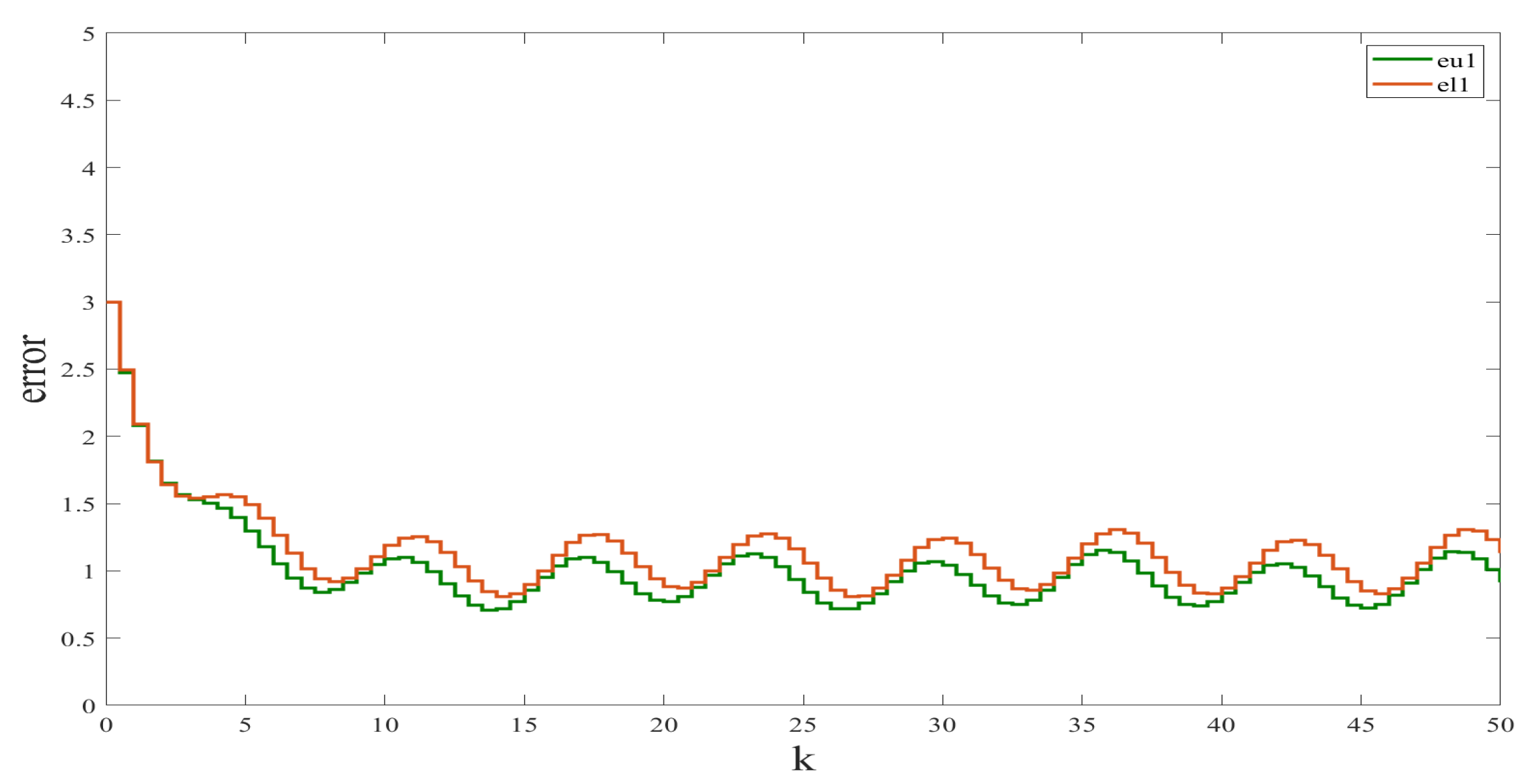
We used the Simulink Toolbox in Matlab to complete the simulation. Figure 1 and Figure 2 show the state and observation trajectories of the system, whose upper and lower bounds of the IO strictly satisfy . Figure 3 and Figure 4 illustrate the bounded convergence of the error system, which shows that the error system eventually converges to a bounded value greater than zero. Consequently, it can be inferred that the designed IO can strictly recover the bounds of the original system state. Therefore, we conclude that the designed IO is effective and feasible.
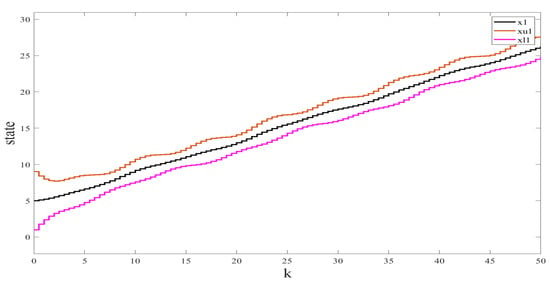
Figure 1.
The states (position ) of the original system and their interval estimates.
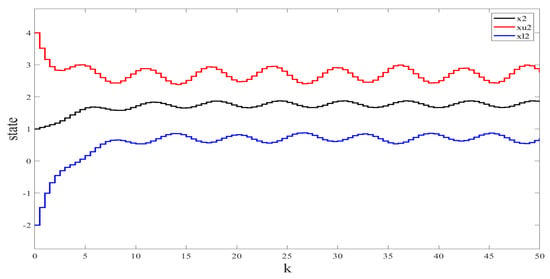
Figure 2.
The states (speed ) of the original system and their interval estimates.
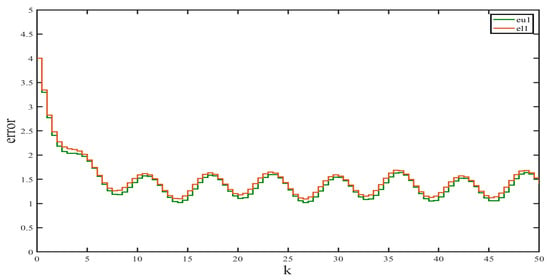
Figure 3.
Error in interval estimation of .
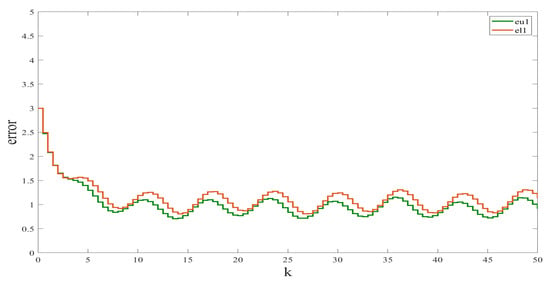
Figure 4.
Error in interval estimation of .
5. Conclusions
This paper presents an IO framework for a class of CPSs with disturbance. According to the state parameters of the original system, the frame of the IO was established based on the positive system theory. For the case that does not satisfy the non-negative property, the method of coordinate transformation was used to make non-negative, and the sufficient conditions for the system gain L to be satisfied were also derived. At the end, one example is simulated to verify the validity of the proposed method. Future attempts are verified by introducing interval estimation into the CPS with cyber attacks.
Author Contributions
Software, H.W.; validation, H.W.; writing—original draft preparation, Y.Q.; writing—review and editing, J.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Project of the Key Laboratory of AI and Information Processing (Hechi University), Education Department of Guangxi Zhuang Autonomous Region (2022GXZDSY015).
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Gouzé, J.; Rapaport, A.; Hadj-Sadok, M. Interval observers for uncertain biological systems. Ecol. Model. 2000, 133, 45–56. [Google Scholar] [CrossRef]
- Moisan, M.; Bernard, O. Interval observers for non monotone systems.application to bioprocess models. Ifac Proc. Vol. 2005, 16, 43–48. [Google Scholar] [CrossRef]
- Moisan, M.; Bernard, O.; Gouzé, J.L. Near optimal interval observers bundle for uncertain bioreactors. Automatica 2009, 45, 291–295. [Google Scholar] [CrossRef]
- Mazenc, F.; Bernard, O. Interval observers for linear time-invariant systems with disturbances. Automatica 2011, 47, 140–147. [Google Scholar] [CrossRef]
- Raissi, T.; Efimov, D.; Zolghadri, A. Interval state estimation for a class of nonlinear systems. IEEE Trans. Autom. Control 2012, 57, 260–265. [Google Scholar] [CrossRef]
- Xiang, W.; Xiao, J.; Iqbal, M.N. Robust observer design for nonlinear uncertain switched systems under asynchronous switching. Nonlinear Anal. Hybrid Syst. 2012, 6, 754–773. [Google Scholar] [CrossRef]
- Zheng, G.; Efimov, D.; Bejarano, F.J.; Perruquetti, W.; Wang, H. Interval observer for a class of uncertain nonlinear singular systems. Automatica 2016, 71, 159–168. [Google Scholar] [CrossRef]
- Degue, K.H.; Efimov, D.; Ny, J.L. Interval observer approach to output stabilization of linear impulsive systems. IFAC-PapersOnLine 2017, 50, 5085–5090. [Google Scholar] [CrossRef]
- Chevet, T.; Dinh, T.N.; Marzat, J.; Wang, Z.; Raïssi, T. Zonotopic kalman filter-based interval estimation for discrete-time linear systems with unknown inputs. IEEE Control Syst. Lett. 2022, 6, 806–811. [Google Scholar] [CrossRef]
- Tahir, A.M.; Açıkmeşe, B. Synthesis of interval observers for bounded jacobian nonlinear discrete-time systems. IEEE Control Syst. Lett. 2022, 6, 764–769. [Google Scholar] [CrossRef]
- Yin, Z.; Huang, J.; Dinh, T.N. Design of distributed interval observers for multiple Euler–lagrange systems. Mathematics 2023, 11, 1872. [Google Scholar] [CrossRef]
- Wang, Z.; Yin, H.; Dinh, T.N.; Raïssi, T. Interval estimation based on the reduced-order observer and peak-to-peak analysis. Int. J. Control 2022, 95, 2876–2884. [Google Scholar] [CrossRef]
- Zhang, H.; Huang, J.; He, S. Fractional-order interval observer for multiagent nonlinear systems. Fractal Fract. 2022, 6, 355. [Google Scholar] [CrossRef]
- Yin, Z.; Huang, J.; Zhang, Y. Event-triggered interval observer design for a class of Euler-lagrange systems with disturbances. Trans. Inst. Meas. Control 2023. [Google Scholar] [CrossRef]
- Cao, X.; Cheng, P.; Chen, J.; Sun, Y. An online optimization approach for control and communication codesign in networked Cyber-physical systems. IEEE Trans. Ind. Inform. 2013, 9, 439–450. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. Secure state estimation for Cyber-physical systems under sparse sensor attacks via a switched Luenberger observer. Inf. Sci. 2017, 417, 454–464. [Google Scholar] [CrossRef]
- Xie, C.H.; Yang, G. Secure estimation for Cyber-physical systems with adversarial attacks and unknown inputs: An L2-gain method. Int. J. Robust Nonlinear Control 2018, 28, 2131–2143. [Google Scholar] [CrossRef]
- Yang, Y.; Li, Y.; Yue, D.; Tian, Y.C.; Ding, X. Distributed secure consensus control with event-triggering for multiagent systems under doS attacks. IEEE Trans. Cybern. 2021, 51, 2916–2928. [Google Scholar] [CrossRef]
- Chen, N.; Geng, S.; Li, Y. Modeling and verification of uncertain Cyber-physical system based on decision processes. Mathematics 2023, 11, 4122. [Google Scholar] [CrossRef]
- Labed, A.; Saadaoui, I.; E, H.; El-Meligy, M.A.; Li, Z.; Sharaf, M. Language recovery in discrete-event systems against sensor deception attacks. Mathematics 2023, 11, 2313. [Google Scholar] [CrossRef]
- Moisan, M.; Bernard, O. Robust interval observers for global Lipschitz uncertain chaotic systems. Syst. Control Lett. 2010, 59, 687–694. [Google Scholar] [CrossRef]
- Efimov, D.; Raïssi, T.; Zolghadri, A. Control of nonlinear and LPV systems: Interval observer-based framework. IEEE Trans. Autom. Control 2013, 58, 773–778. [Google Scholar] [CrossRef]
- Guo, S.; Zhu, F. Interval observer design for discrete-time switched system. IFAC-PapersOnLine 2017, 50, 5073–5078. [Google Scholar] [CrossRef]
- Huang, J.; Fan, J.; Dinh, T.N.; Zhao, X.; Zhang, Y. Event-triggered interval estimation method for Cyber-physical systems with unknown inputs. Isa Trans. 2022, 135, 1–12. [Google Scholar] [CrossRef]
- Shoukry, Y.; Nuzzo, P.; Puggelli, A.; Sangiovanni-Vincentelli, A.L.; Seshia, S.A.; Tabuada, P. Secure state estimation for Cyber-physical systems under sensor attacks: A satisfiability modulo theory approach. IEEE Trans. Autom. Control 2017, 62, 4917–4932. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).